目标信息
IP地址:
10.10.10.48
信息收集
ICMP检测
┌──(root㉿misaka19008)-[/home/…/Documents/pentest_notes/mirai/nmap_reports]
└─# ping -c 4 10.10.10.48
PING 10.10.10.48 (10.10.10.48) 56(84) bytes of data.
64 bytes from 10.10.10.48: icmp_seq=1 ttl=63 time=264 ms
64 bytes from 10.10.10.48: icmp_seq=2 ttl=63 time=266 ms
64 bytes from 10.10.10.48: icmp_seq=3 ttl=63 time=265 ms
64 bytes from 10.10.10.48: icmp_seq=4 ttl=63 time=266 ms
--- 10.10.10.48 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3238ms
rtt min/avg/max/mdev = 263.531/265.051/265.804/0.901 ms攻击机和靶机之间通信状态良好。
防火墙检测
# Nmap 7.94SVN scan initiated Sat Jul 20 21:04:03 2024 as: nmap -sF -p- --min-rate 2000 -oN ./fin_result.txt 10.10.10.48
Warning: 10.10.10.48 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.48 (10.10.10.48)
Host is up (0.30s latency).
Not shown: 65529 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open|filtered ssh
53/tcp open|filtered domain
80/tcp open|filtered http
1402/tcp open|filtered prm-sm-np
32400/tcp open|filtered plex
32469/tcp open|filtered unknown
# Nmap done at Sat Jul 20 21:05:08 2024 -- 1 IP address (1 host up) scanned in 64.77 seconds靶机开放了6个TCP端口。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Sat Jul 20 21:09:12 2024 as: nmap -sS -sV -A -p 22,53,80,1402,32400,32469 -oN ./tcp_result.txt 10.10.10.48
Nmap scan report for 10.10.10.48 (10.10.10.48)
Host is up (0.24s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
| ssh-hostkey:
| 1024 aa:ef:5c:e0:8e:86:97:82:47:ff:4a:e5:40:18:90:c5 (DSA)
| 2048 e8:c1:9d:c5:43:ab:fe:61:23:3b:d7:e4:af:9b:74:18 (RSA)
| 256 b6:a0:78:38:d0:c8:10:94:8b:44:b2:ea:a0:17:42:2b (ECDSA)
|_ 256 4d:68:40:f7:20:c4:e5:52:80:7a:44:38:b8:a2:a7:52 (ED25519)
53/tcp open tcpwrapped
80/tcp open http lighttpd 1.4.35
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: lighttpd/1.4.35
1402/tcp open upnp Platinum UPnP 1.0.5.13 (UPnP/1.0 DLNADOC/1.50)
32400/tcp open http Plex Media Server httpd
|_http-cors: HEAD GET POST PUT DELETE OPTIONS
|_http-favicon: Plex
| http-auth:
| HTTP/1.1 401 Unauthorizedx0D
|_ Server returned status 401 but no WWW-Authenticate header.
|_http-title: Unauthorized
32469/tcp open upnp Platinum UPnP 1.0.5.13 (UPnP/1.0 DLNADOC/1.50)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.18 (96%), Linux 3.2 - 4.9 (96%), Linux 3.16 (95%), Linux 3.12 (95%), Linux 3.13 (95%), Linux 3.8 - 3.11 (95%), Linux 4.2 (95%), ASUS RT-N56U WAP (Linux 3.4) (95%), Linux 4.4 (95%), Linux 4.8 (94%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 32469/tcp)
HOP RTT ADDRESS
1 312.38 ms 10.10.14.1 (10.10.14.1)
2 312.44 ms 10.10.10.48 (10.10.10.48)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Jul 20 21:09:48 2024 -- 1 IP address (1 host up) scanned in 36.37 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Sat Jul 20 21:13:06 2024 as: nmap -sU -p- --min-rate 2000 -oN ./udp_ports.txt 10.10.10.48
Warning: 10.10.10.48 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.48 (10.10.10.48)
Host is up (0.75s latency).
Not shown: 65163 open|filtered udp ports (no-response), 366 closed udp ports (port-unreach)
PORT STATE SERVICE
53/udp open domain
123/udp open ntp
5353/udp open zeroconf
32414/udp open unknown
38276/udp open unknown
54591/udp open unknown
# Nmap done at Sat Jul 20 21:19:26 2024 -- 1 IP address (1 host up) scanned in 379.67 secondsUDP端口详细信息扫描结果
# Nmap 7.94SVN scan initiated Sat Jul 20 21:22:02 2024 as: nmap -sC -sU -sV -A -p 53,123,5353,32414,38276,54591 -oN ./udp_result.txt 10.10.10.48
Nmap scan report for 10.10.10.48 (10.10.10.48)
Host is up (0.24s latency).
PORT STATE SERVICE VERSION
53/udp open domain dnsmasq 2.76
|_dns-recursion: Recursion appears to be enabled
123/udp open ntp NTP v4 (unsynchronized)
| ntp-info:
|_
5353/udp open mdns DNS-based service discovery
| dns-service-discovery:
| 9/tcp workstation
| Address=10.10.10.48 dead:beef::c02b:b52b:ff16:c5ef
| 22/tcp udisks-ssh
|_ Address=10.10.10.48 dead:beef::c02b:b52b:ff16:c5ef
32414/udp open unknown
38276/udp closed unknown
54591/udp closed unknown
Too many fingerprints match this host to give specific OS details
Network Distance: 2 hops
Host script results:
|_clock-skew: 12s
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 317.31 ms 10.10.14.1 (10.10.14.1)
2 25.98 ms 10.10.10.48 (10.10.10.48)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Jul 20 21:24:16 2024 -- 1 IP address (1 host up) scanned in 134.21 seconds同时发现靶机操作系统为Debian Linux。
服务探测
SSH服务(22端口)
端口Banner:
┌──(root㉿misaka19008)-[/home/megumin/Documents/pentest_notes/mirai]
└─# nc -nv 10.10.10.48 22
(UNKNOWN) [10.10.10.48] 22 (ssh) open
SSH-2.0-OpenSSH_6.7p1 Debian-5+deb8u3DNS服务(53端口)
尝试使用DNS区域传输功能:
dig axfr @10.10.10.48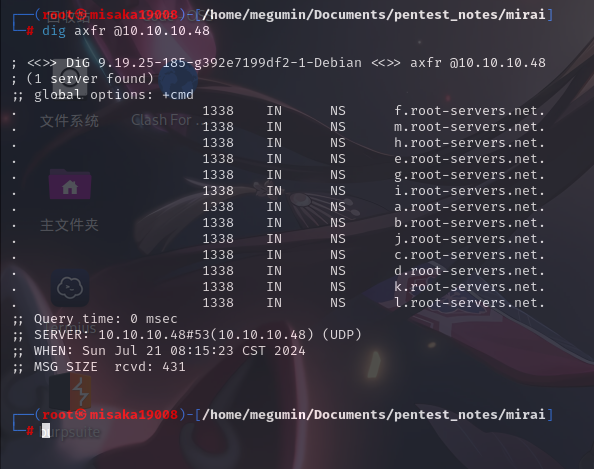
除此之外未发现其它有效信息。
Web应用程序(80端口)
打开主页:http://10.10.10.48/
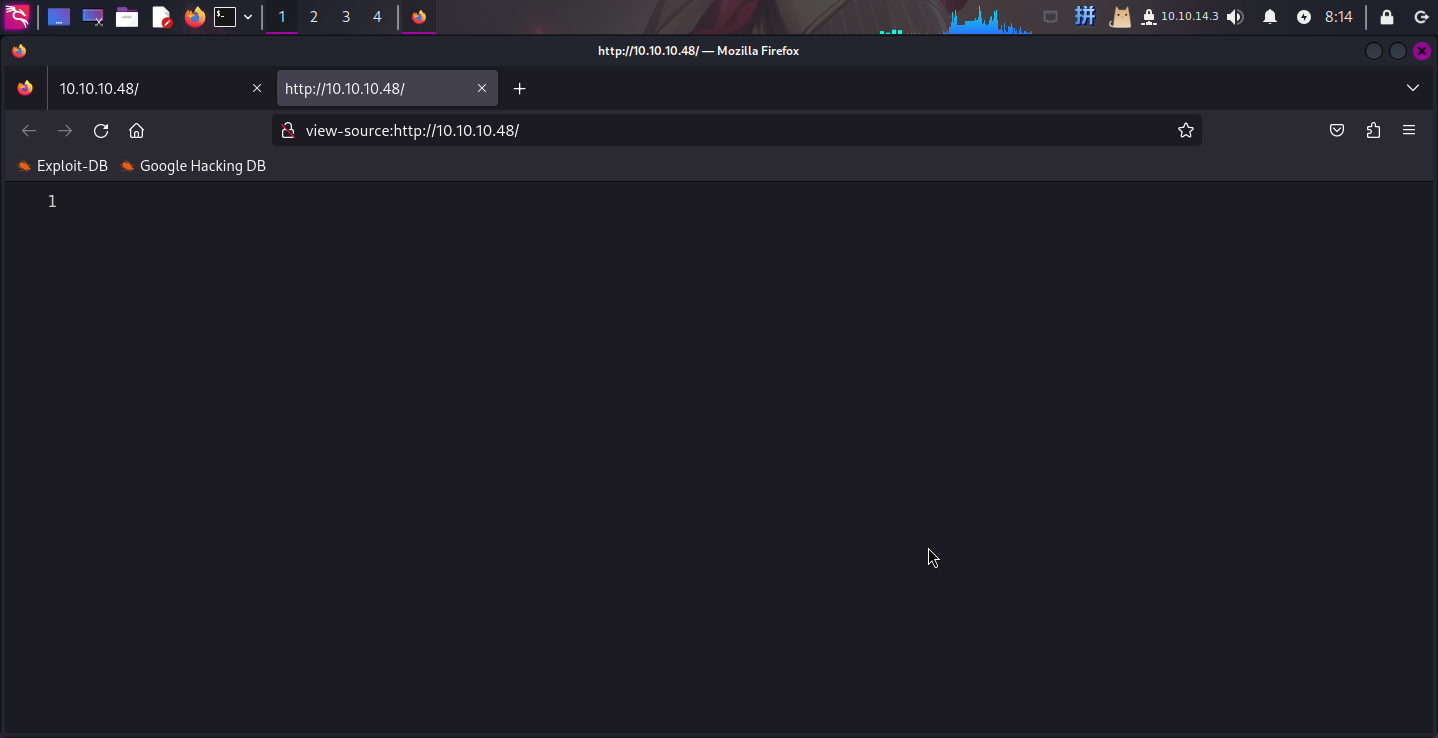
发现主页上没有任何内容,但是在响应头中发现一项奇怪的内容:
HTTP/1.1 404 Not Found
X-Pi-hole: A black hole for Internet advertisements.
Content-type: text/html; charset=UTF-8
Content-Length: 0
Date: Mon, 22 Jul 2024 00:16:27 GMT
Server: lighttpd/1.4.35直接扫描目录:
# Dirsearch started Mon Jul 22 08:35:40 2024 as: /usr/lib/python3/dist-packages/dirsearch/dirsearch.py -u http://10.10.10.48/ -x 400,403,404,500 -e php,js,html,txt,zip,tar.gz,asp,aspx,pcap -t 60 -w /usr/share/wordlists/wfuzz/general/megabeast.txt
301 0B http://10.10.10.48/admin -> REDIRECTS TO: http://10.10.10.48/admin/
200 13B http://10.10.10.48/versions发现/versions文件,内容为:
1721607651,,,访问/admin目录,发现部署了广告拦截系统Pi-Hole,版本为v3.1.4,有可能存在授权命令执行漏洞:
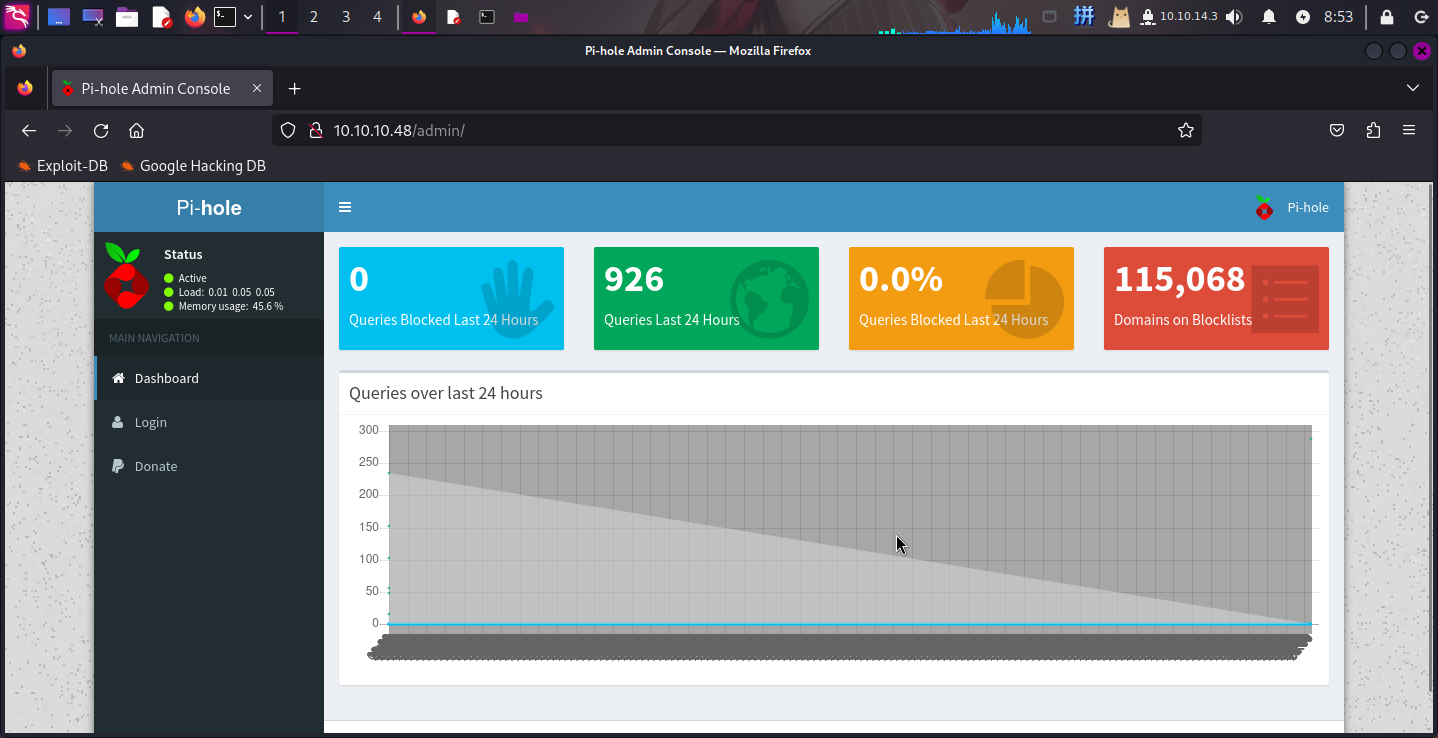
尝试扫描该目录:
# Dirsearch started Mon Jul 22 08:48:16 2024 as: /usr/lib/python3/dist-packages/dirsearch/dirsearch.py -u http://10.10.10.48/admin -x 400,403,404,500 -e php,js,html,txt,zip,tar.gz,asp,aspx,pcap -t 60
301 0B http://10.10.10.48/admin/.git -> REDIRECTS TO: http://10.10.10.48/admin/.git/
200 23B http://10.10.10.48/admin/.git/HEAD
301 0B http://10.10.10.48/admin/.git/logs/refs -> REDIRECTS TO: http://10.10.10.48/admin/.git/logs/refs/
301 0B http://10.10.10.48/admin/.git/logs/refs/remotes -> REDIRECTS TO: http://10.10.10.48/admin/.git/logs/refs/remotes/
301 0B http://10.10.10.48/admin/.git/refs/remotes -> REDIRECTS TO: http://10.10.10.48/admin/.git/refs/remotes/
301 0B http://10.10.10.48/admin/.git/refs/tags -> REDIRECTS TO: http://10.10.10.48/admin/.git/refs/tags/
200 274B http://10.10.10.48/admin/.git/config
301 0B http://10.10.10.48/admin/.git/refs/remotes/origin -> REDIRECTS TO: http://10.10.10.48/admin/.git/refs/remotes/origin/
301 0B http://10.10.10.48/admin/.git/refs/heads -> REDIRECTS TO: http://10.10.10.48/admin/.git/refs/heads/
200 11KB http://10.10.10.48/admin/.git/index
200 240B http://10.10.10.48/admin/.git/info/exclude
200 1KB http://10.10.10.48/admin/.github/PULL_REQUEST_TEMPLATE.md
200 182B http://10.10.10.48/admin/.git/logs/refs/remotes/origin/HEAD
200 182B http://10.10.10.48/admin/.git/logs/refs/heads/master
200 182B http://10.10.10.48/admin/.git/logs/HEAD
200 153B http://10.10.10.48/admin/.gitignore/
200 153B http://10.10.10.48/admin/.gitignore
200 73B http://10.10.10.48/admin/.git/description
301 0B http://10.10.10.48/admin/.git/logs/refs/heads -> REDIRECTS TO: http://10.10.10.48/admin/.git/logs/refs/heads/
200 41B http://10.10.10.48/admin/.git/refs/heads/master
301 0B http://10.10.10.48/admin/.git/logs/refs/remotes/origin -> REDIRECTS TO: http://10.10.10.48/admin/.git/logs/refs/remotes/origin/
200 32B http://10.10.10.48/admin/.git/refs/remotes/origin/HEAD
200 107B http://10.10.10.48/admin/.git/packed-refs
200 1KB http://10.10.10.48/admin/.github/ISSUE_TEMPLATE.md
200 648B http://10.10.10.48/admin/.pullapprove.yml
200 186B http://10.10.10.48/admin/api.php
200 846B http://10.10.10.48/admin/CONTRIBUTING.md
200 14KB http://10.10.10.48/admin/debug.php
301 0B http://10.10.10.48/admin/img -> REDIRECTS TO: http://10.10.10.48/admin/img/
200 14KB http://10.10.10.48/admin/LICENSE
200 2KB http://10.10.10.48/admin/README.md
301 0B http://10.10.10.48/admin/scripts -> REDIRECTS TO: http://10.10.10.48/admin/scripts/
200 14KB http://10.10.10.48/admin/settings.php
301 0B http://10.10.10.48/admin/style -> REDIRECTS TO: http://10.10.10.48/admin/style/发现该目录存在Git源码泄露问题,使用GitHack工具下载其源代码,失败。
Web应用程序(32400端口)
打开主页:http://10.10.10.48:32400/
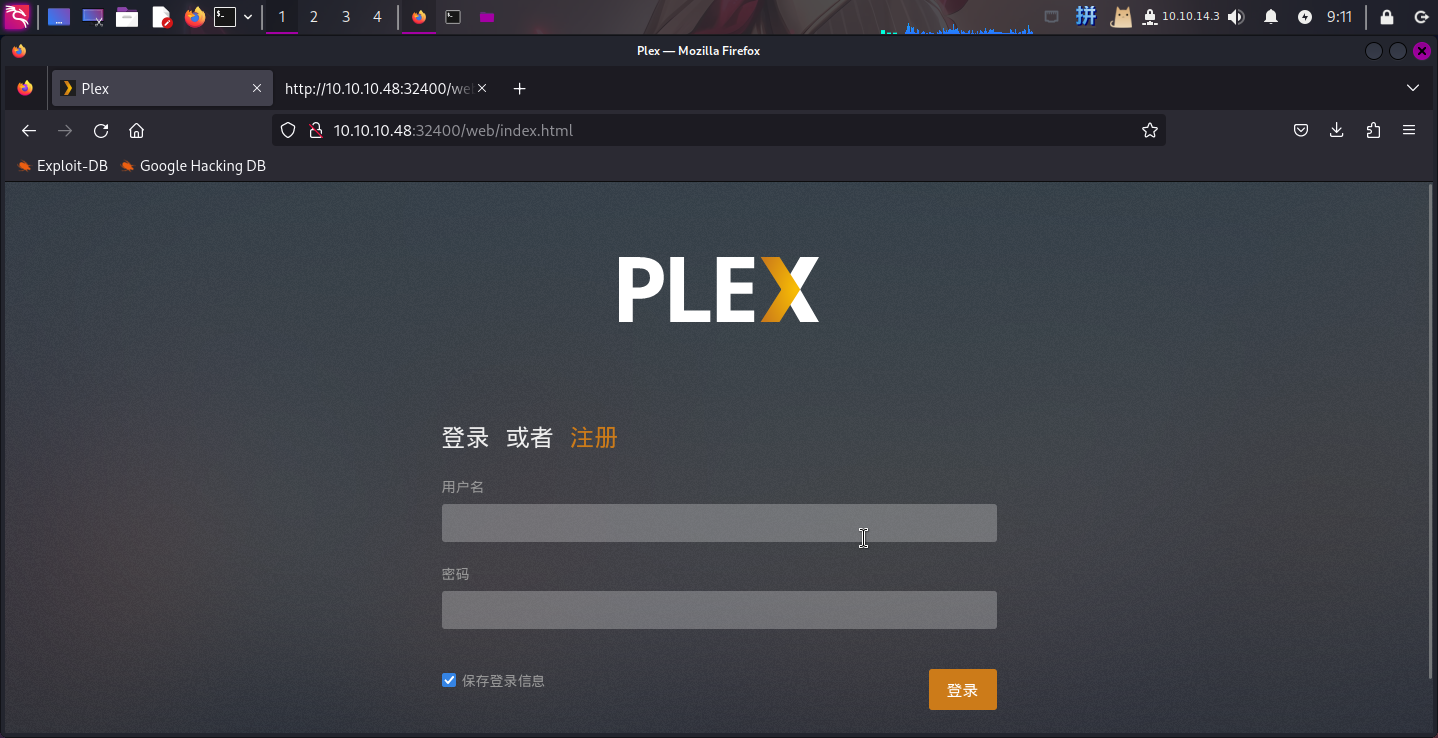
发现部署了Plex网络媒体管理系统,但版本未知。
尝试注册用户,登录之后转到设置界面,发现版本为v3.9.1,没有对应的漏洞:
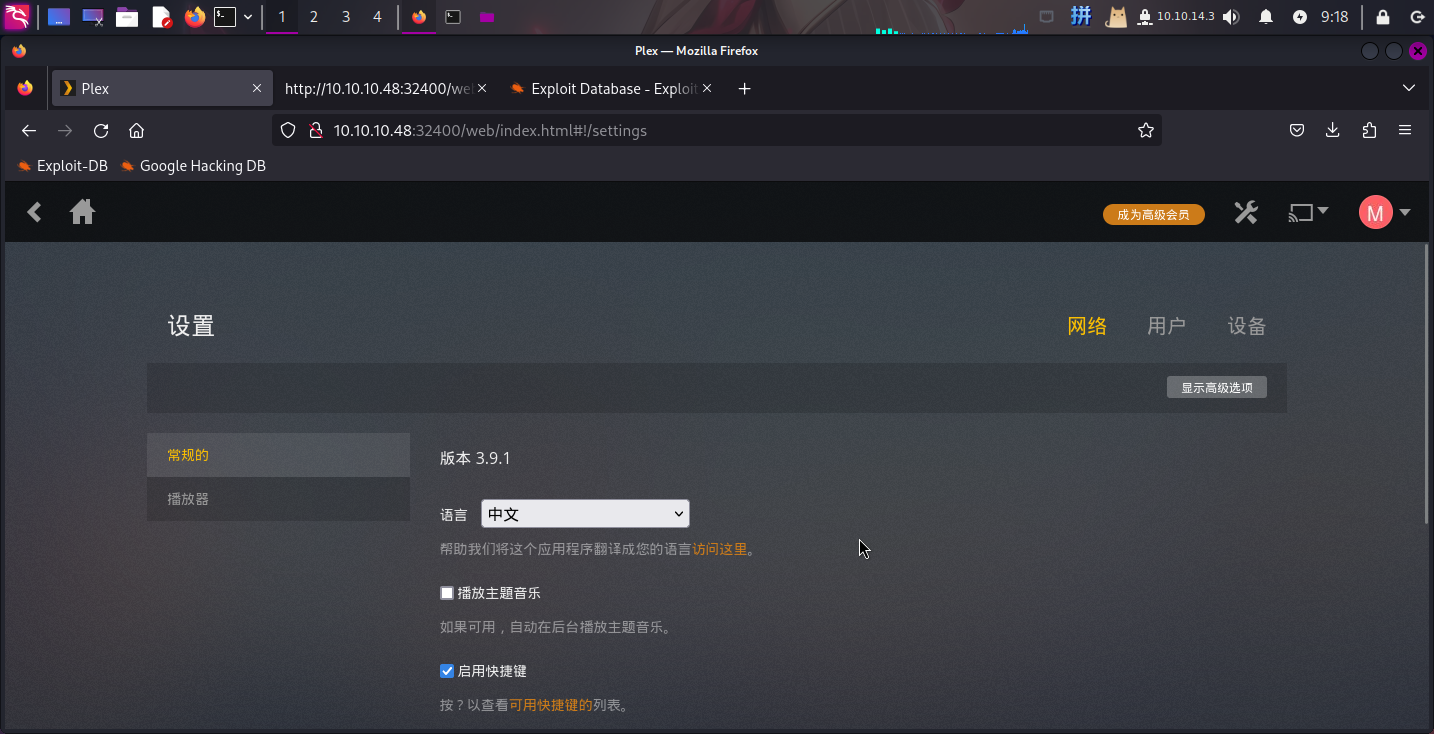
尝试扫描目录,没有发现敏感信息。
渗透测试
猜测SSH用户名密码
根据前期收集到的信息,推断靶机是树莓派设备,因为Pi-Hole只能在树莓派上运行,一般这种设备会被作为内网软路由和网关使用。
尝试使用树莓派默认的登录凭据登录SSH:
- 用户名:
pi - 密码:
raspberry
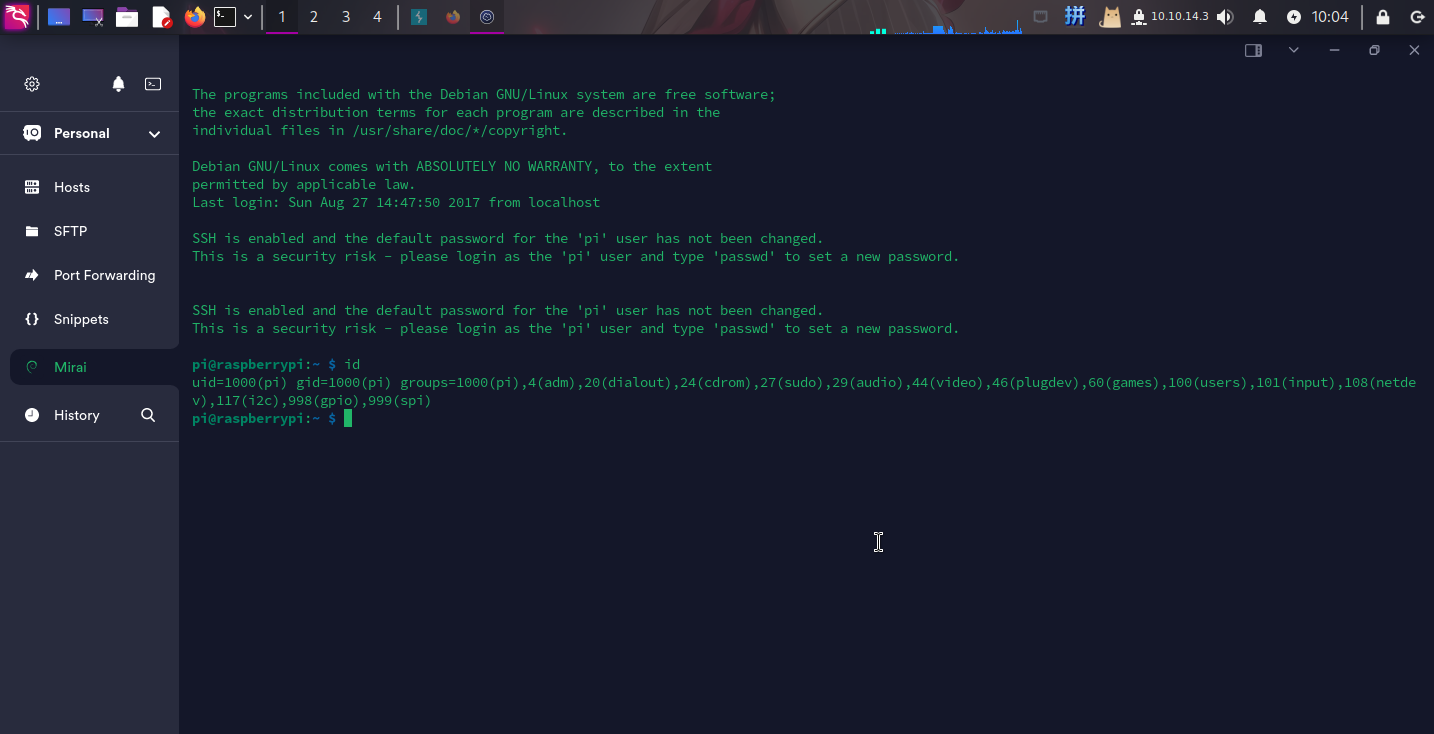
成功!!!
权限提升
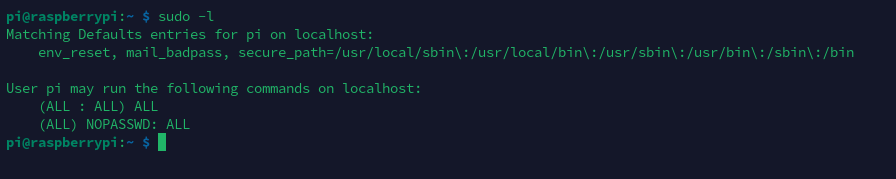
Sudo提权
登录系统之后,发现当前用户pi可以直接以root身份免密运行所有命令:
直接切换用户到root:
sudo su -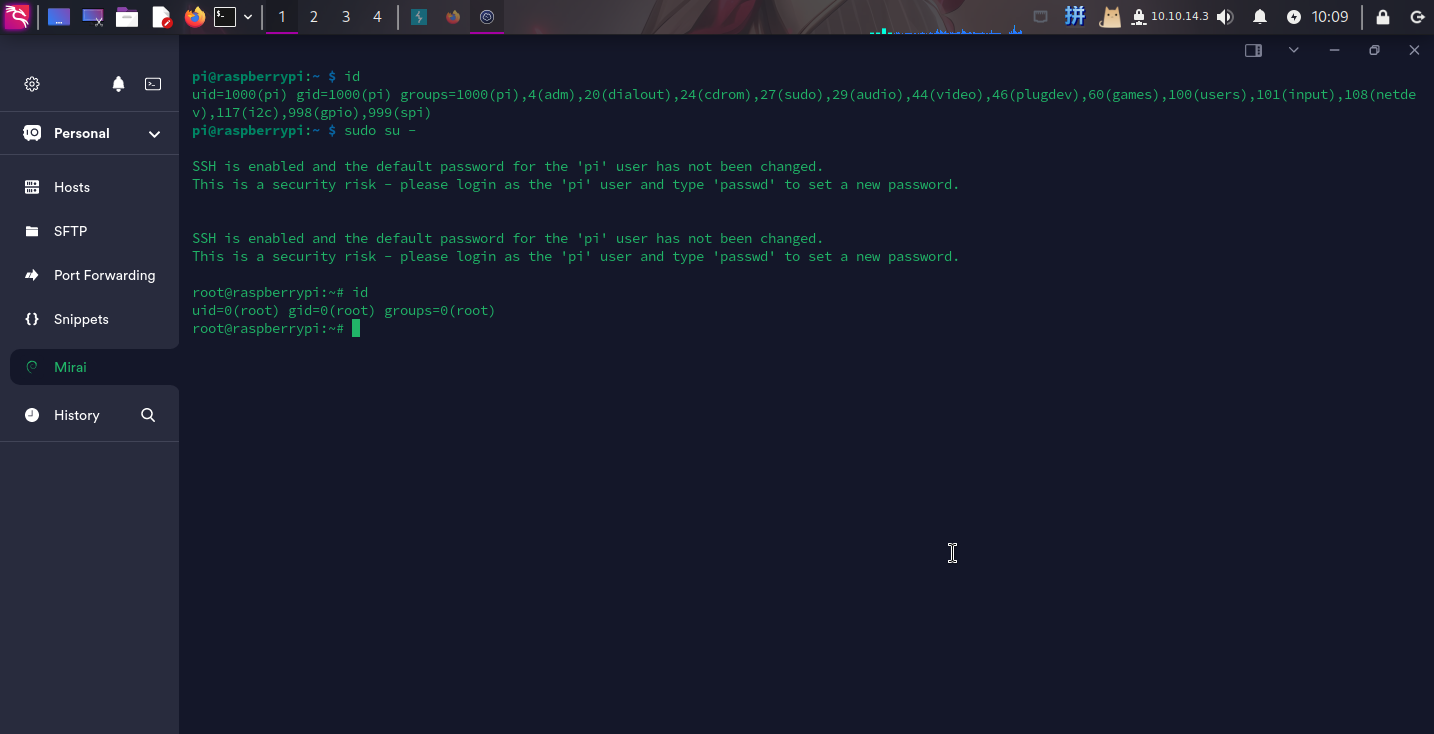
提权成功!!!!
Flag文件展示
注:该Flag使用
strings /dev/sdb找到。登录root后,发现家目录下的Flag提示真正的Flag在USB挂载目录下,经过寻找,发现有/media/usbstick目录,挂载盘为/dev/sdb,使用strings命令列出可打印的字符串后找到Flag。
3d3e483143ff12ec505d026fa13e020b





